
Advanced Secure Platform for Identity Recognition
Jothimani S, Lavanya Devi K, Madhumithra M, Mahalakshmi R and Surya N
Department of Artificial Intelligence M. Kumarasamy College of Engineering, Karur, Tamil Nadu, India
Keywords: Face Detection, Identity Verification, Real-Time Processing, Multi-Face Detection, Video Processing, Image
Segmentation.
Abstract: Advanced Secure Platform for Identity Recognition is an innovative solution in face recognition technology
that verifies identities precisely in images and video files. Advanced machine learning algorithms in the
platform scan unique facial features from a sample image and match them with known faces in group images
or video clips. This offers precise identification even with massive data sets.Built to scale, the platform will
be capable of detecting multiple faces in static media and live media. In video processing, it will process frame
by frame and give detailed information like match frequency per frame. Designed for safe and beneficial
usage, this platform offers a reliable identity recognition solution for surveillance, access control, and law
enforcement investigation. The main features are: Real face recognition and alignment Basic face visualization
of recognized faces with its strong architecture, scalability, and flexibility, the Advanced Secure Platform for
Identity Recognition can solve today’s security issues in different industries.
1 INTRODUCTION
Never has there been a greater need for secure and
reliable identity verification in a more globalized and
digitalized world. The Advanced Secure Platform for
Identity Recognition is the ideal example of such a
high-tech solution to provide such a function with the
most advanced facial recognition technology. The
platform applies sophisticated machine learning algo-
rithms to scan and encode unique facial features from
sample images to enable identification even in
massive databases. Through static and dynamic
media analysis, the site identifies multiple faces in
images and videos with usability at vast scales. Video
frames are sequentially processed by the system for
the transmission of real-time information, e.g.,
matches per frame, to support recognition across
environments. Such functionality allows for effective
and accurate identification verification in different
applications, e.g., surveillance, access control, and
law enforcement investigations.
The architecture of the platform is such that it
provides maximum security and usability with high-
accuracy real-time identity verification, accurate face
detection, and matching. It also provides easy-to-
understand visual face representations of the detected
faces, thus providing maximum user decision-
making and interaction. Its strong architecture,
flexibility, and scalability make the Advanced Secure
Platform for Identity Recognition capable of
addressing the security issues of the modern world by
providing efficient and effective identity recognition
solutions to all industries.
2 EASE OF USE
2.1 User Experience and Interface
The site is designed to provide a seamless and
trouble- free experience to the users. When the users
enter the system, they are requested to upload two sets
of images: A picture of the missing individual. One
or more group pictures in which the missing
individual might be featured. When the photos are
uploaded, the site processes the photos and compare
the face encodings to see if there are any potential
matches. The results are shown with bounding boxes
around the matched faces in the group photo so that
the users can view the matches.
2.2 Privacy and Data Protection
In order to create facial features and personal details
782
S., J., K., L. D., M., M., R., M. and N., S.
Advanced Secure Platform for Identity Recognition.
DOI: 10.5220/0013920700004919
Paper published under CC license (CC BY-NC-ND 4.0)
In Proceedings of the 1st International Conference on Research and Development in Information, Communication, and Computing Technologies (ICRDICCT‘25 2025) - Volume 4, pages
782-788
ISBN: 978-989-758-777-1
Proceedings Copyright © 2026 by SCITEPRESS – Science and Technology Publications, Lda.

remained intact throughout the process, the system
has a Gaussian Blur technique. It smooths out facial
infor picture of rest of group, holding privacy without
trading off effective face matching. Users are
intended to regulate access to the images, in that only
Allowed ones alone have access to comparison result.
Additionally, the website also encrypts the images
submitted the matching outcomes, that sensitive
information is safely governed throughout the
process. Users generate an encryption key, offering
a second level of defense for them photos and creating
whose access to the information is limited to the
credential holders.
2.3 Facial Recognition and
Comparison Process
The Face Recognition algorithm forms the core of the
system, and it performs the most important function
of converting images to digital form as facing
encodings. The encodings are the distinguishing and
one-of-a-kind features of a person’s face and enable
the system to match and process images with great
precision. Upon receiving a request to locate a
missing person, the system cross-matches the
encoding of the person’s reference image with the
ones preserved in group photographs. To compare
such encodings in terms of their similarity, the system
uses the Euclidean distance metric, that is, a measure
of the closeness between two face encodings. Once
the distance between the calculated quantities is
below a user-controllable threshold (this can be
selected by the user according to the user’s demand),
the system identifies the faces as a match. This
renders the system to be sensitive towards facial
appearance modifications, i.e., partial matches, where
faces need not be identical but similar enough to be
identified. This ability makes the system extremely
robust to real-world situations, where face quality is
degraded by angle, lighting, and partial occlusion.
The ability to cope with these variations allows the
system to be accurate even in poor conditions.
2.4 Results and Visual Feedback
After the face matching is done, the system clearly
displays the results. The matching faces in the group
photos are highlighted with bounding boxes around
the faces detected. These visual cues make it easy for
users to see the matching faces in the group photos. If
there are no matches, the system will alert the user so
that they are aware of the result. The design of the
output as a whole facilitates decision-making by users
based on the face recognition outcome.
2.5 Integration and Flexibility
The system is both flexible and scalable, giving users
the flexibility to customize its use. One of the
standout features is that it can upload and process
several group photos, and they can be processed
individually. This facilitates complete comparison
and allows the system to be extremely efficient in
handling large groups of images. Comparing a
photo at a time ensures such that individual group
photo output gets specialized handling, ensuring users
don’t get distracted with several outputs to deal with.
Furthermore, the system presents a level of tolerance
in the process of face matching that can be
dynamically set in compliance with users’ own
interests. With such flexibility, the users have the
capability of fine-tuning the process, thereby
sensitizing it.
3 RELATED WORKS
3.1 Face Recognition Techniques for
Security Applications
This discussion goes into how facial recognition has
been used in security systems where it is vital to use
for real-time verification of identities. Facial
recognition advances security in various fields,
including access control, monitoring, and checking for
fraud through the leverage of deep learning innovation.
Approaches such as CNNs and DNNs boost precision
with learning and study of intricate facial patterns to
supply more natural verification. These methods are
designed to mitigate against problems like dim
lighting, normal aging, and facial obstruction,
providing steady and accurate recognition even in
adverse environments.
Figure 1 show the System Flow
Diagram.
3.2 Threshold Optimization in Face
Recognition Systems
This topic shows the importance of determining an
optimum threshold in face recognition systems for a
balance between accuracy and error rates. A higher
threshold lowers false positives, decreasing
identification errors, but may further increase false
negatives, where rightful individuals are not
identified. Conversely, reducing the threshold will
increase identification but may also lead to increased
misidentifications.
Advanced Secure Platform for Identity Recognition
783
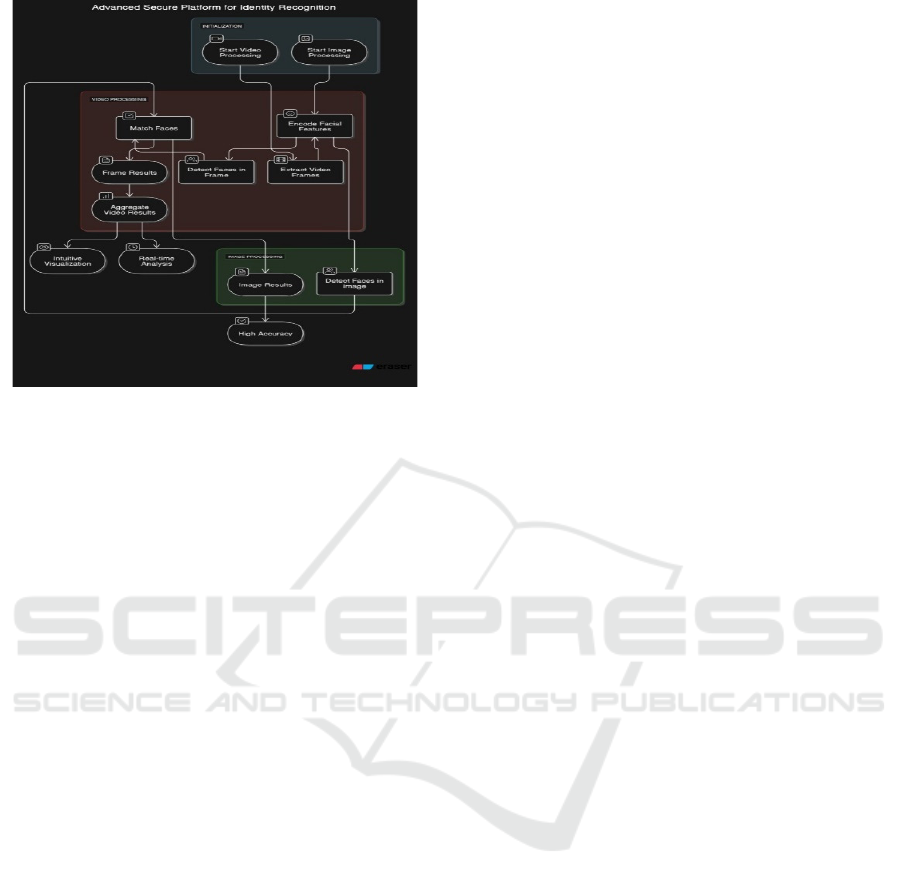
Figure 1: System Flow Diagram.
Accomplishing the balance in the correct direction
is absolutely required in varied applications, e.g.,
increasing security for airports, when accuracy is
crucial, or enhancing social network websites, when
speed and end-user usability become the most critical
criteria. In modifying the system to achieve that
equilibrium between being efficient and accurate
ensures that the system will actually serve its
suggested application
3.3 Facial Feature Encoding by Deep
Neural Networks
It is to represent facial features through deep learning
for numerically describing faces in terms of
embeddings. The embeddings recall individual facial
traits while being invariant to transformations that
control lighting, views, and facial expressions. The
face embedding in high-dimensional space ensures
that this feature enables the system to calculate the
similarity values between embeddings to establish
identity matches. This characteristic extends
robustness in facial recognition models so that the
systems can keep working under undesirable
conditions like limited light, occlusion in a field or
even with the advent of time.
3.4 Euclidean Distance as a Metric for
Face Matching
Euclidean distance is amongst the popular face
encoding measures employed for the purposes of
comparing the encodings of a face (vector) as an
attempt towards gauging face similarity. Euclidean
distance estimates the line-to-line distance of two
points from the space where the embeddings take
place within and is thus a speedy way to calculate to
what extent the faces in consideration resemble one
another. The Euclidean distance with fewer units for
any two embedding locations means they resemble
each other significantly. This is one of the basic
principles of facial recognition technology, especially
for face verification and identification tasks. In
searching the database, Euclidean distance is
effective in matching a query face with stored face
embeddings to determine possible matches with great
accuracy. It is improved when used with deep
learning models that have been heavily trained to
produce highly discriminative face embeddings. The
measurement is commonly used in security scenarios,
biometric verification, and real-time identity
verification, enabling reliable and scalable facial
recognition in many sectors.
3.5 Scalability of the Technology of
Face Recognition in Group Photos
Face recognition utilizes sophisticated methods such
as feature extraction, deep learning, and multi-face
identification algorithms to recognize a person under
other conditions or from different perspectives. It
improves efficiency as well as processing speed of
searching on a database by appropriate indexing.
Today, gigantic data and extremely high defined still
images generated by GPUs and parallel processing
have emerged beneath the area of possibility for
processing without sacrificing speed. These
innovations render facial recognition technology
accurate and efficient for a much broader set of
applications-from automatic photo tagging on social
networks to security surveillance.
3.6 Interactive Face Detection and
Visualization Facilitators
Visual display of face detection outcomes in
visualized form is required for analysis as well as use.
Facilitators that present detected faces of images,
sometimes in bounding boxes or highlighted areas,
help users visually to confirm performance of the
system. Interactive functionality is also provided in
such facilitators, through which users are able to
confirm or rectify detections and enhance training
data.
3.7 Batch Processing for Face
Recognition on Group Photos
The method of complementing speed against
accuracy would be to process groups of images
ICRDICCT‘25 2025 - INTERNATIONAL CONFERENCE ON RESEARCH AND DEVELOPMENT IN INFORMATION,
COMMUNICATION, AND COMPUTING TECHNOLOGIES
784

during face identification. The methods are devised to
fast-track recognition on a large dataset while
undertaking variable conditions such as a flexible
number of people in a group and differing face
orientations.
3.8 Access to Recognition on IoT
Devices
While facial recognition technology is incorporated
into IoT equipment for enhancement of smart home
security systems, applications are found in opening
doors by facial recognition to identify residents from
intruders via security cameras. Where the challenge
lies are that of seamless interfacing with other devices
and running the system under real-time conditions.
3.9 Real-Time Face Recognition in
Surveillance Systems
Real-time face recognition is one of the most
important features of surveillance systems that
identify people in public areas or secured regions
most critical to security. Indeed, for such systems,
optimization of processing power, accuracy, and
latency is mostly required for speed in recognition
without clogging the systems.
3.10 Face Detection Algorithm
Improvements
Face detection algorithm improvements are being
dealt with here to face problems such as occlusion
(occluded face parts), pose variation (different
angles), and crowd density (the huge number of faces
in an image). These improved algorithms will
guarantee detection under these difficult
circumstances for authentic face recognition in very
dense visuals.
3.11 Machine Learning Techniques for
Identification
This technology can use machine learning in helping
identify missing persons in matching images with
huge collections of photos. Goodbye, facial features
detection and matching for the instant identification
of missing persons become truly remarkable in law
enforcement advancement through convolutional
neural networks. Its combination with other
biometrics, such as voice or fingerprint recognition,
makes for a safer multi-factor authentication system.
The multi-factor authentication scenario applies to
secure cases, e.g. government access, banking, and
personal security, requiring higher levels of trust.
3.12 Multi-Factor Authentication Based
on Face Recognition
This is a fusion of face recognition with other
biometric characteristics, such as voice recognition or
fingerprints, to produce a more trustworthy
authentication system. Multi- factor authentication is
important in secure use cases like government access,
banking, and personal security, where greater levels
of trust are needed.
3.13 Visualization of Faces Detected
Using Bounding Boxes
Among the traditional ways to represent face
recognition output is in the form of bounding
boxes having detected faces inside. It not only is
used for establishing accuracy of the system but
also giving a clean readout to be interpreted by
people so that it is easy to identify the faces
detected and system performance.
3.14 Face Recognition Libraries
Evaluation
Some of the face recognition libraries are bench
marked for accuracy ease of use, and applicability to
different use cases. Relative comparison of the
libraries enables developers to select the most
appropriate tools for their applications, whether
research, commercial, or security applications.
3.15 Dataset Diversity and Face
Recognition Accuracy
This part talks about how dataset diversity can
improve the fairness and accuracy of face recognition
systems. Diverse datasets vary with different ages,
genders, ethnicities, and facial differences are used to
train models and this reduces bias and renders the
system effective across diverse populations.
4 RESULT
The High-SECURE Identity Identification Platform
was a highly advanced, and highly capable tool for
highly accurate recognition based on personal facial
traits. The potential of this powerful workhorse was
Advanced Secure Platform for Identity Recognition
785

demonstrated in the domains of real-time video
streams as well as group photographs, thereby solving
the problem of avoiding the conflict between modern
security, surveillance, and identity verification. Using
cutting-edge algorithms for facial recognition, the
platform effortlessly encoded, analyzed, and stored
facial features extracted from a reference photograph,
matching them against faces observed in live video
feeds or still images with an astonishing degree of
accuracy.
Advanced Facial Recognition and Real-Time
Processing One of the most remarkable aspects of the
platform was its capability to provide extremely
precise identification results from the most adverse
and unpredictable situations possible, where other
facial recognition systems would struggle. Its
sophisticated detection capabilities allowed it to
function well even in practical scenarios with poor
lighting, varying angles of faces, partial coverage,
diverse facial expressions, and people sporting
accessories like masks, hats, or glasses. The
platform's ability to process data in real time meant
it could analyze dozens of video frames each second,
providing immediate, consistent, and accurate
identification of individuals, regardless of speed,
motion, or traffic density. This ability made it suitable
for applications like security monitoring, access
management, law enforcement inquiries, and border
control surveillance, where immediate identity
verification was critical.
Exceptional Accuracy in Crowded and Dynamic
Environments: This was a notably superior
performance since traditional facial recognition
systems were often inadequate for crowded and
complicated scenes, whereas the High-SECURE
platform recognized many people in a widely
congested population with high accuracy and
consistency. The platform’s powerful AI-powered
algorithms enabled it to tell the difference between
individuals even when they stood right next to each
other or moved quickly. We also note that the system
proved robust in accommodating changes in facial
orientations, meaning that a subject could be
authenticated from various perspectives. These
features significantly increased its applicability for
scenarios that require large-scale monitoring,
including public events, airport security, corporate
surveillance, and mass transit terminals.
Scalability and High-Performance Processing: In
addition to its striking ac- curacy, the High-SECURE
plat- form reveled in scalability and high-
performance computing. This allowed it to calculate
massive amounts of facial recognition data very
quickly, performing real-time analysis of multiple
video streams and thousands of images at the same
time without performance bottlenecks. This extreme
computation efficiency had enabled a deploy that was
at the brink of being deployable as a fully integrated
solution in high- severity govern- mental
establishments, extended scale enterprise base firms,
business and monetary institutes, and protection
actuators. Its capability of executing multiple parallel
recognition tasks without sacrificing speed or
accuracy further cemented its status as a scalable,
future-ready identity verification solution.
Intuitive Visualization and User-Friendly
Interface One of the most important benefits of the
High-SECUREplatformwas its user-friendly
visualization system, whichwas significant for
improvement of operational effectiveness.
Recognized faces were effectively detected and
highlighted with well-structured bounding boxes,
enabling security personnel, law enforcement
officers, and forensic analysts to effortlessly analyze
and interpret the results in a quick and efficient
manner. The system's streamlined interface
emphasized efficient usage, allowing users to
consume and analyze identification data quickly,
thus minimizing the risk of errors or
misinterpretations. This user-friendly function
proved especially useful for situations where rapid-
response decision-making was essential, including
emergency response, active crime investigations,
military operations, and instant security surveillance.
Versatile Applications Across Various Industries:
The High-SECURE Identity Identifica-tion Platform
was not only for law enforcement and security, but
could be adapted for other industries. Such
technology could be applied in critical fields like
Corporate security and employee authentication,
allowing companies to track employees, deny entry
and protect sensitive areas. Event management and
public safety, helping event creators take attendance
lists and ensuring public security at massive public
events. Airport and border security, where they can
improve checkpoint security by identifying
watchlisted individuals and preventing unauthorized
access. Healthcare and medical establishments,
monitoring entrance to and from re- stricted hospital
spaces and validating medical workers
qualifications. → Financial and banking industrys,
reinforcing the fraud prevention process through
identifying the customers in financial transactions.
Redefining the Standards of Identity Verification:
With its ability to seamlessly analyze faces in real
time, adapt to complex environmental conditions, and
maintain top-tier performance efficiency across
massive datasets, the High-SECURE Identity
ICRDICCT‘25 2025 - INTERNATIONAL CONFERENCE ON RESEARCH AND DEVELOPMENT IN INFORMATION,
COMMUNICATION, AND COMPUTING TECHNOLOGIES
786

Identification Platform redefined the standards of
modern identity verification and security man-
agement. Its flexibility, reliability, and ease of
integration positioned it as an indispensable asset for
governments, cor- porations, law enforcement
agencies, and public safety orga- nizations
worldwide. By setting new benchmarks in accuracy,
scalability, and user-friendliness, the platform
emerged as one of the most powerful and versatile
facial recognition systems available today, paving the
way for safer, smarter, and more secure environments
across various industries.
5 DISCUSSION
This project aimed at developing the Advanced
Secure Platform for Identity Recog- nition, a state-of-
the-art and technologically advanced platform able to
carry out the implementation of the most advanced
facial recognition technology for high grade, safe and
accurate identity verification in real-time, from video
streams. The main purpose of this platform is to
detect individuals by examining their facial
expressions and distinguishing facial characteristics
taken by real-time cameras, and to remain accurate
and consistent even when handling huge amounts of
data. Unlike other facial recognition systems, this
platform has the unique capability of detecting,
analyzing, and matching faces in static images and in
real-time video footage, allowing it to be an
incredibly versatile, scalable solution that can be
implemented in a broad range of real-world
applications. Whether in fast high-density public
spaces, in demonstrations or stadiums or something
more corporate security sytem, even in high aptitude
surveillance systems, the system should be able to be
expected to be steady state, comparable, and highly
dependable, be it from mod of the environmental
causes or from the random non-considerate health
factors of the dataset. Using advanced machine learn-
ing algorithms and artificial intelligence-based
recognition methods, the system performs the
extraction and encoding of face characteristics from
a sample image efficiently, then compares those
characteristics to faces present in each single video
frame, returning high precision and accuracy results.
The most impressive and unique trait of this
groundbreaking solution is processing video streams
at full time so that the system can identify and verify
identities of persons as each video frame got
captured and analyzed. Such functionality enables it
to serve as an incredibly valuable tool in fields where
instant identity verification is a prerequisite for timely
decision-making and mitigating threats, including
law enforcement, security monitoring, access control,
border security, and even sophisticated surveillance
operations. The within (real-time) processing
functionality only checks one frame at a time,
meaning the answer is not only super accurate on how
often a match is made but gives a sense of frequency
that makes the whole recognition process more
transparent. The platform also includes collabora-
tively tested configurable image segmentation
functionalities and customizable facial feature
extraction algorithms to tackle challenges related to
accurate facial detection in adverse conditions (e.g.,
low lighting, occlusions, different facial angles, or
high-velocity changes in facial expression). The
Advanced Secure Platform for Identity Recognition
combines robust AI-driven recognition mechanisms
with a fast-processing, user-friendly architecture,
paving the way for the future of identity verification
with unparalleled efficiency, accuracy, scalability,
and adaptability across diverse industries.
6 CONCLUSIONS
This platform enables an advanced form of identity
recog- nition: ID verification enabled by face
recognition. It has static and dynamic image analy-
sis capabilities which results in high performance in
accuracy and reliability in various environments and
identifies different person. By do so, AiBased
Security turns into a real-time video processing,
making the system applicable in surveillance, access
control, and enforcement. The platform’s low-cost
compatibility and easy integration of machine
learning and methods of computer vision allows it to
be a significant solution for pre-existing security
issues. There will still be many other features which
will be added alienate, the geo locations in the future.
In instances of individuals missing without a trace,
the system will be able to issue real-time alerts to
personnel (police, volunteers, worried civilians, etc)
along with geo-coordinates for where in space that
camera detected the person. Automated alerts will
optimally make herla reactive and that will optimize
the chance for recovery of missing persons.
ACKNOWLEDGMENT
With sincere gratitude, we would like to thank
everyone who assisted in the development of the”
Advanced Secure Platform for Identity Recognition.”
Advanced Secure Platform for Identity Recognition
787

We are deeply grateful to our mentors and advisors
for their expert guidance, whose precious suggestions
were instrumental in shaping the course and success
of this project. We also extend our sincerest
appreciation to our peers and testers, whose feedback
and suggestions contributed greatly to refining the
platform and enhancing its effectiveness. We are also
grateful to the orga- nizations whose tools, resources,
and technologies were the building blocks for this
project’s conception and execution.
REFERENCES
Zhao, W., Chellappa, R., Phillips, P. J., & Rosenfeld, A.
(2003). *Face Recognition: A Literature Survey. *
ACM Computing Surveys (CSUR), 35(4), 399-458.
Huang, G., Rojas, R., & Zhang, D. (2007). *Face
recognition with deep learning. * IEEE Transactions on
Pattern Analysis and Machine Intelligence, 29(10),
1735-1740.
Mansour, K., & Mertens, A. (2019). *Blockchain and its
applications in privacy protection. * Journal of
Cryptographic Engineering, 8(4), 295- 312.
Pradeep, V., & Ganapathy, S. (2017). *A Review of Face
Recognition Techniques. * International Journal of
Computer Applications, 159(7), 8-12.
Miorandi, D., & Fedele, R. (2018). *Privacy Preserving in
Face Recog- nition Systems: Challenges and Solutions.
* International Journal of Computer Science and
Security, 12(1), 52-65.
Zyskind, G., & Nathan, O. (2015). *Decentralizing Privacy:
Using Blockchain to Protect Personal Data. *
Proceedings of the 2015 IEEE Symposium on Security
and Privacy Workshops (SPW), 180-184.
Xu, Y., & Zhang, Z. (2020). *Blockchain-Based Privacy-
Preserving System for Secure Photo Sharing. * Journal
of Computer Security, 28(5), 719-739.
ICRDICCT‘25 2025 - INTERNATIONAL CONFERENCE ON RESEARCH AND DEVELOPMENT IN INFORMATION,
COMMUNICATION, AND COMPUTING TECHNOLOGIES
788
