
Image Constraint Technique Used by Bio-Inspired TSA Optimized
Algorithm for Large Memory Management
Sachin More
a
and Dayanand Ingle
b
Bharati Vidyapeeth College of Engineering, Mumbai University, CBD Belapur, Navi Mumbai, India
Keywords: Image quality, Image Compression, Resolution Scalable Image Compression, Quality Scalable Image
Compression, Highly Scalable Image Compression and TSA Optimized Discrete Wavelet Transform.
Abstract: The well-known classical image compression algorithms are renowned for their outstanding performance,
low computational complexity, and production of an embedded bitstream that can be decoded at different bit
rates with progressively better picture quality more bits are received. It takes a lot of computer memory since
it stores the created sets and the pixel locations in linked lists. The transform's multiresolution capability does
not lead to the generation of a resolution-scalable bitstream that would enable different resolutions to decode
the image. The TSA Optimized Discrete Wavelet Transform approach, which only needs one list of fixed size
measuring 1/4 the size of the image and an average of 2.25 bits/pixel, solves the massive memory problem of
traditional techniques. The study's main contribution is to scale up image quality and resolution in order to
free up more memory. The TSA Optimized Discrete Wavelet Transform approach is recommended in this
study to decrease complexity and increase speed. Due to the algorithm's special characteristics, it is ideal for
addressing the different skills and resolution related preferences of today’s Internet users.
1 INTRODUCTION
The fundamental purpose of lossy image compression
is to decrease the distinction between the unique and
recovered photographs even as also reducing the
common quantity of bits in step with the pixel of the
compressed photo as a good deal as viable. The MSE
among those pictures, or suggest squared errors, is
usually used to quantify the disparity. The
computational complexity and reminiscence use of an
image compression method are extra important
components. For this reason, most of these elements
need to be considered for any algorithm to be truly
judged
(Jayasankar, 2012).
A picture may be recovered the use of a traditional
photo compression scheme at a single bitrate
(pleasant) and resolution (size). This compression
paradigm might not work for all customers because
the existing purchaser base has a wide range of
bandwidth, show resolution, computing power, and
memory capacities. Moreover, clients want to rapid
look through all the searched photographs while
viewing snapshots at the net in advance than choosing
a
https://orcid.org/0000-0003-4077-2251
b
https://orcid.org/0000-0002-2654-3279
the specified image(s). Adopting this approach of
picture compression will bring about time,
bandwidth, memory, and processing electricity
losses. But a scalable image compression gadget
permits the setup person to decode the photo at an
appropriate excellent or/and determination through
controlling the recovered image's outstanding or/and
resolution (length). Most effective the first-rate. By
the usage of the usage of some sorts a QSIC may be
completed. However, the selection of the recovered
image may be modified (Taubman, 2002). Due to the
HSIC's potential to decode snap shots of various best
and resolutions, it's miles specifically appealing to the
desires of cutting-edge clients.
A picture may be recovered the use of a traditional
image compression scheme at an single bitrate (nice)
and backbone (length). This compression paradigm
may not art work for all customers due to the reality
the prevailing character base has a great type of
bandwidth, show selection, computing strength, and
reminiscence capacities. Furthermore, consumers
want to fast look through all the searched snap shots
More, S. and Ingle, D.
Image Constraint Technique Used by Bio-Inspired TSA Optimized Algor ithm for Large Memory Management.
DOI: 10.5220/0013606900004664
Paper published under CC license (CC BY-NC-ND 4.0)
In Proceedings of the 3rd International Conference on Futuristic Technology (INCOFT 2025) - Volume 2, pages 897-903
ISBN: 978-989-758-763-4
Proceedings Copyright © 2025 by SCITEPRESS – Science and Technology Publications, Lda.
897
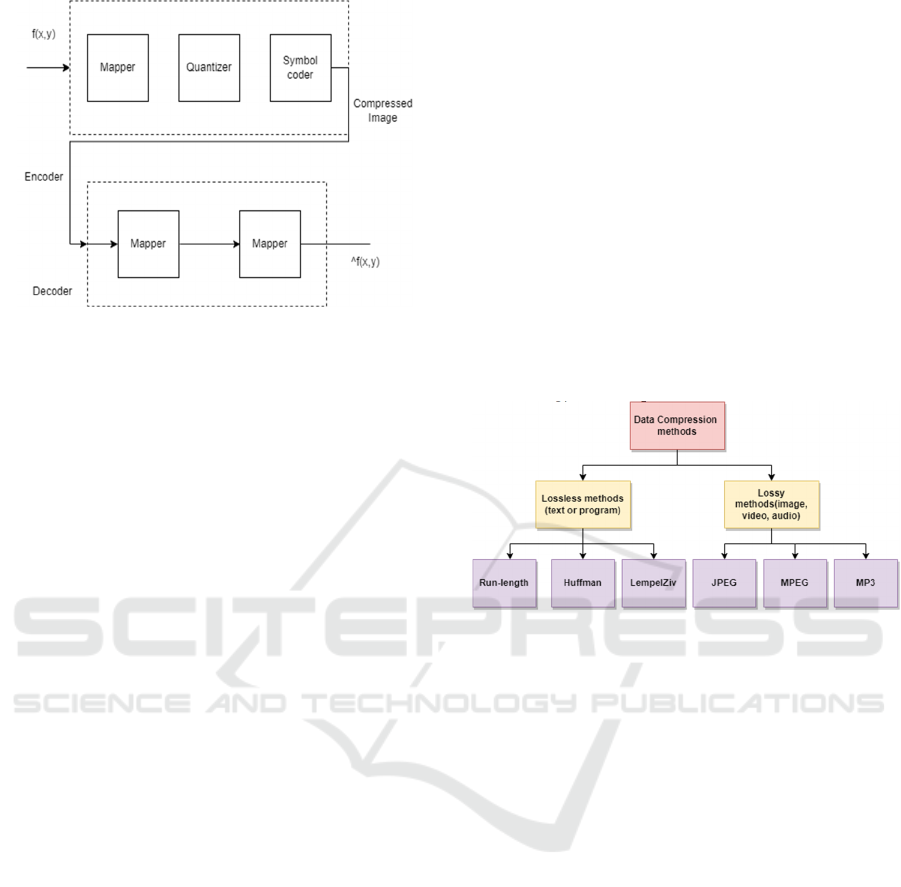
Figure 1: Conventional Image Compression Diagram
while viewing pics on the net earlier than selecting
the required image(s). Certainly, adopting this
technique of photo compression will bring about
time, bandwidth, memory, and processing strength
losses. Instead, a scalable image compression tool
allows the end person to decode the photo at the
suitable extraordinary or/and determination by way of
manner of controlling the recovered photo
satisfactory or/and determination (duration) (Said and
Pearlman, 1996; Lee and Hung, 2019). Because of the
HSIC's capability to decode photographs of diverse,
first-rate resolutions, it is mainly attractive for the
needs of contemporary customers.
The aim of this commentary was modified to
signify a picture compression technique that would
permit large reminiscence space to be maintained
while lowering reminiscence length. The endorsed
compression approach consists of an single image
compression approach and a bit-feet approach for
keeping the compression ratio and uniformity of
photograph excellence at some point of the photo.
The suggested machine, at the facet of the bit fee
management technique, continues widely talking
using the facts collected inside the contemporary
frame. So that you can similarly improve picture
excellence, the approach, also determines series. This
may be completed by using something as
fundamental as the photograph. It can drastically
reduce the problem of image-satisfying imbalance
photograph, a flaw in low-reminiscence compression
strategies that is unavoidable.
The remaining sections of the paper are as
follows: Background material and common
compression techniques are given in Section 2 of this
essay. Section 3 provides a description of the
suggested compression scheme with memory
management. The approach is assessed and the
findings are discussed in Section 4. This essay
concludes in Section 5.
2 LITERATURE SURVEY
Based on zero tree capabilities of wavelet
coefficients, the 1D SPIHT approach (Lee and Hung,
2019) is used. This technique creates 3 dynamic lists
via frequently crossing better bit to the decrease bit
plane to send important bit facts first, enhancing
compression efficiency. This method is simple to use
and proof in opposition to transmission faults.
Because of its prolonged memory accesses at some
point of the repetitious manner coding, the 1D SPIHT
compression technique, nevertheless, incurs good
sized energy consumption
Figure 2: Different Techniques of Image Compression.
The visually lossless compression approach of
line compression emerges as located out in
(Umbaugh, 2023). Whilst errors are harder to
identify, this approach might also carry out median
component detection (MED) prediction of 2 4 blocks.
It could also perform MED prediction of one–four
blocks in complexity and diploma places in which
errors are apparent. After the information has been in
addition compressed through way of a preset non-
uniform quantization step. A frequency adaptive line
compression (FALC) method with less complexity in
evaluation to modern compression techniques has
been suggested in (Chew, 2009). The FALC approach
uses entire after four stages of wavelet adjustments.
The fourth step involves selective zero-area
quantization within the four immoderate-frequency
bands. Redundancy inside the low-frequency
variability has eliminated using predictive coding.
Then, using a Huffman coding-based totally variable
duration coding (VLC) technique, data from every
frequency band are compressed. With a visually
lossless nation, FALC's compression ratio exceeds
3:1. To actively keep more power in contexts in
which IoT programs are used, but, extra advancement
is needed.
INCOFT 2025 - International Conference on Futuristic Technology
898
Because of the reality every line, even inside a
single frame, has precise homes in phrases of
compression effectiveness, the picture high-quality of
the road-based totally compression algorithms
regularly modifications at some stage in a single
body. Both Jiang's and Edirisinghe's line-based
totally bit charge manipulates (BRC) were proposed
for use in the JPEG-LS context (Deepthi and Prasad,
2018). But, in terms of uniformity inside a single
frame, those BRCs lack ok photograph well.
Primarily based at the cutting-edge-day FALC
method, a one-of-a-type bit rate management
mechanism (Al-Janabi and Harbi, 2022) has been
cautioned to decorate the consistency of photograph
fantastic inside one frame. The quantization degree
shift is saved sluggish. Whilst thirds of the frame have
been processed, it additionally evaluates the picture
exquisite and the closing bits to decide the proper
quantization degree to be able to use up the very last
bits.
However, modern-day BRC strategies
nonetheless warfare with inconsistent image
satisfactory, especially whilst scenes or pics are
separated. Consequently, TSA desires to be more
suitable greater earlier than it may be used for
consumer goods
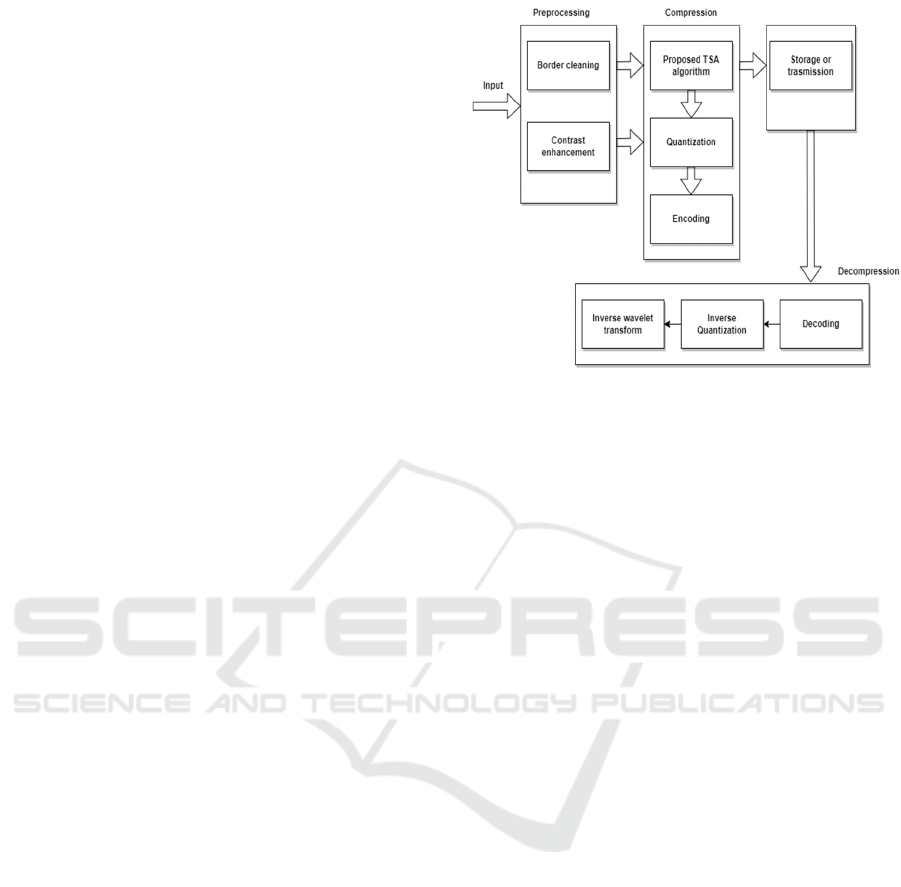
3 PROPOSED METHODOLOGY
The TSA Optimized Discrete Wavelet remodel
techniques are to begin with brought on this section.
In comparison to the alternative techniques, the TSA
Optimized Discrete Wavelet redecorate, set of
guidelines is drastically much less complicated and
plays slightly higher. The number one contribution of
the research is then provided, that is the advised TSA
Optimized Discrete Wavelet rework method for
memory control. A particularly scalable bitstream,
this is each high-quality and backbone scalable in
addition to less in duration and taking on greater
RAM is created by using the usage of the TSA
Optimized Discrete Wavelet remodel set of
regulations.
One of the population-based algorithms is TSA
(Tree Seed Algorithm), and the population will be
referred to as stand moving forward. Eq. 1 (Meraj and
Khan, 2021) is used to derive the stand.
a =𝑇
,
=𝐿
+𝑟
,
×𝑈
−𝐿
, 𝑖 =
1,2,…….,𝑁 𝑎𝑛𝑑
𝑗
=1,2,…..,𝐷
(1
)
Figure 3: Proposed Block Diagram of this Work.
Following the production of the bushes within the
stand, the fitness values of the trees are decided the
usage of a goal characteristic tailor-made to the
optimization mission.
Via utilizing Eq. 2 or three, a positive range of
seeds is generated for every tree at the same time as a
preset termination circumstance is glad (Al-Janabi,
2013)
𝑆
,
=𝑇
,
+𝛼
,
×(𝐵
−𝑇
,
) (2)
𝑆
,
=𝑇
,
+𝛼
,
×(𝑇
,
−𝑇
,
) (3)
The choice of Eqs. 2 or 3 relies upon on a TSA
manage parameter. The ST (search tendency)
manipulate parameter has a variety of [0,1]. If it is
miles vital to intensify the stand across the ideal tree
placement, a high fee for the ST parameter should be
selected. If the stand's exploration ability is extended,
the ST parameter should be set to a low fee. A random
wide variety within the range [0,1] is created for the
selection of equations 2 or 3. The Eq. 2 is selected if
this fee is much less than ST; in any other case, the
Eq. Three is chosen. In a nutshell, the ST parameter
is utilized to modify the stand's potential for
exploration and exploitation. The usage of the
number of seeds can in addition beautify the local
seek abilities around the tree websites. The minimum
and the greatest number of seeds in the TSA
algorithm are 10% of the timber and 25% of the trees,
respectively. Therefore, based totally at the stand, the
number of seeds is determined (Alam and Khan,
2012).
Image Constraint Technique Used by Bio-Inspired TSA Optimized Algorithm for Large Memory Management
899
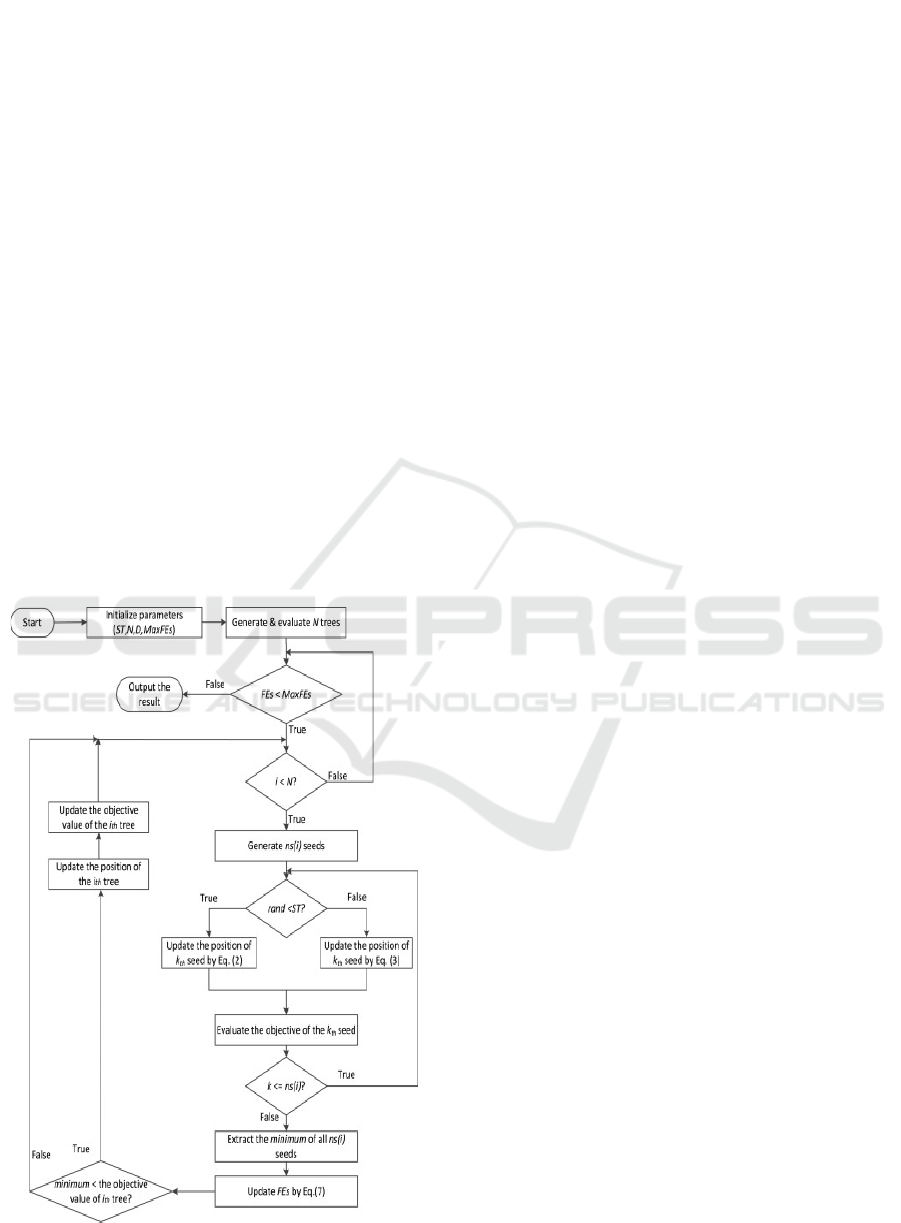
The quest method and equations defined above
are iterated sequentially after the set of rules is
initialized, if a predefined termination situation is
happy.
• Step 1 select the general populace length
(filter out window length), ST Values, and
termination situation.
• Step 2: Initialize the populace in accordance
with the supplied Eqs. (2) and (3).
• Step 3: the usage of the Eqs. (3) based on the
values of ri;j and ST, create seed values for
the modern tree values. If the seed values
supplied progressed health in comparison to
the unique tree values, replace the tree values.
• Step 4: the usage of Eq. (3), pick out the
premier cost and confirm the termination
circumstance.
• Step 5: Assign the optimized values and
record the outcome if the termination
situation is happy; in any other case, repeat
steps 2, three, and four
Figure 4: Tree Seed Algorithm Flowchart.
1. Select the best axolotls, according to
the
f
unction
2. For each axolotl with optimization
value 1≤
𝑗
≤
|
𝑀
|
Compute inverse probability of
transition
If each component I of the current
axolotl as n
Update the optimization value
Update
𝑓
Even as a tree generates new seed web sites, there
can be several seeds present; the variety of seeds
depends on the dimensions of the population. The
bottom wide type of seeds that may be generated
through a set of rules inside the right manner. Eq. (3)
is utilized for if a randomly generated integer in the
range [0, 1] is smaller than ST
.
The suggested method for selecting the best
compression, placing is depicted in determining
Preceding to sending records to the receiver, the
endorsed approach can shop for separately
compressed image statistics using the further
effective compression method is selected because the
output value thru the comparator in the middle, which
forecasts and compares the bits produced through
each compression mode. For images with extra stated
characteristic changes among picture traces, together
with the recommended technique can make sure a
more compression overall performance.
The counselled solution tries to apply get a higher
compression ratio; it then chooses this sort of
predictive coding options that is minimal in length.
Due to the fact differential values exhibited much less
correlations inside the vertical course after making
use of the horizontal predictive coding, we did not use
each prediction modes simultaneously.
Based at the average strength of the H1 bands
from the preceding body, the cautioned approach also
forecasts an regular compression outline for the
present frame. Two centre subsections of the previous
frame's many subsections are examined to look if a
split mode exists. Break up mode may be dealt with
by means of way of the recommended TSA optimized
algorithm technique in a single body. In among
successive frames, it could additionally deal with
scene modifications. If resource of an additional than
a threshold cost (TH) in advance than the closing
quarter of the frame, the scene has altered. If a scene
change happens interior a body, the default TCR
charge (4.00) is used to compress the closing areas.
Moreover, through manner of the usage of break up
mode, this method helps forestall unneeded image
INCOFT 2025 - International Conference on Futuristic Technology
900
best deterioration delivered on by scene changes
among frames.
4 RESULTS AND DISCUSSION
Because of the several problematic interactions
between applications, this section can estimate the
electricity intake of an set of rules running on a goal
embedded system whilst warding off considerable
estimation deviation (Calderbank, 1998). The mean
squared blunders (MSE) among the preliminary N
pixels is used to gauge overall performance. Image
(Io) and the reconstructed image (Ir), each of size M,
are described as MSE as (Hu and Yang, 2020):
𝑀𝑆𝐸 =
1
𝑀𝑁
[𝐼
(
𝑖,
𝑗
)
−𝐼
(𝑖,
𝑗
)
]
(4
)
𝑃𝑆𝑁𝑅 = 10𝑙𝑜𝑔
𝑑𝑒𝑐𝑖𝑏𝑒𝑙
(
𝑑𝑏
)
(5)
𝑀𝐸𝑀
== 2𝑏
(
2𝑁
)
+2𝑐
=4𝑏𝑁
+
𝑐
=
4𝑏 +
𝑁
𝑏𝑖𝑡 (6)
Table 1: PSNR values evaluated for existing and proposed
algorithm.
Bit
rate
(
Bpp)
Encoding time
(
seconds
)
Decoding time
(
seconds
)
Lena Goldhill
SPIHT
(Harbi,2
022)
SLS
(Sara,
2019)
TSA
(Prop
osed)
SPIHT
(Harbi,
2022)
SLS
(Sara,
2019)
TSA
(Propo
sed)
0.06 0.74 0.72 0.52 0.34 0.068 0.020
0.11 1.17 1.14 1.40 0.561 0.082 0.051
0.15 1.06 1.05 1.00 1.000 0.077 0.130
0.5 2.21 2.20 2.15 1.717 0.112 0.175
1 4.60 4.55 3.45 3.400 0.445 0.237
Table 2: Memory necessities of TSA, LHS-TSA, and the
proposed HS-MSLS for different image sizes (Wu and
Wang, 2013)
Image
size
Memory (kb)
TSA LHS-TSA HS-MSLS
(Song, 2017)
MEM
(kb)
% MEM
(kb)
% MEM
(kb)
%
256×256
273 2.12 31 0.24 45 0.35
512×512
1270 2.40 127 0.24 200 0.38
1024×1024
5685 2.67 511 0.24 653 0.41
Table 3: Current and planned algorithms, complexity is expressed by the encoding time and decoding time against the bit
rate
Bit
rate
(Bpp)
PSNR (db)
Lena Goldhill Barbara
SPIHT
(Harbi,
2022)
SLS
(Sara,
2019)
TSA
(Proposed)
SPIHT
(Harbi,
2022)
SLS
(Sara,
2019)
TSA
(Proposed)
SPIHT
(Harbi,
2022)
SLS
(Sara,
2019)
TSA
(Proposed)
0.0615 25.61 26.46 27.69 25.16 25.18 25.25 22.17 22.20 22.50
0.115 28.38 30.14 31.19 26.66 26.69 26.75 23.26 23.31 23.46
0.15 31.61 32.00 34.17 28.65 28.67 28.78 25.86 25.89 25.93
0.5 35.12 35.20 37.41 31.16 31.18 31.30 30.87 30.90 30.96
1 38.40 38.51 39.72 34.41 34.45 34.56 35.15 35.21 35.35
Image Constraint Technique Used by Bio-Inspired TSA Optimized Algorithm for Large Memory Management
901

5 CONCLUSIONS
In this research, a compression approach with bit rate
control was presented for size reduction in memory
management contexts. Given the power constraints of
the memory management environment, the suggested
TSA algorithm employs a low-complexity approach
with the fewest number of processes and memory
accesses. Based on the results of our tests, the
suggested solution outperformed existing methods in
terms of compression ratio while keeping a lower
level of complexity. In terms of size reduction effect
at the system level, it performed better than existing
SPIHT or 4L HEVC methods. In cases where there is
a high/low quality imbalance, picture split mode, and
scene transitions, which frequently occur in
conventional line compression methods, it may retain
superior restorative and constant image quality
performance.
REFERENCES
Jayasankar, U., Thirumal, V., & Ponnurangam, D. (2021).
A survey on data compression techniques: From the
perspective of data quality, coding schemes, data type
and applications. Journal of King Saud University-
Computer and Information Sciences, 33(2), 119-140/
Thanki, R. M., & Kothari, A. (2019). Hybrid and advanced
compression techniques for medical images. Springer
International Publishing
Taubman, D., Ordentlich, E., Weinberger, M., & Seroussi,
G. (2002). Embedded block coding in JPEG
2000. Signal Processing: Image
Communication, 17(1), 49-72.
Rüefenacht, D., Naman, A. T., Mathew, R., & Taubman, D.
(2019). Base-anchored model for highly scalable and
accessible compression of Multiview imagery. IEEE
Transactions on Image Processing, 28(7), 3205-3218.
Van Fleet, P. J. (2019). Daubechies Wavelet
Transformations.
Vetterli, M. (1995). Wavelets and sub band coding.
Said, A., & Pearlman, W. A. (1996). A new, fast, and
efficient image codec based on set partitioning in
hierarchical trees. IEEE Transactions on circuits and
systems for video technology, 6(3), 243-250.
Lee, R. C., & Hung, K. C. (2019). New modified SPIHT
algorithm for data compression system. Journal of
Medical and Biological Engineering, 39, 18-26.
Khan, E., & Ghanbari, M. (2004). An efficient and scalable
low bit-rate video coding with virtual SPIHT. Signal
Processing: Image Communication, 19(3), 267-283.
Senapati, R. K., Pati, U. C., & Mahapatra, K. K. (2012).
Listless block-tree set partitioning algorithm for very
low bit rate embedded image compression. AEU-
International Journal of Electronics and
Communications, 66(12), 985-995.
Umbaugh, S. E. (2023). Digital image processing and
analysis: computer vision and image analysis. CRC
Press.
Chew, L. W., Ang, L. M., & Seng, K. P. (2009, August).
Reduced memory spiht coding using wavelet transform
with post-processing. In 2009 International Conference
on Intelligent Human-Machine Systems and
Cybernetics (Vol. 1, pp. 371-374). IEEE.
Deepthi, S. A., Rao, E. S., & Prasad, M. G. (2018, January).
Image transmission and compression techniques using
SPIHT and EZW in WSN. In 2018 2nd International
Conference on Inventive Systems and Control
(ICISC) (pp. 1146-1149). IEEE.
Alam, M., Khan, E., & Gopal, B. (2012). Modified listless
set partitioning in hierarchical trees (MLS) for memory
constrained image coding applications. Current Trends
in Signal Processing, 2(2), 56-66.
Al-Janabi, A. K., Al-Musawi, H. K., & Harbi, Y. J. (2022).
An efficient and highly scalable listless SPIHT image
compression framework. Journal of applied research
and technology, 20(2), 173-187.
Meraj, Y., & Khan, E. (2021, March). Modified ZM-
SPECK: A low complexity and low memory wavelet
image coder for VS/IoT Nodes. In 2021 International
Conference on Emerging Smart Computing and
Informatics (ESCI) (pp. 494-500). IEEE.
Al-Janabi, A. K. (2013). Low memory set-partitioning in
hierarchical trees image compression
algorithm. International Journal of Video & Image
Processing and Network Security IJVIPNS-
IJENS, 13(2), 12-18.
Alam, M., & Khan, E. (2012). Listless Highly scalable set
partitioning in hierarchical trees coding for
transmission of image over heterogenous
networks. International Journal of Computer
Networking, Wireless Mobile Commun.
Danyali, H., & Mertins, A. (2004). Flexible, highly
scalable, object-based wavelet image compression
algorithm for network applications. IEE Proceedings-
Vision, Image and Signal Processing, 151(6), 498-510.
Calderbank, A. R., Daubechies, I., Sweldens, W., & Yeo,
B. L. (1998). Wavelet transforms that map integers to
integers. Applied and computational harmonic
analysis, 5(3), 332-369.
Hu, Y., Yang, S., Yang, W., Duan, L. Y., & Liu, J. (2020,
July). Towards coding for human and machine vision:
A scalable image coding approach. In 2020 IEEE
International Conference on Multimedia and Expo
(ICME) (pp. 1-6). IEEE.
Al-Janabi, A. K., Al-Musawi, H. K., & Harbi, Y. J. (2022).
An efficient and highly scalable listless SPIHT image
compression framework. Journal of applied research
and technology, 20(2), 173-187.
Sara, U., Akter, M., & Uddin, M. S. (2019). Image quality
assessment through FSIM, SSIM, MSE and PSNR—a
comparative study. Journal of Computer and
Communications, 7(3), 8-18.
Wu, D., Zhang, H., Li, X., & Wang, J. (2013, June).
Multiview Video Coding Based on Wavelet Pyramids.
INCOFT 2025 - International Conference on Futuristic Technology
902

In 2013 International Conference on Computational
and Information Sciences (pp. 225-228). IEEE.
Song, X., Huang, Q., Chang, S., He, J., & Wang, H. (2017).
Three‐dimensional separate descendant‐based SPIHT
algorithm for fast compression of high‐resolution
medical image sequences. IET Image
Processing, 11(1), 80-87.
Image Constraint Technique Used by Bio-Inspired TSA Optimized Algorithm for Large Memory Management
903
