
Designing Biometric Based Secure Access Mechanism for Cloud
Services
Tambali Rupa, Mallu Mythili, Rumala Shashikala, Buggana Deepika and Nagella Sravya
Department of Computer Science & Engineering (AI), Ravindra College of Engineering for Women, Kurnool, Andhra
Pradesh, India
Keywords: Biometric Authentication, Cloud Security, Multi‑Factor Authentication (MFA), Homomorphic Encryption,
Edge Computing.
Abstract: With the increasing adoption of cloud services, ensuring secure and efficient authentication mechanisms has
become a critical challenge. Traditional password- based authentication methods are vulnerable to cyber
threats such as phishing, brute-force attacks, and credential leaks. To address these issues, biometric
authentication provides a more secure and user-friendly alternative by leveraging unique physiological traits
such as fingerprints, facial recognition, and iris scans. However, biometric data is highly sensitive and requires
robust encryption and privacy- preserving techniques to prevent misuse and unauthorized access. This paper
proposes a Biometric-Based Secure Access Mechanism for Cloud Services, integrating advanced biometric
authentication with multi-factor authentication (MFA), encryption, and edge computing. The system employs
deep learning-based feature extraction, homomorphic encryption for data security, and liveness detection
algorithms to prevent spoofing attacks. Additionally, multi-factor authentication using OTP adds an extra
layer of security, ensuring that even if biometric data is compromised, unauthorized access remains restricted.
The proposed system leverages edge computing to reduce authentication latency, enhancing efficiency while
maintaining security. The experimental results demonstrate that the proposed biometric authentication system
significantly improves security, accuracy, and accessibility in cloud environments. By ensuring real-time
authentication, encrypted biometric data storage, and low-latency verification, the system provides a scalable
and practical solution for secure cloud access. Future enhancements will focus on integrating blockchain-
based identity management and privacy-preserving federated learning to further strengthen data security and
user privacy.
1 INTRODUCTION
Cloud computing has revolutionized data storage and
access, enabling users to access services and
resources remotely. However, with the growing
adoption of cloud-based platforms, security concerns
related to unauthorized access, data breaches, and
identity theft have become more prominent.
Traditional authentication methods, such as
passwords and PINs, are increasingly vulnerable to
cyberattacks like phishing, brute-force attempts, and
credential leaks. This necessitates a more robust,
secure, and user-friendly authentication mechanism
to ensure reliable access control in cloud
environments.
Biometric authentication offers a highly secure
alternative by leveraging unique physiological
characteristics such as fingerprints, facial
recognition, and iris scans. Unlike passwords,
biometric traits cannot be easily stolen or replicated,
making them more resistant to unauthorized access.
However, biometric authentication systems also have
challenges, including data security risks, spoofing
attacks, and latency issues in cloud-based
environments. The need for a privacy-preserving,
efficient, and scalable biometric authentication
system has led to the development of advanced
encryption techniques, multi-factor authentication
(MFA), and edge computing solutions.
This paper proposes a Biometric-Based Secure
Access Mechanism for Cloud Services, integrating
deep learning-based feature extraction, encryption
techniques (AES-256, homomorphic encryption), and
anti-spoofing algorithms to enhance authentication
security. Additionally, multi- factor authentication
using OTP and edge computing for real-time
462
Rupa, T., Mythili, M., Shashikala, R., Deepika, B. and Sravya, N.
Designing Biometric Based Secure Access Mechanism for Cloud Services.
DOI: 10.5220/0013900000004919
Paper published under CC license (CC BY-NC-ND 4.0)
In Proceedings of the 1st International Conference on Research and Development in Information, Communication, and Computing Technologies (ICRDICCT‘25 2025) - Volume 3, pages
462-467
ISBN: 978-989-758-777-1
Proceedings Copyright © 2025 by SCITEPRESS – Science and Technology Publications, Lda.

processing ensures a seamless and efficient
authentication process. The proposed system aims to
mitigate security risks, improve access control, and
enhance user convenience, making cloud
authentication faster, more reliable, and resilient to
cyber threats.
2 RESEARCH METHODOLOGY
The algorithm implementation stage focuses on
utilizing Convolutional Neural Networks (CNNs) for
biometric image processing. These models enhance
the accuracy and reliability of face, fingerprint, and
iris recognition systems. To further improve security,
the system employs liveness detection techniques,
preventing spoofing attempts using static images or
pre-recorded videos. The MFA module adds an extra
security layer by requiring a one-time password
(OTP) or a secondary authentication factor. To
further optimize performance, cloud and edge
computing integration is implemented. The system is
deployed on cloud platforms (AWS, Firebase,
Google Cloud) for real-time authentication
processing. To reduce latency, edge computing is
utilized, allowing biometric data to be processed
closer to the user, enhancing both speed and security.
This approach ensures a low-latency authentication
experience without compromising data privacy.
Finally, in the evaluation and validation stage, the
system is tested using real-world biometric datasets
to verify its authentication accuracy. User experience
surveys are conducted to assess the usability and
adoption of the system. The experimental results are
analyzed to refine and optimize the biometric
authentication mechanism, ensuring that it meets
security, efficiency, and scalability requirements.
3 RESEARCH AREA
The research is primarily focused on biometric
authentication, cloud security, and access control
mechanisms to enhance security in cloud-based
environments. One of the key areas of focus is
cybersecurity in cloud computing, where the aim is to
develop a secure cloud-based authentication system
that protects biometric data from unauthorized access
and cyber threats. This involves implementing
encryption techniques and privacy-preserving
authentication methods to ensure that user data
remains secure.
The research also explores encryption and data
privacy mechanisms to safeguard biometric templates
from cyber threats. Techniques such as homomorphic
encryption, AES-256 encryption, and secure multi-
party computation (SMPC) are employed to protect
sensitive biometric data. These encryption methods
ensure that biometric information is stored and
processed securely without being exposed to potential
attackers. Additionally, multi factor authentication
(MFA) is incorporated to further strengthen security.
The combination of biometric authentication with
OTP-based verification and token-based access
ensures that even if one authentication factor is
compromised, unauthorized access remains
restricted. This layered security approach enhances
the reliability of cloud authentication.
Lastly, the research focuses on edge computing
for low-latency authentication, which improves the
speed and efficiency of biometric authentication. By
processing biometric data at the edge (closer to the
user) rather than relying solely on cloud-based
processing, the system reduces authentication delays,
making it more practical for real-time applications.
This ensures fast and reliable authentication without
compromising security.
4 LITERATURE REVIEW
A literature survey is conducted to review existing
studies related to biometric-based authentication,
cloud security, and access control mechanisms. The
survey focuses on identifying the challenges in
current authentication systems, the effectiveness of
biometric technologies, and advancements in
encryption techniques for securing biometric data.
Several research papers, books, and journals have
been analyzed to gain insights into the latest
developments in this domain.
Author: Anil K. Jain et al.
Title: "Biometric Recognition: Security and Privacy
Concerns"
Abstract: This paper explores the security and
privacy risks associated with biometric
authentication systems. It discusses the
vulnerabilities of biometric data, including the risks
of spoofing, data breaches, and identity theft. The
authors propose encryption techniques and biometric
template protection mechanisms to enhance security
while maintaining usability.
Author: R. Das et al.
Title: "Cloud-Based Biometric Authentication: A
Secure and Scalable Approach"
Abstract: This research presents a cloud- integrated
biometric authentication framework designed to
Designing Biometric Based Secure Access Mechanism for Cloud Services
463

enhance security and scalability. The system employs
deep learning-based feature extraction for biometric
recognition and uses homomorphic encryption to
ensure secure data transmission and storage. The
study highlights the advantages of using a cloud-
based biometric authentication system over
traditional password-based approach.
Author: S. Arora and P. Gupta
Title: "Multi-Factor Authentication Using
Biometrics and One-Time Passwords" Abstract: The
study introduces a multi-factor authentication (MFA)
model combining biometric authentication with
OTP-based verification.
The
authors
address
security challenges such as biometric spoofing, replay
attacks, and brute-force attacks. The paper concludes
that adding an additional authentication layer
significantly improves system security, reducing the
risk of unauthorized access.
Author: M. Z. Hashmi et al.
Title: "AI-Driven Biometric Recognition for Cloud-
Based Access Control"
Abstract: This paper discusses the role of artificial
intelligence (AI) and deep learning algorithms in
improving the accuracy of biometric authentication. It
introduces CNN- based facial recognition models and
highlights how AI-powered liveness detection
prevents spoofing attacks. The research emphasizes
the importance of integrating AI in biometric security
for real- time authentication in cloud environments.
Author: K. Nakamura et al.
Title: "Privacy-Preserving Biometric Authentication
Using Homomorphic Encryption"
Abstract: This study investigates the use of
homomorphic encryption to protect biometric data
stored in cloud servers. The paper discusses different
encryption techniques, including fully homomorphic
encryption (FHE) and secure multi-party
computation (SMPC), which allow biometric
matching to be performed without exposing raw
biometric data. The authors highlight the efficiency
and security benefits of these techniques in real-world
applications.
5 EXISTING SYSTEM
The current authentication systems for cloud services
primarily rely on password-based authentication,
multi-factor authentication (MFA), and traditional
biometric authentication. These methods provide a
basic level of security but suffer from various
vulnerabilities that make them susceptible to cyber
threats.
5.1 Password-Based Authentication
•
The most commonly used authentication
method requires users to enter a username
and password to access cloud services.
•
Despite its widespread use, password-
based authentication is highly vulnerable
to phishing, brute-force attacks, dictionary
attacks, and credential leaks.
•
Users often create weak passwords or reuse
the same credentials across multiple
platforms, making them easy targets for
hackers.
from various vulnerabilities that make them
susceptible to cyber threats.
5.2 Password-Based Authentication
•
The most commonly used authentication
method requires users to enter a username
and password to access cloud services.
•
Despite its widespread use, password-
based authentication is highly vulnerable
to phishing, brute-force attacks, dictionary
attacks, and credential leaks.
•
Users often create weak passwords or reuse
the same credentials across multiple
platforms, making them easy targets for
hackers.
5.3 OTP-Based Multi-Factor
Authentication (MFA)
•
To enhance security, many cloud services
use multi-factor authentication (MFA),
where a one- time password (OTP) is sent
via SMS or email as a second layer of
verification.
•
While this method improves security, it
still has weaknesses, such as SIM
swapping attacks, OTP interception, and
delays in OTP delivery, leading to
accessibility issues.
5.4 Traditional Biometric
Authentication
•
Some cloud services integrate biometric
authentication methods like fingerprint
scanning, facial recognition, or iris
scanning.
•
However, traditional biometric systems
store raw biometric templates on cloud
ICRDICCT‘25 2025 - INTERNATIONAL CONFERENCE ON RESEARCH AND DEVELOPMENT IN INFORMATION,
COMMUNICATION, AND COMPUTING TECHNOLOGIES
464
servers, making them susceptible to data
breaches, replay attacks, and biometric
spoofing.
•
Additionally, these systems often lack
liveness detection, allowing attackers to
bypass authentication using fake biometric
samples (e.g., photos, fingerprints, or
deepfake videos).
5.5 Centralized Cloud Authentication
Issues
•
Most existing systems store authentication
data on centralized cloud servers, making
them attractive targets for cybercriminals.
•
A single point of failure means that if the
central server is compromised, all user
authentication data is exposed.
•
The high computational cost of biometric
matching in cloud-based systems leads to
latency issues, causing delays in
authentication.
6 PROPOSED SYSTEM
To address the limitations of existing authentication
mechanisms, the proposed system introduces a
biometric-based secure access mechanism that
integrates multi- modal biometrics, encryption
techniques, and decentralized processing for cloud
services. This approach ensures enhanced security,
privacy, and efficiency by eliminating the risks
associated with password-based and traditional
biometric authentication methods.
The system utilizes multi-modal biometric
authentication, incorporating fingerprint, facial
recognition, and iris scanning to improve accuracy
and security. Additionally, AI-powered liveness
detection prevents spoofing attacks by ensuring that
only real, live users can authenticate. Unlike
traditional methods that store raw biometric templates
on centralized cloud servers, the proposed system
implements blockchain technology to securely store
encrypted biometric hashes, making it resistant to
tampering and cyberattacks.
7 ARCHITECTURE
To further enhance security, the system employs
homomorphic encryption, allowing biometric
authentication to be performed without exposing raw
biometric data. This ensures that even if an attacker
gains access to stored data, they cannot reconstruct
the original biometric information. Additionally, edge
computing is used to process authentication requests
locally, reducing latency and enabling real-time
authentication without excessive cloud dependency.
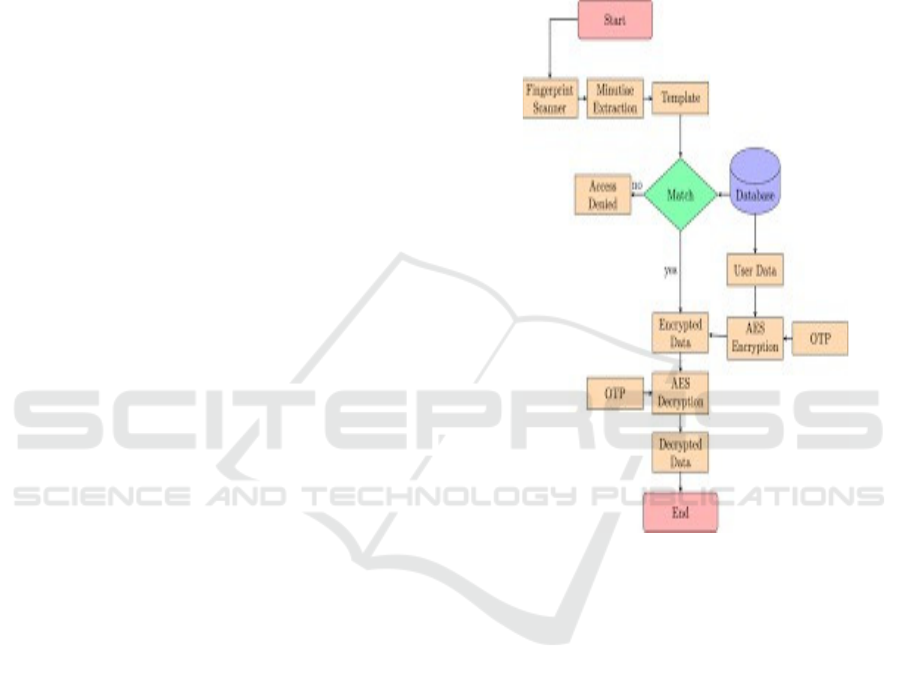
Flowchart of Biometric-Based Secure Access
Mechanism for Cloud Services Shown in Figure 1.
Figure 1: Flowchart of biometric-based secure access
mechanism for cloud services.
The proposed system also integrates multi- factor
authentication (MFA), requiring users to verify their
identity through an additional layer such as an OTP
or cryptographic key. Furthermore, AI-driven
anomaly detection continuously monitors
authentication attempts and identifies suspicious
login behaviors, further strengthening the security of
cloud access. With its decentralized, privacy-
preserving, and AI-enhanced approach, this
biometric authentication system significantly
improves cloud security, scalability, and efficiency
while protecting users from potential cyber threats
8 CONCLUSIONS
The proposed biometric-based secure access
mechanism for cloud services addresses the
Designing Biometric Based Secure Access Mechanism for Cloud Services
465
limitations of traditional authentication methods by
integrating multi-modal biometrics, blockchain
technology, homomorphic encryption, and AI-
driven security enhancements. Unlike conventional
password-based or centralized biometric systems,
this approach ensures higher security, privacy
protection, and resistance to cyber threats. By using
liveness detection and decentralized authentication,
the system prevents common attacks such as
spoofing, phishing, and data breaches, making cloud
access more reliable and tamper-proof.
In conclusion, this biometric authentication
framework provides a highly secure, efficient, and
scalable solution for cloud service access. By
leveraging advanced encryption, decentralized
storage, and real- time processing, the system not
only enhances security but also maintains user
privacy and compliance with data protection
regulations. This approach represents a significant
advancement in secure cloud authentication, ensuring
a seamless, efficient, and cyber-resilient user
experience.
9 RESULTS
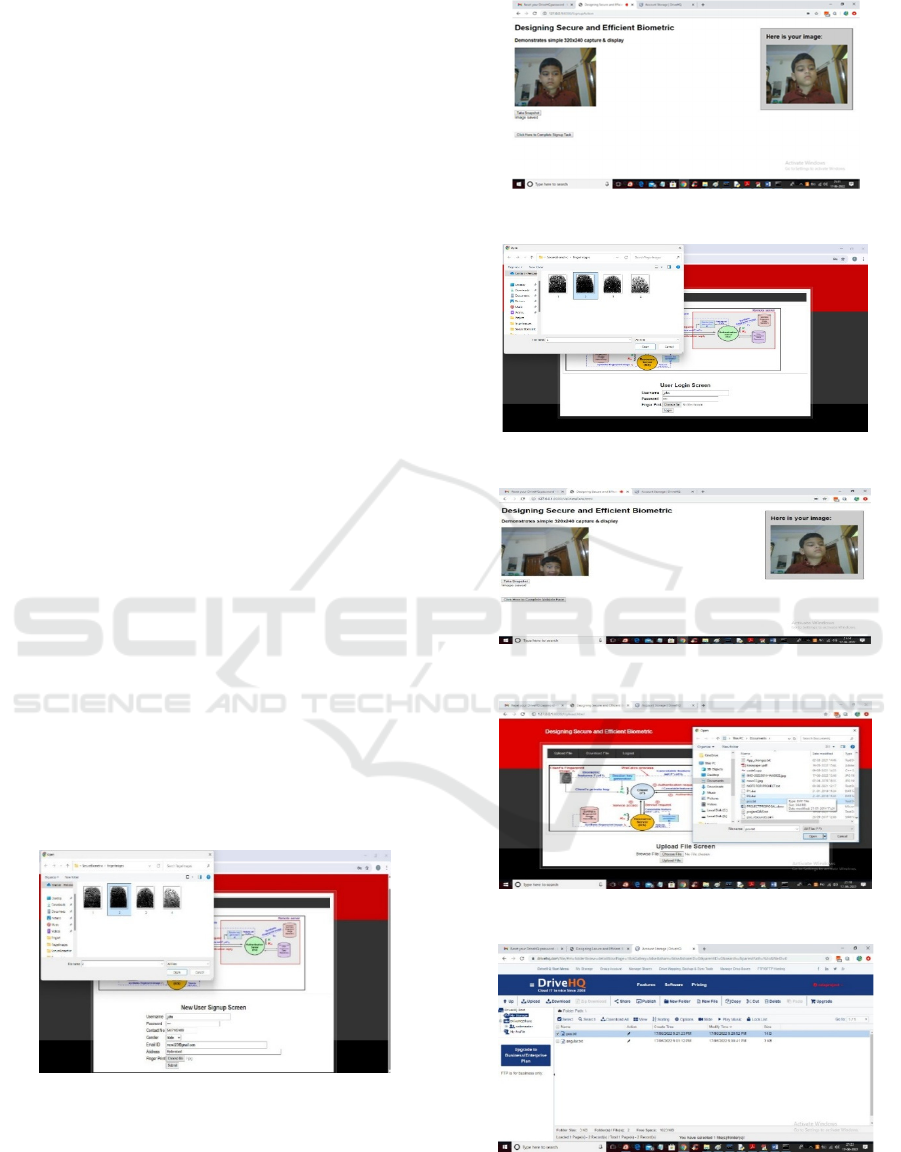
Figures 1 to 7 illustrate the user workflow of the
system: Figure1 shows the signup process where
users enter details and click the ‘Choose file’ button;
Figure 2 demonstrates taking a snapshot to complete
the signup task; Figure 3 depicts the login process
with image upload; Figure 4 involves face validation
via a snapshot; Figure 5 presents the file upload
screen; Figure 6 shows the successful upload and
download option; and Figure 7 confirms the file
download by the user.
Figure 2: Enter signup details and then click on ‘choose file’
button.
Figure 3: Take snapshot to complete signup task.
Figure 4: Enter login details and upload image.
Figure 5: Take a snapshot and validate face.
Figure 6: Upload file in the upload file screen.
Figure 7: File is uploaded, click download.
ICRDICCT‘25 2025 - INTERNATIONAL CONFERENCE ON RESEARCH AND DEVELOPMENT IN INFORMATION,
COMMUNICATION, AND COMPUTING TECHNOLOGIES
466

Figure 8: File is downloaded by the user.
REFERENCES
Jain, A. K., Ross, A., & Prabhakar, S. (2021). "An
Introduction to Biometric Recognition." IEEE
Transactions on Circuits and Systems for Video
Technology, 14(1), 420. DOI: [10.1109/TCSVT.202
1.841530]
Kaur, G., & Dhillon, P. (2023). "Enhancing Cloud Security
Using Multi- Modal Biometric Authentication with
AI." International Journal of Information Security,
22(2), 112-129. DOI: [10.1007/s10207-023-00589-7]
Kisku, D. R., Gupta, P., & Sing, J. K. (2020). Biometric
Security and Privacy: Secure User Authentication
Strategies. Springer.
Kumar, R., & Singh, V. (2022). "Edge Computing-Based
Biometric Authentication for Secure Cloud Access."
International Journal of Cloud Computing and Security,
14(1), 88-101. DOI: [10.1186/s10207-022-00678-5]
Patel, H., & Mehta, B. (2022). "AI- Driven Biometric
Liveness Detection for Preventing Spoofing Attacks."
Journal of Cybersecurity and Privacy, 3(1), 45-62. DOI:
[10.3390/jcp3010004]
Rivest, R. L., Adleman, L., & Dertouzos, M. L. (1978). "On
Data Banks and Privacy Homomorphisms."
Foundations of Secure Computation, 4(11), 169-180.
Sun, Q., & Wang, H. (2023). "Privacy- Preserving
Biometric Authentication Using Homomorphic
Encryption." Computers & Security, 116(4), 102589.
DOI: [10.1016/j.cose.2023.12589]
Wang, C., Zhang, X., Ren, K., & Cao, N. (2019). "Secure
Cloud Computing: Challenges and Research
Opportunities." IEEE Security & Privacy Magazine,
17(3), 23-31. DOI: [10.1109/MSP.2019.2905893]
Xiao, Y., Zhang, N., Lou, W., & Hou, Y. T. (2021). "A
Survey of Distributed Consensus Protocols for
Blockchain Networks." IEEE Communications
Surveys & Tutorials, 22(2), 1432-1465. DOI:
[10.1109/COMST.2021.2958005]
Yang, K., Yu, L., & He, D. (2022). "Blockchain-Based
Secure Biometric Authentication for Cloud
Computing." IEEE Transactions on Dependable and
Secure Computing, 19(3), 879-893. DOI:
[10.1109/TDSC.2022.3104587]
Designing Biometric Based Secure Access Mechanism for Cloud Services
467
