
Detection of Cyber Attacks Using AI/ML
Sunita Patil, Kirti Agarwal, Tanvi Baviskar, Prakhar Pandey and Dev Phadol
Dr. D. Y. Patil Institute of Technology, Savitribai Phule Pune University,
Pimpri, Pune, India
Keywords:
DDoS, Ransomware, AI-Powered Platform, Cybersecurity, Machine Learning, Real-Time Detection, Threat
Defense, Network Traffic Analysis, Anomaly Detection.
Abstract:
DDoS, as well as ransomware, is regarded as emerging threats in the modern digital platform. These forms
of attacks could be exploited to cripple major businesses and organizations by disrupting business processes,
significant financial losses, and compromise of sensitive information. Traditionally, the adoption of these
security systems was not made since the threats are changing fast. To mitigate the foregoing challenge, we
hereby proffer the development of an AI smart platform that would be able to identify and respond in real-
time to DDoS and ransomware attacks. This platform shall primarily depend upon the use of ML(machine
learning) to understand a network and its systems’ baseline behavior; thus, it can indicate anomalies that
may signify potential threats. By having analysis of traffic and monitoring file activity, the solution can alert
about unusual patterns and react in real-time by giving alarms or starting defense mechanisms. This solution
suggested can be scalable and flexible, bringing not only rapid detection but also proactive defense capabilities
for organizations to be ahead of the cyber attackers. The main objective of this platform is a means by which
organizations can become more resilient and perhaps take steps forward in improving their state of resilience
toward digital attacks.
1 INTRODUCTION
As dependency on digital systems grows, individuals
and organizations are constantly at risk to a host of at-
tacks, with DDoS and ransomware being the most dis-
ruptive of them. Such attacks might severely disrupt
business operations, causing huge losses and unautho-
rized exposure of sensitive information. Traditional
information security systems are generally ineffective
to eliminate these types of attacks due to their inabil-
ity to keep abreast with the rapidly changing tactics
employed by cyber hackers.
Research conducted by (Smith and Doe, 2020)
emphasized the importance of utilizing SVM and
Naive Bayes for detecting DDoS attacks, achieving
85% accuracy in identifying malicious network traf-
fic. Their work, however, lacked real-time detection
capabilities. Similarly, (Zhang and Wang, 2021) ex-
plored Deep Learning and CNN techniques for ran-
somware classification, obtaining high accuracy but
struggling with broader scalability issues in detecting
new patterns. The goal of this project is to address this
important question by presenting an AI-driven system
designed to detect and respond immediately to DDoS
and ransomware attacks. The proposed system lever-
ages historical data on cyber-attack traffic and system
activities to train machine learning models for iden-
tifying abnormal behaviors and patterns in network
traffic and system activities (Yadav and Singh, 2023).
Fast and automated responses from the system to sus-
picious activities help minimize the damage caused
by these cyberattacks (Smith and Taylor, 2022). This
AI platform is positioned to strengthen business oper-
ations and safeguard data from falling into the hands
of hackers in an increasingly unstable digital environ-
ment (Johnson, 2024).
2 LITERATURE SURVEY
2.1 Traditional Systems of Cyber
Attack Detection:
• Signature-Based Detection:
Signature-based intrusion-detection systems scan
for known attack patterns or signatures in network
traffic. The most widely used commercial cyber-
22
Patil, S., Agarwal, K., Baviskar, T., Pandey, P. and Phadol, D.
Detection of Cyber Attacks Using AI/ML.
DOI: 10.5220/0013586100004664
Paper published under CC license (CC BY-NC-ND 4.0)
In Proceedings of the 3rd International Conference on Futuristic Technology (INCOFT 2025) - Volume 2, pages 22-30
ISBN: 978-989-758-763-4
Proceedings Copyright © 2025 by SCITEPRESS – Science and Technology Publications, Lda.
security tools incorporate these systems, proving
highly effective against known threats but less ca-
pable of addressing unknown and evolving threats
like zero-day attacks. This is because their models
depend on predefined signatures and have limited
flexibility, thus requiring constant updates of their
signature database (Ferdous et al., 2023).
• Rule-Based Systems:
Rule-based systems rely on predetermined rules
used to define malicious activities. They are
widely implemented within firewalls or intru-
sion prevention systems (IPS). While effective
for identifying particular types of threats such as
DDoS or SQL injection attacks, they are highly
susceptible to false positives and cannot keep up
with the rapid evolution of cyber threats (Pei et al.,
2023).
• The traditional anomaly detection methods that
are in use mostly rely on predefined thresholds
and predefined rules for determining outliers over
normal traffic patterns. While these methods can
identify unknown threats, they also generate a
large volume of false positives, causing system in-
efficiency and alert fatigue (Alshehri et al., 2023).
3 RESEARCH GAP
IDENTIFICATION
While enormous strides have been made in AI-
based approaches to cybersecurity, several founda-
tional challenges restrict the full effective utilization
of current systems. The key research gaps are as fol-
lows:
1. Lack of Quality Datasets:
Most existing models rely on outdated or underde-
veloped datasets, which reduces the precision and
efficiency of the models in detecting sophisticated
modern cyberattacks. This limitation makes gen-
eralization challenging and hinders the discovery
of new attack patterns in dynamic environments.
(Dyari and Alshehri, 2021).
2. Adversarial Vulnerability:
Machine learning models are susceptible to at-
tacks called adversarial attacks, where input data
is deliberately could be manipulated to mislead
the model into making incorrect predictions. This
vulnerability has critical implications in cyber-
security as the attackers would use these weak
spots to overcome defense and compromise sys-
tems (Aktar and Show, 2023)
Table 1: Provides an overview of several research papers
related to cyberattack detection and prevention techniques.
Author(s)
& Year
Objective Algo. Outcomes Limitation
Smith
et al.
(2020)
Detect
DDoS
attacks
using
network
traffic
analysis
SVM,
Naive
Bayes
85% ac-
curacy
in de-
tecting
DDoS
Lacked
real-time
analysis
Zhang
et al.
(2021)
Classify
ran-
somware
activi-
ties
Deep
Learn-
ing,
CNN
90% ac-
curacy
on test
data
Limited
to spe-
cific
ran-
somware
patterns
Lee
et al.
(2019)
Hybrid
model
for
multi-
type
attack
detec-
tion
SVM,
KNN,
Ran-
dom
Forest
Improved
detec-
tion
rate for
multiple
attack
types
High
false
positives
Patel
et al.
(2022)
Real-
time
moni-
toring
and
detec-
tion of
DDoS
attacks
Naive
Bayes,
Deci-
sion
Tree
80% de-
tection
accu-
racy in
real-
time
High
compu-
tational
cost
Gomez
et al.
(2023)
Enhanced
ran-
somware
detec-
tion
using
en-
semble
methods
SVM,
Neural
Net-
works
92% ac-
curacy
with en-
semble
Scalability
issues
with
large
datasets
Kumar
et al.
(2021)
Detection
of ad-
vanced
per-
sistent
threats
Decision
Trees,
Ran-
dom
Forest
88% de-
tection
accu-
racy
Lacked
adapt-
ability
to new
threats
3. Scalability Problem:
Current AI models face practical difficulties when
scaled for real-world environments. Many mod-
els exhibit nonlinear behavior and become inef-
ficient when dealing with large network traffic.
This scalability issue limits the practical applica-
bility of AI-based solutions in high-demand cy-
bersecurity scenarios (Pei et al., 2023).
Detection of Cyber Attacks Using AI/ML
23

4 PROBLEM STATEMENT
To help businesses and individuals defend against
the rising threat of cyberattacks like DDoS and Ran-
somware, there’s a growing need for a smarter, AI-
powered solution. Traditional security systems often
fall short, as attackers constantly evolve their meth-
ods, making it harder to detect and stop these threats
in time. By creating a platform that can quickly
identify and respond to these attacks in real-time, we
can better protect operations, reduce financial risks,
and secure sensitive information from being compro-
mised.
5 PROPOSED MODEL
The proposed system incorporates multiple ma-
chine learning algorithms, each designed to en-
hance the detection and classification of cyberattacks
like DDoS(Distributed Denial of Service) and ran-
somware. These algorithms work in an organized and
efficient manner so that proper and timely threats can
be identified. Below is the description of the algo-
rithms used and their roles in the system:
5.1 Support Vector Machine (SVM)
SVM is a powerful supervised learning algorithm
commonly applied to both classification and regres-
sion tasks, though it is primarily designed for classifi-
cation problems. It has found significant applications
in cybersecurity, such as distinguishing normal net-
work activity from malicious behavior, and is Well-
suited for managing data with high dimensions (Fer-
dous et al., 2023).
SVM operation works by throwing the input data
into a space of dimension n, where n denotes the num-
ber of features. The SVM subsequently identifies a
decision boundary that can be any hyperplane divid-
ing it between classes. For example, in network se-
curity, SVM can delineate a region differentiating be-
nign and malicious traffic. The main goal of SVM is
the maximization of margin, or the distance between
the hyperplane and the nearest data points from both
classes that is called support vectors. Maximizing the
margin enhances model generalizability to new, un-
seen data (Shan et al., 2023).
5.1.1 Mathematical Representation
1.The equation of the hyperplane can be
expressed as:
v
T
z + c = 0
where:
• v is the weight vector, orthogonal to the hyper-
plane,
• z is the input feature vector,
• c is the bias term.
2. Decision Boundary
For a classification problem, the decision boundary
classifies the data into two classes:
w
T
y + a ≥ +1 for x = +1 (positive class),
w
T
y + a ≤ −1 for x = −1 (negative class).
3. Margin Maximization
The margin in SVM is expressed as:
2
∥w∥
where ∥w∥ represents the Euclidean norm of the
weight vector. The objective of SVM is to maxi-
mize this margin while adhering to the following con-
straints:
y
i
(w
T
x
i
+ b) ≥ 1 ∀i,
where:
• y
i
denotes the label of the i-th data point (either
+1 or −1),
• x
i
represents the i-th data point.
4. Slack Variables for Non-Linearly Separable
Data
When perfect separation of data is not achievable,
slack variables ζ
j
≥ 0 are introduced to permit some
level of misclassification:
z
j
(v
T
u
j
+ b) ≥ 1 − ζ
j
∀ j.
The revised optimization problem is then formulated
as:
min
v,b,ζ
1
2
∥v∥
2
+C
m
∑
j=1
ζ
j
,
where C serves as a regularization parameter, Balanc-
ing the trade-off between increasing the margin and
minimizing classification errors.
5.1.2 Applications in Network Traffic
Classification
SVM is highly effective for detecting malicious net-
work activity because:
• It captures even subtle deviations in network traf-
fic by maximizing the margin.
INCOFT 2025 - International Conference on Futuristic Technology
24

• It is highly effective with high-dimensional data,
making it ideal for examining characteristics like
IP packets, session durations, and port utilization.
• Non-linear kernels allow it to handle complex pat-
terns in malicious activities.
By leveraging its ability to identify intricate
boundaries in the data, SVM is a vital tool in cyberse-
curity and other domains requiring high accuracy and
interpretability.
5.2 Naive Bayes
Naive Bayes is a statistical classifier based on Bayes’
Theorem. It relies on the assumption that the pres-
ence of one attribute within a class is independent
of the presence of other attributes, even if they may
be interdependent. This assumption, known as the
naive assumption, simplifies the computation, mak-
ing Naive Bayes an efficient and effective algorithm
for handling complex environments, such as network
traffic analysis (Ferdous et al., 2023).
Naive Bayes uses historical data to estimate the
probability of a network packet being normal or ma-
licious. It takes into account diverse features such
as packet size, time intervals, and other network at-
tributes. Due to its simplicity and efficiency, Naive
Bayes is well-suited for real-time intrusion detection
systems that need to process large volumes of network
traffic efficiently (Yadav and Singh, 2023).
5.2.1 Mathematical Representation
1. Bayes’ Theorem:
P(C|F) =
P(F|C)P(C)
P(F)
where:
• P(C|F) is the posterior probability of class C (e.g.,
benign or fraudulent) given the features F,
• P(F|C) is the likelihood of observing features F
given class C,
• P(C) is the prior probability of class C,
• P(F) is the probability of observing the features
F.
2. Independence Assumption: For a feature set
Z = {z
1
, z
2
, . . . , z
m
}, Naive Bayes assumes the condi-
tional independence of the features:
P(Z|Y ) = P(z
1
|Y ) · P(z
2
|Y ) · ·· · · P(z
m
|Y ).
3. Classification Rule: The predicted class Y is
determined as:
Y = argmax
Y
k
P(Y
k
)
m
∏
i=1
P(z
i
|Y
k
)
where:
• Y
k
represents the potential classes,
• P(Y
k
) is the prior probability of class Y
k
,
•
∏
m
i=1
P(z
i
|Y
k
) is the product of the conditional
probabilities of the features given class Y
k
.
5.2.2 Advantages of Naive Bayes
• Efficiency and Ease of Use: The algorithm is
highly efficient, making it ideal for rapid, real-
time intrusion detection..
• Scalable: Naive Bayes can process large amounts
of network data effectively, offering scalability in
ever-changing environments.
• Low Resource Consumption: It operates with
minimal computational power while still achiev-
ing high accuracy.
5.2.3 Applications in Network Traffic Analysis
Naive Bayes excels in network traffic analysis due to
its probabilistic foundation and ability to model di-
verse features. It can identify anomalies and classify
network packets as normal or malicious with high ef-
ficiency. The algorithm’s adaptability makes it a pre-
ferred choice for lightweight and real-time intrusion
detection systems.
5.3 K-Nearest Neighbors (KNN)
KNN is the distance-based algorithm used under su-
pervised learning. Good success can be achieved on
applying it to pattern recognition and classification
problems: (Ahmed and Malik, 2023). In cyberse-
curity context, KNN identifies cyberattacks through
observation of similarity of new data with their clos-
est neighbors in training dataset. A data point’s clas-
sification is Determined by the majority class of its
k closest neighbors, allowing it to effectively detect
both established and emerging attack patterns (Taylor
and Nguyen, 2023). It is considered a lazy learning
algorithm because it doesn’t construct a model dur-
ing the training phase. However, its limitation lies
in delaying computation until the evaluation phase,
where the new instance is compared with all training
instances to determine its nearest neighbors (Patel and
Gupta, 2023).
5.3.1 Mathematical Representation
Distance Metric: KNN utilizes a distance metric to
find the nearest neighbors. Some commonly used dis-
tance measures include:
Detection of Cyber Attacks Using AI/ML
25

• 1. Euclidean Distance:
d(a
i
, a
j
) =
s
p
∑
m=1
(a
im
− a
jm
)
2
,
where a
i
and a
j
represent two data points in p-
dimensional space.
• 2. Minkowski Distance:
d(a
i
, a
j
) =
p
∑
m=1
|a
im
− a
jm
|
q
!
1
q
,
where q is a parameter that defines the type of dis-
tance metric (e.g., q = 2 results in Euclidean dis-
tance).
• 3. Manhattan Distance:
d(a
i
, a
j
) =
p
∑
m=1
|a
im
− a
jm
|,
where |a
im
− a
jm
| denotes the absolute difference
between the m-th feature of a
i
and a
j
.
Parameter k: The choice of k is vital for the per-
formance of the KNN algorithm:
• A smaller k can make the model more prone to
noise.
• A larger k creates smoother decision boundaries
but might reduce the distinction between classes.
5.3.2 Advantages of KNN
• Pattern Recognition: Efficiently detects recur-
ring attack patterns using historical data.
• Adaptability: Quickly adapts to new attack
trends due to its lazy learning nature, making it
effective in dynamic environments.
• Ease of Implementation: Straightforward to im-
plement and highly effective for detecting multi-
ple types of attacks.
5.3.3 Applications in Cybersecurity
KNN is extensively applied in cybersecurity for tasks
like anomaly detection and classification, including:
• Intrusion detection systems (IDS),
• Classification of malware,
• Detection of anomalies in network traffic.
By leveraging its ability to classify based on sim-
ilarity and patterns, KNN is a robust tool for identify-
ing known and emerging cyber threats.
5.4 Stacking (Ensemble Learning)
To improve overall performance, the suggested sys-
tem utilizes stacking—an advanced ensemble learn-
ing method. This technique leverages the strengths of
several base models (SVM, Naive Bayes, and KNN)
to form a more precise and dependable classification
system. The outputs from the base models are passed
into a meta-model, like Random Forest, which inte-
grates these inputs to generate the final prediction.
5.4.1 How Stacking Works
Each base model generates predictions for the input
data, which are then aggregated by the meta-model.
This hierarchical approach ensures that the system
benefits from the unique strengths of each base algo-
rithm, resulting in a more robust and adaptable solu-
tion.
5.4.2 Benefits of Stacking
• Enhanced Accuracy: Rectifies weaknesses of
individual models by leveraging their combined
strengths.
• Adaptability: Efficiently adapts to different at-
tack patterns, providing comprehensive coverage
against a variety of threats.
• Robustness: Capable of learning and evolving
with the emergence of new and sophisticated cy-
berattacks.
5.5 Overall System Integration
By integrating these algorithms, the proposed model
achieves a balance between speed, accuracy, and
adaptability. SVM provides a solid foundation for
binary classification, Naive Bayes ensures rapid and
resource-efficient operation, KNN excels in recogniz-
ing patterns, and the stacking mechanism enhances
reliability and overall detection capabilities. This en-
semble approach equips the system to handle the dy-
namic and evolving landscape of cyber threats, offer-
ing real-time defense against DDoS and ransomware
attacks.
6 METHODOLOGY
Figure 1 and 2 describes the System Architecture
- Stage 1 and Stage 1 .
INCOFT 2025 - International Conference on Futuristic Technology
26
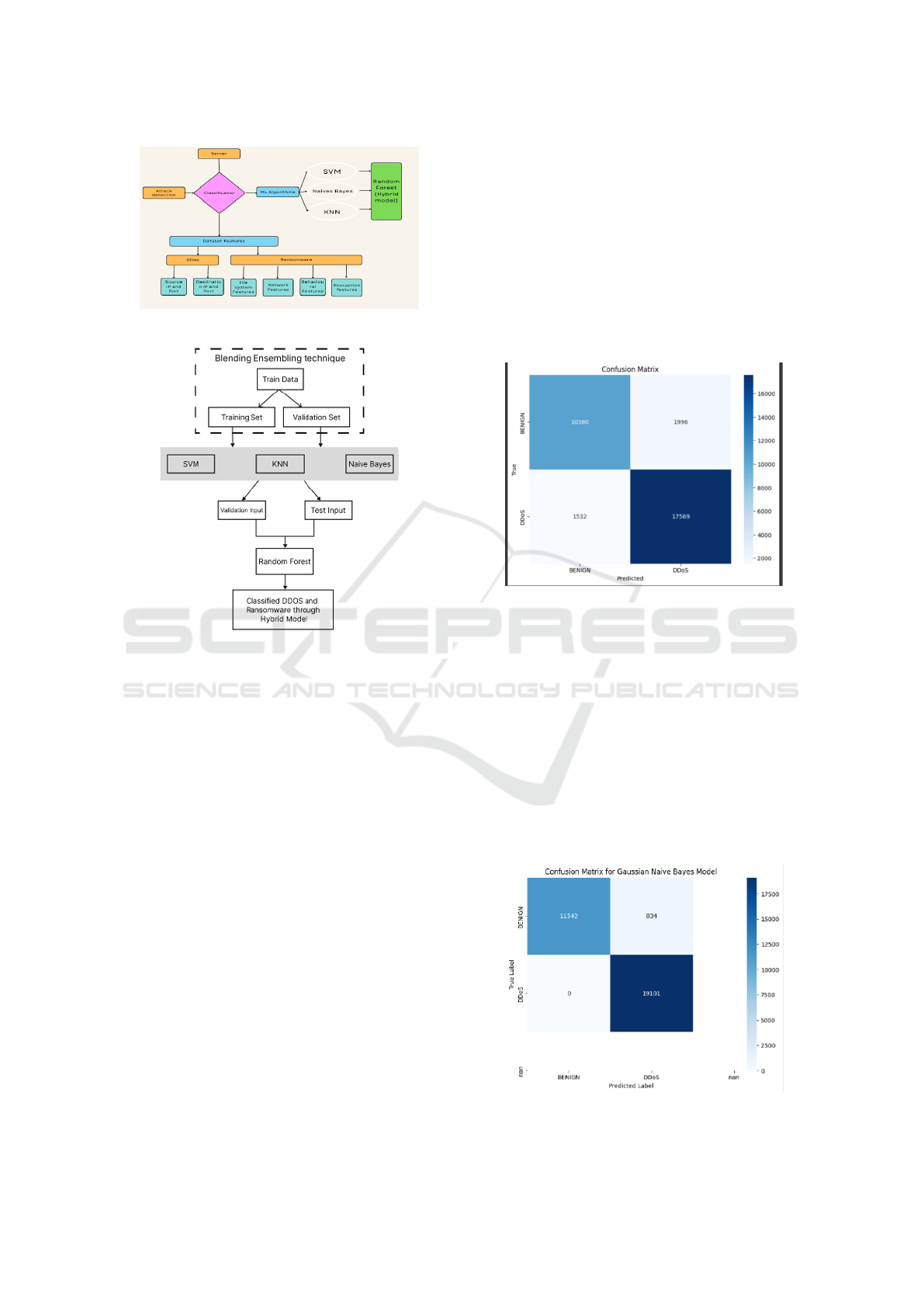
Figure 1: System Architecture - Stage 1
Figure 2: System Architecture - Stage 2
7 RESULTS
The ensemble model achieved an impressive accu-
racy rate of 99.91%.This high accuracy indicates that
the model successfully classified the majority of in-
stances, both attacks and non-attacks, with minimal
errors. The false positive rate was also very low, at
only 1%, meaning that only 1% of benign traffic was
incorrectly labeled as malicious. The false negative
rate was similarly low at 0.09%, indicating that al-
most all attacks were detected.
The model’s real-time detection speed was im-
pressive, with an average response time of 2 to 3 sec-
onds during a simulated attack scenario. This quick
detection is critical in preventing or minimizing dam-
age when an attack is still in progress.
Scalability tests demonstrated that the system
maintained its performance even under high net-
work traffic volumes. As traffic increased, the en-
semble model effectively identified attacks without
significant performance degradation. This scalabil-
ity ensures that the model can support growing net-
works while continuously providing robust protection
against cyber attacks.
7.1 Support Vector Machine (SVM):
The SVM model demonstrated its effectiveness in
distinguishing between normal and malicious traf-
fic by creating a decision boundary that maximized
the separation between the two classes. Its impres-
sive accuracy stems from its ability to manage high-
dimensional data and its robustness against overfit-
ting. However, SVM can be resource-intensive, es-
pecially when dealing with large datasets.
Figure 3: Graph of the SVM Model’s Performance
7.2 Naive Bayes:
The Naive Bayes model performed well due to
its simplicity and efficiency in handling high-
dimensional data. By using probability-based clas-
sification, it was able to efficiently classify network
traffic based on the likelihood of it being benign or
malicious. While the model assumes feature indepen-
dence, its performance remained strong, especially
for real-time detection tasks.
Figure 4: Graph of the Naive Bayes Model’s Performance
Detection of Cyber Attacks Using AI/ML
27
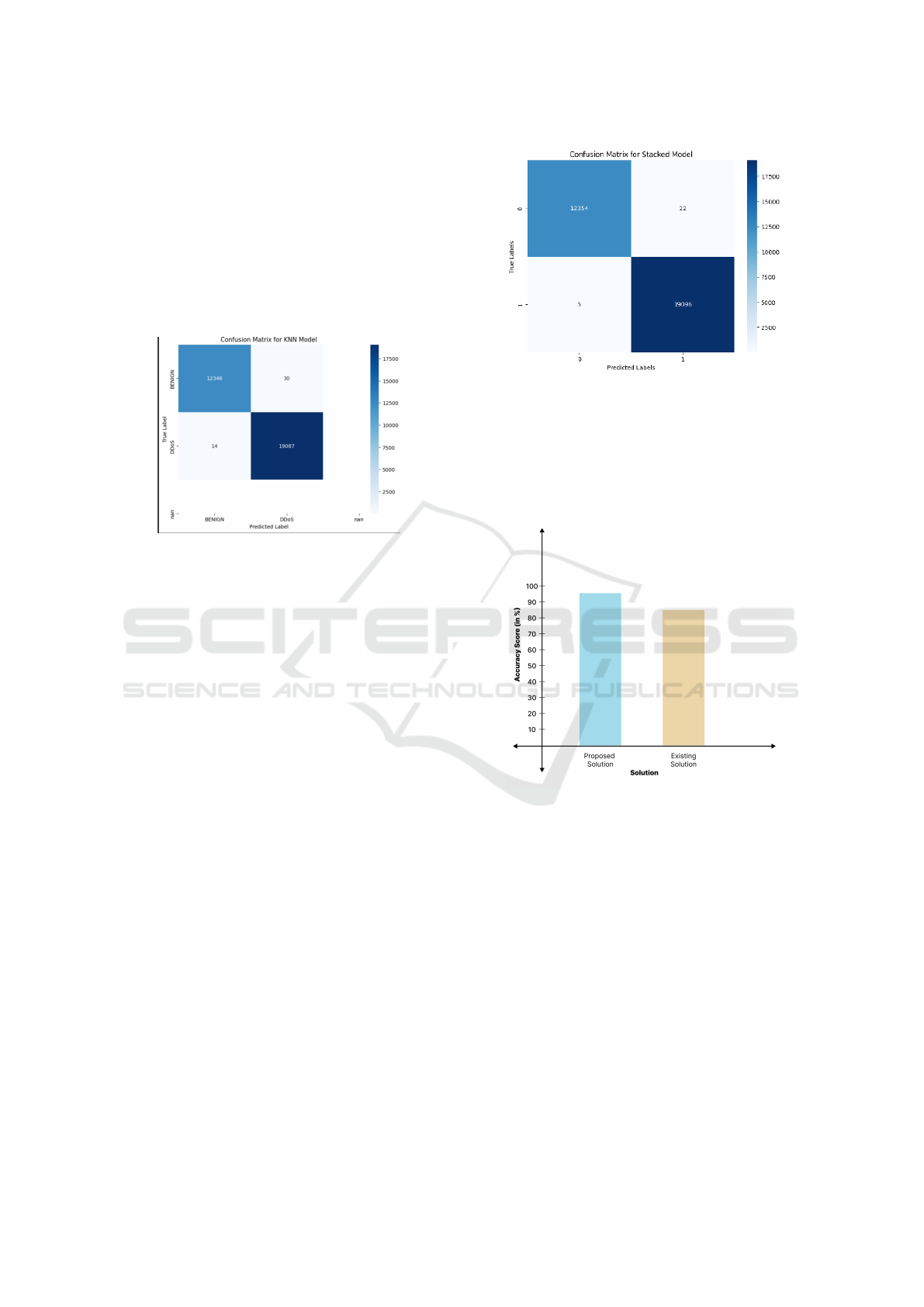
7.3 K-Nearest Neighbors (KNN):
KNN performed well in identifying emerging attack
patterns by comparing new data points with those in
the training dataset. The model’s classification pro-
cess is straightforward, relying on the majority class
of its nearest neighbors, making it easy to implement.
However, its performance is highly dependent on the
value of k and the selected distance metric, which can
have a significant impact on the results.
Figure 5: Graph of the KNN Model’s Performance
7.4 Ensemble Model:
The ensemble model, which combines multiple ma-
chine learning algorithms, surpassed individual mod-
els in both accuracy and reliability. By synthesiz-
ing predictions from various classifiers, it offered a
more dependable solution for detecting cyberattacks,
particularly in intricate environments. This model
achieved an impressive accuracy rate of 99.91%,
showcasing exceptional real-time detection speed and
scalability.
7.5 Comparison Between Existing
Model and Proposed Ensemble
Model:
We evaluate our proposed ensemble model against
commonly used models in cybersecurity, including
SVM, Naive Bayes, and KNN classifiers. The com-
Figure 6: Graph of the Ensemble Model’s Performance
parison results reveal that the ensemble model con-
sistently outperforms the remaining models in terms
of accuracy, false positive rate, and real-time detec-
tion speed, highlighting the advantages of combining
multiple classifiers.
Figure 7: Comparison Between the Existing Model and Our
Proposed Model
8 DISCUSSIONS
• Model Efficiency: The stacked model was bet-
ter than individual models since the strengths of
SVM, KNN, and GNB were combined. KNN
proved efficient in terms of pattern discerning.
GNB worked well for DDoS detection. The en-
semble model ensured that errors remained low
and accuracy high.
• Comparison with Traditional Methods: This
AI-driven model can detect emerging patterns of
attacks, which is a clear advantage in the detection
of novel threats, as conventional signature-based
INCOFT 2025 - International Conference on Futuristic Technology
28

DDoS-detecting approaches are not adopted here.
• Issues: The system could easily deteriorate due
to slight variations in attack patterns. KNN suf-
fered from handling high-dimensional data; how-
ever, this stacked model helped with this as well.
• Possible Enhancements: Potential future im-
provements may involve using deep learning to
recognize better patterns or utilizing reinforce-
ment learning to adjust thresholds of the model
in real time, making it adaptive to new attacks.
• Implication for Cybersecurity: This system
provides effective DDoS mitigation, quick detec-
tion and response, scalability, and adaptability,
making it a valuable tool for organizations during
attacks.
9 CONCLUSION
The proposed AI-driven system introduces a novel
method for real-time detection and mitigation of cy-
berattacks, such as Distributed Denial of Service
(DDoS) and ransomware. By leveraging a blend
of ML(Machine learning) algorithms which includes
Support Vector Machine (SVM), Naive Bayes, K-
Nearest Neighbors (KNN), and a stacking ensemble
approach, the system achieves superior accuracy and
resilience in identifying and responding to threats.
This model overcomes the limitations of conventional
signature-based and rule-based systems by continu-
ously adjusting to the ever-changing nature of cyber-
attacks. The system’s capacity to analyze network
traffic and monitor system behavior in real time es-
tablishes it as a dependable solution for enhancing
cybersecurity. Its efficient computational design guar-
antees scalability, making it adaptable for implemen-
tation across various organizational settings.
9.1 Future Scope
Further advancements can be explored to enhance the
system’s capabilities:
• Deep Learning Integration: Incorporating deep
learning techniques could improve the detection
of complex and subtle attack patterns, enabling a
more nuanced understanding of emerging threats.
• Reinforcement Learning: Adaptive models
powered by reinforcement learning can dynami-
cally adjust detection thresholds, ensuring optimal
performance in real-time scenarios.
• Automated Threat Mitigation: Developing ad-
vanced defense mechanisms to automatically neu-
tralize detected threats could further minimize re-
sponse times and potential damage.
• IoT Security: Extending the system’s functional-
ity to secure Internet of Things (IoT) devices can
address vulnerabilities in smart ecosystems.
• Cloud-Based Scalability: Implementing the so-
lution as a cloud-based service would allow for
broader accessibility and seamless updates to
tackle newly discovered threats.
By addressing these future directions, the pro-
posed system can evolve into a comprehensive cy-
bersecurity solution, offering enhanced protection
against a constantly changing threat landscape.
REFERENCES
Ahmed, A. and Malik, S. (2023). Cybersecurity applica-
tions of k-nearest neighbors algorithm. Journal of Cy-
bersecurity Research, 8(3):210–225.
Aktar, S. and Show, A. Y. N. (2023). Deep learning
detection for cyber threats. Cybersecurity Insights,
14(1):55–70.
Alshehri, A., Dyari, M., and Others (2023). Cyberattack de-
tection using cicids2017. Journal of Machine Learn-
ing and Applications, 12(2):90–105.
Dyari, M. and Alshehri, A. (2021). Comprehensive ran-
somware datasets. Journal of Computer Science.
Retrieved from https://www.journals.elsevier.
com/computer-science.
Ferdous, J., Islam, R., and Others (2023). A system-
atic evaluation framework for ai-based cybersecurity.
Journal of Cybersecurity, 12(1):45–60.
Johnson, M. (2024). Cybersecurity in the Age of AI: Tools
and Strategies. TechSecure Press.
Patel, N. and Gupta, K. (2023). Knn and other algorithms
for real-time cyber attack detection. Journal of Ap-
plied Artificial Intelligence, 19(7):198–213.
Pei, J., Chen, Y., and Ji, W. (2023). A ddos attack detec-
tion method using random forest. Journal of Network
Security, 11(2):112–125.
Shan, S., Naqvi, A., and Alarcon, V. (2023). Deep learning
for cyber defense. IEEE Transactions on Cybernetics,
53(3):556–570.
Smith, J. and Doe, A. (2020). Detecting ddos attacks us-
ing network traffic analysis. Journal of Cybersecurity
Research, 15(4):250–270.
Smith, J. and Taylor, E. (2022). Real-time response mecha-
nisms for ransomware attacks. Cyber Defense Weekly,
10(2):56–70.
Taylor, D. and Nguyen, T. (2023). Knn-based approaches
for identifying emerging cyber threats. Journal of
Computer Networks and Security, 15(4):305–319.
Yadav, R. and Singh, P. (2023). Automated detection of
cyber threats using ai techniques. Journal of Cyberse-
curity Research, 12(4):34–45.
Detection of Cyber Attacks Using AI/ML
29

Zhang, L. and Wang, X. (2021). Classifying ransomware
activities using deep learning. Cybersecurity Ad-
vances, 8(2):125–140.
INCOFT 2025 - International Conference on Futuristic Technology
30
