
Auditing Bitcoin: Ensuring Transparency and Security
C. H. Amarendra
1
, A. Sri Sai Deepak Reddy
1
,
K. Shanmukha Sai Kumar Reddy
1
and A. Phani Sridhar
2
1
Department of ACSE, School of Computing and Informatics, VFSTR Deemed to be University, Vadlamudi, Andhra
Pradesh, India
2
Department of Computer Science and Engineering, Aditya University, Aditya Nagar, Suramplame, Andhra Pradesh, India
Keywords: Black Chain, Bit Coin Audit, Cryptography.
Abstract: Bitcoin, a revolutionary cryptocurrency, has reshaped the financial landscape with its decentralized
architecture and cryptographic security. While this decentralization offers numerous advantages, it also
presents challenges in ensuring transparency and accountability within the Bitcoin ecosystem. This research
delves into the critical role of Bitcoin auditing in maintaining the integrity and security of Bitcoin transactions.
By analyzing transaction patterns, sender-receiver addresses, and other relevant data, auditors can validate the
authenticity and compliance of these transactions. This process is particularly crucial for law enforcement
agencies, as it enables them to trace the flow of funds, identify potential criminal activities, and gather
evidence for investigations and prosecutions. In this study, we examine and evaluate a dataset of Bitcoin
transactions obtained from an online source. By employing specialized forensic and blockchain analysis tools,
we meticulously scrutinize the transactions for authenticity, integrity, and adherence to regulatory standards.
Our analysis focuses on tracing the flow of funds, verifying transaction details, and identifying any anomalies
or potential risks. The broader implications of Bitcoin auditing, including its potential to enhance the overall
security and reliability of the Bitcoin ecosystem. By addressing concerns related to transparency,
accountability, and regulatory compliance, Bitcoin auditing can contribute to the long-term sustainability and
widespread adoption of this groundbreaking technology.
1 INTRODUCTION
Blockchain serves as a distributed ledger technology
facilitating secure and immutable transaction
recording across a network of interconnected nodes.
Unlike conventional centralized systems, blockchain
operates on a decentralized model. In this model, data
and transactions are stored and verified by multiple
participants within the network, rather than relying on
a single controlling entity.
The inception of blockchain dates back to 2009
with the emergence of Bitcoin, introduced by an
anonymous figure named Satoshi Nakamoto. Bitcoin,
recognized as the pioneer and foremost application of
blockchain technology, revolutionized the concept of
peer-to-peer electronic cash systems. By leveraging
blockchain, Bitcoin presented a groundbreaking
solution to the challenge of double-spending in digital
currencies, eliminating the need for intermediaries
like banks or financial institutions. This marked the
onset of a transformative era in decentralized finance.
The concept of auditing Bitcoin transactions
emerges as a vital mechanism to uphold integrity,
validate authenticity, and ensure compliance in this
decentralized financial landscape. Traditional audit
methodologies designed for centralized financial
systems must adapt to the decentralized and
cryptographically secured environment of Bitcoin.
Bitcoin audit, exploring the fundamental principles,
methodologies, and technologies involved. We delve
into the cryptographic foundations that underpin
Bitcoin's security and immutability, understanding
how these principles facilitate transaction verification
and chain of ownership validation.
At its core, Bitcoin represents a departure from
traditional financial systems governed by central
banks and intermediaries. It functions as a
decentralized electronic cash system, operating on a
peer-to-peer basis. Built upon a revolutionary
technology known as block chain. Unlike
conventional currencies, which rely on physical
forms or centralized databases, Bitcoin exists purely
Amarendra, C. H., Reddy, A. S. S. D., Reddy, K. S. S. K. and Sridhar, A. P.
Auditing Bitcoin: Ensuring Transparency and Security.
DOI: 10.5220/0013900500004919
Paper published under CC license (CC BY-NC-ND 4.0)
In Proceedings of the 1st International Conference on Research and Development in Information, Communication, and Computing Technologies (ICRDICCT‘25 2025) - Volume 3, pages
491-495
ISBN: 978-989-758-777-1
Proceedings Copyright © 2025 by SCITEPRESS – Science and Technology Publications, Lda.
491
in the digital realm, with ownership and transactions
verified and recorded on an immutable and
transparent ledger.
The significance of Bitcoin lies not only in its role
as a digital currency but also in its underlying
principles and potential implications. Bitcoin
embodies the ideals of decentralization, censorship
resistance, and financial sovereignty, offering
individuals and communities around the globe an
alternative to traditional banking systems and fiat
currencies.
In a world marked by complexity, uncertainty, and
rapid change, the need for accountability and
transparency has never been more crucial.
Organizations, whether public or private, face a
myriad of risks and challenges that necessitate
diligent oversight and assurance mechanisms to
safeguard their operations, assets, and stakeholders'
interests. At the heart of this endeavor lies the practice
of audit a cornerstone of governance, risk
management, and compliance. Audit, in its essence, is
a systematic examination and evaluation of an
organization's financial records, operational
processes, and internal controls, conducted by
independent professionals known as auditors. Its
primary objective is to assure stakeholders regarding
the accuracy, reliability, and integrity of financial
reporting, as well as the effectiveness of internal
control systems.
In this introduction, we embark on a journey to
explore the multifaceted nature of audit, delving into
its fundamental principles, methodologies, and
overarching objectives. We uncover the role of
auditors as guardians of trust and integrity, tasked
with providing stakeholders with reliable and
unbiased insights into the organization's affairs. Audit
serves as a vital tool for enhancing transparency,
accountability, and governance within organizations.
By identifying weaknesses in internal controls,
detecting errors or fraud, and recommending remedial
actions, audit helps mitigate risks and improve
operational efficiency. Moreover, it installs
confidence among investors, creditors, regulators,
and other stakeholders, fostering trust in the
organization's financial reporting and management
practices.
The audit has unique challenges some of them are
Lack of Regulatory Framework, Complex and
Evolving Technology, Lack of Physical Evidence,
Security and Custody Risks, Global Nature and
Cross-Border Transaction (Kamau, C. G., &
Yavuzaslan, A. 2023).
An electronic coin is defined as a sequence of
digital signatures. Each transfer of ownership
involves digitally signing a hash of the preceding
transaction and the public key of the subsequent
owner. These signatures are appended to the coin,
facilitating its transfer to the next recipient
(Nakamoto, S. 2008).
Data within the block chain is decentralized,
ensuring its integrity, safety, and authenticity.
Utilizing distributed systems, decentralization, time-
series data, and asymmetric encryption, blockchain
technology enables secure storage and verification
through system-wide broadcasting (Cheng, C., &
Huang, Q. 2020).
Utilizing blockchain technology enables the
creation of a highly transparent database capable of
securely storing and updating data in real-time. The
information remains immutable, safeguarding against
tampering, while also allowing for traceability and
seamless sharing across the network (Dunn et al.,
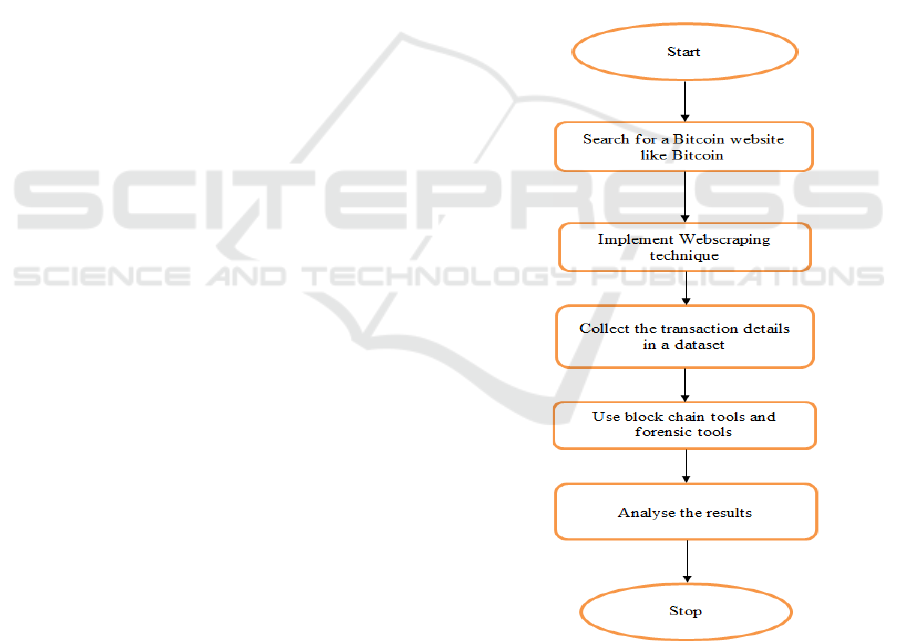
2021). Figure1 gives the bitcoin audit flowchart.
Figure 1: Flow chart of the Bitcoin audit.
There exist two main categories of block chains:
public (or permission less) and private (or
permissioned). Public block chains are openly
accessible and observable by all participants in the
network, devoid of centralized ownership or control.
ICRDICCT‘25 2025 - INTERNATIONAL CONFERENCE ON RESEARCH AND DEVELOPMENT IN INFORMATION,
COMMUNICATION, AND COMPUTING TECHNOLOGIES
492

On the other hand, private or permissioned block
chains are confined to specific organizations or
consortia, allowing access solely to authorized parties
designated by permission (Dyball, M. C., &
Seethamraju, R. 2021).
Every transaction consists of three essential
components: the sender, transaction details, and the
recipient, all secured by encryption. These
transactions are grouped into blocks, forming the
block chain. A Bitcoin wallet, stored as a file in the
user's system, contains public and private key pairs,
facilitating transactions to and from the wallet. These
keys serve the purpose of sending and receiving
Bitcoins securely (Latifa, E. R., & Omar, A. 2017).
In pinpointing potential fraud risks, the dialogue
among key members of the engagement team may
encompass discussions about the likelihood of
significant inaccuracies arising from fraudulent
activities (Dupuis et al., 2023).
The primary advantage of a cryptocurrency,
setting it apart from traditional forms of currency, lies
in its robust security and verifiability mechanisms.
Cryptocurrency is essentially a cryptographic proof
of transaction chronology, facilitated through peer-to-
peer distributed timestamps. It's worth noting that the
original aim of blockchain development was not
solely to introduce a new currency, but rather to
establish the foundations of a decentralized cash
payment system (Procházka, D. 2018).
Auditing is a fundamental responsibility of
accountants, and in this examination, we will utilize
Bitcoin, the world's premier cryptocurrency, to
scrutinize transactions. Bitcoin operates on a unique
transaction system that utilizes a decentralized
network called the block chain. This blockchain
serves as a publicly accessible ledger, recording every
transaction ever executed. The integrity of each
transaction is safeguarded by digital signatures
associated with the sender's addresses, granting users
complete authority over sending bitcoins from their
respective Bitcoin addresses (Moore, P. 2018).
Blockchain technology itself poses a number of
opportunities for the accounting profession, including
vetting of parties to transactions, advancing real-time
accounting, incorporating artificial intelligence into
the process of auditing, and providing assurance
related to smart contracts (Dupuis et al., 2021).
2 METHODS AND MATERIAL
Understanding Bitcoin Transactions and Blockchain
Technology: The first step in conducting a Bitcoin
audit is to gain a comprehensive understanding of
how Bitcoin transactions work and the underlying
blockchain technology. This involves familiarizing
oneself with concepts such as cryptographic hashing,
digital signatures, public and private keys, blocks,
and the decentralized nature of the block chain.
• Scope definition: Define the scope of the audit,
including the specific aspects of Bitcoin transactions
and related activities to be examined. This may
include transaction validation, chain of ownership
verification, compliance with regulatory
requirements, security measures, and risk assessment.
• Data collection: Obtain the Bitcoin transaction
data from the chosen online source or website. This
may involve web scraping, API queries, or accessing
transaction data from blockchain explorers. Ensure
the integrity and completeness of the data collected
for analysis.
• Data Analysis and validation: Utilize forensic
tools and blockchain analysis tools to analyze the
Bitcoin transaction data. Verify the authenticity and
integrity of the transactions by examining transaction
details, including inputs, outputs, timestamps,
transaction amounts, and transaction fees. Use
cryptographic techniques to validate signatures and
confirm compliance with the Bitcoin protocol.
• Wallet and Transaction Audits: Auditors review
Bitcoin wallets and transactions to ensure they are
secure and legitimate. This involves verifying the
ownership of wallets, analyzing transaction history,
and confirming compliance with regulatory
requirements.
• Blockchain Analysis: Auditors leverage
blockchain analysis tools for tracking and analyzing
Bitcoin transactions. This process aids in recognizing
patterns, detecting irregularities, and verifying
adherence to anti-money laundering (AML) and
know-your-customer (KYC) regulations.
• Cryptographic Techniques: Leverage
cryptographic principles to verify the authenticity and
integrity of Bitcoin transactions. Techniques such as
digital signatures, cryptographic hashing, and public-
key cryptography are used to validate transaction data
and ensure compliance with the Bitcoin protocol.
• Data analysis Techniques: Employ data analysis
methodologies, such as statistical analysis, machine
learning algorithms, and network analysis, to
scrutinize Bitcoin transaction data. These approaches
aid auditors in recognizing patterns, detecting
irregularities, and evaluating transaction behavior
within the block chain network.
• Forensic Analysis: In case of suspected fraud or
misconduct, auditors conduct forensic analysis of
Bitcoin transactions to trace the funds, identify
Auditing Bitcoin: Ensuring Transparency and Security
493
perpetrators, and gather evidence for legal
proceedings.
• Documentation and reporting: Document
findings, observations, and recommendations in a
comprehensive audit report. Provide clear
explanations of audit procedures, findings, and
conclusions. Highlight areas of strength, weaknesses,
and opportunities for improvement, along with
actionable recommendations for remediation. Ensure
that the audit report is accurate, objective, and
tailored to the needs of stakeholders. Forensic tools
commonly used for analyzing Bitcoin transactions.
• Chainalysis Reactor: Chainalysis Reactor is a
blockchain analysis tool designed to investigate and
trace cryptocurrency transactions, including those
involving Bitcoin. It allows users to track funds
across the block chain, identify illicit activities, and
generate reports for law enforcement and regulatory
purposes.
• CipherTrace: CipherTrace offers cryptocurrency
intelligence solutions, including forensic tools for
analyzing Bitcoin transactions. Their platform
provides features for tracing funds, identifying risk
factors, and detecting money laundering activities.
CipherTrace also offers compliance solutions for
regulatory reporting and risk assessment.
• Elliptic: Elliptic specializes in blockchain
analytics and risk management solutions for
cryptocurrencies like Bitcoin. Their platform offers
tools for transaction monitoring, risk scoring, and
compliance with regulatory requirements. Elliptic
helps financial institutions, exchanges, and law
enforcement agencies identify and mitigate risks
associated with Bitcoin transactions.
• BlockSci: BlockSci is an open-source blockchain
analysis tool developed by researchers at Princeton
University. It provides a suite of tools for analyzing
and visualizing blockchain data, including Bitcoin
transactions. Block Sci allows users to trace
transaction flows, identify addresses associated with
specific entities, and analyze patterns or anomalies in
the block chain network.
These forensic tools are valuable for conducting
investigations, tracing fund flows, and identifying
illicit activities within the Bitcoin ecosystem. They
provide auditors, investigators, and regulatory
authorities with the necessary tools and insights to
ensure transparency, integrity, and compliance in the
cryptocurrency space.
3 RESULTS AND DISCUSSIONS
The results of a Bitcoin audit provide stakeholders
with assurance regarding the transparency, integrity,
and compliance of Bitcoin transactions within the
digital ecosystem. They help organizations identify
areas for improvement and mitigate risks associated
with Bitcoin transactions effectively.
The dataset obtained from an online website
known as Litecoin. We acquired this dataset using
web scraping techniques, specifically utilizing the
Beautiful Soup library. This process allowed us to
extract data from the website's HTML structure
efficiency.
The analysis of the dataset obtained in the
previous step. By utilizing various data analysis tools
and techniques, we examine the extracted data
comprehensively. This analysis involves exploring
transaction details, identifying patterns, and
uncovering insights into Litecoin transactions.
The forensic tools and blockchain analysis tools
to predict and analyze the data obtained from the
dataset. These specialized tools enable us to delve
deeper into the transaction details, trace fund flows,
identify sender and receiver addresses, and assess
compliance with regulatory standards. By leveraging
these tools, we aim to gain valuable insights into
Litecoin transactions, detect any irregularities or
anomalies, and ensure transparency and integrity
within the block chain ecosystem.
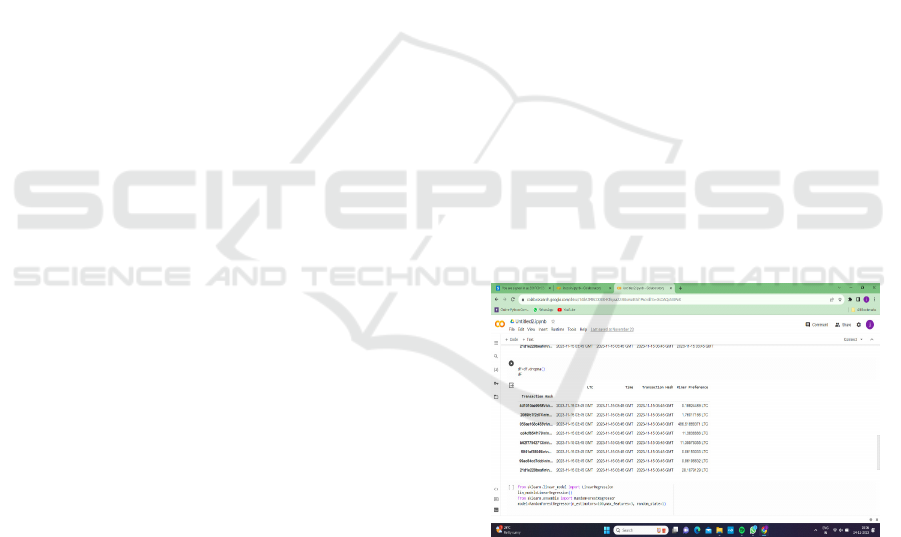
Figure 2: Analysis of Bitcoin transactions.
The Figure 2 provides the litecoin_ data. Describe
() command provides summary statistics for the
numerical columns in the Data Frame. This can help
in understanding the distribution of the data,
identifying outliers, and making informed decisions
about further analysis.
The Figure 3 explains a visualization of Litecoin
transaction data, and Figure 4 indicated the
application of a machine learning model, possibly for
predicting future Litecoin prices or identifying trends.
ICRDICCT‘25 2025 - INTERNATIONAL CONFERENCE ON RESEARCH AND DEVELOPMENT IN INFORMATION,
COMMUNICATION, AND COMPUTING TECHNOLOGIES
494
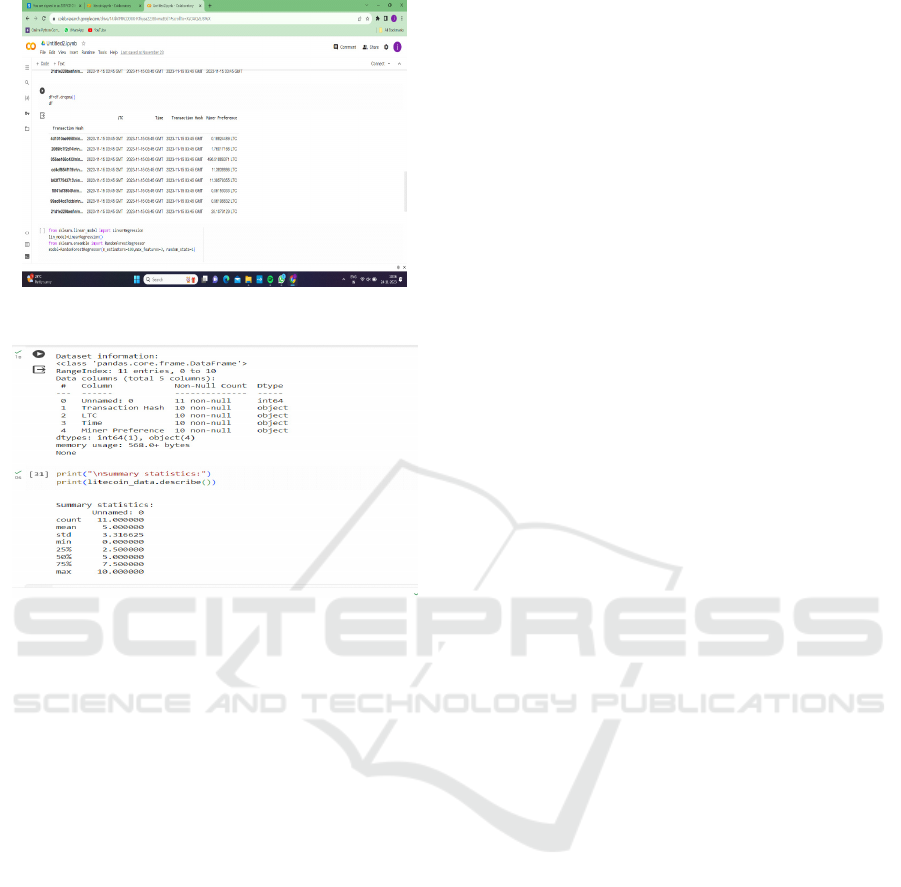
Figure 3: Analysis of Bitcoin transactions.
Figure 4: The data analysis Litecoin transactions.
4 CONCLUSIONS
This comprehensive Bitcoin audit has demonstrated
the critical role of rigorous analysis in ensuring the
integrity and security of blockchain transactions. By
leveraging advanced forensic and blockchain analysis
tools, we have meticulously examined a dataset of
Bitcoin transactions, validating their authenticity,
integrity, and compliance with regulatory standards.
Our findings highlight the importance of robust
auditing practices in mitigating risks associated with
illicit activities and fostering a more transparent and
trustworthy digital financial ecosystem. As the
cryptocurrency landscape continues to evolve, the
need for such rigorous audits will remain paramount
in safeguarding the future of decentralized finance.
REFERENCES
Cheng, C., & Huang, Q. (2020, January). Exploration of the
application of blockchain audit. In 5th International
Conference on Economics, Management, Law and
Education (EMLE 2019) (pp. 63-68). Atlantis Press.
Dunn, R. T., Jenkins, J. G., & Sheldon, M. D. (2021).
Bitcoin and blockchain: Audit implications of the killer
Bs. Issues in Accounting Education, 36(1), 43-56.
Dupuis, D., Gleason, K. C., & Kannan, Y. H. (2021).
Bitcoin and Beyond: Crypto Asset Considerations for
Auditors. Available at SSRN 3903995.
Dupuis, D., Smith, D., Gleason, K., & Kannan, Y. (2023).
Bitcoin and Beyond: Crypto Asset Considerations for
Auditors/Forensic Accountants. Journal of Forensic
and Investigative Accounting, 15(3).
Dyball, M. C., & Seethamraju, R. (2021). The impact of
client use of blockchain technology on audit risk and
audit approach—an exploratory study. International
Journal of Auditing, 25(2), 602-615.
Kamau, C. G., & Yavuzaslan, A. (2023). CryptoAudit:
Nature, requirements and challenges of Blockchain
transaction audit. African Journal of Commercial
Studies, 3(2), 101-107.
Latifa, E. R., & Omar, A. (2017). Blockchain: Bitcoin
wallet cryptography security, challenges and
countermeasures. Journal of Internet Banking and
Commerce, 22(3), 1-29.
Moore, P. (2018). Auditing Crypto Currency Transactions:
Anomaly Detection in Bitcoin (Doctoral dissertation,
Dublin, National College of Ireland).
Nakamoto, S. (2008). Bitcoin: A peer-to-peer electronic
cash system. Available at SSRN 3440802.
Procházka, D. (2018). Accounting for bitcoin and other
cryptocurrencies under IFRS: A comparison and
assessment of competing models. The International
Journal of Digital Accounting Research, 18(24), 161-
188.
Auditing Bitcoin: Ensuring Transparency and Security
495
