
Unloadable Computing Problem Based on Edge Distributed
Computing
Xiaoliang He
1,† a
, Jiazhen Xu
2,‡,* b
and Zhilin Yan
3,** c
1
College of Mathematics and Applied Mathematics, Guangdong University of Foreign and Studies, Guangzhou, China
2
College of Civil Engineering, Inner Mongolia University of Technology, Huhehaote, China
3
College of Data Science, City University of Macau, Macau, China
† ‡
Keywords: Edge Distributed Computing, Computation Offloading, Task Offloading, Resource Allocation.
Abstract: Due to limitations in power, computing power, and storage, mobile devices struggle to meet the demands of
rapidly developing applications. Offloading computing has emerged as a promising solution, becoming a
research focus. Edge distributed systems address this by offloading tasks from mobile devices to nearby edge
servers or networked devices. This paper focuses on edge distributed computing offloading and conducts the
following research: (1) An overview of common MEC mechanisms is provided, covering key technologies
like virtualization, SDN, CDN, SON, cloud computing, and collaborative computing. The characteristics of
edge distributed systems, such as scalability, location relevance, diversity, randomness, time-varying nature,
and autonomy, are discussed. Typical MEC implementation methods and future trends are explored. (2) A
shared bandwidth allocation algorithm using blockchain smart contracts is proposed to address wireless
resource scheduling challenges. This scheme eliminates the need for a central server, reducing latency and
enhancing scalability. (3) An optimized mobile edge collaborative learning algorithm is proposed, which
reduces data traffic and communication delays by shifting machine learning tasks to local devices. A compact
parameter set replaces redundant models to minimize excessive transmission.
1 INTRODUCTION
The rise of the Internet of Things (IoT) has led to a
surge in smart devices (Babatunde, Bodhaswar, 2016),
accompanied by an increase in compute-intensive and
latency-sensitive tasks. However, mobile devices
face significant challenges in processing these tasks
due to limitations in power consumption, computing
capability, and storage capacity. Against this
backdrop, edge computing, as a new computing
paradigm, has emerged. By deploying computing
resources at the network edge, it reduces task
processing latency, lowers energy consumption, and
enhances user experience. Computation offloading,
as one of the key technologies of edge distributed
computing, has become a current research hotspot.
Blockchain technology, with its characteristics of
decentralization, immutability, and transparency,
a
https://orcid.org/0009-0009-5025-2576
b
https://orcid.org/0009-0006-3452-0110
c
https://orcid.org/0009-0002-7818-9176
*
Corresponding author
holds great potential in the field of edge distributed
computing. It ensures task security and reliability
through a distributed ledger and achieves automated
management of computing tasks via smart contracts
(Baranwal, Kumar, Vidyarthi, 2023). Although
blockchain technology has been applied in task
scheduling optimization, enhancement of node
trustworthiness, and improvement of computing
result reliability, its challenges in performance,
scalability, and energy consumption limit its
widespread application (Chen, Wang, Liu, 2021).
This paper delves into the key technologies of
blockchain-based edge distributed computing
offloading, including trust foundation, elastic
offloading, fair scheduling, and security assurance.
The goal is to improve computational efficiency,
ensure security, and optimize user experience. The
research outcomes include a multi-chain
638
He, X., Xu, J. and Yan, Z.
Unloadable Computing Problem Based on Edge Distributed Computing.
DOI: 10.5220/0013703200004670
Paper published under CC license (CC BY-NC-ND 4.0)
In Proceedings of the 2nd International Conference on Data Science and Engineering (ICDSE 2025), pages 638-644
ISBN: 978-989-758-765-8
Proceedings Copyright © 2025 by SCITEPRESS – Science and Technology Publications, Lda.

collaborative trustworthy computing offloading
model that achieves data traceability, a collaborative
computing offloading method that constructs
standardized interaction processes, and a smart
contract-driven adaptive offloading strategy. By
transforming the task allocation problem into a
stochastic optimization problem, the strategy uses
stochastic optimization algorithms to reduce overall
costs and increase task completion rates. The
deployment of smart contracts with
reward/punishment mechanisms incentivizes
computing nodes to participate, ensuring successful
task completion and enhancing system robustness and
scheduling efficiency.
In related research, Li Yun et al. proposed
intelligent collaborative computing offloading and
resource allocation algorithms (Li, Zhang, Yao, 2024),
constructing a joint optimization problem to
minimize system energy consumption while meeting
user latency constraints. The Gat-HMARL algorithm
was employed, and simulations showed performance
improvements. In the joint optimization of intelligent
computing offloading and service caching (Li, Nan,
Yao, et al, 2025), a DAG task offloading and resource
optimization problem was established, and the
MADDPG algorithm was used to explore optimal
strategies. Experiments demonstrated that the
algorithm performed excellently in reducing energy
consumption and improving cache hit rates. Lin
Hongcai proposed the O2O-DRL and DR-DRL
methods based on DRL (Lin, 2024), which addressed
the cold start problem in reinforcement learning and
improved task success rates. In another study with the
same name, a solution for edge distributed computing
offloading was proposed in response to the limitations
of mobile devices. It introduced key technologies and
proposed a blockchain-based shared bandwidth
allocation algorithm driven by smart contracts to
reduce latency and enhance system scalability. An
optimized mobile edge collaborative learning
algorithm was also proposed.
This paper reviews the key technologies of edge
distributed computing offloading, including
computation offloading algorithms, resource
allocation strategies, the application of blockchain
technology in resource scheduling, and the
optimization of mobile edge collaborative learning
algorithms. It aims to summarize the current research
progress and challenges and to propose future
research directions, with the expectation of further
advancing the development of edge computing
technology.
2 DATASETS
The data in this paper presents the architecture of the
edge - distributed computing network, covering the
connections and data flow paths among components
such as edge devices, edge servers, and cloud
computing centers. It also provides symbols and
parameters related to computational offloading, such
as task volume and computing power, laying the
foundation for mathematical modeling. The
experimental parameters are diverse, involving
different computational tasks, network conditions,
and device performance scenarios, which effectively
verify the effectiveness and performance of the
computational offloading method and
comprehensively support the research work.
This paper trains Informer and double LSTM on
the ETTh1, ETTm1, and ECL datasets. Informer is a
prediction model adopting an encoder - decoder
architecture and has 11,330,055 parameters; while the
double - layer long short - term memory network
(LSTM) contains 4,233,735 parameters. ETTh1 and
ETTm1 represent two - year electricity data from two
cities in China. ETTh1 is applicable to hourly
readings, and ETTm1 is used for readings at 15 -
minute intervals. ECL shows the hourly electricity
consumption data of 321 customers in the United
States over two years.
3 EXPERIMENTAL METHODS
3.1 Distributed Reinforcement
Learning
In this paper, the task offloading method based on
distributed reinforcement learning demonstrates
unique research value and practical significance. It is
reflected in the following aspects:
1.Data Quality Assessment (DQ) Phase: Since
edge computing involves multi-source heterogeneous
data, these data may have low-quality issues such as
missing values and erroneous values due to device
differences and network fluctuations. By assessing
from multiple dimensions such as accuracy,
completeness, consistency, and timeliness, a
comprehensive understanding of the data status can
be achieved. For example, in terms of accuracy, data
verification algorithms can be used to compare with
known standards or historical data; completeness
assessment can check whether there is a lack of key
information in the data; consistency is achieved by
cross-checking the same type of data from different
data sources; and timeliness is judged based on the
data generation time and the time requirements of the
Unloadable Computing Problem Based on Edge Distributed Computing
639

application scenario. This step lays the foundation for
subsequent processing and ensures the reliability of
the data.
2.Data Repair (DR) Phase: The repair algorithm
based on a new repair consensus mechanism plays a
role, adopting corresponding technologies for
different types of low-quality data. For example, for
missing values, if the data has time series
characteristics, linear interpolation or spline
interpolation methods can be used; erroneous data can
be corrected according to the data distribution law
and business logic by setting thresholds or rules;
incomplete data blocks can be rebuilt using data
redundancy or backup. These means effectively
improve data quality and reduce its negative impact
on distributed computing.
3.Task Scheduling Distributed Reinforcement
Learning (DELTA) Step: Here, the distributed
reinforcement learning algorithm is used, regarding
edge devices as agents. Each agent makes decisions
based on its own computing resources, network
connection status, and the data quality assessed and
repaired, as well as the information obtained from the
surrounding environment. Agents continuously
interact with the environment during task offloading,
taking actions, such as executing tasks, offloading to
other devices or servers, and learn and optimize
strategies based on reward feedback such as the
timeliness of task completion and the degree of
energy consumption reduction, thereby achieving
efficient task offloading based on a new low-quality
data distribution strategy and ensuring data privacy
with the characteristics of blockchain.
From the perspective of theoretical basis,
distributed reinforcement learning fits the distributed
architecture characteristics of edge computing. Edge
devices have dispersed and limited resources, and
traditional centralized algorithms are powerless in
this environment. Distributed reinforcement learning
endows each edge device with the ability to learn and
make decisions independently, and continuously
optimizes system performance through interaction
and collaboration between devices. The data quality
assessment and repair phase directly hit the core of
the multi-source heterogeneous data problem,
effectively avoiding the disadvantages of computing
convergence delay and result deviation caused by
low-quality data, and laying a solid foundation for
accurate task offloading. The integration of
blockchain technology is the icing on the cake. Its
decentralized and tamper-proof attributes consolidate
the data security line of defense, effectively resist
malicious intrusion and data tampering, and
effectively ensure data privacy and the cornerstone of
system trust.
In the experimental design dimension, a simulated
edge computing scenario covering multiple edge
devices and servers is constructed, and variables such
as task types, data quality levels, and network
conditions are set multidimensionally. Key indicators
such as task completion time, system energy
consumption, data quality improvement, and privacy
protection effectiveness are comprehensively
considered to accurately judge the advantages and
disadvantages of this method compared with other
strategies. The experimental results show its
significant effectiveness. In terms of task completion
time, the offloading strategy that intelligently adapts
to data and network conditions can flexibly allocate
tasks to suitable devices or servers, greatly reducing
processing time. System energy consumption is
effectively controlled due to the reasonable task
allocation mechanism, avoiding device overload, and
distributed reinforcement learning continuously
optimizes strategies to achieve energy consumption
minimization. Data quality is significantly improved
after assessment and repair, effectively ensuring the
accuracy of application d computational resources,
and performance may be limited in complex edge
scenarios and large-scale task offloading. The
accuracy and efficiency of data quality assessment
and repair algorithms also need to be improved.
Compared with other related research, such as the
D2HM algorithm in "Distributed Heterogeneous
Task Offloading Algorithm in Mobile Edge
Computing," which uses distributed game theory and
Lyapunov optimization to achieve differentiated
control of heterogeneous tasks and elastic resource
allocation, reducing average delay; and the JORA
method in "JORA: Blockchain-based efficient joint
computing offloading and resource allocation for
edge video streaming systems," which uses
blockchain smart contract incentive mechanisms to
solve joint offloading, allocation, and video
compression optimization problems, achieving
efficient resource utilization and energy consumption
- accuracy balance. These achievements have opened
up new ideas for the research of blockchain-based
edge distributed computing offloading, and the task
offloading method based on distributed
reinforcement learning is expected to continuously
iterate and optimize in the process of integrating its
own advantages and drawing on the strengths of
others, deeply promoting the development of edge
computing offloading technology, and improving the
system's comprehensive performance and application
efficiency.
ICDSE 2025 - The International Conference on Data Science and Engineering
640

3.2 Test
3.2.1 Identity Information Encryption Test
In this study, in order to deeply evaluate the
performance of algorithms related to identity
information encryption, plaintext identity
information data in the range of ((0, 10]MB) was
specifically generated as the test dataset. The AES
algorithm, ECDH key agreement encryption and
decryption scheme, and ECIES scheme were
implemented using the BouncyCastle library in C#
for encryption and decryption performance testing. At
the same time, development packages such as
BitcoinSVCryptor and BsvSimpleLibrary were used
to better interact with the Bitcoin network.
3.2.2 Zero-Knowledge Identity
Authentication Test
Programming was carried out on two parts of the
crowdsourcing logistics platform: generating zero -
knowledge questions and verifying zero - knowledge
proofs. In the test, 1 to 250 users were simulated to
simultaneously initiate zero - knowledge
authentication challenges to the crowdsourcing
logistics platform.
3.3 Experimental design
In the algorithm comparison experiment of edge
distributed computing, in order to simulate the large-
scale multi-access edge computing (MEC) scenario,
the experimental environment is set to contain
multiple mobile devices (MD) and multiple edge
servers (ES). The amount of MD and ES can be
adjusted according to the specific needs of the
experiment. At the beginning of each time slot, each
MD randomly generates tasks of different sizes
according to the Bernoulli distribution, and the size of
the tasks is expressed in data volume (unit: Mbit). In
the experimental environment of this paper, several
algorithms are compared to evaluate their
performance in dealing with MEC task unloading.
MADDPG algorithm is a multi-agent depth
deterministic strategy gradient algorithm, which is a
classical algorithm to solve MEC task unloading
problem. The algorithm can deal with the cooperation
and competition between multiple agents, but the
computational complexity is high in large-scale
scenarios. In the experiment, MADDPG algorithm is
used as one of the comparison algorithms to evaluate
the performance of MF-MATO algorithm. DDPG
algorithm is a distributed single-agent algorithm,
which can not deal with the interaction between
agents and partial observability. Due to the partial
observability of MEC environments, the performance
of DDPG algorithms may be limited. In the
experiment, DDPG algorithm is used as one of the
comparison algorithms to highlight the advantages of
MF-MATO algorithm in dealing with partially
observable problems. LSTM-DQN algorithm
introduces LSTM network into DQN to solve part of
the observable problem, but it is still a single-agent
algorithm. The algorithm can deal with the partially
observable problem of a single agent, but it cannot
deal with the cooperative relationship between
multiple agents. In the experiment, LSTM-DQN
algorithm is used as one of the comparison algorithms
to evaluate the performance of MF-MATO algorithm
in collaborative task unloading. The Random
algorithm is a simple uninstall strategy in which MD
randomly generates uninstall decisions. The
algorithm does not rely on any optimization algorithm
or model, so it can be used as a benchmark
comparison algorithm to evaluate the performance
improvement of other algorithms. Then the
MADDPG, DDPG, LSTM-DQN and Random
experimental results were compared and analysed.
The performance of different algorithms is evaluated
by comparing the average delay and average task
dropout rate.
4 ANALYSIS OF
EXPERIMENTAL RESULTS
4.1 Distributed Reinforcement
Learning Analysis
In terms of task completion time, the experimental
results show that the method performs excellently.
Due to its ability to intelligently select task offloading
strategies based on data quality and network
conditions, for example, when a certain edge device
has limited resources or data processing capabilities,
it can quickly transfer tasks to other devices or servers
with sufficient resources. This allows tasks to be
processed in a more suitable environment, effectively
avoiding processing delays caused by device
performance bottlenecks or data issues, thereby
significantly reducing task completion time and
improving the system's overall response speed, which
is crucial for edge computing application scenarios
with high real-time requirements.
From the perspective of system energy
consumption, the method has also achieved good
Unloadable Computing Problem Based on Edge Distributed Computing
641

results. Through a reasonable task allocation
mechanism, it avoids the situation where some
devices are overloaded and consume too much energy.
The distributed reinforcement learning algorithm
continuously learns and optimizes task offloading
strategies, enabling tasks to be executed on devices or
servers with lower energy consumption, achieving the
minimization of system energy consumption. In edge
computing environments, devices usually rely on
limited energy supplies (such as battery-powered
mobile edge devices), and reducing energy
consumption helps to extend the device's endurance
time and improve the system's sustainable operation
capability.
Regarding the degree of data quality improvement,
after the data quality assessment and repair steps, the
reliability and availability of the data are significantly
enhanced. Experimental results show that low-quality
data repaired can produce more accurate results in
subsequent task offloading and processing processes.
In application fields with strict data quality
requirements, such as the Industrial Internet of Things
and the Energy Internet, accurate data processing
results are the key to ensuring the normal operation of
the system and the scientific nature of decision-
making. For example, in the monitoring and control
of industrial production processes, high-quality data
can ensure the precise operation of equipment and
timely warning of failures, avoiding production
accidents or efficiency losses caused by data errors.
In terms of privacy protection effects, the
introduction of blockchain technology provides a
solid guarantee for data privacy. Experimental results
have confirmed that the task offloading framework
based on blockchain effectively prevents data leakage
and tampering. In edge computing environments, data
may be transmitted and processed between multiple
devices and servers, facing many security risks. The
decentralized and tamper-proof characteristics of
blockchain ensure the security and integrity of data
throughout the computing offloading process,
protecting user privacy and enhancing user trust in
edge computing systems.
However, the experimental results also reveal
some limitations of the method. For example, the
training and convergence of distributed
reinforcement learning algorithms may require a
longer time and more computational resources. In
edge computing environments, the computing power
of edge devices is relatively weak, which may affect
the deployment and performance of the method in
practical applications. Especially in complex edge
computing environments and large-scale task
offloading scenarios, with a large number of devices
and complex task types, the difficulty of algorithm
training and convergence may further increase,
thereby limiting the application scope and
effectiveness of the method. In addition, the accuracy
and efficiency of data quality assessment and repair
algorithms still need to be further improved to better
cope with the complex and changing data quality
issues in edge computing.
4.2 Distributed Reinforcement
Learning Analysis
The ECDH key agreement scheme takes longer than
the AES algorithm. This is because it not only needs
to derive the shared key but also has to use the shared
key to derive the symmetric key for encryption and
decryption operations. The encryption and decryption
time of the ECDH key agreement encryption and
decryption scheme is shorter than that of the ECIES
scheme. This is because the identity information in
this paper is stored in Bitcoin SV (BSV) blockchain
transactions. During the process of uploading to the
blockchain, the trader signs the transaction with
OP_RETURN, which eliminates the computational
overhead of the MAC verification algorithm in the
ECIES scheme. Although the encryption and
decryption efficiency of the ECDH key agreement
scheme is lower compared to the AES algorithm, the
blockchain - based identity information encryption
and decryption scheme implemented in this study still
has a relatively fast encryption and decryption speed
and strong practicality.
As the number of users increases, when the
number of users is the same, the authentication delay
of the scheme proposed in this paper is shorter than
that of the SHAO scheme, and the authentication
speed is faster. Under the condition of an equal
number of users, the transaction - processing ability
of the scheme proposed in this paper is better than that
of the SHAO scheme. The scheme proposed in this
paper has significantly improved the authentication
delay and authentication efficiency of the
crowdsourcing logistics platform, effectively
enhancing the authentication performance of the
system.
4.3 Algorithm analysis
In Figure 1, the MF-MATO algorithm shows good
performance stability and optimization ability in
dealing with multi-agent cooperation problem and
partially observable problem. MADDPG algorithm
also shows some advantages in dealing with multi-
agent cooperation problem, but its performance
ICDSE 2025 - The International Conference on Data Science and Engineering
642
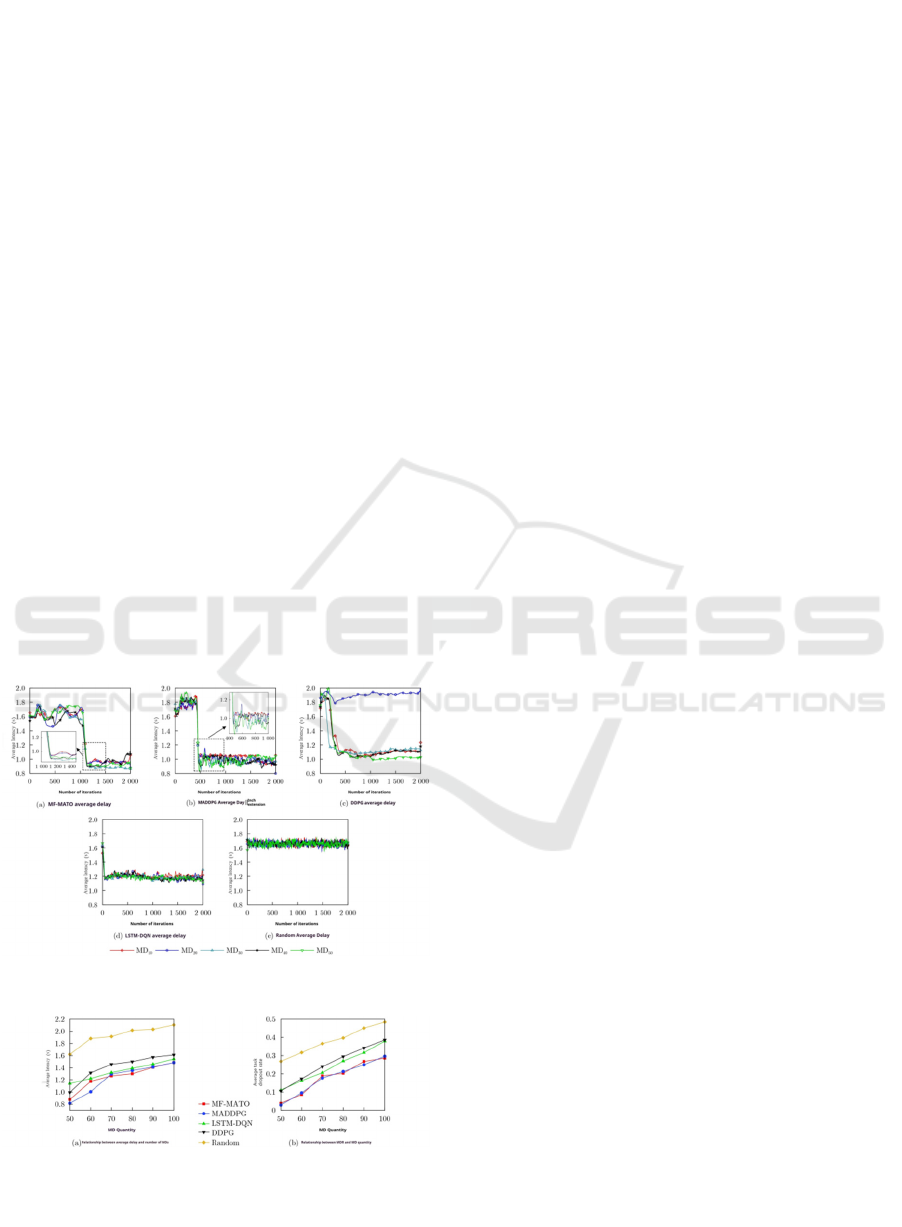
fluctuates greatly. As a single-agent algorithm,
DDPG algorithm may not be as effective as
MADDPG and MF-MATO in dealing with multi-
agent cooperation problems. LSTM-DQN algorithm
has some limitations in dealing with partially
observable problems, but its performance is relatively
stable (Lu, Li, 2024).
In Figure 2, two algorithms, MF-MATO and
LSTM-DQN, are selected for comparison. MF-
MATO may be an algorithm for multi-agent or edge
computing, while LSTM-DQN introduces LSTM
(Long short-term memory) networks in DQN (deep Q
network) to handle partially observable problems.
MF-MATO algorithm may have better performance
stability and optimization ability when dealing with
multi-agent or edge computing tasks. LSTM-DQN
algorithm is sensitive to the state transition mode
when dealing with partially observable problems, so
it needs to be carefully considered in specific
applications. Increasing the number of MD may
affect the performance of the algorithm, depending on
factors such as the algorithm type, state transition
method, and metrics. The average delay and MDR are
used as effective tools to evaluate the performance of
the algorithm (Lu, Li, 2024).
Finally, it is verified that MF-MATO algorithm
and MADDPG algorithm can make MD cooperative
decision in the system, and the utilization rate of
computing resources is higher.
Figure 3: Average latency curve of different algorithms
(Lu, Li, 2024).
Figure 4: Average latency and MDR vary with the number
of MDs (Lu, Li, 2024).
5 CONCLUSIONS
With the rise of Internet of Things (IoT) technology,
the number of smart devices has surged, and the
number of computing-intensive and latency-sensitive
tasks has gradually increased. Due to the limitations
of power consumption, computing power and storage
capacity, mobile devices face huge challenges in
processing these tasks. Edge distributed computing
offloading technology, as a solution, reduces task
processing latency and energy consumption by
deploying computing resources at the network edge.
Scalability, location correlation, diversity,
randomness, time variability and autonomy are the
characteristics of edge distributed systems, which
make edge distributed systems flexibly applied in
different scenarios. The application of blockchain
technology includes the use of the decentralization,
immutable and transparent characteristics of
blockchain technology to ensure the safety and
reliability of tasks in edge distributed computing, and
the automated management of computing tasks
through smart contracts. The paper proposes a smart
contract-based shared bandwidth allocation algorithm
combined with blockchain technology to reduce
delay and improve system scalability, optimize the
mobile edge collaborative learning algorithm, and
improve task unloading efficiency and system
performance. This paper verifies the effectiveness
and performance of the algorithm through
experiments, including task completion time, system
energy consumption, data quality improvement and
privacy protection effect.
The experimental results show that the proposed
method can significantly reduce the task completion
time, improve the overall response speed of the
system, reduce energy consumption and extend the
battery life of the equipment. Compared with other
research results such as D2HM algorithm and JORA
method, this paper shows the unique advantages of
the proposed method in task unloading, resource
allocation and system performance optimization.
In conclusion, this paper explores the key
technologies of blockchain-based edge distributed
computing offloading, proposes the optimization
algorithm method, and verifies its performance.
However, there are still some limitations and
challenges that need to be further explored and
addressed by future research.
Unloadable Computing Problem Based on Edge Distributed Computing
643

AUTHORS CONTRIBUTION
All the authors contributed equally and their names
were listed in alphabetical order.
REFERENCES
Babatunde, S., Bodhaswar, T. J., Attahiru, S. 2016. Solving
resource allocation problems in cognitive radio
networks: a survey. EURASIP J. Wireless Comm. and
Networking. Volume 2016 , Issue 1. PP 1-14.
Baranwal, G., Kumar, D., Vidyarthi, D. P. 2023.
Blockchain based resource allocation in cloud and
distributed edge computing: A survey. Computer
Communications. Volume 209, Issue. PP 469-498.
Chen, J., Wang, Y. L., Liu, T. 2021. A proactive resource
allocation method based on adaptive prediction of
resource requests in cloud computing. EURASIP
Journal on Wireless Communications and Networking.
Volume 2021, Issue 1.
Hisham, M. A. 2025. UAV-assisted mobile edge computing
model for cognitive radio-based IoT
networks. Computer Communications 108071-108071.
Gao, R. L., Zhang, W. Z., Mao, W. Y., Tan, J. J., Zhang, J.,
Huang, H. Y., ... & Huang, F. Y. 2025. Method towards
collaborative cloud and edge computing via RBC for
joint communication and computation resource
allocation. Journal of Industrial Information
Integration 100776-100776.
Li, Y., Nan, Z. Y., Yao, Z. X., et al. 2025. Distributed
intelligent computing offloading and service caching
joint optimization for DAG tasks. Journal of Sun Yat-
sen University (Natural Science Edition in Chinese and
English), 64(1): 71-82.
Li, Y., Zhang, J. X., Yao, Z. X., et al. 2024. Neighborhood-
aware distributed intelligent edge computing offloading
and resource allocation algorithm. Science China:
Information Sciences, 54: 413–429, doi: 10.1360/SSI-
2023-0177
Li, Z. Y., Wu, Y., Zhang, W. W., Li, Y. G. 2022. A Trusted
Identity Authentication Model for Crowdsourcing
Logistics Based on the UTXO - Model Blockchain.
Journal of Jiangsu University.
Lin, H. C., 2024. Research on distributed task offloading
technology under edge computing. Computer Science,
51(6): 1-10.
Lu, X. L. & Li, D. K. 2024. Task unloading algorithm for
large-scale multi-access edge computing scenarios.
Journal of Electronics and Information. 1-11.
ICDSE 2025 - The International Conference on Data Science and Engineering
644
