
Application of Block Chain Technology in Cross Border Food
Information Tracing
Jing Sun
*
and Xueling Zheng
Health and Elderly Caring Industry School, Shandong Institute of Commerce and Technology,
Jinan 250103, Shandong, China
Keywords: Block Chain, Information Traceability, Cross-Border Food, PBFT Algorithm
Abstract: In recent years, blockchain technology has swept the world, because of its complete integration of encryption
algorithm, chain storage, consensus mechanism and other technologies, which makes it a transaction
mechanism that can conduct business communication when distributed nodes are not familiar with each other.
It breaks the traditional trading mechanism of centralized management, high cost, opacity and other problems.
This paper mainly studies the application of blockchain technology in cross-border food information
traceability. This paper proposes an improved PBFT algorithm based on node partitioning, introduces
partitioning and credit mechanism into the PBFT algorithm, and describes the algorithm improvement process
in detail. According to the consensus algorithm of improved Ethereum blockchain, a traceability design
scheme of food supply chain based on improved Ethereum blockchain is designed. Firstly, the traceability
process of supply chain is analyzed and a traceability process scheme based on blockchain is designed. Then,
a traceability system architecture based on blockchain technology is established and the specific
implementation method of the traceability system architecture is explained.
1 INTRODUCTION
With the improvement of people's living standards,
consumers pay more attention to the quality and
safety of products than to the basic needs such as price
and variety. In recent years, food, medicine and other
industries that are directly related to people's life and
health have repeatedly experienced quality problems,
which have significantly increased consumers' doubts
about product quality and safety and their sensitivity
to it (Tsang and Choy, et al. 2019). In recent years,
such as "melamine", "inferior gelatin event",
"longevity vaccine event" and so on product quality
and safety incidents after exposure, these bad
products not only harm the health of body and mind
of the consumer, more sharply reduces the consumer's
trust in the food and drug quality and safety, but also
make the enterprise suffered huge economic losses
(Tan and Gligor, et al. 2020). Therefore, it is
imperative to establish an effective food traceability
system. Using modern information management
technology to assign a unique identification code to
each product, the identification code records the
relevant process information, which can realize the
tracking and traceability of the product (Sharma and
Jhamb, et al. 2020). Once quality problems are found
after the products are marketed, they can be quickly
traced out and recalled to reduce food safety risks
(Pendrous, 2017). In addition to the food field,
traceability technology has also been applied in the
fields of medicine, tobacco, daily chemical industry
and so on (Sander and Semeijn, et al. 2018). Based on
the technological progress and the need of market
competition, consumers can scan the QR code pasted
on the goods through mobile phones to obtain the
business unit, customs declaration number, entry time
and other information of the goods, which has
become a supplementary means for consumers to
obtain information and government departments to
master data (Mengjia and ZENG, et al. 2019).
The application of blockchain in the field of
traceability has its unique advantages and is currently
a hot research direction (Kamath, 2018). The
retroactive application of blockchain technology also
appeared in the world one after another (Deng and
Feng, 2020). The European Union has established a
series of food control systems to address food safety
issues, and proposed for the first time that food can
be traced back to the source of raw materials from the
table (Gao and T-PBFT, 2019). The United States has
532
Sun, J. and Zheng, X.
Application of Block Chain Technology in Cross Border Food Information Tracing.
DOI: 10.5220/0013548500004664
Paper published under CC license (CC BY-NC-ND 4.0)
In Proceedings of the 3rd International Conference on Futuristic Technology (INCOFT 2025) - Volume 1, pages 532-536
ISBN: 978-989-758-763-4
Proceedings Copyright © 2025 by SCITEPRESS – Science and Technology Publications, Lda.

issued a series of bills on food safety guarantee and
risk control, elevating food quality management to
the national level (Zheng and Feng, et al. 2021). The
French government also proposed to establish a food
safety traceability system, and the traceability
information should cover the operation of each node
of the food supply chain. India has also established a
food traceability system, requiring enterprises
responsible for production and processing to record
the operation information of the whole process of
food from raw materials to finished products (Han-
Back and Moo-Sub , et al. 2018). Meanwhile, the
processing company's own information should be
prepared and recorded in the traceability label, so as
to ensure that food can be traced back to the source of
food production when consumers buy it (Zhao and
Wu, et al. 2020).
Based on the blockchain technology and in
combination with the cross-border food traceability
project, the research of this paper aims at the
problems in the cross-border food traceability system,
and makes improvements on the consensus of the
application of blockchain and the additional
difficulties in nodes, so as to build an efficient and
accurate traceability food production chain.
2 APPLICATION OF
BLOCKCHAIN TECHNOLOGY
IN FOOD TRACEABILITY
2.1 Blockchain - Based Traceability
Architecture
Blockchain-based food traceability system
architecture design, the architecture from bottom to
top is divided into operation layer, data acquisition
layer, network layer, data layer, display layer and user
layer, a total of 6 layers, each layer corresponds to
different technical applications and entity objects.
Through iot equipment operation process of each link
of the supply chain data, and through the wireless
network transmission to the supply chain of each
node, and then through the supply chain elected
master node data information for the deal and food
packaged into data information blocks, the entire
network to reach consensus, chain block, block chain
data will be stored in the block chain network, each
node. The information on the chain can not be
tampered with and is true and reliable. Users can trace
the source of consumer food and inquire the
production process of products through the
development platform.
2.1.1 Operation Layer
Each link of the supply chain includes the selection
and purchase of raw materials, food processing,
processed food inspection, food warehouse storage,
processed food packaging and packaged food sales.
The raw material supplier shall purchase raw
materials from the place of production in accordance
with national regulations and company rules, and
input the variety, quantity and source of raw materials
into the system.
2.1.2 Data Acquisition Layer
When the whole supply chain is running, each stage
chooses its own collection method according to its
own characteristics. In the raw material procurement
link of the supply chain, raw material information can
be input through a handheld terminal and generate a
two-dimensional code. Processing manufacturers can
scan the two-dimensional code to check the detailed
information of raw materials and verify the
authenticity of the information when purchasing raw
materials. Raw materials in the production line for
processing, through the intelligent sensor raw
material processing production environment in the
process of information into the system, and generate
the corresponding qr code information, quality
inspection personnel on the inspection of qualified
products to the food with food quality inspection
information, such as processed foods after complete
quality inspection and packaging will complete qr
code information on the package. In the process of
logistics transportation, an RFID tag is assigned to
each package to facilitate the query of package
information in transportation and transit warehouses.
Consumers using mobile terminals can scan the QR
code on the food package to understand the detailed
operation of the food.
2.1.3 Network Layer
The network layer mainly uses wireless transmission
technology. GPRS can provide users with long
distance data transmission, and can realize the
transparent transmission of collected data. ZigBee
and WiFi signal frequencies are the same, but
implementation standards are different. ZigBee has
good stability, small data transmission and low power
consumption, and is suitable for use in the production
stage of raw materials. WiFi has poor stability, short
transmission distance but large data volume, which is
convenient and practical for consumers to query the
detailed information of goods.
Application of Block Chain Technology in Cross Border Food Information Tracing
533

2.1.4 Data Layer
Each node of the supply chain detects data through
Internet of Things devices and transmits it to its own
platform via wireless network. After receiving the
data, the platform will broadcast it to other nodes of
the supply chain. Each node of the supply chain first
selects the master node, and then the master node
sorts the data information received according to the
time stamp and packages a certain amount of data to
generate blocks. Then the blocks are broadcast to
other nodes of the supply chain, and consensus is
reached on the generated blocks through DPOA and
PBFT consensus mechanism and the blocks are
linked up.
2.1.5 Display Layer
This layer designs the relationship between user
authentication and data access rights and defines the
block chain data access interface. For qualified users,
they can query the information collected in the whole
link of the supply chain through the data access
interface and display the information to users in
accordance with certain specifications.
2.1.6 User Layer
The user layer reflects the division of each link of the
supply chain into suppliers, processing
manufacturers, carriers, retailers, etc., as well as
regulatory authorities according to their different
functions.
2.2 PBFT Algorithm and its
Improvement
2.2.1 PBFT Algorithm
PBFT is a distributed consistency algorithm based on
state machine copy replication. To ensure the normal
operation of the algorithm, a view replacement
protocol, a checkpoint protocol and a consistency
protocol are designed in PBFT.
2.2.1.1 View Replacement Protocol
In the PBFT consensus process, all node states must
be consistent, that is, in the same view. A view
contains a primary node and several other backups,
all of which have the same view number V. The
master node receives requests from clients in order of
time, and initiates consensus protocol to broadcast
requests to the slave nodes. View changes are
triggered by a timeout mechanism that prevents the
slave node from waiting indefinitely for the request to
execute. If the slave node I does not receive the
request sent by the master node in view v over
timeout, the slave node will start the view
replacement protocol and change the system view
number v to v+1 to elect a new master node. In PBFT,
assume that the set of all nodes is S and the node
numbers are {0,1,2... , | S | - 1}, when from the node
execution view change agreement, view code v + 1,
the new master node number calculated as follows:(1)
||mod Svp =
(1
)
2.2.1.2 Checkpoint Protocol
The information of the PBFT consensus process is
kept in the replica log, occupying the node memory,
and the checkpoint protocol can be used to clean up
the information and free the node memory. In the
PBFT, when the sequence number of the execution
request is divisible by some constant, a checkpoint S
is generated from the node. Once the stability of the
checkpoint S is proved, the slave node will discard all
pre-prepare, prepare, and commit messages in its log
with a sequence number less than or equal to S, as
well as previous checkpoints and checkpoint
messages. At the same time, the checkpoint protocol
is used to set the next sequence number range: (2)
khH +=
(1
)
h is the sequence number of the last stable
checkpoint, and K is the fixed value set.
2.2.1.3 Conformance Protocol
Consistency protocol is the core protocol of PBFT
algorithm, which uses a three-stage protocol to
broadcast requests to slave nodes, including pre-
prepare, prepare and commit.
2.2.2 Improve the Model
In a large-scale distributed system, layering
technology and agent technology are the basic
technologies of large-scale computing and complex
communication. The I-PBFT model proposed in this
chapter is based on the concepts of layering
technology and agent technology. In the i-PBFT
algorithm, the consensus model is divided into two
layers: the upper layer is the agent node region, and
the lower layer is the consensus node partition. Each
agent node in the upper layer of the consensus model
INCOFT 2025 - International Conference on Futuristic Technology
534
is the local master node of a partition in the lower
layer, and there is a global master node in the agent
node. The PBFT conformance algorithm is performed
within each partition, while the partitioning level is
dynamic and the number of partitions can be changed
as needed.
In the i-PBFT algorithm, the nodes in the whole
network are divided into four categories: client,
global master node, agent node and consensus node.
In the algorithm, the nodes are partitioned first. In the
process of node partitioning, the view replacement
protocol of the original PBFT algorithm is changed in
this paper, and the master node and agent node are
selected according to the node credit value. One
master node and several agent nodes are selected. Set
the number of agent nodes as K. After the agent nodes
are selected, the remaining nodes are merged into the
partition where K agent nodes are located to form a
PBFT consensus network with K partitions. In
addition, the number of nodes of each type is variable
throughout the network, and the total number of
nodes is constantly changing.
3 MODEL SIMULATION
EXPERIMENT
This paper uses Python language to implement a
small multi-node blockchain experimental system,
PBFT algorithm and I-PBFT algorithm proposed in
this paper are simulated. The algorithms are
compared and analyzed in four aspects:
communication overhead, fault tolerance, transaction
delay and throughput.
3.1 Transaction Delay
In order to test the trading delay of the algorithm, the
client constantly initiates trading requests in the
experiment and records the time of completion of
each consensus. For the accuracy of the experiment,
the average value of 100 transaction delays is taken
as the algorithm's transaction delays, and the test is
carried out in the case of different number of nodes to
get the final results.
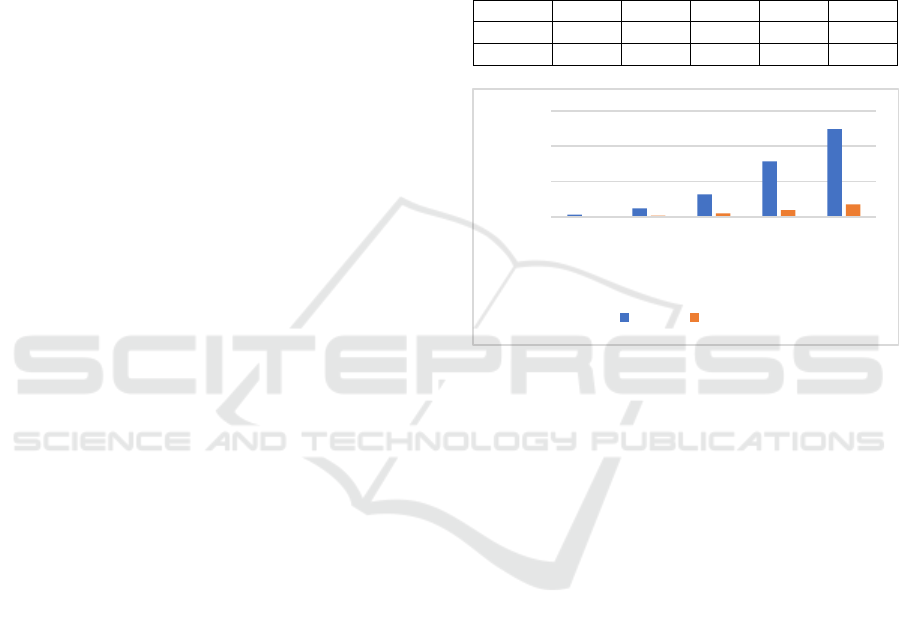
3.2 Throughput
In order to test the throughput of the algorithm in the
same environment, the client was set to send 200
Transaction requests in the experiment, record the
Transaction completion time, and then calculate the
number of transactions completed Per unit time,
namely TPS(Transaction Per Second), according to
the data obtained from the experiment.
4 SIMULATION EXPERIMENT
RESULTS
4.1 Transaction Delay Test
Table 1: Node delay comparison
5 10 20 30 40
PBFT 0.12 0.47 1.27 3.14 4.96
I-PBFT 0.03 0.07 0.19 0.38 0.71
Figure 1: Node delay comparison
As shown in Table 1 and Figure 1, the transaction
delay of the PBFT algorithm increases significantly
with the increase of nodes, and the delay of the I-
PBFT algorithm is far less than that of the PBFT
algorithm. The average delay of PBFT is 1.99s, and
the average delay of I-PBFT algorithm is reduced to
0.27s. With the increase of the number of nodes, the
communication overhead of PBFT algorithm
increases exponentially in the consensus process. In
this paper, the node partition method is adopted to
reduce the communication overhead of the node to
about 1/4. Meanwhile, the four partitions
synchronously carry out consensus, and the
transaction delay is nearly 8 times lower than that of
PBFT.
4.2 Throughput Test
As shown in Figure 2, the throughput comparison
between i-PBFT and PBFT algorithm in the number
of nodes from 15 to 50 is shown. The throughput of
the I-PBFT algorithm is higher than that of the PBFT
algorithm. The average throughput of the PBFT is
102TPS, and the average throughput of the i-PBFT is
increased to 152TPS.
0
2
4
6
5 10203040
Time delay(s)
Number of nodes
PBFT I-PBFT
Application of Block Chain Technology in Cross Border Food Information Tracing
535
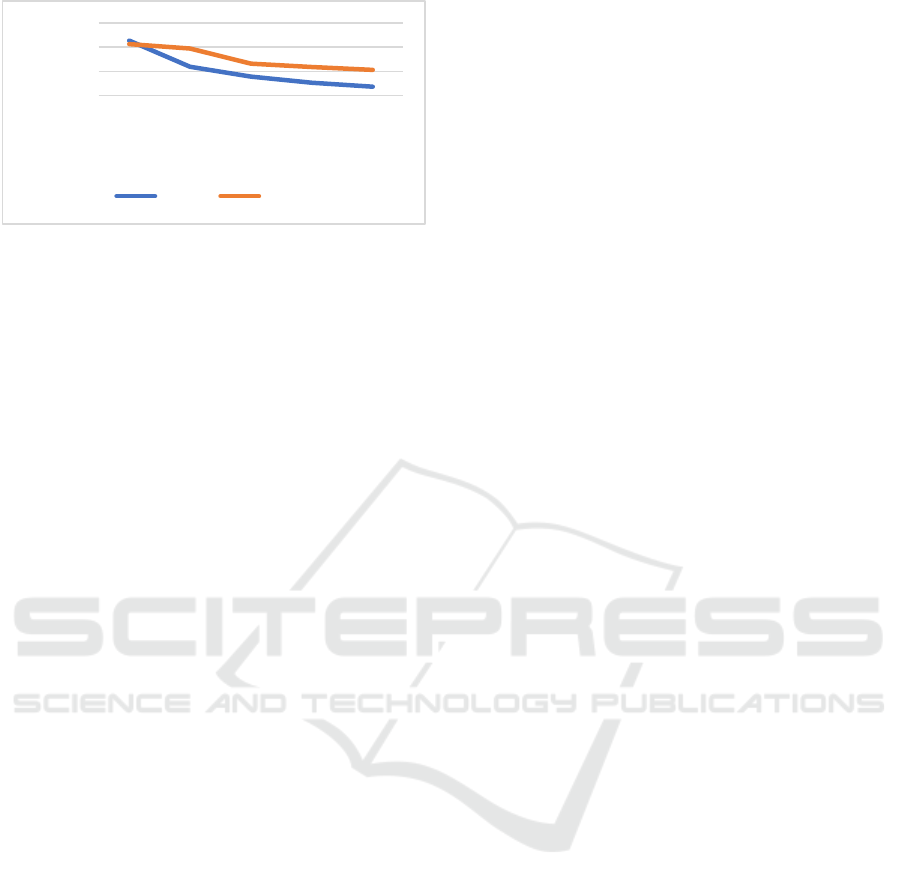
Figure 2: Throughput comparison
Compared with PBFT algorithm, I-PBFT
algorithm reduces the communication times of nodes
in the consensus process, effectively reduces the
network communication overhead, and reduces the
generation of malicious nodes through the node credit
mechanism. Experimental results show that I-PBFT
algorithm performs well when there are more nodes,
and its delay and throughput are better than PBFT
algorithm.
5 CONCLUSIONS
The main work of this paper is to solve the problem
of cross-border food safety traceability. Due to the
problems of centralization and information tampering
in the cross-border food traceability system, the
authenticity of food information in the whole
traceability process cannot be guaranteed. Therefore,
combining with modern blockchain technology to
solve the problem of data centralization, food
information is not controlled by a certain node or link
of the supply chain. Through the analysis of the
current food supply chain data acquisition mode and
other industry data acquisition mode, this paper puts
forward a comprehensive combining qr code and
RFID solutions to solve the problem of food
information collection, in combination with manual
input of food processing environment parameters,
such as planting, so that greatly reduces the
traceability platform of supply chain operating costs.
This paper designs an improved consensus algorithm
based on PBFT, optimizes the consistency protocol,
and proposes an improved PBFT algorithm for node
partitioning based on credit, I-PBFT. The experiment
proves that the consensus efficiency of the optimized
consensus algorithm is improved, and the
consumption of network communication is reduced,
which proves the feasibility of the algorithm.
REFERENCES
Tsang Y P , Choy K L , Wu C H , et al. Blockchain-driven
IoT for Food Traceability with an Integrated Consensus
Mechanism[J]. IEEE Access, 2019, 7(1):129000-
129017.
Tan A , Gligor D , Ngah A . Applying Blockchain for Halal
food traceability[J]. International Journal of Logistics,
2020(103):1-18.
Sharma A , Jhamb D , Mittal A . Food Supply Chain
Traceability by Using Blockchain Technology[J].
Journal of Computational and Theoretical Nanoscience,
2020, 17(6):2630-2636.
Pendrous R . Blockchain takes off in food and drink[J].
Food Manufacture, 2017, 92(10):27-27.
F Sander, Semeijn J , Mahr D . The acceptance of
blockchain technology in meat traceability and
transparency[J]. British Food Journal, 2018,
120(9):2066-2079.
Mengjia, ZENG, Xu, et al. Process Monitoring of Harmless
Disposal for Dead or Sick Livestock Based on
Blockchain[J]. Agricultural Biotechnology, 2019,
v.8(03):184-190.
Kamath R . Food Traceability on Blockchain: Walmart's
Pork and Mango Pilots with IBM[J]. The Journal of
British Blockchain Association, 2018, 1(1):1-12.
Deng M , Feng P . A Food Traceability System Based on
Blockchain and Radio Frequency Identification
Technologies[J]. Journal of Computer and
Communications, 2020, 08(9):17-27.
Gao S . T-PBFT: An EigenTrust-Based Practical Byzantine
Fault Tolerance Consensus Algorithm[J]. China
Communications, 2019, 16(12):111-123.
Zheng X , Feng W , Huang M , et al. Optimization of PBFT
Algorithm Based on Improved C4.5[J]. Mathematical
Problems in Engineering, 2021, 2021(2):1-7.
Han-Back S , Moo-Sub K , Sunmi K , et al. Quantitative
analysis of prompt gamma ray imaging during proton
boron fusion therapy according to boron
concentration[J]. Oncotarget, 2018, 9(3):3089-3096.
N Zhao, Wu H , Zhao X . Consortium Blockchain-Based
Secure Software Defined Vehicular Network[J].
Mobile networks & applications, 2020, 25(1):314-327.
0
100
200
300
15 20 30 40 50
TPS
Number of nodes
PBFT I-PBFT
INCOFT 2025 - International Conference on Futuristic Technology
536
