
Optimization of Audit Daemon for Preventing Ransomware Attacks
on Linux Servers
Jacob Lumbantoruan, Bimo Makarim, Nanang Trianto and Kiko Wahyudi Setiawan
Department of Cyber Security Engineering, National Cyber and Crypto Polytechnic, Bogor, West Java, Indonesia
Keywords: Ransomware, Linux, Auditd, VirusTotal, Ubuntu.
Abstract: This Ransomware is one of the growing cybersecurity threats, causing financial losses and operational
disruptions. This study aims to develop a ransomware detection and response system in a Linux environment
by utilizing Auditd as a process monitoring tool. The system is designed to detect suspicious programs using
Auditd, analyze them through VirusTotal to verify whether the programs are ransomware, and automatically
terminate processes detected as ransomware. Testing was conducted on three versions of Ubuntu (18.04, 20.04,
and 22.04) using four ransomware samples: Shougolock, AvosLocker, InterLock, and MarioLocker. The
evaluation parameters used were Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR). The
test results showed that the system was able to detect ransomware with an average MTTD of 503.7 ms and
respond with an average MTTR of 15.8 ms consistently across all Ubuntu versions. Ubuntu 20.04
demonstrated the best performance in detection, while Ubuntu 18.04 excelled in response speed. These results
demonstrate that the developed system is effective in detecting and addressing ransomware threats across
various Ubuntu environments, with potential for further improvement through configuration optimization and
integration of additional security tools.
1 INTRODUCTION
Ransomware attacks pose a major threat to computer
security, including for users of Linux-based server
systems. These attacks typically involve encrypting
critical data, followed by a ransom demand in
exchange for the decryption key. Over the past
decade, ransomware has evolved into an increasingly
sophisticated and financially damaging threat,
targeting not only individual users but also large
enterprises and critical infrastructure (Beaman et al.,
2021). In 2024, a ransomware incident in Indonesia
caused a national service disruption, where the threat
actors exploited the Pusat Data Nasional Sementara
(PDNS) containing critical data from multiple
government institutions. This incident highlights the
urgent need for proactive detection and response
mechanisms to effectively mitigate the impact of
ransomware attacks.
Reliance on traditional security solutions such as
antivirus software and Endpoint Detection and
Response (EDR) faces limitations in server
environments. Many server administrators prefer
vendor-based security products; however, these often
require substantial system resources and compel
organizations to entrust sensitive data to third parties,
raising concerns about privacy and data sovereignty
(Adkins et al., 2020). A safer alternative is leveraging
Auditd, a built-in Linux tool that provides a robust
and customizable system monitoring framework
without compromising control over confidential data.
The focus of this research is to explore methods
for optimizing Auditd in detecting ransomware
attacks. Although Auditd has strong logging
capabilities, its default configuration may be
insufficiently specific for identifying security threats,
including ransomware. Recent studies emphasize the
need for more targeted optimization to enhance
Auditd’s detection performance in Linux
environments (Guo et al., 2024; Neweva et al., 2024).
For example, leveraging file system characteristics
can improve the accuracy of ransomware detection
mechanisms (Guo et al., 2024), while integrating
forensic approaches such as memory and process
monitoring can strengthen real-time detection and
analysis of ransomware behavior (Neweva et al.,
2024). Without such optimization, the assumption
that Linux systems are inherently secure can create a
false sense of protection, potentially increasing
exposure to attacks (Golev et al., 2022).
114
Lumbantoruan, J., Makarim, B., Trianto, N. and Wahyudi Setiawan, K.
Optimization of Audit Daemon for Preventing Ransomware Attacks on Linux Servers.
DOI: 10.5220/0014266200004928
Paper published under CC license (CC BY-NC-ND 4.0)
In Proceedings of the 1st International Conference on Research and Innovations in Information and Engineering Technology (RITECH 2025), pages 114-121
ISBN: 978-989-758-784-9
Proceedings Copyright © 2025 by SCITEPRESS – Science and Technology Publications, Lda.

This study aims to design and validate an effective
approach to optimizing Auditd for ransomware
detection and response. By establishing benchmarks
using Mean Time to Detection (MTTD) and Mean
Time to Recovery (MTTR), this research evaluates
the effectiveness of the proposed improvements and
their applicability in real-world environments
(Alavian et al., 2021). The implementation of
automated scripts to send suspicious log data to
external analysis platforms, such as VirusTotal, is
expected to accelerate incident response and enhance
defense mechanisms against ransomware (Johnson et
al., 2024). Furthermore, proactive mitigation
measures—such as terminating processes exhibiting
malicious behavior—are introduced to minimize the
impact of detected ransomware activity.
To ensure robust validation, the proposed system
is tested across three Ubuntu versions: 18.04, 20.04,
and 22.04. The inclusion of multiple versions allows
for assessing detection consistency across different
kernel builds and default security configurations,
thereby offering insights into how system variation
influences ransomware detection and response.
Ubuntu 18.04 represents legacy server environments,
Ubuntu 20.04 provides a stable baseline for
performance comparison, and Ubuntu 22.04 delivers
the latest LTS release with enhanced security patches.
Collectively, these versions ensure that the evaluation
results remain relevant for both existing and modern
Linux-based infrastructures.
2 METHODOLOGY
The research design is based on knowledge applied in
the form of development, techniques and methods,
models, and theory development to produce products
that meet predetermined functional requirements. The
main aspect of research design or models is obtaining
reliable and valid information. This is because
reliability and validity depend on how the instruments
are used and what conclusions the researcher wants to
draw (Richey & Klein, 2014).
This study uses the Design Science Research
(DSR) methodology in designing technical guide
modules. DSR is a research method that focuses on
the design and development of technological products
with the aim of solving specific problems through
appropriate solutions. The resulting solutions must be
accountable and relevant to the problems to be solved.
The DSR methodology consists of five
interconnected stages: Problem Awareness, Proposal,
Development, Evaluation, and Conclusion. These
stages form a cycle that illustrates the relationship
between the process, knowledge flow, and results of
DSR, known as the DSR cycle (Venable, Pries-Heje,
& Baskerville, 2017).
Mean Time to Detect (MTTD) is an important
metric in various fields, especially in cybersecurity
and network traffic incident detection. MTTD
represents the average duration required by a
cybersecurity system to identify a security incident
from the moment it occurs. A decrease in MTTD
indicates an increase in threat detection speed,
thereby narrowing the exploitation window for
attackers and reducing the duration of risk exposure
(Morais & De Camargo, 2023). In the context of
network traffic incidents, this metric also reflects the
latency between the occurrence of an incident and its
detection (Tavassoli Hojati et al., 2014). MTTD can
be measured by dividing the total detection time of
each incident by the number of incidents using the
following formula (Morais & De Camargo, 2023).
MTTD =
∑
(
,
,
)
(1)
Where:
• 𝑡
,
= detection time of the 𝑖−𝑡ℎ
incident
• 𝑡
,
= execution time of the 𝑖−𝑡ℎ
incident
• 𝑛 = total number of incidents
Example:
If a ransomware sample is executed at 10:00:00.000
and detected at 10:00:00.500, the detection time is
500 𝑚𝑠. For five tests with detection times of 500,
510, 495, 505, and 510 𝑚𝑠:
MTTD =
= 504 𝑚𝑠 (2)
Mean Time to Respond (MTTR) is a metric that
measures the average time it takes for a security or IT
operations team to begin responding to an incident
after it is detected (Johnson et al., 2024). This metric
is an important indicator in assessing the
effectiveness of an incident response team, because
the faster an incident is handled, the less potential
damage it will cause. In the context of cybersecurity,
MTTR describes how quickly a system responds to
threats such as cyberattacks, ransomware, or other
suspicious activities after they are first detected by the
monitoring system. MTTR can be measured by
dividing the total response time for each incident by
Optimization of Audit Daemon for Preventing Ransomware Attacks on Linux Servers
115
the number of incidents using the following formula
(Alavian et al., 2021).
MTTR =
∑
(
,
,
)
(3)
Where:
• 𝑡
,
= response completion time of the
𝑖−𝑡ℎ incident
• 𝑡
,
= detection time of the 𝑖−𝑡ℎ
incident
• 𝑛 = total number of incidents
Example:
If a ransomware is detected at 10:00:00.500 and the
process is terminated at 10:00:00.515, the response
time is 15 𝑚𝑠. With five tests averaging 16 𝑚𝑠, the
MTTR is calculated as:
MTTR =
= 16 𝑚𝑠
(4)
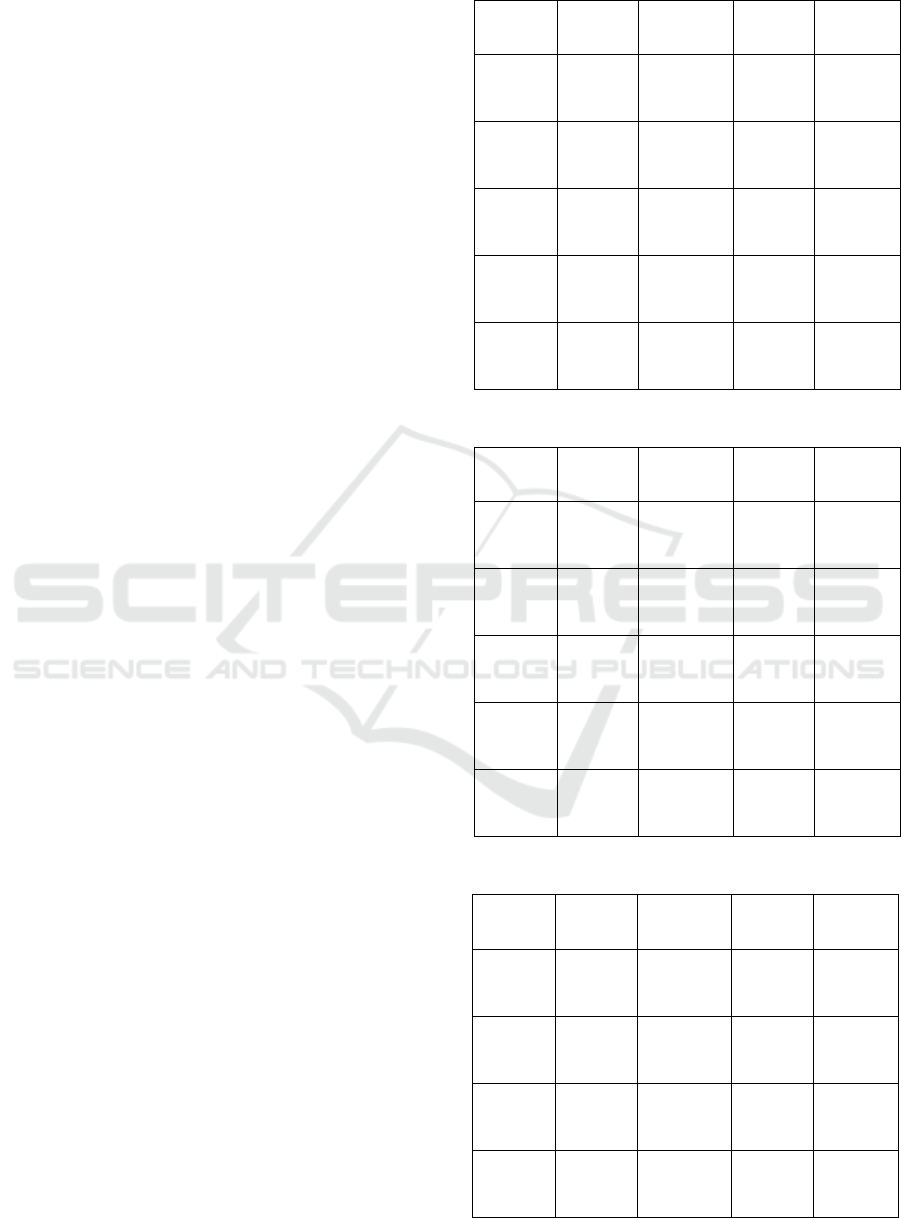
2.1 Process Workflow
The experimental setup was implemented on a
Windows operating system as the host machine, with
Oracle VirtualBox used to run multiple guest
environments as shown in Figure 1. Three different
Ubuntu Server versions were installed as virtual
machines: Ubuntu 18.04, Ubuntu 20.04, and Ubuntu
22.04. These versions were selected to represent
legacy (18.04), stable (20.04), and the latest release
with updated security patches (22.04). The tester
interacted with the system through the host machine,
executing ransomware samples inside the virtualized
Ubuntu environments to evaluate detection and
response performance under controlled conditions.
This setup ensured that the testing environment was
isolated, reproducible, and representative of real-
world Linux server deployments.
Figure 1: Experimental setup for testing environment.
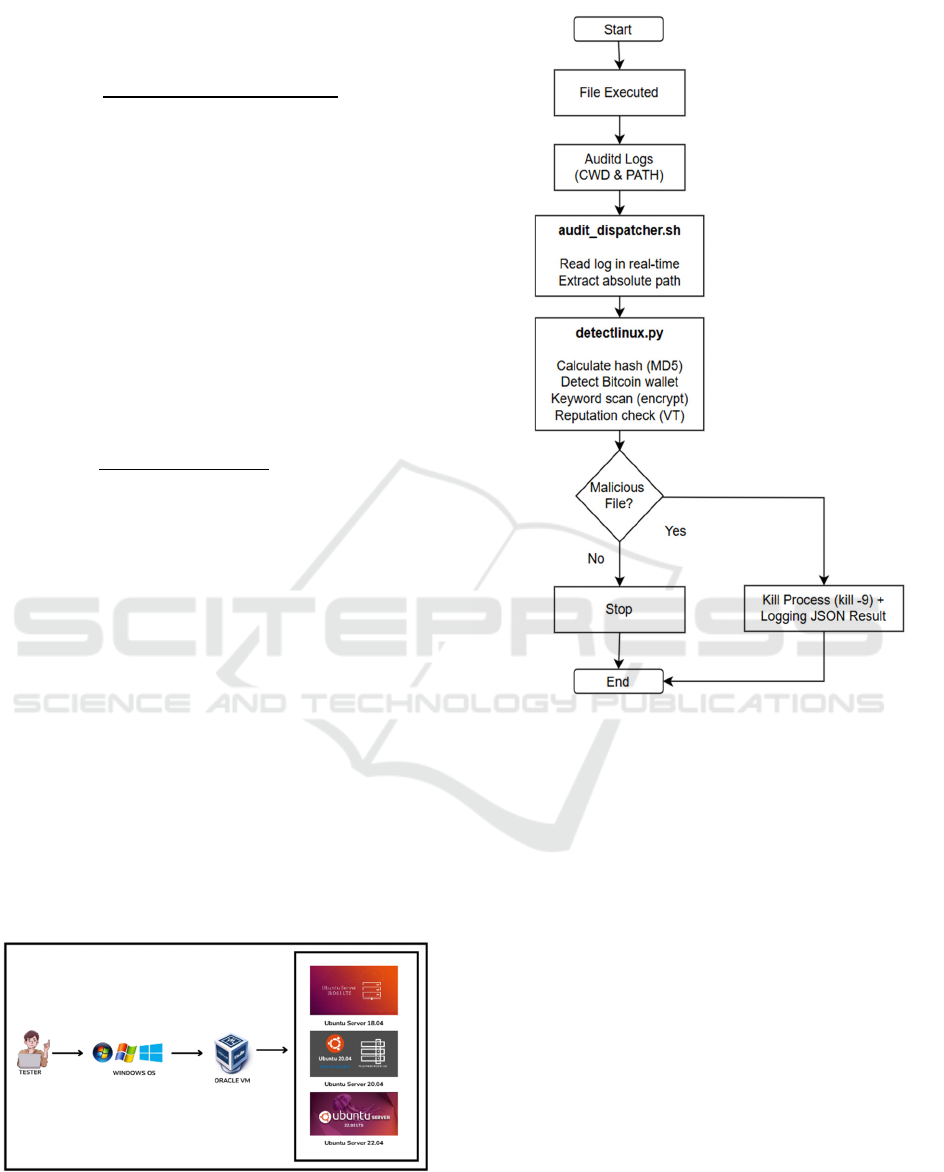
Figure 2: Flowchart of detection and response process.
The detection and response workflow is
illustrated in Figure 2, which shows the sequence of
actions from file execution to process termination.
When a file is executed, Auditd records system
events, which are forwarded through a dispatcher
script for real-time processing. The script calls a
Python detection module that performs several
checks: (i) file hash calculation (MD5) used as the
input for reputation analysis, (ii) pattern matching of
Bitcoin wallet addresses using regular expressions,
(iii) keyword-based scanning for suspicious
behaviors such as “encrypt,” and (iv) submission of
the hash to VirusTotal. The VirusTotal service
operates as a cloud-based SaaS API, ensuring that the
detection results are always based on the latest
reputation database. If a file is flagged as malicious,
the corresponding process is immediately terminated
using a kill -9 command, and the results are logged in
JSON format for reproducibility.
RITECH 2025 - The International Conference on Research and Innovations in Information and Engineering Technology
116
2.2 Evaluation Platform
The experiments were conducted on a dedicated
testbed with the following specifications: Intel Core
i7-10750H CPU @ 2.60 GHz, 16 GB RAM, 512 GB
SSD, and running Ubuntu 18.04, 20.04, and 22.04
(64-bit). This configuration ensured consistent
performance across multiple test scenarios and
avoided bias caused by hardware limitations.
3 RESULT AND DISCUSSION
This ransomware detection system consists of three
main components that are integrated with each other.
The first component is Auditd, which monitors file
execution activities in important directories such as
/home, /var, and /etc, using rules defined in
/etc/audit/rules.d/audit.rules. These activity logs are
recorded in /var/log/audit/audit.log, specifically
entries of type=CWD (indicating the current working
directory) and type=PATH (the name of the executed
file). The second component, the audit_dispatcher.sh
script, reads the log in real time using tail -Fn0,
combines information from CWD and PATH to
obtain the absolute file path, and then records it to
/var/log/ransomware_detection.log. This file path is
then sent to a Python script for further analysis.
The third component is the Python script
detectlinux.py, which is responsible for analyzing
executed files. This script calculates the MD5 hash of
the file for identification, detects Bitcoin wallet
address patterns (a common indicator of
ransomware), and checks the file's reputation through
API integration with VirusTotal. Additionally, the
script scans the file's contents for keywords such as
“encrypt” or “ransom.” The analysis results are stored
in JSON format. If a file is identified as malicious by
VirusTotal, the system performs automatic
mitigation: a Bash script uses the lsof command to
identify processes associated with the file, then
forcefully terminates them using kill -9. With this
approach, the system is capable of early detection and
rapid response to potential ransomware attacks in a
Linux environment.
The ransomware detection and response system
was tested by measuring the MTTD and MTTR. The
testing was conducted on four different types of
ransomwares Shougolock (Table 1), AvosLocker
(Table 2), Interlock (Table 3) and MarioLocker
(Table 4).
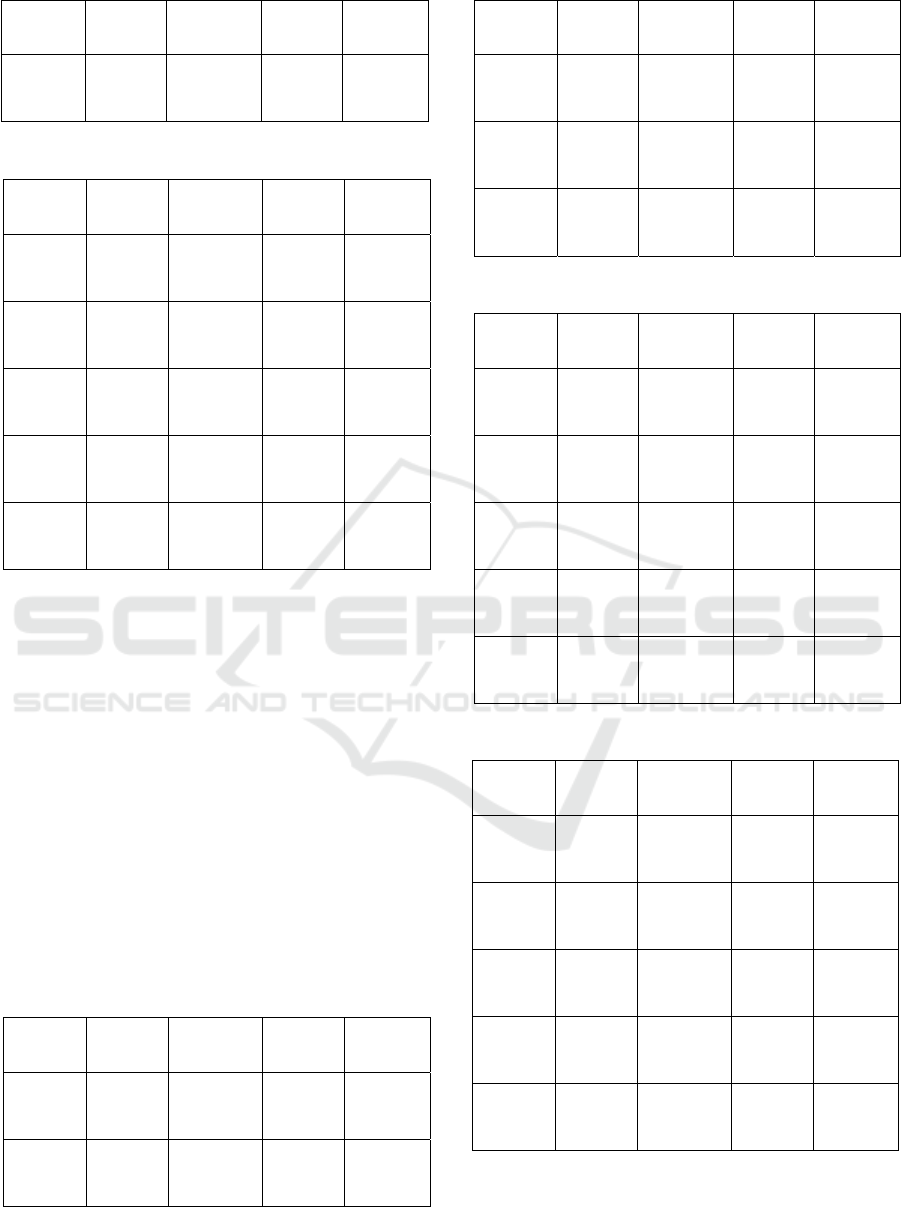
Table 1: Ubuntu 18.04 Shougolock Ransomware Testing.
Ransom
Executed
Ransom
Detected
Range
Detected
Ransom
Respond
Range
Respond
2025-03-
08_16:06:
40.438
06:41.0 514.000 ms 06:41.0 14.000 ms
2025-03-
08_16:07:
08.117
07:08.6 514.000 ms 07:08.6 14.000 ms
2025-03-
08_16:07:
13.726
07:14.2 513.000 ms 07:14.3 14.000 ms
2025-03-
08_16:07:
18.191
07:18.7 513.000 ms 07:18.7 14.000 ms
2025-03-
08_16:07:
22.680
07:23.2 515.000 ms 07:23.2 14.000 ms
Table 2: Ubuntu 18.04 AvosLocker Ransomware Testing.
Ransom
Executed
Ransom
Detected
Range
Detected
Ransom
Respond
Range
Respond
2025-03-
08_16:09:
57.387
09:57.9 513.000 ms 09:57.9 15.000 ms
2025-03-
08_16:10:
22.302
10:22.8 512.000 ms 10:22.8 14.000 ms
2025-03-
08_16:10:
28.214
10:28.7 512.000 ms 10:28.7 13.000 ms
2025-03-
08_16:10:
32.446
10:33.0 514.000 ms 10:33.0 17.000 ms
2025-03-
08_16:10:
36.930
10:37.4 514.000 ms 10:37.5 14.000 ms
Table 3: Ubuntu 18.04 Interlock Ransomware Testing.
Ransom
Executed
Ransom
Detected
Range
Detected
Ransom
Respond
Range
Respond
2025-03-
08_16:13:
15.150
13:15.7 512.000 ms 13:15.7 14.000 ms
2025-03-
08_16:13:
24.885
13:25.4 511.000 ms 13:25.4 14.000 ms
2025-03-
08_16:13:
54.804
13:55.3 514.000 ms 13:55.3 16.000 ms
2025-03-
08_16:13:
54.804
13:55.3 514.000 ms 13:55.3 16.000 ms
Optimization of Audit Daemon for Preventing Ransomware Attacks on Linux Servers
117
Ransom
Executed
Ransom
Detected
Range
Detected
Ransom
Respond
Range
Respond
2025-03-
08_16:14:
00.524
14:01.0 516.000 ms 14:01.1 14.000 ms
Table 4: Ubuntu 18.04 MarioLocker Ransomware Testing.
Ransom
Executed
Ransom
Detected
Range
Detected
Ransom
Respond
Range
Respond
2025-03-
08_16:19:
23.271
19:23.8 510.000 ms 19:23.8 15.000 ms
2025-03-
08_16:19:
47.013
19:47.5 522.000 ms 19:47.5 14.000 ms
2025-03-
08_16:19:
51.070
19:51.6 512.000 ms 19:51.6 13.000 ms
2025-03-
08_16:19:
55.182
19:55.7 515.000 ms 19:55.7 14.000 ms
2025-03-
08_16:19:
59.210
19:59.7 520.000 ms 19:59.7 14.000 ms
Testing results for ubuntu 18.04 for Shougolock
ransomware show that the system successfully
detected threats with an average Mean Time to Detect
(MTTD) of 513.8 ms and Mean Time to Respond
(MTTR) of 14.0 ms. Detection via VirusTotal was
also consistent, with each attempt successfully
identified as ransomware. For the AvosLocker
ransomware, the average MTTD was recorded at
513.0 ms and MTTR at 14.6 ms, with consistent
detection results from VirusTotal. The Interlock
ransomware showed an MTTD of 513.4 ms and
MTTR of 14.8 ms, and all tests were also successfully
detected by VirusTotal. For the MarioLocker
ransomware, the system recorded an MTTD of 515.8
ms and an MTTR of 14.0 ms, with successful
VirusTotal detection in every test.
Table 5: Ubuntu 20.04 Shougolock Ransomware Testing.
Ransom
Executed
Ransom
Detected
Range
Detected
Ransom
Respond
Range
Respond
2025-03-
07_15:07:
49.521
07:50.0 448.000 ms 07:50.0 14.000 ms
2025-03-
07_15:08:
02.815
08:03.2 413.000 ms 08:03.2 15.000 ms
Ransom
Executed
Ransom
Detected
Range
Detected
Ransom
Respond
Range
Respond
2025-03-
07_15:08:
10.682
08:11.1 430.000 ms 08:11.1 16.000 ms
2025-03-
07_15:08:
20.560
08:21.1 524.000 ms 08:21.1 15.000 ms
2025-03-
07_15:09:
01.518
09:02.0 514.000 ms 09:02.0 16.000 ms
Table 6: Ubuntu 20.04 AvosLocker Ransomware Testing.
Ransom
Executed
Ransom
Detected
Range
Detected
Ransom
Respond
Range
Respond
2025-03-
07_15:16:
34.463
16:34.5 84.000 ms 16:34.6 20.000 ms
2025-03-
07_15:16:
40.147
16:40.7 536.000 ms 16:40.7 14.000 ms
2025-03-
07_15:16:
45.599
16:46.1 472.000 ms 16:46.1 15.000 ms
2025-03-
07_15:16:
51.998
16:52.5 541.000 ms 16:52.6 14.000 ms
2025-03-
07_15:16:
59.286
16:59.7 439.000 ms 16:59.7 16.000 ms
Table 7: Ubuntu 20.04 Interlock Ransomware Testing.
Ransom
Executed
Ransom
Detected
Range
Detected
Ransom
Respond
Range
Respond
2025-03-
08_16:06
:40.438
06:41.0
514.000
ms
06:41.0
14.000
ms
2025-03-
08_16:07
:08.117
07:08.6
514.000
ms
07:08.6
14.000
ms
2025-03-
08_16:07
:13.726
07:14.2
513.000
ms
07:14.3
14.000
ms
2025-03-
08_16:07
:18.191
07:18.7
513.000
ms
07:18.7
14.000
ms
2025-03-
08_16:07
:22.680
07:23.2
515.000
ms
07:23.2
14.000
ms
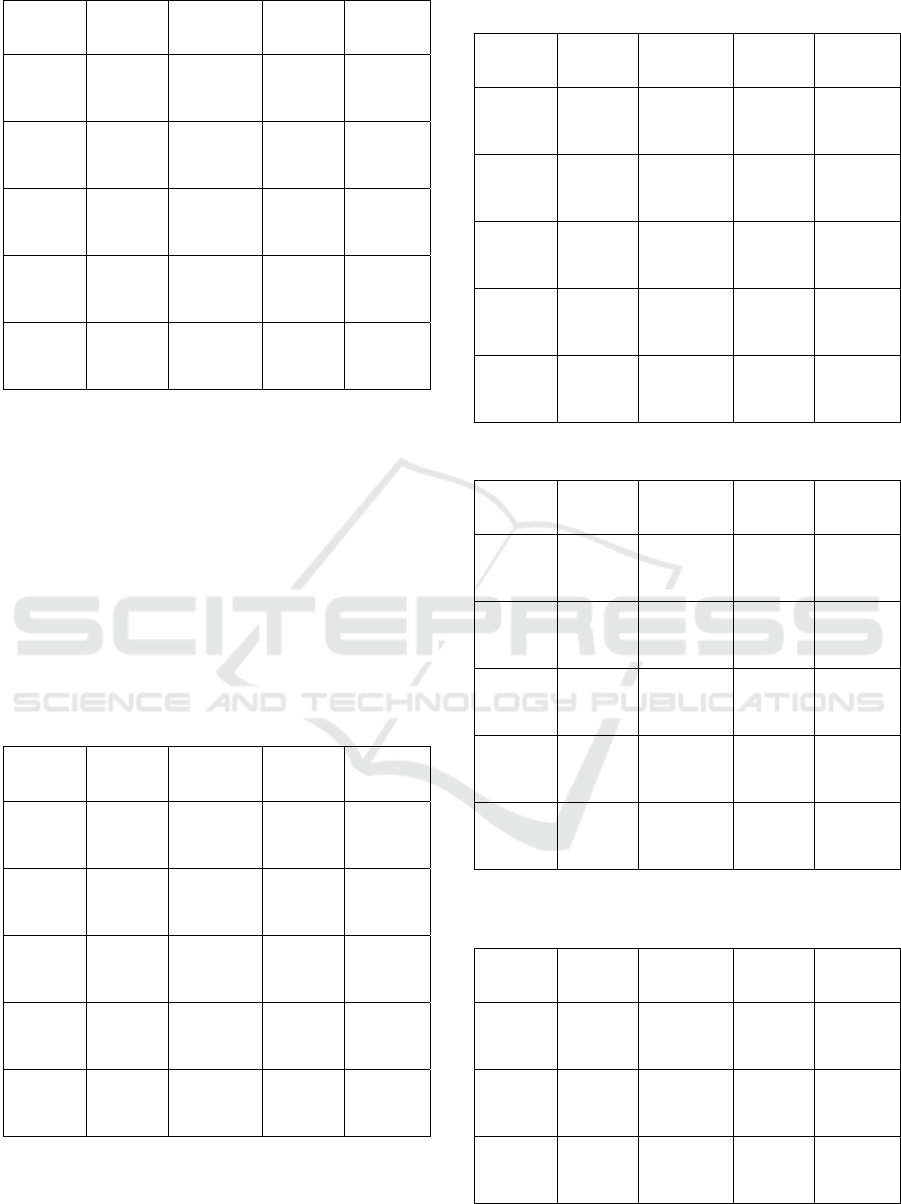
Table 8: Ubuntu 20.04 MarioLocker Ransomware Testing.
RITECH 2025 - The International Conference on Research and Innovations in Information and Engineering Technology
118
Ransom
Executed
Ransom
Detected
Range
Detected
Ransom
Respond
Range
Respond
2025-03-
08_16:06:
40.438
06:41.0 514.000 ms 06:41.0 14.000 ms
2025-03-
08_16:07:
08.117
07:08.6 514.000 ms 07:08.6 14.000 ms
2025-03-
08_16:07:
13.726
07:14.2 513.000 ms 07:14.3 14.000 ms
2025-03-
08_16:07:
18.191
07:18.7 513.000 ms 07:18.7 14.000 ms
2025-03-
08_16:07:
22.680
07:23.2 515.000 ms 07:23.2 14.000 ms
Ransomware testing on Ubuntu 20.04 (Table 5-8)
showed that the system was able to detect and respond
to threats quickly and consistently. The average
MTTD for the four ransomware strains was between
414.4 ms and 509.4 ms, and the MTTR ranged from
14.6 to 15.2 ms, with stable detection and response
times. Despite significant variation in AvosLocker
(84–541 ms), response performance remained
consistent. All samples were successfully detected by
VirusTotal, demonstrating the system's accuracy and
reliability in recognizing various types of
ransomwares.
Table 9: Ubuntu 22.04 Shougolock Ransomware Testing.
Ransom
Executed
Ransom
Detected
Range
Detected
Ransom
Respond
Range
Respond
2025-03-
08_13:51:
15.779
51:16.3 545.000 ms 51:16.3 18.000 ms
2025-03-
08_13:52:
09.879
52:10.4 545.000 ms 52:10.4 16.000 ms
2025-03-
08_13:52:
16.547
52:17.1 550.000 ms 52:17.1 18.000 ms
2025-03-
08_13:52:
23.362
52:23.9 552.000 ms 52:23.9 17.000 ms
2025-03-
08_13:52:
30.154
52:30.7 552.000 ms 52:30.7 17.000 ms
Table 10: Ubuntu 22.04 AvosLocker Ransomware Testing
Ransom
Executed
Ransom
Detected
Range
Detected
Ransom
Respond
Range
Respond
2025-03-
08_14:08:
04.648
08:05.2 528.000 ms 08:05.2 19.000 ms
2025-03-
08_14:08:
21.237
08:21.8 528.000 ms 08:21.8 18.000 ms
2025-03-
08_14:08:
28.533
08:29.1 530.000 ms 08:29.1 19.000 ms
2025-03-
08_14:08:
33.349
08:33.9 530.000 ms 08:33.9 18.000 ms
2025-03-
08_14:08:
37.929
08:38.5 530.000 ms 08:38.5 17.000 ms
Table 11: Ubuntu 22.04 Interlock Ransomware Testing.
Ransom
Executed
Ransom
Detected
Range
Detected
Ransom
Respond
Range
Respond
2025-03-
08_16:06:
40.438
06:41.0 514.000 ms 06:41.0 14.000 ms
2025-03-
08_16:07:
08.117
07:08.6 514.000 ms 07:08.6 14.000 ms
2025-03-
08_16:07:
13.726
07:14.2 513.000 ms 07:14.3 14.000 ms
2025-03-
08_16:07:
18.191
07:18.7 513.000 ms 07:18.7 14.000 ms
2025-03-
08_16:07:
22.680
07:23.2 515.000 ms 07:23.2 14.000 ms
Table 12: Ubuntu 22.04 MarioLocker Ransomware
Testing.
Ransom
Executed
Ransom
Detected
Range
Detected
Ransom
Respond
Range
Respond
2025-03-
08_14:25:
33.297
25:33.8 531.000 ms 25:33.8 19.000 ms
2025-03-
08_14:25:
42.969
25:43.5 534.000 ms 25:43.5 18.000 ms
2025-03-
08_14:25:
46.577
25:47.1 532.000 ms 25:47.1 17.000 ms
Optimization of Audit Daemon for Preventing Ransomware Attacks on Linux Servers
119
Ransom
Executed
Ransom
Detected
Range
Detected
Ransom
Respond
Range
Respond
2025-03-
08_14:25:
50.184
25:50.7 530.000 ms 25:50.7 17.000 ms
2025-03-
08_14:25:
54.424
25:55.0 528.000 ms 25:55.0 18.000 ms
Ransomware testing on Ubuntu 22.04 (Table 9-
12) showed that the system was able to detect and
respond to threats with stable performance.
Shougolock recorded an MTTD of 548.8 ms and an
MTTR of 17.2 ms, while AvosLocker, Interlock, and
MarioLocker showed MTTDs in the range of 529.2–
531.0 ms and MTTRs between 17.8–18.2 ms.
Detection and response times for all samples were
consistent within a narrow range, indicating system
stability. All samples were also successfully detected
by VirusTotal, confirming the system's accuracy and
reliability in identifying ransomware.
Overall, the system demonstrated excellent and
consistent performance in detecting and responding
to ransomware in Ubuntu 18.04, 20.04, and 22.04
environments. On Ubuntu 18.04, the average MTTD
was 514.0 ms and MTTR was 14.4 ms, indicating
detection capabilities of less than one second and
extremely fast response times. Ubuntu 20.04 recorded
the best performance in terms of fast detection and
stable response, while Ubuntu 22.04 showed slightly
slower detection with an MTTD of 534.8 ms and an
MTTR of 17.8 ms, possibly due to differences in
system optimization or higher system load. However,
the stable response time across all versions
demonstrates the system's efficiency in handling
threats. Consistent validation by VirusTotal
throughout the testing further reinforces the reliability
and accuracy of this system, while small differences
in MTTD and MTTR values between samples are
primarily due to variations in the complexity and
behavior of each ransomware.
3.1 Assessment of Ransomware Impact
within MTTD and MTTR
In addition to measuring detection and response
times, we assessed the practical impact of
ransomware within the MTTD and MTTR windows.
Observations showed that only a small number of
files were encrypted before the malicious process was
terminated. For instance, MarioLocker typically
encrypted 1–2 files during the ~500 ms detection
window, while AvosLocker and Interlock affected
fewer than 3 files. These findings highlight that
although the system does not completely prevent file
encryption, the sub-second detection and
millisecond-level response significantly reduce the
potential damage compared to uncontrolled
execution. However, this study did not perform a
detailed quantitative analysis of file types and sizes
encrypted during the window, which remains a
limitation to be addressed in future work.
4 CONCLUSION
The ransomware detection and response system
developed in a Linux environment using Auditd and
VirusTotal has proven effective in detecting and
handling ransomware threats. The system
successfully detected four types of ransomware
(Shougolock, AvosLocker, InterLock, and
MarioLocker) with an average MTTD of 503.7 ms
and an average MTTR of 15.8 ms across three Ubuntu
versions (18.04, 20.04, and 22.04). Ubuntu 20.04
showed the best detection performance, while Ubuntu
18.04 had the highest response speed.
These findings highlight that Linux servers, often
considered inherently secure, still require proactive
defense mechanisms. The system provides a
lightweight and practical approach that can be
deployed in real-world environments to minimize
ransomware impact.
However, this study is limited to four ransomware
families and relies on VirusTotal, which may reduce
effectiveness against unknown or zero-day
ransomware. These limitations point to opportunities
for further research. Future enhancements include
integrating artificial intelligence (AI) for behavioral
analysis, reducing false positives, and improving
adaptability against emerging ransomware threats.
REFERENCES
Adkins, H., Beyer, B., Blankinship, P., Lewandowski, P.,
Oprea, A., & Stubblefield, A. (2020). Building secure
and reliable systems: Best practices for designing,
implementing, and maintaining systems. Google.
https://sre.google/books/
Guo, J., Liang, H., & Long, J. (2024). Leveraging file
system characteristics for ransomware mitigation in
Linux operating system environments. Research
Square, 1–6. https://doi.org/10.21203/rs.3.rs-
000000/v1 (if no DOI, you can omit this line)
Neweva, W., Fitzwilliam, O., & Waterbridge, J. (2024).
Forensic analysis of live ransomware attacks on Linux-
based laptop systems: Techniques and evaluation.
RITECH 2025 - The International Conference on Research and Innovations in Information and Engineering Technology
120

Research Square.
https://www.researchsquare.com/article/rs-4900486/v1
Golev, A., Hristev, R., Veselinova, M., & Kolev, K. (2022).
Crypto-ransomware attacks on Linux servers: A data
recovery method. International Journal of Differential
Equations and Applications, 21(2), 19–29.
https://doi.org/10.12732/ijdea.v21i2.2
Beaman, C., Barkworth, A., Akande, T. D., Hakak, S., &
Khan, M. K. (2021). Ransomware: Recent advances,
analysis, challenges, and future research directions.
Computers & Security, 111, 102490.
https://doi.org/10.1016/j.cose.2021.102490
Richey, R. C., & Klein, J. D. (2014). Design and
development research. Routledge.
https://doi.org/10.4324/9780203826034
Venable, J. R., Pries-Heje, J., & Baskerville, R. (2017).
Choosing a design science research methodology. In
Proceedings of the 28th Australasian Conference on
Information Systems (ACIS 2017).
Morais, M. A., & De Camargo, R. Y. (2023). Real-time
incident detection in public bus systems using machine
learning. In Proceedings of the IEEE Conference on
Intelligent Transportation Systems (ITSC) (pp. 2044–
2049).
https://doi.org/10.1109/ITSC57777.2023.10422471
Tavassoli Hojati, A., Ferreira, L., Washington, S., Charles,
P., & Shobeirinejad, A. (2014). Modelling total
duration of traffic incidents including incident detection
and recovery time. Accident Analysis & Prevention, 71,
296–305. https://doi.org/10.1016/j.aap.2014.06.006
Johnson, O. B., Olamijuwon, J., Cadet, E., Osundare, O. S.,
& Weldegeorgise, Y. W. (2024). Developing real-time
monitoring models to enhance operational support and
improve incident response times. International Journal
of Engineering Research and Development, 20(11),
1296–1304.
Alavian, P., Eun, Y., Liu, K., Meerkov, S. M., & Zhang, L.
(2021). The (α, β)-precise estimates of MTBF and
MTTR: Definition, calculation, and observation time.
IEEE Transactions on Automation Science and
Engineering, 18(3), 1469–1477.
https://doi.org/10.1109/TASE.2020.3017134.
Optimization of Audit Daemon for Preventing Ransomware Attacks on Linux Servers
121
