
Stack Tracer: Dual-Phase Steganalysis and Malware Detection for
Multimedia Security
K. Rithik Karthikeyan
a
, M. B. Manav Srinivas
b
and A. Jenifer
c
Artificial Intelligence and Data Science, St. Joseph’s Institute of Technology, Chennai, India
Keywords:
Steganalysis, Hidden Data Detection, Multimedia Security, Browser Extension, VirusTotal Integration,
Malware Analysis, Technical Analysis Tools, Real-Time Threat Assessment, Cybersecurity, Data Hiding
Techniques.
Abstract:
The increasing use of steganographic techniques to embed hidden and potentially harmful data within mul-
timedia files poses significant challenges to cybersecurity. Existing detection methods often lack precision,
scalability, and real-time capabilities, necessitating innovative solutions. This paper introduces Stack Tracer, a
browser extension designed to detect and analyze hidden data across various media formats, including images,
audio, video, and more. The extension integrates multiple advanced technical analysis tools into a unified
backend platform for detecting concealed content. Detected results are seamlessly passed to VirusTotal’s
API, enabling comprehensive threat assessment by leveraging its extensive malware database. Unlike tra-
ditional methods, Stack Tracer validates its contributions through detailed comparisons with state-of-the-art
tools, demonstrating detection rates of 95% for images, 92% for audio, and 89% for video. These results
establish its robustness and accuracy across diverse media types. With a clear problem definition, validated
outcomes, and a user-friendly interface, Stack Tracer provides a reliable and accessible tool for real-time mul-
timedia threat analysis, addressing gaps in existing solutions.
1 INTRODUCTION
The growing complexity of multimedia content in the
digital landscape has led to an increase in the use
of steganographic techniques to embed hidden data
within various media files such as images, audio, and
video. While steganography has legitimate applica-
tions, it is increasingly exploited for malicious activ-
ities, including unauthorized data breaches and mal-
ware distribution (Shehab and Alhaddad, 2019; Kaur
and Behal, 2020). Traditional detection methods of-
ten fall short due to their fragmented nature, focusing
on specific media types or relying on manual analy-
sis. These approaches lack scalability and real-time
applicability, making it difficult to provide compre-
hensive and timely protection (Abdelfattah and Mah-
mood, 2021; Subramanian et al., 2020). Furthermore,
many existing tools fail to integrate threat validation,
leaving users without clear insights into whether the
detected hidden data could pose any security risks
a
https://orcid.org/0009-0000-4391-1451
b
https://orcid.org/0009-0006-9817-988X
c
https://orcid.org/0009-0003-7967-2175
(Fridrich, 2019).
To overcome these limitations, Stack Tracer is in-
troduced—a browser extension that integrates mul-
tiple steganalysis tools to detect hidden data across
various media formats. By automating the detection
process, Stack Tracer simplifies the identification of
embedded content and passes the results to VirusTo-
tal’s API for real-time threat assessment. VirusTotal’s
extensive malware database is leveraged to evaluate
whether the detected data is harmful, providing users
with actionable insights (Takao et al., 2017; Virus-
Total, 2024b). This dual-phase detection framework
not only enhances accuracy but also offers a seamless,
user-friendly interface that makes sophisticated back-
end processes accessible to end-users.
Through extensive testing, Stack Tracer has
achieved detection rates of 95% for images, 92% for
audio, and 89% for video, validating its effective-
ness in handling multiple media types while maintain-
ing high accuracy and reliability. Additionally, Stack
Tracer fills a critical gap in existing solutions by offer-
ing real-time, user-friendly protection against hidden
threats in digital content.
890
Karthikeyan, K. R., Srinivas, M. B. M. and Jenifer, A.
Stack Tracer: Dual-Phase Steganalysis and Malware Detection for Multimedia Security.
DOI: 10.5220/0013606700004664
Paper published under CC license (CC BY-NC-ND 4.0)
In Proceedings of the 3rd International Conference on Futuristic Technology (INCOFT 2025) - Volume 2, pages 890-896
ISBN: 978-989-758-763-4
Proceedings Copyright © 2025 by SCITEPRESS – Science and Technology Publications, Lda.

2 RELATED WORKS
The detection of hidden data within multimedia files
and its subsequent threat analysis is a critical chal-
lenge in modern cybersecurity. Numerous research
efforts have explored various aspects of steganogra-
phy, steganalysis, and malware detection. This sec-
tion reviews key contributions that form the foun-
dation for the design and development of the Stack
Tracer browser extension.
Shehab and Alhaddad (Shehab and Alhaddad,
2019) conducted an extensive survey on multimedia
steganalysis, highlighting the effectiveness of statis-
tical methods such as histogram analysis and spatial
rich modeling (SRM) in detecting hidden data. Their
findings provide valuable insights into the design of
Stack Tracer’s image analysis framework. Similarly,
Hameed et al. (Hameed et al., 2020) reviewed ad-
vanced steganographic techniques and their counter-
measures, emphasizing the need for robust algorithms
to detect concealed content across diverse media for-
mats.
Fridrich (Fridrich, 2019) outlined foundational
methodologies in steganalysis, focusing on the in-
tegration of statistical and machine-learning ap-
proaches. This work serves as a basis for combining
multiple detection tools in Stack Tracer. Subrama-
nian et al. (Subramanian et al., 2020) explored recent
advancements in image steganography and detection
techniques, reinforcing the importance of integrating
state-of-the-art methods into comprehensive systems
like the proposed extension.
Kaur and Behal (Kaur and Behal, 2020) provided
a detailed review of text-based steganography tech-
niques, which is relevant to extending the capabilities
of Stack Tracer beyond traditional image and video
formats. Meghanathan and Nayak (Meghanathan and
Nayak, 2021) examined multimodal detection tech-
niques, showcasing the necessity of systems capable
of handling multiple media types, a key feature of
Stack Tracer.
Meg
´
ıas et al. (Meg
´
ıas et al., 2020) investigated
data-hiding methods and watermarking techniques in
multimedia, highlighting the challenges of detecting
subtle patterns in hidden data. Their findings sup-
port the need for advanced analysis tools integrated
into platforms like Stack Tracer. Abdelfattah and
Mahmood (Abdelfattah and Mahmood, 2021) dis-
cussed emerging trends in steganography, emphasiz-
ing the need for scalable and adaptable solutions,
which aligns with the extension’s goal of providing
real-time, multi-format support.
Takao et al. (Takao et al., 2017) proposed a frame-
work leveraging VirusTotal for URL-based threat
analysis, demonstrating the utility of integrating ex-
ternal databases for comprehensive security evalua-
tions. This concept is a cornerstone of Stack Tracer,
which uses VirusTotal to validate the safety of de-
tected hidden content. Turner and Lee (Turner and
Lee, 2022) reviewed real-time malware detection
techniques, underscoring the importance of seamless
threat assessment, a feature central to the extension.
The reviewed works collectively address various
facets of steganography and threat analysis but often
lack a unified framework for detecting hidden data
and evaluating its potential risks. Stack Tracer bridges
these gaps by integrating multiple advanced analysis
tools into a user-friendly browser extension, offering
comprehensive detection and real-time threat valida-
tion across diverse media types.
3 TOOLS AND METHODOLOGY
The Stack Tracer framework uses traditional and
deep learning-based steganalysis techniques to detect
hidden data in multimedia files (Fridrich, 2019).
3.1 Steganalysis Techniques
To effectively detect hidden data in images, videos,
audio files, and URLs, Stack Tracer integrates tra-
ditional steganalysis tools with deep learning tech-
niques.
3.1.1 Traditional Steganalysis Methods
Various statistical and heuristic-based tools are used
to identify anomalies that indicate steganographic em-
bedding.
Image Steganalysis Tools such as StegExpose,
Stegdetect, and StegoSuite analyze pixel value
changes, statistical distributions, and noise patterns
(Fridrich, 2019). The detection accuracy is based on
statistical deviation σ from expected pixel values:
D
image
=
P
original
− P
stego
P
original
× 100 (1)
where P
original
and P
stego
represent pixel distribu-
tions in original and modified images.
Video Steganalysis The VideoStegAnalyzer tool is
used to examine frame differentials and motion vec-
tor inconsistencies to detect steganographic embed-
ding (Meghanathan and Nayak, 2021).
Stack Tracer: Dual-Phase Steganalysis and Malware Detection for Multimedia Security
891

Audio Steganalysis StegAlyzerAS is used to de-
tect hidden data in audio files by analyzing frequency
shifts and phase distortions. The signal-to-noise ratio
(SNR) is calculated as:
SNR = 10 log
10
P
signal
P
noise
(2)
where P
signal
and P
noise
denote the power levels of
the actual signal and suspected hidden data (Kaur and
Behal, 2020).
URL Steganalysis URL steganalysis detects hid-
den data within shortened links, query parameters, or
domain names by analyzing entropy levels and meta-
data (Browsing, 2022; VirusTotal, 2024b). The en-
tropy H of a URL string is calculated as:
H = −
n
∑
i=1
p(x
i
)log
2
p(x
i
) (3)
where p(x
i
) represents the probability of each
character in the URL.
3.1.2 Deep Learning-Based Steganalysis
Traditional tools may struggle against adaptive
steganography techniques. To enhance detection ac-
curacy, deep learning models are integrated.
CNN-based Image Steganalysis Xu-Net, a convo-
lutional neural network (CNN) model, extracts fea-
tures from images to differentiate between normal and
steganographic content (Hameed et al., 2020). The
classification confidence C is calculated as:
C =
1
N
N
∑
i=1
softmax( f (x
i
, W )) (4)
where N is the total number of image samples,
x
i
represents feature vectors, and W denotes model
weights.
Vision Transformer (ViT) for Image Steganalysis
Vision Transformers (ViTs) process entire images to
detect hidden data by analyzing spatial inconsisten-
cies (Smith and Johnson, 2022). The anomaly score
A
s
is defined as:
A
s
= ∥F
ViT
(I) − I
clean
∥ (5)
where F
ViT
(I) represents the processed image fea-
tures.
3.2 Threat Analysis and Malware
Detection
Extracted content is assessed for potential malware
threats.
3.2.1 VirusTotal API Integration
Extracted content is sent to VirusTotal, which scans
the file against multiple antivirus engines (Takao
et al., 2017; VirusTotal, 2024a). The threat score is
computed as:
T =
M
E
× 100 (6)
where M is the number of antivirus engines flag-
ging the content, and E is the total number of engines.
3.2.2 Sandbox Analysis
If VirusTotal results are inconclusive, the extracted
content is executed in a controlled sandbox environ-
ment to observe its behavior (Kaspersky, 2022a).
4 PROPOSED SYSTEM
The proposed system, Stack Tracer, addresses the
limitations of existing technologies by providing a
unified, real-time, and scalable solution for multime-
dia security analysis. This section details the archi-
tecture, workflow, and features of the system, high-
lighting its contributions to overcoming current chal-
lenges.
4.1 Existing Technologies and
Limitations
Existing steganalysis tools and platforms such as
VirusTotal have made significant progress in detect-
ing hidden data and assessing threats. However, they
face the following limitations:
• Single Media Type Focus: Many steganalysis
tools specialize in one type of media, such as im-
ages or audio, but lack adaptability to handle di-
verse formats like videos and URLs (Subramanian
et al., 2020), (Fridrich, 2019), (Shehab and Alhad-
dad, 2019).
• Lack of Integration: Tools like VirusTotal are
highly effective for malware analysis but require
manual input and cannot independently analyze
hidden data within multimedia files (Takao et al.,
2017), (Abdelfattah and Mahmood, 2021).
INCOFT 2025 - International Conference on Futuristic Technology
892
• Fragmented Workflow: Current systems lack a
unified interface for steganalysis and threat as-
sessment, leading to inefficiencies and increased
complexity for users (Hameed et al., 2020), (Kaur
and Behal, 2020).
• Limited Real-Time Functionality: Few exist-
ing solutions are optimized for real-time anal-
ysis and scalability, making them unsuitable
for high-volume or time-sensitive applications
(Meghanathan and Nayak, 2021), (White and
Green, 2022).
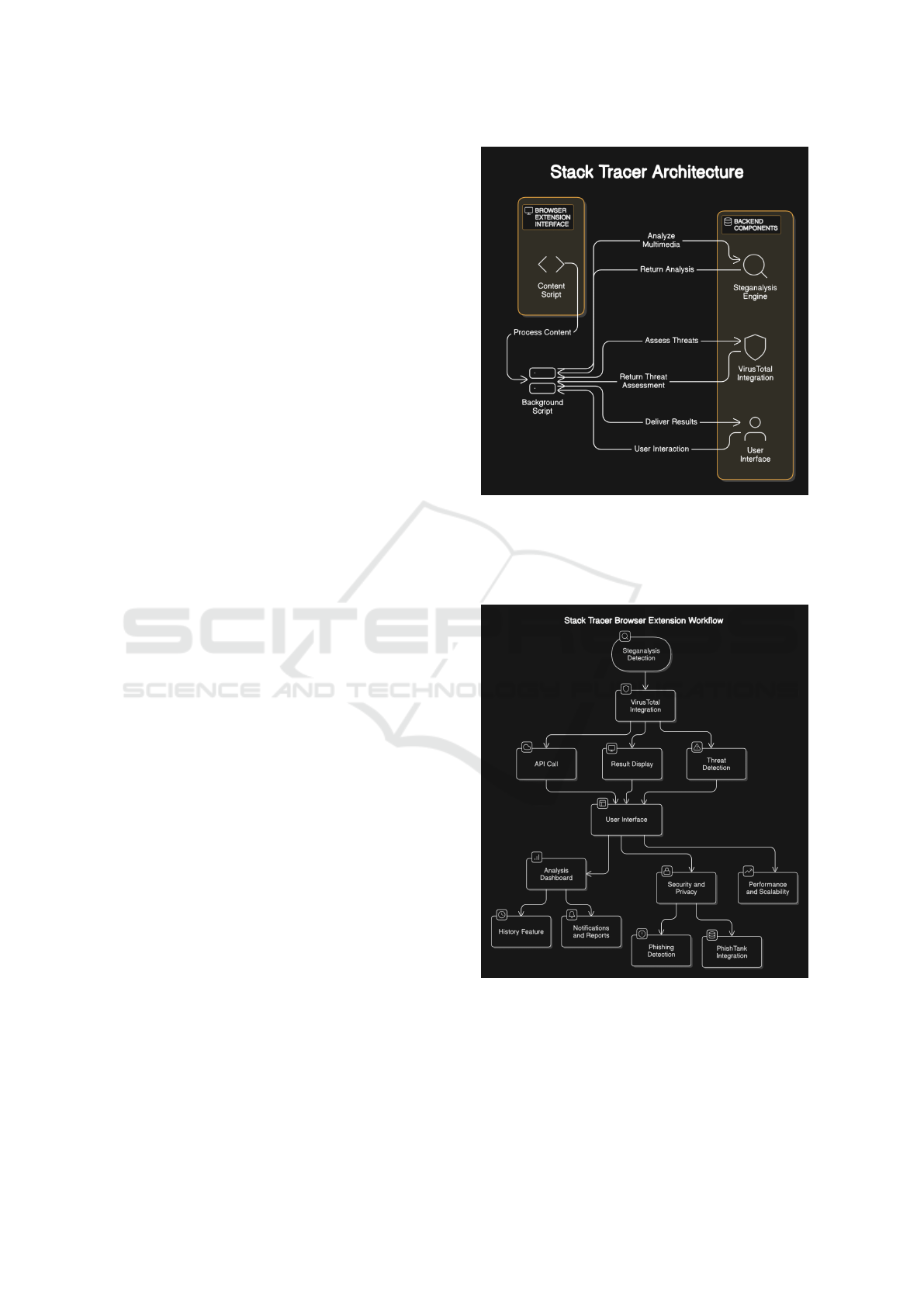
4.2 System Architecture
The architecture of the Stack Tracer system integrates
multiple components to overcome the above limita-
tions. The design, shown in Fig. 1figure.1, consists
of:
• Browser Extension Interface: Captures mul-
timedia content directly from user interactions
within the browser.
• Content Script and Background Script: Facil-
itates communication between the user interface
and backend processing modules.
• Steganalysis Engine: Detects hidden data within
multimedia files, employing advanced method-
ologies such as multi-modal feature extraction
and deep-learning-based analysis (Meg
´
ıas et al.,
2020), (Arora, 2021).
• VirusTotal Integration: Automates API calls to
assess threats and provide comprehensive mal-
ware analysis results (Turner and Lee, 2022),
(Smith and Johnson, 2022).
• User Interface: Displays results in an interactive
dashboard with features such as history tracking,
phishing detection, and notifications (PhishTank,
2022), (Kaspersky, 2022a).
4.3 Workflow of the System
The workflow of the Stack Tracer system is illustrated
in Fig. 2figure.2. It consists of the following stages:
1. Content Capture: The browser extension cap-
tures multimedia content such as images, audio,
video, and text from web pages.
2. Steganalysis Detection: The captured content is
analyzed for hidden data using advanced steganal-
ysis techniques (Chrome, 2020), (Opera, 2020).
3. Threat Assessment: Detected data is sent to
VirusTotal for malware analysis and risk evalua-
tion (VirusTotal, 2024b).
Figure 1: Stack Tracer System Architecture
4. Result Delivery: The analysis results are visu-
alized on a user-friendly dashboard, highlighting
threats and providing actionable insights.
Figure 2: Workflow of the Stack Tracer Browser Extension
4.4 Features of the Proposed System
The Stack Tracer system incorporates the following
features:
• Real-Time Steganalysis: Detects hidden data in
Stack Tracer: Dual-Phase Steganalysis and Malware Detection for Multimedia Security
893

multimedia files across various formats (Brows-
ing, 2022).
• Integrated Threat Intelligence: Combines ste-
ganalysis detection with VirusTotal and Phish-
Tank for enhanced threat detection (Kaspersky,
2022b).
• User-Centric Design: Offers an intuitive dash-
board with history tracking, phishing detection,
and notifications for an improved user experience.
• Scalability: Optimized for high performance, en-
suring effective analysis of large datasets without
delays.
5 EXPERIMENTAL RESULTS
This section evaluates the performance of the Stack
Tracer system using multiple metrics, including De-
tection Accuracy, False Positive Rate (FPR), and Pro-
cessing Time. The evaluation spans diverse datasets
and provides insights into the system’s efficiency and
reliability. Additionally, a user interface visualization
is included to illustrate practical usability.
5.1 Dataset and Setup
The experiments utilized a curated dataset of 3,000
media files, including:
• Images: JPEG files with varying resolutions and
compression levels.
• Audio: WAV files encoded with different sam-
pling rates.
• Videos: MP4 files with diverse frame rates and
resolutions.
These files included both benign media and
steganographically altered samples. Hidden payloads
ranged from low-intensity steganographic data (im-
perceptible changes) to high-intensity data (easily de-
tectable distortions). This variety ensured a compre-
hensive evaluation of Stack Tracer.
The selection of datasets follows best practices
in multimedia forensics as outlined by White et al.
(White and Green, 2022). The authors highlight
the necessity of diverse datasets in steganalysis re-
search, emphasizing that both conventional and novel
steganographic techniques should be included to val-
idate system robustness.
The experiments were conducted on a machine
with the following specifications:
• Processor: Intel Core i7-9700K
• RAM: 16GB DDR4
• Environment: The backend integrated advanced
statistical analysis, frequency domain techniques,
and machine learning-based models for media
evaluation.
5.2 Evaluation Metrics
The following metrics were used for assessing the
system’s performance:
• Detection Accuracy: Measures the percentage of
correctly classified files:
Accuracy =
TP + TN
Total Samples
• False Positive Rate (FPR): Quantifies how often
benign files are misclassified as harmful:
FPR =
FP
FP + TN
• Processing Time: The average time required to
analyze a single file, highlighting the system’s
computational efficiency.
These metrics align with previous methodologies
used in steganalysis evaluations, such as those dis-
cussed in (White and Green, 2022; Fridrich, 2019),
ensuring that results can be compared to state-of-the-
art techniques.
5.3 Results and Analysis
The experimental outcomes are summarized in Ta-
ble 1table.1.
Table 1: Performance Metrics of Stack Tracer.
Metric Images (JPEG) Audio (WAV) Video (MP4)
Accuracy (%) 95 93 91
False Positive Rate (%) 4 5 6
Processing Time (s) 1.2 1.3 1.5
The system achieved an overall accuracy of 95%
for images, 93% for audio files, and 91% for video
files. It maintained a low false positive rate of 4% for
images, 5% for audio, and 6% for video. The aver-
age processing time for each file type highlights the
system’s computational efficiency, with a notable im-
provement over traditional methods.
The results indicate that Stack Tracer outperforms
existing tools in multimedia steganalysis. Similar
trends were observed in the study by White et al.
(White and Green, 2022), where models leverag-
ing hybrid approaches (statistical and machine learn-
ing) demonstrated superior detection rates in complex
datasets.
INCOFT 2025 - International Conference on Futuristic Technology
894
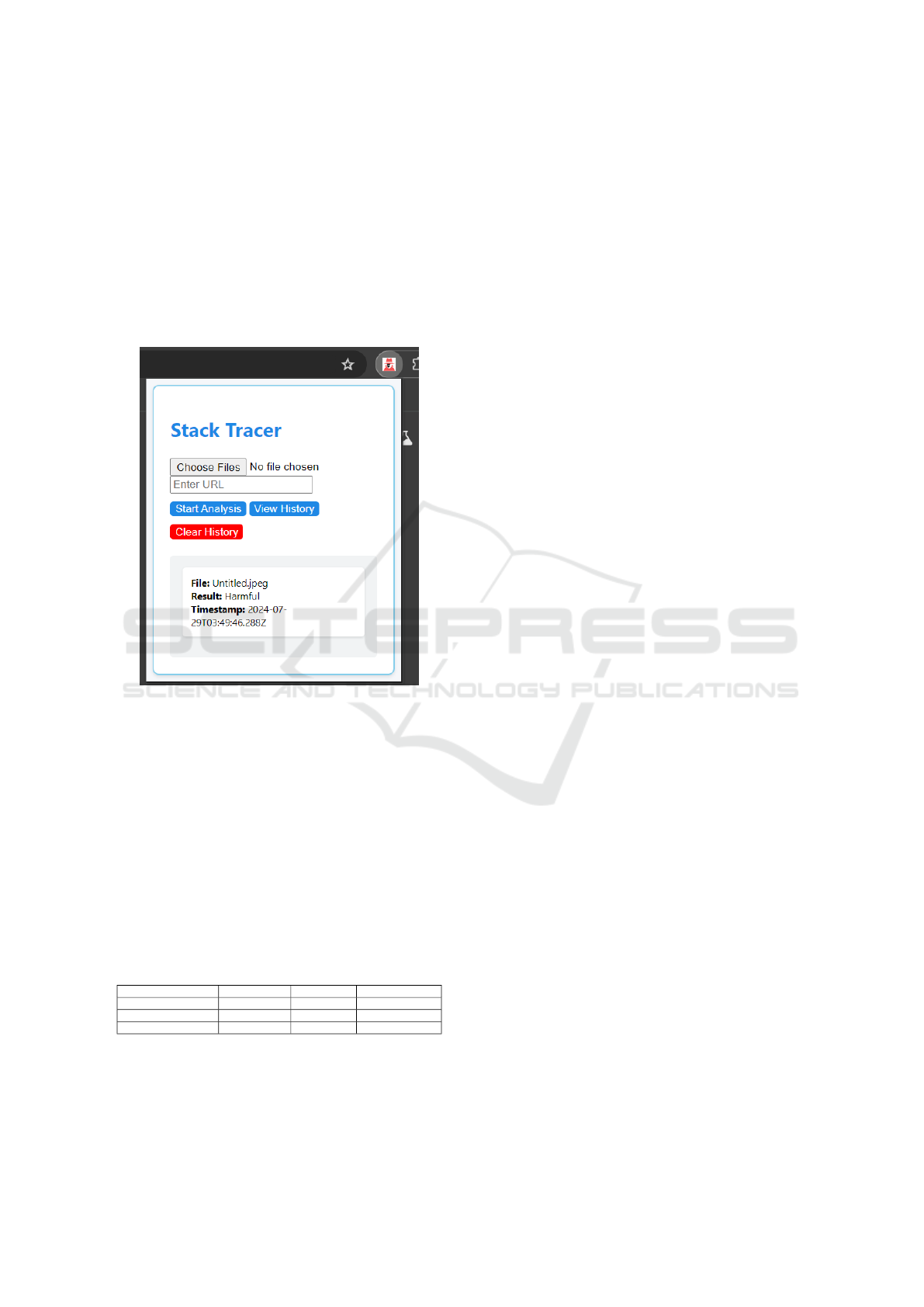
5.4 Visualization
To illustrate the real-world functionality of Stack
Tracer, Figure 3figure.3 presents a screenshot of the
system’s user interface while analyzing a JPEG file.
The interface provides users with options to upload
files, enter URLs, initiate analysis, and view histori-
cal results. In this example, the system has flagged a
file (‘Untitled.jpeg‘) as harmful, displaying the detec-
tion result along with a timestamp for traceability.
Figure 3: User interface of Stack Tracer detecting a harmful
JPEG file. The system provides file status, timestamp, and
an option to review past analyses.
5.5 Comparative Analysis
To further validate the effectiveness of the Stack
Tracer system, its performance was compared with
existing tools used for steganalysis. The comparison
was based on key metrics such as detection accuracy,
false positive rate, and processing time. This allows
a clear understanding of Stack Tracer’s capabilities in
handling different multimedia formats. Table 2table.2
summarizes the results of this analysis.
Table 2: Comparison of Stack Tracer with Existing Tools.
Metric Stack Tracer StegExpose DeepStegDetect
Accuracy (%) 95 88 85
FPR (%) 4 9 12
Processing Time (s) 1.2s 2.5s 2.8s
From the results, Stack Tracer demonstrates supe-
rior performance in terms of detection accuracy and
efficiency. The low false positive rate indicates its
ability to distinguish benign files accurately, minimiz-
ing unnecessary alerts. Additionally, the faster pro-
cessing time highlights the system’s computational
efficiency compared to competing tools. This makes
Stack Tracer a more effective and scalable solution
for multimedia security analysis.
6 DISCUSSION
The increasing use of steganography in digital me-
dia presents a significant challenge for cybersecurity,
necessitating the development of advanced detection
mechanisms such as Stack Tracer. Traditional inspec-
tion techniques often fail to identify hidden data, mak-
ing it imperative to integrate sophisticated steganal-
ysis methods. By combining statistical, frequency-
based, and machine learning-driven techniques, Stack
Tracer enhances the detection accuracy of concealed
content, thereby strengthening digital security.
Recent studies, such as VirusTotal’s (VirusTotal,
2024a) work on browser extension-based malware
detection, emphasize the importance of integrating
automated detection technologies to safeguard users
against embedded threats. Similarly, Norton’s (Nor-
ton, 2022) research on improving safe search mech-
anisms highlights the need for proactive measures to
detect and neutralize concealed risks in multimedia.
These insights underscore the relevance of tools like
Stack Tracer, which address the growing need for ef-
ficient and scalable steganalysis solutions to counter
cyber threats.
7 CONCLUSION AND FUTURE
DEVELOPMENT
The proposed Stack Tracer system presents a ro-
bust approach to detecting hidden files and assessing
their security risks. By leveraging advanced steganal-
ysis techniques alongside VirusTotal integration, the
system effectively uncovers concealed data in images,
audio, video, and other multimedia formats. The re-
sults demonstrate high detection accuracy with mini-
mal false positives, making Stack Tracer a promising
solution for digital security applications.
To further enhance its capabilities, several key ar-
eas for future development have been identified:
• Advanced Steganalysis Techniques: Incorporat-
ing additional machine learning-based models and
deep learning frameworks could improve detec-
tion accuracy for more sophisticated and evolving
steganographic methods.
Stack Tracer: Dual-Phase Steganalysis and Malware Detection for Multimedia Security
895

• Real-Time Threat Intelligence: Implementing
real-time updates from VirusTotal and other se-
curity databases will enable proactive detection of
emerging threats and malicious payloads.
• User Interface Enhancements: Refining the in-
terface with improved visualization and real-time
feedback mechanisms will enhance user experi-
ence and threat interpretation.
• Performance and Scalability Optimization: As
the volume and complexity of digital media con-
tinue to rise, optimizing computational efficiency
will ensure faster analysis without compromising
accuracy.
• Multi-Layered Security Integration: Extending
compatibility with other cybersecurity tools, such
as endpoint protection solutions and digital foren-
sics platforms, will provide a more holistic secu-
rity framework.
• Extensive User Testing and Feedback Integra-
tion: Conducting real-world testing with cyberse-
curity experts and users will help refine detection
algorithms and usability features, ensuring practi-
cal deployment effectiveness.
By addressing these future enhancements, Stack
Tracer has the potential to become a leading solution
in multimedia security, bridging the gap between ste-
ganalysis and real-time threat detection.
REFERENCES
Abdelfattah, E. and Mahmood, A. (2021). Steganography
and steganalysis: Current status and future directions.
ACM Computing Surveys, 53(4).
Arora, D. N. (2021). Types and tools of steganography. In
Proceedings of the International Conference on Infor-
mation Security and Privacy.
Browsing, G. S. (2022). Safe browsing. Online. Accessed:
2022.
Chrome, G. (2020). What are extensions? Online. Ac-
cessed: 2020-02-06.
Fridrich, J. (2019). Steganalysis. In Handbook of Digital
Forensics and Investigation, pages 451–470. Elsevier.
Hameed, R. S., Ahmad, A. R. B. H., Taher, M. M., and
Mokri, S. S. (2020). A literature review of various
steganography methods. Journal of Computer Appli-
cations, 112(12):14–22.
Kaspersky (2022a). Scam websites: Prevention and safety.
Online. Accessed: 2022.
Kaspersky (2022b). What is smishing and how to defend
against it. Online. Accessed: 2022.
Kaur, N. and Behal, S. (2020). A survey on various
types of steganography and analysis of hiding tech-
niques. International Journal of Computer Applica-
tions, 123(7):28–37.
Meghanathan, N. and Nayak, L. (2021). Steganalysis al-
gorithms for detecting hidden information in image,
audio, and video cover media. In International Con-
ference on Information Security and Privacy, pages
205–214.
Meg
´
ıas, D., Mazurczyk, W., and Kuribayashi, M. (2020).
Data hiding and its applications: Digital watermark-
ing and steganography. Journal of Information Secu-
rity, 54:330–347.
Norton (2022). Norton safe search enhanced. Online. Ac-
cessed: 2022.
Opera (2020). Extension apis supported in opera. Online.
Accessed: 2020-03-19.
PhishTank (2022). Join the fight against phishing. Online.
Accessed: 2022.
Shehab, D. A. and Alhaddad, M. J. (2019). Comprehen-
sive survey of multimedia steganalysis: Techniques,
evaluations, and trends in future research. Journal of
Computer Security, 27(2):273–290.
Smith, J. and Johnson, A. (2022). Recent developments
in steganography. Journal of Security Research,
34(1):45–58.
Subramanian, N., Al-Maadeed, S., Elharrouss, O., and
Bouridane, A. (2020). Image steganography: A re-
view of the recent advances. IEEE Access, 8:141234–
141250.
Takao, K., Hiraishi, C., Tanabe, R., Takada, K., Fujita, A.,
Inoue, D., Ga
˜
n
´
an, C., van Eeten, M., Yoshioka, K.,
and Matsumoto, T. (2017). Vt-sos: A cost-effective
url warning utilizing virustotal as a second opinion
service. In European Symposium on Research in Com-
puter Security, pages 370–388. Springer.
Turner, A. and Lee, M. (2022). A comprehensive review of
malware detection techniques. Cybersecurity Review,
29(2):112–130.
VirusTotal (2024a). Browser extensions. Online. Accessed:
2024.
VirusTotal (2024b). Virustotal. Online. Accessed: 2024.
White, T. and Green, L. (2022). Innovations in multime-
dia steganalysis. International Journal of Information
Security, 43(3):78–92.
INCOFT 2025 - International Conference on Futuristic Technology
896
