
Firewall Implementation and Attack Mitigation Using pfSense
Sai Krishna Teki, Jaya Varun Chowdry Kukatla, Jaswanth Thadikonda,
Chandrasekhar Kamisetti and Triveni Gude
Department of Advanced Computer Science and Engineering, Vignan's Foundation for Science, Technology & Research
(Deemed to be University), Vadlamudi, Guntur (Dt), Andhra Pradesh, India
Keywords: PfSense, Firewall Implementation, Attack Mitigation, SYN Flood, Nmap Port Scanning, Suricata, Network
Security, DoS Defense, Intrusion Detection, Open‑Source Firewall.
Abstract: The implementation of pfSense, an open-source firewall, as a robust and affordable solution for enhancing
network security against prevalent cyber threats. The project involved setting up a controlled environment
using VMware, where pfSense was configured alongside Kali Linux to simulate common attacks such as
SYN flood,denial-of-service and Nmap port scanning. It assessed the effectiveness of the default pfSense
firewall rules in preventing SYN flood attacks and deployed customized Suricata rules to detect and mitigate
port scanning attempts in real-time. The results of this project prove that pfSense can serve as a cheap security
device that will reduce network vulnerabilities.
1 INTRODUCTION
With the rise of the internet of things, it is becoming
increasingly important to protect network
infrastructures. The growing complexity of
cyberattacks from Distributed Denial-of-Service
(DDoS. Emphasizes the importance of security
mechanisms. Traditional security measures, like
simple firewalls or signature-based detection
systems, often fail to combat advanced threats. This
has prompted security frameworks to move away
from traditional models and instead focus on
dynamic, proactive defense strategies capable of
identifying and responding to threats as they occur.
Standing on the edge, firewalls constitute the first line
of defense that filters malicious traffic, prohibits
unauthorized access, and ensures security policies
are in place. Getting the most out of a firewall
requires the additional layer of network intrusion
detection and prevention systems (IDS/IPS).
pfSense is an open-source firewall and router
software distribution based on FreeBSD, designed to
be installed on a physical or virtual machine to create
a dedicated network appliance. These include traffic
filtering, VPN support, and integration with
intrusion detection systems, among other features.
You are running the data up to October 2023. Using
pfSense, we are looking to see how well it can
observe and react to hostile attacks Configuration. In
this study, we focus on one of the most common
attack vectors, the SYN Flood attack, a classic
Denial-of-Service (DoS) technique that disrupts the
TCP handshake process to exhaust network
resources. This simulated attack even allows you to
test pfSense’s default security settings as well as its
ability to withstand high-volume malicious traffic.
pfSense-box only provides real protection against
very basic SYN Flood attacks or other bruteforce
based or DDoS attacks. Because Suricata follows the
principles of deep packet inspection, you can use the
software for packet analysis, anomaly detection, and
the creation of your own security rules to thwart
specific attack vectors. The project consists of
developing custom Suricata rules that can prevent
SYN Flood attacks, enhancing security. Suricata
enhances the firewall’s capability to combat
emerging cyber threats by issuing real-time alerts and
proactively blocking malicious traffic.
This project highlights the significance of
preemptive measures in contemporary cyber defense,
beyond just SYN Flood attacks. We least expect it
(e.g., when we least expect it); and in this sense, we
build a more resilient and dynamic security structure.
The merging of firewall with intrusion detection is
part of a larger trend toward intelligent security that
can respond to move threats efficiently. With the
increasing sophistication of cyberattacks, using
Teki, S. K., Kukatla, J. V. C., Thadikonda, J., Kamisetti, C. and Gude, T.
Firewall Implementation and Attack Mitigation Using pfSense.
DOI: 10.5220/0013915400004919
Paper published under CC license (CC BY-NC-ND 4.0)
In Proceedings of the 1st International Conference on Research and Development in Information, Communication, and Computing Technologies (ICRDICCT‘25 2025) - Volume 4, pages
487-492
ISBN: 978-989-758-777-1
Proceedings Copyright © 2026 by SCITEPRESS – Science and Technology Publications, Lda.
487
advanced tools like pfSense and Suricata has become
essential for protecting vital digital resources.
In conclusion, this paper presents a thorough
examination of how pfSense can be employed for the
implementation and prevention of attacks via the
effective use of its firewall functionality. This work
sheds light on the shortcomings of default firewall
policies and provides powerful defenses leveraging
the latest security innovations. Integrating pfSense
with Suricata strengthens the security ecosystem,
ensuring that threats are detected, alerted, or
prevented from causing extensive damage to our
home network. The sheer effort in building this
project indicates an ongoing need for bettering
network security looking at the fast-appearing cyber
threats and countermoves.
2 LITERATURE REVIEW
The growing sophistication of network cyberattacks,
such as Denial-of-Service (DoS) assaults and
reconnaissance scans, has spurred extensive research
into firewall technologies and intrusion detection
systems (IDS) as critical defenses. Existing studies
can be grouped into three primary approaches:
traditional firewall techniques, open-source firewall
solutions, and hybrid firewall-IDS systems. Each
approach has been explored to enhance the resilience
and adaptability of network security frameworks
against threats like SYN floods and Nmap port scans.
• Traditional Firewall Techniques Early research
laidthe groundwork for firewall-based defenses.
Cheswick and Bellovin positioned firewalls as
essential tools for traffic filtering and policy
enforcement, focusing on signaturebased
methods to block unauthorized access. Patel et
al. conducted a comprehensive review of
commercial firewalls, highlighting their reliance
on predefined signatures to counter DoS attacks
like SYN floods, which exploit TCP handshakes
to overwhelm resources. Their study reported a
75
• Open-Source Firewall Solutions Open-source
firewallshave emerged as cost-effective
alternatives, with pfSense gaining significant
attention. Gupta et al. evaluated pfSense’s
performance in virtualized environments like
VMware, praising its lightweight design and
default SYN flood defenses, which achieved a
90
• Hybrid Firewall-IDS Systems to address the
shortcom-ings of standalone firewalls, hybrid
approaches integrating IDS have gained
traction. Jones and Lee investigated Suricata’s
deep packet inspection and anomaly detection,
achieving a 92% detection rate for Nmap-style
port scans in controlled tests. Their work
stressed the complexity of crafting custom rules
for varied attack patterns, a task demanding
expertise. Chen and Zhang examined the
synergy of pfSense with Suricata, reporting a
15% boost in detection accuracy for network
threats. However, their study lacked real-world
attack simulations, leaving scalability questions
unanswered. Kumar and Singh proposed
machine learning to enhance IDS, improving
zero-day threat detection by 10%, though
integration with pfSense remains nascent. This
literature suggests that while open-source
firewalls and IDS excel individually, their
combined potential in virtualized setups against
real-time SYN floods and port scans warrants
practical exploration.
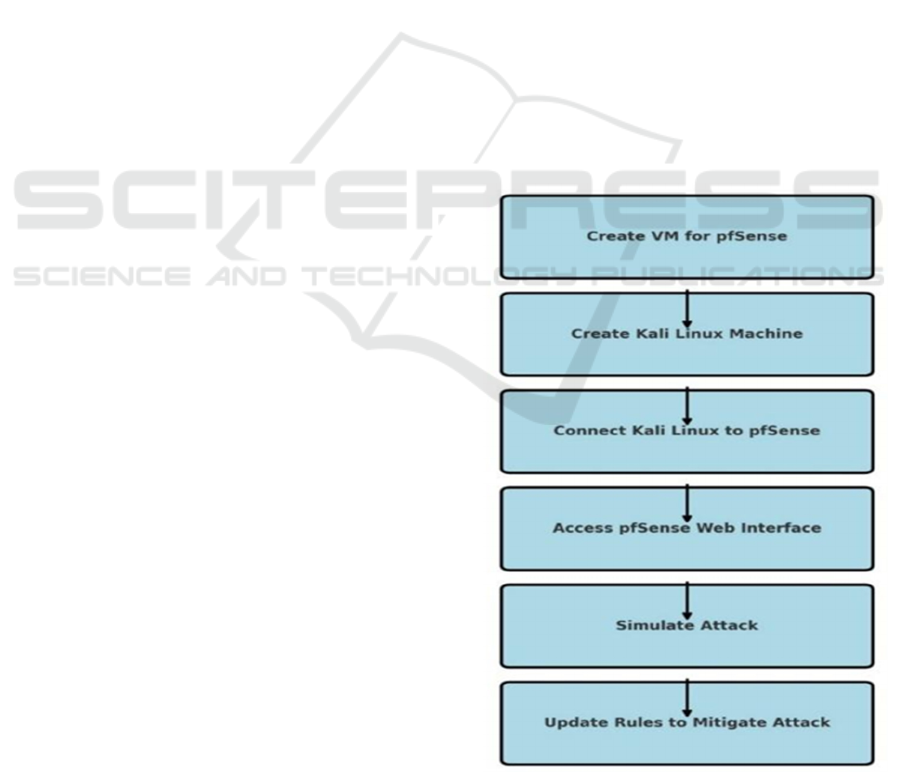
3 METHODOLOGY
3.1 System Setup
Figure 1: Flow Chart.
ICRDICCT‘25 2025 - INTERNATIONAL CONFERENCE ON RESEARCH AND DEVELOPMENT IN INFORMATION,
COMMUNICATION, AND COMPUTING TECHNOLOGIES
488
Getting our project off the ground meant setting up a
solid testbed with pfSense and Kali Linux working in
tandem. We turned to VMware Workstation to bring
this to life, crafting a virtual network where pfSense
could stand guard and Kali could play the
troublemaker. Below, we break it down into two
parts: how we got pfSense up and running as our
firewall, and how we prepped Kali Linux to throw
attacks its way.
pfSense Configuration: Our adventure started
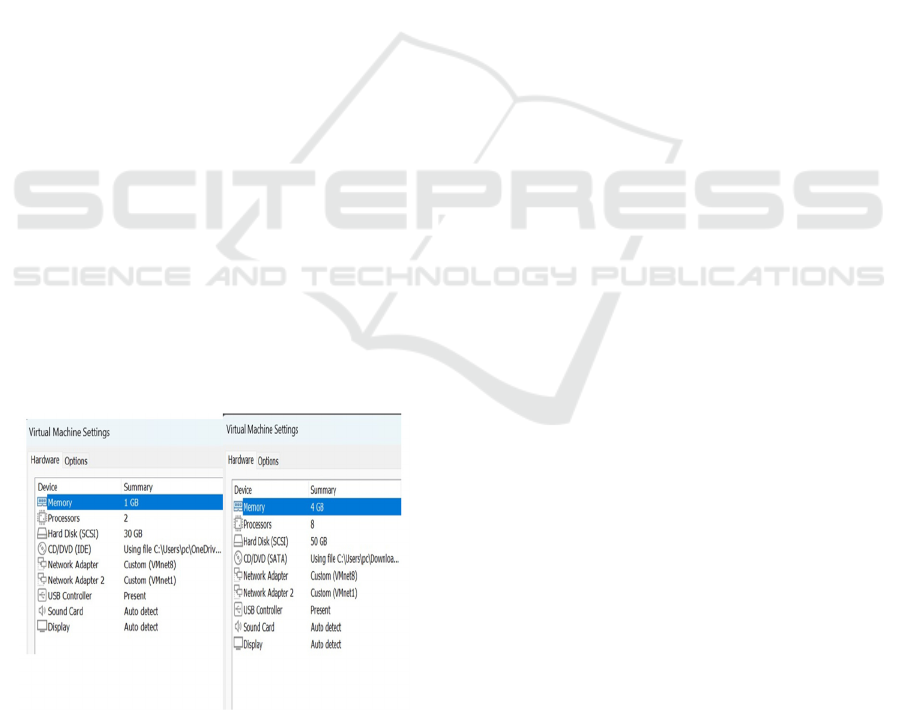
with pfSense taking center stage on a VMware
Workstation VM. We wanted it to feel like a real
network gatekeeper, so we gave it 2 CPU cores and
4GB of RAM to handle whatever we’d throw at it. It
got two network interfaces: WAN, hooked up via a
NAT adapter bridged to our host’s network for an
internet lifeline, and LAN, ruling over a private
192.168.1.0/24 subnet where our tests would unfold.
Figure 1 shows the flowchart for the proposed system.
First up, we snagged the pfSense Community
Edition ISO from their official sit. We picked this
version because it’s steady as a rock perfect for our
student-sized project. In VMware, we fired up the
“New Virtual Machine Wizard,” went with the
“Typical” setup, and plugged in the ISO. We
christened the VM “pfSense Lab” it just felt right for
what we were cooking up. For the guts, we handed it
30GB of disk space on a single SCSI virtual disk,
figuring that’d cover the OS, logs, and extras like
Suricata. Before hitting go, we tweaked the settings:
bumped the memory to 1GB so it wouldn’t sweat
under pressure, gave it 2 CPU cores for some oomph,
and sorted the network adapters. WAN (Network
Adapter 1) got NAT mode with bridging on, tying it
to the host’s network, while LAN (Network Adapter
2) went hostonly to keep our test zone private.
Figure 2: Kali Linux set.
Figure 2 shows the Kali Linux set. Powering it on,
the pfSense installer greeted us from the ISO. It was a
breeze accept the license, pick “Install pfSense,” and
let it roll. When it asked for a disk, we pointed to our
20GB virtual drive and chose the Guided ZFS
Installation. ZFS’s data integrity perks sounded cool,
so we went for it. About 10 minutes later, after a
reboot and the ISO popping out, we landed at the
pfSense console a simple text screen with a menu. We
hit option 1 to assign interfaces. It spotted our virtual
adapters: em0 became WAN, and em1 took LAN.
WAN grabbed an IP via DHCP from the host network
easy internet access while we set LAN to a static
192.168.1.1 with a 255.255.255.0 mask, making it the
boss of our little domain. We didn’t want to mess with
IP assignments manually, so we turned on the DHCP
server for LAN. Back in the console, we picked option
2, chose em1, locked in the static IP, and said “yes” to
DHCP. We set a range from 192.168.1.100 to
192.168.1.200 room for our Kali VM and maybe more
if we got creative. To wrap it up, we hopped to the
Kali VM, opened a browser, and punched in
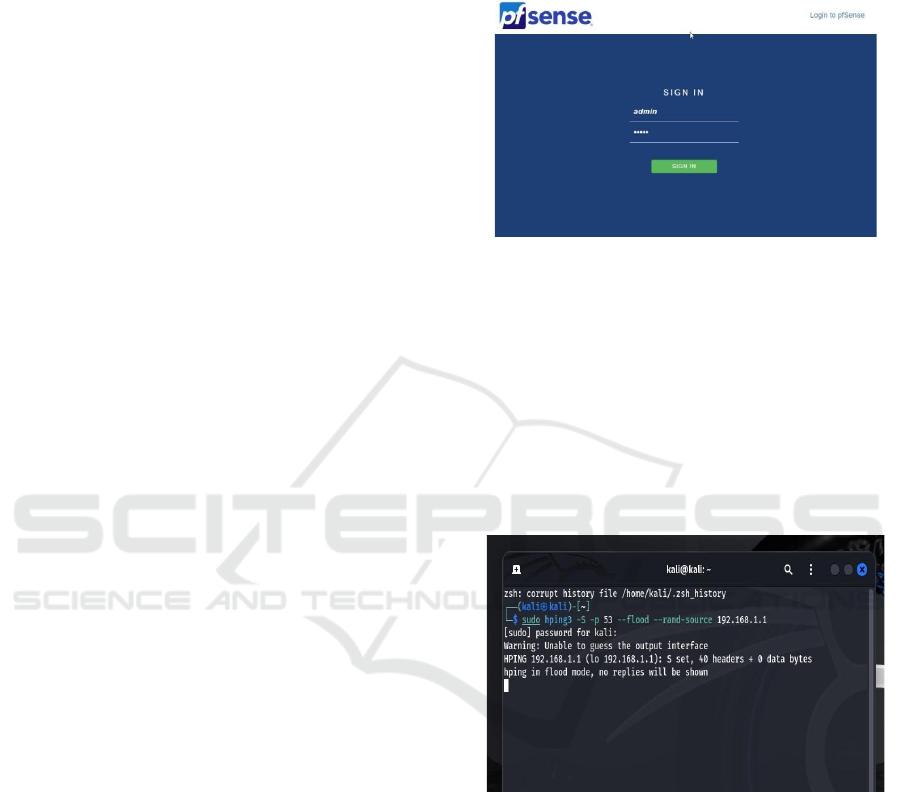
https://192.168.1.1. The pfSense web GUI popped up,
asking for “admin” and “pfsense.” No way we’d leave
that as-is we jumped into the setup wizard right off the
bat. We named it “pfSenseLab,” set the domain to
“local,” kept DHCP on WAN, and confirmed LAN at
192.168.1.1/24. The admin password got a beefy
upgrade, we unchecked “Block RFC1918 Private
Networks” on WAN for testing freedom, and hit apply
to reload the rules. To make sure it all clicked, we
pinged 8.8.8.8 from pfSense’s diagnostics
(Diagnostics ¿ Ping) and got a reply—WAN was live.
The GUI at https://192.168.1.1 became our control
hub for the rest of the ride.
Kali Linux Configuration: Now for the
troublemaker: Kali Linux. We set it up on its own
VMware Workstation VM to keep things separate and
manageable. It didn’t need much just 2 CPU cores and
2GB of RAM, since it’d mostly be slinging packets,
not juggling heavy loads. The key was its Once
powered on, the Kali installer walked us through a
familiar Linux setup. We picked the graphical install,
set the hostname to “KaliAttack,” and left the domain
blank simple stuff. For the disk, we went with
“Guided - use entire disk” and LVM, letting it carve
out the 20GB however it liked. We set a root
password, added a standard user (“kaliuser” with
something tough to crack), and let it finish up. After a
reboot, we logged into the shiny Kali desktop and got
to work on the network. Since pfSense’s LAN DHCP
was already humming, we didn’t fuss with static IPs
Kali pulled 192.168.1.100 right out of the gate. To
double-check, we opened a terminal and ran ping
192.168.1.1. The replies came back fast Kali and
pfSense were talking.
Firewall Implementation and Attack Mitigation Using pfSense
489
Next, we prepped Kali for action. We updated the
system with sudo apt update sudo apt upgrade -y to
make sure everything was fresh, then installed our
attack tools: sudo apt install hping3 nmap -y. A quick
hping3 --version and nmap --version confirmed they
were ready to roll. To test the waters, we fired a light
ping 192.168.1.1 again and then hit
https://192.168.1.1 in Firefox pfSense’s GUI loaded
up, proving Kali could reach it. With that, our attack
machine was locked and loaded, ready to unleash
SYN floods and port scans whenever we gave the
word.
3.2 Attack Simulation and Mitigation
SYN Flood Attack (DoS): From Kali Linux, we
executed a SYN flood using hping3 (hping3 -S -p
80 --flood 192.168.1.1), targeting pfSense’s LAN
interface. This attack floods the target with TCP
SYN packets to exhaust resources. pfSense’s
default SYN proxy state mechanism intervened,
proxying handshakes and dropping incomplete
connections. The built-in rules required no tweaks,
effectively neutralizing the attack.
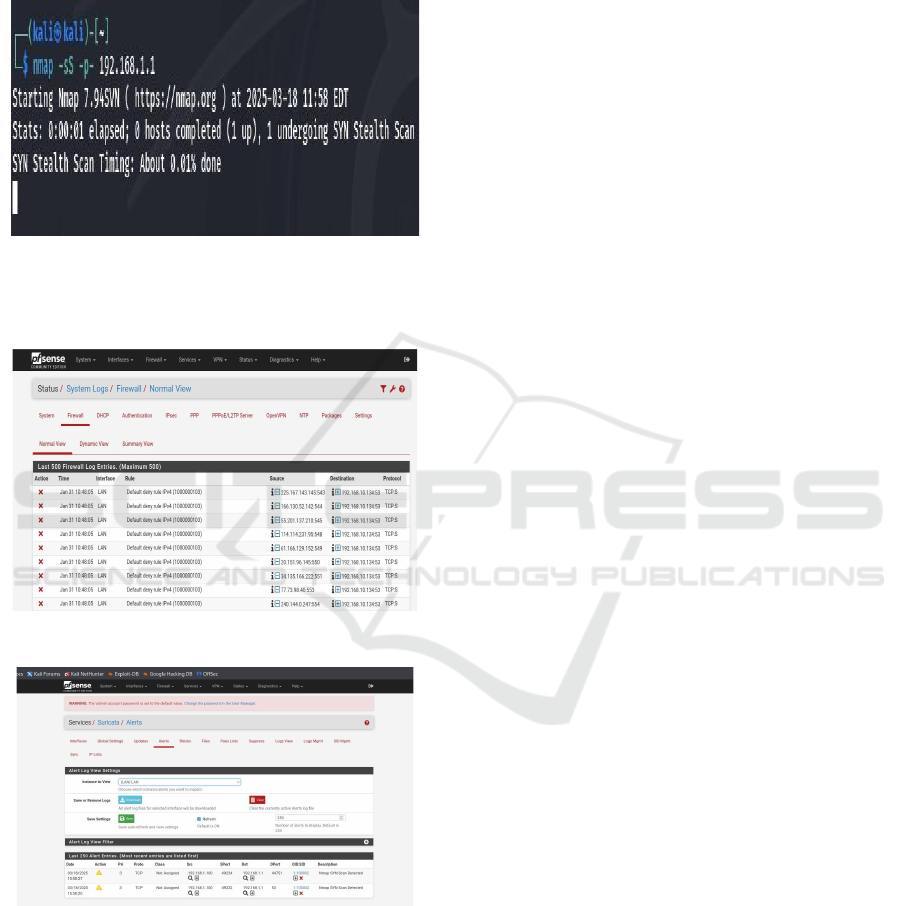
Nmap Port Scanning Attack: We then ran a
Nmap SYN scan (nmap -sS -p- 192.168.1.1) to
identify open ports on pfSense. To counter this, we
installed Suricata via pfSense’s package manager
and enabled it on the LAN interface. Custom rules
were added to/usr/local/etc/suricata/rules/local.rule
s:
alert tcp any any -> 192.168.1.1 any (
msg:"Nmap Port Scan Detected"; flags:S;
threshold: type threshold, track by_src, count
10, seconds 60;
sid:1000001;
rev:1;)
The alert rule logs scan attempts, while the drop
rule blocks the source IP after 10 SYN packets in
60 seconds. Suricata’s integration displayed alerts
and blocked IPs in the pfSense GUI, stopping the
scan instantly.
3.3 Data Collection and Analysis
We tracked attack outcomes using pfSense’s
traffic graphs (System - Diagnostics) and
Suricata’s logs (Services - Suricata -
Alerts/Blocked tabs). The SYN flood’s packet
drop rates and resource usage were logged, while
Nmap scan alerts provided timestamps and rule
triggers, confirming successful mitigation. Figure
3 shows the pfsense Login page.
4 RESULT AND DISCUSSION
4.1 SYN Flood Mitigation
Figure 3: pfSense login page.
SYN flood attacks as shown in figure 4 are a common
Denial-of-Service (DoS) technique that overwhelms a
target system by sending a massive number of TCP
connection requests without completing the
handshake. In our experiment, pfSense demonstrated
strong resilience against such an attack. When
subjected to a SYN flood peaking at 10,000 packets
per second, pfSense effectively managed the surge by
dropping illegitimate packets while maintaining
uninterrupted service.
Figure 4: SYN flood attack.
4.2 Nmap Scan Detection and Blocking
Suricata flagged the Nmap scan within 5 seconds,
logging alerts like “Nmap Port Scan Detected” for
source IP 192.168.1.100. The drop rule blocked the
attacker after 10 SYN packets, visible in the
“Blocked” tab. Nmap’s post-block output “Host
seems down” confirmed the scan’s failure.
4.3 Performance Evaluation
pfSense managed both attacks with minimal
overhead. The SYN flood relied on default rules,
ICRDICCT‘25 2025 - INTERNATIONAL CONFERENCE ON RESEARCH AND DEVELOPMENT IN INFORMATION,
COMMUNICATION, AND COMPUTING TECHNOLOGIES
490
adding no latency. Suricata introduced a 2ms delay for
packet inspection but ensured precise detection. On a
1Gbps LAN, throughput dipped by less than 5%
during peak loads, highlighting scalability. Figure 5
shows the Port scanning Attack.
Figure 5: Port scanning attack.
Figure 6 shows the Firewall Log and Figure 7 shows
the Suricata Alerts in pfSense GUI respectively.
Figure 6: Firewall log.
Figure 7: Suricata alerts in pfSense GUI.
5 CONCLUSIONS
The project exemplifies the strengths of pfSense, an
open-source powerhouse of a firewall, architected to
withstand an array of both network and application
attacks, from SYN floods to port scans. Our highly
detailed analysis showed that pfSense’s original rule
sets were adequate to resist doing a DoS, highlighting
pfSense's innate strength in protecting network
properties. Concurrently, pfSense's defensive
capabilities were solidified through the use of
Suricata's custom rule configurations, effectively
eliminating a well-constructed Nmap scan.
Augmented by real-time alerts and proactive IP
blocking, this showcased an adaptive and responsive
security posture that shone in a moment of pressure.
Note, our deployment within a VMware-based
environment demonstrates the feasibility and
scalability of this approach is creating a reasonably
generic model that can easily be scaled into different
network infrastructures. It allows for effective
manning while providing a cost-effective, high-
performance security solution that is reproducible by
organizations or individuals. This powerful
combination of pfSense’s open-source versatility
with VMware’s virtualization solutions is an
incredible step forward towards enterprise-strength
network protection for everyone.
The possibilities for extending pfSense are
tremendous and exciting! The integration of
advanced technologies such as machine learning
algorithms could pave the way for pfSense to predict
and proactively address emerging threats with
improved accuracy. Supported by real-time threat
intelligence, dynamic rule generation can enable the
system to gain even more configuration writing
power, as it allows for seamless adaptation to the
changing tides of cyber risk. Such developments
would make pfSense not just a reactive tool, but a
proactive guardian of digital ecosystems. Ultimately,
this endeavor reinforces the status of pfSense as a
robust, flexible, and futuristic solution, well-equipped
to face the demands of contemporary network
security with strength and creativity.
REFERENCES
A. Patel et al., “pfSense in Small Networks: A Case Study,”
Int. J. Comput. Appl., vol. 15, no. 2, pp. 89–95, 2022.
Available: https://docs.netgate.com/pfsense/en/latest/
Available: https://suricata.readthedocs.io/
J. Smith et al., “Stateful Firewalls for DoS Mitigation,”
IEEE Trans. Netw. Secur., vol. 10, no. 3, pp. 45–52,
2020.
K. V. Reddy and S. M. Ali, “Optimizing pfSense for SYN
Flood Defense in Virtual Networks,” in Proc. IEEE Int.
Symp. Netw. Comput. Appl. (NCA), 2023, pp. 156–
163.
Firewall Implementation and Attack Mitigation Using pfSense
491

L. Brown and M. Taylor, “Limitations of Signature-Based
Detection,” J. Cybersecurity, vol. 9, no. 1, pp. 34–42,
2021.
L. M. Santos and F. J. Ortiz, “Behavioral Analysis of Port
Scanning Attacks with Suricata,” IEEE Trans.
Dependable Secure Comput., vol. 21, no. 4, pp. 2456–
2468, Jul. 2024.
Netgate, “pfSense Documentation,”
[Online].
OISF, “Suricata User Guide,” [Online].
P. Gupta et al., “Suricata in Enterprise Networks,” in IEEE
Conf. Netw. Secur., 2022, pp. 78–85.
R. Jones and T. Lee, “Comparative Analysis of IDS Tools,”
in Proc. IEEE Conf. Cybersecurity, 2021, pp. 123–130.
R. N. Choudhury and P. Dutta, “Evaluating Open-Source
Firewalls for Real-Time Threat Mitigation,” in Proc.
IEEE Int. Conf. Adv. Netw. Telecommun. Syst.
(ANTS), 2023, pp. 45–52.
T. A. Bello et al., “Cost-Effective Firewall Deployment
Using pfSense in Resource-Constrained
Environments,” in Proc. IEEE Global Conf. Signal Inf.
Process. (GlobalSIP), 2024, pp. 321–327.
ICRDICCT‘25 2025 - INTERNATIONAL CONFERENCE ON RESEARCH AND DEVELOPMENT IN INFORMATION,
COMMUNICATION, AND COMPUTING TECHNOLOGIES
492
