
Masked Vector Sampling for HQC
Maxime Spyropoulos
1,2
, David Vigilant
1
, Fabrice Perion
1
, Renaud Pacalet
2
and Laurent Sauvage
2
1
Thales, Meudon, France
2
LTCI, T
´
el
´
ecom Paris, Institut Polytechnique de Paris, France
Keywords:
HQC, Masking, Side-Channel Attack, Post-Quantum Cryptography.
Abstract:
Anticipating the advent of large quantum computers, NIST started a worldwide competition in 2016 aiming
to define the next cryptographic standards. HQC is one of these post-quantum schemes selected for standard-
ization. In 2022, Guo et al. introduced a timing attack that exploited a weakness in HQC rejection sampling
function to recover its secret key in 866,000 calls to an oracle. The authors of HQC updated its specification
by applying an algorithm to sample vectors in constant time. A masked implementation of this function was
later proposed for BIKE but it is not directly applicable to HQC. In this paper we propose a specification-
compliant masked version of the HQC vector sampling which relies, to our knowledge, on the first masked
implementation of the Barrett reduction.
1 INTRODUCTION
Post-Quantum Cryptography (PQC) gained interest
when NIST, anticipating that the current public-key
cryptosystems might be broken by quantum com-
puters by 2030, launched its competition. In 2024
the competition reached an important milestone with
the publication of three standards (nis, 2024) derived
from three selected algorithms, out of 69 initially sub-
mitted. An extra fourth round took place and ended
in March 2025 with the selection of HQC (nis, 2025).
NIST also posted a call for proposals for extra short
signature schemes (nis, 2022) that would ideally not
rely on the problems of structured lattices.
In the meantime regarding the quantum threat,
progresses are still ongoing on both technology and
algorithms. Oded Regev published in 2023 an algo-
rithm to factor an n-bits integer using O(n
3/2
) quan-
tum gates instead of Shor’s original O(n
2
) (Regev,
2023). The same year, IBM presented its 1000+ qbits
quantum computer and aims to reach 4000+ qbits by
year 2025 (ibm, 2023).
HQC (Melchor et al., 2018) is a code-based Key-
Encapsulation Mechanism (KEM), used to securely
share a symmetric key between two parties. Its se-
curity relies on the hardness of random linear code
decoding and is proved to be Indistinguishable under
Adaptive Chosen Cipher Attack (IND-CCA2). It has
reduced public key and ciphertext sizes, thanks to its
quasi-cyclic structure. Its fast key generation and de-
capsulation made it “one of the two best candidates of
the fourth round” (Alagic et al., 2022).
The capacity to develop side-channel resistant and
efficient implementations of the algorithm is an ex-
plicit and important criterion for selection (nis, 2016).
Side-Channel Attacks (SCA) have been first intro-
duced by Kocher in 1996 (Kocher, 1996). They take
advantage of data-dependent physical leakage (power
consumption, execution time, . . . ) emanating from
an implementation of a cryptographic algorithm. If a
leak is correlated to operations involving a secret, an
attacker can exploit it to recover information about the
secret without breaking any underlying mathematical
hard problem. The security evaluation of the scheme
in the “real world” setup also raises questions about
performance. Indeed, hardening an implementation
against SCA may hinder its performance and com-
petitiveness. HQC has already been thoroughly vet-
ted against SCA, either against Timing Attack (Paiva
and Terada, 2020; Wafo-Tapa et al., 2019; Guo et al.,
2022) or Template Attack (Goy et al., 2022; Goy
et al., 2024; Ba
¨
ısse et al., 2024).
In (Guo et al., 2022) the execution time of the re-
jection sampling function of HQC was exploited to
recover the secret key. The HQC team updated the
specification to patch this vulnerability with a coun-
termeasure designed by Sendrier (Sendrier, 2021)
to sample vectors in constant time. In 2024 De-
750
Spyropoulos, M., Vigilant, D., Perion, F., Pacalet, R., Sauvage and L.
Masked Vector Sampling for HQC.
DOI: 10.5220/0013637400003979
In Proceedings of the 22nd Inter national Conference on Security and Cryptography (SECRYPT 2025), pages 750-758
ISBN: 978-989-758-760-3; ISSN: 2184-7711
Copyright © 2025 by Paper published under CC license (CC BY-NC-ND 4.0)

mange and Rossi (Demange and Rossi, 2024) pro-
vided the first complete high-order masked imple-
mentation of BIKE, another code-based algorithm, in-
cluding a masked version of Sendrier’s countermea-
sure. Although the new masked vector sampling is
well suited for BIKE, it is not directly applicable to
HQC, which specifications differ.
Contributions. This paper presents a masked
specification-compliant vector generation function
for HQC that relies on the first masked Barrett re-
duction to our knowledge. We also give a theoreti-
cal security proof backed by a practical evaluation of
our implementation on a STM32 board. This practi-
cal evaluation raises a warning about our secure im-
plementation and the one proposed by Demange and
Rossi, showing that compilation optimizations should
be handled carefully.
Organization. The remaining of the paper is orga-
nized as follows. Section 2 describes HQC, the mask-
ing and what motivated our approach. In Section 3
we adapt the BIKE secure implementation and pro-
pose our masked version of the HQC vector sampling,
with security proof. Section 4 summarizes the practi-
cal evaluations of our implementation on an STM32
device. Finally, Section 5 concludes the paper.
2 BACKGROUND
2.1 HQC
HQC is a post-quantum scheme based on the theory of
quasi-cyclic codes, where the secret key is generated
independently from the code, such that the security
reduction is independent from the decoding algorithm
used for decryption. Our work refers to the specifica-
tion of February 2025.
The authors use the Hofheinz-H
¨
ovelmanns-Kiltz
transformation (a variant of the Fujisaki-Okamoto
transformation that handles decryption failures) to
turn the IND-CPA secure Public Key Encryption
scheme (PKE) into an IND-CCA2 KEM.
HQC.PKE. The PKE version of HQC consists of
three algorithms. k is the length of the shared key
(128, 256 or 512 bits), it is a parameter set at initial-
ization. Algorithm 8 generates public key pk and se-
cret key sk given seed R . The weights ω are parame-
ters that depend on k. Algorithm 9 encrypts message
m using pk and seed θ. C is the HQC public con-
catenated code. Finally, Algorithm 10 shows the de-
cryption of ciphertext c knowing sk. The secret key is
(x,y,σ) although only y is needed for decryption.
HQC.KEM. The KEM version of HQC relies
on three hash functions (G, H ,K ), all based on
SHAKE256, and consists of 2 algorithms. The sender
generate a random symmetric key K with Algo-
rithm 11 and exchange it as a ciphertext. The receiver
retrieves the symmetric key with Algorithm 12.
2.2 Guo et al. Timing Attack
HQC June 2021 specification suffered from a tim-
ing flaw in its encryption function, which relies on
the sampling of three fixed weights random vectors.
The support of each vector was computed from ran-
dom bytes generated by an eXtendable Output Func-
tion (XOF) named seedexpander. In most cases
there was no collision between the indexes drawn and
seedexpander was called only 3 times, once per vec-
tor. However, if at least one collision occurred, a sec-
ond call to seedexpander was made.
This difference in the number of calls was notice-
able in timing and the authors used this distinguisher
to perform a Timing Attack and recover the secret key
in ≈ 8.7 × 10
5
decapsulations (Guo et al., 2022).
2.3 Sendrier’s Countermeasure
In 2021, Sendrier proposed an algorithm to sample
vectors in constant time in order to patch this vul-
nerability in both BIKE and HQC rejection sampling
functions (Sendrier, 2021). The idea is to always ask
for the same amount of pseudo randomness. In the
event of a collision between two indexes, the index
that was drawn is replaced by the current index of the
loop iteration (see Algorithm 1). This is made possi-
ble by the introduction of a small bias that has no sig-
nificant impact on the distribution (Sendrier, 2021).
In Algorithm 1, compare is a constant-time func-
tion returning 0xF...F if the two input values are
equal, else 0x0...0. Following recommendations of
Guo et al., the HQC team added this countermeasure
in their 2023 update of the scheme.
2.4 Masking the Vector Sampling
Masking. The principle of masking is to add ran-
domness to any sensitive variable in the algorithm.
A common masking scheme is the boolean mask-
ing (Chari et al., 1999; Goubin and Patarin, 1999)
where any sensitive variable x is split into d + 1
boolean shares, d of which are random, such that
x = x
0
⊕ ... ⊕ x
d
. d is the masking order. During
Masked Vector Sampling for HQC
751

Algorithm 1: Sendrier’s constant time vector sampling.
Data: s,seed,n
Result: sup[0],.. ., sup[s − 1]
1 prng ← prng init(seed);
2 for i = 0 to s − 1 do
3 sup[i] ← i + rand(prng,n − i) ;
/* sup[i] ∈ [i,n[ */
4 end
5 for i = s − 1 downto 0 do
6 f ound ← 0 ; /* collision flag */
7 for j = i + 1 to s − 1 do
8 f ound ←
f ound ∨ compare(sup[i],sup[ j]);
9 end
10 sup[i] ← (i ∧ f ound) ⊕ (sup[i]∧ ¬ f ound);
11 end
computations the shares are processed such that any
combination of d intermediate variables is indepen-
dent of any sensitive variable. The observations of an
attacker with access to up to d intermediate variables
is thus independent of any secret. The algorithm is
said d-probing secure.
Security Proof. To prove the security of an algo-
rithm, the easiest way is to prove the security property
of elementary functions, called gadgets. To achieve
overall security one can follow the composition prop-
erty outlined in (Barthe et al., 2016, Proposition 4):
An algorithm P is t-NI provided all its gadgets are
t-NI, and all masked variables are used at most once
as argument of a gadget call other than refresh.
t-NI is also introduced in (Barthe et al., 2016):
Definition 1. A gadget is t-non-interfering (t-NI) iff
any set of at most t observations can be perfectly sim-
ulated from at most t shares of each input.
Remark 1. t-NI implies t-probing secure.
Remark 2. Any linear operation in binary finite field
F
2
is a t-NI gadget, as long as it is applied share-wise.
The refresh function was introduced in (Coron,
2013) to increase the overall randomness of an algo-
rithm by re-randomizing the shares encoding a se-
cret variable. Informally, Proposition 4 states that a
masked input value has to be refreshed before being
used as input in another gadget.
Masked Implementation. In 2024, Demange and
Rossi proposed a fully masked and provably secure
implementation of BIKE (Demange and Rossi, 2024)
featuring a masked version of Sendrier’s algorithm,
named SecFisherYates. It is proved t-NI and the
authors provided a C implementation publicly avail-
able on GitHub (dem, 2024).
Algorithm 2: Demange-Rossi masked SecFisherYates.
Data: s ∈ N, n ∈ N
Result: JrK ∈ Z
s
n
a randomly generated
vector without repeated values
1 for i = s − 1 downto 0 do
2 Jr
i
K ← sec
rand
(n − i);
3 JiK ← refresh(i);
4 Jr
i
K ← sec
+
(Jr
i
K,i);
5 for j = i + 1 to s − 1 do
6 Jr
j
K ← refresh(Jr
j
K);
7 JbK ← sec
=
(Jr
i
K,Jr
j
K);
8 Jr
i
K ← refresh(Jr
i
K);
9 JiK ← refresh(JiK);
10 Jr
i
K ← sec
i f
(JiK,Jr
i
K,JbK);
11 end
12 end
3 PROPOSED
COUNTERMEASURE
BIKE and HQC differ in the way they draw a random
number in interval Z
n
. Given a p bits random num-
ber a, BIKE multiplies it by n and shifts p bits to the
right (Algorithm 3, Line 4), whereas HQC returns the
remainder of a modulo n (Algorithm 4, Line 3).
Algorithm 3: BIKE vector sampling.
Data: seed,len, wt
Result: wlist, a list of wt distinct elements of
{0,. .. ,len − 1}.
1 wlist ← () ; /* empty list */
2 s
0
,. .. ,s
wt−1
←
SHAKE256-Stream(seed,32 · wt) ;
/* parse as a sequence of wt non
negative 32-bits integers */
3 for i = wt − 1 downto 0 do
4 pos ← i + ⌊(wt − i)s
i
/2
32
⌋;
5 wlist ← wlist,(pos ∈ wlist) ? i : pos;
6 end
Algorithm 4: HQC vector sampling.
Data: n, w, seed
Result: w distinct elements of {0,...,n}
1 prng ← prng init(seed);
2 for i = w − 1 downto 0 do
3 l ← i + (rand(prng) mod (n − i));
4 pos[i] ← (l ∈ {pos[ j],i < j < t) ? i : l ;
5 end
6 return pos[0],..., pos[w − 1]
SECRYPT 2025 - 22nd International Conference on Security and Cryptography
752

This difference means that the SecFisherYates
algorithm cannot be directly transposed to an HQC
implementation, as it would not follow the specifica-
tions. We must thus design a side-channel resistant
function that computes the remainder of a boolean
masked value a modulo a public value n. Our design
does not use division or modulo instructions because
on some architectures their execution time depends on
the numerator which, in our case, is a secret variable;
a variation in execution time could leak information
about the secret. Moreover, they are not directly ap-
plicable to boolean masking. We solve this problem
with a masked Barrett reduction. Non-masked Bar-
rett reduction was actually implemented in September
2023 in the PQClean version of HQC before being
added to the HQC specification in February 2024.
3.1 Barrett Reduction
The Barrett reduction (Barrett, 1987) efficiently com-
putes the remainder of an integer division in constant-
time. To compute x mod n one can use r = x −
⌊x/n⌋ × n. Instead of using a division, Barrett ap-
proximates the quotient with an integer m such that
m
2
p
≈
1
n
. We usually take m = ⌊
2
p
n
⌋.
Remark 3. In our case, p = 32, because the function
rand of HQC (Algorithm 4, Line 3) outputs pseudo-
random 32-bits unsigned integers.
Since the quotient
m
2
p
is only guaranteed to be less
or equal
1
n
, a final subtraction is sometimes required.
The main advantages are that variable m can be pre-
computed, and dividing by 2
p
comes down to a shift
p bits to the right, which is virtually free.
Algorithm 5: Barrett reduction.
Data: a, n, p and m s.t. m = ⌊
2
p
n
⌋
Result: r = a mod n
1 q ← (a × m) ≫ p;
2 r ← a − q × n;
3 if r ≥ n then
4 r ← r −n;
5 end
3.2 Masked Implementation
Our fully masked implementation of the Barrett re-
duction, uses gadgets introduced in (Demange and
Rossi, 2024). It is constant-time by design, provably
secure and works with any masking degree.
In the following, JxK denotes the array contain-
ing the boolean shares of masked variable x. All
binary secure operations for which it makes sense
come in two flavours: sec
op
(JAK,JBK) (both operands
masked), sec
op
(JAK,B) (left operand masked, right
operand public and unmasked). On top of the avail-
able gadgets we developed a new one, sec
−
(JaK,JbK),
to compute the subtraction JaK−JbK of 2 masked vari-
ables (see Algorithm 13 in appendix).
Algorithm. To preserve the constant-time property,
we always compute the conditional subtraction. We
first subtract n from the computed value a qn = a −
q × n), and store the result in A (Line 7). There are
2 possibilities: either A is negative and a qn is the
correct result or A is positive and the correct result.
To evaluate the sign of A we shift it by 31 bits to the
right and store the result in z; if A is negative then z is
equal to 1, else A is positive and z is equal to 0.
Algorithm 6: Masked Barrett reduction.
Data: JaK, m,n
Result: JrK = JaK mod n
1 JqK ← sec
×
(JaK,m);
2 JqK ← JqK ≫ 32 ; /* Sharewise shift */
3 JqnK ← sec
×
(JqK,n);
4 JaK ← refresh(JaK);
5 Ja qnK ← sec
−
(JaK,JqnK);
6 minus n ← 2
32
− n;
7 JAK ← sec
+
(Ja qnK,minus n);
8 JzK ← JAK ≫ 31;
9 JAK ← refresh(JAK);
10 Ja qnK ← refresh(Ja qnK);
11 JrK ← sec
i f
(Ja qnK,JAK, JzK) ;
/* JzK ? Ja qnK : JAK */
Theorem 1. Masked Barrett reduction is t-NI secure
Proof. m and n are public values, we do not need
to mask them. as it operates independently on each
share, the shift operation (Lines 2, 8) is t-NI. All used
gadgets are t-NI. The only masked variables that are
used twice without modification are a (Lines 1, 5), A
(Lines 8, 11) and a qn (Lines 7, 11). They are all re-
freshed (Lines 4, 9, 10) before their re-use.
4 EXPERIMENTAL RESULTS
We conducted our experiments on the STM32
Nucleo-F439ZI development board equipped with an
ARM Cortex-M4 core at 180 MHz. We selected
the pqm4 (Kannwischer et al., ) implementation of
HQC. We retrieved the code of the gadgets from
Github (dem, 2024) and implemented our solution.
After setting the masking order to one, we ran 10,000
executions of our masked Barrett reduction, once with
fixed inputs and once with random ones; and recorded
Masked Vector Sampling for HQC
753
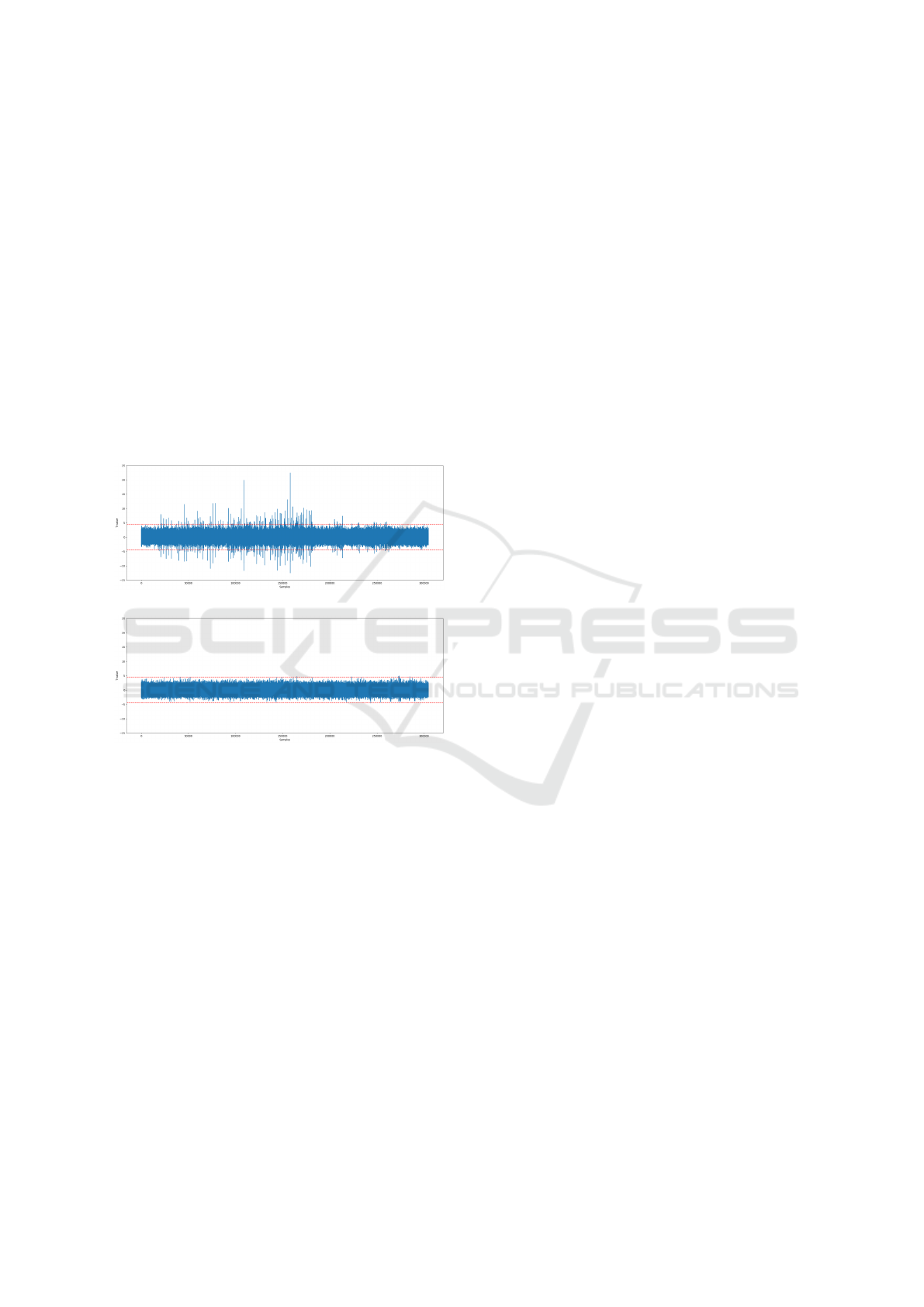
the resulting electro-magnetic traces. For compari-
son purposes, we ran this first experiment while fix-
ing the masks to zero (virtually unmasking the se-
cret value). Using a Test Vector Leakage Assess-
ment (TVLA) (Becker et al., 2013) we confront these
two sets of traces and obtain Figure 1a. The nu-
merous peaks well above and below the ±4.5 thresh-
old (Schneider and Moradi, 2016) (dotted red lines)
indicates the presence of leaks. We then ran a second
experiment, this time relying on the integrated True
Random Number Generator (TRNG) of the board to
produce the random masks required for the computa-
tion. This time, there are no visible peaks (Figure 1b)
which is expected from a first order leakage analysis
of a first order masking. Hence, the absence of leaks
in the second experiment gives us better confidence
concerning the soundness of our solution.
(a) with masks set to zero.
(b) with random masks.
Figure 1: TVLA of the masked Barrett reduction.
Remark 4. A formal security proof on the pseudo
or source code is not a complete guarantee. Due to
all optimizations performed by the compilation tool
chain and even by the hardware, executing the corre-
sponding compiled software on a real hardware CPU
can leak secret data, even when the abstract algorithm
was proved t-NI secure. Further analyzes on the as-
sembly code, on the linked and loaded binary or even
on the actual execution by the processor are needed
before one can conclude that the masking provides the
expected security level, as demonstrated for instance
in (Coron et al., 2012).
Our results were obtained with the -Og compila-
tion flag and all caches ON. While testing another
configuration, we found out that compiling with the
-O3 flag introduces leaks (see Figure 3 in Appendix).
As we explain in Appendix these leaks are due to a
different mapping of the various shares on the physi-
cal CPU registers.
4.1 Accelerating the Multiplication
Boolean masking is one of several masking tech-
niques. Arithmetic masking, for instance, splits a se-
cret variable x into d + 1 shares such that:
x = x
0
+ ··· + x
d
mod 2
k
(1)
In (Demange and Rossi, 2024) the authors decided
to avoid conversions between boolean and arithmetic
masking (BtoA and AtoB) because they are consid-
ered as expensive and because most BIKE operations
are binary. As HQC also uses binary vectors and op-
erations, taking advantage of this structure to do effi-
cient computations (e.g., the addition of two vectors is
a bitwise exclusive OR (XOR) of their components),
the choice of boolean masking makes sense.
However, if we could find an operation which is
faster under arithmetic masking, even taking into ac-
count the cost of the conversions, we could expect a
performance improvement. The multiplication of our
Barrett reduction function is an interesting candidate
because in boolean masking it represents nearly 80%
of the function, while multiplying by a public value
n in arithmetic masking simply consists in multiply-
ing each share of x by n; the cost is in O(d). We
thus compared the cost of a multiplication in boolean
masking and the cost of a sequence BtoA, arithmetic
multiplication, AtoB:
1. Boolean multiplication, no conversion:
O(k × log k × d
2
)
2. Arithmetic multiplication, with conversions:
O(log k × d
2
)
with k = 32 bits and d the order of masking.
It appears that, theoretically, the multiplication
could be significantly accelerated. We designed a
new version of our masked Barrett reduction, replac-
ing the boolean multiplications with arithmetic ones
and the appropriate conversions (see Algorithm 7).
For simplicity sake, we will refer to this version as
Arithmetic Barrett, to contrast our first solution which
relied exclusively on boolean masking. We based
the code for the conversions on the pseudo-code de-
scribed in (Coron et al., 2014, Algorithm 4 & 6). We
ran the same experiments as described at the begin-
ning of Section 4 to check if this new solution was
still secure. The results are presented in Figure 2.
As expected, using mask conversions and arithmetic
masking does not affect the security of our solution.
SECRYPT 2025 - 22nd International Conference on Security and Cryptography
754

Algorithm 7: Arithmetic Barrett.
Data: JaK,m,n
Result: JrK = JaK mod n
1 Jari aK ← BtoA(JaK);
2 Jari qK ← Jari aK × m ; /* Multiplication
on each share */
3 JqK ← AtoB(Jari qK);
4 JqK ← JqK ≫ 32
5 Jari qK ← BtoA(JqK);
6 Jari qnK ← Jari qK × n;
7 Jari a qnK ← Jari aK − Jari qnK;
/* Sharewise subtraction */
8 Ja qnK ← AtoB(Jari a qnK);
9 minus n ← 2
32
− n;
10 JAK ← sec
+
(Ja qnK,minus n);
11 JzK ← JAK ≫ 31;
12 JAK ← refresh(JAK);
13 Ja qnK ← refresh(Ja qnK);
14 JrK ← sec
i f
(Ja qnK,JAK, JzK);
(a) with masks set to zero.
(b) with random masks.
Figure 2: TVLA of the masked Barrett reduction with mask
conversions.
4.2 Performance Comparison
In Table 1, we compare the performance of the sam-
pling of random vectors with weight 75 in five dif-
ferent settings: the HQC and BIKE reference imple-
mentations, HQC with our Barrett reduction masked
at order one in boolean and arithmetic masking, and
the Demange and Rossi masking scheme for BIKE.
The following results were all obtained with the -Og
compilation flag.
Our fully boolean masked solution is 51% more
computationally intensive compared to the one pro-
posed for BIKE. This is due to the fact that BIKE
specification only requires a masked multiplication
Table 1: Comparison of the number of cycles needed to
sample a random vector of weight w = 75 (ARM Cortex-
M4 @180 MHz, caches ON).
Vector sampling Cycles Overhead
HQC 747,500 −
HQC Boolean Barrett 17,496,000 2340%
HQC Arithmetic Barrett 12,203,000 1632%
BIKE 746,500 −
BIKE Boolean 11,606,000 1554%
and a shift. In comparison, following HQC spec-
ification requires to execute the entire masked Bar-
rett reduction (Algorithm 6). However, by using the
arithmetic masking to accelerate the multiplications,
our second solution achieves a performance only 5%
slower than BIKE, despite the conversions. The im-
pact of our second solution on the performance is thus
limited while providing the key advantage of preserv-
ing the HQC specification.
5 CONCLUSION
This paper proposes a first masked version of
HQC vector sampling, based on Demange and
Rossi’s SecFisherYates, and new gadgets that
we introduce, mainly the masked Barrett reduction,
which was not publicly available so far. Adapting
SecFisherYates to HQC is now as simple as replac-
ing Line 2 in Algorithm 2 with our masked Barrett
reduction.
Moreover, we developed a faster version with
mask conversions and multiplications under arith-
metic masking. We underline that BIKE’s vector sam-
pling could as well benefit from this acceleration.
The security assessment of our modular Barrett re-
duction is two-fold: we provide a security proof for
our new gadgets, and we perform a practical side-
channel evaluation on an STM32 device, that shows
the absence of remaining leakages in this specific set-
ting. This practical evaluation raises some warnings
about compiler options, since some leakage appears
with aggressive compiler optimization settings. It re-
minds the importance of practical validations.
We provide a publicly available C implementa-
tion. Vector sampling is only a part of the HQC al-
gorithms. Even if side-channel resistant implementa-
tions of some other parts of HQC have been studied
in (Goy et al., 2022), building a full HQC masked im-
plementation is still let as future work.
Masked Vector Sampling for HQC
755

ACKNOWLEDGMENTS
This work was partially funded by the grant 2022154
from the Appel
`
a projets 2022 th
`
eses AID Cifre-
D
´
efense by the Agence de l’Innovation de D
´
efense
(AID), Minist
`
ere des Arm
´
ees (French Ministry of De-
fense). We wish to thank Beno
ˆ
ıt Cogliati for helpful
discussions.
REFERENCES
(2016). Announcing request for nominations for
public-key post-quantum cryptographic al-
gorithms. https://csrc.nist.gov/News/2016/
Public-Key-Post-Quantum-Cryptographic-Algorithms.
(2022). Pqc standardization process: Announcing
four candidates to be standardized, plus fourth
round candidates. https://csrc.nist.gov/News/2022/
pqc-candidates-to-be-standardized-and-round-4.
(2023). The ibm quantum development roadmap. https:
//www.ibm.com/quantum/roadmap.
(2024). Announcing approval of three federal in-
formation processing standards (fips) for post-
quantum cryptography. https://csrc.nist.gov/News/
2024/postquantum-cryptography-fips-approved.
(2024). masked bike code. https://github.com/loicdemange/
masked BIKE code.
(2025). Nist selects hqc as fifth algorithm
for post-quantum encryption. https:
//www.nist.gov/news-events/news/2025/03/
nist-selects-hqc-fifth-algorithm-post-quantum-encryption.
Alagic, G., Apon, D., Cooper, D., Dang, Q., Dang, T.,
Kelsey, J., Lichtinger, J., Miller, C., Moody, D., Per-
alta, R., et al. (2022). Status report on the third round
of the nist post-quantum cryptography standardization
process. US Department of Commerce, NIST.
Balasch, J., Gierlichs, B., Grosso, V., Reparaz, O., and Stan-
daert, F.-X. (2015). On the cost of lazy engineering
for masked software implementations. In Joye, M.
and Moradi, A., editors, Smart Card Research and
Advanced Applications, pages 64–81, Cham. Springer
International Publishing.
Barrett, P. (1987). Implementing the rivest shamir and adle-
man public key encryption algorithm on a standard
digital signal processor. In Odlyzko, A. M., editor,
Advances in Cryptology — CRYPTO’ 86, pages 311–
323, Berlin, Heidelberg. Springer Berlin Heidelberg.
Barthe, G., Bela
¨
ıd, S., Dupressoir, F., Fouque, P.-A.,
Gr
´
egoire, B., Strub, P.-Y., and Zucchini, R. (2016).
Strong non-interference and type-directed higher-
order masking. In Proceedings of the 2016 ACM
SIGSAC Conference on Computer and Communica-
tions Security, CCS ’16, page 116–129, New York,
NY, USA. Association for Computing Machinery.
Ba
¨
ısse, C., Moran, A., Goy, G., Maillard, J., Aragon, N.,
Gaborit, P., Lecomte, M., and Loiseau, A. (2024).
Secret and shared keys recovery on hamming quasi-
cyclic with sasca. Cryptology ePrint Archive, Paper
2024/440. https://eprint.iacr.org/2024/440.
Becker, G. T., Cooper, J., DeMulder, E. K., Goodwill, G.,
Jaffe, J., Kenworthy, G., Kouzminov, T., Leiserson,
A. J., Marson, M. E., Rohatgi, P., and Saab, S. (2013).
Test vector leakage assessment ( tvla ) methodology
in practice.
Chari, S., Jutla, C. S., Rao, J. R., and Rohatgi, P. (1999). To-
wards sound approaches to counteract power-analysis
attacks. In Advances in Cryptology—CRYPTO’99:
19th Annual International Cryptology Conference
Santa Barbara, California, USA, August 15–19, 1999
Proceedings 19, pages 398–412. Springer.
Coron, J.-S. (2013). Higher order masking of look-up ta-
bles. Cryptology ePrint Archive, Paper 2013/700.
https://eprint.iacr.org/2013/700.
Coron, J.-S., Giraud, C., Prouff, E., Renner, S., Rivain,
M., and Vadnala, P. K. (2012). Conversion of secu-
rity proofs from one leakage model to another: A new
issue. In Schindler, W. and Huss, S. A., editors, Con-
structive Side-Channel Analysis and Secure Design,
pages 69–81, Berlin, Heidelberg. Springer Berlin Hei-
delberg.
Coron, J.-S., Großsch
¨
adl, J., and Vadnala, P. K. (2014).
Secure conversion between boolean and arithmetic
masking of any order. In International Workshop
on Cryptographic Hardware and Embedded Systems,
pages 188–205. Springer.
Demange, L. and Rossi, M. (2024). A provably masked im-
plementation of bike key encapsulation mechanism.
Cryptology ePrint Archive.
Gigerl, B., Hadzic, V., Primas, R., Mangard, S., and Bloem,
R. (2021). Coco: Co-Design and Co-Verification of
masked software implementations on CPUs. In 30th
USENIX Security Symposium (USENIX Security 21),
pages 1469–1468. USENIX Association.
Goubin, L. and Patarin, J. (1999). Des and differential
power analysis the “duplication” method. In Crypto-
graphic Hardware and Embedded Systems: First In-
ternationalWorkshop, CHES’99 Worcester, MA, USA,
August 12–13, 1999 Proceedings 1, pages 158–172.
Springer.
Goy, G., Loiseau, A., and Gaborit, P. (2022). A new key re-
covery side-channel attack on hqc with chosen cipher-
text. In International Conference on Post-Quantum
Cryptography, pages 353–371. Springer.
Goy, G., Maillard, J., Gaborit, P., and Loiseau, A. (2024).
Single trace hqc shared key recovery with sasca. IACR
Transactions on Cryptographic Hardware and Em-
bedded Systems, 2024(2):64–87.
Guo, Q., Hlauschek, C., Johansson, T., Lahr, N., Nilsson,
A., and Schr
¨
oder, R. L. (2022). Don’t reject this: Key-
recovery timing attacks due to rejection-sampling in
hqc and bike. IACR Transactions on Cryptographic
Hardware and Embedded Systems, pages 223–263.
Kannwischer, M. J., Petri, R., Rijneveld, J., Schwabe, P.,
and Stoffelen, K. PQM4: Post-quantum crypto library
for the ARM Cortex-M4. https://github.com/mupq/
pqm4.
SECRYPT 2025 - 22nd International Conference on Security and Cryptography
756

Kocher, P. C. (1996). Timing attacks on implementations
of Diffie-Hellman, RSA, DSS, and other systems. In
Annual International Cryptology Conference, pages
104–113. Springer.
Melchor, C. A., Aragon, N., Bettaieb, S., Bidoux, L.,
Blazy, O., Deneuville, J.-C., Gaborit, P., Persichetti,
E., Z
´
emor, G., and Bourges, I. (2018). Hamming
quasi-cyclic (hqc). NIST PQC Round, 2(4):13.
Paiva, T. B. and Terada, R. (2020). A timing attack on
the hqc encryption scheme. In Selected Areas in
Cryptography–SAC 2019: 26th International Confer-
ence, Waterloo, ON, Canada, August 12–16, 2019,
Revised Selected Papers 26, pages 551–573. Springer.
Regev, O. (2023). An Efficient Quantum Factoring Algo-
rithm.
Schneider, T. and Moradi, A. (2016). Leakage assessment
methodology: Extended version. Journal of Crypto-
graphic Engineering, 6:85–99.
Sendrier, N. (2021). Secure sampling of constant-weight
words–application to bike. Cryptology ePrint Archive.
Wafo-Tapa, G., Bettaieb, S., Bidoux, L., Gaborit, P., and
Marcatel, E. (2019). A practicable timing attack
against hqc and its countermeasure. Cryptology ePrint
Archive.
A APPENDICES
A.1 HQC
Algorithm 8: HQC.KeyGen.
Data: R
Result: sk, pk
1 h = Sample(R );
2 x = Sample(R , ω);
3 y = Sample(R , ω);
4 σ = rand(F
k
2
);
5 sk = (x,y,σ);
6 pk = (h,s = x + h · y);
Algorithm 9: HQC.Encrypt.
Data: pk,m,θ
Result: c = (u,v)
1 r
1
= Sample(θ, ω
r
);
2 r
2
= Sample(θ, ω
r
);
3 e = Sample(θ,ω
e
);
4 u = r
1
+ h · r
2
;
5 v = C .Encode(m) + s · r
2
+ e;
Algorithm 10: HQC.Decrypt.
Data: sk,c
Result: m
1 m = C .Decode(v − u · y);
Algorithm 11: HQC.Encaps.
Data: pk
Result: K, c,salt
1 m = rand(F
k
2
);
2 salt = rand(F
128
2
);
3 θ = G(m∥firstBytes(pk)∥salt);
4 c = HQC.Encrypt(pk,m,θ);
5 K = K (m,c);
Algorithm 12: HQC.Decaps.
Data: sk,c,salt
Result: K
1 m
′
= HQC. Decrypt(sk, c);
2 θ
′
= G(m
′
∥firstBytes(pk)∥salt);
3 c
′
= HQC. Encrypt(pk,m
′
,θ
′
);
4 if m
′
=⊥ ∨ c ̸= c
′
then
5 K = K (σ,c);
6 end
7 else
8 K = K (m,c);
9 end
Algorithm 13: sec
−
(JaK,JbK) (secure minus).
Data: JaK, JbK
Result: JrK = JaK − JbK
1 JnbK ← JbK;
2 JnbK
0
← ¬JnbK
0
; /* NOT of the first
share */
3 JmbK ← sec
+
(JnbK,1) ; /* −b = (¬b) + 1
*/
4 JrK ← sec
+
(JaK,JmbK);
Theorem 2. The masked subtraction Algorithm 13 is
t-NI.
Proof. The only gadget manipulating the data is
sec
+
, which is t-NI, and the negation is linear and
only manipulates the first share.
A.2 Example of Leak Introduced by the
Compiler Optimizations
When testing our solution with the more aggressive
-O3 compilation option we discovered that the com-
piler decided to reuse the same register for two shares
as can be seen on Listing 1. Since we use a first or-
der masking, the transition between the two states of
the register induces a XOR between the two values,
which unmasks the secret as illustrated by Figure 3.
On Line 6, the value of y[0] is loaded in r2 then
on Line 8 the value of y[1] is loaded in r2. Physi-
cally, for the register to switch from the value y[0] to
Masked Vector Sampling for HQC
757

Figure 3: TVLA of the masked Barrett reduction compiled
with -O3.
y[1] there is an implicit XOR between the two val-
ues. As y = y[0] ⊕ y[1], for all 0-bits of y there is no
transition (that is, no consumed energy) between the
corresponding bits of y[0] and y[1], while for all 1-
bits of y there is a transition from 0 to 1 or from 1 to
0, that consumes energy.
This involuntarily exposes the secret y and advo-
cates for further analyses on the assembly code, on
the linked and loaded binary or even on the actual
execution by the processor as proposed for instance
by (Gigerl et al., 2021). Increasing the masking or-
der, as suggested by (Balasch et al., 2015), is another
option but it is costly.
1 < boolean_sec_and >:
2 push { r3 ,r 4 , r5 ,r6 , r7 , lr}
3 mo v r5 , r1 ; stor e y a dd re ss in
r5
4 ldrd r1 , r3 ,[ r0 ] ; r1 = x [0] , r3 = x
[1]
5 mo v r4 , r2
6 ld r r2 ,[ r5 , #0] ; r2 = y [ 0]
7 ands r1 , r2 ; r1 = x [0] & y [0]
8 ld r r2 ,[ r5 , #4] ; r2 = y [ 1]
9 .. .
Listing 1: Abstract of the assembly code of sec
&
for -O3.
SECRYPT 2025 - 22nd International Conference on Security and Cryptography
758
