
UOV-Based Verifiable Timed Signature Scheme
Erkan Uslu
1,2 a
and O
˘
guz Yayla
2 b
1
ASELSAN Inc., Ankara, Turkey
2
Middle East Technical University, Ankara, Turkey
Keywords:
Verifiable Timed Signatures, UOV Signature Scheme, Threshold Secret Sharing, Post-Quantum Cryptography.
Abstract:
Verifiable Timed Signatures (VTS) are cryptographic primitives that enable the creation of a signature that
can only be retrieved after a specific time delay, while also providing verifiable evidence of its existence. This
framework is particularly useful in blockchain applications. Current VTS schemes rely on signature algo-
rithms such as BLS, Schnorr, and ECDSA, which are vulnerable to quantum attacks due to the vulnerability
of the discrete logarithm problem to Shor’s Algorithm. We introduce VT-UOV, a novel VTS scheme based on
the Salt-Unbalanced Oil and Vinegar (Salt-UOV) Digital Signature Algorithm. As a multivariate polynomial-
based cryptographic primitive, Salt-UOV provides strong security against both classical and quantum adver-
saries.
1 INTRODUCTION
Verifiable Timed Signatures (VTS) [Thyagarajan
et al., 2020] are cryptographic protocols designed for
using with digital signature schemes. In essence, a
signer may wish for a digital signature to be acces-
sible only after a certain period of time. By embed-
ding the signature into a time-lock puzzle, it is en-
sured that the signature can only be retrieved once
the predefined time has elapsed. Regarding verifia-
bility, before solving the time-lock puzzle, a verifier
can check whether the signature is valid [Rivest et al.,
1996]. This prevents computational efforts from be-
ing wasted on an invalid signature.
Existing VTS schemes primarily rely on signa-
ture algorithms such as BLS [Boneh et al., 2001],
Schnorr [Schnorr, 1991], and Elliptic Curve Digi-
tal Signature Algorithm (ECDSA) [Johnson et al.,
2001]. These schemes, referred to as VT-BLS, VT-
Schnorr, and VT-ECDSA, respectively, are based on
the discrete logarithm problem. However, with the ad-
vancement of quantum computing, Shor’s Algorithm
[Shor, 1999] can efficiently solve the discrete loga-
rithm problem, rendering these signature algorithms
insecure.
The Unbalanced Oil and Vinegar (UOV) signa-
ture scheme is a post-quantum digital signature algo-
rithm [Kipnis et al., 1999]that relies on the hardness
a
https://orcid.org/0000-0001-8033-8922
b
https://orcid.org/0000-0001-8945-2780
of solving multivariate quadratic polynomial equa-
tions over finite fields. It is widely considered resis-
tant to both classical and quantum adversaries. Due to
its short signature length, fast verification and strong
security guarantees, UOV has been a promising can-
didate to be standardized for NIST’s Additional Post-
Quantum Digital Signature Standardization Process
[Alagic et al., 2024].
The current UOV design [Beullens et al., 2023]
in NIST’s standardization process is based on the
salt-UOV [Sakumoto et al., 2011] structure, which
is designed to meet the desired security proofs. In
this work, we integrate Salt-UOV, a quantum-resistant
digital signature scheme, into the Verifiable Timed
Signature (VTS) framework and introduce VT-UOV,
a VTS scheme based on the Unbalanced Oil and Vine-
gar (UOV) digital signature algorithm. Compared to
discrete logarithm-based schemes like BLS, Schnorr,
and ECDSA, UOV involves a fundamentally differ-
ent cryptographic structure, as it relies on multivari-
ate quadratic equations over finite fields. This leads
to distinct computational requirements for key gener-
ation, signing, and verification.
A VTS system typically employs Non-Interactive
Zero-Knowledge proofs, Time-Lock Puzzles, Range
Proofs, Threshold Secret Sharing (TSS), and digi-
tal signature algorithms. To integrate any signature
scheme, its secret keys, public keys, and signatures
must be split into shares (via TSS) and reconstructed
when a sufficient number of shares combine. The
Uslu, E., Yayla and O.
UOV-Based Verifiable Timed Signature Scheme.
DOI: 10.5220/0013521300003979
In Proceedings of the 22nd International Conference on Security and Cryptography (SECRYPT 2025), pages 613-618
ISBN: 978-989-758-760-3; ISSN: 2184-7711
Copyright © 2025 by Paper published under CC license (CC BY-NC-ND 4.0)
613
overall process involves:
1. Splitting the secret key into TSS-compliant
shares, which remain private.
2. Generating shared public keys from these secret
shares, ensuring the main public key can be re-
constructed.
3. Producing shared signatures using the shared se-
cret keys so that a main signature can be recovered
from a threshold of shares.
4. Verifying each shared signature with its corre-
sponding shared public key.
This approach preserves the security properties of
VTS while accommodating various digital signature
schemes.
The outline of this paper is as follows. In Sec-
tion 2, we present the necessary cryptographic struc-
tures and definitions required for defining VT-UOV.
Section 3 introduces the UOV-Based Verifiable Timed
Signature scheme, its sub-algorithms. Additionally,
we give the correctness of the defined sub-algorithms
and performance analysis of VT-UOV. Finally, in Sec-
tion 4, we conclude our work and discuss potential
future directions.
2 PRELIMINARIES
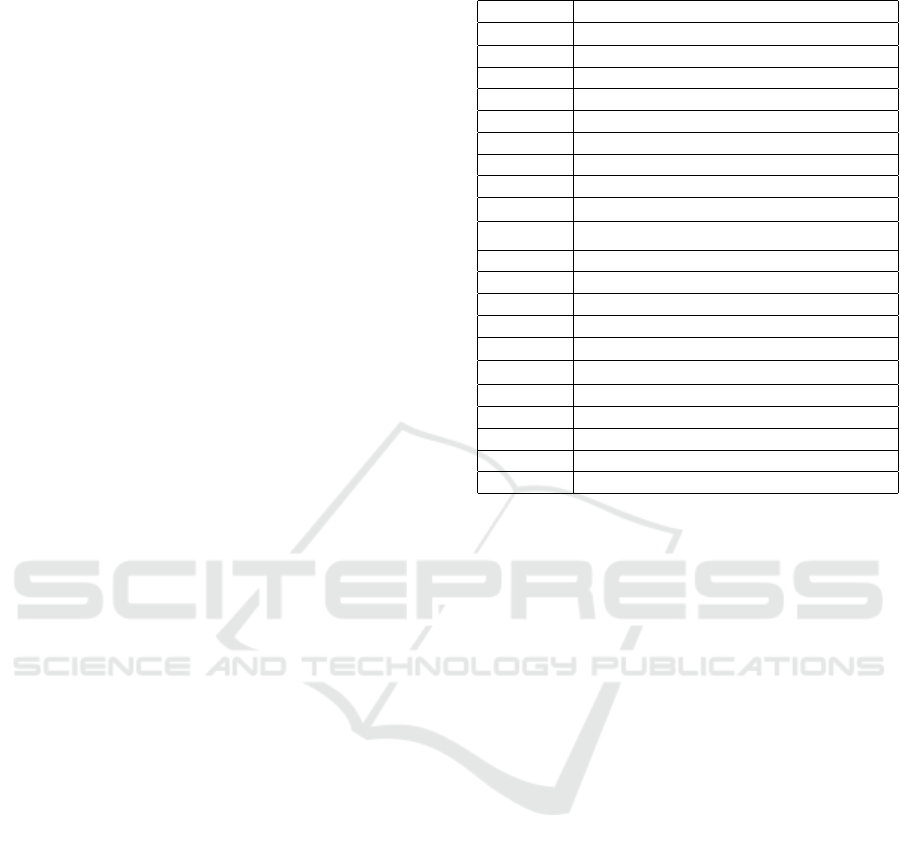
The list of parameters used in our work are provided
in Table 1.
2.1 Cryptographic Primitives
VTS schemes are structures formed by the combina-
tion of multiple cryptographic components. There-
fore, in order to define a VTS scheme, certain crypto-
graphic structures must be determined. In this section,
the cryptographic primitives of VTS schemes are pre-
sented.
2.1.1 Digital Signatures
Digital signatures [Katz, 2010] are mathematical con-
structs designed to verify the authenticity and in-
tegrity of messages or documents. They involve creat-
ing a unique signature that is appended to the message
by the sender. Using a secret key, a digital signature
is generated, and it can only be verified with the cor-
responding public key. Digital signatures ensure that
the message has not been altered during transit and
originates from the claimed sender.
Table 1: List of Parameters.
F
q
Finite Field order q
F
n
q
n-dimensional vector space over F
q
t Threshold Value of TSS
n Whole Shares of TSS
[n] Set of Containing Integers {1,.. ., n}
o Number of Oil Values
v Number of Vinegar Values
w
i
i’th polynomial of w
w[i] i’th integer coefficient of w
w
(i)
i’th vector share of w
w
(i)
j
i’th polynomial share of w
j
∈ w
λ Security Parameter
pk Public Key of Main Signature
sk Secret Key of Main Signature
σ Main Signature
pk
i
= P
(i)
Shared Public Key of σ
i
(F
(i)
,T ) Shared Secret Key of σ
i
σ
i
i’th Shared Signature of σ
crs Common Reference String
ℓ
i
(·) i’th Lagrange interpolation basis
T Linear transformation in UOV
F UOV polynomials defining the secret key
2.1.2 Time-Lock Puzzles (TLP)
TLPs [Rivest et al., 1996] are cryptographic con-
structs that secure data or messages such that access
is only possible after a specific time has elapsed. For
VT-UOV, we define a general description of time-lock
puzzles:
Definition 1. The following TLP functions are incor-
porated into the VT-UOV construction:
• pp
:
= TLP.PuzzleSetup(1
λ
,T): Generates public
parameters pp based on security parameter λ and
desired time T.
• Z
i
:
= TLP.PuzzleGen(pp,σ
i
;r
i
): Produces puz-
zles Z
i
using public parameters pp, shared sig-
natures σ
i
, and random coins r
i
.
• σ
i
:
= TLP.PuzzleSolve(pp, Z
i
): Solves the puzzle
Z
i
to obtain the shared signature σ
i
.
2.1.3 Verifiable Timed Signatures (VTS)
Let σ represent a digital signature. In a VTS scheme,
σ is embedded into a commitment C. The ForceOp al-
gorithm ensures σ is retrievable after time T, provided
the Vrfy algorithm outputs 1. The formal definition of
VTS is as follows:
Definition 2. Verifiable timed signatures consist of
these algorithms:
• (C,π)
:
= Commit(σ,T): Creates a commitment C
and proof π from a signature σ and time T.
SECRYPT 2025 - 22nd International Conference on Security and Cryptography
614

• 0/1
:
= Vrfy(pk,M,C, π): Verifies whether C con-
tains a valid signature with respect to public key
pk, message M, and proof π.
• σ
:
= ForceOp(C): Retrieves signature σ from C
after time T.
2.1.4 Non-Interactive Zero-Knowledge Proofs
(NIZKPs)
NIZKPs [Blum et al., 1991] are cryptographic tools
that allow a prover to demonstrate the validity of
a statement without requiring direct interaction with
the verifier. This is especially beneficial in scenarios
where direct communication is unfeasible. NIZKPs
are used in VTS schemes to generate valid proofs for
signatures embedded in puzzles.
Definition 3. A NIZKP comprises the following algo-
rithms:
• crs
:
= ZKsetup(1
λ
): Produces a common refer-
ence string crs from the security parameter λ.
• π
:
= ZKprove(crs,x,w): Generates proof π for
statement x using witness w.
• 0/1
:
= ZKverify(crs,x,π): Verifies proof π for
statement x and returns 1 if valid, otherwise 0.
2.1.5 Threshold Secret Sharing (TSS)
TSS [Shamir, 1979] securely distributes a secret
among multiple participants such that it can only be
reconstructed when a threshold number of shares are
combined. This ensures no individual has full access
to the secret, enhancing protection against unautho-
rized access.
Definition 4. TSS involves the following algorithms:
• (s
(1)
,. . .,s
(n)
)
:
= TSS.IntShare(s): Splits a secret
s into n integer shares.
• s
:
= TSS.IntRecon(s
(1)
,. . .,s
(t)
): Combines t
shares to reconstruct the secret s.
The secret is embedded in the constant term of a
polynomial f (x) = a
0
+ a
1
x + ·· · + a
n−1
x
n−1
, where
a
0
is the secret. Shares are points (i, f (i)) = (x
i
,y
i
)
for i ∈ [n]. Using Lagrange interpolation, the secret
a
0
is reconstructed as:
a
0
= f (0) =
k−1
∑
j=0
y
j
ℓ
j
(0), ℓ
j
(x) =
∏
0≤m≤k
m̸= j
x − x
m
x
j
− x
m
.
In the VT-UOV scheme, we utilize a t-out-of-n
TSS approach. This means that in our scheme, any
t shares (where t ≤ n) are sufficient to reconstruct the
secret.
2.2 Salt-UOV Scheme and Its Security
Argument
The Salt-UOV [Sakumoto et al., 2011] scheme is a
variant of the submitted UOV scheme to NIST stan-
dardization process introduced earlier. The primary
difference lies in the signing algorithm, where Salt-
UOV incorporates a random ”salt” value to enhance
security. During the signing process, a random vine-
gar vector v ∈ F
v
q
is selected, followed by uniformly
and independently chosen multiple salt values. The
system of linear equations F
v
u
= Hash(µ∥salt)
is solved until a valid solution is found. The full de-
tails of the scheme are provided in [Beullens et al.,
2023].
3 UOV-BASED VERIFIABLE
TIMED SIGNATURE SCHEME
In this chapter, we define our VTS scheme, VT-UOV,
based on the Unbalanced Oil and Vinegar (UOV) sig-
nature scheme. The general structure of VT-UOV is
presented in Figure 1.
3.1 Supportive Algorithms for VT-UOV
In this section, we introduce the supporting algo-
rithms for the VT-UOV scheme. These algorithms
explain how to set up a t-out-of-n Threshold Se-
cret Sharing mechanism, where t ≤ n, to securely
divide and reconstruct the secret components of the
scheme. We also describe the process for generating
keys and signatures in VT-UOV, ensuring compatibil-
ity with the Verifiable Timed Signature (VTS) frame-
work. Additionally, we provide an algorithm for ver-
ifying VT-UOV signatures, which allows for the val-
idation of each shared signature and ensures the cor-
rectness of the overall reconstructed signature. These
algorithms form the foundation for the secure and ef-
ficient operation of VT-UOV.
UOV-Based Verifiable Timed Signature Scheme
615

3.1.1 Key Generation of VT-UOV
The key generation process of the VT-UOV scheme is
defined in Algorithm 5.
The pk.Shares parameters generated by Algorithm
5 must allow the reconstruction of the main public
key pk in a TSS manner using at least the threshold
value t ≤ n. This reconstruction process is detailed in
Algorithm 6.
3.1.2 Signature Process of VT-UOV
Algorithm 7 takes the message µ, sk.Shares, and the
main signature σ as input and outputs the shared sig-
natures sign.Shares.
Algorithm 8 is used in the reconstruction phase of
the main signature in the VT-UOV scheme.
Input: Time T, Security Parameter λ
Output: Common Reference String crs
crs
range
← ZKsetup(1
λ
);
pp ← TLP.PSetup(1
λ
,T);
return crs ← (crs
range
, pp);
Algorithm 1: VT-UOV.Setup(λ,T).
Input: crs,σ = (s,salt), sk = (F ,T )
Output: Commitment C and Range Proof π
(sk.Shares,pk.Shares) ← VT-UOV.KeyGen(F );
sign.Shares ← VT-UOV.SignShares(σ = (s, salt),sk.Shares,Message µ);
for i ∈ [n] do
r
i
← {0,1}
λ
// Random Sampling
Z
i
← TLP.PGen(pp,σ
i
;r
i
);
π
range,i
← ZKprove(crs
range
,(Z
i
,0, 2
λ
,T), (σ
i
,r
i
));
end
I ← H
′
(pk,(pk
1
,Z
1
,π
range,1
),. .., (pk
n
,Z
n
,π
range,n
)) where H
′
: {0,1}
∗
→ I ⊂ [n] of size |I| = t − 1 ;
return π ← ({pk
i
,π
range,i
}
i∈[n]
,I,{σ
i
,r
i
}
i∈I
) and C ← (Z
1
,. .., Z
n
,T);
Algorithm 2: VT-UOV.CommitAndProof.
Input: Commitment C ← (Z
1
,. .., Z
n
,T), Proof π
Input: Common Reference String crs ← (crs
range
, pp), Message µ, Main Public Key pk
Output: Accept or Reject
if VT-UOV.PkRecon(pk.Shares) ̸= pk and ∃ j ∈/ I such that pk
j
∈/ pk.Shares then
return Reject;
end
if ZKverify(crs
range
,(Z
i
,0, 2
λ
,T), π
range,i
) ̸= 1 for any i ∈ [n] then
return Reject;
end
if ∃i ∈ I such that Z
i
̸= TLP.PGen(pp,σ
i
;r
i
) or VT-UOV.SignVerify(pk
i
,M,σ
i
) ̸= 1 then
return Reject;
end
if I ̸= H
′
(pk,(pk
1
,Z
1
,π
range,1
),. .., (pk
n
,Z
n
,π
range,n
)) then
return Reject;
end
return Accept;
Algorithm 3: VT-UOV.Verify.
Input: Commitment C ← (Z
1
,. .., Z
n
,T)
Output: Main Signature σ
for i = 1 to t do
σ
i
∈ sign.Shares ← TLP.PSolve(pp,Z
i
);
end
return σ ← VT-UOV.SignRecon(sign.Shares,s);
Algorithm 4: VT-UOV.ForceOpen.
Figure 1: VT-UOV Scheme.
SECRYPT 2025 - 22nd International Conference on Security and Cryptography
616

Input: Main Secret Key sk=
(F
:
= f = ( f
1
,. . ., f
o+v
),T )
Output: Shared Public Keys pk.Shares,
Shared Secret Keys sk.Shares
(F
(1)
,. . .,F
(n)
)
:
= TSS.VectorShare(F ) ;
for i = 1 to n do
pk
i
= P
(i)
← F
(i)
◦ T ;
end
pk.Shares ← (P
(1)
,. . .,P
(n)
);
sk.Shares ← ((F
(1)
,T ) ..., (F
(n)
,T ));
return (pk.Shares,sk.Shares);
Algorithm 5: VT-UOV.KeyGen Algorithm.
Input: A subset of pk.Shares,(P
(1)
,. . .,P
(t)
)
where t ≤ n
Output: Main Public Key pk
pk = P ← TSS.VectorRecon(P
(1)
,. . .,P
(t)
)
return pk;
Algorithm 6: VT-UOV.PkRecon Algorithm.
Input: sk.Shares, Message µ
Input: Main Signature σ := (s, salt)
Output: sign.Shares
v ← F
v
q
;
repeat
(salt
(1)
,. . .,salt
(n)
) ← TSS.IntShare(salt);
for i = 1 to n do
k
i
← Hash(µ∥salt
(i)
);
∆
t
i
←
v
u
∈ F
o+v
q
where F
(i)
v
u
= k
i
;
end
until w
i
← ∆
k
i
| ∀i ∈ [n];
for i = 1 to n do
s
i
← T
−1
(w
i
);
σ
i
← (s
i
,salt
(i)
);
end
sign.Shares
:
= (σ
1
,. . .σ
n
);
return sign.Shares;
Algorithm 7: VT-UOV.Sign Algorithm.
3.1.3 Verification Process of VT-UOV
The VT-UOV.SignVerify algorithm is used to verify
a shared signature against the corresponding shared
public key at the same index along with the message.
Input: A subset of sign.Shares,(σ
1
,. . .σ
t
)
where t ≤ n
Input: First tupple of σ, s
Output: Main Signature σ
salt ← TSS.IntRecon(salt
(1)
,. . .,salt
(t)
);
σ ← (s, salt);
return σ;
Algorithm 8: VT-UOV.SignRecon Algorithm.
Input: µ, P
(i)
, σ
i
= (s
i
,salt
(i)
)
Output: Boolean value indicating signature
validity
k
i
← Hash(µ∥salt
(i)
);
k
′
i
← P
(i)
(s
i
);
return (k
i
== k
′
i
);
Algorithm 9: VT-UOV.SignVerify Algorithm.
3.2 Threshold Secret Sharing for
salt-UOV’s Parameters
To divide the parameters of VT-UOV into shares us-
ing the TSS algorithm, it is essential first to define a
method for splitting an array or a vector into shares
and then reconstructing them accurately. Throughout
this paper, we employ a t-out-of-n TSS scheme where
t ≤ n, meaning that at least t of the generated shares
are required to successfully reconstruct the original
value. This ensures both flexibility and security in the
secret-sharing process.
In the proposed scheme, we define Algorithm 10,
which takes a array used in VT-UOV as input and out-
puts its shares. Algorithm 11 is then used to recon-
struct the original array from its shares.
Input: Coefficients f [i] of f for all
i ∈ [o · (o + v)] where f ∈ F
o·(o+v)
q
Output: Shares ( f
(1)
,. . ., f
(n)
) of f , where
f
(i)
∈ F
o·(o+v)
q
.
for i = 0 to o · (o + v) do
( f
(1)
[i],. . ., f
(n)
[i]) ← TSS.IntShare( f [i])
// Shared coefficients of f
end
for i = 1 to n do
f
(i)
← ( f
(i)
[0],. . .,z
(i)
[o · (o + v) − 1])
// Construct array shares
end
return ( f
(1)
,. . ., f
(n)
)
Algorithm 10: TSS.ArrayShare for VT-UOV.
UOV-Based Verifiable Timed Signature Scheme
617

Input: Chosen t-threshold arrays from
( f
(1)
,. . ., f
(n)
).
Output: f ∈ F
o·(o+v)
q
for i = 0 to o · (o + v) do
f [i] ← TSS.IntRecon( f
(1)
[i],. . ., f
(t)
[i])
end
return f
Algorithm 11: TSS.ArrayRecon for VT-UOV.
Additionally, we define Algorithm 12 and Algo-
rithm 13 to generate secret shares of a vector used
in VT-UOV operations and to reconstruct the vector
from its shares.
Input: Vector of Arrays f = ( f
1
,. . ., f
ℓ
).
Output: Vector shares (f
(1)
,. . .,f
(n)
) of f.
for i = 1 to ℓ do
( f
(1)
i
,. . ., f
(n)
i
) ← TSS.ArrayShare( f
i
)
// Share each array in the
vector
end
for i = 1 to n do
f
(i)
← ( f
(i)
1
,. . ., f
(i)
ℓ
) // Construct
vector shares
end
return (f
(1)
,. . .,f
(n)
)
Algorithm 12: TSS.VectorShare for VT-UOV.
Input: Chosen t-threshold vector shares from
(f
(1)
,. . .,f
(n)
).
Output: Vector f = ( f
1
,. . ., f
ℓ
).
for i = 1 to ℓ do
f
i
← TSS.PolyRecon( f
(1)
i
,. . ., f
(t)
i
)
end
return f = ( f
1
,. . ., f
ℓ
)
Algorithm 13: TSS.VectorRecon for VT-UOV.
4 CONCLUSION
In this work, we introduced VT-UOV, a Verifiable
Timed Signature scheme based on a quantum-secure
structure Salt-UOV Digital Signature Algorithm. We
successfully integrated UOV into a VTS framework
by ensuring that all key parameters, including the se-
cret key, public key, and signature, can be divided into
shares and reconstructed using Shamir’s Threshold
Secret Sharing algorithm. Additionally, we demon-
strated that for any given index, the shared secret
key can generate the corresponding shared public key
and shared signature at the same index. Despite the
challenges posed by UOV’s large parameter sizes and
complex multivariate quadratic equations, we suc-
cessfully addressed these obstacles and achieved the
desired functionality.
REFERENCES
Alagic, G., Bros, M., Ciadoux, P., Cooper, D., Dang, Q.,
Dang, T., Kelsey, J. M., Lichtinger, J., Miller, C. A.,
Moody, D., Peralta, R., Perlner, R., Robinson, A., Sil-
berg, H., Smith-Tone, D., Waller, N., and Liu, Y.-K.
(2024). Status report on the first round of the ad-
ditional digital signature schemes for the nist post-
quantum cryptography standardization process.
Beullens, W., Chen, M.-S., Ding, J., Gong, B., Kannwis-
cher, M. J., Patarin, J., Peng, B.-Y., Schmidt, D., Shih,
C.-J., Tao, C., and and, B.-Y. Y. (2023). Unbanalced
oil and vinegar. https://www.uovsig.org/.
Blum, M., De Santis, A., Micali, S., and Persiano, G.
(1991). Noninteractive zero-knowledge. SIAM Jour-
nal on Computing, 20(6):1084–1118.
Boneh, D., Lynn, B., and Shacham, H. (2001). Short sig-
natures from the weil pairing. In International confer-
ence on the theory and application of cryptology and
information security, pages 514–532. Springer.
Johnson, D., Menezes, A., and Vanstone, S. (2001). The
elliptic curve digital signature algorithm (ecdsa). In-
ternational journal of information security, 1:36–63.
Katz, J. (2010). Digital signatures, volume 1. Springer.
Kipnis, A., Patarin, J., and Goubin, L. (1999). Unbalanced
oil and vinegar signature schemes. In Stern, J., editor,
Advances in Cryptology — EUROCRYPT ’99, pages
206–222, Berlin, Heidelberg. Springer Berlin Heidel-
berg.
Rivest, R. L., Shamir, A., and Wagner, D. A. (1996). Time-
lock puzzles and timed-release crypto.
Sakumoto, K., Shirai, T., and Hiwatari, H. (2011). On prov-
able security of uov and hfe signature schemes against
chosen-message attack. In Post-Quantum Cryptog-
raphy: 4th International Workshop, PQCrypto 2011,
Taipei, Taiwan, November 29–December 2, 2011.
Proceedings 4, pages 68–82. Springer.
Schnorr, C.-P. (1991). Efficient signature generation by
smart cards. Journal of cryptology, 4:161–174.
Shamir, A. (1979). How to share a secret. Communications
of the ACM, 22(11):612–613.
Shor, P. W. (1999). Polynomial-time algorithms for prime
factorization and discrete logarithms on a quantum
computer. SIAM review, 41(2):303–332.
Thyagarajan, S. A. K., Bhat, A., Malavolta, G., D
¨
ottling, N.,
Kate, A., and Schr
¨
oder, D. (2020). Verifiable timed
signatures made practical. In Proceedings of the 2020
ACM SIGSAC Conference on Computer and Commu-
nications Security, pages 1733–1750.
SECRYPT 2025 - 22nd International Conference on Security and Cryptography
618
