
Research on the Role of Computer Security Management in
Preventing Financial Technology Risks
Lanlan Wan
School of Economics and Management, Shanghai University of Political Science and Law, 201701, China
Keywords: Computer Network, Security Management Technology, Meta-Network Approach, Fintech Risks.
Abstract: The role of computer security management technology in preventing financial technology risks is very
important, but there is a problem of inaccurate assessment of risk judgment results. The intrusion detection
method cannot solve the problem of result judgment error in fintech risk prevention management. Therefore,
a computer security management scheme based on meta-network method is proposed to prevent financial
technology risks Analyse. Firstly, the concept of trust domain is adopted to determine different entity sets
according to different levels of security requirements, and divide the levels according to the risk prevention
annotation to reduce the interference factor of the error of determining the risk level. Then, through the
information interaction properties within the meta-network structure, the computer network with specific
needs and functions can be described, and the results of preventing financial technology risks can be
comprehensively analyzed. The results of MATLAB simulation experiments show that under the background
of unified judgment standards, the meta-network is based The computer security management technology of
the method is applied to financial technology risk prevention, and its accuracy and timeliness are better than
that of the intrusion detection method.
1 INTRODUCTION
With the rapid development of Internet technology,
computer networks, especially securities, futures and
banks and many other enterprises have also been
widely used, and the business of enterprises is
basically based on computer networks (Agustina, and
Subagyo, et al. 2022). Although the maintenance and
security of computer networks of financial and
securities companies will be periodically managed,
there are still certain network security incidents
(Rahmattullah, and Suman, et al. 2021). Some
scholars believe that applying business process-based
computer security methods to enterprise fintech risk
detection can effectively detect the security problems
existing in enterprise networks and provide
corresponding support for enterprise network security
prevention (Marandi, and dogra, et al. 2022). On this
basis, this paper proposes a meta-network method to
optimize the risk scheme of enterprise
fintech and
verify the effectiveness of the model (ALMahadin,
and Hiari, et al. 2022).
2 RELATED CONCEPTS
2.1 Mathematical Description of the
Meta-Network Approach
The meta-network method uses the concept of trust
domain to optimize the security system, and finds the
insecure factors in the security system according to
the indicators in the security system and integrate the
security precautionary scheme to finally judge the
feasibility of computer security management
(Chenniappanadar, and Gnanamurthy, et al. 2022).
The meta-network method combines the advantages
of trust domain theory, and uses the characteristics of
information interaction within the meta-network
structure to describe the specific functions of the
computer network, thereby enhancing the risk of
fintech of the quality of prevention.
Suppose I. Fintech risk prevention requirements
are
i
x
, computer network security management
scheme is
i
f
it
, computer network security
management scheme satisfaction is
i
N
, The
Wan, L.
Research on the Role of Computer Security Management in Preventing Financial Technology Risks.
DOI: 10.5220/0013545600004664
Paper published under CC license (CC BY-NC-ND 4.0)
In Proceedings of the 3rd International Conference on Futuristic Technology (INCOFT 2025) - Volume 1, pages 463-467
ISBN: 978-989-758-763-4
Proceedings Copyright © 2025 by SCITEPRESS – Science and Technology Publications, Lda.
463

judgment function of the computer network security
management scheme is
(0)
i
Tx≈
as shown in
Equation (1).
()
ii i
Tx
f
it N
∧
=⎯⎯→
(1
)
2.2 Selection of Computer Network
Security Management Scheme
Hypothesis II The fintech risk prevention function is
()
i
Qx
and the weight coefficient is
i
w
, then, the
security management requirements are not applied,
the fintech risk prevention model as shown in
Equation (2):
()= (, )
ii ii i
Qx K Fx N w
τ
⋅−⊗
∏
(1)
2.3 Analysis of Fintech Risk Security
Management Program
Before the meta-network method, a multi-
dimensional analysis of the enterprise fintech risk
prevention scheme should be carried out, and the risk
prevention requirements should be mapped to the
computer network security management database to
eliminate unqualified risk prevention Scheme. First,
the fintech risk prevention scheme is
comprehensively analyzed, and the threshold and
index weights of the risk prevention scheme are set to
ensure the accuracy of the meta-network method.
Financial technology risk prevention management is
a system test security management plan, which needs
to be optimized and improved. If the fintech risk is in
a non-normal distribution, its computational network
security management scheme will be affected,
reducing overall risk prevention management
accuracy. In order to improve the accuracy of the grey
correlation algorithm and improve the level of risk
prevention management, it is necessary to select the
risk security management plan, and the specific
scheme selection is shown in Figure 1 shown.
The investigation of the risk and security
management scheme shows that the risk security
management scheme presents a multi-dimensional
distribution, which is in line with the objective facts.
Risk security management is not directional,
indicating that the risk security management scheme
User terminal
Network
connection
device
Network
access
device
Central
Management
Server
Network
ReliableDNS
Tampered
withDNS
Figure 1: Results of selection of fintech risk prevention
solutions
has strong randomness, so it is regarded as a high
analytical study. Risk security management meets the
normal requirements, mainly the meta-network
method adjusts the financial technology risk
prevention management, removes duplicate and
irrelevant schemes, and supplements the default
scheme, so that the whole The dynamic correlation of
risk prevention management solutions is strong.
3 OPTIMIZATION STRATEGIES
FOR FINTECH RISK
PREVENTION MANAGEMENT
The meta-network method adopts a random
optimization strategy for fintech risk prevention, and
adjusts talent parameters to optimize the solution of
fintech risk prevention management. The meta-
network method divides fintech risk prevention into
different management levels, and randomly selects
different solutions. In the iterative process, the risk
prevention schemes of different prevention
management levels are optimized and improved.
After the optimization and promotion analysis is
completed, the prevention and management level of
different solutions is compared, and the best financial
technology risk prevention and management methods
are recorded.
4 PRACTICAL CASES OF
FINTECH RISK PREVENTION
MANAGEMENT
4.1 Introduction to Risk Prevention
and Management
In order to facilitate fintech risk management, this
paper takes fintech risk management in complex
situations as the research object, with 12 paths and a
INCOFT 2025 - International Conference on Futuristic Technology
464
test time of 12h The evaluation scheme of fintech risk
management is shown in Table 1.
Table 1: Fintech risk management requirements
Scope of
a
pp
lication
Management
level
Manage
effects
Manage
q
ualit
y
Bank I 64.38 61.74
II 63.74 62.41
Securities
companies
I 62.75 64.64
II 63.09 62.55
Futures
companies
I 65.05 62.16
II 64.95 57.99
The fintech risk management process in Table 1 is
shown in Figure 2.
Risk prevention of
financial technology
Computer
security
Meta-network
method
Risk
prediction
Data set
Constraint
condition
Results
Figure 2:The analysis process of fintech risk prevention
management
Compared with the intrusion detection method,
the computer security management scheme of the
meta-network method is closer to the actual fintech
risk prevention management requirements. In terms
of the rationality and fluctuation range of financial
technology risk prevention management, the meta-
network method is better than the PLD teaching
mode. The changes in the fintech risk prevention
management scheme in Figure II show that the meta-
network method has better stability and faster
judgment speed. Therefore, the meta-network
method's fintech risk prevention and management
scheme has more advantages in the speed and
stability of the judgment of security issues.
4.2 Fintech Risk Management
The financial technology risk prevention program for
computer security management includes non-
structural, semi-structured, and structural
information. After the pre-selection of the meta-
network method, a preliminary fintech risk
prevention scheme for computer security
management is obtained, and the computer security
management is obtained Analysis of the feasibility of
fintech risk prevention solutions. In order to more
accurately verify the effect of financial technology
risk prevention and management, select different risk
prevention levels of financial technology risk
prevention solutions to prevent the management
effect This is shown in Table 2.
Table 2: The overall situation of the fintech risk prevention
management plan
Level of
p
rotection
Manage
satisfaction
Risk
determination
Class I 85.73 74.21
Class II 85.47 79.38
Grade III 83.41 76.82
Class IV 82.65 74.42
Class V 85.95 76.17
P=4.15
4.3 The Effect and Stability of
Financial Technology Risk
Prevention in Computer Security
Management
In order to verify the accuracy of the meta-network
method, the fintech risk prevention scheme is
compared with the intrusion detection method, and
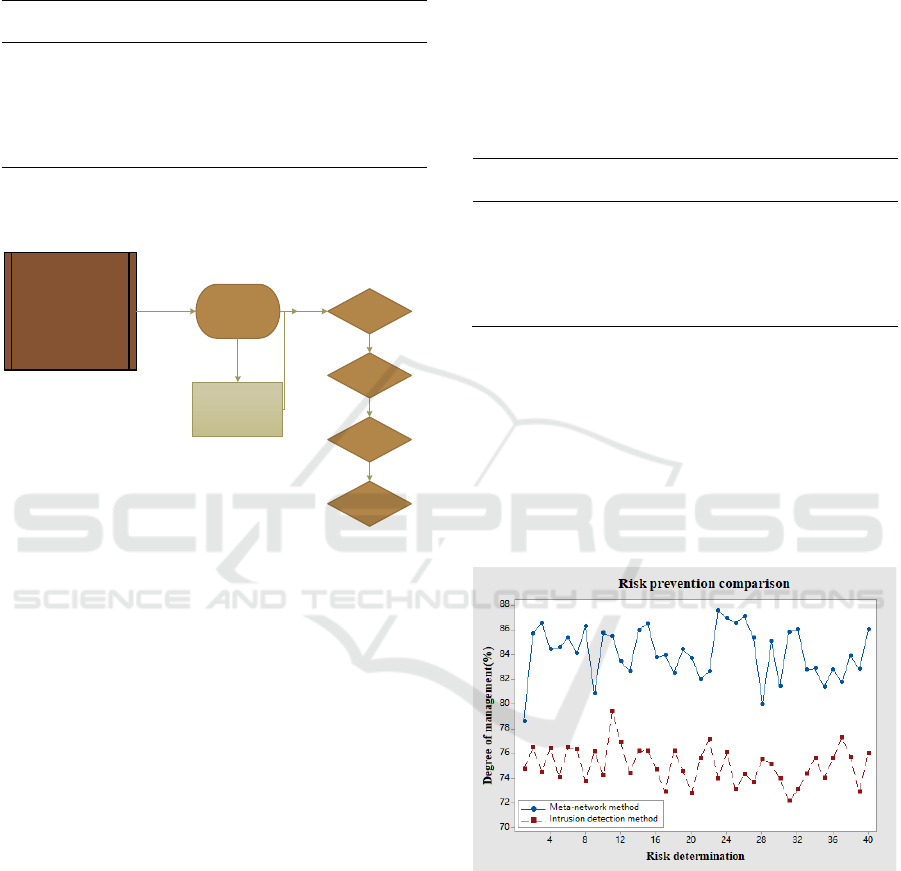
the prevention evaluation effect is shown in Figure 3.
Figure 3: Fintech risk prevention results of different
algorithms
It can be seen from Figure 3 that the fintech risk
prevention effect of the meta-network method is
higher than that of the intrusion detection method, but
the error rate is lower, indicating that the meta-
network method is based on it The risk prevention
effect of computer security management of fintech is
relatively stable, while the risk prevention detection
of intrusion detection method is uneven. The average
Research on the Role of Computer Security Management in Preventing Financial Technology Risks
465
preventive effect of the above methods is shown in
Table 3.
Table 3. Comparison of risk prevention accuracy of
different methods
Algorithm Quality of
risk
p
revention
Magnitude
of change
Error
Meta-network
methods
90.58 91.87 1.29
Intrusion
detection
79.09 83.26 4.17
Network
antivirus
detection
64.38 61.27 3.11
By Table 3, it can be seen that the intrusion
detection method has deficiencies in the prevention
effect and stability of financial technology risk
prevention effect, the quality of risk prevention has
changed significantly, and the error rate is high. The
general results of the meta-network method have a
higher quality of risk prevention than the intrusion
detection method. At the same time, the quality of
financial technology risk prevention management of
computer security management is greater than 90%,
and the accuracy has not changed significantly. In
order to further verify the superiority of the meta-
network method. In order to further verify the
effectiveness of the proposed method, the meta-
network method is generally analyzed by different
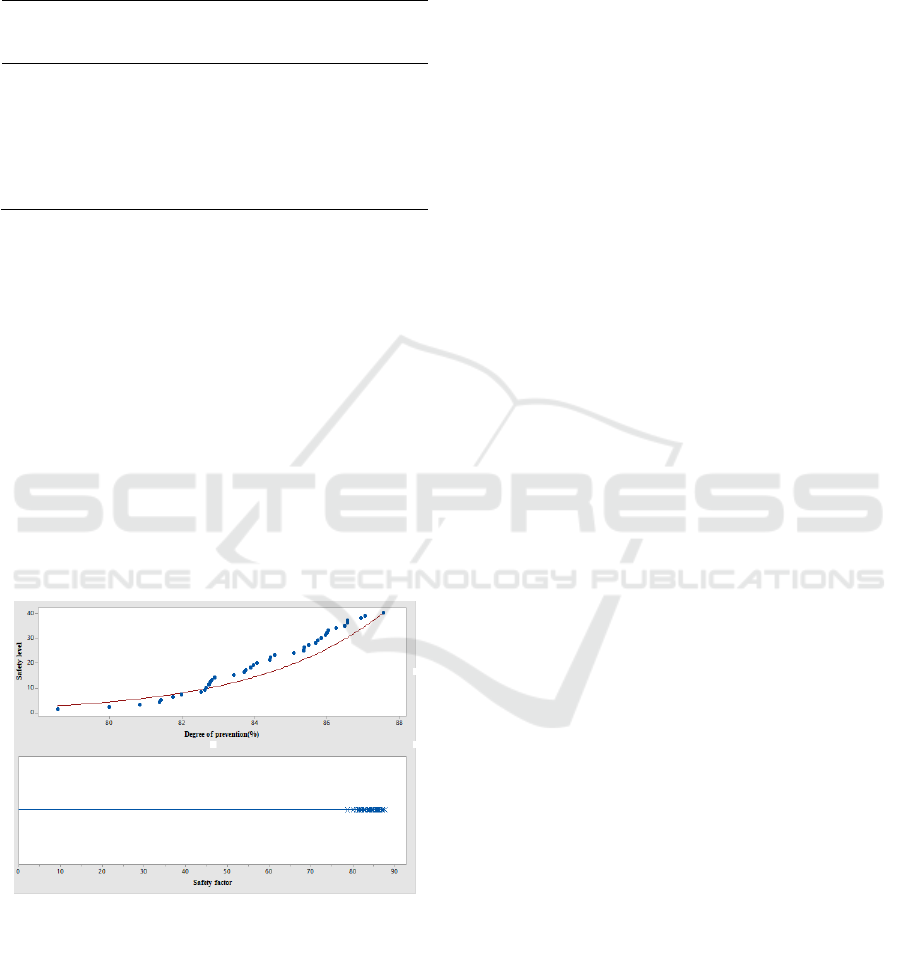
methods, as shown in Figure 4.
Figure 4: Fintech risk prevention based on meta-network
approach
By Figure 4 It can be seen that the fintech risk
prevention quality of the meta-network method is
significantly better than that of the intrusion detection
method, and the reason is that the meta-network
method increases the financial risk prevention Adjust
the coefficient, and set the threshold of talents, and
eliminate risk prevention plans that do not meet the
requirements.
5 CONCLUSIONS
Aiming at the problem that financial technology risk
prevention is not ideal, this paper proposes a
computer security management scheme based on
meta-network method, and combines the trust domain
theory to optimize the risk prevention management of
financial technology. At the same time, the risk
prevention management requirements and threshold
sets are analyzed in depth, and the requirements of
different information are constructed. The research
shows that the meta-network method can improve the
accuracy of fintech risk prevention and management,
and stability can prevent and manage fintech risks
Conduct general effect judgments. However, in the
process of meta-network method operation, too much
attention is paid to the analysis of risk prevention
quality evaluation, resulting in irrationality in the
selection of financial technology risk prevention
management indicators.
REFERENCES
Agustina, Y., Subagyo, & Istanti, L. N. (2022). How money
circulates in Indonesian SMEs: An analysis of Financial
Literacy, Business Performance, Financial
Management Behavior and Financial Attitude .
Educational Administration: Theory and Practice,
28(02), 122–132.
Rahmattullah, M. ., , W., Suman, A. ., & Witjaksono, M. .
(2021). Economic learning Educational Practices for
Local Values of "Baharit" Culture Based
on the Perspective of Sustainable Development
. Educational Administration: Theory and
Practice, 27(3), 1160–1167.
Marandi, D. A. K. ., dogra, M. ., Bhatt, R. ., Gupta, . M. R.
., Reddy, S. ., & Barve, D. A. . (2022). Generative
Boltzmann Adversarial Network in Manet Attack
Detection and QOS Enhancement with
Latency. International Journal of Communication
Networks and Information Security (IJCNIS), 14(3),
199–213.
ALMahadin, G. ., Hiari, M. O. ., Hussein, A. H. ., Turab,
N. M. M. ., Alkhresheh, A. ., & Al-Tarawneh, M. A. B.
. (2022). Performance Evaluation of an Intelligent and
Optimized Machine Learning Framework for Attack
Detection. International Journal of Communication
Networks and Information Security (IJCNIS), 14(3),
358–371.
Chenniappanadar, S. K. ., Gnanamurthy, S. ., Sakthivelu,
V. K. ., & Kaliappan, V. K. . (2022). A Supervised
INCOFT 2025 - International Conference on Futuristic Technology
466

Machine Learning Based Intrusion Detection Model for
Detecting Cyber-Attacks Against Computer
System. International Journal of Communication
Networks and Information Security (IJCNIS), 14(3),
16–25.
Research on the Role of Computer Security Management in Preventing Financial Technology Risks
467
