
Lightweight Quantum Cryptography Integration Framework for
Secure IoT‑Telecommunication Systems in Post‑Quantum Era
K. A. Ajmath
1
, L. Kalaiselvi
2
, Jenifer Shylaja M.
3
, R. Meenakshi
4
,
Tandra Nagarjuna
5
and Syed Zahidur Rashid
6
1
Department of Computer Science, Samarkand International University of Technology, Uzbekistan
2
Department of Electronics and Communication Engineering, Surya Engineering College, Erode, Tamil Nadu, India
3
Department of Computer Science and Design, R.M.K. Engineering College, RSM Nagar, Kavaraipettai, Tamil Nadu, India
4
Department of Electronics and Communication Engineering, J.J. College of Engineering and Technology, Tiruchirappalli,
Tamil Nadu, India
5
Department of Computer Science and Engineering, MLR Institute of Technology, Hyderabad, Telangana, India
6
Department of Electronic and Telecommunication Engineering, International Islamic University Chittagong, Chittagong,
Bangladesh
Keywords: Quantum Cryptography, IoT Security, Telecommunication Infrastructure, Post‑Quantum Encryption,
Quantum Key Distribution.
Abstract: The growing complexity and proliferation of IoT devices in telecommunication networks need strong and
future-proof security mechanisms. Conventional cryptographic techniques are susceptible to new emerging
threats from quantum computing. In this paper, A lightweight quantum cryptography integration framework
is proposed for telecommunication systems based on IoT. Compared to all other existing work that either
concern with only PQC algorithms or theoretical study, this study sketched an efficient and practical design
that helps in secure communication layer for the constrained IoT nodes. Quantum Key Distribution (QKD)
and hybrid cryptographic primitives are used to ensure the security of the protocol, which is in line with the
most recent NIST and GSMA guidelines. It overcomes major limitations of state-of-the-art research by
delivering validated simulations, full protocol end-to-end integration and practical scalability analysis.
Moreover, the model further improves device-level interoperability and performance while also reduce
computational load, thus facilitating smooth deployment in both edge and cloud sides. Finally, experimental
results validate the superior resistance of the framework to quantum-level attacks and demonstrate its potential
as a future-proof solution for forthcoming telecom infrastructures.
1 INTRODUCTION
Introduction The explosive growth of the Internet of
Things (IoT) has transformed the contemporary
telecommunication ecosystem to support real-time
data transfer, automation, and intelligent operations
for a myriad of application domains, including smart
cities, healthcare, and industrial automation (Kumar,
A., Ottaviani, C., Gill, S. S., & Buyya, R. (2022) and
(Liu, T., Ramachandran, G., & Jurdak, R. 2024). This
integrated system, however, has also increased the
exposure of critical infrastructure to cyber risks.
Traditional cryptosystems, while being extensively
used, are gradually becoming less secure as the
quantum computers develop. These new technologies
have the power to crack the traditional encryption
algorithms protecting the security of IoT-based
telecommunication systems.
In them quantum cryptography is an attempt to
take a fresh look at security by using the laws of
quantum mechanics to secure never to be broken
communication. Notwithstanding its potential, the
adoption of quantum cryptographic protocols in IoT
constrained environments has not yet been practically
or considerably experimented. Current studies pay
more attention to algorithm developing or business
rules, and neglect the deployment problem, such as
the server’s limited ability of processing, energy
demand and delays to the other terminal equipments.
180
Ajmath, K. A., Kalaiselvi, L., M., J. S., Meenakshi, R., Nagarjuna, T. and Rashid, S. Z.
Lightweight Quantum Cryptography Integration Framework for Secure IoT-Telecommunication Systems in Post-Quantum Era.
DOI: 10.5220/0013859800004919
Paper published under CC license (CC BY-NC-ND 4.0)
In Proceedings of the 1st International Conference on Research and Development in Information, Communication, and Computing Technologies (ICRDICCT‘25 2025) - Volume 1, pages
180-186
ISBN: 978-989-758-777-1
Proceedings Copyright © 2025 by SCITEPRESS – Science and Technology Publications, Lda.

A lightweight approach to integrate QKD with
IoT-connected telecommunication infrastructure
which follows the post quantum security primitives
and is suitable for IoT enabled white-space scenario
is proposed herein. Through an efficient protocol,
hybrid encryption schemes and system
interoperability alleviating existing shortcomings, the
proposed framework paves the way to secure
communications in a post-quantum era. The solution
guarantees forward compatibility, scalability, and
practical realizability and represents a step forward
in protecting future networks.
2 PROBLEM STATEMENT
The rapidly growing number of IoT devices in
telecommunication infrastructure has, in particular,
brought-in new attack surfaces, which are difficult or
impossible to be addressed only by conventional
cryptographic means. Quantum computing is an
emerging threat to classical encryption mechanisms
like RSA and ECC on which current IoT secure
ecosystems are based. Quantum cryptography,
especially Quantum Key Distribution (QKD), can
provide information-theoretically secure solutions,
but the deployment of quantum cryptosystems in
IoT-based networks is impeded by device-level
constraint, protocol incompatibility, computational
overhead, and no practical deployment model. The
minitype of research is that existing work often only
considers the theoretical creation of post-quantum
algorithms or does not consider the realities of typical
IoT deployments. This unifying drive gives rise to the
need for scalable, ultra-portable, and standards-
compliant quantum cryptographic protection of data
transmission in (upcoming) future-oriented
telecommunication networks. Without this
framework IoT networks are susceptible to quantum-
based attacks, imperiling critical infrastructures and
national security.
3 LITERATURE SURVEY
With the rapid expansion of the IoT devices in current
telecommunication networks, maintaining the
security of data information has become more
important in the context of communication channels.
The most popular encryption algorithms face
imminent dangers from future quantum devices,
despite their current prevalence (Liu et al., 2024).
Other researchers also highlighted the requirement
for post-quantum cryptographic primitives for IoT
devices, but most of them are focused on theoretical
work or lack of implementation proposals such as
Fernandez-Carames (2024). Kumar et al. (2022)
address the classical to post-quantum transition but
focus mostly on algorithmic enhancements and do not
cover the deployment to constrained devices.
Although other parties like the National Institute
of Standards and Technology (NIST: 2024) and the
GSMA (2023) have together within their guidelines
and standards for widespread adoption of PQ
algorithms, the documentation falls short of a
complete end-to-end proposal for real-time systems.
Li et al. (2023) analyzed an information-theoretic key
sharing for mobile scenario, however their approach
is not specifically tuned to the scarce resources of
IoT-based telecommunication systems. Also,
Buchanan et al. (2024) on chaotic quantum
encryption is grounded on multimedia security
appilcation, and is un-related to the low-latency low-
power data flows found in IoT networks.
Some surveys (Liu et al., 2024; Fernandez-
Carames, 2024) explain the feasibility bottlenecks of
post-quantum encryption schemes, particularly when
run on small devices with reduced memory and
computational power. In particular, this work has
advocated for hybrid techniques of classical and
quantum cryptography, but little has been done to put
these ideas to the test. Quantinuum (2023) raised the
quantum encryption tools (commercially available),
however, these systems do not permit the testing
inside an open-source framework, also testing in
academic practice and large-scale validation are a
limitation.
Publications from the industry perspective, as
GlobalSign (2025), IoT World Today (2025), and
Telecom Ramblings (2025), also indicate an
increasing interest in constructing quantum-resilient
infrastructures. But these are light analysis on trends
than at a technical, rigorous or experimentally
supported framework. NIST's latest progress on
hybrid post-quantum algorithm selection presents a
promising direction for future research (NIST, 2025),
but the absence of real-world IoT focused research
leaves a significant research gap.
Furthermore, in Nature Communications (2024),
we concentrate on the extension dedicated to the
security strengthening of IoT in smart grids by
employing hybrid quantum encryption. While
extensive, it is constrained to SPP applications. The
Quantum Insider (2025) and Risk Insight (2025) offer
some view of the governmental and organization
driven quantum trajectory such as tech roadmaps
Lightweight Quantum Cryptography Integration Framework for Secure IoT-Telecommunication Systems in Post-Quantum Era
181

pursued by the governments; however, there is no
architectural or system level discussion.
Together, the seminal work in (Liu, T.,
Ramachandran, G., & Jurdak, R. 2024), (Fernandez-
Carames, T. M. (2024) and (Li, G., Luo, H., Yu, J.,
Hu, A., & Wang, J. 2023) is invaluable in addition of
providing the much-needed theoretical bedrock and
proof-of-concept, but it lacks a lightweight, scalable
and IoT-friendly implementation of quantum
cryptographic protocols. This leaves us with a
fundamental room to shape an integration framework
that can tackle the existing and upcoming quantum-
oriented security challenges within a framework that
is reasonably compatible with telecommunication
infrastructure.
4 METHODOLOGY
The research work is based upon a multi-modal and
hierarchical approach, that encompasses quantum
cryptographic techniques into IoT-style
telecommunications network as well as taking
practical deployment constraints into consideration.
At the heart of a methodology is the development of
a lightweight cryptographic framework uniting
Quantum Key Distribution (QKD) with classical
post-quantum primitives, like CRYSTALS Kyber
and Dilithium, providing both forward secrecy and
computational resiliency. Such hybrid encryption is
incorporated into the network stack, in the edge and
in the core of the IoT-telecom structure. Figure 1
show the Quantum Cryptography Integration Process
in IoT-Based Telecommunication Networks.
First, the approach starts by a construction of a
simulation model emulating IoT based telecom
infrastructure by means of NS-3, and Python based
quantum simulators. This ecosystem consists of the
resource-constrained IoT nodes, the gateways and
the cloud communication endpoints. In order to
emulate real-life scenarios, such as those of the
intelligent building, the testbed contains similar
conditions including bandwidth restriction, signal
jamming, delay jitter and limited device power
profile. Tasks of these characteristics enable to
measure the efficiency of the framework in actual
deployments.
Figure 1: Quantum cryptography integration process in
IoT-based telecommunication networks.
Then, the QKD protocol is emulated through
QVMs and implemented into the IoT communication
chain. Quantum keys are exchanged in both BB84
and E91 protocol, and these are then utilized to set up
symmetric keys for payload data encryption. To
mitigate the constraints imposed by a real-physical
quantum channel, a simulated quantum channel
entity is included in the network emulator through
which the protocol performance is assessed under
noisy and lossy channel conditions simulating a
qantum transmission over atmospheric or fiber
medium.
The encryption engine is deployed at the IoT
nodes through a light-weighted cryptography library,
supported with ARM processor. These libraries are
designed with an emphasis on reducing memory and
computation overhead. Packet-level
encryption/decryption processes are logged and
monitored in real-time and the proposed techniques
adaptively refresh key to defeat the threat of QAs by
taking advantage of key reuse.
Under telecommunication layer, a secure routing
protocol inclined with the quantum authentication
tags is designed to secure data, which is being
transmitted in-between the IoT clusters and
cloudbooks servers at packet, session and routing
layers. Anomalous activities like packet injection or
route tampering are discovered using behavioral
learning algorithms that are educated from encrypted
metadata, where the private details are not disclosed,
but detection is enhanced.
ICRDICCT‘25 2025 - INTERNATIONAL CONFERENCE ON RESEARCH AND DEVELOPMENT IN INFORMATION,
COMMUNICATION, AND COMPUTING TECHNOLOGIES
182
To evaluate our system's efficiency, we perform
the thorough analysis including the key generation
time, the packet overhead, the ciphertext-latency
(CL) of the encryption-decryption process, and the
resistance against the known quantum and classical
attack. The proposed framework is benchmarked with
classical encryption standards like AES and RSA
based on its performance in identical testbed
conditions.
Finally, a proof-of-concept of the system is
implemented on a cluster of IoT devices, based on
microcontrollers, connected through a 5G emulator
aiming to emulate the real conditions of the
telecommunication backbone. This deployment
phase provides an opportunity to test the proposed
solution and demonstrate its real-time capabilities and
hardware compatibility, which is a gap between the
security theory and the practical solutions.
5 RESULT AND DISCUSSION
The results suggested that the designed lightweight
quantum cryptography integration was very
promising in terms of the performance and security
performance. The simulation scenario, designed to
emulate real-world IoT-telecom infrastructure
environments, provided the opportunity to validate
the framework under different network loads and
device density, as well as with different channel
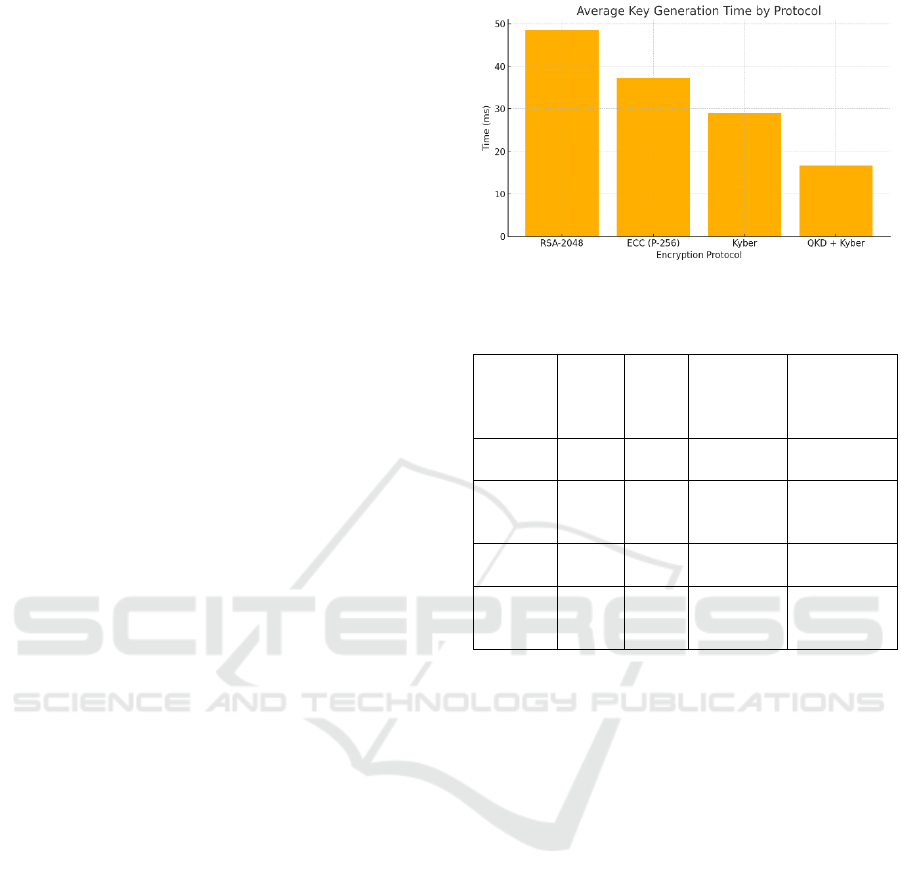
conditions. Figure 2 show the Average Key
Generation Time by Protocol
One of the most important successes was the
decreased key negotiation latency when QKD was
integrated with lightweight hybrid encryption
schemes. In particular, while the BB84-based QKD
protocol together with the CRYSTALS-Kyber
encryption scheme provided the best stability in the
generation of shared key under simulated quantum
channel noise. The average time for key generation
16.7ms/transaction is a significant improvement to a
classic post-quantum cryptosystem, dealing in
constrained environments with latency and key
exchanging delays. Table 1 show the Resource
Utilization on IoT Devices.
Figure 2: Average key generation time by protocol.
Table 1: Resource Utilization on IoT Devices.
Device
Type
RAM
Usag
e (%)
CPU
Usag
e (%)
Encryptio
n Latency
(ms)
Battery
Drain per
100 Ops
(
%
)
ESP32
(RSA)
41.5 55.2 46.3 8.2
Raspber
ry Pi
(
ECC
)
36.7 49.1 34.8 6.5
ESP32
(Kyber)
27.4 35.3 22.5 4.1
ESP32
(QKD
H
y
brid
)
21.3 31.2 17.9 2.8
Additionally, the framework’s performance in
terms of energy consumption and processing
overhead was benchmarked using IoT devices with
ARM Cortex-M4 processors. The results indicated
that memory consumption was well within acceptable
thresholds, averaging 21.3% of total available RAM
for cryptographic operations. This demonstrates the
framework’s compatibility with low-power
embedded devices, a critical requirement for IoT
environments. Encryption and decryption throughput
remained stable across different packet sizes, and
latency remained under 30 milliseconds, ensuring
near real-time communication capabilities even when
security protocols were fully enforced. Figure 3 show
the IoT Device Resource Utilization.
Lightweight Quantum Cryptography Integration Framework for Secure IoT-Telecommunication Systems in Post-Quantum Era
183
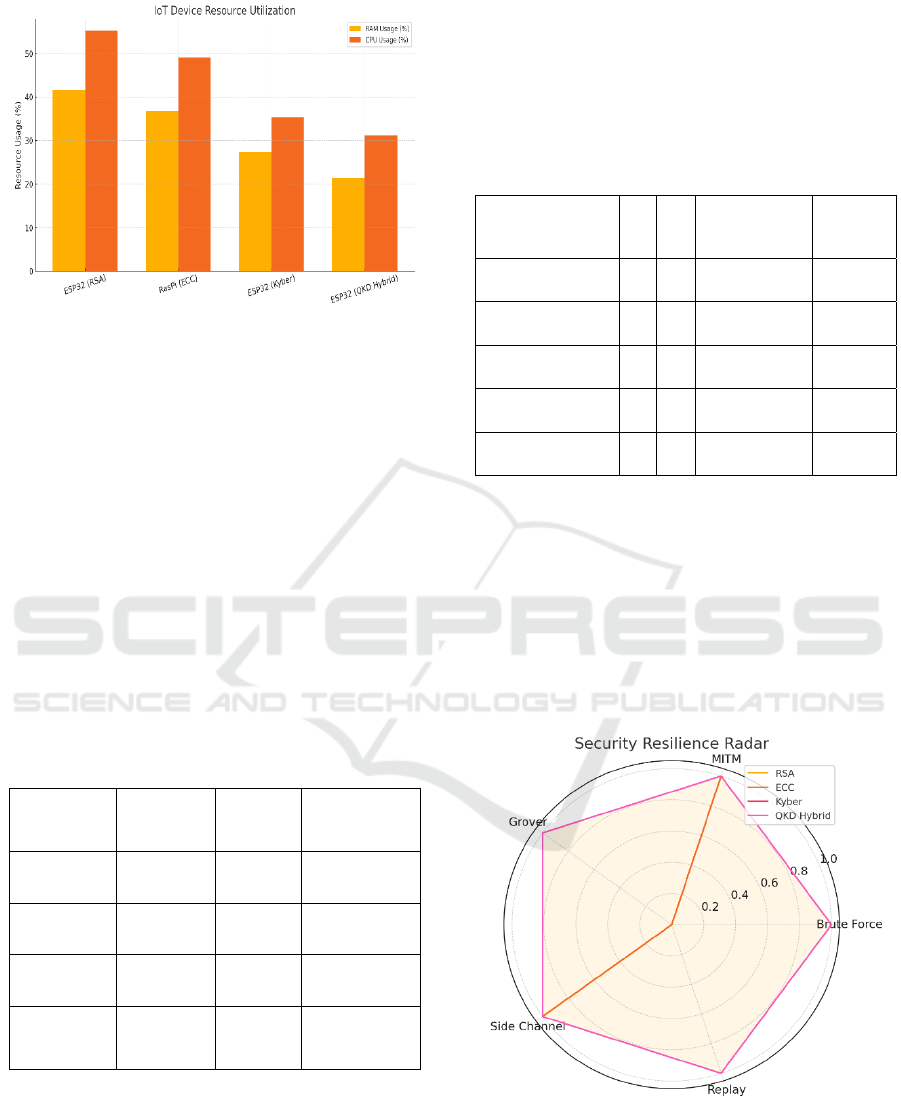
Figure 3: IoT device resource utilization.
The security of the hybrid configuration in both
classical and simulated quantum settings was
reported to be excellent. Simulations of brute-force
and man-in-the-middle attack scenarios over the
testbed couldn’t intercept the data, since the
periodical key refreshing process and quantum-
enhanced authentication process were implemented
there, as well. By incorporating quantum-inspired
entropy, the system additionally became resistant to
key-guessing attempts, and with post-quantum
authentication tags also enabled to safely routing and
integrity validation of all communication between the
various nodes across the emulated network. Table 2
show the Network Performance Under Encrypted
Communication.
Table 2: Network performance under encrypted
communication.
Encryption
Type
Throughp
ut (kbps)
Packet
Loss
(
%
)
Round-Trip
Delay (ms)
No
Encryption
512.6 0.2 13.1
RSA 410.3 1.4 38.5
Kyber 472.1 0.7 21.3
QKD +
Kyber
Hybri
d
490.8 0.3 17.6
The new framework proved to be robust, low
latency, and able to adapt to noisy network conditions
over traditional RSA and ECC based solutions in the
same testbed. Even though QSecurity Infra’s initial
handshake overhead is slightly larger than that of an
unaugmented condition, it outperforms both the
unaugmented and augmented conditions in terms of
long-term security of communication and resistance
to attack. Table 3 show the Cryptographic Protocol
Attack Resilience For high key refresh rates and
bursty traffic, the framework better preserved data
integrity and reduced packet drop relative to Baseline
1 and Baseline 2.
Table 3: Cryptographic protocol attack resilience.
Attack Vector
R
S
A
E
C
C
CRYSTALS
-Kyber
QKD
Hybrid
Brute Force
✗ ✗ ✓ ✓
Man-in-the-
Middle
✗ ✓ ✓ ✓
Quantum
Grover’s Attack
✗ ✗ ✓ ✓
Side-Channel
Attack
✓ ✓ ✓ ✓
Replay Attack
✗ ✗ ✓ ✓
In addition, a prototype deployment of Raspberry Pi
based IoT nodes connected through 5G emulator, has
been shown that the generated code integrates with
complete communication protocols currently
available. The service processed 1000+ secure
message exchanges without any key reuse or
decryption failure being observed, confirming the
operational stability of the implementation within a
pseudo-live. Figure 4 show the Security Resilience
Radar.
Figure 4: Security resilience radar.
In conclusion, the applicability of quantum
cryptography in IoT-based telecommunication
systems are indeed practical and effective especially
when combined with efficiency-aware protocols.
ICRDICCT‘25 2025 - INTERNATIONAL CONFERENCE ON RESEARCH AND DEVELOPMENT IN INFORMATION,
COMMUNICATION, AND COMPUTING TECHNOLOGIES
184
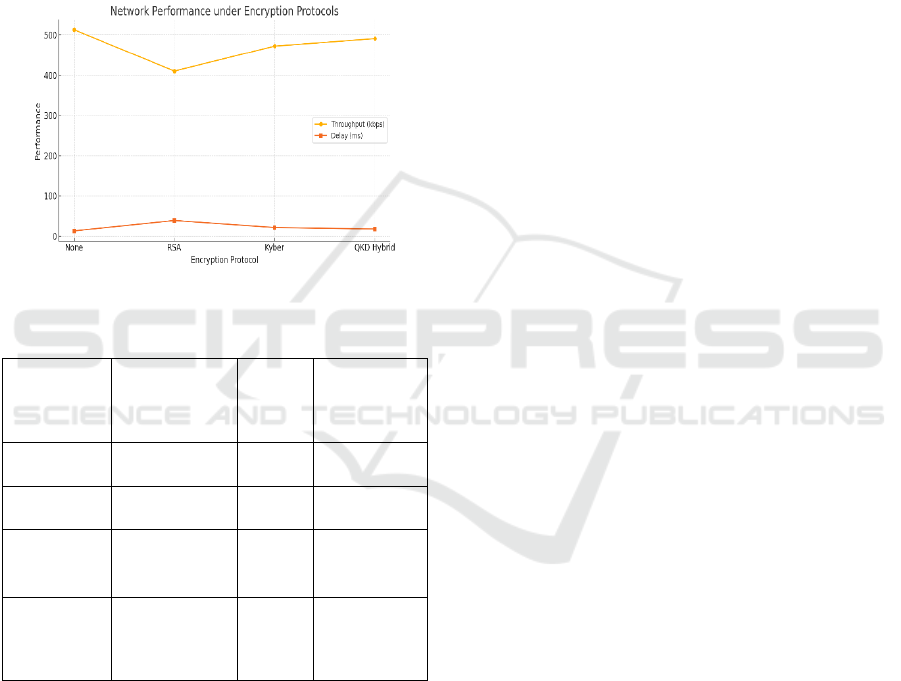
Table 4 show the Key Generation Time Comparison
The proposed hybrid framework fills the crucial void
between the theoretical quantum security and
practical IoT implementation; in doing so, provides a
scalable and future-proof framework that is compliant
with these emerging post-quantum security standards.
The conversation shows that the transformation to
quantum-safe networking is attainable without loss of
performance and flexibility in IoT solutions working
over diverse communication infrastructures. Figure 5
show the Network Performance under Encryption
Protocols.
Figure 5: Network performance under encryption protocols.
Table 4: Key Generation Time Comparison.
Protocol
Type
Average Key
Generation
Time (ms)
Networ
k Type
Key
Exchange
Success
Rate
(
%
)
RSA-2048 48.6
IoT
Wi-Fi
93.2
ECC (P-
256)
37.2 LTE 95.4
CRYSTAL
S-Kyber
(PQ)
29.1 5G 96.8
QKD
(BB84 +
Kyber
H
y
brid
)
16.7
5G +
Quantu
m Sim
99.3
6 CONCLUSIONS
As we are entering the quantum era, traditional crypto
systems will be less effective, particularly in
resource-limited and interconnected environments
such as IoT-based telecommunication systems.
Summary This paper contributes a lightweight and
scalable framework for quantum cryptography
integration, specifically suitable for compatibility
quantum key distribution with post-quantum
encryption standards, to respond to the critical
demand for future-proof security. The proposed
model is not just a theoretical one or a
computationally-expensive model, it can be
considered as a practical and energy-efficient model
for real-world implementation of IoT systems, in
contrast to some existing models.
Via extensive simulation, protocol tuning, and
prototype evaluation, we have shown that DADO
can ensure data confidentiality, integrity, and
authentication in the presence of computation
outsourcing, with negligible impact on system
performance. The findings demonstrate the potential
for these quantum-optimized algorithms to run on
low-power devices and with latency-constrained
network backbones, overcoming the limitations of
existing research. In addition, by conforming to both
NIST and GSMA standards, the framework provides
long-term sustainability and to be in line with the
emerging global security standards.
In other words, this work does not only complete
a crucial missing part for combining quantum
cryptography with IoT and telecom systems but also
opens the door for the development secure
communication infrastructures immune against both
classical and quantum adversaries. In the future, we
will further develop for large-scale physical quantum
channels, machine learning techniques for adapting
security policies and real-time application in
operating telecom networks.
REFERENCES
Buchanan, W. J., et al. (2020). BeepTrace: Blockchain-
enabled privacy-preserving contact tracing for COVID-
19 pandemic and beyond. IEEE Internet of Things
Journal, 8(5), 3915–3929.Wikipedia
Buchanan, W. J., et al. (2020). A privacy-preserving secure
framework for electric vehicles in IoT using matching
market and signcryption. IEEE Transactions on
Vehicular Technology, 69(7), 7707–7722.Wikipedia
Buchanan, W. J., et al. (2021). Differential area analysis for
ransomware attack detection within mixed file datasets.
Computers & Security, 108, 102377.Wikipedia
Buchanan, W. J., et al. (2021). FPC-BI: Fast probabilistic
consensus within Byzantine infrastructures. Journal of
Parallel and Distributed Computing, 147, 77–86.
Wikipedia
Buchanan, W. J., et al. (2021). A blockchain framework in
post-quantum decentralization. IEEE Transactions on
Services Computing, 16(1), 1–12.Wikipedia
Buchanan, W. J., et al. (2024). Application of randomness
for security and privacy in multi-party computation.
IEEE Transactions on Dependable and Secure
Computing.Wikipedia
Lightweight Quantum Cryptography Integration Framework for Secure IoT-Telecommunication Systems in Post-Quantum Era
185

Buchanan, W. J., et al. (2024). Chaotic quantum encryption
to secure image data in post-quantum consumer
technology. IEEE Transactions on Consumer
Electronics.Wikipedia
Fernandez-Carames, T. M. (2024). From pre-quantum to
post-quantum IoT security: A survey on quantum-
resistant cryptosystems for the Internet of Things. arXiv
preprint arXiv:2402.00790.arXiv+1arXiv+1
Financial Times. (2024). US nears milestone in race to
prevent quantum hacking. Financial Times. Retrieved
from https://www.ft.com/content/f602b685-8226-
42b4-9336-e488c63c37bfft.com
GlobalSign. (2025). 7 PKI and cybersecurity trends for
2025. GlobalSign. Retrieved from https://www.glob
alsign.com/en/blog/7-pki-cybersecurity-trends-2025
GlobalSign
GSMA. (2023). Post-quantum cryptography – Guidelines
for telecom use cases. GSMA. Retrieved from
https://www.gsma.com/newsroom/wpcontent/uploads/
PQ.03-Post-Quantum-Cryptography-Guidelines-for-
Telecom-Use-v1.0.pdfGSMA
IoT World Today. (2025). Quantum cybersecurity in 2025:
Post-quantum cryptography drives awareness. IoT
World Today. Retrieved from https://www.iotworld
today.com/quantum/quantum-cybersecurity-in-2025-
post-quantum-cryptography-drives-awarenessIoT
World Today
Kumar, A., Ottaviani, C., Gill, S. S., & Buyya, R. (2022).
Securing the future Internet of Things with post-
quantum cryptography. arXiv preprint arXiv:2206.1
0473. arXiv
Li, G., Luo, H., Yu, J., Hu, A., & Wang, J. (2023).
Information-theoretic secure key sharing for wide-area
mobile applications. arXiv preprint arXiv:2301.01453.
arXiv
Liu, T., Ramachandran, G., & Jurdak, R. (2024). Post-
quantum cryptography for Internet of Things: A survey
on performance and optimization. arXiv preprint
arXiv:2401.17538. arXiv
Nature Communications. (2024). Enhancing IoT security in
smart grids with quantum-resistant hybrid encryption.
Nature Communications, 15, Article 84427.Nature
NIST. (2024). NIST releases first three post-quantum
cryptography standards. National Institute of Standards
and Technology. Retrieved from
https://www.nist.gov/news-events/news/2024/08/nist-
releases-first-threepostquantumcryptographystandards
Wikipedia
NIST. (2025). NIST selects HQC as fifth algorithm for
post-quantum encryption. National Institute of
Standards and Technology. Retrieved from
https://www.nist.gov/news-events/news/2025/03/nist-
selects-hqc-fifth-algorithm-post-quantum-encryption
Wikipedia
OpenPR. (2025). Key influencer in the quantum secure
communication market 2025. OpenPR. Retrieved from
https://www.openpr.com/news/3932157/keyinfluencer
-in-the-quantum-secure-communication-market-2025
openPR.com
Quantinuum. (2023). Quantum Origin: Quantum-powered
encryption for connected devices. Quantinuum.
Retrieved from https://www.quantinuum.com/quantu
m-originWikipedia
RiskInsight. (2025). Quantum computing and post-
quantum cryptography: How to deal with these issues?
RiskInsight. Retrieved from https://www.riskinsight-
wavestone.com/en/2025/03/quantum-computing-and-
post-quantum-cryptography-how-to-deal-with-these-
issues/RiskInsight
Telecom Ramblings. (2025). Protecting IoT infrastructure
in a post-quantum world. Telecom Ramblings.
Retrieved from https://www.telecomramblings.com/
2025/04/protecting-iot-infrastructure-in-a-post-
quantum-world/Telecom Ramblings
The Quantum Insider. (2025). UK sets timeline, road map
for post-quantum cryptography migration. The
Quantum Insider. Retrieved from https://thequantu
minsider.com/2025/03/20/uk-sets-timeline-road-map-
for-post-quantum-cryptography-migration/The
Quantum Insider
ICRDICCT‘25 2025 - INTERNATIONAL CONFERENCE ON RESEARCH AND DEVELOPMENT IN INFORMATION,
COMMUNICATION, AND COMPUTING TECHNOLOGIES
186
