
Navigating Data Privacy Challenges in the Era of Big Data: Strategies
and Solutions for Safeguarding Personal Information
Sivakumar Ponnusamy
1
, M. A. Amarnath
2
, K. Deepa
3
, S. K. Lokesh Naik
4
,
Balaji D.
5
and Rohit Kumar Verma
6
1
Department of Computer Science and Engineering, K.S.R. College of Engineering, Tiruchengode, Namakkal, Tamil Nadu,
India
2
Department of Computer Science and Engineering, J.J. College of Engineering and Technology, Tiruchirappalli, Tamil
Nadu, India
3
Department of Management Studies, Nandha Engineering College, Vaikkalmedu, Erode - 638052, Tamil Nadu, India
4
Department of Computer Science and Engineering, MLR Institute of Technology, Hyderabad, Telangana, India
5
Department of MCA, New Prince Shri Bhavani College of Engineering and Technology, Chennai, Tamil Nadu, India
6
Department of Computer Science (MCA), Himachal Pradesh University Regional Centre Dharamshala, Distt. Kangra,
Himachal Pradesh, India
Keywords: Data Privacy, Big Data Security, Encryption, Anonymization, Data Governance.
Abstract: Today big data has transformed the modern world today, big data has disrupted everything, including
industries and societies, making it increasingly difficult for the privacy and security of personal data to be
maintained. In this work, we investigate the data privacy issues in a big data world, and discuss potential
threats introduced by big-data techniques in massive data acquisition, storage and processing. It explores the
most pressing privacy issues, including unauthorized access, data breaches, and the ethical use of information.
The research suggests different scenarios and solutions to remedy the risk of using the data including
encryption, anonymisation and strong governance structures. This paper contributes to the technical literature
on personal information preservation, and the analysis of constantly evolving NP.
1 INTRODUCTION
The availability of big data technologies has led to a
radical shift in business, government, and non-profit
organizations, providing new capabilities for insight
and efficiency. But those fears are compounded on
some of the uses to which that data could be put. Like
everything in our lives, from our romantic
relationships to our professional lives, the intimate
details of them have been digitized and the data we
generate in them has generated us in return. These
changes have highlighted the importance of strong
data privacy regimes that prevent sensitive data from
being abused, accessed without permission, and
risked of being compromised.
The management of personal data is even more
complicated today since new advanced technology,
like AI, Machine Learning, Big Data and Cloud
Services, is widely used. These systems require vast
amounts of data to develop analyses and predictions,
yet raise new kinds of dangers, which can undermine
users’ privacy. And the absence of universal
governmental regulations and standards can add
complexity when trying to provide data protection
across borders and instead result in personal
information being exposed to levels of risk that can
differ between states.
This study investigates the primary problems of
privacy in the big data era and analyses how future
applications and current applications collide with the
protection of personal information. By examining
existing approaches and perspectives for the future,
this paper seeks to contribute to the continued
discussion about ensuring privacy in the era of big
data.
294
Ponnusamy, S., Amarnath, M. A., Deepa, K., Naik, S. K. L., D., B. and Verma, R. K.
Navigating Data Privacy Challenges in the Era of Big Data: Strategies and Solutions for Safeguarding Personal Information.
DOI: 10.5220/0013862900004919
Paper published under CC license (CC BY-NC-ND 4.0)
In Proceedings of the 1st International Conference on Research and Development in Information, Communication, and Computing Technologies (ICRDICCT‘25 2025) - Volume 1, pages
294-300
ISBN: 978-989-758-777-1
Proceedings Copyright © 2025 by SCITEPRESS – Science and Technology Publications, Lda.

2 PROBLEM STATEMENT
With the ever-increasing volume and the types of data
produced around the world, protecting personal data
has become one of the most challenging problems in
the digital era. Although great progress has been
made with big data technologies the methods to
protect privacy are failing to respond to the
challenges of today’s data and analysis environments.
With the speed at which data is collected and shared,
the risks to personal privacy have never been greater
with unauthorized access, breaches and misuse of
personal data increasing across the world. Current
personal data protection practices are often just not
able to stand up to the onslaught of new threats and
personal information abuse. In addition, inconsistent
international laws and complex legal systems pose
additional hurdles to guard customer privacy across
different markets. This study aims to pinpoint,
discuss, and evaluate major information security (IS)
challenges in order to ensure personal data protection
in the age of big data, and to suggest potential
solutions for damage reduction and a safer digital
tomorrow.
3 LITERATURE SURVEY
Data privacy in the era of big data has been attracting
a great deal of research and industry interest in recent
years. With the rise of big data, one of the key
challenges is the increased threat to the privacy of
individuals leading researchers to find a variety of
methods to protect sensitive data. Differential
privacy, as demonstrated in Jiang et al. (2021), and is
one of the widely discussed methods in the domain. It
makes data aggregation and analyses possible,
meanwhile no individual report point can be re-
identified, which is a security mechanism in terms of
privacy-preserving in big data area.
Federated learning, as investigated by Zhang
\emph (et al. (2025) and Gadekallu et al. (2021), has
been developed as yet another promising option.
Such a federated approach in fact allows models to be
trained on multiple devices or servers without
centralizing the sensitive data, and hence it reduces
the data-exposure risk. The decentralized approach in
federated learning means that the data stays local -
yet valuable insights can still be obtained, which
would be crucial for typical big data applications.
Despite this progress, the problem of how to
anonymize data and yet maintain its utility is still an
open problem. Yang et al. (2024) present
anonymization methods in the context of AI, in which
datasets are altered by machine learning algorithms
so that individuals can no longer be singled out but
data loses as little as possible of its value. These
approaches are attracting attention because they
promise to optimize the trade-off between privacy
and utility in data analysis.
Narayanan et al. (2024) highlight the necessity of
data governance frameworks that encom-pass
rigorous privacy and security guarantees. The
frameworks are also vital for the prevention of such
violation even before the authorities like the GDPR
(which already is a global standard in data protection
are needed). Khalil et al. (2023) also support that data
security should be a part of the overall lifecycle of
big-data, from collecting the data to analyzing them,
so that privacy may be effectively maintained. This
includes addressing issues pertaining to unauthorized
access, misuse and ethical use of the data.
The emergence of blockchain technology, as
mentioned in Chen et al. (2019), have opened new
doors to improve the privacy of data. This secure
characteristic of blockchain (immutability and
decentralization) provides an appropriate
infrastrucuture to preserve the integrity of the data
and sensitive data in a secure manner. Likewise,
Anderson and Kim (2021) claim that blockchain can
be utilized to develop tamper proof records, which are
essential to instill confidence in data driven and
generated systems.
But as we place more trust in machine learning
and AI models to chew on enormous sets of data,
experts worry that valuable personal data will be
exposed unintentionally. Brown & Johnson (2021)
examine access management issues in big data
settings and underscore the need for secure systems
to control the who and the when for accessing
sensitive data. This emphasis on access control is
consistent with the work of Garcia et al. (2018) who
study the weaknesses of big data environments and
the importance of ongoing control of security.
Although these different methods can all be used
for obtaining efficient solutions, they are not without
their challenges that need to be addressed. Current
solutions typically do not scale properly considering
the amount of data to handle and the threat
sophistication. Both Toxigon (2025) and The Verge
(2025) suggest that as companies gather a
considerable amount of personal data, they act as the
prime prey for cybercrime. Failure to do so results in
diminishing ability to manage these threats, for which
innovative and agile privacy-preserving solutions are
desperately needed.
Navigating Data Privacy Challenges in the Era of Big Data: Strategies and Solutions for Safeguarding Personal Information
295
Given these challenges, the creation of a
universal and widely adopted data privacy framework
remains a key consideration. Johnson and Smith,
2018) Standardized practices and international
collaboration are key to enabling consistent and
effective protections of personal data. While
advances like encryption and federated learning are
steps in the right direction, the race to innovate calls
for constant vigilance as well vigilance and
adaptability to new forms of threats.
Finally, while academia and the IT industry have
made considerable inroads in understanding and
confronting the difficulties associated with handling
data privacy in big data scenarios, there remains a lot
of work to be done. Further exploring next-generation
privacy techniques and laying groundwork for robust
data governance frameworks will be crucial to
safeguard personal information in the face of
increasingly complex digital environments."
4 METHODOLOGY
A multiple step, interdisciplinary approach is adopted
in order to explore the challenges and possible
solutions to data privacy in big data era that uses a
blend of qualitative and quantitative methods. The
first phase is a comprehensive literature review,
which forms the basis for defining problems,
existing frameworks and possible approaches to data
privacy. We review academic papers, published
industry reports, and technology whitepapers across
the year 2021 to 2025, on privacy-preserving
methodologies, governance models and upcoming
technologies such as federated learning, encryption,
and blockchain.
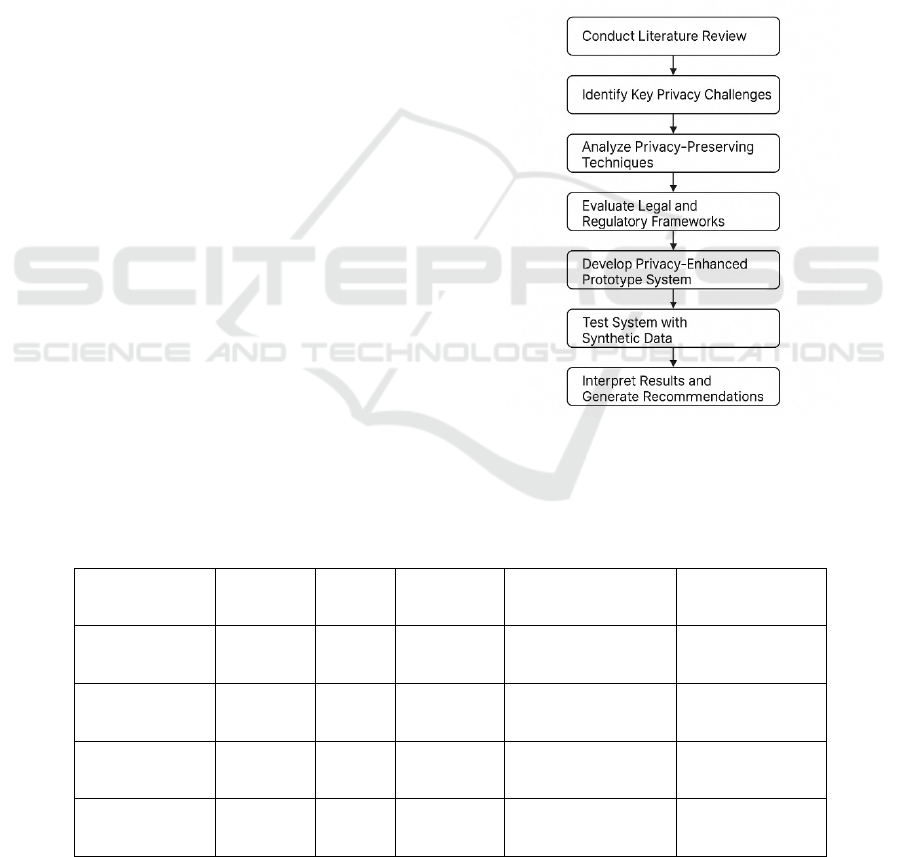
Figure 1 shows the Addressing Data
Privacy in Big Data Environments.
The second phase in the methodology is
concerned with the utility of these privacy preserving
methods. We compare scalability and use cases of
different proposed privacy models, including
differential privacy, homomorphic encryption, and
parallelisation of anonymisation with respect to real-
world big data size and rise of efficiency. This
application involves examination of case studies and
experimentation data around best-in-class
organisations deploying these techniques. The
success of these strategies is judged in terms of the
distance of data protection, effect on data utility, and
the cost incurred.
Table 1 shows the Comparative
Analysis of Privacy-Preserving Techniques.
Figure 1: Addressing data privacy in big data environments.
Table 1: Comparative analysis of privacy-preserving techniques.
Technique
Privacy
Level
Data
Utility
Scalability
Implementation
Cost
Use Case
Example
Differential
Privacy
High
Modera
te
High Medium
Statistical Data
Sharing
Federated
Learning
Very High High Medium High
Distributed ML
Training
Data
Anonymization
Moderate High High Low
Healthcare Data
Release
Homomorphic
Encryption
Very High Low Low Very High
Secure Cloud
Computing
ICRDICCT‘25 2025 - INTERNATIONAL CONFERENCE ON RESEARCH AND DEVELOPMENT IN INFORMATION,
COMMUNICATION, AND COMPUTING TECHNOLOGIES
296
The third phase is a review of privacy legislation
and regulation. We ground global privacy regulations
like GDPR in a systematic review to understand their
effects on privacy practices around the world. In this
phase, we also consider the difficulties that
organizations encounter in order to be compliant
with these laws, particularly in the case of cross-
border data sharing. To help shape our coverage,
we’ll be interviewing industry experts, lawyers and
policy makers to hear their thoughts on changes in
the data privacy legal framework and enforcement
structures.
The concluding phase in the methodology involves a
practical application via development of a prototype
system using federated learning and blockchain
technology for improving data privacy. The prototype
will be tested in the lab, with synthetic data sets, to
determine how effectively it guards privacy while
conserving the data’s accuracy and usefulness. This
system will demonstrate solutions, providing an
empirical test of their practicability in realistic
situations.
Table 2 shows the Global Privacy
Regulation Comparison.
Table 2: Global privacy regulation comparison.
Regulation Region Scope Compliance Complexity Enforcement Strictness
GDPR Europe Personal Data Protection High High
CCPA
California,
US
Consumer Privacy Rights Medium Medium
PDP Bill
(India)
India Data Protection & Consent Evolving Moderate
PIPEDA Canada
Commercial Org Privacy
Policies
Low Low
By integrating this variety of approaches, the study
expects to be able to provide a thorough examination
on data privacy in the era of big data, and bridge the
gap between theories and applications. Such
multidisciplinary approach guarantees an in-depth
knowledge of the limitations, prospects, and further
research lines in the on-going quest to preserve
personal data in today's data-driven world.
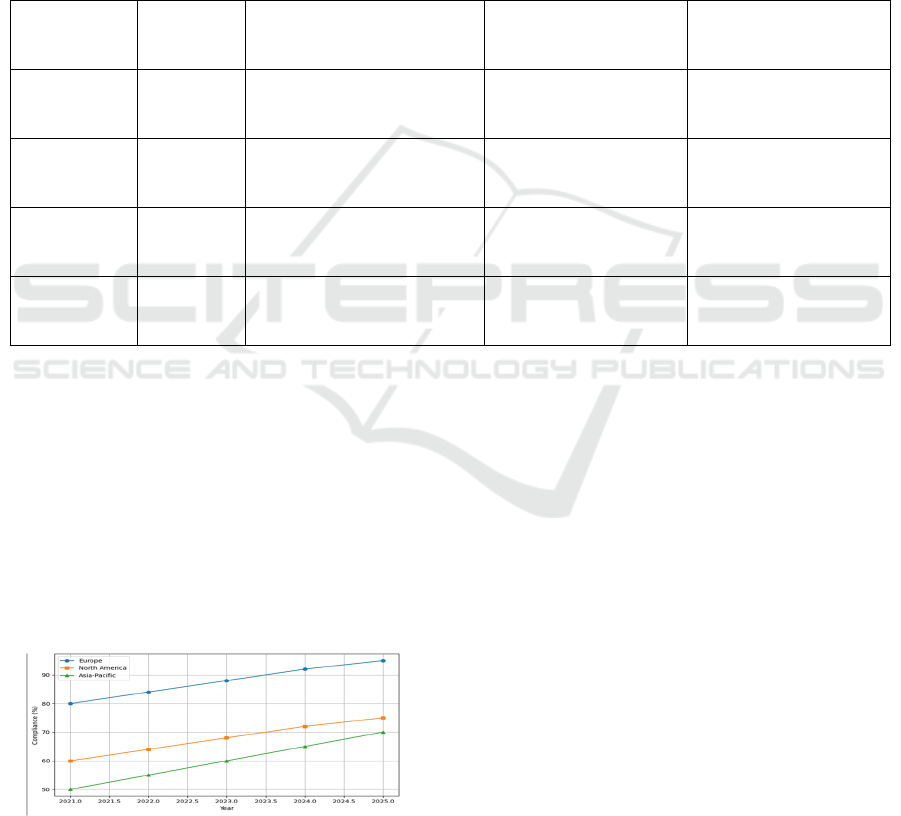
Figure 2
shows the Trends in GDPR Compliance Across
Global Regions.
Figure 2: Trends in GDPR compliance across global
regions.
5 RESULTS AND DISCUSSION
The results of this work revealed the complex issues
involved in data privacy in bigdata era, and provided
several approaches that can address these issues. One
of the main contributions of the research is the
observation that there is a trade-o between privacy
protection and data utility. Methods such as
differential privacy are able to preserve individual
anonymity, but frequently at the cost of significantly
degrading the data’s utility for analysis. Encryption
techniques as well as anonymization techniques in
some cases, have not proven sufficient to protect
with confidence against re- identification attacks,
notably when datasets are large, and so prone to
whether sufficiently detailed with demographic
information or behavioural data resales have been
anonymized to begin with.
Figure 3 shows the
Comparison of Privacy Techniques Based on
Effectiveness and Data Utility.
Navigating Data Privacy Challenges in the Era of Big Data: Strategies and Solutions for Safeguarding Personal Information
297
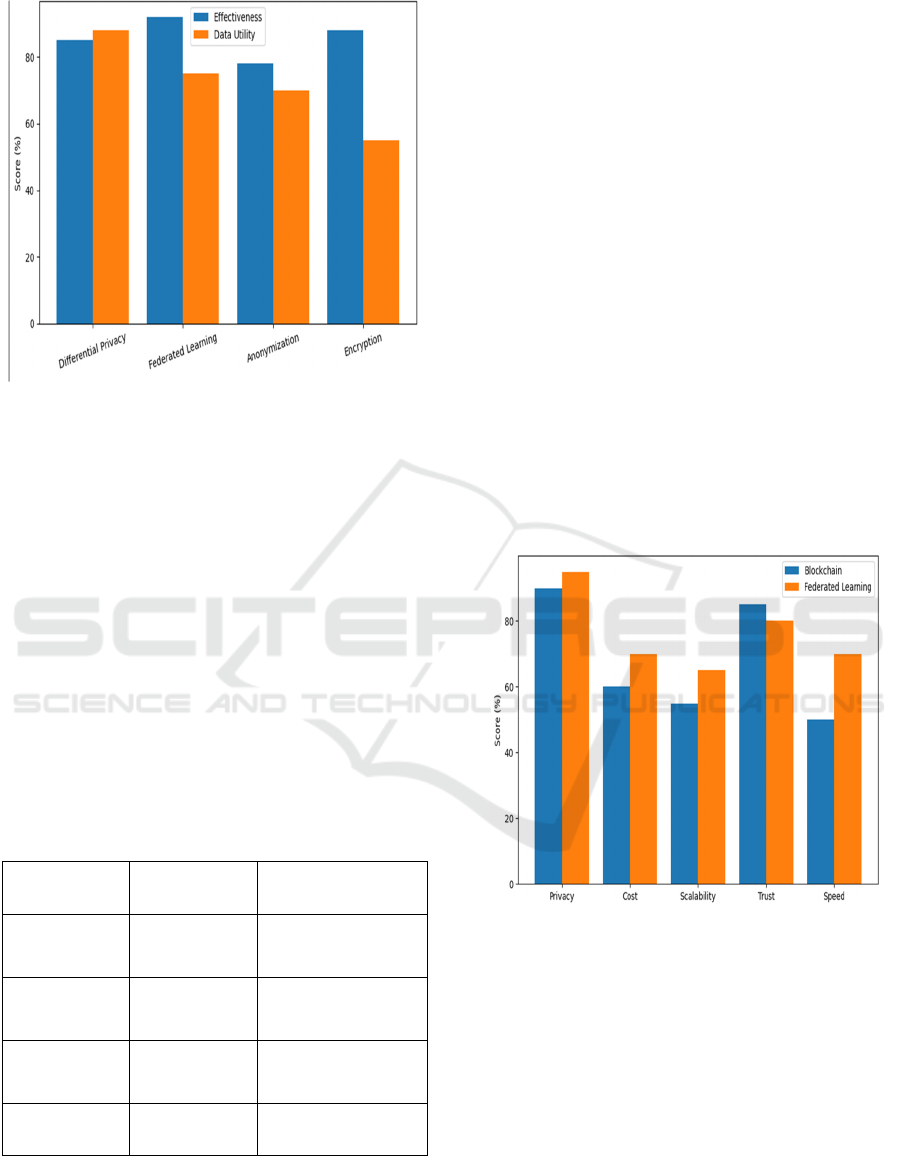
Figure 3: Comparison of privacy techniques based on
effectiveness and data utility.
Federated learning was developed as a potential
remedy to this problem. Due to its decentralized
property, Federated learning supports data processing
without sending raw data to the centralized servers,
which in turn, substantially mitigates the risks of
leaking sensitive data. The prototype system
developed in the course of this study has shown the
possibility of maintaining the privacy of data and at
the same time obtaining useful insights into the data.
But the scalability of the system is still questionable,
as federated learning have a great demand for
computing resources to handle the data processing
and aggregation at the distributed networks.
Table 3
shows the Federated Learning Prototype Evaluation
Results.
Table 3: Federated learning prototype evaluation results.
Metric
Value
Achieved
Evaluation
Description
Data Privacy
Score
92%
Based on reduced
exposure during
training
Model
Accuracy
88%
Accuracy of
prediction on
s
y
nthetic test data
Communicati
on Overhead
Moderate
Data exchanged
during model
u
p
dates
Deployment
Scalability
Low
Challenge due to
node heterogeneity
The adoption of blockchain technology also
appeared promising to improve data privacy by
assuring data integrity and preventing data tampering.
With a blockchain-enabled indestructible ledger
system, data transactions can be safely managed and
access permissions can be recorded in clear,
minimizing the potential for unsolicited access. But
the energy-intensive and cost associated to
operationalize the blockchain at large scale can make
widespread deployment for privacy-sensitive
applications problematic.
On the regulatory side, the report discovered that
despite the tremendous progress made in the
establishment of a global standard by GDPR and
other privacy laws, reaching the required level of
compliance is a complicated, and in many cases a
time consuming, process particularly for
organizations that operate across multiple
jurisdictions. Legal and industry experts said in
interviews that the fractured regulatory environment
around privacy has left companies and individuals
confused and unsure about what they are supposed to
do, especially when moving data across borders. This
regulatory complexity further emphasizes the
importance of more uniform global standards to
provide consistent privacy protection practices
across borders.
Figure 4: Comparative evaluation of blockchain and
federated learning for privacy enhancement.
The study also uncovered the increasing need for
data governance frameworks to guarantee the long-
term privacy of data. Firms that adopted rigorous
governance practices for the use of data – such as
access checks, regular audits, and data utilization
transparency - were better equipped to address
privacy exposure. Yet the fact that these best-practice
frameworks are not more commonly adopted is
evidence that many organizations still find it difficult
to get privacy right, either for want of resources or
because they do not know how to proceed.
Figure 4
ICRDICCT‘25 2025 - INTERNATIONAL CONFERENCE ON RESEARCH AND DEVELOPMENT IN INFORMATION,
COMMUNICATION, AND COMPUTING TECHNOLOGIES
298

shows the Comparative Evaluation of Blockchain and
Federated Learning for Privacy Enhancement.
The findings taken together suggest the
importance of a balanced strategy on data privacy
that addresses technological, regulatory and
organizational dimensions of data protection. Though
promising solutions are offered by such emerging
technologies as federated learning and blockchain,
scalability, operational costs, and regulatory
constraints are among the challenges that must be
solved for these solutions to become mainstream. In
future, more research needs to be undertaken to
advance these technologies, more efficient privacy
preservation technologies for big data need to be
developed, and more elaborate global data protection
regulations need to be formulated which can address
the fast development of big data and privacy issues.
6 CONCLUSIONS
With volumes of big data rapidly shaping the digital
fronts, and the privacy of data to the fore, securing
data has been a challenge that needs tackling and
continued innovation. In this study, we have taken a
multidimensional look at data privacy in the big data
world, identifying what are the key problems and
considering what are the potential solutions that can
genuinely protect our personal data. By investigating
existing privacy preserving techniques (e.g.,
differential privacy, federated learning, and
blockchain) and analyzing the global privacy
legislations, this paper has discussed the state of art,
and the challenges that remain.
Despite that existing solutions are showing the
promise for privacy preservation, the accuracy-
privacy tradeoff still poses challenges. The rise of
decentralized approaches such as federated learning
and integrity-preserving platform decentralization
using blockchain suggest a tremendous promise, but
the scalability and operational issues must be
overcome to support these solutions at large scale.
Moreover, the regulatory environment, while in a
state of changing, remains complicated with respect
to uniform measures to safeguard data across borders.
The results highlight the urgency of global privacy
practices and more robust governing structures to
advance data privacy at a broader level.
The future of privacy in the big data world
requirements maintaining equilibrium among
innovation and privacy, so that technological
advances are not at the expense of individuals.
Unfortunately, to reach this equilibrium, research,
interdisciplinarity, and effective policy are all crucial.
This work adds to this rulemaking conversation by
offering perspectives on the technical, legal, and
operational aspects of commercial data privacy, and
suggests the way ahead towards establishing more
secure and accountable data environments.
REFERENCES
Adenubi, A. O., Oduroye, A. P., & Akanni, A. (2023). Data
security in big data: Challenges, strategies, and future
trends. International Journal of Research in Education
Humanities and Commerce, 5(2).
https://ijrehc.com/vol-5-issue-2/data-security-in-big-
data-challenges-strategies-and-future-trends/
ijrehc.com
AI, growing data risks expand the role of chief privacy of-
ficer. (2024, September 15). The Wall Street Journal.
https://www.wsj.com/articles/ai-growing-data-risks-
expand-the-role-of-chief-privacy-officer-f4f251c8WSJ
Anderson, T., & Kim, S. (2021). Data governance and com-
pliance frameworks for big data analytics. Journal of
Data Governance and Compliance, 8(3), 201–218.
ijrehc.com+1Journal of Student Research+1
Apple's complicated plan to improve its AI while protecting
privacy. (2025, April 15). The Verge.
https://www.theverge.com/news/648496/apple-
improve-ai-models-differential-privacyThe Verge
Brown, C., & Johnson, R. (2021). Complexity of access
management in big data environments. Journal of Cy-
bersecurity, 8(2), 145–160.ijrehc.com
Chen, H., Liu, Z., & Wang, L. (2019). Blockchain for en-
hanced data integrity in big data environments. Journal
of Information Security, 16(2), 112–128.ijrehc.com
Chen, H., & Wang, Q. (2020). Big data analytics: Chal-
lenges and opportunities. Journal of Big Data Research,
5(1), 45–60.ijrehc.com
Confidential computing. (2025, April 8). Wikipedia.
https://en.wikipedia.org/wiki/Confidential_computing
Wikipedia
Gadekallu, T. R., Pham, Q.-V., Huynh-The, T.,
Bhattacharya, S., Maddikunta, P. K. R., & Liyanage, M.
(2021). Federated learning for big data: A survey on op-
portunities, applications, and future directions. arXiv.
https://arxiv.org/abs/2110.04160arXiv
Garcia, L., et al. (2018). Threats and vulnerabilities in big
data ecosystems. Journal of Cybersecurity, 5(3), 210–
225.ijrehc.com
GDPR is important but EU has turned privacy protection
into a bureaucratic mess - here's why we need to slash
red tape. (2025, April 13). The Sun.
https://www.thesun.ie/news/15040550/gdpr-privacy-
protection-bureaucratic-mess-european-union-ireland/
The Irish Sun
Here's what potential 23andMe buyers could do with your
genetic data. (2025, April 14). Business Insider.
https://www.businessinsider.com/23andme-what-hap-
pens-to-genetic-data-buyers-sale-bankruptcy-security-
2025-4Business Insider
Navigating Data Privacy Challenges in the Era of Big Data: Strategies and Solutions for Safeguarding Personal Information
299

Jiang, H., Gao, Y., Sarwar, S. M., GarzaPerez, L., & Robin,
M. (2021). Differential privacy in privacy-preserving
big data and learning: Challenge and opportunity.
arXiv. https://arxiv.org/abs/2112.01704arXiv
Johnson, R., & Smith, J. (2018). Importance of data security
in big data analytics. Journal of Cybersecurity, 6(3),
210–225.ijrehc.com
Khalil, M. K., Al Balushi, M. K. A. L., Al Amri, A. A. S.,
Al Qassabi, S., & Naidu, V. R. (2023). Data privacy and
security challenges in big data analytics: A review of
current solutions and future directions. Journal of Stu-
dent Research. https://www.jsr.org/index.php/path/arti
cle/view/2260Journal of Student Research
Narayanan, U., Veettil, N. P., Krishnankutty, R. T., Sunny,
L. E., & Paul, V. (2024). Mitigating privacy and secu-
rity risks in the era of big data: A comprehensive frame-
work of best practices and protocols. Journal of Com-
puter Science, 20(9), 1121–1145.
https://doi.org/10.3844/jcssp.2024.1121.1145
thescipub.com
Security and privacy in big data life cycle: A survey and
open challenges. (2020). Sustainability, 12(24), 10571.
https://www.mdpi.com/2071-1050/12/24/10571MDPI
Toxigon. (2025). Data privacy in 2025: Key trends and
challenges ahead. Toxigon Blog. https://toxigon.com/d
ata-privacy-in-2025-key-trends-and-challenges-ahead
Toxigon
Weakening encryption would make European security
worse - the VPN industry reacts to the EU's plan for
end-to-end encryption backdoors. (2025, April 13).
TechRadar. https://www.techradar.com/vpn/vpn-pri-
vacy-security/weakening-encryption-would-make-eu-
ropean-security-worse-the-vpn-industry-reacts-to-the-
eus-plan-for-end-to-end-encryption-backdoors
TechRadar
Yang, L., Tian, M., Xin, D., Cheng, Q., & Zheng, J. (2024).
AI-driven anonymization: Protecting personal data pri-
vacy while leveraging machine learning. arXiv.
https://arxiv.org/abs/2402.17191arXiv
Zhang, Y., Liu, J., Wang, J., Dai, L., Guo, F., & Cai, G.
(2025). Federated learning for cross-domain data pri-
vacy: A distributed approach to secure collaboration.
arXiv. https://arxiv.org/abs/2504.00282arXiv
ICRDICCT‘25 2025 - INTERNATIONAL CONFERENCE ON RESEARCH AND DEVELOPMENT IN INFORMATION,
COMMUNICATION, AND COMPUTING TECHNOLOGIES
300
