
Reverse Engineering LockBit Ransomware to Build Protection
Method for Post-Compromised Machine
Ahmad Mujahid Malhadi
a
and Ady Wahyudi Paundu
b
Department of Informatics, Faculty of Engineering, Universitas Hasanuddin, Gowa, South Sulawesi, Indonesia
Keywords: Ransomware, Lockbit, Shell-Link, Cyber-Resilience.
Abstract: Ransomware-as-a-Service (RaaS) has driven a global surge in ransomware attacks, particularly targeting
corporations and government institutions. This research introduces a file protection method against
ransomware attacks by leveraging extension exclusion patterns and directory path exceptions commonly used
by modern ransomware groups, such as LockBit and Conti, which operate professionally with affiliate-based
business models on the anonymous TOR network. Our approach camouflages critical user files by
transforming them into extensions typically avoided by ransomware (such as .dll, .exe, and .sys) and
relocating them to designated "safe" directories, while maintaining access through .LNK shell links that serve
as launchers. Effective testing against nine prominent ransomware variants demonstrated that eight out of
nine samples failed to encrypt the protected files, confirming the method's viability. The protection system
offers several advantages, including storage efficiency, instant recovery capabilities that are independent of
external hardware, and enhanced resistance to data exfiltration attempts. While limitations exist regarding
potential future ransomware evolution, the open-source implementation in Rust provides organizations with
an accessible tool to enhance cyber-resilience against double extortion techniques and other evolving
ransomware threats.
1 INTRODUCTION
Cybersecurity threats have evolved dramatically with
the digital transformation of valuable assets, with
ransomware becoming particularly problematic in
recent years. In 2025, attacks from top ransomware
groups still accounted for 37% reported attacks
(Fortinet, 2025). The emergence of user-friendly
Ransomware-as-a-Service platforms has
democratized cybercrime, allowing even technically
unskilled individuals to deploy sophisticated attacks
while service operators collect percentage-based
commissions from successful extortions (Q.Kerns
and B.Payne, 2021).
Traditional defense mechanisms that rely on
recognizing structural patterns or monitoring API
calls have proven to be ineffective (S. Poudyal and D.
Dasgupta, 2021) as criminals develop sophisticated
evasion techniques. Behavior-based detection (S.
Sheen et al, 2022) requires the ransomware process to
be run first in the system. This risks the monitoring
a
https://orcid.org/0009-0007-5878-8477
b
https://orcid.org/0000-0002-8761-7892
processes being terminated before detection happens,
and valuable data may become compromised during
the detection delay.
A promising alternative approach focuses on
resilient protection rather than reactive detection,
which serves as a final defense layer, particularly for
Critical National Infrastructure (CNI), where no
downtime can be tolerated. The Colonial Pipeline
case (Egan.M, 2021) demonstrates why quick
operational recovery is essential. During the six-day
shutdown, each hour meant significant financial
losses—not just from halting operations that normally
transport over 100 million gallons of fuel daily, but
also from related effects, including supply chain
disruptions across the country. The incident turned
local cyber incidents into national problems.
To address these challenges, we developed a
method that prioritizes resilience over detection.
During our development phase, we also considered
the assumption that an attacker is already present
within the same system as our protection mechanism.
Mujahid Malhadi, A. and Wahyudi Paundu, A.
Reverse Engineering LockBit Ransomware to Build Protection Method for Post-Compromised Machine.
DOI: 10.5220/0014265700004928
Paper published under CC license (CC BY-NC-ND 4.0)
In Proceedings of the 1st International Conference on Research and Innovations in Information and Engineering Technology (RITECH 2025), pages 95-101
ISBN: 978-989-758-784-9
Proceedings Copyright © 2025 by SCITEPRESS – Science and Technology Publications, Lda.
95

Furthermore, we acknowledged that attackers would
attempt to reverse-engineer and discover information
about the protection mechanisms employed.
Therefore, we implemented techniques
commonly used by ransomware authors, specifically
obfuscation to utility tools. Our approach includes
several key components:
▪ Language Selection: We chose Rust as our
primary development language due to its
compiled nature, producing Windows Portable
Executable (PE) binaries that are inherently more
difficult to analyze than interpreted languages like
Python (Lee et al., 2023).
▪ String Obfuscation: We employed the obfstr()
library to hide string literals, making static
analysis more challenging for potential attackers.
▪ Reverse Engineering Resistance: The binaries
produced by Rust are inherently difficult to
reverse-engineer. Current industry-standard
reverse engineering tools are primarily optimized
for binaries compiled from C and C++ languages.
Additionally, there is limited expertise and fewer
practitioners in the field of reverse engineering
Rust binaries, creating an additional layer of
protection through obscurity.
Adversarial-aware design philosophy ensures that
the protection mechanisms remain effective even
when operating in a compromised environment.
Below are several contributions from this paper:
▪ We developed a resilient protection method that
considers an attacker-in-mind approach.
▪ We demonstrate that the methods are still
effective and relevant even against the most recent
ransomware family.
2 RELATED WORK
Most research on ransomware protection uses
behavior-based detection methods. These systems
watch what a user process does and check their API
calls to find ransomware patterns. However, these
methods have a common problem: it works too late.
This happens because the ransomware will be running
and start encrypting files before the detection system
can see the rogue behavior. They will always be one
step behind because they have to wait and watch.
Arabo et al developed a process behavior analysis
method to identify ransomware samples. Their
system watches which APIs are called and how much
system resources are used. They collect data about
file extensions, API calls, and disk usage, then feed
this information into machine learning models to alert
administrators if a program might be ransomware.
However, their approach has several problems. First,
it has low accuracy and lacks proper false-positive
analysis, meaning it might miss real ransomware or
wrongly flag a benign program. More importantly,
their system depends on a separate Linux machine to
do the analysis work. This creates a serious weakness
because if the network connection between the
Windows system (where ransomware runs) and the
Linux analysis machine gets cut off, the entire
detection system stops working. This network
dependency is especially dangerous because many
ransomware attacks include steps to disrupt network
communications or target network infrastructure. An
attacker could easily break the connection between
machines, leaving the Windows system completely
unprotected while the ransomware encrypts files
(Arabo et al., 2020).
Hampton et al. (2018) studied how ransomware
behaves on Windows systems by looking at which
APIs it calls. They found that ransomware uses
certain APIs more often than normal programs, which
can help identify ransomware without checking code
signatures. However, their research has important
gaps when dealing with obfuscated binaries. The
detection system is still weak because it only looks at
API calls that can be seen during static analysis. It
cannot detect API calls in programs that use Dynamic
API Resolving techniques, where the real API calls
are only revealed at runtime.
Microsoft has introduced Controlled Folder
Access (Microsoft, 2023), a security feature that only
allows trusted programs to access protected folders.
This is meant to stop ransomware from changing files
in those folders. However, this feature has several
serious problems. First, it depends heavily on user
permissions and doesn't protect against bad programs
that run in unprotected areas of the computer. If
attackers have enough system privileges, they can
easily bypass this protection. More importantly,
Controlled Folder Access relies on Windows
Defender's Real-Time Protection (RTP) service to
work properly. This creates a critical weakness
because many ransomware programs are designed to
kill Windows Defender and other security services as
their first step. Once the RTP service is disabled or
terminated, the Controlled Folder Access feature
stops working completely, leaving the protected
folders vulnerable to encryption.
While the R-Locker approach by (Gómez-
Hernández et al, 2018) shows innovation in using
honeyfiles to detect ransomware, their detection
mechanism has a significant weakness. The system
relies on placing honeyfiles in various locations to
catch ransomware activity. However, this approach is
RITECH 2025 - The International Conference on Research and Innovations in Information and Engineering Technology
96
risky because the ransomware is still allowed to run
and start encrypting files before their detection
system can respond. This creates a dangerous time
window where real user data can be damaged or
encrypted before the honeyfiles are detected as
modified and the protection system activates.
Therefore, while this method can detect ransomware
relatively quickly, it cannot completely prevent data
loss in the early stages of an attack, which is a critical
limitation for real-time data protection.
Behavior-based detection methods are better
suited for detecting Remote Access Trojan (RAT) or
Dropper malware rather than Ransomware. RATs are
designed to be persistent and run for months on the
operating system, frequently making API calls to
invoke various processes for data stealing and
remote-control activities. This gives detection
systems plenty of time and behavioral patterns to
analyze. In contrast, ransomware operates with a
completely different approach - it follows a "hit-and-
run" strategy where it encrypts files as quickly as
possible and then stops. This one-time destructive
behavior leaves very little opportunity for behavioral
analysis systems to collect enough data patterns
before the damage is already done.
In many real-world cases (Avast, 2018),
(Security.com, 2024), adversaries who infiltrate
organizations have already deployed RATs in the
network long before they work as affiliates with RaaS
gangs. Despite recent reports (Google Cloud, 2025)
showing a year-over-year decrease in dwell time for
cyber-attacks, the minimum dwell time observed in
ransomware incidents remains above 7 days. This
window still offers sufficient opportunity for RAT
operators to tailor their tooling to the specific target
environment.
3 METHODOLOGY
3.1 Samples Preparation
To initiate the development of protection methods,
normalized ransomware samples are required. Since
ransomware typically includes anti-analysis, anti-
VM, anti-debugging, and packing features (Moser et
al., 2007), a preparation phase is necessary to ensure
the ransomware can be executed (especially in an
isolated VM environment) from start to finish,
completely encrypting the file system on the OS.
This is where the reverse-engineering work of PE
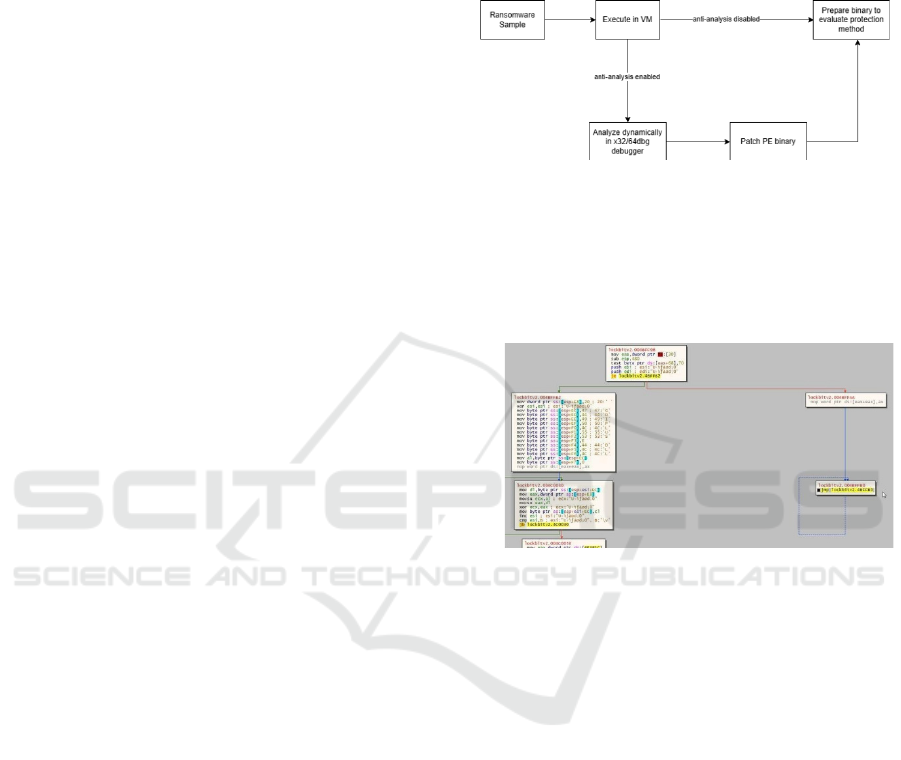
binary executables takes place. Figure 1 illustrates the
workflow of ransomware sample preparation. Several
methods were used, like patching the binary assembly
x86 ISA by simply changing it from JE to JNE to
redirect the execution flow. And by using the Scylla
Hide plugin for x64dbg/x32dbg (x64dbg, 2024) to
circumvent the ransomware anti-debugging
mechanism.
Figure 1: Ransomware samples preparation flow.
One of the ransomware samples we used, LockBit
v2, implements an anti-debugging mechanism where
its subroutine checks the Process Environment Block
(PEB) flags and traps the x32dbg debugger into an
infinite loop, as shown in Figure 2.
Figure 2: Infinite loop routine on LockBit v2.
3.2 Protection Mechanism
This paper implements a dual-layer strategy—
replacing the original file with a link while
simultaneously relocating it to directories that
ransomware typically excludes from its targeting
routines. Though not designed to prevent ransomware
execution itself, this technique is meant to disrupt
ransomware's ability to locate valuable data while
maintaining seamless access for legitimate users
through specially configured shortcut files which act
as a launcher.
When a user decides to protect a file, the Hider
utility creates a hash of the original filename, moves
the actual file to a safe location within paths typically
excluded by ransomware (as configured in
dirpath.conf), and renames it using extensions that
ransomware typically ignores (from extension.conf).
In its original location, the file is replaced with a
specially crafted .LNK file that points to the Launcher
utility with the file's hash as an argument. When the
user double-clicks this .LNK file, the Launcher utility
Reverse Engineering LockBit Ransomware to Build Protection Method for Post-Compromised Machine
97
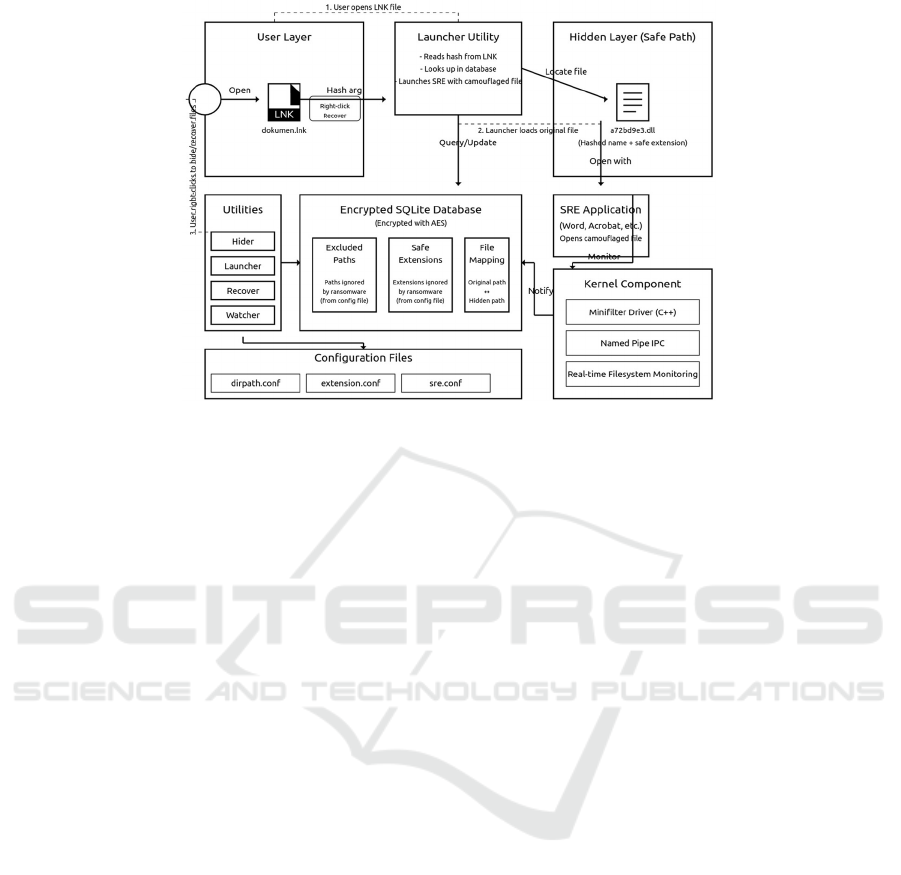
Figure 3: Protection mechanism flow.
queries the encrypted SQLite database to locate the
camouflaged file, then opens it using the appropriate
Software-Related Extension (SRE) application
configured in sre.conf. Throughout this process, a
kernel-level Minifilter Driver continuously monitors
filesystem operations on protected files, sending real-
time notifications through a Named Pipe IPC to the
Watcher utility, which can alert the user of suspicious
access attempts. If the user wishes to restore a file to
its original state, they simply right-click on the .LNK
file and select the Recover option, which reverses the
process by retrieving the camouflaged file from its
safe location and placing it back in its original file
position. The whole process is illustrated in Figure 3.
4 RESULTS
After preparing multiple ransomware samples and
developing the utility, we conducted two types of
tests. First, an effectiveness test to evaluate whether
the protection method was reliable against various
ransomware brands and variants. Second, a
performance test to measure the utility's speed when
users applied it to different file quantities.
4.1 Effectiveness Method
For these Multi-Brand tests, we use a VirtualBox VM
(Windows 10 image installed with FlareVM). We
first prepared several dummy files (documents and
text files) placed in the directory C:\Users\IEUser\
Documents\corporate-file. We then designated C:\
Users\IEUser\AppData\Local\cache\ as the directory
for storing camouflaged files. Ideally, this path should
be a known excluded directory by the ransomware
samples. However, for testing purposes, we allowed
all ransomware samples to encrypt files in this
directory to determine whether camouflaged files
would be encrypted. Next, we identified extensions
typically excluded by ransomware samples.
Generally, ransomware avoids encrypting files with
.dll, .exe, and .sys extensions, as encrypting these
would damage the Windows OS and discourage
victims from paying the ransom. We then created a
.json configuration file for Software-Related
Extensions (SRE) based on the software installed on
the system. In this case, we used WPS Office for
accessing documents or spreadsheets and Notepad for
plaintext files. After configuring the system, we
camouflaged several
dummy files with .docx, .pdf,
.json, .txt, and .xlsx extensions. The original files
were moved to
C:\Users\IEUser\AppData\Local\cache,while .LNK
shell link files were created in their original locations
to serve as launchers. Finally, we created VM
snapshots to restore the virtual machine to its initial
state for testing with different ransomware samples.
After conducting extensive tests against multiple
ransomware brands or variants, we provide the
conclusion as presented in Table 1. Our tests across
nine different ransomware variants demonstrate that
the file camouflage protection method is largely
effective. Eight of the nine tested ransomware
samples failed to encrypt our camouflaged files,
allowing for successful file recovery through the
.LNK shell links. The results confirm that the method
RITECH 2025 - The International Conference on Research and Innovations in Information and Engineering Technology
98
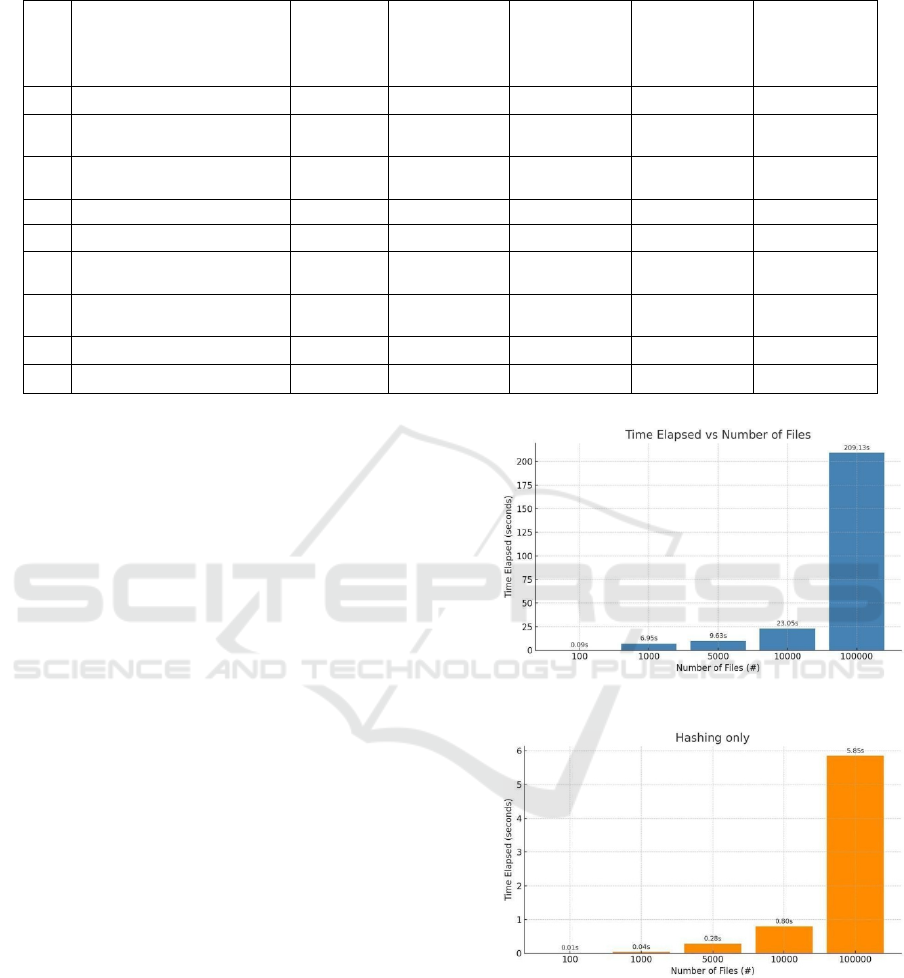
Table 1: Results of running several ransomware brands inside the VM.
No Brand Year
LNK
Preserved
Camouflage
file preserved
SRE
preserved
Encrypted file
extension
1
LockBit v2 2021
✓ ✓ ✓
.lockbit
2
LockBit v3 2023
✓ ✓ ✓
.8FP4QI
PET
3
LockBit v4 2024
✓ ✓ ✓
12 hex
cha
r
4
Babuk v3 2022
╳ ╳ ╳
.BABYK
5
CONTI 2021
✓ ✓ ✓
.CECJF
6
DARKSIDE 2021
✓ ✓ ✓
.9D660D
45
7
MOUNTLOCKER 2021
✓ ✓ ╳
.F638D8
A0
8
PLAY 2021
✓ ✓ ╳
.PLAY
9
CLOP 2023
✓ ✓ ✓
.Clop
provides effective protection against most modern
ransomware variants by leveraging their tendency to
exclude specific system file extensions and paths.
BABUK v3 was the only exception that encrypted all
files regardless of extension or location, which aligns
with its notorious reputation among cybercriminals
for corrupt encryption processes (Dmitry.S, 2022).
Additionally, we observed that while PLAY and
MOUNTLOCKER ransomware damaged WPS
Office components, basic text files remained
accessible through Notepad, demonstrating partial
SRE access capability even in compromised
environments.
4.2 Utility Performances
In these Mass-Hiding tests, we use a bare-metal
Windows 10 running on top of a DELL XPS 15 9500
Laptop with Intel Core i9 and 32 gigabyte of RAM
with a SAMSUNG SSD NVME. We first mass-
generate a dummy file using the provided utility. The
command is generator-file.exe --target-path "C:\
Users\IEUser\Desktop\dummyfile\" --use-extension
".txt,.json,.docx,.xlsx,.pptx" --file-amount 1000 --
range-size "124-2096". This would produce 1000
unique files with size between 100KB to 2MB in the
target path, mimicking real user corporate files. Next,
we camouflage the entire directory with hider-
folder.exe utility. Various file amounts are also
tested, as shown in Figure 4. And then we do another
test with disk I/O operation disabled so only filename
hash is running with no shell link .LNK created and
original file not moved. The hashing test results show
reasonable performance speeds, as shown in Figure 5.
Figure 4: Benchmarking with disk I/O enabled.
Figure 5: Benchmarking with disk I/O disabled.
5 DISCUSSIONS
Based on testing conducted on various ransomware
families, the developed protection method has been
proven effective in safeguarding user files. However,
there are several advantages and limitations that
Reverse Engineering LockBit Ransomware to Build Protection Method for Post-Compromised Machine
99

should be considered by administrators planning to
implement this method, as well as by researchers
aiming to extend this work.
5.1 Advantages of the Method
The protection method that has been built and tested
offers several advantages. First, it's storage efficient
as original files are only moved to a different
directory path with changed extensions. The created
.LNK shell link shortcut files are only 1 kilobyte in
size. Second, Instant recovery because the backup
system exists on the same system, not relying on other
hardware or volume shadow copies that are typically
deleted by ransomware. Restoring files to their
original state only requires right-clicking and
selecting the "Recover this file" option. The
camouflage feature also makes it difficult for
attackers to mass exfiltrate data directly from the
system, as original files have been transformed into
.dll, .exe, and .sys extensions that are typically
excluded by default in exfiltration tools.
5.2 Limitations of the Method
The proposed protection method also has several
limitations. It may become ineffective in the future if
ransomware authors implement features that verify
file extensions against their corresponding magic
bytes. Additionally, the method is not suitable for
SREs that rely solely on a GUI and do not support
CLI arguments to specify which files to open. It is
also ineffective for SREs who validate file extensions
before opening files and reject any that do not match
expected formats. For example, if WPS Office only
allows files with .pdf, .docx, or .xlsx extensions to be
opened.
5.3 Future Improvement
The following points can be addressed for future
development:
Special protection is needed to protect the
SQLite database file. If the .db file on the disk
is deleted, the entire protection mechanism will
not work.
Authentication management, such as
passwords, PINs, fingerprints, or
specialbiometrics should be developed for
launcher and recovery features, ensuring that
only the legitimate system user can operate
them.
Development and integration of better
minifilter drivers using C++, as Rust
compatibility for Windows driver development
was very limited at the time of this research.
Consideration for utilizing the static .lockbit or
.BABYK as a camouflaged extension would be
ineffective in the future since we have seen
newer samples like LockBit v4, which spread
in 2024 were using randomized extensions for
each file name.
The Rust source code, along with ransomware
samples, is available in a public repository (Camo-
LNK, n.d.) including the modified minifilter driver
code with IPC components (Minispy-IPC, n.d.).
6 CONCLUSIONS
This research proposes a protection method to
safeguard files from ransomware attacks by
leveraging extension exclusion features or directory
path exceptions of related samples. Testing results
demonstrate that the developed method effectively
protects camouflaged files while allowing users to
maintain access through .LNK shell links that
function as launchers for their Software-Related
Extension (SRE). The choice of the Rust
programming language for building the hider,
launcher, and recover utilities also makes it more
difficult for attackers to understand the protection
mechanism in detail. Administrators wishing to
integrate this method only need to distribute the PE
binary executable to the computers within their
organization and add registry keys for the right-click
menu functionality. With this protection method
implemented, the instant recovery feature is expected
to enhance organizations cyber- resilience following
ransomware attacks, allowing business operations to
continue functioning at minimum capacity.
Additionally, by providing open- source code, other
researchers have unrestricted access to modify or add
features to the existing utilities.
REFERENCES
Arabo, A., Dijoux, R., Poulain, T., & Chevalier, G. (2020).
Detecting ransomware using process behavior analysis.
Procedia Computer Science, 168, 289–296.
Avast Threat Labs. (2018, April 12). Recent findings from
CCleaner APT investigation reveal that attackers
entered the Piriform network via TeamViewer. Avast
Blog. https://blog.avast.com/update-ccleaner-attackers-
entered-via-teamviewer
Camo-LNK. (n.d.). Ransomware LNK Protection Method.
RITECH 2025 - The International Conference on Research and Innovations in Information and Engineering Technology
100

Dmitry, S. (2024). An interview with initial access broker
Wazawaka: 'There is no such money anywhere as there
is in ransomware'. https://therecord.media/an-
interview-with-initial-access-broker-wazawaka-there-
is-no-such-money-anywhere-as-there-is-in-
ransomware
Egan, M. & Duffy, C. (2021, May 12). Colonial Pipeline
launches restart after six-day shutdown. CNN Business.
https://edition.cnn.com/2021/05/12/business/colonial-
pipeline-restart/index.html
Fortinet Fortiguard Labs. (2025). 2025 Global Threat
Landscape Report.
https://www.fortinet.com/content/dam/fortinet/assets/t
hreat-reports/threat-landscape-report-2025.pdf
GitHub. https://github.com/hexdemsion/camo-lnk
Minispy-IPC. (n.d.). Modified Minifilter with IPC.
GitHub. https://github.com/hexdemsion/minispy-IPC
Google Cloud. (2025). M-Trends 2025. Google Cloud
Blog. https://cloud.google.com/blog/topics/threat-
intelligence/m-trends-2025
Kerns, Q., Payne, B., & Abegaz, T. (2021). Double-
extortion ransomware: A technical analysis of maze
ransomware. In Proceedings of Future Technology
Conference (FTC) (Vol. 3, pp. 82–94).
https://doi.org/10.1007/978-3-030-89912-7_7
Lee, S., Lee, S., Park, J., Kim, K., & Lee, K. (2023). Hiding
in the crowd: Ransomware protection by adopting
camouflage and hiding strategy with the link file. IEEE
Access, 11, 92693-92704.
https://doi.org/10.1109/ACCESS.2023.3309879
Microsoft Corporation. (2023, June 4). Protect important
folders with controlled folder access. Microsoft 365
Defender. https://learn.microsoft.com/en-us/microsoft-
365/security/defender-endpoint/controlled-
folders?view=o365-worldwide
Moser, A., Kruegel, C., & Kirda, E. (2007, December).
Limits of static analysis for malware detection. In
Proceedings of the 23rd Annual Computer Security
Applications Conference (ACSAC) (pp. 421–430).
https://doi.org/10.1109/ACSAC.2007.21
Poudyal, S., & Dasgupta, D. (2021). Analysis of crypto-
ransomware using ML-based multi-level profiling.
IEEE Access, 9, 122532–122547.
https://doi.org/10.1109/ACCESS.2021.3109260
ScyllaHide. (n.d.). Advanced usermode anti-anti-debugger
for x64dbg/x32dbg [Computer software]. GitHub.
https://github.com/x64dbg/ScyllaHide
Security.com. (2024, December). US-China espionage.
https://www.security.com/threat-intelligence/us-china-
espionage
Sheen, S., Asmitha, K. A., & Venkatesan, S. (2022). R-
Sentry: Deception based ransomware detection using
file access patterns. Computers & Electrical
Engineering, 103, 108346.
https://doi.org/10.1016/j.compeleceng.2022.108346
Reverse Engineering LockBit Ransomware to Build Protection Method for Post-Compromised Machine
101
