
A Novel Methodology to Ensure Rider Safety Measures Based on
Helmet Detection System Using Deep Learning Mechanism
Gokulkannan M., Elandhiraiyan K., Gokulraj G. and Thirunavukkarasu G.
Department of Computer Science and Engineering, Mahendra Engineering College, Namakkal, Tamil Nadu, India
Keywords: Rider Safety, Helmet Detection, Image Processing, Deep Learning, EYOLO, Convolutional Neural Network,
CNN, Driver Safety.
Abstract: Motorbikes are a prevalent mode of conveyance in numerous countries. Nevertheless, the absence of the
appropriate safety apparatus poses a significant danger when operating a motorcycle. Consequently, it is
strongly advised that individuals don helmets while operating a bicycle to ensure their safety. In order to
eliminate this manual dependence, it is imperative to develop a self-powered helmet detection system that can
identify motorcycle offenders. This research is dedicated to the development of a helmet detection system for
two-wheelers that is both reliable and efficient. The Enhanced You Only Look Once (EYOLO) algorithm is
employed in this system and it is cross-validated with the traditional deep learning algorithm, Convolutional
Neural Network (CNN), to assess the effectiveness of the proposed model. The headgear status of the rider is
continually monitored by this system, which operates in real-time. It rapidly determines whether the
motorcyclist is donning a helmet by utilizing sophisticated artificial intelligence techniques. The primary goal
of this system is to ensure that riders adhere to helmet regulations in order to enhance their safety. The system
automatically precludes the vehicle from commencing in cases where the rider is not wearing a helmet,
thereby encouraging the use of helmets. This proactive approach is designed to substantially reduce the risk
of head injuries in the event of incidents, thereby contributing to the overall safety of the road as well as
decreasing the severity of prospective injuries. Our system endeavors to improve passenger safety and reduce
the negative repercussions of noncompliance with helmet regulations by combining state-of-the-art
technology with regulatory compliance.
1 INTRODUCTION
Today, traffic accidents involving scooters and
motorbikes are surprisingly widespread, making the
safety of passengers on two-wheelers an urgent issue
Gopinath D, et al., 2024. In order to tackle this
pressing problem, our research utilizes artificial
intelligence to identify helmet wear in real-time. Our
objective is to utilize state-of-the-art technologies in
a proactive manner to improve rider safety and
decrease the number of serious injuries caused by
accidents. The incidents are that cases of two-
wheeler accidents are greatly on the rise, and the
riders necessitate wearing a helmet. However, still a
good number of motorcyclists prefer riding without
such basic safety features, knowing very well that it
is important. This system aims to develop and
implement a helmet-detecting system in real-time to
back up helmet regulation enforcement and accident
prevention (Xuejun Jia, et al., 2020). Project
objectives include enhancing rider safety and
addressing environmental problems related to road
accidents. Efforts are being made to lessen the toll
that road accidents take on the environment by
increasing safety measures and decreasing the
severity of injuries through prompt medical attention.
Furthermore, we aim to promote helmet usage by
taking proactive steps like not allowing the vehicle to
start without a helmet. This will help establish a
safety culture among riders and promote a more
sustainable way of getting about. With this system in
place, not only would individual riders reap many
benefits, but healthcare systems already
overburdened by injuries sustained in accidents may
also see substantial relief. We encourage sustainable
mobility behaviors and contribute to society's well-
being by minimizing the frequency and severity of
injuries occurring from two-wheeler accidents. We
want to build healthier communities and safer roads
552
M., G., K., E., G., G. and G., T.
A Novel Methodology to Ensure Rider Safety Measures Based on Helmet Detection System Using Deep Learning Mechanism.
DOI: 10.5220/0013869100004919
Paper published under CC license (CC BY-NC-ND 4.0)
In Proceedings of the 1st International Conference on Research and Development in Information, Communication, and Computing Technologies (ICRDICCT‘25 2025) - Volume 1, pages
552-561
ISBN: 978-989-758-777-1
Proceedings Copyright © 2025 by SCITEPRESS – Science and Technology Publications, Lda.
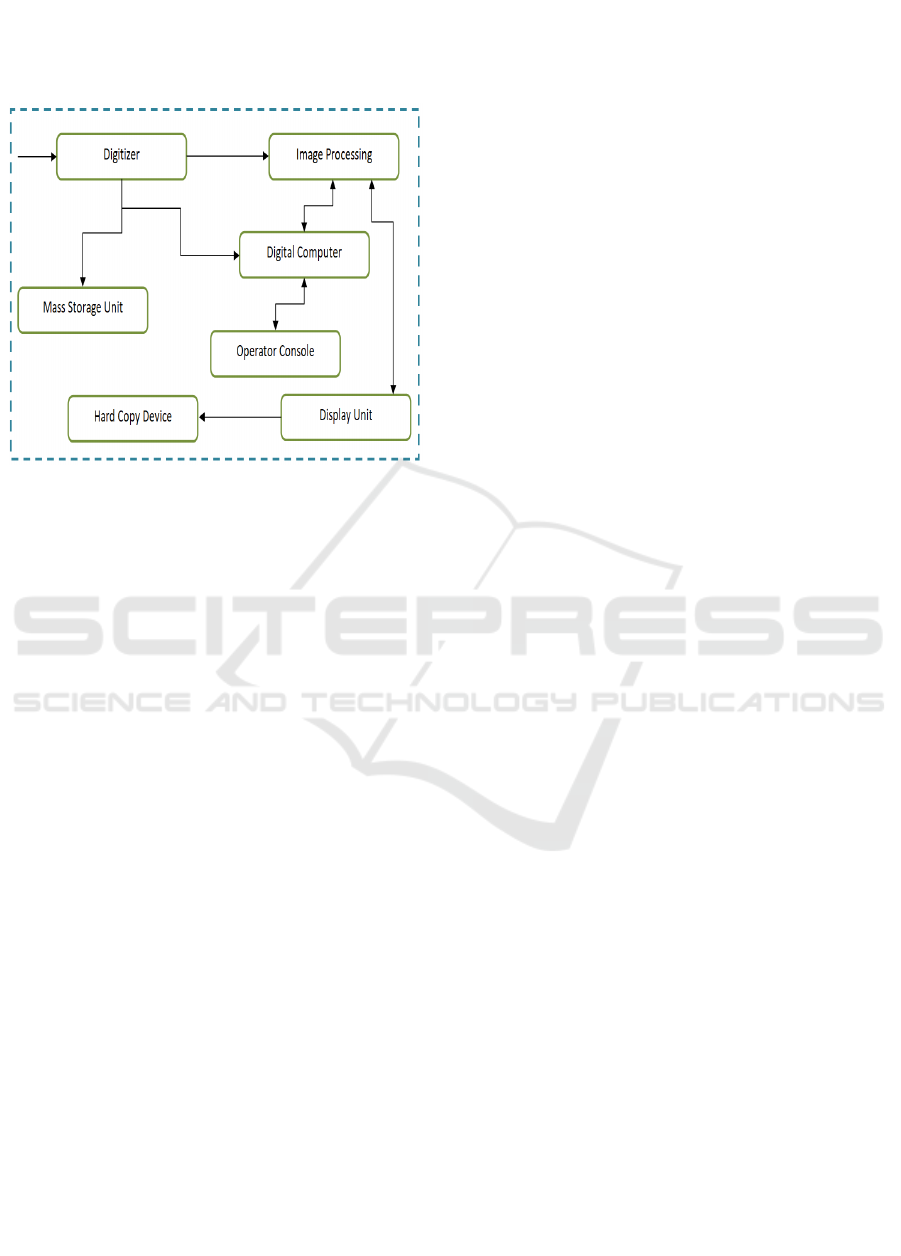
for everyone via teamwork and new ideas, such as the
real-time helmet detection system (Hanhe Lin, et
al., 2020). The following figure 1 shows the image
processing block diagram.
Figure 1: Image processing block diagram.
A digital image is a two-dimensional picture that
has been processed by a digital computer. Any two-
dimensional data may be digitally processed in a
larger sense. In digital storage, each bit represents an
integer array that can be either real or complex. The
initial step in digitizing and storing an image in
computer memory is to convert it from a digital
format, such as a transparency, slide, picture, or X-
ray. Digitizing the image allows for high-quality
processing and/or display on a (TVYongze Ji, et al.,
2022). A rapid-access buffer memory stores the
image for display, and it refreshes the monitor at 25
frames per second to provide an optically continuous
display (Bingyan Lin 2024). A digitizer is a machine
that takes an image and turns it into a numerical form
that a digital computer can understand. A few
popular digital converters include
• Microdensitometer
• Flying spot scanner
• Image dissector
• Videocon camera
• Photosensitive solid- state arrays.
(Wei Jia, et al., 2021) Once an image has been
acquired, stored, preprocessed, segmented,
represented, recognized, and interpreted, finally, this
image could be displayed or recorded by an image
processor. The image sensor and digitizer work
together in capturing an image, which is the first stage
in the process (M. Saravanan, et al., 2024) The next
stage is the preprocessing stage, where the image is
enhanced for subsequent operations. Enhancement,
noise removal, area isolation, etc. are common topics
in preprocessing. An image can be "segmented" into
its individual elements by using this technique. Raw
pixel data, including either the region's border or the
pixels inside the region, is often what comes out
during segmentation. To prepare the raw pixel data
for further processing by the computer, a procedure
known as representation must be carried out. The
primary focus of description is the extraction of
characteristics that serve as fundamental
differentiators between various object classes. Based
on the data supplied by the object's descriptors,
recognition provides it a label. The process of
interpretation entails giving significance to a set of
identified items. The knowledge base is enriched
with knowledge acquired from the knowledge body
relevant to the problem domain. (Sheela S
Maharajpet, et al., 2024). The knowledge base further
governs the inner workings of the processing modules
and their interactions among themselves. Not all
modules need to be in place to do a particular job. The
application specifies the composition of the image
processing system. Typically, the image processor's
frame rates are around 25 fps (Maros Jakubec, et al.,
2023).
(i) Digital Computer: On the digital image, the
computer applies mathematical operations including
adding, subtracting, averaging, and convolution.
(ii) Mass Storage: Auxiliary storage devices like as
floppy discs and CD ROMs are widely used.
(iii) Hard Copy Device: This device stores the
relevant software and creates a permanent copy of the
picture.
(iv) Operator Console: In order to make software
adjustments or verify intermediate results, the
operator console has the necessary tools and
configurations. Moreover, the operator may validate
the entering of all necessary data and any errors that
may have arisen in consequence.
Digital image processing is when image data is
processed supported by some digital means. Images
originate most of the time in an optical way; the
modern state of the cameras just takes images
massively in digital form. The other option is to
video-capture them and converts to the digital form.
During the digitization process, sampling and
quantization are performed. These images would
normally be processed by one or more of the five
basic operations (Chentao Shen, et al., 2023). Several
A Novel Methodology to Ensure Rider Safety Measures Based on Helmet Detection System Using Deep Learning Mechanism
553

methods for processing images are detailed in this
section.
(i) Image Enhancement: Operations that increase a
image quality, such as enhancing its contrast and
brightness, decreasing its noise content, or sharpening
its features, are known as image enhancement. This
only improves the image by making it more
comprehensible while still revealing the same
information. It doesn't enrich it with any new details.
(ii) Restoring Images: Just like image enhancement,
image restoration works to restore a image quality,
but it relies heavily on measurements or known
degradations to do so. Geometric distortion, out-of-
focus areas, repeated noise, and camera shake are all
examples of image restoration issues. Images have
the means for the correction of known degradations.
(iii) Analyzing Images: Operations in image analysis
can turn attributes of the original image into either
numerical or graphical data. Dismantle them to put
them in categories. The statistics of the images will
govern their use. Common tasks include object
categorization, automated measurement, scene and
image feature extraction and description, and
automated measurement. The majority of image
analyzers' usage is in machine vision tasks.
(iv) Image Compression: Compressing and
decompressing images lessens the amount of data
needed to describe a image. Compressing photos gets
rid of all the unnecessary data that is often included
in them. The size is lowered by compression, making
it ideal for convenient storage or transportation.
Decompression occurs when seeing the image.
Lossy compression enhances compression at the
expense of the original picture, in contrast to lossless
compression, which preserves all of the original
image's data.
(v) Image Synthesis: Operations in image synthesis
generate new images from existing ones or from data
that does not contain images at all. In most cases,
image synthesis techniques produce results that
would be extremely difficult.
Several methods of image encoding are detailed
below.
• A binary image, in which each pixel is either
black or white. We just require one bitper pixel
since each pixel may take on one of two
potential values (0 or 1).
• A grayscale image typically uses a range of
grayscale values, from 0 (black) to 255 (white),
for each pixel. Because of this range, a single
byte—eight bits can represent each pixel. In
most cases, grayscale values are a power of 2,
however, other values are utilized.
• A color map matrix plus an array makes up an
indexed image. In this array, each pixel value is
an index into a color map. The array is denoted
by the variable name X in this text, whereas the
color map is referred to as map.
• A RGB image, often known as a true color
image, is one in which the relative amounts of
red, green, and blue give rise to distinct colors
for each pixel. There would be 2563 distinct
color combinations if the values of these
variables could vary from 0 to 255. A "stack" of
three matrices, one for each pixel's red, green,
and blue values, constitutes such an image. So,
there are three values that correspond to each
pixel.
2 RELATED WORKS
Motorbike use as a mode of transportation is a
common practice in many countries. However, the
absence of certain protective gear while riding poses
a threat to a rider (Rupesh Chandrakant Jaiswal, et al.,
2022). Therefore, wearing a helmet is very necessary
for your safety while riding. Therefore, it is cardinal
to build such a system to identify motorcycle helmets
and criminals in order to eliminate this dependence
on the human inspectors. Some biker riders don't see
the need to wear a helmet, but some only do when
they see a traffic cop. This project endeavors to
design an autonomous system functional in real-time,
with a focus on the YOLO deep learning approach.
The YOLO CNN is trademarked for real-time object
detection.
Safety helmets are essential in many outdoor and
indoor industrial settings, including high-temperature
metallurgical activities and the construction of
towering buildings (Qing An, et al., 2023).
Nevertheless, human error and a lack of compliance
are common problems with manual monitoring,
which also adds to its high cost. In addition, accuracy
is often lacking while detecting tiny target objects. A
potential solution to these problems is to enhance
safety helmets using the helmet detection algorithm.
Lightweight deep learning object identification
model YOLOv5s was updated and showcased in this
study. Recalculating the prediction frames,
clustering using the IoU metric, and altering the
anchor frames using the K-means++ approach
improve the performance of the suggested model,
ICRDICCT‘25 2025 - INTERNATIONAL CONFERENCE ON RESEARCH AND DEVELOPMENT IN INFORMATION,
COMMUNICATION, AND COMPUTING TECHNOLOGIES
554

which is an extension of the YOLOv5s network
model. In order to strengthen the YOLOv5s
network's backbone and neck networks, a mix of the
global attention mechanism and the convolutional
block attention module was utilized. Deep learning
neural networks are able to extract more features
thanks to these attention techniques, which enhance
the representation of global interactions and minimize
the loss of information characteristics. Improving
target feature extraction and reducing computation
required for model operation are both achieved by the
inclusion of the CBAM into the CSP module. The
suggested model employs the most current SIoU
(SCYLLA-IoU LOSS) as the boundary box loss
function to enhance the prediction box regression. A
lightweight network model that meets the demands of
real-time monitoring is constructed on top of the
upgraded YOLOv5s model. Knowledge distillation
technology reduces the model's computational effort
while enhancing detection speed. All three
metrics—precision, recall, and mean average
precision—show that the suggested model beats the
prior YOLOv5s network model in experimental
results. Even in dim light and from varying distances,
the suggested model might be able to better detect
helmet wear.
The workplace must be visually inspected and
immediately inform the workers when they do not
wear a safety helmet so that injuries on the job could
be avoided (Yange Li, et al., 2020). For that matter, a
need arises for automatic real-time detection from the
great amounts of unstructured visual data created by
on-site video monitoring systems. Despite the
abundance of research on deep learning-based helmet
detection models for traffic surveillance, there has
been surprisingly little discussion of a suitable
solution for industrial use, especially when
considering the complexity of the environment on a
construction site. To that end, we create a system that
uses deep learning to identify safety helmets on the
job site in real time. This approach makes use of the
convolutional neural network-based SSD-MobileNet
algorithm. A public dataset with 3,261 photos of
safety helmets was created and made available to the
public. The photographs came from two sources: the
workplace's video surveillance system and open
images retrieved with web crawler technology. The
picture set is sampled in a manner that is about 8:1:1,
with each set serving as a training set, validation set,
and test set. Using the SSD-MobileNet method, the
experimental findings show that the given deep
learning-based model can efficiently and accurately
detect risky operations including the failure to wear a
helmet on a construction site.
A comprehensive system of safety management
has been built up by power grid enterprises within
China to regulate restrictions, such as all safety rules
and two tickets embodied into one, for the assurance
of the operation's stability and protection of staff
(Songbo Chen, et al., 2020). On the other hand, a
good number of workers still show lack of safety
consciousness by not wearing helmets in their jobs
inside substations. Electric power workers must
always wear safety helmets to protect their heads
from potentially lethal accidents including electric
shock and strikes. Not only does working without a
helmet contradict the safety control system; it depicts
one as careless with the lives and possessions of
people. However, these controlling measures
currently are not efficient, effective, and quick
enough to detect and prevent such acts. This research
suggests using the Improved Faster R-CNN algorithm
to check if a person is wearing a safety helmet so that
we may better prevent this dangerous behavior.
Taking into account the actual circumstances, the
Retinex image improvement is implemented to
increase the quality of images captured in substations
of outside complex situations. Additionally, the K-
means++ technique is utilized to enhance the helmet's
adaptability to its little size. The findings of the
experiments demonstrate that the Improved Faster R-
CNN algorithm achieves better mean-average
precision than the Faster R-CNN method, allowing
for the automated identification of safety helmet
wears in real-time.
The construction industry is still sky-high in its
expansion, hence new and unique dangers to workers'
health and safety arise out of active construction.
Wearing helmets while on a construction site can
greatly lower the chance of incurring an injury
(Lihong Wei, et al., 2024). Hence, the objective of
this research is to propose a deep learning approach
in real-time for detecting whether construction
workers are using helmets or not. This study
examines the training outcomes of the YOLOv5s
network that was chosen through trials. Given that it
has a weak ability to identify tiny items and objects
that are partially obscured. This leads to a number of
improvements to the YOLOv5s network, a change to
the feature pyramid network to a BiFPN bidirectional
feature pyramid network, and an upgrade to Soft-
NMS from NMS, the post-processing methodology.
The loss function is optimized hereby enhancing the
convergence and detection speed of the model, which
introduces BiFEL-yolov5s: A YOLO V5 series
model enhanced by a combination of BiFPN
networks and Focal-EIoU Loss. The model's average
accuracy is improved by 0.9%, its recall rate is
A Novel Methodology to Ensure Rider Safety Measures Based on Helmet Detection System Using Deep Learning Mechanism
555
enhanced by 2.8%, and its detection speed is kept
relatively constant. It meets the needs of helmet
detection in a variety of work situations and is thus
more suitable to real-time safety helmet object
detection.
3 METHODOLOGY
A wide range of scientific and technological
disciplines can benefit from image processing
techniques. Some examples of the many uses for
image processing are presented in this brief list.
(i) Processing Documents: scanning and
transmitting them involves processing the documents,
which involves transforming them into digital
images, compressing them, and then storing them on
magnetic tape. It also has additional applications in
document reading, such as automatic feature
detection and recognition.
(ii) Health Care: examining and interpreting X-ray,
magnetic resonance imaging (MRI), computed
tomography (CT) pictures, images of individual cells,
and chromosomal karyotypes. The processing of
medical images from radiology, nuclear magnetic
resonance (NMR), and ultrasonic scanning, including
chest X-rays, cineangiograms, and projection pictures
of transaxial tomography, is one area of interest in
medical applications. These images may find value
in cancer and other illness screenings, patient
monitoring, and diagnosis.
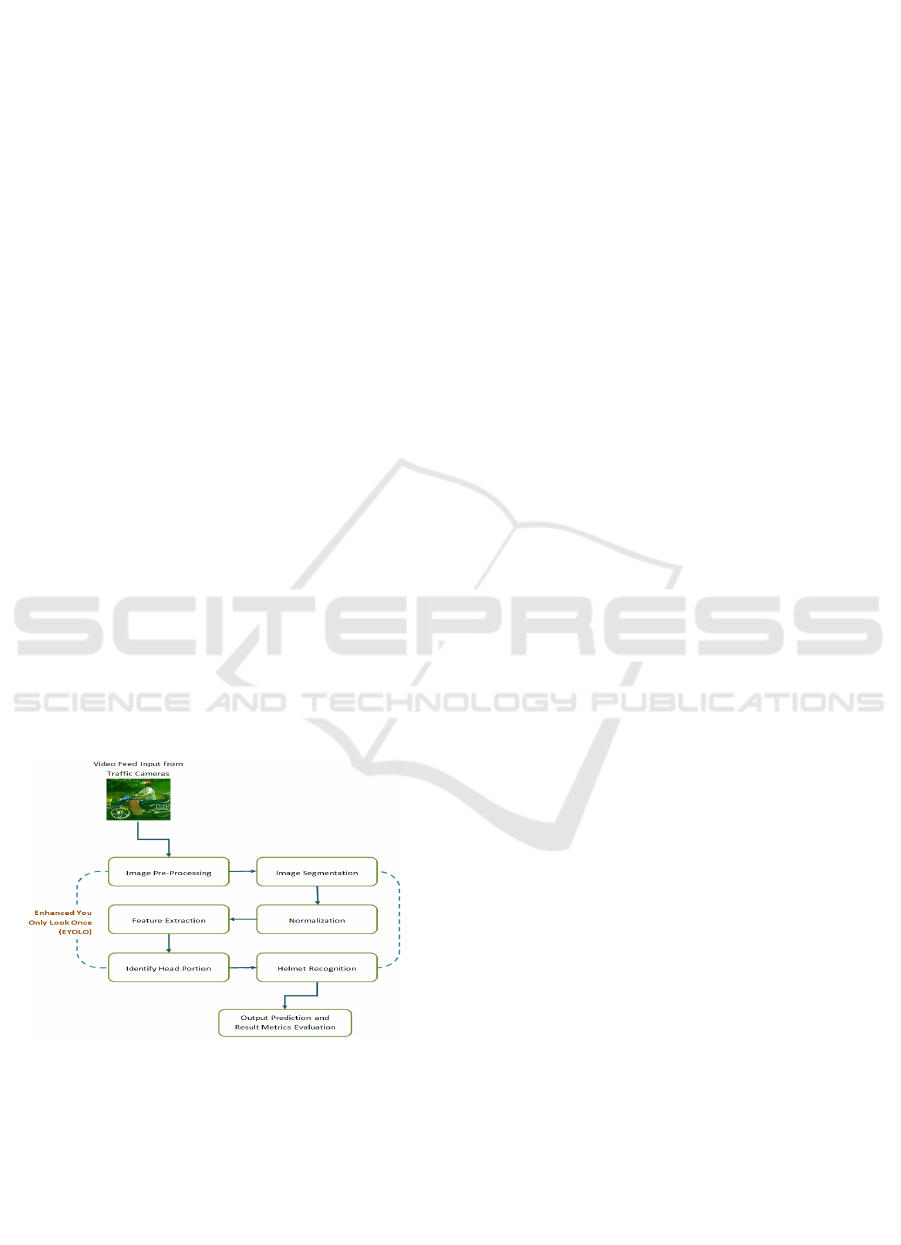
Figure 2: Proposed block diagram.
(iii) Industry: Paper sample inspection, automated
checking of manufacturing line items.
(iv) Defense/Intelligence: Applications include
reconnaissance photo-interpretation, which uses
automated analysis of Earth satellite imagery to seek
for sensitive targets or military threats, and target
acquisition and guidance, which aids in the
identification and tracking of targets in real-time
smart-bomb and missile-guidance systems.
(v) Radar Imaging System: Aircraft and missile
systems obtain their guiding and maneuvering
information from radar and sonar images, which are
utilized for target identification and recognition.
(vi) Agriculture: Satellite and aerial images of land
may be utilized for a variety of reasons, such as
measuring land usage, researching which places are
most suited for certain crops, and inspecting product
to determine if it is fresh or old.
3.1 Video Feed from Camera
The camera on-board to record all activities of a two-
wheeler rider is the most vital technology for helmet
recognition. The camera stands right at the forefront
of sensory input for the AI system by providing live
visual information about the activities of the rider and
the environment around them. As a streaming device,
the camera allows live monitoring of the rider for any
possible helmet compliance violation. The camera
captures the activities and motions of the rider to
determine whether the person is wearing a helmet or
not. Information that a live video stream provides
would give the system enough room to spring into
action anytime the rider is not wearing a helmet. With
this contextual information, such as traffic and road
barriers from the camera, the overall safety of the
rider can be assessed in a more effective manner. This
function of capturing live video input is an important
aspect of the helmet detection system, which is
designed to take proactive measures toward
enhancing rider safety in two-wheelers. Figure 2
shows the Proposed Block Diagram.
3.2 Capture the Image
The two-wheeler helmet recognition system relies on
the following steps: the capturing of images that will
mostly contain everything required by the recognition
analysis. The images are basically frames extracted
from the real-time video stream captured from the
camera. An image therefore, is like a snapshot during
a period in time, the raw material that makes up every
processing and analysis that will go on afterward. The
system is that it enables continuous data feed for
helmet detection whereby frames are taken at regular
intervals to allow for real-time checks on the state of
the rider's helmet. It, therefore, assists better in the
efficient utilization of computing resources and
speedy decisions on the wearing of helmets. This step
ICRDICCT‘25 2025 - INTERNATIONAL CONFERENCE ON RESEARCH AND DEVELOPMENT IN INFORMATION,
COMMUNICATION, AND COMPUTING TECHNOLOGIES
556

thus becomes the important component in detecting
the helmet and enables the system to determine the
rider's actions while taking requisite measures toward
the safety security of two-wheelers.
3.3 Preprocessing
The two-wheeler helmet identification system relies
heavily on preprocessing to get the recorded images
ready for analysis. Several preprocessing processes
are performed on the collected frames from the live
video feed to improve their quality and make them
more suitable for further analysis. Since various
images need to be processed fast and with lower
computational complexity, it is predetermined that
their sizes must be equal. There are various
normalization techniques which can standardize the
pixel values to allow for better comparison and study
of different images. Other noise filtering methods
such as median filtering and Gaussian blurring can
really help in reducing interference caused by noise
and beautifying the image quite nice. After these
preprocessing techniques, which enhance the
obtained photographs for accurate helmet detection,
the system can safely and rightly evaluate the rider's
helmet standing and therefore take measures to
provide safety on two-wheelers.
3.4 Feature Extraction
The important thing in helmet identification system
of two-wheelers is feature extraction, which
punctuates absorbing knowledge from the pre-
processed images whereby they will tell the system if
the rider is armed with a helmet. Important features
extracted from the pre-processed images may include
color, shape, and texture. While shape features detail
the external outline and structure of possible helmets
in the image, color features captured assist in
analyzing the patterned colors of helmets. Anyway,
texture features sometimes help distinguish helmets
from other items or backgrounds in the picture by
serving as a clue to some properties of the surface of
these items. Thus, the feature extraction process
serves to strengthen the information providing a
clearer picture of the shots enabling the system to
distinguish between helmet on or off instances. This
will allow the system to check when the rider is
wearing a helmet and then take measures concerning
perhaps a safety crackdown concerning two-
wheelers.
3.5 Database Collection
A reliable AI model built on the two-wheeler helmet
recognition system relies on database collection. The
first step is to prepare a large dataset of labeled
images containing both helmeted and helmetless
bikers. Each image in the collection is doted by well-
defined annotation to indicate the presence of a
helmet or not. The deep learning algorithm is then
trained over the labeled dataset, which is intended to
convey the model to find features relating to helmet
identification. The dataset, when used to train the
model, allows the model to generalize better on
unseen data by showing the examples of various
conditions under which the helmets are worn and
non-worn. Creating a strong and dependable two-
wheeler helmet detection system would depend on
database collecting.
3.6 Training
The phase during which identification of helmets on
two-wheeled vehicles is being undertaken is the
training one, which must be handled with extreme
care since it's here where the AI model gets to learn
to differentiate among different types of helmets
through observing patterns from a labeled dataset.
The training is generally performed using deep
learning algorithms like YOLO, which means "You
Only Look Once." In training, the model gets its
internal parameters tuned, i.e., reduces the difference
in predictions and actual ground truth labels, by
iteratively iterating over the labeled dataset. The
model learns how to identify helmets distinguishing
images of people wearing helmets from the images of
people not wearing helmets by modifying its
parameters repeatedly through backpropagation. The
model's training is aimed toward making it the best in
detecting helmets in varied environments,
illumination, and orientation and background. The
model's training helps it to be good at detecting
helmets on live video feeds, improving the safety of
motorcyclists.
3.7 Testing
In the two-wheeler helmet recognition system, testing
holds great importance. It is used to assess both the
efficacy of the training techniques and how well the
trained model may generalize. After having trained
itself on the labeled data sets, the model is evaluated
with another new set of test images, unseen
previously. The test images incorporated some real-
life scenes such as varying lighting, different rider
A Novel Methodology to Ensure Rider Safety Measures Based on Helmet Detection System Using Deep Learning Mechanism
557

positions, or many backgrounds. Each test picture
will be analyzed by the model for the presence of
helmets and outputs are made based on the analyses.
The predictions made by the model are then
compared to the ground truth labels in order to assess
model performance, i.e., accuracy, precision, recall,
and so forth. Testing on unseen data is important for
assessing a model's generalizability along with its
potential for high accuracy in helmet detection in
various real-life situations. This step is critical to
ensuring that the helmet detection system is both
reliable and effective in enhancing the rider's safety
while riding two-wheelers.
3.8 Identified Helmet Wear (or)
Helmet not Wear
In each frame of the live video feed in real-time, the
model trained on helmet detection infers decision
from past data as whether a helmet is in use or not.
Based on criteria set for attributes learned during
training, this once again assures, based on one frame,
the model decides whether a biker has put on a helmet
or not. This makes it possible for the vehicle to
proceed if the model sees a helmet that is sufficiently
confident to meet safety standards. If, however, a
helmet is not seen or seen with low confidence by the
model, the system would not allow the rider to move
forwards on the bike until one was placed on. In doing
so, the preventive measures aim at lowering the
chances of head injuries during mishaps and the
compulsory wearing of the helmet for rider safety. By
keeping a constant check on the state of the rider's
helmet in real-time, the technology establishes a
culture of safety and compliance on two-wheelers.
4 RESULTS AND DISCUSSION
Using the EYOLO (Enhanced You Only Look Once)
architecture, this research suggests a real-time helmet
identification system that has been trained on 4,956
photographs, with 80% of the images being used for
training and 20% for validation. This suggested
EYOLO achieved the highest prediction accuracy of
98.84% among the numerous deep learning variations
that were assessed, demonstrating exceptional
performance in the identification of safety helmets,
even in low-light conditions. The EYOLO model, in
conjunction with learning and classification methods,
was employed to identify helmet infractions among
motorcyclists in this research. The model
demonstrated the ability of deep learning to identify
helmet rule violators in challenging illumination and
weather conditions after being trained on 250 films
that were captured at 25 frames per second and each
lasted 25 seconds. The proposed model's potential for
real-time traffic surveillance and enforcement is
underscored by its high accuracy score. In general,
helmet detection systems have been significantly
improved by advancements in deep learning,
particularly in the context of EYOLO architectures.
The model that has been proposed underscores the
exceptional accuracy and real-time performance of
various EYOLO architectures in the detection of
helmet usage, thereby promoting enhanced safety
measures in traffic surveillance and construction
areas. A representation of the input image for the
proposed technique may be seen in the accompanying
figure, which is referred to as Figure 3. This image is
obtained from the video feed of traffic cameras.
Figure 3: Input image gathered from traffic cameras video
feed.
The consequences of the suggested method for
picture pre-processing and segmentation are depicted
in the accompanying figures, namely Figure 4 and
Figure 5.
ICRDICCT‘25 2025 - INTERNATIONAL CONFERENCE ON RESEARCH AND DEVELOPMENT IN INFORMATION,
COMMUNICATION, AND COMPUTING TECHNOLOGIES
558

Figure 4: Image pre-processing.
Figure 5: Segmentation.
The outputs of the feature extraction and helmet
identification stages of the proposed technique are
depicted in the accompanying figures, namely Figure
6 and Figure 7.
Figure 6: Feature extraction.
Figure 7: Helmet recognition.
The prediction accuracy level analysis of the
proposed scheme, EYOLO, is depicted in the
accompanying figure, Figure 8. This analysis is
conducted by cross-validating the proposed model
with the traditional learning algorithm, CNN, in order
A Novel Methodology to Ensure Rider Safety Measures Based on Helmet Detection System Using Deep Learning Mechanism
559
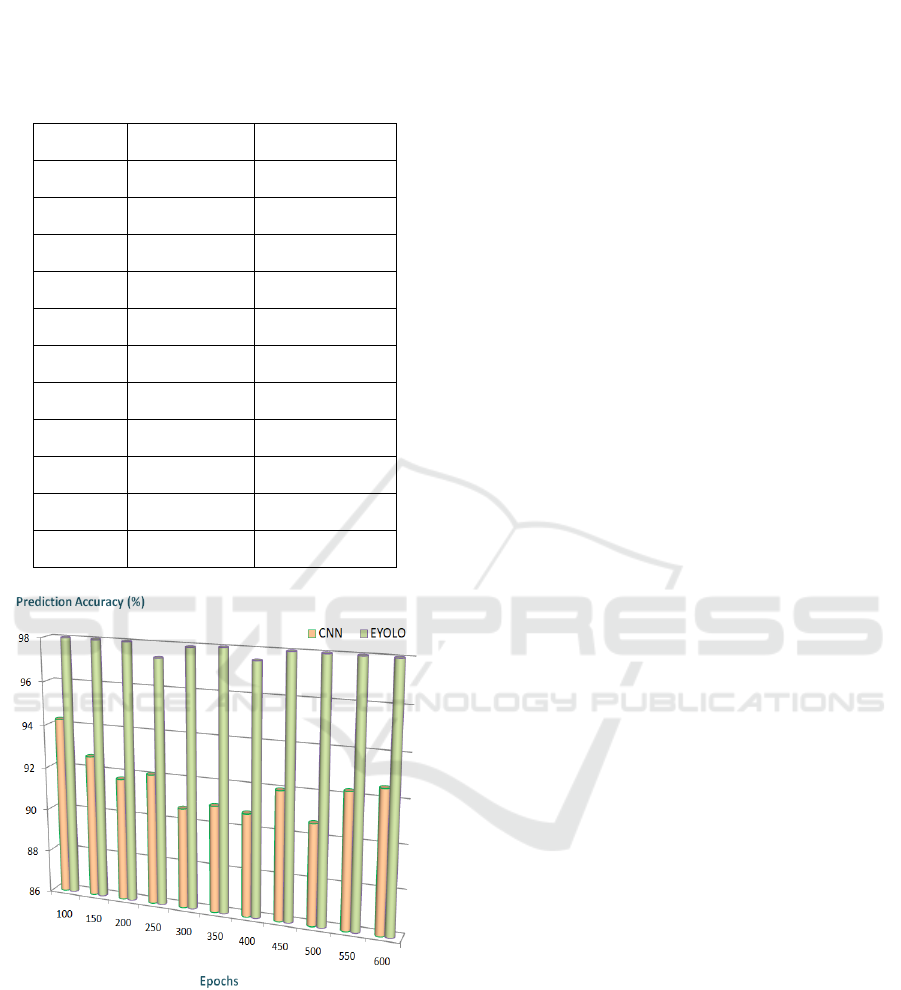
to assess its prediction accuracy. Table 1 is a
descriptive representation of the aforementioned.
Table 1: Analysis of prediction accuracy between CNN and
EYOLO.
Epochs CNN (%) EYOLO (%)
100 94.25 98.83
150 92.64 98.58
200 91.72 98.49
250 92.08 97.37
300 90.67 97.92
350 90.96 98.09
400 90.78 97.53
450 91.99 98.34
500 90.69 98.52
550 92.27 98.84
600 92.56 98.84
Figure 8: Prediction accuracy.
5 CONCLUSIONS
In summary, the helmet detection system for two-
wheelers is a proactive measure that integrates real-
time monitoring capabilities and artificial intelligence
to enhance passenger safety. The system effectively
determines whether motorcyclists are wearing
helmets by analyzing live video transmissions,
thereby facilitating the enforcement of safety
regulations. The system obtains commendable
accuracy in detecting helmets across diverse real-
world scenarios through extensive testing, rigorous
model training, and meticulous database collection.
Consequently, it cultivates a culture of safety, thereby
reducing the likelihood of head injuries on two-
wheelers and making a substantial contribution to the
safety of roads and the overall well-being of
motorcyclists. In conclusion, the helmet detection
system is a critical technological solution in the field
of road safety, providing tangible advantages in the
areas of regulatory compliance and injury prevention.
Its significance in promoting safer riding practices
and decreasing the incidence of head injuries is
emphasized by its capacity to promptly identify non-
compliance and implement enforcement measures.
This system not only improves the safety of
individual motorcyclists but also contributes to the
overarching objective of establishing safer road
environments for all road users, thereby fostering a
culture of responsibility and well-being within the
community, by utilizing state-of-the-art AI
technologies.
This work can be improved in the future by
promoting safer cycling behaviors and encouraging
helmet usage by providing real-time alerts or
feedback to the rider. In addition to enhancing rider
safety by expanding the system to detect other safety
gear or objects of interest, such as reflective clothing
or road hazards, and by integrating the helmet
detection system with vehicle systems to enable
features such as automatic emergency braking or
adaptive cruise control based on the rider's safety
status.
REFERENCES
Bingyan Lin, "Safety Helmet Detection Based on Improved
YOLOv8", IEEE Access, 2024.
Chentao Shen, et al., "Small-scale helmet detection based
on improved YOLOv5 and moving object detection",
Proceedings of the 2023 ACM Symposium on Spatial
User Interaction, 2023.
Gopinath D, et al., "Detection of Helmet and License Plate
Using Machine Learning", International Journal of
Intelligent Systems and Applications in Engineering,
2024.
Hanhe Lin, et al., "Helmet Use Detection of Tracked
Motorcycles Using CNN-Based Multi-Task Learning",
IEEE Access, 2020.
ICRDICCT‘25 2025 - INTERNATIONAL CONFERENCE ON RESEARCH AND DEVELOPMENT IN INFORMATION,
COMMUNICATION, AND COMPUTING TECHNOLOGIES
560

Lihong Wei, et al., "Research on helmet wearing detection
method based on deep learning", Scientific Reports,
2024.
M. Saravanan, et al., "Comprehensive study on the
development of an automatic helmet violator detection
system (AHVDS) using advanced machine learning
techniques", Computers and Electrical Engineering,
2024.
Maros Jakubec, et al., "Deep Learning-Based Automatic
Helmet Recognition for Two-Wheeled Road Safety",
Transportation Research Procedia, 2023.
Qing An, et al., "Research on Safety Helmet Detection
Algorithm Based on Improved YOLOv5s", Sensors,
2023.
Rupesh Chandrakant Jaiswal, et al., "Helmet Detection
Using Machine Learning", Journal of Emerging
Technologies and Innovative Research, 2022.
Sheela S Maharajpet, et al., "Advanced Safety Helmet
Detection: Enhancing Industrial Site Safety with AI",
QTanalytics Publication, 2024.
Songbo Chen, et al., "Detection of Safety Helmet Wearing
Based on Improved Faster R-CNN", International Joint
Conference on Neural Networks, 2020.
Wei Jia, et al., "Real-time automatic helmet detection of
motorcyclists in urban traffic using improved YOLOv5
detector", IET Image Processing, 2021.
Xuejun Jia, et al., "High-Precision and Lightweight Model
for Rapid Safety Helmet Detection", Sensors, 2024.
Yange Li, et al., "Deep Learning-Based Safety Helmet
Detection in Engineering Management Based on
Convolutional Neural Networks", Advances in Civil
Engineering, 2020.
Yongze Ji, et al., "Research on the Application of Helmet
Detection Based on YOLOv4", Journal of Computer
and Communications, 2022.
A Novel Methodology to Ensure Rider Safety Measures Based on Helmet Detection System Using Deep Learning Mechanism
561
