
RAHE: A Robust Attribute-Based Aggregate Scheme Enhanced with
Homomorphic Encryption for 5G-Connected Delivery Drones
Aagii Mariam Thomas
a
and Sana Belguith
b
Department of Computer Science, The University of Bristol, U.K.
Keywords:
Drones, Attribute-Based Encryption, Homomorphic Encryption, Data Aggregation.
Abstract:
Unmanned Aerial Vehicles (UAVs), commonly known as drones, have become essential for transporting pack-
ages, food, medicines, and other goods due to the growing demand for fast and efficient delivery services. The
implementation of 5G technology provides high-speed, low-latency, and reliable connectivity, which allows
drones to exchange mission-critical data effectively. However, drones utilizing 5G networks are susceptible
to security threats that could compromise essential security requirements such as confidentiality, authentica-
tion, integrity, and availability. In this paper, we propose a robust communication framework designed for
secure interactions among 5G-connected delivery drones. Our framework relies on a novel Attribute-Based
Encryption with Aggregation that is composed by an enhanced multi-level Attribute-Based Encryption (ABE)
scheme with Homomorphic Encryption (HE). By integrating HE with the ABE scheme, the Ground Control
Station (GCS) and the parent drone can decrypt mission-critical messages as required. This ensures that only
authorized entities have access to sensitive data. Additionally, in scenarios that require data aggregation with-
out exposing the underlying content, the HE property within the ABE scheme facilitates this process. As a
result, encrypted data subsets can be aggregated anywhere in the network without the need for decryption,
thereby preserving data confidentiality and enhancing both communication and computational efficiency. We
utilize a hierarchical Chain-Based Data Aggregation (CBDA) model for the structural organization of drones,
which enhances communication efficiency and reduces energy consumption. By integrating multi-level ABE
for flexible and secure access control with HE, our framework effectively addresses major security challenges
faced by 5G-based drone networks, ensuring the security and efficient management of mission-critical data.
1 INTRODUCTION
Unmanned Aerial Vehicles (UAV) a.k.a drones are
now used in many sectors like the military, aviation,
and civil fields, for purposes like surveillance, search
and rescue, and disaster relief. Recently, drones have
started to gain traction in the transportation sector be-
cause they can deliver goods quickly, even to places
that are difficult to reach. With growing demand
for fast, efficient deliveries, a drone delivery system
could be an ideal solution. Not only are drones faster,
but they also reduce road traffic, which helps cut down
on C O
2
emissions, benefiting the environment.
To function properly, drones need reliable wire-
less connectivity to share information like images,
video, commands, and sensor data with a Ground
Control Station (GCS). A standardized cellular net-
a
https://orcid.org/0000-0001-8677-3968
b
https://orcid.org/0000-0003-0069-8552
work with wide coverage can help ensure high-quality
connectivity, which is especially important for drones
operating beyond the line of sight, which means they
are out of the operator’s direct view. This is where 5G
wireless technology comes in, as it can connect many
devices at once with faster data speeds, low latency,
and better reliability than older networks. With 5G,
drone delivery systems can handle their tasks effec-
tively and maintain stable, high-quality connections.
However, using 5G to connect drones for trans-
portation has its challenges, particularly around se-
curity. Drones often operate in both supervised ar-
eas and unsupervised, potentially hostile zones, which
makes them vulnerable to security threats like eaves-
dropping, data tampering, and even hijacking. For ex-
ample, if two drones are communicating and a mali-
cious attacker intercepts the data, they could gather
information to compromise part or all of the com-
munication. Because of this, securing the communi-
cation channels, between drones and between drones
400
Thomas, A. M., Belguith and S.
RAHE: A Robust Attribute-Based Aggregate Scheme Enhanced with Homomorphic Encryption for 5G-Connected Delivery Drones.
DOI: 10.5220/0013521800003979
In Proceedings of the 22nd International Conference on Security and Cryptography (SECRYPT 2025), pages 400-411
ISBN: 978-989-758-760-3; ISSN: 2184-7711
Copyright © 2025 by Paper published under CC license (CC BY-NC-ND 4.0)

and the GCS, is crucial to protect against these types
of attacks.
To ensure safe drone operations, especially in de-
livery, we need measures like encryption, access con-
trols, and secure communication protocols. With
these in place, drones can expand securely into de-
livery services, meeting the demand for fast, safe, and
environmentally friendly deliveries, even in challeng-
ing areas. Combining 5G’s high-speed, reliable con-
nectivity with strong security can unlock the potential
of drones in the logistics industry, setting them up as
essential tools for the future of delivery.
Several researchers have explored the various se-
curity threats and vulnerabilities that drone networks
face. Menouar et al. (Menouar et al., 2017) and Alwa-
teer et al. (Alwateer and Loke, 2020) have presented
works discussing security attacks that target drone
communication systems. A comprehensive look at
these security threats is provided by Ossamah et al. in
(Ossamah, 2020), where they detail the specific vul-
nerabilities and challenges drones face.
Additionally, Guvenc et al. (Guvenc et al., 2018)
conducted a survey on methods to detect and track
unauthorized UAVs, which pose a risk to drone oper-
ations through both physical and cyber-physical at-
tacks, such as hijacking, spoofing, sniffing, hack-
ing, and network exploitation. Although several re-
searchers have proposed solutions for securing drone
networks, most have focused on Blockchain as the
primary method (Han et al., 2021; Wu et al., 2021).
Encryption techniques, which ensure confidential-
ity for data exchanges within a drone network, are
also widely regarded as highly suitable for protecting
drone communications (Ismael et al., 2021; Cheon
et al., 2018).
In this paper, we present RAHE novel Multi-
Authorisation Attribute Based Encryption (MA-
ABE) scheme with aggregation. This scheme uses the
Homomorphic Encryption properties to enable aggre-
gating ciphertexts without any need for decryption.
To the best of our knowledge, this is the first ABE
scheme that offers an aggregation functionality. We
apply and test the proposed RAHE in a real-world
scenario based on drone communications. This pa-
per’s key contributions are as follows:
• We extend the MA-ABE scheme proposed by
Kaaniche et al. (Kaaniche et al., 2018) to support
an aggregation functionality. This allows for ag-
gregating ciphertext without the need for decryp-
tion or re-encryption.
• We leverage a chain-based data aggregation
method to improve communication efficiency in
drone networks by organizing the drones into par-
ent and children. This design minimizes energy
consumption and supports scalable, structured
communication between multiple drones and the
GCS, which is crucial in resource-constrained
drone networks.
• Unlike most ABE techniques, the size of the re-
sulting ciphertext does not depend on the number
of attributes involved in the access policy, which
makes our scheme more suitable for bandwidth-
limited applications such as drone communica-
tions.
• By employing a multi-level authorization ABE
scheme, this framework efficiently minimizes
the communication overhead between the GCS
and the drones. Instead of communicating di-
rectly with multiple child drones, the GCS sends
mission-critical data only to the parent drone.
This significantly reduces the communication
load, as the parent drone is responsible solely
for relaying the encrypted information to its con-
nected child drones. Child drones can selectively
decrypt the relevant data based on their access
permissions, ensuring data confidentiality without
imposing a computational burden on the parent
drone.
• We prove that RAHE scheme is secure under stan-
dard assumptions and achieves Indistinguisha-
bility under Chosen Ciphertext Attack (IND-
CCA). RAHE can defeat the main security at-
tacks against drone transportation systems such as
eavesdropping and injection attacks thanks to the
use of encryption, as well as Man in the middle
attack thanks to the use of CBDA.
• We provide a detailed theoretical and experimen-
tal analysis of the proposed scheme that proves its
efficiency and reduced costs making it suitable for
drones applications.
The remainder of this paper is organized as follows:
In section 2, a detailed literature review is presented.
In section 3, a brief description of the background is
presented. In section 4, we introduce the framework
specifications, which include the system and threat
models as well as the security requirements and se-
curity model. In section 5 a detailed description of
the proposed secure communication framework is ex-
plained. We perform a security analysis in Section
6 based on the defined security requirements before
presenting a performance analysis in Section 7. And
in section 8 an experimental analysis of the proposed
scheme is presented. Finally, we conclude the paper
in Section 9.
RAHE: A Robust Attribute-Based Aggregate Scheme Enhanced with Homomorphic Encryption for 5G-Connected Delivery Drones
401

2 LITERATURE REVIEW
Security in 5G-connected drone networks has been
widely studied, with existing works primarily focus-
ing on blockchain, traditional encryption, and authen-
tication mechanisms. However, these approaches of-
ten fail to balance security, computational efficiency,
and scalability in resource-constrained drone environ-
ments. Several studies have identified critical secu-
rity threats affecting UAV communication. Guvenc et
al. (Guvenc et al., 2018) introduced threat detection
methodologies for unauthorized UAVs but did not
propose encryption-based countermeasures. While
this paper highlights security challenges, it lacks con-
crete cryptographic solutions for securing real-time
drone communication. Blockchain has been explored
as a security solution for UAV networks. Ismael et
al. (Ismael et al., 2021) introduced a lightweight au-
thentication mechanism using blockchain for secure
drone communication. Although blockchain ensures
tamper-proof data integrity, its high computational
and communication overhead limits applicability in
drone networks, where low latency and energy effi-
ciency are critical.
Recent research efforts have addressed emerging
security concerns and proposed novel solutions for
UAV security and privacy. L. He et al. (He et al.,
2025) introduced an efficient threshold attribute-
based proxy signature scheme for UAV networks, im-
proving authentication and integrity in multi-entity
drone systems. Kaushik et al. (Kaushik et al.,
2025) proposed an end-to-end homomorphically en-
crypted UAV navigation system, leveraging a fu-
sion of reinforcement learning and deep neural net-
works to ensure secure autonomous navigation. Meng
et al. (Zhang et al., 2025) designed a lightweight
acoustic fingerprint-based drone authentication sys-
tem, providing an alternative non-cryptographic se-
curity mechanism that enhances UAV identity veri-
fication. Feng et al. (Feng et al., 2021) introduced
blockchain-integrated ABE for drone authentication,
focusing solely on authentication rather than secure
mission-critical data transmission.
Efficient data aggregation is essential for optimiz-
ing communication in UAV networks. Traditional
ABE schemes lack support for secure data aggre-
gation, necessitating their combination with homo-
morphic encryption. Homomorphic Encryption (HE)
has been employed for data aggregation in various
fields, including IoT and Wireless Sensor Networks
(WSNs). Loukil et al. (Loukil et al., 2021) com-
bined blockchain and HE for secure IoT data aggrega-
tion, demonstrating how HE can facilitate data com-
putations without decryption. Othman et al. (Othman
et al., 2015) proposed a homomorphic encryption-
based aggregation scheme ensuring message integrity
and flexibility in computational cost and security as-
sumptions. Li et al. (Li et al., 2022) extended HE
for UAV-assisted WSNs, enhancing data aggregation
efficiency through blockchain integration. However,
these studies primarily focus on IoT and healthcare
applications, failing to address drone-specific chal-
lenges such as real-time encrypted communication
and dynamic network topology changes.
These recent studies collectively reinforce the
need for a unified security framework integrating
ABE, HE, and CBDA to address access control, com-
putational efficiency, and secure data aggregation in
5G-enabled UAV networks. Our proposed framework
seeks to bridge these gaps by providing a scalable and
efficient cryptographic model for securing UAV com-
munications in 5G and beyond.
Hu et al. (Hu et al., 2019) introduced Chain-
Based Data Aggregation (CBDA) to enhance energy
efficiency in WSNs by structuring nodes in a chain
topology. Wan et al. (Wan et al., 2020) further re-
fined energy-efficient chain communication for peri-
odic data collection in WSNs. While CBDA enhances
structured communication, its integration with ABE
and HE for secure aggregation in UAV networks re-
mains unexplored.
3 BACKGROUND
3.1 Attribute Based Encryption
Attribute-Based Encryption (ABE) (Belguith et al.,
2016) is an encrypted access control mechanism
which is being widely used in multiple applications
such as IoT, cloud computing, vehicular networks,
etc. In ABE, the data owner sets an access policy to
define the users who can access the data. The data is
encrypted with respect to the access policy which is
embedded in the ciphertext in order to enforce access
control policies. A user is able to decrypt a ciphertext
only if there is a match between their attributes and
the access policy embedded in the ciphertext. ABE
has a significant advantage over the traditional public
key encryption primitives as it achieves flexible one-
to-many encryption instead of one-to-one.
3.2 Homomorphic Encryption
Homomorphic encryption (HE) is an encryption
scheme that allows computation to be performed
over encrypted data without any need to decrypt it
(Shrestha and Kim, 2019). Just like other forms of
SECRYPT 2025 - 22nd International Conference on Security and Cryptography
402
encryption, homomorphic encryption uses a public
key to encrypt the data. It uses an algebraic system
to allow functions to be performed on the data while
it is still encrypted. Then, only the individual with
the matching private key can access the unencrypted
data after the functions and manipulation are com-
plete. This allows the data to be and remain secure
and private even when someone is using it. HE has
been applied in different fields because of its ability
to compute on encrypted data while providing secu-
rity and privacy to the users.
3.3 Chain Based Data Aggregation
Chain-Based Data Aggregation (CBDA) (Hu et al.,
2019) is a hierarchical method used to efficiently ag-
gregate data in wireless sensor networks by forming a
structured chain among nodes. This approach reduces
data traffic and prevents eavesdropping by establish-
ing secure paths for data transmission. In the con-
text of multiple drones, CBDA enables a tree topology
where one drone functions as the parent node, while
others connect as leaf nodes. A chain is constructed
among drones based on their residual energy, prior-
itizing nodes with higher energy as leaf nodes. This
structure supports efficient data aggregation by allow-
ing each node to relay information through the chain,
minimizing overall energy consumption and ensuring
secure, structured communication.
4 FRAMEWORK
SPECIFICATION
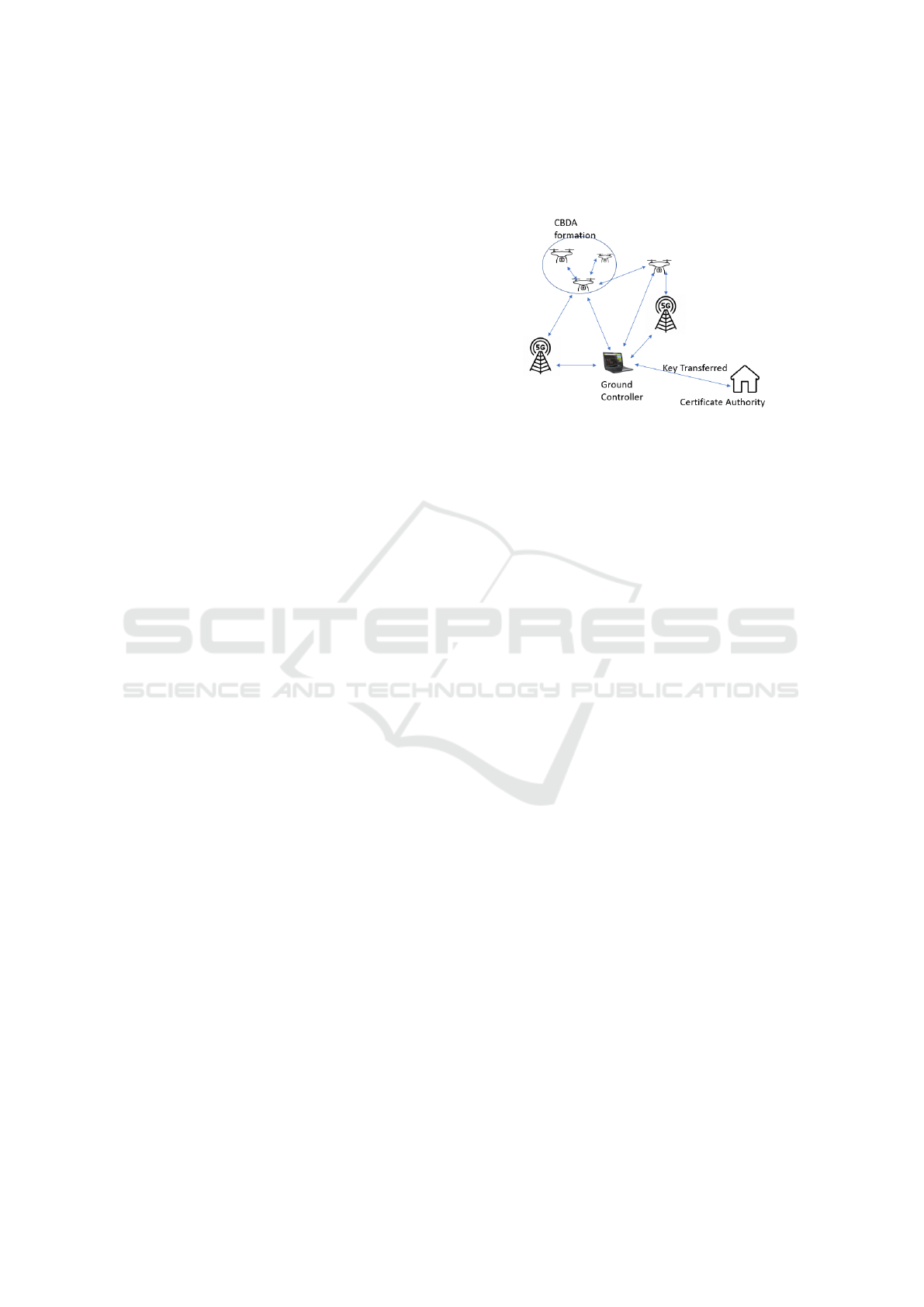
4.1 System and Threat Models
In our scheme, we consider a swarm of delivery
drones and a base station that sends the signal and
data to and from. In the proposed model (Figure 1),
there are four main components:
• Certificate authority (CA) – CA is responsible for
the registration and issue of keys to the Ground
Controller and the drones.
• Ground Control Station (GCS)- GCS sends the
information relating to the remote control com-
mands, telemetry information, and mission sensor
information to the drones. This infrastructure uses
wireless communication.
• Drones – They are responsible for delivering the
packages to the destination based on the com-
mands received from GCS.
• 5G network Base station – They provide a reliable
connection between drones and GCS to transfer
data between them
Figure 1.
The possible adversaries are:
1. Malicious Drone – They are drones that are not
part of the swarm delivery drones and try to inter-
fere with drone-to-drone communication as well
as drone-to-GCS.
2. Malicious ground Controller – They send false in-
formation to delivery drones.
3. A User Equipment – They try to listen to the in-
formation from the GCS and also try to give false
signals to UAVs and control them.
4.2 Security Requirements
In order to have proper secure communication be-
tween the drones and GCS we need to consider the
following requirements:
• Access Control: data exchanged between drones
and between GCS and drones should be secure
against unauthorised access.
• Data Confidentiality: ensures the secrecy of the
exchanged data between drones and with the
GCS.
• Data Aggregation: maintains lower energy con-
sumption, removes data redundancy, improves
network overhead
• Low processing and storage overheads - the
framework should provide low communication
and processing overheads.
4.3 Security Model
To formally demonstrate the security of the proposed
scheme, we will prove that it satisfies Indistinguisha-
bility under Chosen Ciphertext Attack (IND-CCA)
RAHE: A Robust Attribute-Based Aggregate Scheme Enhanced with Homomorphic Encryption for 5G-Connected Delivery Drones
403

standards. IND-CCA security guarantees that an ad-
versary cannot differentiate between the encryptions
of any two chosen messages, even when they can
make adaptive decryption queries. To evaluate the
scheme’s resistance to chosen-ciphertext attacks, the
security model involves an interaction between an ad-
versary A and a challenger C , where A attempts to
distinguish between two challenge messages while
having access to adaptive decryption queries.
Game Initialization - The adversary A selects a set
of encryption attributes A
enc
, corresponding to the at-
tributes defined in the access policy. These attributes
are associated with threshold values t
j
, where t
j
∈
{t
1
,t
2
,...t
m
}, where m is the number of threshold val-
ues. A sends A
enc
to the challenger C .
Setup - The challenger C runs the setup algorithm
and generates the public parameters pp and the ac-
cess policies, with associated thresholds t
j
for each
attribute set S and sends it to the adversary A.
Decryption Query Phase - During this phase,
A makes adaptive decryption and key generation
queries:
Key Generation: The adversary A requests a decryp-
tion key for each session i by selecting an encryption
attribute set A
i
U
corresponding to a threshold value t
j
,
where t
j
∈ {t
1
,t
2
,...t
m
}. The challenger C processes
this request by generating the decryption key SK
A
i
U
and providing it to the adversary A, ensuring that the
key complies with the required threshold t
j
.
Decryption Query: The adversary A submits a re-
quest to decrypt a ciphertext C under a threshold t
j
while considering the encryption attribute set A
enc
.
The challenger C responds by generating the corre-
sponding secret key SK
A
enc
, ensuring that the attribute
set A
enc
satisfies the predefined policy conditions. The
challenger then executes the decryption algorithm,
which results in either the original plaintext message
M if the decryption policy is met, or a rejection sym-
bol ⊥ if the access conditions are not satisfied.
Challenge Phase - In the Challenge Phase, adversary
A selects two plaintext messages of equal length and
submits them to challenger C , along with an attribute
set that has not been used in any decryption queries.
The challenger C randomly selects one of the two
messages, encrypts it according to the access policy
and returns the challenge ciphertext to A . The goal of
the adversary is to determine which of the two mes-
sages was encrypted, using any information gained
from previous queries.
Guess Phase - In the Guess Phase, A attempts to cor-
rectly identify the encrypted message by outputting a
guess bit. The security of the scheme is confirmed
if the adversary’s probability of guessing correctly
remains close to random (50%), meaning they gain
no meaningful advantage. The adversary’s success is
mathematically defined as:
Adv
A
[Exp
Con f
(1
ξ
)] =
P(a = ˆa) −
1
2
Thus, the security model ensures that this advantage
remains negligible, proving that A cannot distinguish
between ciphertexts with probability greater than one-
half. This confirms the framework’s resistance to
adaptive chosen-ciphertext attacks (IND-CCA).
5 THE PROPOSED
FRAMEWORK
The framework proposes a secure and efficient com-
munication between drones and ground control sta-
tions (GCS), with GCS and a parent drone holding
full authority. In a network of multiple drones, by the
use of Chain Based Data Aggregation (CBDA), a tree
topology is formed, where one drone acts as the par-
ent node and others connect as leaf nodes (Hu et al.,
2019). The chain formation process is as follows.
• Tree Formation: Parent drone broadcasts
invite messages. Drones without a parent re-
ply with join and become children. Each child
repeats this to expand the tree. Drones receiving
multiple invites select a parent randomly.
• Chain Formation: Leaf drones form chains by
sequentially connecting to neighbors that reply to
chain messages, based on residual energy or ran-
dom choice.
When the Ground Control Station wants to send a
message to the drone or drone to GCS we are using
the ABE algorithm with the homomorphic encryption
scheme. Attribute-Based encryption is a good candi-
date for sending mission data to the drones. We as-
sume that the chain has been already formed and the
parent node is the responsible node for relaying the
information to children nodes. To this end, we use
a multi-level authorisation ABE scheme where the
parent node can decrypt all the information but also
forward the subset of data needed to children nodes
(Kaaniche et al., 2018). The GCS will first define an
access policy composed by a set of attributes and a set
of thresholds.
For example, the set attributes can be as follows:
S = (Parent,Destination,Location), while the thresh-
olds are (t
1
,t
2
) = (3,2). In this case, the GCS has set
two access policies (t
1
,S) and (t
2
,S) where only the
parent node can satisfy the first one and therefore ac-
cess the related data and a child node can only match
the second access policy. Thus, only the parent node
SECRYPT 2025 - 22nd International Conference on Security and Cryptography
404

can decrypt and access the full encrypted data sent by
the GCS and a child node can access a restricted sub-
set of data. Here if more than one child drone sends
the data to the parent drone, then the messages can be
aggregated with the help of homomorphic encryption
scheme. This helps to add the encrypted messages
together without the need of decryption.
5.1 The RAHE Scheme
This scheme consists of five algorithms:
• Setup : Setup algorithm is run by the Certificate
Authority and it takes as input a security param-
eter. It outputs the public parameter (pp) and the
master secret key (MSK).
• KeyGen : Keygen algorithm is executed by the
CA to derive the secret keys for GCS and drones
based on the attributes.
• Encrypt : The encryption algorithm is performed
by the encrypting entity and it takes pp, multi
level threshold access policy and the message.
This algorithm outputs an encrypted message re-
ferred to as E.
• Aggregation : The aggregation algorithm is per-
formed when there is a need to add two encrypted
messages together even without decrypting the
message.
• Decrypt : The decryption algorithm is executed
by the user. It takes as inputs the pp, user’s secret
key, multi level threshold access policy, and the
encrypted message. If the algorithm is successful
then the message is obtained.
5.2 Concrete Construction of the
Framework
This scheme relies on five algorithms defined as fol-
lows:
Setup. The certificate authority, responsible for se-
cure initialization between drones and GCS, selects
a bilinear group ˆe, p,G
1
,G
2
,G of prime order p,such
that ˆe : G
1
× G
2
→ G. It selects random generator
g ∈ G
1
and a random value z ∈ G
1
along with a set of
G
2
generators {q
j
}{ j = 1,··· , m} such that m = |T |
is the cardinal of the threshold universe T , required
for drone-GCS communication. In addition, it defines
an encoding function ε such that ε : U → (Z/pZ)
∗
,
where |U| = n and U is an attribute universe. For
each attribute a ∈ U, corresponds to a property of ei-
ther a drone or the GCS. The encoded attribute values
ξ(a
i
) = x
i
are pairwise different, where i ∈ [1,n].
Then, the setup algorithm selects a set O =
{o
1
,··· , o
n−1
} of n − 1 pairwise distinct elements of
(Z/pZ)
∗
, ensuring they differ from ξ(a
i
), for all a
i
∈
U.
Let O
i
represent the subset o
1
,··· , o
i
. Thus, the
setup algorithm computes u defined as u = gαγ and
outputs the global public parameters pp as follows:
pp = {G
1
,G
2
,G, ˆe,u,{q
αγ
i
j
}
{i=0,···,2n−1; j=1,··· ,m}
,
O,ξ,z,{ ˆe(g
α
,q
j
)}
{ j=1,···,m}
}
The Certificate authority holds the master key, de-
fined as
msk = (g,α, γ)
where α,γ are two random values from (Z/pZ)
∗
.
Keygen. For any subset A
U
⊂U of attributes associ-
ated with a drone or the GCS, the certificate authority
selects a random value k
U
∈ (Z/pZ)
∗
and computes
the corresponding secret key:
sk = ({g
k
u
γ+ξ(a)
}a ∈ A
i
,{q
k
U
γ
i
j
}
i=0,···,n−2, j=1,··· ,m
,
{q
k
u
−1
γ
j
}
j=1,···m
= (sk1,sk2,sk3)
Encrypt. Let ({t
j
}{ j = 1,· ·· , l}, S) be the access
policy where {t
j
} is the set of threshold values and
S ⊂ U is an attribute set that a drone or GCS must
process to access the message. The entity E(eg.,a
drone or GCS) encrypts a message D using a random
κ ∈ Z/pZ and a random blinding factor r
j
∈ Z/pZ,
producing ciphertext E = (E
1 j
,E
2 j
,E
3 j
){ j = 1,· ·· , l}
defined as:
E
1 j
= g
−kαγ
.g
d
j
.z
r
j
E
2 j
= q
kα
∏
a∈S
(γ+ξ(a))
∏
o∈O
n+t
j
−1−s
(γ+o)
j
E
3 j
= d
j
ˆe(g
α
,q
j
)
k
= d
j
K
j
The entity outputs the encrypted message D as E =
(E
1 j
,E
2 j
,E
3 j
){ j = 1,· ·· , l}.
Aggregate. For two messages D
1
and D
2
from dif-
ferent drones, aggregation proceeds as follows :
For message D
1
:
E
11 j
= g
−k
1
αγ
.g
d
1
.z
r
1
E
21 j
= q
k
1
α
∏
a∈S
(γ+ξ(a))
∏
o∈O
n+t
j
−1−s
(γ+o)
j
RAHE: A Robust Attribute-Based Aggregate Scheme Enhanced with Homomorphic Encryption for 5G-Connected Delivery Drones
405

E
31 j
= d
1
ˆe(g
α
,q
j
)
k
1
= d
1
K
j1
For message D
2
:
E
12 j
= g
−k
2
αγ
.g
d
2
.z
r
2
E
22 j
= q
k
2
α
∏
a∈S
(γ+ξ(a))
∏
o∈O
n+t
j
−1−s
(γ+o)
j
E
32 j
= d
2
ˆe(g
α
,q
j
)
k
2
= d
2
K
j2
Now, the aggregated encrypted message :
E
1 j
= E
11 j
.E
12 j
= g
d
1
+d
2
g
−(k
1
+k
2
)αγ
.z
r
1
+r
2
E
2 j
= E
21
.E
22
E
3 j
= E
31
.E
32
= (d
1
+ d
2
).K
j
K
j
= ˆe(g,q
j
)
α(k
1
+k
2
)
Decrypt. In the decryption phase, there is two sub-
cases, the first one is when the received message is
the encrypted message generated by the Encrypt algo-
rithm, and the second sub-case is when the aggregate
algorithm is applied:
The decrypting entity U, drone or GCS, with a set
of attributes A
U
that satisfies the threshold |A
U
∩ S|=
t
j
can decrypt the encrypted message d
j
under the ac-
cess policy ({t
j
}{ j = 1, ··· ,l},S)), at the threshold
level t
j
. This process allows only authorized drones
or the GCS with sufficient attributes to access the in-
formation.
For this purpose, for all a ∈ A
U
,U, the decrypting
entity U (drone or GCS) first summates its attributes,
with respect to the threshold t
j
satisfied by its certified
attributes, as follows:
A = aggreg({g
k
u
γ+ξ(a)
,ξ(a)}
a∈A
u
) = g
k
u
∏
a∈A
u
(γ+ξ(a))
Subcase 1:
For the encrypt case, U uses the summated secret key
A and the ciphertext element E
2, j
, associated with the
satisfied threshold t
j
, to compute:
L
j
= ˆe(g
κ
u
∏
a∈A
u
(γ+ξ(a))
,E
2 j
)
= ˆe(g,q
j
)
κ
u
κα
∏
a∈S\A
u
(γ+ξ(a))
∏
o∈O
n+t
j
−1−s
(γ+o)
Then, U defines the polynomial P
(A
U
,t
j
,S)
(γ) to help
with attribute aggregation:
P
(A
u
,t
j
,S)
(γ) =
1
γ
(
∏
a∈S∪O
n+t
j
−1−s
\A
s
(γ + ξ(a))
−
∏
a∈S∪O
n+t
j
−1−s
\A
u
ξ(a))
Afterwards, U uses the summated secret key A and
the sk
2
key elements to compute:
[ ˆe(E
1 j
,q
κ
u
P
(A
u
,t
j
,A)
(γ)
j
)L
j
]
1
∏
a∈S∪O
n+t
j
−1−s
\A
u
ξ(a)
= e(g,q
j
)
kακ
u
Next, the decrypting entity U uses its secret key
element sk
3
, related to t
j
to deduce the deciphering
key K
j
as follows:
K
j
= ˆe(E
1 j
,sk
3
) ˆe(g,q
j
)
kκ
u
α
where,
ˆe(E
1 j
,sk
3
) = ˆe(g
−kαγ
g
d
z
r
j
,q
k
u
−1
γ
j
)
Finally, combining terms as needed:
K
j
=
ˆe(g
−kαγ
,q
k
u
−1
γ
j
) ˆe(g
d
,q
k
u
−1
γ
j
)e(z
r
j
,q
k
u
−1
γ
j
) ˆe(g,q
j
)
kκ
u
α
Since the first and last terms contain the encryp-
tion randomness, and the second and third terms in-
volves the message d and the random factor z, these
terms enable the recovery of K
j
:
K
j
= ˆe(g,q
j
)
ακ
Finally, U recovers the sub-message d
j
, with re-
spect to related access level t
j
, by computing
d
j
=
E
3 j
K
j
=
E
3 j
ˆe(g,q
j
)
ακ
Thus, the message d
j
is decrypted and obtained,
allowing drone or GCS to retrieve the necessary in-
formation securely.
Subcase 2:
In this aggregate case, U uses the summated secret
key A and the ciphertext element E
2 j
, associated with
the satisfied threshold t
j
, to compute:
L
j
= ˆe(g
κ
u
∏
a∈A
u
(γ+ξ(a))
,E
2 j
)
= ˆe(g,q
j
)
κ
u
(k
1
+k
2
)α
∏
a∈S\A
u
(γ+ξ(a))
∏
o∈O
n+t
j
−1−s
(γ+o)
Then, U defines the polynomial P
(A
U
,t
j
,S)
(γ) to
help with attribute aggregation:
P
(A
u
,t
j
,S)
(γ) =
1
γ
(
∏
a∈S∪O
n+t
j
−1−s
\A
s
(γ + ξ(a))
−
∏
a∈S∪O
n+t
j
−1−s
\A
u
ξ(a))
Afterwards, U uses the summated secret key A and
the sk
2
key elements to compute:
SECRYPT 2025 - 22nd International Conference on Security and Cryptography
406

[ ˆe(E
1 j
,q
κ
u
P
(A
u
,t
j
,A)
(γ)
j
)L
j
]
1
∏
a∈S∪O
n+t
j
−1−s
\A
u
ξ(a)
= e(g,q
j
)
kακ
u
Next, the decrypting entity U uses its secret key
element sk
3
, related to t
j
to deduce the deciphering
key K
j
as follows:
K
j
= ˆe(E
1 j
,sk
3
) ˆe(g,h
j
)
(k
1
+k
2
)κ
u
α
ˆe(E
1 j
,sk
3
) = ˆe(g
(d1+d2)
.g
−(k
1
+k
2
)αγ
.z
(r
1
+r
2
)
,q
k
u
−1
γ
j
)
This K
j
equation simplifies to :
K
j
= ˆe(g,q
j
)
α(k
1
+k
2
)
Finally, U recovers the sub-message d
j
, with re-
spect to related access level t
j
, by computing
d
j
=
E
3 j
K
j
where d
j
is d1 + d2 in this case. Thus,
d1 + d2 =
E
3 j
K
j
=
(d1 + d2).K
j
K
j
Where the aggregated message is recovered.
6 SECURITY ANALYSIS
In this section, we are considering two main cases
to demonstrate the behaviour of the framework under
different conditions.
Case 1: Unauthorized Drone Attempting De-
cryption
In this case, we are considering an unauthorised
drone without sufficient attributes to decrypt a mes-
sage encrypted under the access policy. Let us as-
sume that the access policy threshold for decryption is
t = 3 with attributes S = {ID,Location,Destination}.
Let an unauthorised drone D have an attribute set
A
D
= {Location}, which does not satisfy the required
threshold policy t = 3. To prove case 1; First, the CA
generates a secret key for D based on the attribute set
A
D
. Which can produce a key term like :
sk = {g
k
D
γ+ξ(a)
}a ∈ A
D
Since D has only one attribute, it lacks the com-
plete key structure needed to satisfy the threshold pol-
icy. Now when trying to decrypt the ciphertext com-
ponent.
E
2 j
= q
kα
∏
a∈S
(γ+ξ(a))
∏
o∈O
n+t
j
−1−s
(γ+o)
j
It needs to compute a pairing term that aggregates
all the attributes in S to satisfy the threshold. With-
out the rest of the attributes, D cannot construct the
polynomial that is required for decryption. Thus, the
unauthorised drone attempts to decrypt the message
and fails which ensures that the framework is secure
against unauthorised access.
Case 2: Aggregation of Two Messages
In this case, when we are trying to add two en-
crypted messages, the decrypted result will yield the
sum of the original message. Let us consider two
messages M1 = 3 and M2 = 5 and are encrypted
as E1 and E2. Now when GCS is encrypting the
messages for the parent drone with the attribute S =
{ID, Location, Destination} and t = 3. The aggrega-
tion of M1 and M2 results as:
E
1 j
= E
11 j
.E
12 j
= g
M1+M2
g
−(k
1
+k
2
)αγ
.z
r
1
+r
2
E
2 j
= E
21 j
.E
22 j
E
3 j
= E
31 j
.E
32 j
= (M1 + M2).K
j
K
j
= ˆe(g,q
j
)
α(k
1
+k
2
)
Now, for decrypting the message the decrypt al-
gorithm as explained in section 5.1 is called and exe-
cuted and results in a simplified equation as :
K
j
= ˆe(g,q
j
)
α(k
1
+k
2
)
Now recovering the sum of the message M1 + M2
M1 + M2 =
E
3 j
K
j
=
(M1 + M2).K
j
K
j
Which results in the sum of encrypted messages.
When originally the two messages are added, the ex-
act result of the encryption as obtained above is re-
ceived. Thus, we prove the correctness of this case
that homomorphic addition enables data aggregation
for encrypted data without requiring intermediate de-
cryption.
Based on these cases the security analysis for the
framework based on the requirements and models as
mentioned in 4.3 and 4.2 is as follows:
Confidentiality. The scheme guarantees confiden-
tiality based on the IND-CCA model. This means that
an adversary without the correct decryption key can-
not identify any differences between the encryptions
of two chosen messages. Even if the adversary selects
two distinct messages, the encrypted outputs remain
indistinguishable.
Proof of Confidentiality:
RAHE: A Robust Attribute-Based Aggregate Scheme Enhanced with Homomorphic Encryption for 5G-Connected Delivery Drones
407

• Setup : Let (G
1
,G
2
,G, ˆe) be bilinear groups of
prime order p and a bilinear map ˆe : G
1
×G
2
→ G.
Let α,γ, r
j
∈ Z
∗
p
be random values chosen by the
certificate authority (CA).
• Encryption : For a message D to be encrypted, we
generate a ciphertext E containing:
E
1 j
= g
−kαγ
· g
D
· z
r
j
,
E
2 j
= q
kα
∏
a∈S
(γ+ξ(a))
∏
o∈O
n+t
j
−1−s
(γ+o)
j
,
where S is the set of attributes required for decryp-
tion, and z is a generator of G
1
.
• IND-CCA : Suppose an adversary A chooses two
messages D
0
and D
1
. The encryption scheme cre-
ates ciphertexts E
0
,E
1
for these messages with
random r
j0
and r
j1
:
E
10
= g
−kαγ
· g
D
0
· z
r
j0
, E
11
= g
−kαγ
· g
D
1
· z
r
j1
.
Without knowledge of k,α,γ, or r
j
, A cannot dis-
tinguish between E
10
and E
11
due to the random-
ization by r
j
and the hardness of the Decisional
Bilinear Diffie-Hellman (DBDH) assumption.
Thus, the security relies on the Decisional Bilinear
Diffie-Hellman (DBDH) assumption. The Cipher-
text components include a random blinding factor r
j
,
ensuring that without the correct secret key, decryp-
tion is computationally infeasible. Which ensures the
scheme is IND-CCA secure, proving confidentiality.
Access Control. The framework enforces access
control by requiring nodes to meet threshold-based
attributes to decrypt specific parts or all of a mes-
sage. The scheme enforces access control by allowing
only entities with attributes that satisfy the predefined
threshold to decrypt specific parts of the message.
• Setup : Define an attribute set S = {a
1
,. .., a
n
}
and an access policy (t
j
,S) where t
j
is the thresh-
old required for decryption.
• Threshold Policy : For a drone U with an at-
tribute set A
U
⊂ S, let |A
U
∩ S| = t
j
. To de-
crypt, U requires a secret key element sk =
g
k
U
γ+ξ(a)
: a ∈ A
U
and computes:
L
j
= ˆe
g
k
U
∏
a∈A
U
(γ+ξ(a))
,E
2 j
!
= ˆe(g,q
j
)
k
U
kα
∏
a∈S\A
U
(γ+ξ(a))
∏
o∈O
n+t
j
−1−s
(γ+o)
.
• Threshold Satisfaction: If |A
U
∩ S| < t
j
, then U
cannot compute the product terms necessary for
decryption, as
∏
a∈S\A
U
(γ + ξ(a)) ̸= 0. Therefore,
U cannot obtain L
j
, preventing unauthorized ac-
cess.
This proves that only drones meeting the threshold t
j
can decrypt the message, enforcing access control.
Key Management Security. The scheme relies on
a centralized certificate authority (CA) for secure key
management, ensuring unique keys and authorization.
1. Key Generation: The CA generates the master key
msk = (g,α, γ) and public parameters pp during
the setup phase, including a secret k
U
for each
user U with attributes A
U
.
2. Unique Secret Key: For each user U , the secret
key sk is generated as:
sk =
g
k
U
γ+ξ(a)
: a ∈ A
U
.
The random k
U
guarantees unique keys for each
user. Thus, keys are user-specific and cannot be
reused across drones.
3. Key Update and Revocation: The CA can issue
updated k
U
values to rekey drones or revoke ac-
cess by not reissuing keys. This ensures that only
authorized drones retain access to their data.
This proves that the framework maintains secure key
management through centralized control, unique key
generation, and flexible rekeying.
Based on the above analysis, the proposed framework
can defeat the main security attacks against drone
transportation systems. The use of encryption can
stop eavesdropping attacks, for example, if a ma-
licious drone tries to access the data exchanged be-
tween drones or between drones and GCS, it will not
be able to decrypt the data as it is encrypted using
ABE with homomorphic encryption. A Man in the
middle attack cannot be successful due to the use
of CBDA among drones to prevent malicious drones
from joining the chain which prevents other nodes
from hearing the encrypted message. In addition, we
use an attribute-based encryption scheme with homo-
morphic encryption scheme where the messages are
encrypted and only the legitimate user can decrypt it,
as the third person will not be able to access it as
their attributes do not satisfy to the access structure.
Finally, the proposed scheme helps to prevent data
injection attack as we use a homomorphic encryp-
tion scheme within the ABE scheme. When a mes-
sage is sent between drones, the data is encrypted,
and a merging of data is only happening among the
chain; no adversary is able to inject data into the com-
munication. As a chain is being formed first, it pre-
vents unauthorised drones or devices from accessing
the chain and injecting data to it.
SECRYPT 2025 - 22nd International Conference on Security and Cryptography
408

7 PERFORMANCE ANALYSIS
The multi-level Attribute-Based Encryption (ABE)
scheme used in this framework is specifically de-
signed for efficiency, resulting in smaller ciphertexts.
The size of the ciphertext primarily depends on the
number of thresholds defined in the multi-level ac-
cess policy. In the context of communication between
Ground Control Stations (GCS) and drones, where the
typical setup consists of just two threshold levels, the
size of the ciphertext can be considered effectively
constant. This feature simplifies performance met-
rics, as both encryption and decryption overheads are
affected only by these limited and manageable thresh-
old levels.
Moreover, by employing a multi-level authoriza-
tion ABE scheme, this framework efficiently mini-
mizes the communication overhead between the GCS
and the drones. Instead of communicating directly
with multiple child drones, the GCS sends mission-
critical data only to the parent drone. This signifi-
cantly reduces the communication load, as the parent
drone is responsible solely for relaying the encrypted
information to its connected child drones. In this
configuration, the parent drone does not need to per-
form additional encryption; it simply forwards the en-
crypted data received from the GCS. Child drones can
selectively decrypt the relevant data based on their ac-
cess permissions, ensuring data confidentiality with-
out imposing a computational burden on the parent
drone.
Without the multi-level ABE scheme, the parent
drone would need to decrypt the received message
from the GCS and re-encrypt data fragments for each
child drone. This process introduces significant en-
cryption overhead and redundant operations, which
drastically reduce system efficiency. Thus, the en-
cryption scheme in our framework optimizes both
computational and communication costs as in table 1.
The Chain-Based Data Aggregation (CBDA)
method further enhances communication efficiency
by reducing interactions among drones as well as be-
tween drones and the GCS. By limiting communica-
tion to the parent drone, the volume of data exchanged
across the network is minimized, thereby enhancing
the overall efficiency of the communication system.
Additionally, incorporating homomorphic encryp-
tion enables efficient data aggregation at the parent
drone. This allows the parent node to combine en-
crypted data from child drones without the need for
decryption, thereby avoiding the overhead associated
with traditional encryption schemes. This approach
ensures that the encryption and decryption load at
the parent node remains low, contributing to a more
streamlined and efficient data aggregation process.
8 EXPERIMENTAL ANALYSIS
To evaluate the performance of the proposed scheme,
we implemented an experimental testbed using a
Raspberry Pi 4 Model B as a drone and a laptop run-
ning Ubuntu on a virtual machine (VM) as the Ground
Control Station (GCS). The Raspberry Pi acts as a
computational proxy for an autonomous drone, while
the laptop simulates the processing environment of a
ground control station in a real-world scenario.
The system utilizes a structured key distribution
process, where a Certificate Authority (CA) running
on the laptop generates the public key and the master
secret key. These keys are securely distributed to both
the drones and the GCS, ensuring that all participating
entities have the necessary cryptographic credentials
for secure encrypted data exchange and computation.
The experimental setup focuses on a drone-to-GCS
communication scenario, which is assessed under two
different configurations.
• Parent Drone to GCS: In this scenario, a single
Raspberry Pi serves as the parent drone, which
encrypts a message using the RAHE scheme be-
fore transmitting it to the Ground Control Station
(GCS). Upon receiving the encrypted message,
the GCS decrypts it based on the established ac-
cess policy. This scenario illustrates a basic im-
plementation of the scheme where the encryption
and decryption processes occur without any addi-
tional operations, such as data aggregation.
• Child Drone to GCS: In this scenario, we con-
sider a network of three Raspberry Pi devices,
with one acting as the parent drone and the other
two as child drones. The child drones encrypt and
send their messages to the parent drone. Instead
of forwarding each individual encrypted message,
the parent drone performs aggregation using our
RAHE scheme that combines ABE and HE in one
go. Therefore, the parent drone does not need
to re-encrypt the message but only aggregate re-
ceived encrypted fragments from each child drone
and forward it to the GCS. GCS, then decrypts
to retrieve the original data. This scenario as-
sesses the efficiency gains from integrating ABE
and HE, particularly in reducing redundant de-
cryption operations and optimizing the aggrega-
tion of encrypted data.
To analyze the performance of the proposed RAHE
scheme, we conducted experimental trials with 1 to 10
attributes, averaging each iteration over 10 runs. The
RAHE: A Robust Attribute-Based Aggregate Scheme Enhanced with Homomorphic Encryption for 5G-Connected Delivery Drones
409
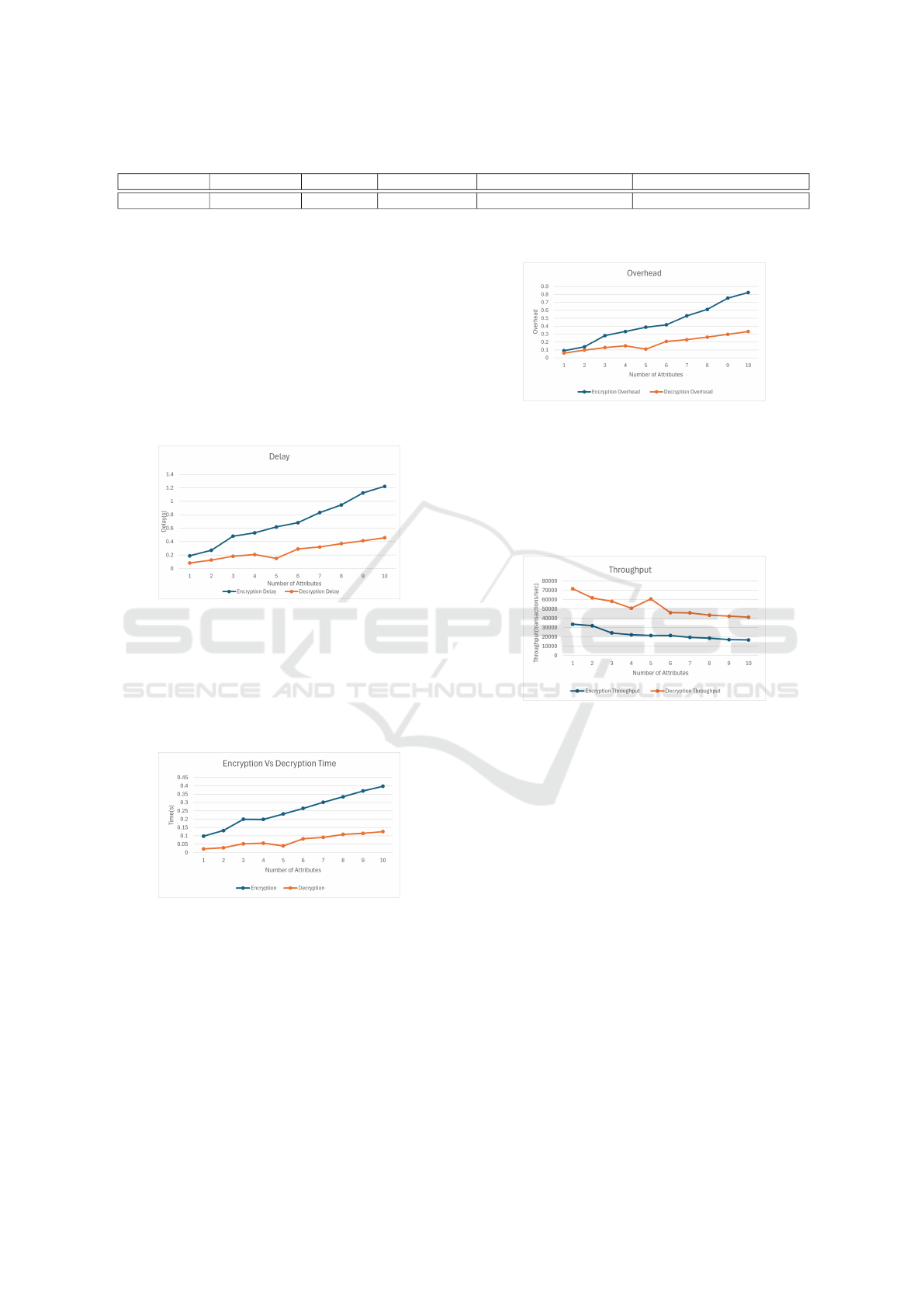
Table 1: Computation and Storage Costs of Multi-Level Attribute-Based Encryption Scheme with Homomorphic Encryption.
Scheme Access Policy Multi-level Ciphertext Size E Computation Overhead U Computation Overhead
ABE with HE Threshold Yes 3n E
1
(2n + 1)+ nE
2
+ nEξ
p
(t
i
+ 1)E
1
+ 4nξ
p
+ E(3n + 1)
E and U are the encrypting entity and the decrypting user. t, n, and m are the size of the threshold, the cardinal of the threshold universe and
the attribute universe, respectively. E
1
, E
2
, E represent exponentiation costs in G
1
, G
2
, G
T
, while ξ
p
is the cost of a pairing operation.
below figures represent the analysis highlighting the
key findings regarding the delay, encryption and de-
cryption time, computational overhead and through-
put.
Delay: The graph in figure 2 compares the en-
cryption and decryption delays. Encryption delay in-
creases as attribute expansion introduces additional
computational overhead, exhibiting a polynomial-like
growth. Decryption delay also rises but remains sub-
stantially lower than encryption delay.
Figure 2.
Encryption vs. Decryption Time: The line graph
in figure 3 further highlights the encryption and de-
cryption times. Encryption time increases linearly as
the number of attributes increases. This demonstrates
that decryption is consistently faster, likely due to a
less complex computational process.
Figure 3.
Overhead: In Figure 4, we observe the computa-
tional overhead for both encryption and decryption.
The overhead for encryption increases as the number
of attributes rises, reaching a value of 0.82 with 10
attributes. In contrast, the decryption overhead grows
at a much slower rate, suggesting that the decryption
process is less complex.
Throughput: The final graph in figure 5 illus-
trates the data processing capabilities of encryption
and decryption. Throughput decreases as the num-
Figure 4.
ber of attributes increases for both processes. Encryp-
tion throughput declines, while decryption throughput
shows a more gradual decrease. However, decryption
maintains a relatively higher throughput, as it requires
fewer computational steps than encryption, leading to
reduced complexity in access policy enforcement.
Figure 5.
Overall, these graphs indicate that encryption is
more computationally intensive, introducing higher
delays and lower throughput, whereas decryption is
significantly faster and more efficient. This insight
is crucial for optimizing the encryption-decryption
process in real-time or resource-constrained environ-
ments.
The experimental results confirm that CP-ABE
with homomorphic encryption enhances secure en-
crypted data processing in drone networks. However,
the computational cost associated with encryption re-
mains a significant factor. On the other hand, decryp-
tion and aggregation demonstrate more favourable
performance, making the scheme suitable for real-
time drone communication over 5G networks.
9 CONCLUSION
In this paper, we present a robust and efficient se-
cure communication framework for 5G-connected de-
SECRYPT 2025 - 22nd International Conference on Security and Cryptography
410

livery drones. Our approach utilizes an Attribute-
Based Encryption (ABE) scheme integrated with Ho-
momorphic Encryption (HE) to enhance both data
security and computational efficiency. By incorpo-
rating HE into the ABE structure, our framework
enables secure data aggregation, and encrypted ac-
cess control without the need for repeated decryption
operations, thereby preserving the confidentiality of
mission-critical information.
Furthermore, we introduce a hierarchical Chain-
Based Data Aggregation (CBDA) model that op-
timizes communication between drones and the
Ground Control Station (GCS). This model reduces
energy consumption and ensures scalability. Our
comprehensive approach addresses critical security
challenges in drone networks, such as access control,
data confidentiality, and low-latency communication,
making it well-suited for real-time 5G-based delivery
applications. As, a future work will focus on other
techniques such as edge computing and other optimiz-
ing libraries to reduce the encryption and decryption
overheads.
REFERENCES
Alwateer, M. and Loke, S. W. (2020). Emerging drone ser-
vices: Challenges and societal issues. IEEE Technol-
ogy and Society Magazine, 39(3):47–51.
Belguith, S., Kaaniche, N., Jemai, A., Laurent, M., and
Attia, R. (2016). Pabac: a privacy preserving at-
tribute based framework for fine grained access con-
trol in clouds. In SECRYPT 2016: 13th International
Conference on Security and Cryptography, volume 4,
pages 133–146. Scitepress.
Cheon, J. H., Han, K., Hong, S.-M., Kim, H. J., Kim, J.,
Kim, S., Seo, H., Shim, H., and Song, Y. (2018). To-
ward a secure drone system: Flying with real-time ho-
momorphic authenticated encryption. IEEE access,
6:24325–24339.
Feng, C., Yu, K., Bashir, A. K., Al-Otaibi, Y. D., Lu, Y.,
Chen, S., and Zhang, D. (2021). Efficient and se-
cure data sharing for 5g flying drones: A blockchain-
enabled approach. IEEE Network, 35(1):130–137.
Guvenc, I., Koohifar, F., Singh, S., Sichitiu, M. L., and Ma-
tolak, D. (2018). Detection, tracking, and interdiction
for amateur drones. IEEE Communications Magazine,
56(4):75–81.
Han, T., Ribeiro, I. d. L., Magaia, N., Preto, J., Segundo,
A. H. F. N., de Mac
ˆ
edo, A. R. L., Muhammad, K.,
and de Albuquerque, V. H. C. (2021). Emerging drone
trends for blockchain-based 5g networks: Open issues
and future perspectives. IEEE Network, 35(1):38–43.
He, L., Gan, Y., and Yin, Y. (2025). Efficient threshold
attribute-based signature scheme for unmanned aerial
vehicle (uav) networks. Electronics, 14(2):339.
Hu, S., Liu, L., Fang, L., Zhou, F., and Ye, R. (2019). A
novel energy-efficient and privacy-preserving data ag-
gregation for wsns. IEEE Access, 8:802–813.
Ismael, H. M. et al. (2021). Authentication and encryption
drone communication by using hight lightweight algo-
rithm. Turkish Journal of Computer and Mathematics
Education (TURCOMAT), 12(11):5891–5908.
Kaaniche, N., Belguith, S., and Russello, G. (2018). Ema-
lab: Efficient multi authorisation level attribute based
access control. In Network and System Security: 12th
International Conference, NSS 2018, Hong Kong,
China, August 27-29, 2018, Proceedings, pages 187–
201. Springer.
Kaushik, A. R., Jutla, C., and Ratha, N. (2025). Towards
building secure uav navigation with fhe-aware knowl-
edge distillation. In International Conference on Pat-
tern Recognition, pages 373–388. Springer.
Li, G., He, B., Wang, Z., Cheng, X., and Chen, J. (2022).
Blockchain-enhanced spatiotemporal data aggrega-
tion for uav-assisted wireless sensor networks. IEEE
Transactions on Industrial Informatics, 18(7):4520–
4530.
Loukil, F., Ghedira-Guegan, C., Boukadi, K., and Ben-
harkat, A.-N. (2021). Privacy-preserving iot data ag-
gregation based on blockchain and homomorphic en-
cryption. Sensors, 21(7):2452.
Menouar, H., Guvenc, I., Akkaya, K., Uluagac, A. S.,
Kadri, A., and Tuncer, A. (2017). Uav-enabled intelli-
gent transportation systems for the smart city: Appli-
cations and challenges. IEEE Communications Mag-
azine, 55(3):22–28.
Ossamah, A. (2020). Blockchain as a solution to drone cy-
bersecurity. In 2020 IEEE 6th World Forum on Inter-
net of Things (WF-IoT), pages 1–9. IEEE.
Othman, S. B., Bahattab, A. A., Trad, A., and Youssef, H.
(2015). Confidentiality and integrity for data aggrega-
tion in wsn using homomorphic encryption. Wireless
Personal Communications, 80(2):867–889.
Shrestha, R. and Kim, S. (2019). Integration of iot with
blockchain and homomorphic encryption: Challeng-
ing issues and opportunities. In Advances in Comput-
ers, volume 115, pages 293–331. Elsevier.
Wan, H., David, M., and Derigent, W. (2020). Energy-
efficient chain-based data gathering applied to com-
municating concrete. International Journal of Dis-
tributed Sensor Networks, 16(8):1550147720939028.
Wu, Y., Dai, H.-N., Wang, H., and Choo, K.-K. R. (2021).
Blockchain-based privacy preservation for 5g-enabled
drone communications. IEEE Network, 35(1):50–56.
Zhang, M., Lu, L., Wu, Y., Yan, Z., Sun, J., Lin, F., and
Ren, K. (2025). Droneaudioid: A lightweight acous-
tic fingerprint-based drone authentication system for
secure drone delivery. IEEE Transactions on Infor-
mation Forensics and Security.
RAHE: A Robust Attribute-Based Aggregate Scheme Enhanced with Homomorphic Encryption for 5G-Connected Delivery Drones
411
