
Smart and Secured Healthcare System
Prashant Uppar
a
, Pratiksha Angadi
b
, Chandni Kumari
c
, Swapnil Shahapurkar
d
and U. V. Somanatti
e
Department of Computer Science and Engineering, KLE Tech, University’s Dr. MSSCET, Belagavi, India
Keywords:
Network, Security, IOT, Automation, OSPF, Routing, ASA Firewall, VPN, Remote Login.
Abstract:
The growing reliance on digital infrastructure in healthcare institutions necessitates robust solutions to address
data security and operational efficiency. This paper presents a smart and secure healthcare network framework
that integrates advanced firewall configurations, dynamic routing protocols, and IoT enabled safety automa-
tion. The proposed system ensures data confidentiality, integrity, and availability by implementing optimized
OSPF routing, multi layered traffic filtering through firewalls, and secure remote access using VPN with SSH
encryption. IoT technologies enhance hospital safety by enabling automated fire detection, temperature con-
trol, and smoke detection systems. Experimental results validate the efficiency of this framework in mitigating
unauthorized access, streamlining network management, and automating safety measures. This approach of-
fers a scalable and effective solution to modern healthcare challenges, emphasizing secure communication and
reliable automation.
1 INTRODUCTION
The healthcare sector is increasingly dependent on
digital technologies to manage patient data, stream-
line hospital operations, and automate various safety
measures. However, the digitization of healthcare has
also led to the exponential growth of sensitive in-
formation, making these networks prime targets for
cyber attacks and unauthorized access (Sendelj and
Ognjanovic, 2022). These vulnerabilities not only
compromise patient privacy but can also disrupt hos-
pital operations, potentially leading to severe conse-
quences for both patients and healthcare providers.
Therefore, it is paramount to implement robust secu-
rity measures that protect critical data and ensure the
continuous operation of healthcare systems (Namo
˘
glu
and Ulgen, 2013). Despite the growing importance of
network security, existing systems often fail to suffi-
ciently address the complex needs of modern health-
care environments. Healthcare networks are usually
large and involve various interconnected devices, sys-
tems, and departments. This complexity increases
the difficulty of ensuring secure data transmission,
a
https://orcid.org/0009-0004-2892-9636
b
https://orcid.org/0009-0003-2499-1646
c
https://orcid.org/0009-0004-0613-7574
d
https://orcid.org/0009-0004-4044-4324
e
https://orcid.org/0000-0002-6930-6628
maintaining privacy, and safeguarding against unau-
thorized intrusions. Moreover, many traditional secu-
rity mechanisms struggle to balance cost efficiency,
scalability, and flexibility, often requiring expensive
infrastructure or overly simplistic solutions that fail
to meet all requirements (Wazid et al., 2022).
One of the key challenges in securing healthcare
networks is the diverse range of communication pro-
tocols and devices in use, coupled with misconfigura-
tions in routing and inadequate traffic filtering. These
gaps can result in data breaches, downtime, and sys-
tem vulnerabilities, putting sensitive patient informa-
tion at risk. Furthermore, the integration of Inter-
net of Things (IoT) technologies into hospital oper-
ations such as smart fire detection systems, temper-
ature regulation, and smoke detection adds another
layer of complexity. While these devices can au-
tomate safety features and improve operational effi-
ciency, they also introduce new security risks, par-
ticularly in terms of secure communication and re-
mote access (Alsbou et al., 2022). The proposed work
addresses these issues by designing a Smart and Se-
cured Healthcare System that aims to improve both
the security of hospital data and the automation of es-
sential safety functions. The system employs several
advanced techniques, including optimized dynamic
routing with OSPF, advanced firewall configurations,
and IoT-based automation for fire detection, tempera-
676
Uppar, P., Angadi, P., Kumari, C., Shahapurkar, S. and Somanatti, U. V.
Smart and Secured Healthcare System.
DOI: 10.5220/0013600000004664
Paper published under CC license (CC BY-NC-ND 4.0)
In Proceedings of the 3rd International Conference on Futuristic Technology (INCOFT 2025) - Volume 2, pages 676-684
ISBN: 978-989-758-763-4
Proceedings Copyright © 2025 by SCITEPRESS – Science and Technology Publications, Lda.

ture control, and smoke monitoring. These features
work together to provide a comprehensive solution
that not only secures hospital data but also ensures op-
erational efficiency and safety (Alsbou et al., 2022).
The key objectives of this work are, Network Se-
curity,To design and implement a secure network ar-
chitecture for a hospital environment, using subnet-
ting for network segmentation, static routing for ini-
tial traffic management, and dynamic OSPF routing to
ensure optimized, efficient data transfer across depart-
ments. Traffic Filtering and Intrusion Prevention,
To deploy advanced firewall mechanisms that filter
traffic, monitor network activity, and prevent unau-
thorized access, ensuring that only authorized person-
nel and devices can access the hospital’s internal sys-
tems. Remote Access Security, To ensure secure,
encrypted communication for remote access to hos-
pital systems via VPN and SSH encryption. The use
of VPN provides a secure tunnel for all internet traf-
fic, while SSH is used for secure remote command
execution and system management. IoT-Based Au-
tomation, To integrate IoT technologies for automat-
ing safety operations within the hospital, including
systems for fire detection, temperature regulation, and
smoke detection. These systems will operate in real
time, ensuring the safety of patients and hospital in-
frastructure.
The structure of the paper is organized as fol-
lows: Section 2 reviews related work, emphasizing
limitations in current approaches and how the pro-
posed work addresses these gaps. Section 3 details the
methodology, including network configuration and
IoT-based safety integration. Section 4 presents the
results, analyzes performance and accuracy, and com-
pares the proposed system to existing solutions. Sec-
tion 5 concludes the paper with a summary of contri-
butions, key findings, and recommendations for future
research.
2 RELATED WORKS
The evolution of healthcare systems has driven exten-
sive research in security, IoT integration, and automa-
tion. Existing studies explore various methodolo-
gies, including blockchain, firewalls, and smart IoT
systems, to enhance data privacy, network security,
and operational efficiency. While advancements like
Healthcare 5.0 and medical IoT platforms showcase
potential, gaps such as scalability, real world valida-
tion, and emerging technologies persist. This survey
consolidates insights to guide future implementations
addressing these challenges.
In (Priya et al., 2017) reviewed security attacks
in electronic healthcare systems, discussing security
requirements such as authentication, integrity, and
confidentiality. They categorized attacks based on
the data phases of gathering, transmission, and stor-
age. The study offers a comprehensive categorization
of security attacks, emphasizing the importance of
multi layered security and theoretical insights. How-
ever, it lacks practical implementation, experimental
validation, and quantitative benchmarks. The gaps
identified include the absence of specific solutions,
a lack of integration with emerging technologies like
AI or blockchain, and limited adaptability to real time
threats.
In (Jin et al., 2019) conducted a survey of secure
and privacy preserving medical data sharing mecha-
nisms, with a focus on blockchain based approaches.
They categorized the mechanisms into permissionless
and permissioned types and analyzed techniques such
as cryptography, anonymization, and SDN. The re-
view highlights the potential of blockchain in health-
care, especially in cryptographic solutions and SDN
integration. However, it relies on off chain storage
due to blockchain limitations, lacks real world imple-
mentation, and does not use a specific dataset. The
study identifies challenges in ensuring fine grained
access control, compatibility across domains, and the
need for a unified query mechanism, as well as holis-
tic solutions integrating blockchain with cryptogra-
phy and SDN.
In (Makhdoomi et al., 2022) reviewed conven-
tional and next generation firewalls (NGFWs), their
deployment methods, and comparative features. They
explored distributed firewalls and NAT/PAT firewalls,
highlighting the advanced features of NGFWs such
as IPS and application layer filtering. While the study
provides a thorough theoretical review, it lacks prac-
tical implementation and experimental results. Gaps
include insufficient research on distributed firewall
policies, topologies, and effective real world imple-
mentations of access control mechanisms.
In (Sendelj and Ognjanovic, 2022) systematically
analyzed cybersecurity challenges in healthcare, iden-
tifying risks, consequences of attacks, and best prac-
tice recommendations. The study offers a compre-
hensive overview, leveraging recent statistical data to
provide actionable insights. However, it is primar-
ily descriptive, lacks empirical testing of solutions,
and does not cover all emerging technologies. The
gaps identified include the need for case studies on
successful implementations, exploration of emerging
technologies, and research on the effectiveness of pro-
posed frameworks.
In (Wazid et al., 2022) proposed a secure frame-
work for Healthcare 5.0, analyzing its applications,
Smart and Secured Healthcare System
677

security requirements, threat models, and existing
mechanisms. The framework provides a robust ap-
proach to addressing security challenges and com-
pares existing performance metrics. However, it re-
mains theoretical, with no extensive empirical valida-
tion. Gaps include the need for practical case studies,
exploration of emerging technologies, and further re-
search on framework effectiveness.
In (Pandey et al., 2020) conducted a systematic
literature review and scientometric analysis to assess
healthcare data integrity techniques. The study offers
a roadmap for future research by highlighting effec-
tive techniques like blockchain. However, it is lim-
ited by a focus on previously used methods and a lack
of exploration of new approaches. The gaps include
a need for comprehensive studies addressing multi-
faceted data integrity challenges in healthcare.
In (Namo
˘
glu and Ulgen, 2013) conducted a case
study in a 150 bed private hospital in Turkey, exam-
ining vulnerabilities in hospital information systems
and proposing a secure network infrastructure. The
study identifies security vulnerabilities and provides
best practices based on standards like HIPAA and ISO
80001. However, the lack of extensive sample data
and security concerns in revealing the hospital’s iden-
tity are limitations. Gaps include insufficient compli-
ance with healthcare standards, inadequate staff train-
ing, and a lack of privacy agreements with external
users.
In (Alsbou et al., 2022) designed and simulated an
IoT based smart hospital using Cisco Packet Tracer.
The system integrates IoT devices like sensors and ac-
tuators for real time patient data transmission. It en-
hances patient care and response times, but the sim-
ulation is limited by scalability challenges, network
congestion, and insufficient evaluation of data secu-
rity in complex environments. Gaps include the need
for real world testing, scalability assessment, and ad-
vanced security measures for IoT based systems.
In (Walia et al., 2023) developed a safe and secure
smart home using IoT technology in Cisco Packet
Tracer. The system includes RFID based access con-
trol, burglary detection, fire and smoke systems, and
water and temperature monitoring. The study en-
hances security and safety but relies heavily on sta-
ble internet connections and lacks features like voice
recognition or predictive analytics. Gaps include ro-
bust cybersecurity measures, scalability exploration,
and advanced features for smart home ecosystems.
In (Fu et al., 2023) developed a comprehensive
Medical IoT platform to unify healthcare scenarios
and devices, addressing data fragmentation through
technical standards. The platform supports seamless
data collection, real time decision making, and health
data fusion but faces challenges with interoperability
and validation of data reliability. Gaps include insuf-
ficient device integration, improved data sharing stan-
dards, and comprehensive evaluations of platform ef-
fectiveness in real world settings.
In (Roy et al., 2023) implemented a smart home
automation system in Cisco Packet Tracer, integrat-
ing IoT devices for fire safety and enhanced network
security. While the system provides comprehensive
automation, it is limited by simulation constraints and
device interoperability challenges. Gaps include fur-
ther research on real world applicability, advanced se-
curity measures, and diverse IoT device integration
for enhanced functionality.
In (Karunamurthy et al., 2023) implemented the
Routing Information Protocol (RIP) for managing IoT
devices across different LANs. The study highlights
enhanced IoT management and automation but fo-
cuses on simulation in controlled environments. Gaps
include research on scalability and emerging tech-
nologies for better IoT management solutions.
In (Yudidharma et al., 2023) conducted a system-
atic literature review to analyze messaging protocols
and electronic platforms for smart homes. The study
identifies commonly used protocols like MQTT and
CoAP and evaluates performance. However, it fo-
cuses on existing literature, leaving gaps in emerging
technologies and user centric solutions.
In (Abdunabi et al., 2023) developed a secure
system architecture for Body Area Networks (BAN),
incorporating Spatio Temporal Attribute Based Ac-
cess Control (STABAC) and blockchain for policy
integrity. While the study enhances healthcare data
management, it lacks performance evaluation and
consideration of insider threats. Gaps include assess-
ments of mobile user access and the proposed model’s
real world effectiveness.
In (Madhav et al., 2023) designed and simulated a
smart hospital using IoT technologies in Cisco Packet
Tracer. The system integrates automation for safety
and security but lacks real world deployment, predic-
tive analytics, and scalability for larger hospital net-
works. Gaps include real time patient monitoring, ad-
vanced predictive models, and integration of speech
recognition and machine learning for smart hospitals.
In (Alzu’bi et al., 2024), a systematic literature re-
view was conducted to define research questions, for-
mulate keywords, filter articles, and classify results.
This study provides a comprehensive overview of pri-
vacy and security concerns in edge computing, iden-
tifying key privacy needs and discussing potential so-
lutions. However, the study is limited in its focus on
practical implementations and does not explore other
computing paradigms in detail. The research identi-
INCOFT 2025 - International Conference on Futuristic Technology
678
fies a significant gap in privacy-preserving strategies
and integration studies for intelligent edge systems in
healthcare applications.
In (Samudrala et al., 2024), IoT devices were in-
tegrated using Cisco Packet Tracer for centralized fire
detection employing a star topology. This method-
ology enhances fire detection through the use of
smoke and motion sensors, enabling real-time alerts
and monitoring. Despite its advantages, the study
is simulation-based and does not fully address real-
world variables. Further research is necessary to test
this system in real-world scenarios and integrate it
with other safety measures.
In (Salunkhe et al., 2024), the use of microser-
vices in healthcare was analyzed, particularly for clin-
ical applications. This approach improves scalability,
maintainability, and responsiveness within healthcare
systems. Nevertheless, challenges persist regarding
data consistency, security compliance, and integra-
tion with legacy systems. Future studies should focus
on empirical evaluations and strategies for integrating
user experiences into microservice architectures.
In (Khan et al., 2024), a home server using PCIe
technology for Network Attached Storage (NAS) was
designed, and performance comparisons were con-
ducted. The findings emphasize the benefits of scal-
ability, centralized management, and data security.
However, the study has limited consideration of en-
ergy efficiency and potential security vulnerabilities.
Further research is recommended to develop energy-
efficient solutions and conduct real-world analyses of
such systems.
In (Ghasab et al., 2024), a centralized virtual
network for fire stations in Iraq was proposed us-
ing Cisco Packet Tracer. This approach aims to im-
prove emergency coordination, response times, and
resource allocation. However, the study lacks a de-
tailed analysis of server failures and the resilience of
the proposed network to cyber threats. Further inves-
tigation is required to evaluate the network’s impact
and incorporate enhanced security measures.
In reviewing the existing literature and ap-
proaches, it is evident that current healthcare systems
face significant limitations, particularly in areas such
as network segmentation, security, scalability, and
IoT integration. Many systems rely on flat network
topologies, outdated security protocols, and manual
monitoring, which can lead to performance bottle-
necks, data vulnerabilities, and slower response times
during emergencies. Furthermore, existing systems
often lack scalability, requiring expensive overhauls
to accommodate growing needs. The proposed Sys-
tem addresses these gaps by implementing advanced
network management techniques like subnetting and
dynamic routing, enhancing security with modern en-
cryption and automated access controls, integrating
IoT devices for real time monitoring and response,
and ensuring scalability and cost efficiency for long
term adaptability.
3 PROPOSED METHODOLOGY
Fig.1, illustrates the logical architecture of the pro-
posed system, focusing on how different layers and
components interconnect to achieve efficient health-
care network management. This design emphasizes
the conceptual structure and modularity of the system,
ensuring scalability, reliability, and security across all
layers
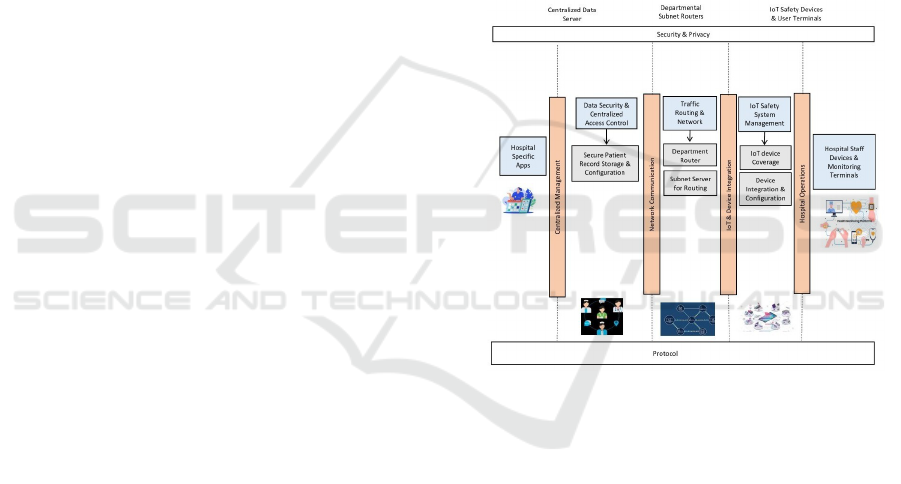
Figure 1: Logical Architecture of the Proposed System
Centralized Management layer ensures secure
storage of patient data, centralized configuration,
and access control. It acts as the primary control
hub for the entire system. Network Communication
Comprising departmental subnet routers and traffic
routing mechanisms, this layer manages data flow and
network connectivity across departments. IoT and
Device Integration section is dedicated to integrating
IoT safety devices and ensuring seamless device
configuration and coverage for real time operations.
Hospital Operations is Focused on hospital staff and
monitoring systems, this layer supports applications
that facilitate operational workflows and device
interactions. Security and Privacy ,Spanning all
layers, this ensures robust encryption, firewalls, and
authentication mechanisms, safeguarding the system
from vulnerabilities. This logical design serves as
a blueprint, providing a high level view of how the
system functions conceptually.
Smart and Secured Healthcare System
679
The logical design has been seamlessly trans-
lated into a virtual implementation using Cisco Packet
Tracer. This practical setup incorporates the config-
uration of essential networking components, includ-
ing routers, switches, IoT devices, and safety sys-
tems, while closely aligning with the blueprint pro-
vided by the logical architecture. The representation
of the Cisco Packet Tracer implementation is shown
below in Fig 2.
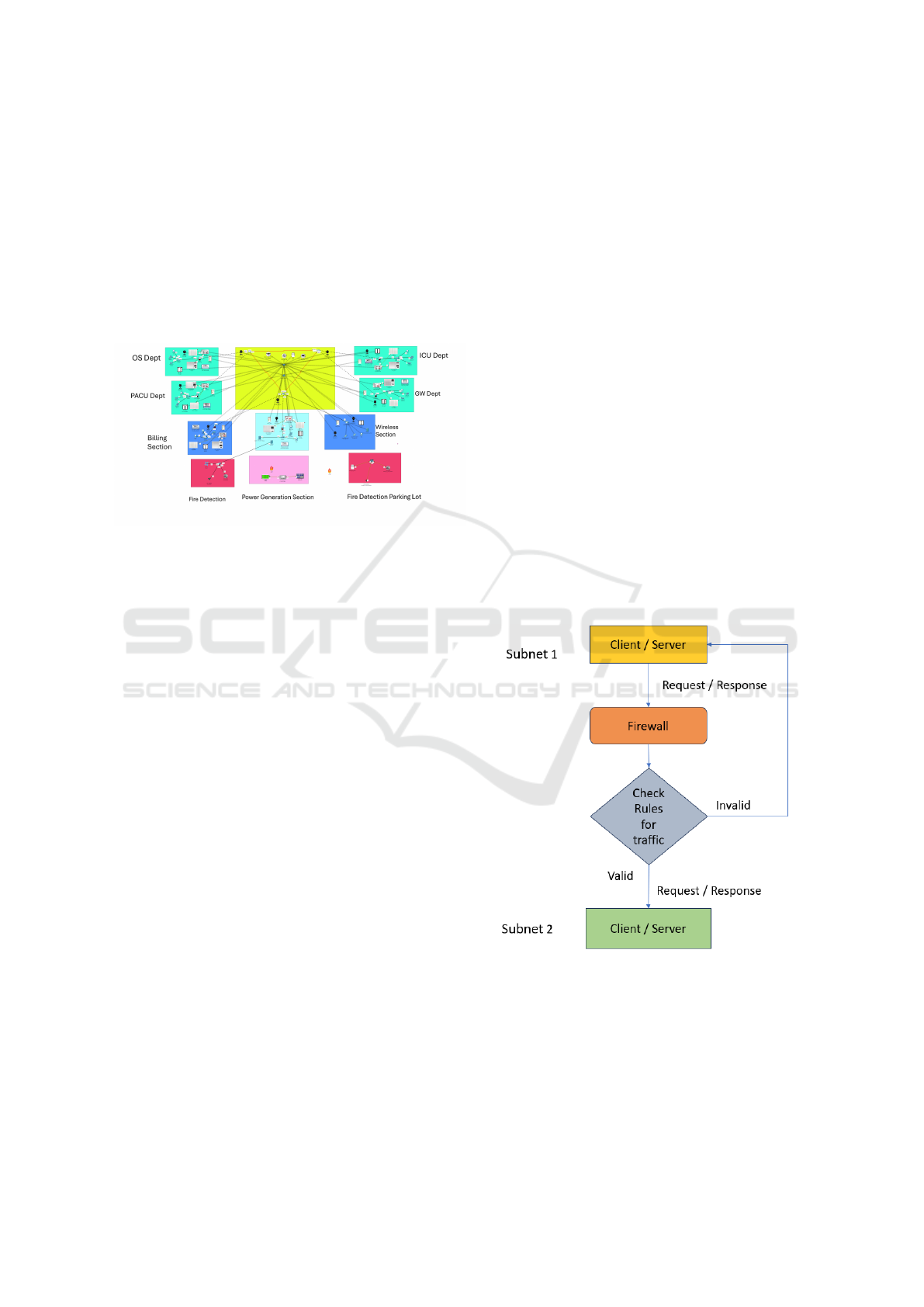
Figure 2: Cisco Network Implementation and Architecture
Centralized Core Network represents the back-
bone of the network, hosting the central data server
and managing communication between subsystems
and Configured with routing protocols (e.g., OSPF)
to optimize data flow and ensure redundancy. Depart-
mental Subnetworks are segregated based on hospital
departments, each with its own routers, switches,
and IoT devices. and Dynamic routing protocols
and firewalls are implemented to ensure secure
communication and adaptability to varying network
demands. In Safety and Automation Systems, IoT
enabled safety mechanisms include fire detection,
temperature control, and smoke detection systems.
and Devices are connected through IoT protocols
and integrated with monitoring dashboards for real
time alerts. In Interconnectivity, all systems are
interconnected via secure VPN tunnels and encrypted
communication channels to safeguard sensitive data.
Load balancing ensures high availability and fault tol-
erance across departments. This design emphasizes
modularity, scalability, and security, aligning with the
logical architecture’s blueprint while addressing real
world constraints.
In the proposed healthcare system, OSPF (Open
Shortest Path First) routing ensures dynamic and effi-
cient communication across hospital subnetworks. It
connects departmental routers to the centralized data
server, enabling optimal data flow for IoT devices and
monitoring systems. OSPF dynamically calculates
the shortest, most reliable paths for data, adapting to
changes like link failures or congestion to maintain
uninterrupted healthcare operations. Its hierarchical
structure segments the network into zones, reducing
routing overhead while ensuring high speed commu-
nication. This protocol facilitates seamless integra-
tion of IoT sensors for fire detection, temperature con-
trol, and patient safety, ensuring robust connectivity,
operational efficiency, and scalability.
VPN (Virtual Private Network) establishes a se-
cure and encrypted connection between devices over
an untrusted network, such as the internet. It ensures
that data exchanged between endpoints remains con-
fidential and protected from unauthorized access. By
creating a private network tunnel, VPNs prevent po-
tential threats like eavesdropping or data interception.
VPN is utilized to safeguard communication between
hospital networks and remote users. This implemen-
tation provided encrypted channels for accessing sen-
sitive information like patient records, ensuring se-
cure data exchange across different departments and
external entities. The use of SSH (Secure Shell) en-
cryption further enhanced the security of the VPN by
adding an additional layer of protection to data trans-
fers, ensuring only authorized users could access the
network resources.
Figure 3: Firewall Traffic Filtering.
As shown in Fig. 3, the firewall acts as a security
barrier between Subnet 1 and Subnet 2, monitoring
and controlling data flow based on predefined rules.
Requests and responses passing through the firewall
are evaluated against these rules to determine their
validity. Valid traffic is allowed to proceed, ensuring
seamless communication between clients and servers,
INCOFT 2025 - International Conference on Futuristic Technology
680
while invalid traffic is blocked to protect the network
from unauthorized access or malicious activity. This
configuration safeguards sensitive data, prevents po-
tential breaches, and ensures compliance with secu-
rity policies. Additionally, the firewall enforces traffic
filtering and access control.
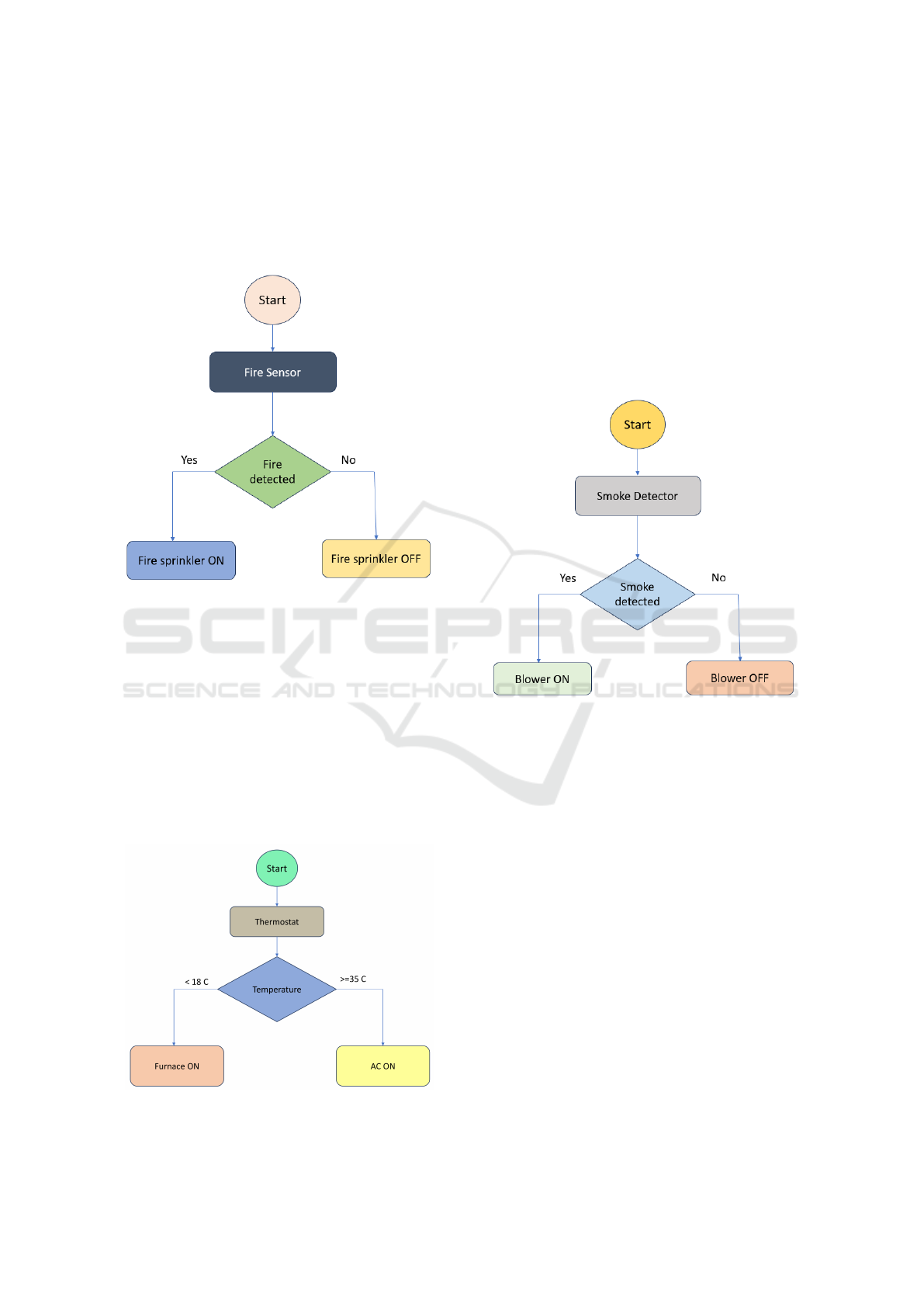
Figure 4: Fire Detection.
As shown in Fig. 4, the diagram illustrates the
process of fire detection and response. The system
begins with a fire sensor monitoring the environment
for potential fire events. If the sensor detects a fire, it
triggers the activation of the fire sprinkler system to
mitigate the threat. If no fire is detected, the sprin-
klers remain inactive, ensuring resource efficiency.
This automated system collects real time environmen-
tal data to promptly identify fire hazards. Upon detec-
tion, sprinklers are activated to minimize damage and
enhance safety. The integration ensures seamless co-
ordination and effective hazard management.
Figure 5: Temperature Control.
As shown in Fig. 5, the diagram depicts the mon-
itoring and control of temperature through a ther-
mostat. The system evaluates the temperature and
initiates corresponding actions. If the temperature
falls below 18°C, the furnace is activated to main-
tain warmth. Conversely, if the temperature reaches
or exceeds 35°C, the air conditioning (AC) is turned
on to cool the environment. This setup automates
temperature-based actions to maintain optimal envi-
ronmental conditions. By dynamically controlling the
heating and cooling systems, it ensures effective re-
source utilization while addressing extreme tempera-
ture scenarios efficiently.
Figure 6: Smoke Detection.
As shown in Fig. 6, the diagram illustrates a
smoke detection system. The process begins with
a smoke detector monitoring the environment. If
smoke is detected, the system activates a blower to
mitigate the smoke and improve air quality. If no
smoke is detected, the blower remains off to conserve
energy and resources. This configuration ensures
timely detection and response to smoke, preventing
potential hazards while maintaining efficient oper-
ation in normal conditions. The automated control
enhances environmental safety by addressing smoke
related risks effectively.
4 RESULTS AND DISCUSSION
As shown in Fig. 7, The graph illustrates the accu-
racy and efficiency of OSPF routing over a 24 hour
period, with packets sent, delivered, and overall ef-
ficiency analyzed. High alignment between pack-
Smart and Secured Healthcare System
681
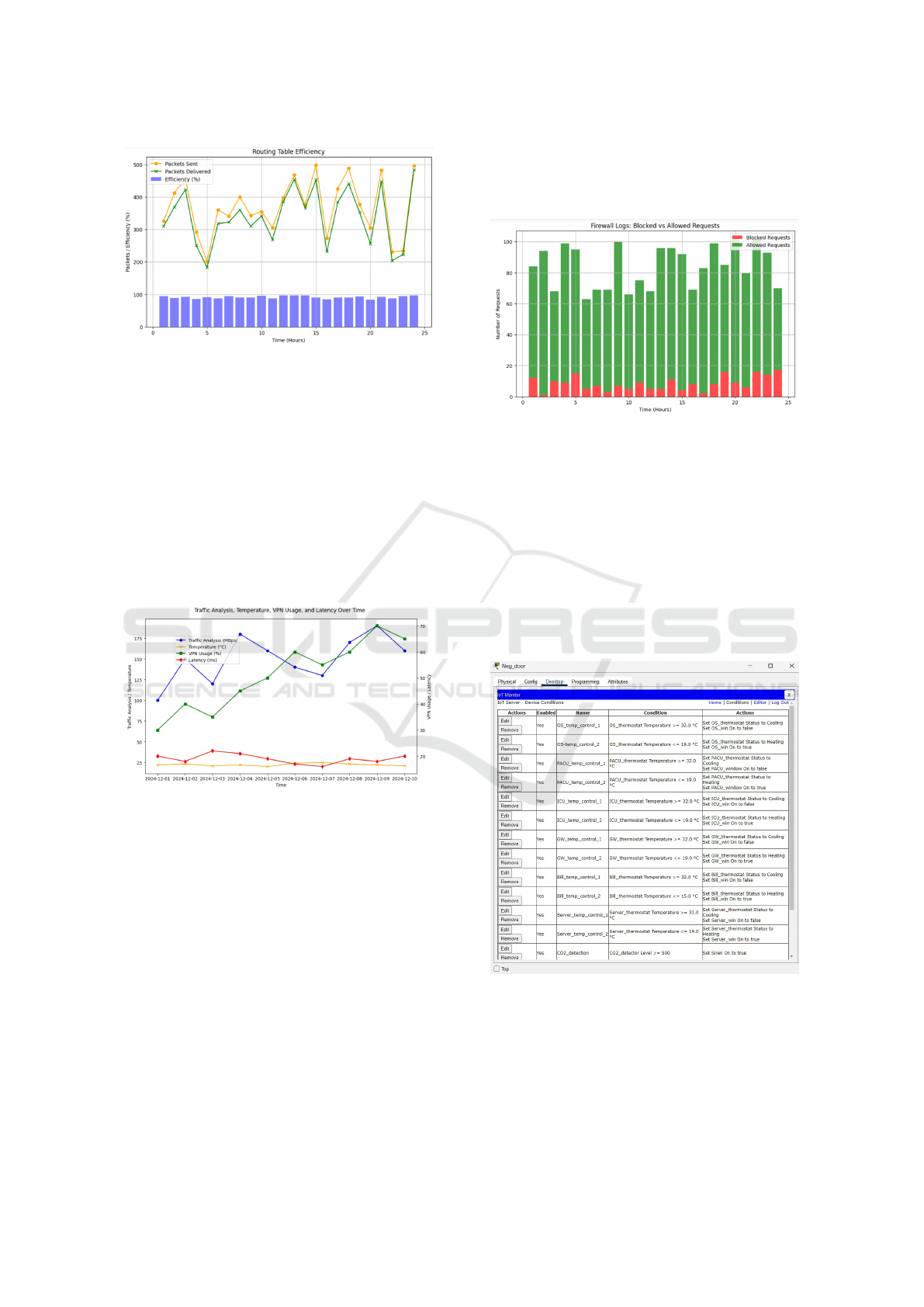
Figure 7: OSPF Routing Accuracy Analysis
ets sent and delivered demonstrates OSPF’s ability
to adapt to dynamic network conditions by maintain-
ing updated routing tables. Efficiency remains consis-
tent at most intervals, reflecting stable network perfor-
mance, while occasional drops, such as at hours 5 and
20, suggest transient issues like increased network
traffic or link updates. These variations highlight the
protocol’s robustness in maintaining data flow despite
disruptions. The consistent performance underscores
the reliability of OSPF in ensuring accurate packet de-
livery and optimal resource utilization across diverse
conditions.
Figure 8: Temperature, VPN Success, Network Traffic and
Latency Analysis Over Time
As shown in Fig. 8, The graph showcases the in-
terplay between traffic analysis (in Mbps), tempera-
ture (°C), VPN usage (%), and latency (ms) within
the configured smart healthcare system. An upward
trend in traffic analysis and VPN usage is observed,
indicating increased network activity and secure com-
munication demands during peak operational periods.
Despite the rise in traffic, latency remains consistently
low (around 20–25 ms), signifying efficient traffic
management and robust VPN implementation. Tem-
perature, a critical IoT metric, remains relatively sta-
ble, reflecting the efficacy of temperature control sys-
tems. The synchronization between high VPN usage
and minimal latency highlights the VPN’s effective-
ness in securely transmitting data without significant
delays. These results validate the system’s capabil-
ity to handle dynamic workloads while ensuring data
security and system performance.
Figure 9: Firewall Traffic Filtering Analysis
As shown in Fig. 9, graph represents firewall ac-
tivity within the Smart and Secured Healthcare Sys-
tem over a 24 hour period, highlighting the number
of blocked and allowed requests. Red bars corre-
spond to blocked requests, representing unauthorized
access attempts or malicious traffic, while green bars
depict legitimate requests from authorized users and
devices. The consistent blocking pattern, with occa-
sional peaks, underscores the firewall’s role in safe-
guarding network traffic and maintaining the health-
care system’s secure operation.
Figure 10: Temperature Control and Smoke Detection
Rules
As shown in Fig. 10, IoT configuration in
Cisco Packet Tracer automates temperature control
and smoke detection across different areas in a smart
and secure healthcare network. The system uses ther-
mostats and windows to regulate temperature within
INCOFT 2025 - International Conference on Futuristic Technology
682

specified ranges for critical zones such as operat-
ing rooms (OS), ICUs, PACUs, and general wards
(GW). For instance, when the temperature exceeds
32°C, cooling is activated, and windows close; when
it drops below 19°C, heating is enabled, and windows
open. Additionally, a CO2 detector monitors air qual-
ity, triggering an alarm if levels exceed 500 ppm, en-
suring prompt action for safety. This setup enhances
environmental control and safety in healthcare facili-
ties.
The comparison of the proposed System to
existing healthcare solutions , Network Configu-
ration and Routing in the proposed system utilizes
subnetting and OSPF for efficient data flow and
reduced congestion. In contrast, existing systems
often use flat topologies, leading to bottlenecks and
poor scalability due to lack of dynamic routing.
Security and Traffic Management are strengthened
in the proposed system through VPN with SSH
encryption and a robust firewall. Existing systems
typically rely on basic security protocols and lack
modern encryption, making them more vulnerable
to breaches. Integration of IoT and Smart Features
enhances safety in the proposed system with auto-
mated IoT devices like fire detection and temperature
control. Many existing systems still use manual
monitoring methods, which are prone to delays and
human error. Scalability and Adaptability are built
into the proposed system, allowing easy expansion
with new devices and protocols as the hospital grows.
Existing systems often struggle to scale, requiring
costly upgrades due to rigid architectures. Cost
Efficiency of the proposed system leverages existing
infrastructure and optimizes resources, reducing both
upfront and long term costs. Existing systems tend
to have high initial costs and ongoing maintenance
expenses, with limited scalability.
5 CONCLUSION
In conclusion, this paper presented the design and im-
plementation of a Smart and Secured Healthcare Sys-
tem, integrating advanced networking technologies
such as OSPF routing, VPN with SSH encryption, and
IoT based safety features. The system demonstrated
efficient routing, secure data transmission, and reli-
able environmental monitoring, as evidenced by the
performance analysis of network traffic, latency, and
IoT metrics. Key findings include the robustness of
OSPF routing in dynamic environments, the effective-
ness of VPN in ensuring data confidentiality, and the
stability of IoT driven temperature and smoke con-
trol systems. Future research could explore the im-
plementation of the system with upcoming protocols
to enhance scalability and adaptability further.
REFERENCES
Abdunabi, R., Basnet, R., and Amin, M. A. (2023). Secure
access control for healthcare information systems: A
body area network perspective. In 2023 IEEE 13th An-
nual Computing and Communication Workshop and
Conference (CCWC), pages 1036–1045.
Alsbou, N., Price, D., and Ali, I. (2022). Iot-based smart
hospital using cisco packet tracer analysis. In 2022
IEEE International IOT, Electronics and Mechatron-
ics Conference (IEMTRONICS), pages 1–6.
Alzu’bi, A., Alomar, A., Alkhaza’leh, S., Abuarqoub, A.,
and Hammoudeh, M. (2024). A review of privacy and
security of edge computing in smart healthcare sys-
tems: Issues, challenges, and research directions. Ts-
inghua Science and Technology, 29(4):1152–1180.
Fu, L., Lin, Q., Li, C., Liu, A., Liu, X., Yang, H., and
Li, H. (2023). Medical iot platform with its appli-
cations in total course of disease and health manage-
ment. In 2023 8th International Conference on Com-
munication, Image and Signal Processing (CCISP),
pages 41–47.
Ghasab, W. H., Hadi, A. A., Alshami, A. G., Radhi, A. D.,
Al-Amri, R. M., and Mousa, A. H. (2024). Construc-
tion a virtual central network for all iraq’s fire station.
Babylonian Journal of Internet of Things, 2024:151–
160.
Jin, H., Luo, Y., Li, P., and Mathew, J. (2019). A review of
secure and privacy-preserving medical data sharing.
IEEE Access, 7:61656–61669.
Karunamurthy, A., Victoire, T. A., Vasuki, M., and Britto,
V. L. (2023). Managing iot devices with routing in-
formation protocol. A Journal for New Zealand Her-
petology, 12(02):2643–2651.
Khan, M. F., Hazela, B., Pandey, D., Singh, K. K., and
Singh, S. (2024). Design of a home server employing
pcie. International Journal of Telecommunications &
Emerging Technologies, 10(1):1–12p.
Madhav, G. S., Kommana, C., Chandana, B. S., and
Khanna, M. (2023). Design and simulation of a
healthcare unit. In 2023 IEEE 3rd International Con-
ference on Technology, Engineering, Management for
Societal impact using Marketing, Entrepreneurship
and Talent (TEMSMET), pages 1–6.
Makhdoomi, A., Jan, N., Handa, P., and Goel, N. (2022).
Conventional and next generation firewalls in network
security and its applications. pages 964–969.
Namo
˘
glu, N. and Ulgen, Y. (2013). Network security vul-
nerabilities and personal privacy issues in healthcare
information systems: A case study in a private hospi-
tal in turkey. Studies in health technology and infor-
matics, 190:126–128.
Pandey, A., Khan, A., Abushark, Y., Alam, M. M., Agrawal,
A., Kumar, R., and Khan, P. R. (2020). Key issues in
Smart and Secured Healthcare System
683

healthcare data integrity: Analysis and recommenda-
tions. IEEE Access, 8:40612–40628.
Priya, R., Sivasankaran, S., Ravisasthiri, P., and Sivachandi-
ran, S. (2017). A survey on security attacks in
electronic healthcare systems. In 2017 International
Conference on Communication and Signal Processing
(ICCSP), pages 0691–0694.
Roy, B., Nivethika, S. D., Manju, G., and Pandian, M. S.
(2023). Comprehensive smart home automation: Net-
work setup, fire prevention, and network security us-
ing cisco packet tracer. In 2023 Intelligent Comput-
ing and Control for Engineering and Business Systems
(ICCEBS), pages 1–4.
Salunkhe, V., Daram, S., Mehra, A., Jain, S., and Agar-
wal, R. (2024). Leveraging microservices architecture
in healthcare: Enhancing agility and performance in
clinical applications. Available at SSRN 4985002.
Samudrala, S. S. H., Thambi, J., Vadluri, S. R., Rajagopal,
S. M., and Bhaskaran, S. (2024). Iot-based fire alarm
system and motion detector: A comprehensive pro-
tocol analysis for enhanced performance. In 2024
IEEE 9th International Conference for Convergence
in Technology (I2CT), pages 1–6.
Sendelj, R. and Ognjanovic, I. (2022). Cybersecurity Chal-
lenges in Healthcare, volume 300.
Walia, S., Iyer, T., Tripathi, S., and Vanaparthy, A. (2023).
Safe and secure smart home using cisco packet tracer.
arXiv preprint arXiv:2304.11827.
Wazid, M., Das, A. K., Mohd, N., and Park, Y. (2022).
Healthcare 5.0 security framework: Applications, is-
sues and future research directions. IEEE Access,
10:129429–129442.
Yudidharma, A., Nathaniel, N., Gimli, T. N., Achmad,
S., and Kurniawan, A. (2023). A systematic litera-
ture review: Messaging protocols and electronic plat-
forms used in the internet of things for the purpose of
building smart homes. Procedia Computer Science,
216(1):194–203.
INCOFT 2025 - International Conference on Futuristic Technology
684
