
Implementation of WireGuard and L2TP/IPSec with DNS Sinkhole
Using Raspberry Pi
M. Luthfan Putra Sopian
1
, Dimas Febriyan Priambodo
1
, Arizal
1
, Mohamad Syahral
2
, Jacob Lumbantoruan
1
and Rheva Anindya Wijayanti
3
1
Cyber Security Engineering, National Cyber and Crypto Polytechnic, Ciseeng, Bogor Regency, Indonesia
2
Crypto Hardware Engineering, National Cyber and Crypto Polytechnic, Ciseeng, Bogor Regency, Indonesia
3
Crypto Software Engineering, National Cyber and Crypto Polytechnic, Ciseeng, Bogor Regency, Indonesia
Keywords: DNS Sinkhole, Raspberry Pi, VPN.
Abstract: The increasing use of Virtual Private Networks (VPNs) highlights their importance in securing
communication over public networks. However, most VPN services still provide only basic features and lack
advanced protection against evolving internet threats. This research develops a VPN prototype integrated with
a DNS sinkhole to block unwanted content and enable parental controls, enhancing both user security and
experience. The system is implemented on a Raspberry Pi for its compact size, low power usage, and sufficient
computational performance. The prototype supports IPv6 connectivity through WireGuard, addressing IPv4
exhaustion, and is developed using a modified SDLC waterfall method. Functionality and performance were
evaluated through Quality of Service (QoS) metrics, including bandwidth, delay, jitter, packet loss, and
throughput. Experimental results show that WireGuard on a Raspberry Pi 3B achieved a “Very Good” QoS
index of 4.0 during file downloads, with 0 ms delay and 5.59 Mbps throughput, outperforming L2TP/IPSec,
thereby providing a practical, scalable, and secure VPN solution.
1 INTRODUCTION
A Virtual Private Network (VPN) enables private,
encrypted communication over public networks and
is widely used to provide secure, cost-efficient access
to organizational resources (Li, 2025; Dahnial, 2019).
It is widely used to ensure secure, low-cost access to
information resources (Taib, 2020; Jyothi & Reddy,
2018).
Various VPN protocols offer different trade-offs:
PPTP is easy but insecure, SSTP is secure but
complex, and IPSec with L2TP provides end-to-end
encryption but may reduce performance (Rasuanda &
Haeruddin, 2020; Thiruvasagam & George, 2019).
WireGuard, a newer protocol, offers better efficiency,
simplicity, and strong security (Dekker & Spaans,
2020). While many VPN providers—such as
NordVPN and ProtonVPN—still rely on IPv4, only a
few support IPv6 effectively, including Hide.me and
AirVPN (Cooper, 2023; Turki, 2024; Chapman,
2023). Comparative analyses of static and dedicated
IP VPNs also highlight the importance of stability for
modern applications (Cooper, 2023).
Despite their benefits, VPNs face threats like
MITM attacks, DNS hijacking, and malware
infections via Trojans and worms (Bansode &
Girdhar, 2021; Budhisantosa, 2016; Ibrahim,
Dewanta, & Cahyani, 2023). Prior studies show that
VPN infrastructures are also vulnerable to
misconfigurations and common exploits (Bansode &
Girdhar, 2021), while malware can propagate rapidly
through infected endpoints and removable storage if
not contained (Budhisantosa, 2016). Dynamic
analysis of malware samples further demonstrates the
evolving sophistication of malicious behavior
(Ibrahim et al., 2023). In August 2023, the National
Cyber and Crypto Agency of Indonesia (Badan Siber
dan Sandi Negara [BSSN]) recorded over 7 million
anomalies related to phishing and malware (BSSN,
2023). To enhance network security, techniques like
DNS Sinkhole can block malicious domains using
blocklists (Marta, Achmad Daengs, Daniar, Seprina,
& Menayang, 2019).
Previous research has explored VPN deployment
on Raspberry Pi and the use of DNS Sinkholes to
improve browsing security (Taib, 2020). However,
Sopian, M. L. P., Priambodo, D. F., Arizal, , Syahral, M., Lumbantoruan, J. and Wijayanti, R. A.
Implementation of WireGuard and L2TP/IPSec with DNS Sinkhole Using Raspberry Pi.
DOI: 10.5220/0014272500004928
Paper published under CC license (CC BY-NC-ND 4.0)
In Proceedings of the 1st International Conference on Research and Innovations in Information and Engineering Technology (RITECH 2025), pages 129-135
ISBN: 978-989-758-784-9
Proceedings Copyright © 2025 by SCITEPRESS – Science and Technology Publications, Lda.
129

few studies compare the performance of WireGuard
and L2TP/IPSec when integrated with DNS Sinkhole
on Raspberry Pi. This research addresses that gap by
developing a VPN prototype with a GUI, DNS
Sinkhole, and SIEM (Wazuh stack) integration,
aimed at delivering a secure, user-friendly
environment with parental control features.
Raspberry Pi was chosen for its compact size, low
power usage, and adequate performance, supported
by a large community and hardware availability
(Taib, 2020). The result is a practical, low-cost, and
flexible solution that supports future development
and broad accessibility.
Several comparative studies of commercial VPN
services have also highlighted this limitation. For
instance, Turki (2024) and Chapman (2023)
emphasize that while many VPN providers focus
primarily on tunneling protocols and speed
optimization, they rarely integrate advanced
protective features such as DNS filtering, malware
blocking, or parental controls. Similarly, Dekker and
Spaans (2020) demonstrated that the majority of
widely used VPN solutions—including OpenVPN
and IPSec- based services—prioritize connectivity
and performance rather than comprehensive security
mechanisms. This indicates that the current
commercial VPN ecosystem remains insufficient in
addressing evolving cyber threats, thereby justifying
the need for research on VPN prototypes that
incorporate additional protective layers such as DNS
sinkholes and SIEM integration.
2 METHODOLOGY
The object of this research is to implement VPN
WireGuard, L2TP/IPSec, and DNS Sinkhole on a
Raspberry Pi. The analysis will be carried out based
on Quality of Service (QoS) parameters, which
include bandwidth, delay, jitter, packet loss, and
throughput. In addition, an analysis will be conducted
on the resource usage in the prototype, resulting in the
minimum requirements for this prototype. This
research utilizes the System Development Life Cycle
(SDLC) waterfall, which aligns with the requirements
for developing this prototype. This method consists
of the Planning, Analysis, Design, and
Implementation stages. In this model, each stage must
be completed before proceeding to the next stage. The
advantages gained through this model involve
gradual and systematic system development,
resulting in a sound system with a minimal number of
errors. In addition, the resulting documentation will
be well-organised. The following is an explanation of
each stage in the waterfall approach.
In this study, a modified version of the classical
SDLC waterfall model was applied to accommodate
the iterative nature of system prototyping. While the
traditional waterfall method progresses strictly in
sequential phases—planning, analysis, design,
implementation, and testing—the modified approach
used here incorporates feedback loops at each stage.
For example, after the implementation stage, results
from unit and integration testing were used to refine
the design and adjust system requirements, thereby
reducing the risk of critical errors being identified
only at later stages.
This adjustment is particularly relevant for
research involving network security systems, where
rapid changes in configuration and performance
validation are necessary. Similar adaptations of the
waterfall method have been employed in networking
and security projects to balance the benefits of
structured documentation with the flexibility of
iterative refinement (Marta et al., 2019). Compared
with agile methods, the modified waterfall model
ensures comprehensive documentation and
systematic progression while still allowing backward
transitions to improve the prototype. Thus, the chosen
methodology provides both rigor and adaptability,
aligning well with the objectives of developing a
secure and stable VPN prototype on Raspberry Pi.
2.1 Planning Stage
The System Development Life Cycle (SDLC) begins
with the planning stage, which aims to define the
purpose of system development and how it will be
carried out. This stage consists of two main steps. The
first is project initiation, which determines the
direction of the research by identifying the system's
benefits and needs. At this stage, a literature review is
conducted on key technologies relevant to the study,
such as the WireGuard VPN protocol, L2TP/IPSec,
DNS Sinkhole, and the Raspberry Pi device. The
gathered information is then compared with the
technical specifications of the Raspberry Pi to assess
its feasibility for implementation. The second step is
research planning, which involves preparing research
elements, including ideas, background, problem
formulation, system overview, and the sequential
steps to be taken during the development process.
2.2 Analysis Stage
The analysis stage focuses on identifying system
users, core functionalities, and operational contexts
RITECH 2025 - The International Conference on Research and Innovations in Information and Engineering Technology
130
such as usage time and location. It involves gathering
and analysing data related to user needs, system
goals, and environmental factors. This phase defines
both functional and non-functional requirements,
along with the necessary hardware and software
specifications to support system prototyping and
fulfill research objectives.
2.2.1 Network Topology
The prototype was built in a standalone network
environment using an internet source from a mobile
hotspot. This network uses the private IP
192.168.173.0/24 and IPv6 2404:c0:202d:7090::/64.
The laptop, acting as the client, and the Raspberry Pi,
acting as the server, are connected through the same
network. The topology design of this network is
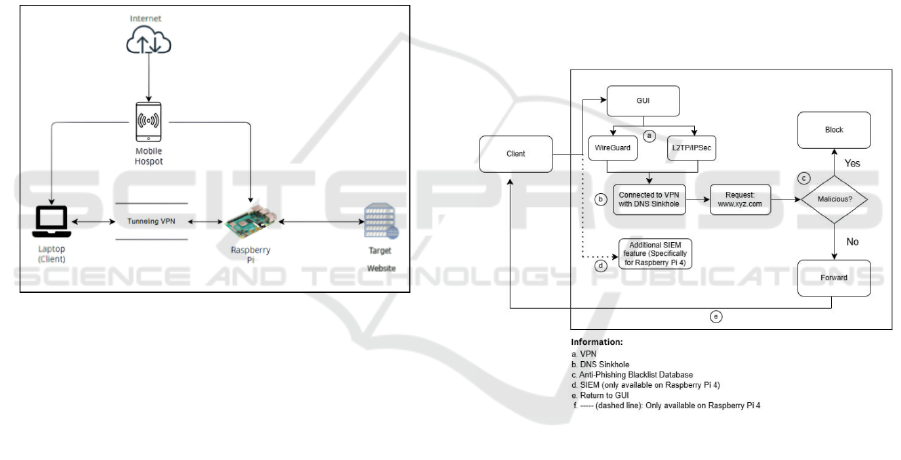
shown in Figure 1.
Figure 1: Network Topology Design.
2.2.2 System Overview Details
The decision to combine WireGuard with
L2TP/IPSec in this research is based on the
complementary strengths of both protocols. While
WireGuard offers superior efficiency, simplicity, and
modern cryptographic design, its relatively recent
adoption has resulted in limited compatibility with
legacy systems and some enterprise-grade
infrastructures (Dekker & Spaans, 2020). Conversely,
L2TP/IPSec, although less efficient, is widely
supported across operating systems and network
devices, making it an essential protocol for ensuring
interoperability in heterogeneous environments
(Thiruvasagam & George, 2019).
The decision to combine WireGuard with
L2TP/IPSec in this research is based on the
complementary strengths of both protocols. While
WireGuard offers superior efficiency, simplicity, and
modern cryptographic design, its relatively recent
adoption has resulted in limited compatibility with
legacy systems and some enterprise- grade
infrastructures (Dekker & Spaans, 2020). Conversely,
L2TP/IPSec, although less efficient, is widely
supported across operating systems and network
devices, making it an essential protocol for ensuring
interoperability in heterogeneous environments
(Thiruvasagam & George, 2019). A hybrid approach
therefore leverages WireGuard’s performance
advantages while maintaining backward
compatibility through L2TP/IPSec. Similar strategies
have been suggested in VPN deployment studies,
where multi- protocol integration ensures broader
device support, enhanced reliability, and fallback
options in case one protocol is blocked or degraded
by restrictive networks (Jyothi & Reddy, 2018;
Rasuanda & Haeruddin, 2020). This combination
thus provides not only improved security and
performance, but also greater flexibility and
resilience compared to relying solely on WireGuard.
Figure 2: System overview.
A hybrid approach therefore leverages
WireGuard’s performance advantages while
maintaining backward compatibility through
L2TP/IPSec. Similar strategies have been suggested
in VPN deployment studies, where multi- protocol
integration ensures broader device support, enhanced
reliability, and fallback options in case one protocol
is blocked or degraded by restrictive networks (Jyothi
& Reddy, 2018; Rasuanda & Haeruddin, 2020). This
combination thus provides not only improved
security and performance but also greater flexibility
and resilience compared to relying solely on
WireGuard. Figure 2 is an overview of the system that
will be used in this research.
Implementation of WireGuard and L2TP/IPSec with DNS Sinkhole Using Raspberry Pi
131

The system includes several main components:
a. VPN
The VPN operates using either WireGuard or
L2TP/IPSec protocols to establish a secure
connection. The VPN secures communication
between the user's device and the internet by
encrypting data at the client side, transmitting it
through a secure tunnel to the VPN server, and then
decrypting it before reaching the internet. The return
traffic follows the same encrypted path in reverse.
This process ensures that all transmitted data remains
confidential and protected from interception or cyber
threats.
b. DNS Sinkhole
The DNS Sinkhole mechanism prevents access
to malicious domains by redirecting DNS requests to
the sinkhole IP address and logging the activity in a
log for further analysis.
c. Repository Blacklist Anti-Phishing Feature
DNS Sinkhole uses blocklists to block access to
phishing sites, ensuring that clients cannot access
malicious sites.
d. SIEM Server
The SIEM Server design uses software such as
Wazuh, Filebeat, Elasticsearch, and Kibana to
collect, store, and analyze logs, and display data
visualizations through interactive dashboards.
e. GUI
After logging in, users can access settings menus
such as peer configuration, accounts, security, and
dashboard display. The “Config (wg0)” menu allows
users to add, delete, and download peer
configurations as well as network diagnostics.
Meanwhile, the “Pi-Hole” menu provides access to
the dashboard, query logs, domain management,
block lists, local DNS, and other settings. This GUI is
designed to simplify the structured and efficient
management of VPN and DNS filtering.
2.3 Implementation Stage
The implementation involved several key security
components deployed on a Raspberry Pi. First, Pi-
hole was configured as a DNS Sinkhole to block
access to malicious domains using a regularly
updated blocklist. Next, WireGuard is installed as the
primary VPN server, with L2TP/IPSec set up as an
additional option, involving both secure key
generation and user authentication. To enhance
phishing protection, a repository-based blocklist of
phishing domains is integrated into the DNS
Sinkhole, automatically blocking dangerous URLs
and redirecting users to a warning page. This setup is
continuously monitored and tested to ensure its
effectiveness. For centralized monitoring and event
analysis, a lightweight SIEM solution is deployed
using Wazuh, Filebeat, Elasticsearch, and Kibana, all
tailored to work efficiently on Raspberry Pi 4
hardware. Finally, a user-friendly GUI is developed
using Flask, PHP, HTML, and Bootstrap, providing
an intuitive interface for administrators to manage
VPN services and monitor network activity.
2.4 Unit and Integration Testing
Unit testing was performed on all system components
and showed that VPN (WireGuard and L2TP/IPsec),
DNS Sinkhole, and anti-phishing features work well.
The SIEM system (Wazuh, Elasticsearch, Kibana,
Filebeat) has been successfully integrated and
displays relevant information via the dashboard. The
user interface (GUI) also functions optimally,
supporting login features, peer management, VPN
server control, and QR code generation. Integration
testing ensures that all GUI and backend features
work correctly according to specifications,
demonstrating stable system integration and
workflow compliance.
2.5 Unit and Integration Testing
Performance and system testing indicate that the
prototype has successfully met its objectives as an
efficient and reliable network security solution. In
terms of performance, the Raspberry Pi 4B offers the
highest computational capability but with the highest
resource consumption, while the Raspberry Pi Zero
W exhibits processing limitations, especially when
using the WireGuard protocol. The Raspberry Pi 3B
is considered the most ideal option, providing a
balanced combination of efficiency and stability.
The scalability of implementing VPN and DNS
Sinkhole services on Raspberry Pi is an important
consideration for broader deployment. Raspberry Pi
devices are cost- effective, compact, and energy-
efficient, making them attractive for small- to
medium-scale applications such as home networks,
small businesses, and educational environments.
Prior studies (Taib, 2020; Dahnial, 2019) have shown
that Raspberry Pi-based VPN solutions can handle
moderate traffic loads efficiently, provided that the
number of concurrent users and the overall bandwidth
requirements remain within the device’s processing
limits.
RITECH 2025 - The International Conference on Research and Innovations in Information and Engineering Technology
132
However, as the number of users or the volume of
encrypted traffic increases, resource constraints such
as CPU utilization, memory, and network interface
throughput become more pronounced. For instance,
WireGuard sessions scale well on Raspberry Pi 3B
and 4B for up to several dozen clients, but heavy
enterprise-scale deployment would require clustering
or migration to more powerful hardware. The
modular nature of Raspberry Pi also allows horizontal
scaling by deploying multiple devices in parallel,
with centralized management through SIEM or
orchestration tools. Therefore, while Raspberry Pi
offers practical scalability for lightweight to mid-
scale scenarios, its role in large-scale or high-
bandwidth enterprise environments is best suited as a
complementary edge security device rather than a
primary backbone solution.
Functionally, the system effectively implements
key features such as VPN protocols, DNS Sinkhole,
SIEM integration, and connection management.
From a non- functional perspective, it includes a user-
friendly graphical interface (GUI), a QR Code feature
for quick configuration, and informative DNS
statistics. These testing results confirm that the
prototype operates reliably across all components and
fulfills the defined system requirements.
2.6 QoS Testing
Quality of Service (QoS) testing was conducted using
various activities with IPv4 and IPv6 protocols. To
interpret the numerical QoS values into qualitative
categories, this study refers to the TIPHON/ETSI
classification. Table 1 presents the classification for
delay, jitter, packet loss, and throughput, each
mapped to a QoS index (1–4). This index is then used
to determine the overall quality labels such as
Moderate, Good, or Very Good.
For IPv4, both WireGuard and L2TP/IPSec
demonstrated measurable Quality of Service (QoS)
values. For instance, YouTube streaming tests on
Raspberry Pi 4B with WireGuard produced an
average delay of 10 ms, jitter of 10 ms, packet loss of
0.11%, and throughput of 1.2 Mbps. According to the
TIPHON/ETSI QoS classification (Table X), these
correspond to indices of Delay = 4, Jitter = 3, Packet
Loss = 4, Throughput = 3, yielding a mean QoS index
of 3.5, categorized as “Good.” In contrast, file
download tests under the same conditions showed
delay of 0 ms, jitter of 0 ms, packet loss of 0.07%, and
throughput of 5.59 Mbps, mapping to all indices = 4.
The mean QoS index is 4.0, corresponding to “Very
Good.”
Table 1: QoS Classification Based on TIPHON/ETSI
Standard.
Parameter Very Goo
d
Good Moderate Poor
Delay
<150
ms
150-
300 ms
300-450
ms
>450
ms
Jitter 0 ms
0-75
ms
75-125
ms
125-
225 ms
Packet Loss
0-2% 3-14% 15-24% >25%
Throughput
>2.1
Mbps
1.2-2.1
Mbps
0.7-1.2
Mbps
<0.7
Mbps
In IPv6 testing with WireGuard, performance was
deemed satisfactory despite lower throughput
compared to IPv4. The Raspberry Pi Zero W
exhibited the least stable QoS performance among
the tested devices. Figures 3–7 provide a visual
overview of the QoS testing results across different
Raspberry Pi models and VPN protocols.
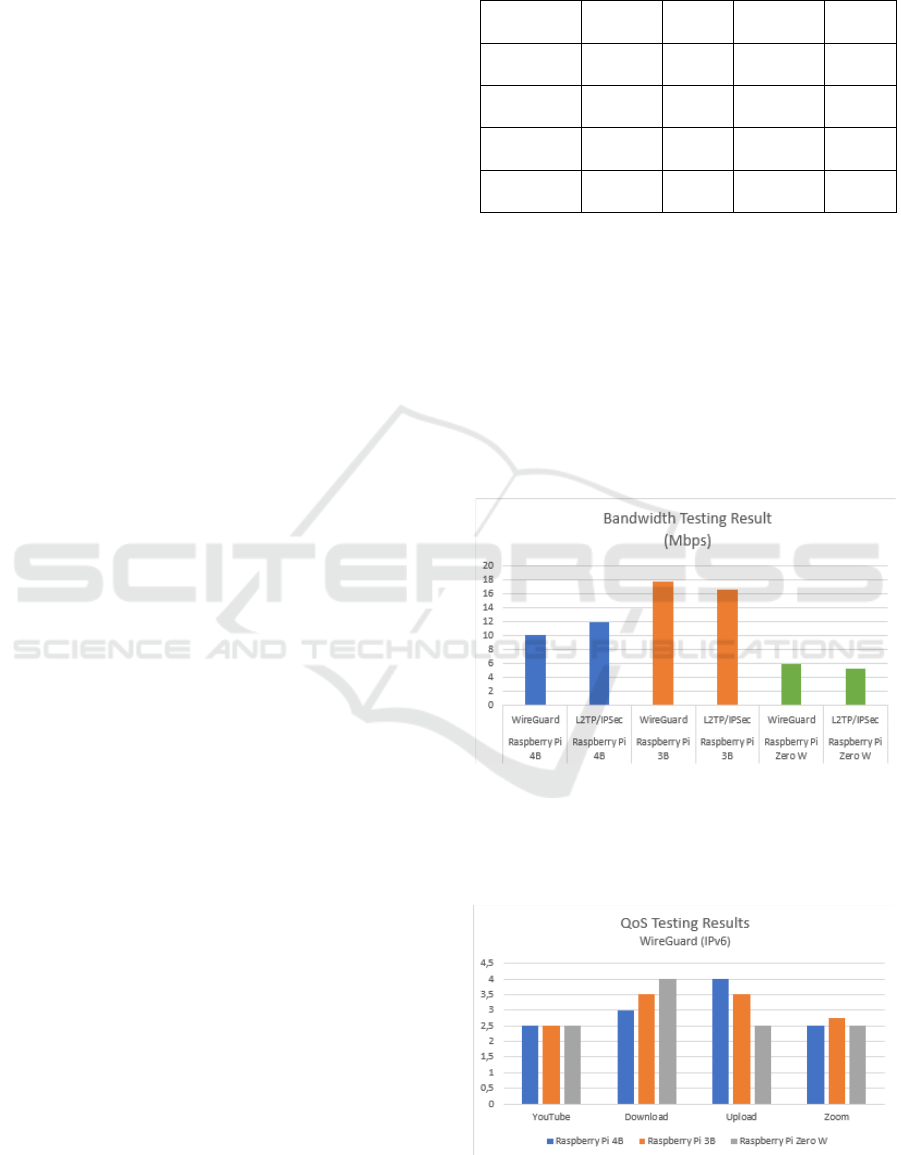
•
Figure 3 illustrates the bandwidth performance,
highlighting how L2TP/IPSec slightly outperforms
WireGuard on the Raspberry Pi 4B, while
WireGuard achieves better results on the 3B.
Figure 3: Bandwidth Testing Results.
•
Figure 4 presents QoS scores under IPv6 conditions,
showing consistent performance across all models,
with the Raspberry Pi Zero W excelling in download
scenarios.
Figure 4: QoS Testing Results on WireGuard IPv6.
Implementation of WireGuard and L2TP/IPSec with DNS Sinkhole Using Raspberry Pi
133
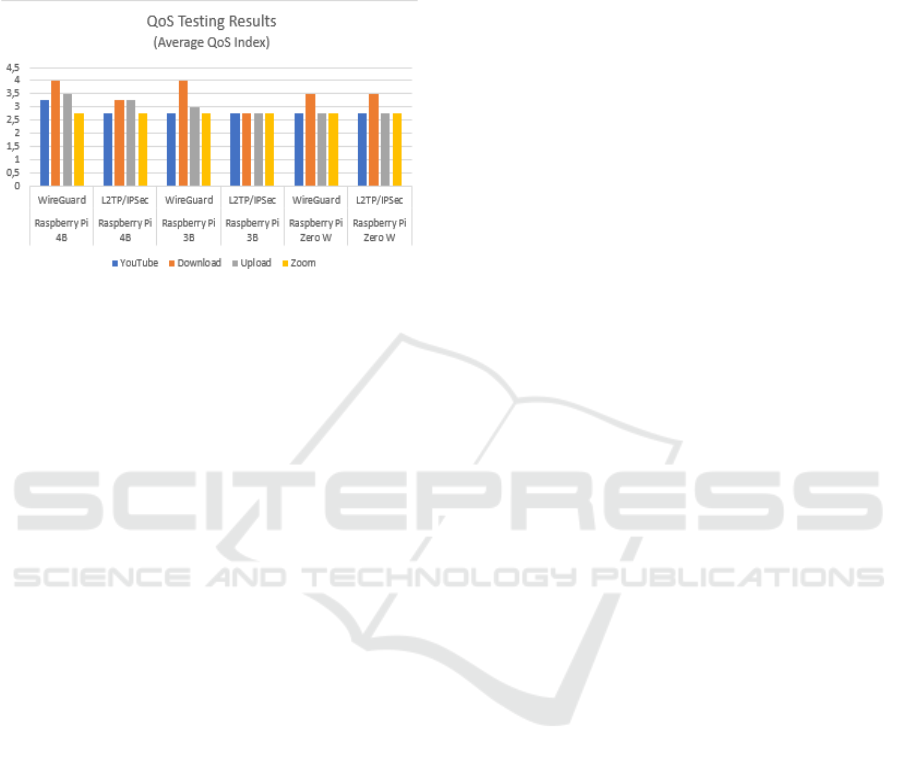
•
Figure 5 summarizes the average QoS index across
key activities (YouTube, download, upload, Zoom),
confirming that WireGuard delivers overall better
QoS, particularly on the Raspberry Pi 3B.
Figure 5: Bandwidth Testing Results.
Overall, Quality of Service (QoS) test results
show that the WireGuard protocol performs better
than L2TP/IPSec, especially when downloading. The
Raspberry Pi 3B was the most stable and efficient. At
the same time, for the IPv6 protocol, performance
remained reliable, with the Raspberry Pi Zero W
excelling at downloading and the Pi 4B excelling at
uploading. A comparison between IPv4 and IPv6
shows that WireGuard consistently delivers good
performance on both protocol versions. Overall, the
Raspberry Pi 3B and 4B provide the best
performance in various scenarios, while Raspberry Pi
Zero W is suitable for download activities. Therefore,
the choice of Raspberry Pi model can be tailored to
the dominant type of network activity to achieve
optimal QoS. Although IPv4 is still widely used,
testing demonstrates that WireGuard implementation
on IPv6 continues to provide reliable performance
and offers advantages such as a larger address space,
improved routing efficiency, and enhanced security.
3 CONCLUSIONS
The results of the device performance testing show
that Raspberry Pi 3B is the ideal choice for the
implementation of WireGuard or L2TP/IPSec VPN
protocols with DNS Sinkhole. The Raspberry Pi 3B
offers a good balance between performance and
resource efficiency compared to the other models.
The Raspberry Pi 4B, although providing higher
performance, has significant resource consumption,
while the Raspberry Pi Zero W shows limited CPU
performance in terms of available device resources.
The implementation of DNS Sinkhole, both with
WireGuard and combined with L2TP/IPSec on all
Raspberry Pi models, successfully blocks non-
essential DNS queries. From the QoS point of view,
WireGuard VPN protocol shows better QoS
performance compared to L2TP/IPsec in various
parameters such as bandwidth, jitter, delay, packet
loss, and throughput. It is evident from the tests that
WireGuard excels in terms of bandwidth, ranking
first. In addition, in the download, upload, and
YouTube tests, WireGuard still outperforms
L2TP/IPSec in terms of QoS. In addition, IPv6 testing
has also been conducted, and WireGuard still shows
reliable performance, although IPv4 still outperforms
in terms of results.
REFERENCES
Badan Siber dan Sandi Negara. (2023). Laporan bulanan
publik hasil monitoring keamanan siber.
https://cloud.bssn.go.id/s/GgpKGGGSDzLE5go
Bansode, R., & Girdhar, A. (2021). Common
vulnerabilities exposed in VPN – A survey. Journal of
Physics: Conference Series, 1714(1).
https://doi.org/10.1088/1742-6596/1714/1/012045
Budhisantosa, N. (2016). Optimasi Access Control List
sebagai bagian reaksi cepat tanggap atas gangguan
infeksi malware Skypee pada media penyimpanan
jaringan komputer pada PT. Forum Ilmiah, 13(1), 32.
Chapman, S. (2023, December 14). The best IPv6 VPN in
2023: IPv4 & IPv6 support. Cloudwards.
https://www.cloudwards.net/best-ipv6-
vpn/#:~:text=Do%20VPNs%20Work%20on%20IPv6,
risk%20when%20not%20properly%20supported
Cooper, S. (2023, December 14). Best VPNs for static and
dedicated IPs in 2023: Stabilize connections.
Comparitech. https://www.comparitech.com/blog/vpn-
privacy/vpn-dedicated-ip-static-ip/
Dahnial, D. (2019). Analisa perbandingan Quality of
Service antara protokol PPTP dan L2TP pada Virtual
Private Network berbasis router Mikrotik. Jurnal Ilmiah
Informatika Global, 10(2).
https://doi.org/10.36982/jiig.v10i2.858
Dekker, E., & Spaans, P. (2020). Performance comparison
of VPN implementations WireGuard, strongSwan, and
OpenVPN in a 1 Gbit/s environment.
Ibrahim, K., Dewanta, F., & Cahyani, N. E. W. (2023).
Analisis perilaku malware menggunakan metode
analisis dinamis. e-Proceeding of Engineering, 10,
4122–4125.
Jyothi, K. K., & Reddy, D. I. B. (2018). Study on Virtual
Private Network (VPN), VPN’s protocols and security.
International Journal of Scientific Research in
Computer Science, Engineering and Information
Technology, 3, 919–932.
Li, J., Feng, B., & Zheng, H. (2025). A survey on VPN:
Taxonomy, roles, trends and future directions.
Computer Networks, 257, 110964.
https://doi.org/10.1016/j.comnet.2024.110964
RITECH 2025 - The International Conference on Research and Innovations in Information and Engineering Technology
134

Marta, R. F., Achmad Daengs, G. S., Daniar, A., Seprina,
W. O., & Menayang, A. P. (2019). Information security
risk and management in organizational network.
International Journal of Engineering and Advanced
Technology, 8(6, Special Issue 2).
https://doi.org/10.35940/ijeat.F1286.0886S219
Rasuanda, M., & Haeruddin. (2020). Perbandingan
performa VPN menggunakan PPTP dan SSTP over
SSL dengan metode Quality of Service. Journal of
Information Systems and Technology, 1(2), 110–123.
Retrieved from
https://journal.uib.ac.id/index.php/joint/article/downlo
ad/4314/1116
Taib, M. (2020). Securing network using Raspberry Pi by
implementing VPN, Pi-Hole, and IPS (VPiSec).
International Journal of Advanced Trends in Computer
Science and Engineering, 9(1.3), 457–464.
https://doi.org/10.30534/ijatcse/2020/7291.32020
Thiruvasagam, P., & George, K. J. (2019). IPSec:
Performance analysis in IPv4 and IPv6. Journal of ICT
Standardization, 7(1), 59–76.
https://doi.org/10.13052/jicts2245-800X.714
Turki, O. (2024). A comparison of VPN providers focusing
on their security and speed.
Implementation of WireGuard and L2TP/IPSec with DNS Sinkhole Using Raspberry Pi
135
