
Improving Cybersecurity for Smart Home Systems
Tauheed Waheed
a
, Eda Marchetti
b
and Antonello Calabr
`
o
c
CNR-ISTI Pisa, Italy
Keywords:
Cybersecurity, Smart Home Systems, Testing, User-Centric.
Abstract:
Smart home systems consist of various interconnected devices that can be vulnerable to security risks, poten-
tially compromising the integrity of the entire system. This paper aims to address cybersecurity challenges and
identify research gaps to enhance cybersecurity for smart home systems. We aim to highlight the significance
and impact of testing on smart home systems, with a focus on the drawbacks of current testing strategies. The
limitations in current testing methodologies have identified the lack of user involvement in the testing process.
We have proposed our user-centric SCTM (Smart-home Cybersecurity Testing Methodology) and its behav-
ioral model to leverage cybersecurity in smart home systems.
1 INTRODUCTION
IoT is revolutionizing our everyday lives by allow-
ing the easy use of a wide range of smart devices
to improve our lifestyle, convenience, efficiency,
and safety. It has been evident that people’s and
users’ perspectives on technology would be drasti-
cally changed (ElArwady et al., 2024). For instance,
remote monitoring tools and telehealth platforms en-
able continual tracking of patients’ vital signs and
health metrics from the comfort of their homes, em-
power healthcare providers to make informed deci-
sions based on up-to-date information, and improve
the quality of care delivered to patients, particularly
those with chronic conditions. GPS systems can sug-
gest the quickest routes based on real-time traffic con-
gestion, contributing to the reduction of travel times
and fuel consumption, leading to both financial sav-
ings and a smaller carbon footprint.
Considering in particular Smart Home systems,
advanced sensors and automated controls, can auto-
matically manage lighting levels and temperature ac-
cording to preferences and routines for an optimal
living environment (Zhou et al., 2022). Addition-
ally, their interaction with different devices (smart-
watches, mobile phones, and tablets) can leverage the
user experience by providing full control and tracking
of what is going on.
a
https://orcid.org/0009-0006-0489-7697
b
https://orcid.org/0000-0003-4223-8036
c
https://orcid.org/0000-0001-5502-303X
However, despite the benefits, IoT brings signif-
icant concerns about data privacy and cybersecurity
due to the vast amounts of personal data collected
and transmitted across networks. For instance, users’
names, dates of birth, addresses, and credit card num-
bers can be typical examples of shared data among
the Smart home sensors. They could be used for pro-
filing the individuals’ interactions and behavior, with
a consequent privacy risk. Therefore, the use of ro-
bust security protocols for protecting against potential
threats and ensuring that the adoption of IoT remains
safe, secure, and effective is mandatory.
In this process, a crucial point is the level of trust-
worthiness guaranteed by the IoT device producers.
Indeed, to reduce production costs and time, many
devices are shipped without secure configurations by
default and with important vulnerabilities. More-
over, given their embedded nature, these devices fre-
quently lack regular security updates and patches af-
ter deployment. Hackers and intruders can take ad-
vantage of these vulnerabilities, potentially leading to
significant financial losses that could amount to mil-
lions of dollars. Furthermore, security breaches can
severely damage companies’ customer relationships,
ultimately eroding trust and harming brand reputa-
tion.
To mitigate these risks, this paper investigates
the main cybersecurity challenges and solutions that
can be considered to ensure robust security proto-
cols and stringent compliance governance across all
touchpoints associated with IoT devices (Sharma and
Jindal, 2024). Specific attention will also be de-
220
Waheed, T., Marchetti, E. and Calabrò, A.
Improving Cybersecurity for Smart Home Systems.
DOI: 10.5220/0013783700003985
Paper published under CC license (CC BY-NC-ND 4.0)
In Proceedings of the 21st International Conference on Web Information Systems and Technologies (WEBIST 2025), pages 220-227
ISBN: 978-989-758-772-6; ISSN: 2184-3252
Proceedings Copyright © 2025 by SCITEPRESS – Science and Technology Publications, Lda.

voted to cybersecurity countermeasures by proposing
a testing methodology designed for smart home de-
vice producers useful for improving their trustworthi-
ness. By integrating perspectives from IoT special-
ists, testers, cybersecurity experts, and cognitive psy-
chologists, the proposed testing platform combines
technical cybersecurity evaluations, thereby promot-
ing a comprehensive understanding of trustworthiness
in smart home systems.
In its exploration, the paper overviews the follow-
ing research questions (RQs):
RQ 1: Why is cybersecurity testing critical for
smart home systems? We specifically investigate
the consequences of insufficient testing processes
for smart home systems and the potential mitiga-
tion techniques or countermeasures that can create
awareness for the smart home industry to incul-
cate cybersecurity testing.
RQ 2: What are the current solutions for main-
taining smart home cybersecurity level? In
particular, we evaluate and scrutinize the current
solutions and their effectiveness in maintaining
cybersecurity quality and standards. It focuses
on comprehending the robustness and security of
the recent IoT devices and third-party software
trusted by manufacturers, customers, and organi-
zations to integrate their smart home systems.
RQ 3: What are the main research gaps? We ex-
amine existing research trends in cybersecurity for
smart home systems to identify critical gaps and
ensure the creation of a secure, reliable, and sus-
tainable platform that adheres to legal, social, in-
clusive, and ethical benchmarks.
RQ 4: Which could be a possible solutions? We
provide a robust testing methodology and frame-
work for smart home users/industry to en-
hance cybersecurity quality and trustworthiness in
broader perspectives.
Considering the paper structure, in Section 2, cur-
rent cybersecurity challenges, testing strategies, and
available solutions are presented. In Section 3, the
main research gaps are discussed, and the role of cy-
bersecurity testing is presented. The proposed testing
methodology is depicted in Section 4, while in Sec-
tion 5, the testing platform components are schema-
tized. Section 6 includes the conclusion and future
work.
2 RELATED WORK
To address the aforementioned research questions,
we conducted a rapid review of the literature, focus-
ing on the main databases and using the following
generic query: "(Cybersecurity AND ( Testing
AND IoT AND ( Smart-home AND Systems )"
The query was used for searching by title, ab-
stract, and keywords on English papers from 2020
to 2025 and executed over the following electronic
sources: Scopus
1
, ACM Digital Library
2
, IEEE eX-
plore
3
, SpringerLink
4
. The execution provided an ini-
tial merged collection of 335 papers (excluding dupli-
cation) distributed as: ACM Digital Library - 110 pa-
pers; IEEE eXplore - 83 papers; SpringerLink - 155
papers; Scopus - 14 papers.
By reading their title, abstract, and keywords the 8
papers reported in Table 1 have been selected accord-
ing to the following stringent criteria:
• Exclude papers that do not specifically concen-
trate on paper topics;
• Exclude papers that provide state-of-the-art re-
views or surveys;
• Exclude papers that do not qualify as original or
comprehensive research publications, such as for-
wards, editorials, monographs, books, and contri-
butions that are not peer-reviewed or are too brief;
• Exclude short and poor-quality papers, such as
those with unclear objectives or focused solutions.
Each paper provides specific considerations, such
as scope, contribution, limitations, and testing strat-
egy, as reported in the following and Table 1.
(Piasecki et al., 2021): Smart home cybersecu-
rity standards are based on cloud-based architectures,
which is a shortcoming in their longevity. Edge com-
puting approaches like the Databox can provide ad-
vantages for security, privacy and legal compliance
over cloud-based approaches. However, the current
cybersecurity standards do not consider internal hu-
man threats within smart homes, such as domestic
abuse and social surveillance.
(Aldahmani et al., 2023): The researchers clas-
sify the attacks into three layers (perception, net-
work, and application) and countermeasures and se-
curity solutions have been considered for each of
them. Recommended security solutions includes se-
cure firmware updates, multi-factor authentication,
and next-generation firewalls, to protect IoT devices,
networks, and applications against cyber-attacks.
(Heiding et al., 2023): The researchers discov-
ered 17 new vulnerabilities in 22 connected house-
hold devices, some of which were recognized as crit-
ical by the National Vulnerability Database (NVD).
1
http://www.scopus.com
2
http://dl.acm.org
3
http://ieeexplore.ieee.org
4
https://link.springer.com
Improving Cybersecurity for Smart Home Systems
221
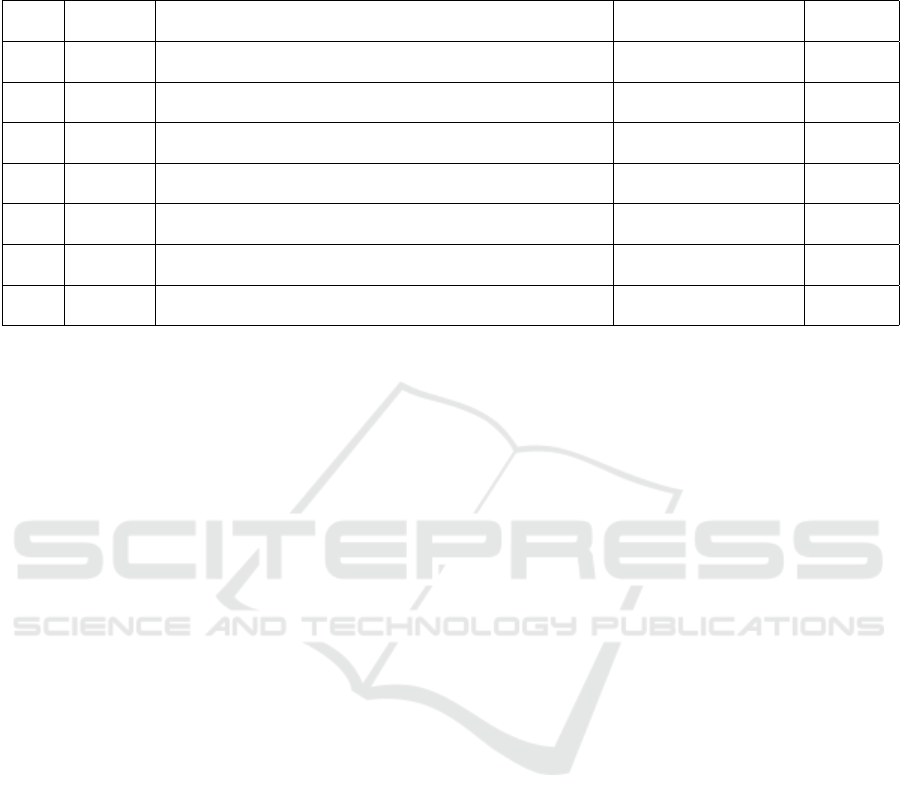
Table 1: Rapid Review.
P.Year Scope
Contribution Limitation
Testing
Strategy
2024 Network
Designed a network intrusion detection system (IDS).
Excessive time
for training algorithm
Confusion
Matrix
2023 Educational
Shaping smart-home users’ attitudes toward cybersecurity awareness training. User-centricity
Not
specified
2023 Testing
Identified vulnerabilities may result in serious repercussions for residents,
including the risk of an attacker obtaining physical access to the home.
Difference in expertise
of student testers
Penetration
Testing
2023 Security
Recommended to inculcate next generation firewalls to protect embeded IoTs
in smart home systems.
Methodology
Testing Platform
Not
Specified
2021 Hardware
Provided technique to improve sensor identity protection for
smart home systems.
Benchmark value is not
determined for home settings.
Not
specified
2021 Educational
Evaluating Denial of Service (DoS) and Man in the Middle (MiM)
cyber-attacks for smart home systems.
Focusing on just particular
IoT devices under attack.
Performance
Testing
2021 Safety
Provided methodology to automatically track the location and
movement of elderly people.
No sensors
for monitoring oxygen level.
Machine
Learning
2021 Security
Explores current smart home cybercrimes and cybersecurity standards.
Not focusing on
internal human threats.
Not
specified
However, the tested devices are already being sold
and used worldwide, with the risk that an attacker
could gain physical access to the house. Future ac-
tions to improve the security infrastructure of house-
hold IoT are necessary.
(Chen, 2021): The researchers proposed a home
monitoring system that uses beacon technology to
track the location and movement of elderly residents
automatically and can detect potential safety issues.
The system uses federated learning to enhance the
object recognition capabilities of the faster R-CNN
model while protecting user privacy by keeping per-
sonal data on a local server.
(Abdusalomov et al., 2024):The researchers pro-
posed a network intrusion detection system (IDS) de-
signed mainly for IoT-enabled smart home systems,
featuring a deployment strategy that compensates for
a wide range of network security challenges.
(Douha et al., 2023): The researchers investi-
gated how cultural differences can impact smart-
home users’ interest in and satisfaction with non-
financial rewards for cybersecurity behaviors between
British and Japanese smart-home users. They claim
that cybersecurity awareness training and the scope
of training programs should be according to the target
audience’s cultural and socioeconomic backgrounds.
(Trabelsi, 2021): The researchers investigated the
impact of hands-on lab exercises on vulnerability is-
sues. They concluded that, despite positive student
feedback, the students did not feel adequately pre-
pared to assess vulnerabilities in IoT devices other
than those used in the lab. Indeed, the exercises failed
to cover a broader range of IoT devices and attack
types, limiting the comprehensiveness of the IoT se-
curity education provided.
(Alshboul et al., 2021): The researchers proposed
a 3-phase technique that significantly enhanced the
protection of sensor identities in smart home area net-
works. The threshold value that defines the time inter-
val for each sensor impacted the proposed technique’s
performance
The related work demonstrates that testing frame-
works and methodologies for the cybersecurity of
smart home systems are not robust and comprehen-
sive. It is evident from Table 1 that cybersecurity for
smart home systems has been improved while consid-
ering various scopes and domains. However, testing
is the most under-utilized research domain, while fo-
cusing on generic penetration testing. Moreover, col-
laborative efforts are required to integrate testing to
address modern cybersecurity challenges (Marchetti
et al., 2024). The next section will explore research
gaps and why we need cybersecurity testing in smart
home systems.
3 RESEARCH GAPS
Diverse research gaps in smart home systems empha-
size the significance of cybersecurity testing. They
include:
Cyber-Attacks: It emphasizes the increasing
skills of cybercriminals who exploit vulnerabilities
in various interconnected devices such as smart ther-
mostats, security cameras, and voice assistants. This
situation emphasizes the need for enhanced protection
and user awareness to maintain smart home systems’
security.
Broader Attack Surface: It encompasses a range
of devices such as smart TVs, security cameras, and
smart plugs because they often operate on outdated
software versions or have inadequate security proto-
WEBIST 2025 - 21st International Conference on Web Information Systems and Technologies
222

Figure 1: Impact of Cybersecurity Testing.
cols. Consequently, the risks associated with their
rooted flaws increase, creating enticing possibilities
for hackers to exploit.
Privacy: Management of personal data, includ-
ing user needs, habits, and even sensitive informa-
tion related to security and health, makes these de-
vices vulnerable to cyber-attacks by unauthorized in-
dividuals and increases the need for robust cyberse-
curity measures. Common risks can be identity theft,
unauthorized surveillance, and potential manipula-
tion of smart home systems(Harkai, 2024). Prioritiz-
ing strong encryption, regular software updates, and
secure password practices is essential to safeguard
against these privacy challenges.
Heterogeneity: The integration of a wide range
of smart devices increases the complexity and the po-
tential points of failure within the system. Moreover,
every IoT device comprises unique specifications and
security protocols contributing to a heterogeneous en-
vironment (Tatipatri and Arun, 2024). However, this
diversity creates significant cybersecurity vulnerabil-
ities; for example, if one device is compromised due
to invalid passwords, outdated firmware, or inherent
malware, it can be a massive opportunity for cyber-
attackers to compromise the entire network, gain
unauthorized access to sensitive data, and control over
other devices. The challenge is to ensure that all de-
vices, regardless of manufacturer or connection type,
are secured and monitored to prevent such breaches.
Regulation: government and regulatory author-
ities are keen to prioritize the cybersecurity of con-
nected devices, through severe directives, standards,
and regulations such as the Radio Equipment Direc-
tive (RED) for smart home systems (Mueck et al.,
2025) or the EU Cyber Resilience Act (Car and
De Luca, 2022). Compliance with them ensures that
manufacturers implement mandatory security mea-
sures, address vulnerabilities that could compromise
device functionality, protect the integrity of smart
home devices, and gain prosumer trust.
Emerging Threats: Cyber threats frequently
evolve with a broader range of hacking strategies
and malware, raising an urgent need for cyberse-
curity testing to defend against these potential dan-
gers(Bonaventura et al., 2025). Indeed, cybersecu-
rity testing targets the discovery of weaknesses and
enhances the robustness of the system against the
modern attack strategies that cybercriminals might
utilize. Therefore, cybersecurity testing and timely
updates directly impact the safety and reliability of
smart home technologies.
The importance and need for cybersecurity testing
have been discussed in detail, and in the next section,
we discussed limitations of current strategies and pre-
sented our testing methodology and its conceptualiza-
tion.
4 TESTING METHODOLOGY
The testing methodology has been conceived while
evaluating current solutions their limitations and re-
search gaps discussed in Section 2 and Section 3. The
core of our methodology comprises four attributes:
User-Centric: The focused is on prioritizing us-
ability as a fundamental principle for fostering inno-
vative solutions that are deeply rooted in the needs
and preferences of the user (Waheed et al., 2024).
By placing the end-user at the forefront of the design
process, security measures can be more intuitive and
seamlessly integrated into the user experience. The
proposed user-centric methodology entails a thorough
reevaluation of authentication methods, emphasizing
ease of use. For instance, implementing biometric
Improving Cybersecurity for Smart Home Systems
223
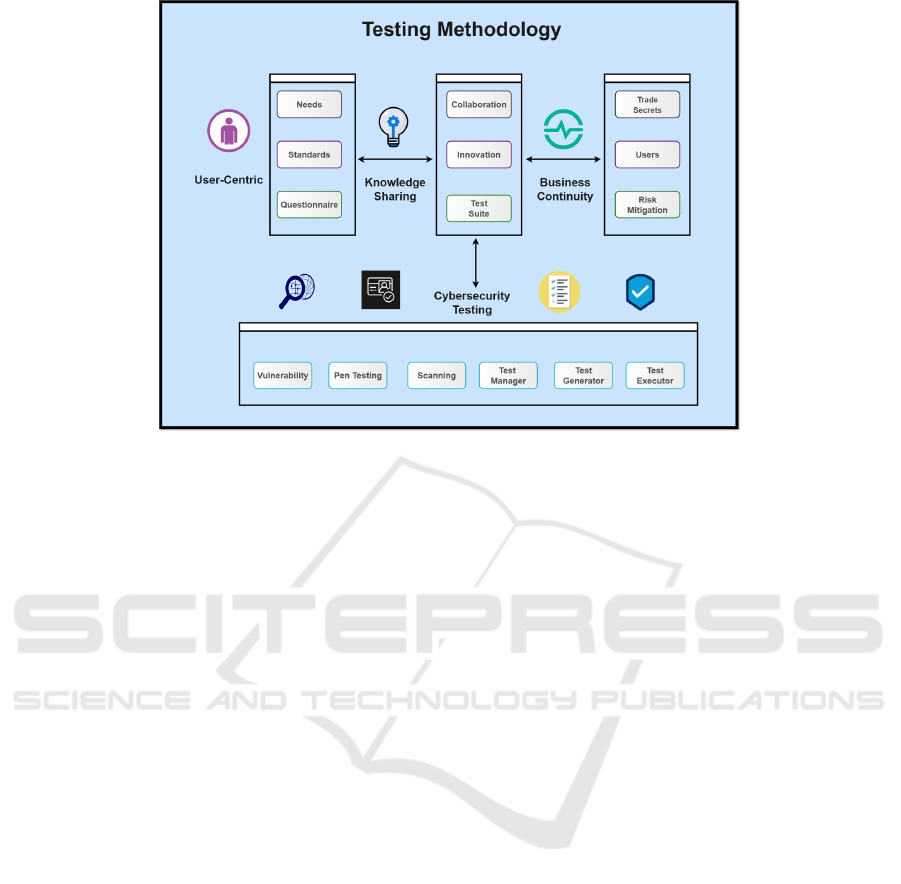
Figure 2: Testing Methodology.
authentication or multi-factor authentication options
that are customizable allows users to select the secu-
rity measures that best fit their individual needs. Ad-
ditionally, communication regarding security notifica-
tions is designed to be clear and actionable. Users re-
ceive straightforward alerts that not only inform them
of potential security issues but also guide them on
how to respond effectively, thereby reducing confu-
sion and empowering users to take control of their
security settings. Overall, this approach not only en-
hances the security framework but also significantly
improves the overall usability and satisfaction of the
users interacting with the system.
Cybersecurity Testing: This process involves
rigorous assessments such as penetration testing, vul-
nerability scanning, and threat modeling, which col-
lectively help in revealing potential security flaws
(Waheed and Marchetti, 2023). It is crucial to proac-
tively identify and rectify these weaknesses to pre-
vent exploitation by malicious actors, who are con-
stantly evolving their tactics. Implementing compre-
hensive and proactive cybersecurity strategies is es-
sential, and this includes conducting thorough testing
throughout the entire life cycle of the system from the
initial design phase to deployment and beyond. Reg-
ular and systematic evaluations not only bolster secu-
rity but also enhance overall resilience against cyber
threats, ensuring that protective measures remain ro-
bust against emerging risks.
Knowledge Sharing: Cultivating a robust culture
of knowledge sharing and open dialogue regarding
cybersecurity threats (Waheed et al., 2025) and best
practices is critical for any organization. Over the
years, valuable insights about potential threats and ef-
fective countermeasures have been meticulously gath-
ered and analyzed. These findings are then shared
with employees at all levels, as well as management,
to significantly enhance overall productivity and effi-
ciency through collaborative initiatives. Additionally,
fostering teamwork is important for strengthening the
overall security framework(Adewuyi et al., 2024). By
encouraging cross-departmental cooperation and en-
gaging with industry allies, organizations can lever-
age diverse perspectives and expertise, leading to in-
novative solutions and proactive approaches to miti-
gate risks.
Business Continuity: The resilience of an in-
dustry significantly enhances when organizations ac-
tively work to minimize downtime and mitigate the
repercussions of critical incidents. Developing a com-
prehensive business continuity plan is essential; it
should delineate specific protocols and strategies for
responding to various cyber incidents, ranging from
data breaches to ransomware attacks. Regularly up-
dating this plan is just as important, ensuring that it
reflects the latest threat landscape and incorporates
lessons learned from previous incidents. A robust
business continuity plan equips an organization to re-
bound swiftly from cyber-attacks, thereby reducing
the duration of disruptions and maintaining essen-
tial operations. By implementing preventative mea-
sures, conducting regular training sessions for em-
ployees, and establishing clear communication chan-
nels, organizations can further bolster their resilience
against cyber threats and ensure sustained operational
integrity, even in the face of adversity.
WEBIST 2025 - 21st International Conference on Web Information Systems and Technologies
224

Our holistic testing strategy strengthens defenses
against cyber threats and drives continuous improve-
ment and adaptability in IoT infastructure of smart
home systems. The following section discusses the
behavioral model of our testing methodology to lever-
age cybersecurity testing in smart home systems.
5 TESTING BEHAVIORAL
MODEL
The section describes the behavioral model and work-
flow of our testing methodology. The testing method-
ology aims to facilitate the transition from conven-
tional reactive quality control approaches to a more
proactive and collaborative model. Moreover, it can
assist businesses in optimizing their operations while
reducing cybersecurity risks, maintaining their repu-
tation, and enabling trust among users of industrial
and commercial smart home systems. Our cyberse-
curity testing framework explicitly addresses the lim-
itations of current solutions outlined in Section 4 and
suggests a testing strategy and workflow for integrat-
ing advanced technologies such as all while tackling
cybersecurity issues and enhancing quality for smart
home users.
Our proposed SCTM (Smart Home Cybersecu-
rity Testing Methodology) is a user-centric testing
environment that promotes shared responsibility to
counter modern-day cyber-attacks on smart home sys-
tems. Interestingly, Figure 3 showcases the compo-
nents and the communication flow between them.
A Test Manager (TM) collects thorough user re-
quirements to identify clear and specific testing objec-
tives. It will be accomplished through questionnaires
to clarify and align user expectations with their testing
needs. Moreover, the component manages the testing
feedback and various decisions made during the ex-
ecution of testing activities for smart home systems.
Furthermore, all user interactions will be performed
through a dedicated User Interface (UI) (TM UI) .
The Test Generator (TG) aids in managing the
generation and selection of test cases to the specific
needs and requirements of users. Based on varying
conditions, the component can suggest testing strate-
gies and assist users in choosing the most adequate
one. The test generator component will prioritize the
test cases generated to identify and mitigate potential
security vulnerabilities. Furthermore, executing these
test cases will ensure the continuous availability, con-
fidentiality, and overall cybersecurity of sensitive in-
formation in smart home systems.
The Test Executor (TE) provides testing libraries
that aid in finalizing the test cases for the user smart
home execution environment. Moreover, the exe-
cution environment can be supplied directly by the
user, inculcating specific user requirements and pref-
erences. Alternatively, it may be sourced from various
innovative open-source proposals, ensuring a well-
rounded and flexible testing strategy that accommo-
dates user needs and scenarios.
Test Controller (TC) offers a range of testing
strategies and pre-defined test cases when applica-
ble. It assists in generating questionnaires for test
managers and verifies that the test cases align with
the specified requirements. Furthermore, it utilizes
Generative AI to create robust test case instances and
widen the scope of test suites, ensuring quality stan-
dards in light of the changing cybersecurity threats en-
countered by smart home systems.
It helps comprehend the effects of vulnerabilities
and identify unnecessary pathways within the source
code of application domains, connected IoT devices
in smart home systems, and third-party libraries or
APIs (Application Programming Interface). The anal-
ysis primarily utilizes path coverage testing. Further-
more, the prominent role of this component is to eval-
uate the test results produced by SCTM and generate
reports for users through the interface of our test man-
ager.
The Test DB (Database) (AR) efficiently gathers
knowledge and results from testing activities. This
component provides essential resources to intercon-
nected platforms like GitHub and offers tools for cre-
ating structured questionnaires and datasets of pre-
defined test cases. It maintains and stores test reports
and user feeds; the component enhances future ques-
tionnaire design and improves the overall SCTM test-
ing process, facilitating continuous improvement and
more reliable results.
The SCTM testing platform is thoughtfully devel-
oped for smart home systems, specifically address-
ing the unique needs of their users. This architecture
adopts a user-centered focus in cybersecurity, allow-
ing for highly customized testing scenarios tailored to
individual requirements. These scenarios effectively
simulate a range of malicious behaviors and poten-
tial system vulnerabilities, creating a realistic envi-
ronment. This approach encourages users to iden-
tify and understand risks and empowers them to take
proactive steps to mitigate these threats, significantly
enhancing their understanding of cybersecurity regu-
lations and testing methodologies.
Improving Cybersecurity for Smart Home Systems
225
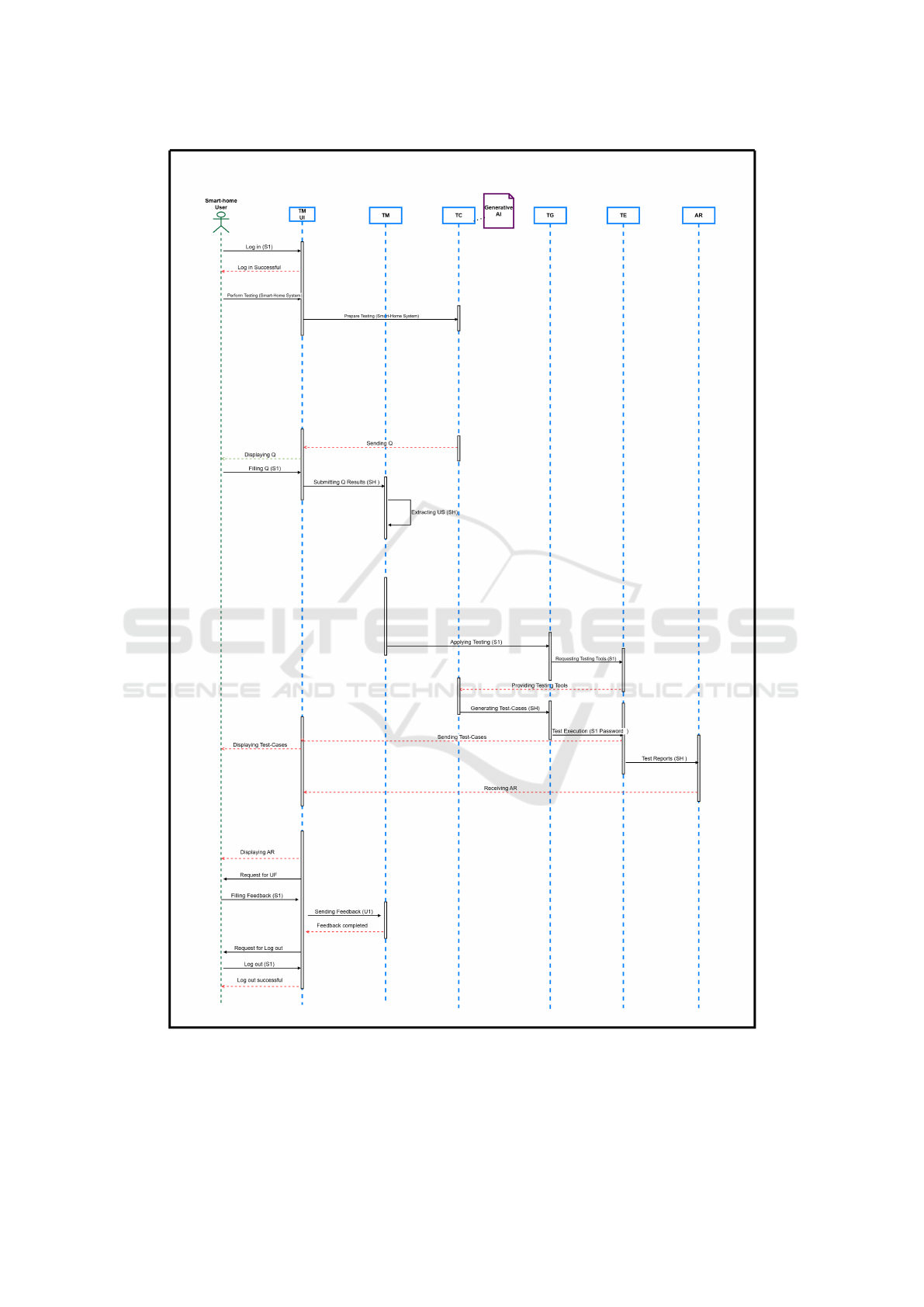
Figure 3: Behavioral Model SCTM Note: TM: Test Manager; S1: Tester-1;Q: Questionnaire; UI: User Interface; SH: Smart
home devices; TC: Test Controller TG: Test Generator TE: Test Executor AR: Analysis and Results (Smart home device to
be tested against cyber-attacks;Generating test-cases for the smart home IoT devices as per US (User Specifications).
WEBIST 2025 - 21st International Conference on Web Information Systems and Technologies
226

6 CONCLUSION
As cybersecurity testing evolves through the SCTM
behavioral model, it is focused on addressing the
complex risks that arise from IoT devices in smart
home systems. The primary objective is to encour-
age an environment where security is viewed as a
shared responsibility among all participants, from de-
vice manufacturers to end-users.
The collaboration among stakeholders empha-
sizes the importance of robust testing strategies and
comprehensive business continuity in case of cyber-
attacks on smart home systems. By actively engaging
users in the testing process, the SCTM testing model
helps them gain valuable insights into their behaviors
and expectations, ultimately paving the way for devel-
oping more secure and resilient smart home systems.
Future work involves testing various IoT devices
and anti-theft systems as it will broaden the scope of
cybersecurity testing for smart home systems through
SCTM. Furthermore, the focus will be on firmware
updates and innovative cyber-attacks that will make
our users aware of cybersecurity challenges.
ACKNOWLEDGEMENTS
This work was partially supported by the project SER-
ICS (PE00000014) under the NRRP MUR program
funded by the EU - NextGenerationEU.
REFERENCES
Abdusalomov, A. B., Kilichev, D., Nasimov, R., Rakhmat-
ullayev, I., and Cho, Y. I. (2024). Optimizing smart
home intrusion detection with harmony-enhanced ex-
tra trees. IEEE Access, 12:117761–117786.
Adewuyi, A., Oladele, A. A., Enyiorji, P. U., Ajayi, O. O.,
Tsambatare, T. E., Oloke, K., and Abijo, I. (2024).
The convergence of cybersecurity, internet of things
(iot), and data analytics: Safeguarding smart ecosys-
tems. World Journal of Advanced Research and Re-
views, 23(1):379–394.
Aldahmani, A., Ouni, B., Lestable, T., and Debbah, M.
(2023). Cyber-security of embedded iots in smart
homes: challenges, requirements, countermeasures,
and trends. IEEE Open Journal of Vehicular Tech-
nology, 4:281–292.
Alshboul, Y., Bsoul, A. A. R., Al Zamil, M., and Sama-
rah, S. (2021). Cybersecurity of smart home systems:
Sensor identity protection. Journal of Network and
Systems Management, 29(3):22.
Bonaventura, D., Esposito, S., and Bella, G. (2025). A case
of smart devices that compromise home cybersecurity.
Computers & Security, 151:104286.
Car, P. and De Luca, S. (2022). Eu cyber resilience act.
EPRS, European Parliament.
Chen, M.-Y. (2021). Establishing a cybersecurity home
monitoring system for the elderly. IEEE Transactions
on Industrial Informatics, 18(7):4838–4845.
Douha, N. Y.-R., Renaud, K., Taenaka, Y., and
Kadobayashi, Y. (2023). Smart home cybersecurity
awareness and behavioral incentives. Information &
Computer Security, 31(5):545–575.
ElArwady, Z., Kandil, A., Afiffy, M., and Marzouk, M.
(2024). Modeling indoor thermal comfort in build-
ings using digital twin and machine learning. Devel-
opments in the Built Environment, 19:100480.
Harkai, A. (2024). Managing cyber-security risks associ-
ated with iot devices for conducting financial trans-
actions within the smart home ecosystem. Procedia
Computer Science, 242:200–210.
Heiding, F., S
¨
uren, E., Oleg
˚
ard, J., and Lagerstr
¨
om, R.
(2023). Penetration testing of connected households.
Computers & Security, 126:103067.
Marchetti, E., Waheed, T., and Calabr
`
o, A. (2024). Cyber-
security testing in drones domain: A systematic liter-
ature review. IEEE Access, 12:171166–171184.
Mueck, M., Roberts, T., Du Boisp
´
ean, S., and Gaie, C.
(2025). Introduction to the european cyber resilience
act. In European Digital Regulations, pages 91–110.
Springer.
Piasecki, S., Urquhart, L., and McAuley, D. (2021). De-
fence against the dark artefacts: Smart home cyber-
crimes and cybersecurity standards. Computer law &
Security review, 42:105542.
Sharma, N. and Jindal, N. (2024). Emerging artificial in-
telligence applications: metaverse, iot, cybersecurity,
healthcare-an overview. Multimedia Tools and Appli-
cations, 83(19):57317–57345.
Tatipatri, N. and Arun, S. (2024). A comprehensive re-
view on cyber-attacks in power systems: Impact anal-
ysis, detection, and cyber security. IEEE Access,
12:18147–18167.
Trabelsi, Z. (2021). Iot based smart home security
education using a hands-on approach. In 2021
IEEE Global Engineering Education Conference
(EDUCON), pages 294–301. IEEE.
Waheed, T. and Marchetti, E. (2023). The impact of iot cy-
bersecurity testing in the perspective of industry 5.0.
In International Conference on Web Information Sys-
tems and Technologies.
Waheed, T., Marchetti, E., and Calabr
`
o, A. (2024). Securer:
User-centric cybersecurity testing framework for iot
system. In International Conference on Web Informa-
tion Systems and Technologies.
Waheed, T., Marchetti, E., and Calabr
`
o, A. (2025). Vulner-
ability mapping and mitigation through ai code anal-
ysis and testing. Proceedings of the 13th Interna-
tional Conference on Model-Based Software and Sys-
tems Engineering.
Zhou, X., Krishnan, A., and Dincelli, E. (2022). Examining
user engagement and use of fitness tracking technol-
ogy through the lens of technology affordances. Be-
haviour & Information Technology, 41(9):2018–2033.
Improving Cybersecurity for Smart Home Systems
227
