
Secure and Hybrid Clustering for IoT Networks: An Adaptive Dynamic
Reconfigurability Approach
Osama Mohammed Dighriri
1,2 a
, Priyadarsi Nanda
2 b
, Manoranjan Mohanty
3 c
and Ibrahim Haddadi
4 d
1
Department of Computer Science, College of Engineering and Computer Science, JAZAN University, K.S.A.
2
School of Electrical and Data Engineering, Faculty of Engineering and IT, University of Technology Sydney, Australia
3
School of Information System, Carnegie Mellon University, Qatar
4
Department of Computer Engineering, College of Computer Science and Engineering, TAIBAH University, K.S.A.
Keywords:
Internet of Things (IoT), Hybrid and Secure Clustering, Dynamic Reconfigurability, AES-128 Encryption.
Abstract:
Current Internet of Things (IoT) networks face significant challenges in scalability, energy efficiency, and
security within resource-constrained environments. This paper proposes a hybrid clustering framework com-
bining BIRCH with DBSCAN algorithms while integrating AES-128 encryption for secure communication.
Our proposed scheme is implemented using Contiki-NG simulator and analyzed using Python 3. Our approach
demonstrates a 20% improvement in resource utilization, 43.26% reduction in latency, and 99.91% message
success rate conducted across 2,154 test runs, with security overhead below 5%. This reduces cluster recon-
figuration frequency and improves system stability, addressing limitations in adaptability, data integrity, and
optimization for dynamic IoT infrastructures.
1 INTRODUCTION
The Internet of Things (IoT) is rapidly expanding,
with connected devices expected to reach 30 billion
by 2027 (Mansour et al., 2023). However, IoT net-
works face critical challenges, such as; scalability, in-
teroperability, and security issues due to constrained
resources and heterogeneous devices (Nasri et al.,
2021; Canavese et al., 2024).
Industrial IoT deployments such as; smart grids,
factory automation, and remote monitoring require
real-time secure clustering to ensure timely data ag-
gregation, prevent unauthorized access, and maintain
low latency despite limited energy and hardware ca-
pabilities (Kumar et al., 2021; Gyamfi and Jurcut,
2022; Zhang et al., 2023). Traditional encryption
methods, although effective, often introduce signifi-
cant power consumption, reducing device life span.
Existing clustering and edge computing methods of-
fer partial solutions but, frequently fall short in ad-
a
https://orcid.org/0000-0002-1917-0275
b
https://orcid.org/0000-0002-5748-155X
c
https://orcid.org/0000-0002-0258-4586
d
https://orcid.org/0000-0002-7557-4258
dressing adaptability, security, and efficiency simulta-
neously (Bouguettaya et al., 2021; Xiang et al., 2023;
Chiang et al., 2023). Moreover, static clustering lacks
flexibility, leading to instability and reduced perfor-
mance in dynamic environments.
Motivated by these challenges, this study pro-
poses a hybrid clustering framework by leveraging
BIRCH for scalability and DBSCAN for refinement,
enhanced with adaptive QoS metrics for dynamic
reconfiguration and AES-128 encryption for secure,
low-overhead communication. The framework ad-
dresses the need for secure, efficient, and adaptive
IoT clustering, enabling real-time adjustments, opti-
mizing performance, and improving resilience.
Our key contributions in this paper include but not
limited to:
• Design of hybrid clustering method addressing
scalability, security, and adaptability limitations
in dynamic IoT environments.
• A QoS-driven reconfiguration approach that dy-
namically optimizes network latency, throughput,
and energy efficiency.
• A lightweight AES-128 encryption framework
ensuring robust security for IoT communication
412
Dighriri, O. M., Nanda, P., Mohanty, M., Haddadi and I.
Secure and Hybrid Clustering for IoT Networks: An Adaptive Dynamic Reconfigurability Approach.
DOI: 10.5220/0013525600003979
In Proceedings of the 22nd International Conference on Security and Cryptography (SECRYPT 2025), pages 412-419
ISBN: 978-989-758-760-3; ISSN: 2184-7711
Copyright © 2025 by Paper published under CC license (CC BY-NC-ND 4.0)
with minimal computational overhead.
The remainder of this paper as follows: Section 2
reviews relevant literature; Section 3 details the pro-
posed method; Section 4 outlines the system model;
Section 5 discusses results and comparative analysis;
and Section 6 concludes future research directions.
2 BACKGROUND AND RELATED
WORK
IoT clustering techniques have evolved significantly,
addressing challenges like resource constraints, scal-
ability, and heterogeneity. These techniques primar-
ily aim to optimize energy efficiency, extend network
longevity, and enhance security while balancing com-
putational overheads.
Evolutionary algorithms, including Genetic Algo-
rithms (GA) and Fuzzy Logic (FL), have improved
IoT clustering efficiency but face scalability chal-
lenges in large-scale deployments (Ajayi et al., 2021;
Mohamed et al., 2020). Similarly, Swarm-based
methods such as Particle Swarm Optimization (PSO)
and Ant Colony Optimization (ACO) have shown
promise in adaptive clustering but, struggle with con-
sistent reconfiguration in dynamic settings (Sadrisho-
jaei et al., 2022).
Security introduces critical trade-offs, often in-
creasing computational overhead. Lightweight AES-
based encryption approaches have emerged, sig-
nificantly reducing resource use (Ferrag et al.,
2020). Nevertheless, studies indicate frequent secu-
rity breaches in deployments prioritizing energy effi-
ciency over robust encryption, highlighting the neces-
sity of adaptive security solutions (Li et al., 2023).
Dynamic reconfiguration methods are essential
to maintain IoT clustering efficiency in fluctuat-
ing environments. Techniques like Predictive Edge
Computing (PEC) offer improved responsiveness
but, face scalability limitations (Jere et al., 2020).
Context-aware reconfiguration approaches demon-
strate adaptability yet, struggle in highly dynamic,
large-scale conditions (Wang et al., 2022). Software-
Defined Networking (SDN)-based solutions also suf-
fer throughput limitations when deployed in dynamic
infrastructures (Abuarqoub, 2020).
Recent hybrid frameworks integrating clustering
and security show promise but, often lack compre-
hensive optimization in heterogeneous deployments.
Building on these insights, our study introduces a uni-
fied framework integrating hierarchical BIRCH and
DBSCAN clustering methods, combined with AES-
128 encryption. Our approach addresses existing gaps
by dynamically optimizing security, latency, energy
efficiency, and scalability simultaneously.
3 PROPOSED FRAMEWORK
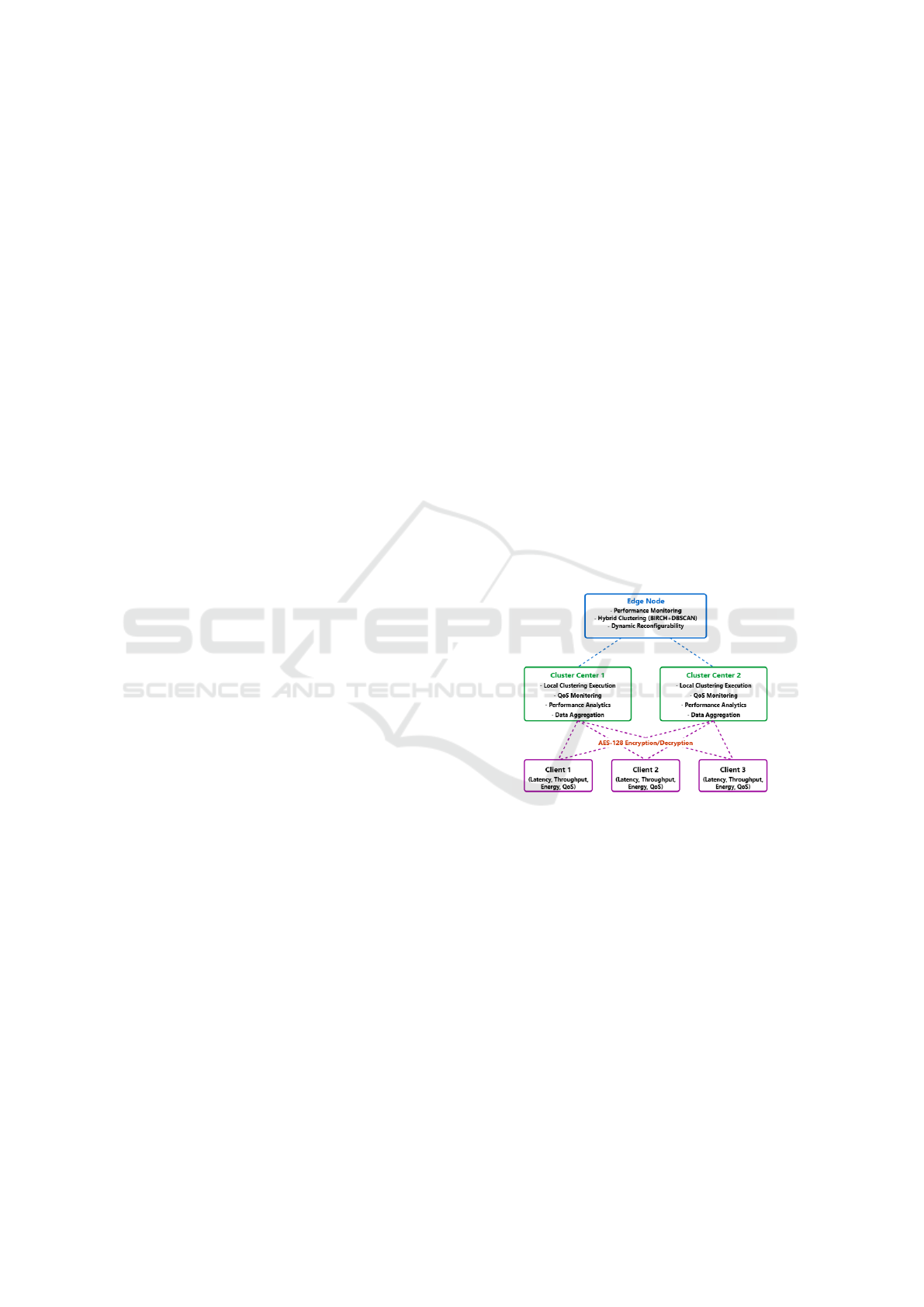
Our work integrates three major components as il-
lustrated in Figure 1: (1) A hybrid clustering frame-
work combining BIRCH’s coarse-grained classifica-
tion with DBSCAN’s refinement capabilities for en-
hanced accuracy and noise detection; (2) QoS-driven
dynamic regulation where cluster centers optimize
network efficiency under changing conditions; and
(3) Secure communication using lightweight AES-
128 encryption.
The motivation for combining BIRCH and DB-
SCAN stems from the need to balance scalability,
adaptability, and clustering precision in dynamic IoT
environments. BIRCH efficiently processes large-
scale datasets with minimal memory overhead, while
DBSCAN provides robustness against noise and out-
lier detection. Together, this hybrid approach enables
responsive and resilient clustering under varying net-
work conditions and data distributions.
Figure 1: Framework Architecture.
The architecture operates across three distinct lay-
ers: The edge node (top layer) manages monitor-
ing, hybrid clustering, and dynamic reconfigurabil-
ity. Cluster centers (middle layer) execute local-
ized clustering, QoS monitoring, and data aggrega-
tion. Client nodes (bottom layer) report performance
metrics and communicate securely via AES-128 en-
cryption. The implementation uses Contiki-NG for
cluster-based logic and adaptive reconfiguration, with
simulation outputs processed through Python 3 for
evaluation.
3.1 Mathematical Formulas
This section presents the problem formulation within
four essential components:
Secure and Hybrid Clustering for IoT Networks: An Adaptive Dynamic Reconfigurability Approach
413

• Node Metrics: Performance parameters govern-
ing clustering decisions
N
i
= (l
i
, t
i
, e
i
, q
i
) (1)
• Clustering and Refinement: BIRCH-inspired
feature vectors enabling real-time adaptation
CF
k
= (N
k
, LS
k
, SS
k
) (2)
Node similarity uses a normalized distance metric:
D(n
i
, n
j
) =
v
u
u
t
∑
d∈{l,t,e}
n
i
[d] − n
j
[d]
max
d
− min
d
2
(3)
DBSCAN identifies core points using:
CorePoint(p) = |{q : D(p, q) ≤ ε}| ≥ MinPts (4)
• Dynamic Cluster Management: QoS-driven
size adjustment and load balancing, where cluster
size is dynamically determined by:
Size(C
k
) = min
MAX Ck,
∑
N
k
i=1
q
i
QoS Threshold
!
(5)
Thresholds adapt to QoS changes:
T (t) = T
0
· (1 +α · ∆QoS) (6)
Load balancing uses load factors:
L
k
=
∑
N
k
i=1
d
i
MAX RANGE
(7)
• Performance Metrics: QoS evaluation integrat-
ing reliability and resource utilization
Cluster QoS combines message success rate with
resource utilization:
QoS(G
k
) =
mesgs acked
k
mesgs sent
k
·
active nodes
k
MAX CLUSTER SIZE
(8)
Energy efficiency is maintained by node proximity
enforcement:
E
total
(k) =
N
k
∑
i=1
e
i
·
1 + α ·
d
i
MAX RANGE
(9)
System performance is evaluated through cluster
stability and global efficiency:
S(C
k
) =
1 −
reconf count
k
MAX RECONFS
· QoS(C
k
) (10)
P
global
=
∑
K
k=1
|C
k
| · S(C
k
)
∑
K
k=1
|C
k
|
(11)
3.2 Proposed Algorithm
Our framework operates in three phases: hybrid clus-
tering, dynamic reconfiguration, and secure commu-
nication. Algorithm 1 synthesizes these components,
where BIRCH provides initial coarse-grained classifi-
cation, DBSCAN refines cluster boundaries, and con-
tinuous QoS monitoring enables adaptive optimiza-
tion. AES-128 encryption ensures data protection
with minimal overhead.
Input: IoT Dataset D, Parameters T
0
, Thresholds
{E
th
, L
th
, T
th
}
Output: Optimized Clusters C, QoS Metrics,
Performance P
global
begin
Initialize system parameters and communication
links;
// Hybrid Clustering Phase
Apply BIRCH clustering for initial clusters using
CF
k
(Eq. 2);
Refine using DBSCAN with metric D(n
i
, n
j
) (Eq.
3);
// Dynamic Reconfiguration Phase
while System is Active do
foreach Cluster Center C
c
do
Monitor metrics and recalculate QoS(C
k
)
(Eq. 8);
if metrics exceed thresholds then
Update thresholds using Eq. 6;
Reassign nodes based on updated
parameters;
end
Apply AES-128 encryption for secure
communication;
Validate data integrity and update
configurations;
end
Compute P
global
(Eq. 11);
end
return Optimized Clusters, QoS Metrics, and
P
global
;
end
Algorithm 1: Hybrid Secure Clustering with Dynamic Re-
configurability.
4 IMPLEMENTATION AND
SYSTEM MODEL
This section outlines the implementation strategy and
system model tailored for constrained IoT environ-
ments, optimizing IPv6-based communication lever-
ages IEEE 802.15.4, 6LoWPAN compression, and
RPL-Lite routing. The edge node coordinates cluster
centers, each managing client nodes. Cluster centers
aggregate data, balance workloads, and ensure consis-
tent messaging. Client nodes, distributed across ap-
plications continuously report performance metrics.
SECRYPT 2025 - 22nd International Conference on Security and Cryptography
414
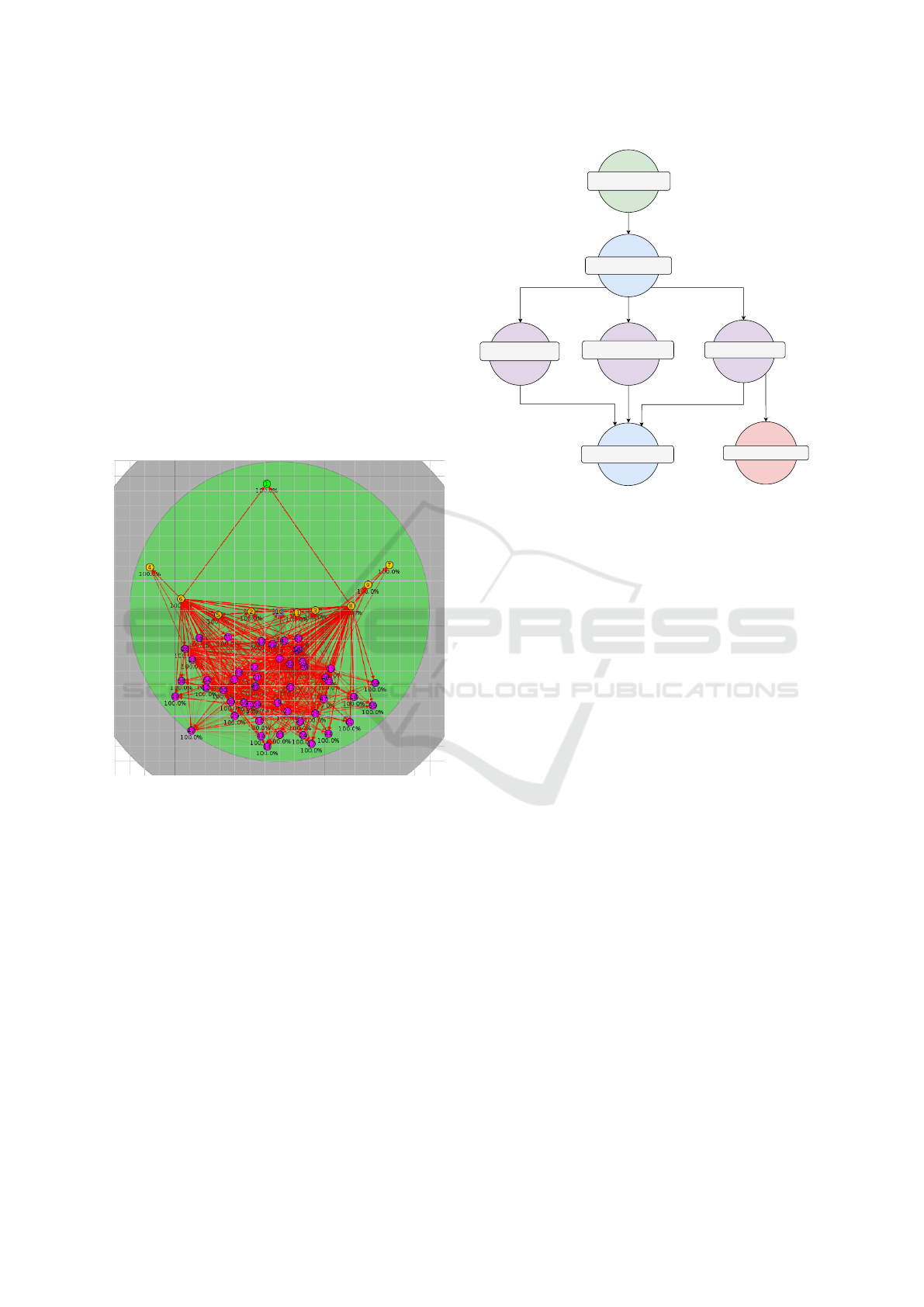
4.1 Experimental Setup
The simulation was conducted within a 100× 100 m
2
area, as depicted in Figure 2, with a communication
radius of 100 meters. The system achieves complete
connectivity, a latency threshold of 60 ms, and a data
rate above 1 Mbps. Energy usage ranges between
0.1 and 7.0 watts based on node-specific constraints.
The network consists of an Edge Node (Green Mote)
serving as the central node for data aggregation and
synchronization, Cluster Centers (Yellow Motes) that
conduct adaptive clustering, and routing, and Client
Nodes (Purple Motes) that transmit real-time metrics
(latency, throughput, energy, QoS) securely. The sim-
ulation uses Cooja motes and Contiki-NG’s internal
power profiling, accurately modeling resource effi-
ciency and scalability.
Figure 2: Simulated topology showing mote connectivity.
4.2 Dynamic Reconfigurability
To maintain optimal performance, the framework dy-
namically adapts based on real-time metrics. As de-
picted in Figure 3, reconfiguration is triggered when
energy consumption drops below 20%, mobility ex-
ceeds 50%, or throughput falls below 80% of base-
line values. Otherwise, current configurations remain.
This appraoch is crucial in IoT environments, where
rapid changes in mobility, energy, or traffic can de-
grade performance. By continuously adjusting clus-
tering parameters, the system improves resilience, re-
duces unnecessary reconfigurations, and sustains QoS
under dynamic conditions.
Tigger Reconfiguration
No Action
Mobility > 50% Range
Monitor Metrics
Start
Throughput < 80%
Energy < 20%
Figure 3: Dynamic Reconfiguration Decision Flowchart.
4.3 Assumptions
The framework assumes performance feasibility
where nodes can manage clustering, security, and
IPv6 communication, scalability and Resilience that
supports over 2,000 simultaneous transmissions, self-
adjusting QoS where devices autonomously adapt to
changing network conditions, and distributed coordi-
nation in which the edge node oversees real-time clus-
tering and synchronization.
4.4 Design Requirements
Key operational requirements include integrated clus-
tering with initial segmentation through BIRCH and
refinement by DBSCAN, real-time adaptability offer-
ing adaptive reconfiguration for efficiency and sta-
bility, and secure communication utilizing AES-128
encryption with minimal overhead, and performance
consistency optimization.
5 RESULTS AND DISCUSSION
5.1 Hybrid Clustering Algorithm
This section evaluates our hybrid clustering method-
ology that integrates BIRCH with DBSCAN to in dy-
namic IoT environments. Performance metrics are
improved through data parsing to extract relevant
metrics, with cluster labels normalized using Python
3. Figure 4 compares the three clustering approaches
that manage dynamic network conditions efficiently.
Secure and Hybrid Clustering for IoT Networks: An Adaptive Dynamic Reconfigurability Approach
415
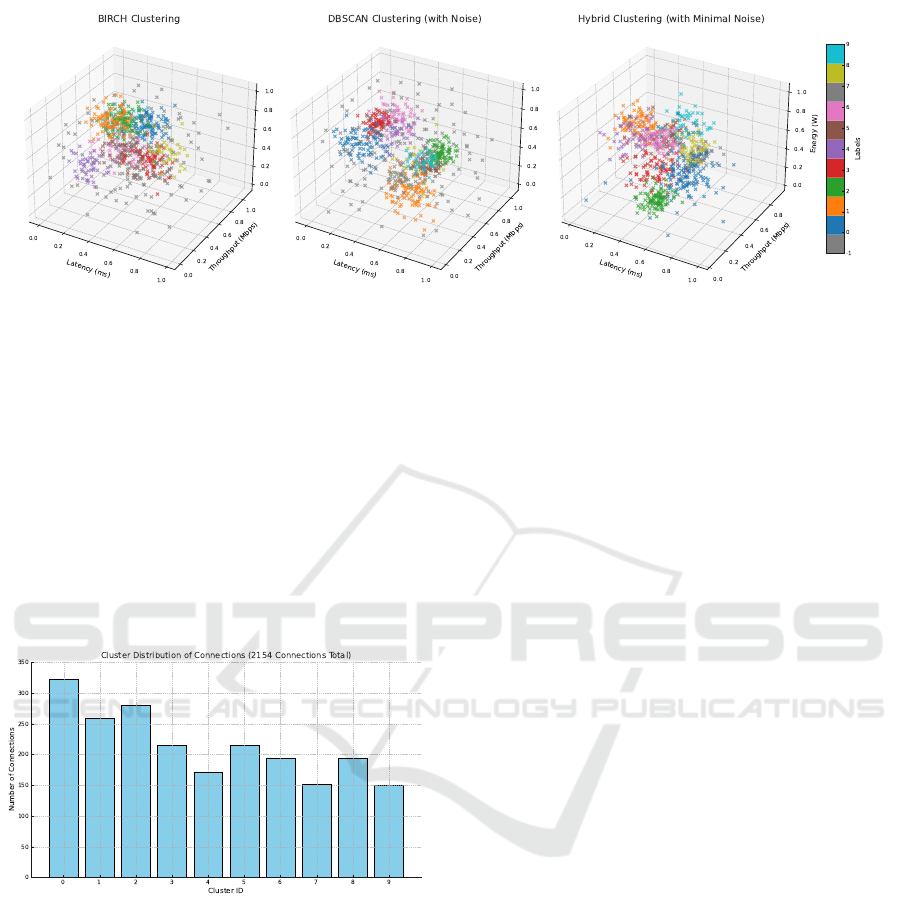
Figure 4: Comparison of clustering results on IoT metrics: the left plot shows clear clusters with few outliers, the center
detects anomalies well but is noise-sensitive, and the right achieves a balanced, structured grouping.
BIRCH forms well-separated clusters with high
computational efficiency, suitable for large datasets,
but lacks outlier detection capabilities. DBSCAN
excels at anomaly detection (gray-labeled instances)
but often produces larger, less precise clusters with
increased likelihood of misclassifying valid pat-
terns. Our hybrid approach combines BIRCH’s struc-
tured clustering with DBSCAN’s anomaly detection,
achieving clear separation while effectively distin-
guishing valid patterns from anomalies—making it
ideal for IoT environments requiring both accuracy
and adaptability.
Figure 5: Connection distribution across clusters.
The dataset comprises 2,154 communications dis-
tributed across clusters 0–9 as shown in Figure 5.
Cluster distribution demonstrates specialized func-
tionality: high-volume exchange (Cluster 0, 15.2%),
connectivity aggregation (Cluster 2, 13.4%), trans-
mission intermediation (Cluster 1, 13.0%), network
traffic balancing (Clusters 3 and 5, 11.6% and 9.8%),
specialized tasks (Cluster 4, 8.1%), occasional inter-
actions (Cluster 7, 7.0%), and general-purpose com-
munication (Clusters 6, 8, 9, 7.0–10.2%).
Figure 6 provides an integrated view of latency,
throughput, energy consumption, and QoS distribu-
tions across various clusters. The plot shows perfor-
mance metrics across 10 clusters (0-9). Cluster 7 has
high latency ( 48ms) and throughput ( 45 Mbps) with
moderate energy use ( 3.4W). Cluster 3 offers maxi-
mum throughput ( 47 Mbps) but highest energy con-
sumption ( 6.0W). Cluster 8 provides minimal latency
( 10ms) ideal for time-critical applications but lim-
ited throughput ( 2 Mbps). Cluster 0 excels in energy
efficiency ( 0.2W) but with performance trade-offs.
Cluster 6 achieves the highest QoS ( 0.61) with bal-
anced performance metrics, while Cluster 4 shows the
lowest QoS ( 0.40). Clusters 1, 2, 5, and 9 maintain
intermediate performance profiles across all metrics,
offering balanced operation for general-purpose ap-
plications. These distinct profiles enable selecting ap-
propriate cluster configurations based on specific IoT
application requirements.
Our hybrid framework outperforms alternatives,
maintaining a mean QoS of 0.52 with optimized
energy use (2.74W), supports bandwidth-intensive
operations (23.35 Mbps throughput) with low la-
tency (28.38ms), and achieves exceptional reliability
(99.95% message success rate).
5.2 Security Implementation
Our IoT clustering security solution integrates the
hybrid BIRCH-DBSCAN method with AES-128 en-
cryption to ensure robust data protection while main-
taining performance efficiency. The system adapts
dynamically to environmental variability, with secu-
rity embedded through two key strengths: (1) per-
fect data authenticity via bit-to-bit matching after
encryption-decryption cycles, and (2) operational re-
silience with stable, low-latency processing suitable
for IoT deployments. Figure 7 illustrates the encryp-
tion and decryption results, demonstrating the frame-
work’s resilience and energy efficiency. Encrypted
data shows high entropy with no visible patterns. Us-
ing secure random keys and PKCS7 padding, the
dataset size increased from 25,379 to 34,230 bytes
SECRYPT 2025 - 22nd International Conference on Security and Cryptography
416
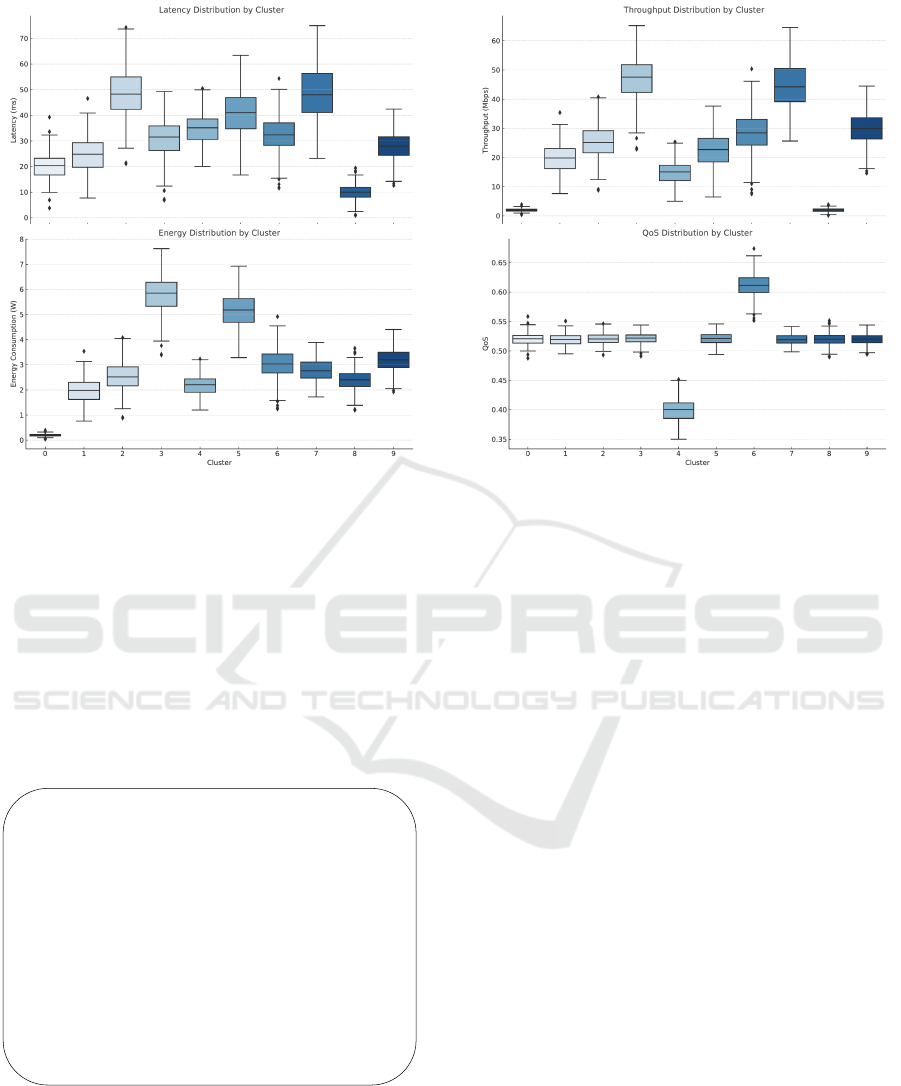
Figure 6: Integrated View of Cluster Metrics: Latency, Throughput, Energy Consumption, and QoS Distributions.
to support 2,154 connections. Encryption took only
0.0020 seconds, while decryption restored the data
in 0.0012 seconds with 100% integrity verification.
Despite a 34.9% increase in size due to padding and
headers, processing latency decreased from 2ms to
1.2ms. Bandwidth usage dropped slightly (from 250
to 240 kbps), preserving real-time execution. En-
cryption throughput reached 12.36 MB/s, and decryp-
tion 20.60 MB/s, confirming the framework’s suitabil-
ity for lightweight, secure data exchange in resource-
constrained IoT environments.
# Encryption and Decryption Results
## 4.1 Original Data
Length: 25379 bytes
Sample: b"\xeb\xedg\x3d\xbe\xa3\xfb\x0eU\xd2\xaf\xbc\xcOV\xxBA\xa7\x97\xf8
\xd\x03\xc0\xax\xbs\xda\xba\x2\x19\xaa\xal\xbecB\xdF\xBs\xBeb3\xFa(\xcl"
## 4.2 Encrypted Data
Length: 34230 bytes
Sample: b"gARAAABNiajtev«popgzeTSFFjjGyDUIVeLTAoNEp7OHDFGCNAB"
## 4.3 Decrypted Data
Length: 25379 bytes
Sample: b"\xeb\xedg\xod\xbe\xa3\xfb\x0eU\xd\xa\xbc\xcOV\xa\xa7\x97\xf\xd\x03
\xc0\xa\xb\xca\xba\xd2\x19\xaal\xbeCB\xdFBS\xBeb3\xFa(\xct"
## 4.4 Performance Analysis
Encryption Time: 0.0020 seconds
Decryption Time: 0.0012 seconds
Data Integrity Check: Successful
Figure 7: Encryption and decryption results.
The cluster analysis reveals three distinct de-
vice profiles based on performance characteristics as
shown in both figures 8 and 9. The security-critical
devices (clusters 0, 5, 9 - represented by circles) prior-
itize data protection with higher energy consumption
( 2.5W) and superior QoS (0.575-0.650), operating
at moderate latency (22.5-30ms) and throughput (22-
30 Mbps). Energy-constrained devices (clusters 4, 7,
8 - marked with ”x”) optimize for power efficiency
with minimal energy usage ( 0.5W), moderate QoS
(0.450-0.550), lower latency (10-15ms), and reduced
throughput (2-5 Mbps). General-purpose devices
(clusters 1, 2, 3, 6 - shown as squares) maintain bal-
anced performance with moderate energy consump-
tion ( 2.0W), stable QoS (0.475-0.550), and balanced
latency (17-22.5ms) and throughput (15-25 Mbps).
These patterns demonstrate how the clustering frame-
work effectively segments IoT devices according to
their operational requirements, enabling optimal re-
source allocation for diverse application scenarios.
Figure 10 illustrates the security-performance
trade-offs across clusters, where security scores (nor-
malized between 0 and 1) are derived from encryp-
tion overhead, communication latency, and opera-
tional complexity. Lower scores (0.24–0.29) indi-
cate high-security clusters with stringent encryption
policies (e.g., frequent AES-128 encryption and re-
duced flexibility), while higher scores (0.64–0.66)
reflect energy-efficient clusters with minimal con-
straints. General-purpose clusters maintain moder-
ate scores (0.32–0.39), balancing security with per-
formance requirements.
Figure 11 reveals performance metric correla-
tions. Processing time strongly correlates with data
exchange rates ( 0.96), while power utilization per-
fectly correlates with data transmission ( 1.00). Se-
Secure and Hybrid Clustering for IoT Networks: An Adaptive Dynamic Reconfigurability Approach
417
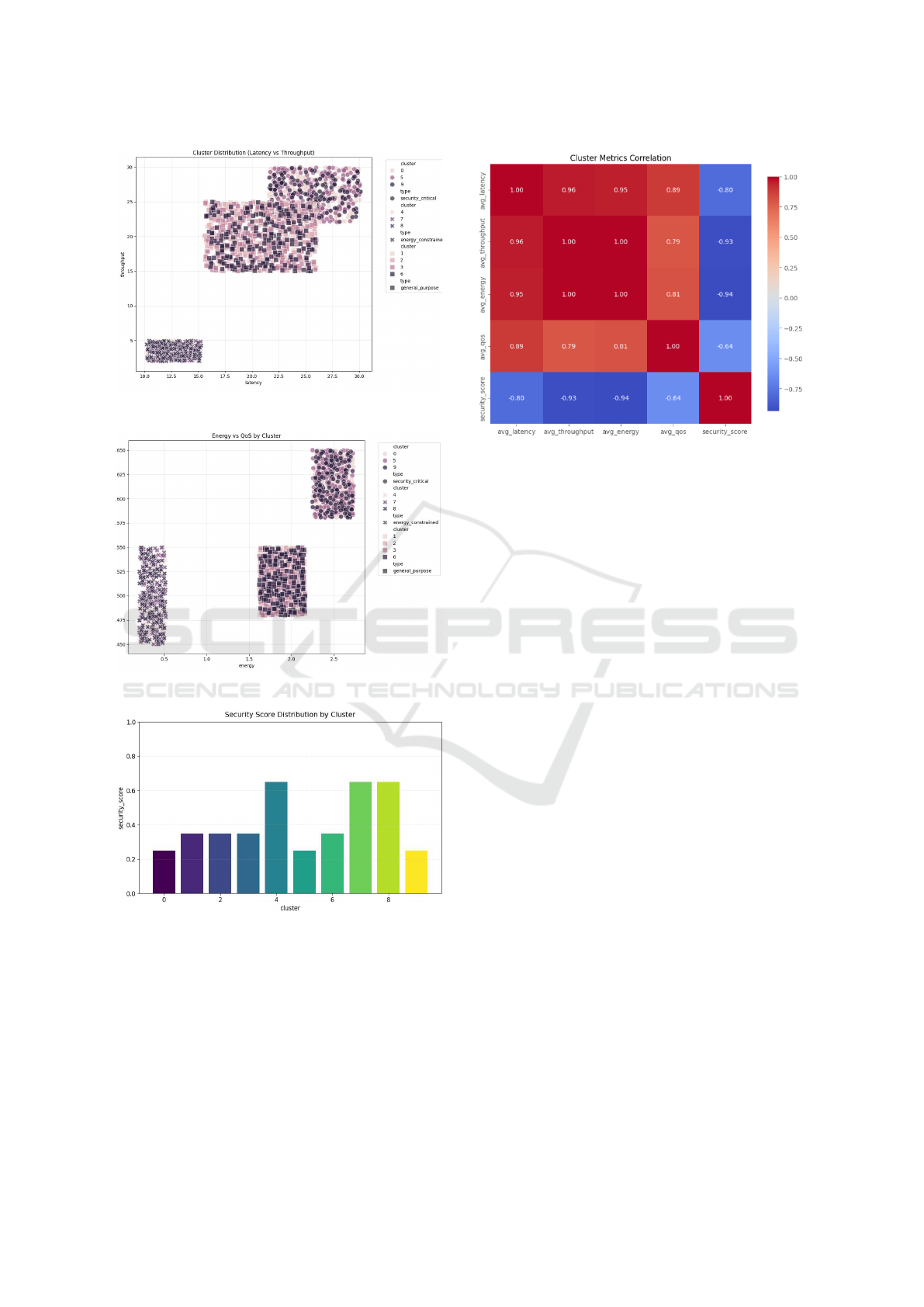
Figure 8: Cluster Distribution (Latency vs Throughput)
Figure 9: Energy vs QoS by device type
Figure 10: Security Score Distribution across clusters.
curity measures show negative correlation with per-
formance metrics (-0.93 to -0.94), confirming the
security-performance trade-off. QoS and security ex-
hibit inverse relationship (-0.64), indicating that oper-
ational optimization may affect resilience.
5.3 Comparative Analysis
Table 1 highlights our framework’s superior perfor-
mance compared to recent approaches. It achieves
Figure 11: Correlation heatmap showing trade-offs.
28.37 ms latency (43.26% improvement over base-
line and 20% better than DLGA), 92% energy effi-
ciency (exceeding Trust-HC, D-ACSM, and DLGA
at 76.5%, 74.2%, and 81.7% respectively), and
23.35 Mbps throughput (compared to Trust-HC at
14.8 Mbps, D-ACSM at 18.1 Mbps, and DLGA at
19.9 Mbps). Network stability reaches 98% ver-
sus competitors’ 81.3-87.9%, with a 99.91% mes-
sage delivery success rate. Unlike Trust-HC’s trust-
based mechanism and D-ACSM’s partial security, our
framework implements comprehensive AES-128 en-
cryption, making it ideal for time-critical, energy-
constrained IoT deployments.
6 CONCLUSION AND FUTURE
WORKS
This paper proposed a hybrid clustering framework
combining BIRCH, DBSCAN, and AES-128 encryp-
tion to enhance security, adaptability, and perfor-
mance in IoT networks. The system achieved no-
table improvements in power efficiency (20%), la-
tency reduction (43.26%), and message success rate
(99.91%). The framework presents certain limita-
tions: increased implementation complexity, due to
reliance on simulation. Future work will address these
challenges by extending the framework to real-world
IoT testbeds, improving interoperability with existing
protocols and standards, and assessing its robustness
across diverse network topologies. We also plan to re-
lease the implementation as open source and explore
lightweight enhancements to further reduce security
overhead in resource-constrained environments.
SECRYPT 2025 - 22nd International Conference on Security and Cryptography
418
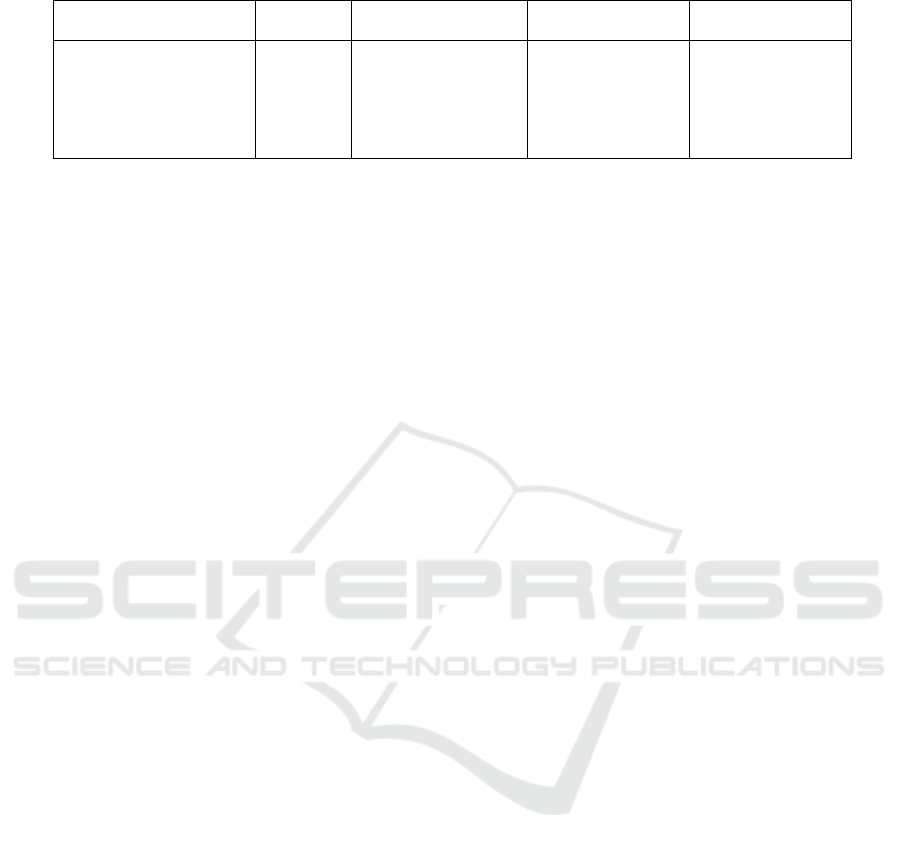
Table 1: Detailed Performance Comparison of Recent Approaches.
Feature Our Work Trust-HC D-ACSM DLGA
(2025) (Lapegna et al., 2023) (Balakrishna, 2022) (Merah et al., 2024)
Latency (ms) 28.37 46.1 41.5 35.8
Energy Efficiency (%) 92 76.5 74.2 81.7
Throughput (Mbps) 23.35 14.8 18.1 19.9
Security Implementation AES-128 Trust-based Limited SDN-based
Network Stability (%) 98 81.3 84.7 87.9
Message Success Rate (%) 99.91 84.9 87.5 89.8
ACKNOWLEDGMENTS
This work was supported by the Department of Com-
puter Science, College of Engineering and Computer
Science, JAZAN University, KSA; Department of
Computer Engineering, College of Computer Science
and Engineering, TAIBAH University, KSA; and the
School of Electrical and Data Engineering, Faculty of
Engineering and IT, University of Technology Syd-
ney, Australia.
REFERENCES
Abuarqoub, A. (2020). A review of the control plane scala-
bility approaches in software-defined networking. Fu-
ture Internet, 12(3):49.
Ajayi, O., Rafferty, J., Santos, J., Garcia-Constantino, M.,
and Cui, Z. (2021). Beca: A blockchain-based edge
computing architecture for internet of things systems.
IoT, 2:610–632.
Balakrishna, S. (2022). D-acsm: A technique for dy-
namically assigning and adjusting cluster patterns for
iot data analysis. The Journal of Supercomputing,
78:12873–12897.
Bouguettaya, A., Sheng, Q. Z., Benatallah, B., Neiat, A. G.,
Mistry, S., Ghose, A., Nepal, S., and Yao, L. (2021).
An internet of things service roadmap. Commun.
ACM, 64(9):86–95.
Canavese, D., Mannella, L., Regano, L., and Basile, C.
(2024). Security at the edge for resource-limited iot
devices. Sensors, 24(2).
Chiang, Y., Zhang, Y., Luo, H., Chen, T.-Y., Chen, G.-H.,
Chen, H.-T., Wang, Y.-J., Wei, H.-y., and Chou, C.-T.
(2023). Management and orchestration of edge com-
puting for iot: A comprehensive survey. IEEE Internet
of Things Journal, PP:1–1.
Ferrag, M. A., Shu, L., Yang, X., Derhab, A., and Maglaras,
L. (2020). Security and privacy for green iot-based
agriculture: Review, blockchain solutions, and chal-
lenges. IEEE Access, PP.
Gyamfi, E. and Jurcut, A. (2022). Intrusion detection
in internet of things systems: A review on design
approaches leveraging multi-access edge computing,
machine learning, and datasets. Sensors, 22:3744.
Jere, S., Fan, Q., Shang, B., Li, L., and Liu, L. (2020).
Federated learning in mobile edge computing: An
edge-learning perspective for beyond 5g. ArXiv,
abs/2007.08030.
Kumar, U., Verma, P., and Abbas, S. (2021). Bringing edge
computing into iot architecture to improve iot network
performance. pages 1–5.
Lapegna, M., Mele, V., and Romano, D. (2023). Cluster-
ing algorithms for enhanced trustworthiness on high-
performance edge-computing devices. Electronics,
12:1689.
Li, X., Song, Y., and Li, Y. (2023). An approach to de-
tect iot botnet attacks based on hierarchical clustering.
page 75.
Mansour, M., Gamal, A., Ahmed, A. I., Said, L. A., Elbaz,
A., Herencsar, N., and Soltan, A. (2023). Internet of
things: A comprehensive overview on protocols, ar-
chitectures, technologies, simulation tools, and future
directions. Energies, 16(8).
Merah, M., Aliouat, Z., and Mabed, H. (2024). Dynamic
load balancing of traffic in the iot edge computing en-
vironment using a clustering approach based on deep
learning and genetic algorithms. Cluster Computing,
28.
Mohamed, A., Saber, W., Elnahry, I., and Hassanien, A. E.
(2020). Coyote optimization based on a fuzzy logic
algorithm for energy-efficiency in wireless sensor net-
works. IEEE Access, 8:185816–185829.
Nasri, M., Lamiri, A., Maaref, H., and Mghaieth, R. (2021).
Adaptive dynamic multi-hop technique for clustering
protocol in wireless sensor networks assisted-internet
of things applications. IET Networks, 11.
Sadrishojaei, M., Navimipour, N., Reshadi, M., Hossein-
zadeh, M., and Unal, M. (2022). An energy-aware
clustering method in the iot using a swarm-based al-
gorithm. Wireless Networks, 28.
Wang, J., Ping, G., Wang, H., Zhang, W., Sun, C., Zhao, B.,
and Chen, e. (2022). A right transfer access control
model of internet of things based on smart contract.
Security and Communication Networks, 2022:1–11.
Xiang, Z., Wang, D., He, M., and Chen, Y. (2023). Dy-
namic system reconfiguration in stable and green edge
service provisioning. Mobile Networks and Applica-
tions, pages 1–17.
Zhang, Y., Yu, H., Zhou, W., and Man, M. (2023). Applica-
tion and research of iot architecture for end-net-cloud
edge computing. Electronics, 12(1).
Secure and Hybrid Clustering for IoT Networks: An Adaptive Dynamic Reconfigurability Approach
419
