
Stegoslayer: A Robust Browser-Integrated Approach for Thwarting
Stegomalware
Rushikesh Kawale
1 a
, Sarath Babu
2 b
and Virendra Singh
1 c
1
Department of Electrical Engineering, Indian Institute of Technology Bombay, Mumbai, India
2
Department of Computer Science & Engineering, National Institute of Technology, Warangal, India
Keywords:
Stegomalware, Steganography, Polyglots, Browser, Image.
Abstract:
Over the years, various threat groups (APTs) have exploited innocuous-looking images as carriers for mal-
ware payloads, data exfiltration, and covert command and control communication by utilizing steganographic
and polyglot techniques. Due to the widespread use of browsers as entry points to the internet, they have
become the primary targets of online attacks. The attackers use the browser as an initial vector for carrying
out steganographic-based attacks due to the browser’s ability to execute JavaScript. Attackers leverage this
feature to extract and run hidden payloads from polyglot and steganographic media. To the best of our knowl-
edge, no existing work prevents stegomalware attacks exploiting web-browser vulnerabilities, even though
modern browsers remain susceptible to such attacks. Thus, to counter stegomalware attacks, we propose a
steganographic attack prevention algorithm, Stegoslayer. Stegoslayer is an image-cleaning web extension and
technique that ensures the image is free of malicious content while maintaining its quality. We performed func-
tional tests against F5, Outguess and Openstego steganographic algorithm and stegosploit stegomalware. Fur-
ther, we analyzed the performance of Stegoslayer against the state-of-the-art prevention method, Stegowiper.
The results indicate that the output image of Stegoslayer has 20% better PSNR value than stegowiper.
1 INTRODUCTION
More than 63% of people around the world use the
internet, and it is increasing about 2.8% per year.
Among these users, more than 94.5% users use so-
cial media every month (Petrosyan, 2024). The in-
creasing number of internet users and the rising fre-
quency of cyber attacks targeting individuals and or-
ganizations becomes growing concerns about security
and privacy. Cyber attacks include harmful activi-
ties such as stealing confidential information, spying
or monitoring, and causing harm (sometimes signif-
icant) to the victim’s device. As browsers are users’
primary point of interaction with the internet, they are
more convenient for attackers while mounting an at-
tack. Many unauthorized websites provide paid con-
tent (such as images, documents, or videos) for free
to attract users. Besides, these sites often contain
malicious ads, pop-ups, or hidden malware that can
compromise user security. Intrusion Detection Sys-
a
https://orcid.org/0009-0001-4640-9982
b
https://orcid.org/0000-0003-3823-2213
c
https://orcid.org/0000-0002-7035-7844
tem (IDS) are developed to provide protection against
such attacks by analysing executable files. However,
attackers use non-executable files to mount an attack
and hide from current anti-malware solutions. Failing
to detect such attacks can infect the system. The pop-
ular evasion techniques used in non-executable files
are (i) steganography and (ii) polyglots.
Steganography is a technique that hides informa-
tion/data in the header or body of the multimedia file
(carrier) such as image, video, document, audio, etc.
However, the carrier looks same or indistinguishable
by human. The attackers began employing steganog-
raphy to conceal malware within non-executable files,
a tactic known as Stegomalware. The most popular
and commonly used file format such as JPEG, PNG,
etc., are used with steganographic technique for mali-
cious activity. Stegomalware appears to be the harm-
less non-executable file that anti-malware programs
fail to detect, even though it contains malware. The
modern browsers provide extended features to load
images and documents in the browser itself. There-
fore, the users are less dependent on the individual
application viewer software, facilitating attackers to
mount attacks through image and document files. Ste-
Kawale, R., Babu, S., Singh and V.
Stegoslayer: A Robust Browser-Integrated Approach for Thwarting Stegomalware.
DOI: 10.5220/0013509200003979
In Proceedings of the 22nd International Conference on Secur ity and Cryptography (SECRYPT 2025), pages 601-606
ISBN: 978-989-758-760-3; ISSN: 2184-7711
Copyright © 2025 by Paper published under CC license (CC BY-NC-ND 4.0)
601

i m g
img
img
+ img
+ img
+ img
A
B
local
system
local
system
Anti-
malware
Anti-
malware
Browser
Browser
malware is
undetected
malware is
removed
Network
Figure 1: Stegomalware-based Browser Exploit.
gomalware primarily exploits network covert chan-
nels created by hiding malicious data in legitimate
traffic to enable cloaked communication paths (Cav-
iglione and Mazurczyk, 2022), as shown in Figure 1.
Stegosploit (Shah, 2015) is such tool used to create
stegomalware that employs image to mount an attack
browser on system.
On the other hand, Polyglot is a single file whose be-
haviour is based on the program or application used to
access it. Polyglot is a sophisticated method of evad-
ing security mechanisms by embedding executable
content within seemingly innocent image files, pos-
ing significant challenges to the traditional detection
system (Albertini, 2015). Polyglot files can be exe-
cuted by multiple application programs or in multiple
language compilers without errors. Polyglots are used
to bypass security systems based on file types, as most
of the defence system targets specific file types (.exe,
.vbs, .sh, etc.). Malicious files can bypass the detec-
tion system by acting as innocent (safe) valid files.
The steganography and polyglots techniques are be-
coming the attacker’s powerful tool for concealing
malware, evading detection and executing sophisti-
cated attacks due to the ability to bypass the modern
detection system. The recent major stegomalware at-
tacks performed against the organisation are as fol-
lows (Caviglione and Mazurczyk, 2022):
• In July 2022, Alibaba’s cloud storage buckets
were compromised by malicious shell scripts
and malware payloads were disseminated using
steganography (Cyble, 2022)
• In 2022, KNOTWEED malware used the JPEG
file to hide Corelump malware.
• In July 2020, attackers used steganography to im-
plement a C&C channel nested in email traffic to
distribute a varient of OilRig malware.
• In December 2018, an enterprise cyber security
company, Trend Micro, reported cyber criminals
used memes on Twitter (JPEG images) to convey
commands to malware (Cohen et al., 2020).
The increase in online activities has expanded the at-
tack surface for malicious actors. Browsers are the
primary tool for general users to access online infor-
mation and services. However, browsers often have
vulnerabilities to process and execute malicious con-
tent embedded by the attacker in webpage images.
The malware hidden in the webpage images evade de-
fense mechanism and successfully execute the attack.
Early prevention against stegomalware minimizes po-
tential damage and protects user privacy. The exist-
ing state-of-the-art technique is not effectively pre-
venting stegomalware attacks. The frequent use of
steganographic algorithms by attackers or APTs to
evade the security system motivated us to propose
an algorithm for the stegomalware prevention tech-
nique. Therefore, we proposed a browser-integrated
approach that filters the malicious content from im-
ages on the webpage and the local system.
2 RELATED WORK
Anti-steganographic algorithms can be categorized
into detection or prevention based algorithms. The
detection-based algorithm analyses the pattern and
identifies the presence of malicious content. Mean-
while, the prevention technique modifies or recon-
structs to sanitize the image. Over the years, var-
ious advanced steganographic algorithms emerged,
and statistical models such as such as noise, spectrum
or histogram-based analysis and signature matching
became ineffective for detecting hidden content in
an image. Thus, machine learning (ML) models are
adopted to distinguish between benign and stego files
based on the noise characteristic of the image. As
our focus is towards preventing the stegomalware at-
tack through browsers, we reviewed the state-of-the-
art prevention techniques.
Zuppelli et al. (Zuppelli et al., 2021) proposed a deep
neural network to disrupt information hidden inside
PNG image using the Invoke-PSImage tool. However,
it does not eliminate the content within the metadata
fields. Stegowiper (Alfonso Mu
˜
noz, 2022) removes
the metadata and add noise to the pixels to clean or
remove the steganographic content in an image. Im-
age quality degrades due to noise addition, and pri-
vacy may be compromised as a proxy intercepts the
communication. Attackers can bypass the system by
modifying the HTTP content type or embedding the
images in an HTML file. Content Disarm and Re-
construction (CDR) is a tool that sanitizes files by de-
constructing the content and analysing the elements
of files for malicious activity. DocBleach (Guerreiro,
2024) sanitizes office documents, pdf and rtf files. It
iterates over file elements and removes suspicious el-
ements and then rebuilds the file. If malware is not in
the element, then CDR is ineffective.
SECRYPT 2025 - 22nd International Conference on Security and Cryptography
602
Input image
Extract pixel data from input image
Prepare temporary webp file
Extracting necessary properties
Adapting compression
Adapting header
Extract data from temporary WebP image
Encode in original format
Output image
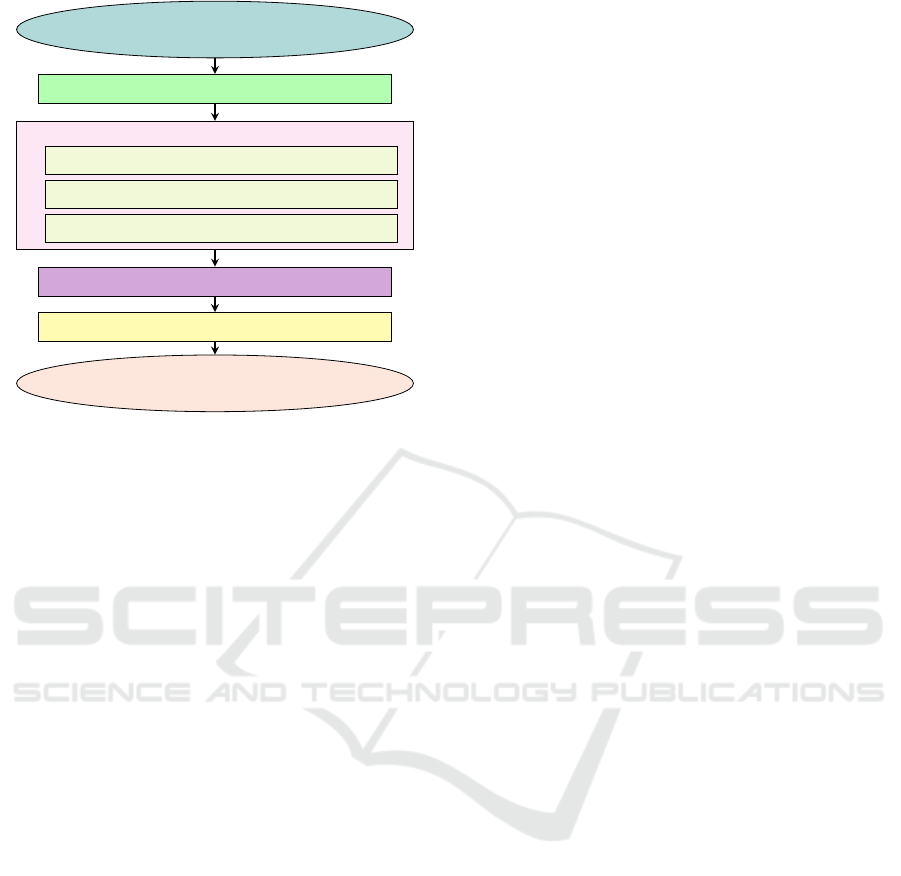
Figure 2: Stegoslayer Flowchart.
The current prevention techniques disrupt the image
in order to remove the hidden content. However, the
current prevention techniques are limited to particular
steganographic algorithms, and they degrade image
quality.
3 PROPOSED SCHEME
We introduce a defense mechanism named
Stegoslayer to counter attacks involving stego-
malware and polyglot. Our approach specifically
addresses threats targeting web browsers, which
leverage these techniques to exploit vulnerabili-
ties for penetration and malicious activities. We
developed a browser extension to defend against
browser-based attacks, leveraging steganographic
images as a carrier and polyglots.
3.1 Stegoslayer
Stegoslayer is a technique that removes the hidden
malware/content inside the image file. In order to re-
move malware hidden inside the image, the pixel val-
ues of the image file are decoded from an actual image
format (JPEG, PNG, BMP, etc.) and transformed into
a WebP file format. Transformation into webp for-
mat involves three basic modules: (i) Extracting Im-
age Properties and Data, (ii) Adapting Compression,
and (iii) Adapting Header.
i) Extracting Image Properties and Data
In this step, image properties and metadata are
identified and extracted into a buffer. The pro-
cess begins by converting the image into a byte se-
quence. Based on the file format, essential proper-
ties such as color space and dimensions are iden-
tified and extracted.
ii) Adapting Compression
From the extracted byte sequence, the pixel infor-
mation undergoes predictive coding, followed by
entropy coding and alpha compression (Develop-
ers, 2025; Inc., 2025) to achieve compression for
the WebP format. Predictive coding minimizes
redundancy by estimating pixel values based on
neighboring data, while entropy coding enhances
compression by assigning shorter codes to fre-
quently occurring patterns. Finally, alpha com-
pression optimizes transparency data for efficient
storage and transmission.
iii) Adapting Header
The extracted properties are mapped to the corre-
sponding WebP header. This ensures the neces-
sary content of the image header is only retained
in the fresh generated image.
After compression, the binary data is written to an
output file with WebP headers and a block structure.
The output file has the “.webp” extension. Once im-
ages are passed through modules of Stegoslayer, un-
necessary content from the infected image is effec-
tively filtered out. While applying the WebP compres-
sion algorithm on decompressed input images, hid-
den content is removed from the pixels of the im-
age. When transforming decompressed image pixels
in WebP format, the original image structure is con-
verted and stored according to the WebP format speci-
fications. The WebP file is converted back to the orig-
inal image format to retain the original file format,
as shown in Figure 2. Because the user is expecting
the actual format that was downloaded or stored. The
filtered image contains only image data, which is cre-
ated from WebP image as the output image pixels are
generated by decoding temporary WebP image data,
resulting in a safe image.
3.2 Stegoslayer Browser Extension
The attackers exploit web browser vulnerabilities to
evade the detection system using stegomalware. The
attacker embeds the decoder or other malicious action
code snippets written in JavaScript into the HTML
file, which is masked as images. The proposed
Stegoslayer browser extension checks for polyglots
and filters steganographically hidden data from im-
ages within a web page, as shown in Figure 3. The
Stegoslayer browser extension consists of three sub-
modules: (i) Header Validation, (ii) Image Conver-
sion, and (iii) Delay Insertion.
Stegoslayer: A Robust Browser-Integrated Approach for Thwarting Stegomalware
603
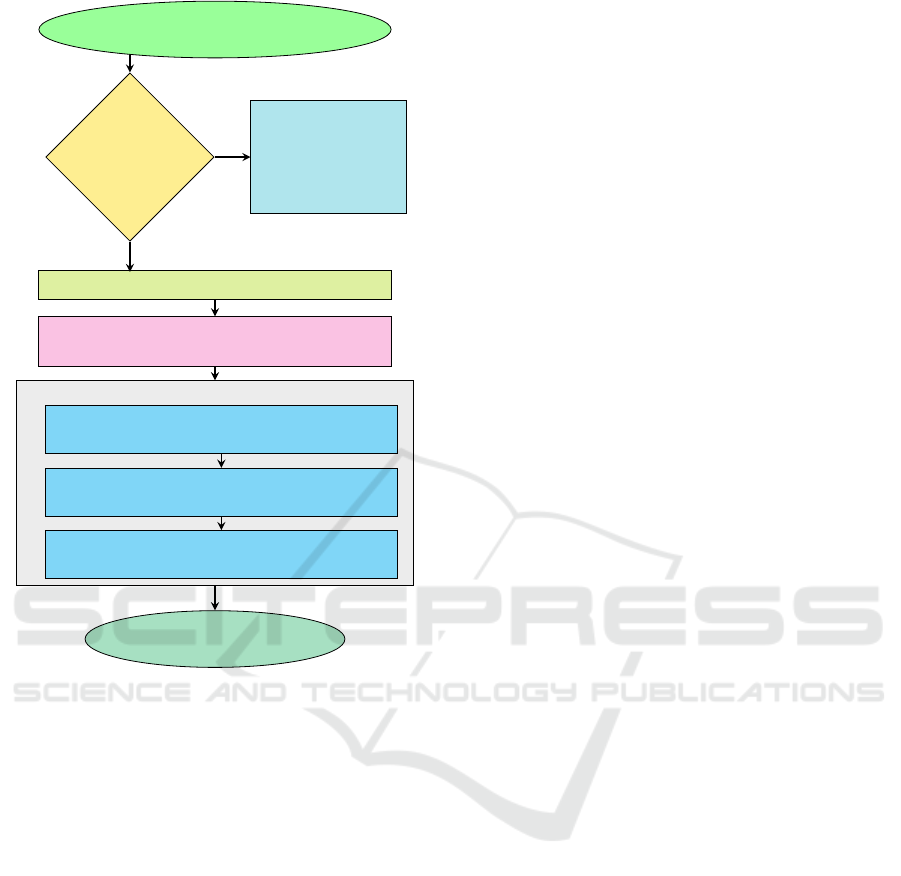
Validate Header
Header Mis-match
(warning: might
be polyglot file)
No
Loading of HTML is finished
Insert Delay
Yes
List all images
i.e., object with ’img’ tag
Convert each image to WebP
Create base64 encoded blob
object using original source
New WebP blob object is created using
blob object created in the previous step
Create URL for new WebP blob
object and replace original source
All images processed
Figure 3: Flowchart of Stegoslayer Browser Extension.
i) Header Validation
Attackers include malicious content in the header
or represent malicious content as an HTML file to
evade detection systems and carry out attacks. For
example, the Stegosploit (Shah, 2015) tool hides
the malicious image (JPEG/PNG) in an HTML
file to avoid detection. The polyglot contains
headers of multiple file types, discussed in Sec-
tion 1. To prevent such attacks, header validation
is incorporated as part of the Stegoslayer. During
header validation, Stegoslayer matches the header
tag of the HTML file to ensure that malicious con-
tent or files are not embedded within the HTML
file.
ii) Image Conversion
To prevent stegomalware attacks, the browser
extension clean the images present on the web
pages. As soon as the web page is loaded, the
browser extension lists all images in the webpage
by iterating through elements with an “img”
tag. If the image data is embedded within the
webpage, the browser store it as a Blob object. In
order to clean the image, initially, the Blob object
of the image is converted to base64 encoded data.
Further, a new blank canvas element is created,
and the original image is drawn on the new canvas
using base64 encoded data. The new canvas is
used to create a new blob object that contains
WebP-encoded image data. The URL for the new
image is created and the image source is replaced
by it.
iii) Delay Insertion
The webpage loading is completed before
Stegoslayer processing, potentially causing harm
to the system as browsers load the image before
cleaning or filtering it. To prevent malware trig-
gers before Stegoslayer’s processing, a delay is
introduced during webpage loading.
While regenerating entire images using “base64”-
encoded data of the original image, metadata is re-
moved from the header section and data hidden within
the pixels of the image body is lost. If the image
already contains a decoder embedded in its header,
it will not function because a new header is created
when generating a new WebP blob object. An at-
tacker’s attempt to extract data from the image us-
ing another script on the webpage will fail or result in
wrong data. Because the pixels are regenerated with-
out any hidden data. This leads to the failure of ste-
gomalware execution.
4 EXPERIMENTS AND RESULTS
4.1 Experimental Setup
We evaluated performance of the proposed scheme
using multiple steganographic techniques such as F5
(Westfeld, 2001), outguess (Provos, 2001) and open-
stego (Vaidya, 2024) by hiding malware inside JPEG
and PNG files. We have used thousand PNG files
ffhq-dataset (Karras et al., 2018) from the Nvidia
Research project and ALASKA2 (Addison Howard,
2020) dataset for JPEG cover images five hundred
each. We collected the malware dataset from the
VirusShare (VirusShare, 2024) repository. We also
created a stegomalware dataset by embedding cover
images of the ALASKA2 dataset with malware using
F5 and outguessed steganographic techniques. We
embedded PNG files with malware using the open-
stego tool. Moreover, data is embedded in the multi-
ple segments of JPEG images to test effectiveness.
We conducted an assessment of our scheme using
three different approaches. Initially, we evaluated the
effectiveness of extracting malware from stegomal-
SECRYPT 2025 - 22nd International Conference on Security and Cryptography
604
ware images generated by Stegoslayer. In addition,
the quality of images generated by the proposed tech-
nique Stegoslayer is assessed. Finally, we tested the
effectiveness of our prevention method in real-world
scenarios to determine its performance under realistic
conditions. The system configuration given in Table
1 is employed for the final test using a browser ex-
tension. We used the recent stegomalware prevention
tool Stegowiper to verify and compare our technique.
Table 1: Experimental Setup.
Parameters Specification
OS KALI 2024.1 (VM)
Memory 4 GB DDR4 2400MHz
Processor Intel(R) Core(TM) i7-8565U
CPU @ 1.99 GHz
Core 2
Browser Firefox 115.7.0 esr (64-bit)
4.2 Results and Discussion
4.2.1 Sanitization Effectiveness Analysis
The created stegomalware images were passed to
the steganographic retrieval algorithm before and af-
ter applying Stegoslayer to recover the hidden con-
tent. Before passing through the Stegoslayer, the
steganographic tool recovered the malicious data suc-
cessfully. However, after passing the stegomalware
images through the Stegoslayer, the steganographic
tools either fail to recover the data or some garbage
data is recovered, entirely different from hidden data.
The Stegoslayer eliminates the hidden content during
the image reconstruction. After passing the stego-
malwares through the stegowiper, the steganographic
tools retrieve false data. However, the stegowiper em-
ploys the Gaussian noise distribution. Therefore, the
attacker can develop a steganographic algorithm to
hide and retrieve data in unaltered bits by Gaussian
noise distribution.
4.2.2 Quality Analysis
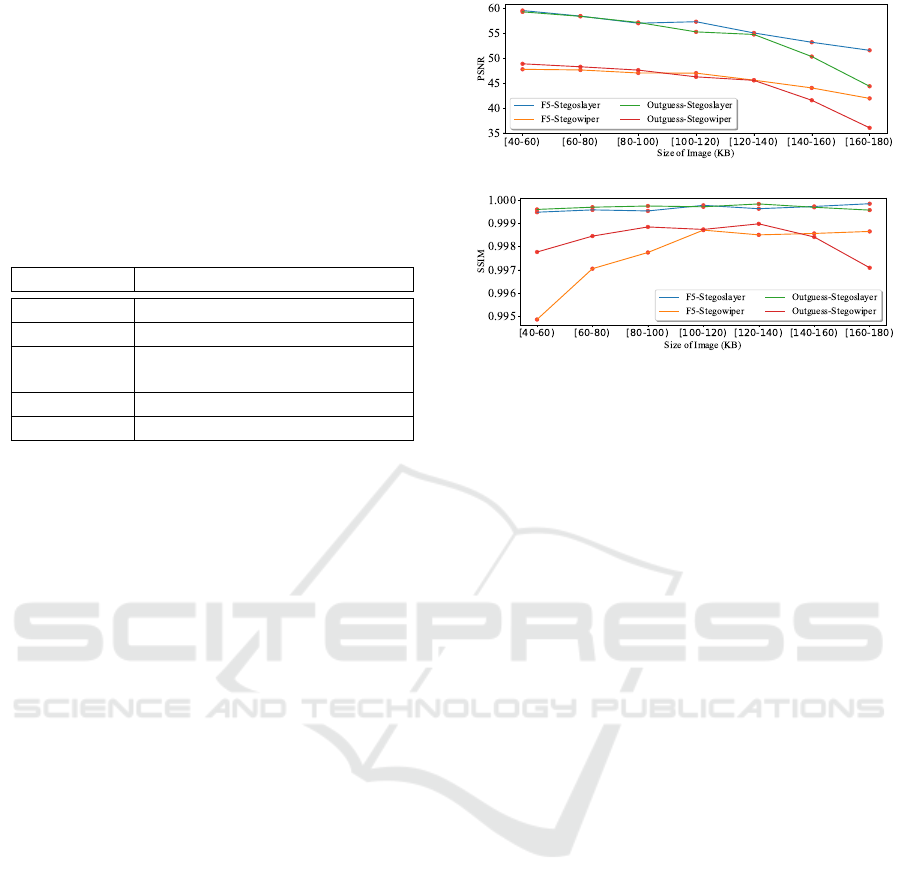
To compare the quality of images of output images
from Stegoslayer and Stegowiper, we employed the
quality matric, Peak Signal to Noise Ratio (PSNR)
and Structural Similarity Index Measure (SSIM).
PSNR measures the ratio of the peak signal power of
an original image compared to the power of the fil-
tered image in decibels. The higher PSNR indicates a
better quality of the image. SSIM measures the struc-
tural similarity between an original and reconstructed
image. SSIM value closer to 1 indicates higher struc-
tural similarity and better quality.
Figure 4: PSNR output image.
Figure 5: SSIM output image.
The result indicates that Stegoslayer maintains higher
PSNR values than Stegowiper while processing the
images embedded using F5 and outguess stegano-
graphic algorithms, as shown in Figure 4 Stegoslayer
achieves 20% higher PSNR value over stegowiper.
Figure 5 show our method maintains an SSIM value
closer to 1 than stegowiper, indicating better image
quality.
4.2.3 Real Time Evaluation
We simulated a stegosploit attack using JGEP and
PNG images, in which the decoder is fused with an
image (image + HTML + JavaScript) in a single file
IMAJS. IMAJS is an image (JPEG/PNG) file with
“.HTML” as file extension, HTML code and decoder
JavaScript inserted inside the APP0 segment of JPEG
image or tEXt chunk in PNG image. When this web-
page is accessed by the user, the malware gets de-
coded and executed by the decoder javascript program
in the HTML file of the webpage. Another attack is
simulated via a browser where the decoder code is
in an HTML file, and malware data is embedded in-
side the image file. We also tested the performance
of Stegoslayer on frequently used websites, such as
Google, Wikipedia, Linkedin, etc., it has been eval-
uated for delays in processing time with the size of
images.
We enabled the Stegoslayer browser extension and
executed the attack. The browser extension can ef-
fectively prevent the attack by removing the malware
payload hidden in the image pixels by regenerating
the pixels before the decoder JavaScript program ac-
cesses it. However, due to the regeneration of the im-
age in Webp, the decoder cannot extract data as its
image structure is changed due to a change in for-
mat. Stegowiper ignores if the image is embedded in a
webpage (HTML file) or it is renamed with an exten-
Stegoslayer: A Robust Browser-Integrated Approach for Thwarting Stegomalware
605
sion such as HTML (as in stegosploit), .txt, .pdf, etc.
However, stegowiper filters the content based on the
HTTP content type and applies the prevention tech-
nique if the content type is an image. Thus, the Ste-
gowiper can not prevent stegosploit attacks due to the
attacker evading the image in the HTML file. Our
browser extension will remove images in webpages if
they are embedded inside the webpage or images re-
named as different file types and used as the image
source in the webpage.
To analyse user convenience we measured the pro-
cessing time or delay caused by the extension on most
used sites such as Google, Wikipedia, Linkedin, etc.,
We observed that, the delay caused by the browser
extension for processing the images with size ≤ 1KB
is less than 1ms. If the image size is around 100KB,
the time required is a maximum of 100ms, and for a
1MB image, the maximum delay is 300ms. The tim-
ing analysis is tabulated in Table 2 (time required to
process image in webpage by extension) We observe
that most frequently used standard websites use im-
ages of size ≤ 50KB for better performance or to re-
duce the loading time.
Table 2: Size of image vs Delay.
Size of Image Delay
< 1 KB < 1 ms
≈ 100 KB ≈ 100 ms
≈ 1 MB ≈ 300 ms
5 CONCLUSION
Digitalization has significantly increased the attack
surface, making robust cybersecurity measures more
critical than ever to protect sensitive information and
ensure system integrity. As cyber-attacks become
more sophisticated, cyber security issues pose signif-
icant threats to individuals and organizations. The
sophistication includes packing malware or potential
threats within images or media files using steganog-
raphy and polyglot methods, making detection and
prevention more challenging for traditional security
measures. Because browsers are widely used for in-
ternet access, they are the prime vector for attackers to
exploit vulnerabilities, execute malicious scripts, and
deliver hidden payloads through techniques such as
steganography and polyglot files. A robust browser-
integrated approach for preventing Stego-malware
was implemented and tested in real-time. The im-
age reconstruction removes the data hidden inside
the header sections and regenerates the pixels. The
experimental results indicate that the Stegoslayer is
more effective and reliable compared to stegomal-
ware prevention techniques such as stegowiper. The
Stegoslayer is able to prevent more sophisticated at-
tacks than stegowiper without losing the image qual-
ity. The Stegoslayer achieves 20% higher PSNR value
over the stegowiper images indicating improved qual-
ity.
REFERENCES
Addison Howard, GIBOULOT Quentin, P. R. C. W. C.
(2020). Alaska2 image steganalysis.
Albertini, A. (2015). Funky file formats. The International
Journal of PoC||GTFo7.
Alfonso Mu
˜
noz, D. M. U. (2022). stegowiper: powerful
and flexible active attack for disrupting stegomalware.
https://github.com/mindcrypt/stegowiper.git.
Caviglione, L. and Mazurczyk, W. (2022). Never mind the
malware, here’s the stegomalware. IEEE Security &
Privacy, 20(5):101–106.
Cohen, A., Nissim, N., and Elovici, Y. (2020). Maljpeg:
Machine learning based solution for the detection of
malicious jpeg images. IEEE Access, 8:19997–20011.
Cyble (2022). Stegomalware identifying possible attack
vectors. Accessed: 2024-04-28.
Developers, P. (2025). Pillow (PIL Fork) Documentation.
Accessed: 2025-01-06.
Guerreiro, M. (2024). DocBleach - an advanced content dis-
arm and reconstruction software. https://github.com/
docbleach/DocBleach. Accessed: 2024-12-17.
Inc., G. (2025). WebP: Lossless and Lossy Image Compres-
sion. Accessed: 2025-01-06.
Karras, T., Laine, S., and Aila, T. (2018). Flickr-
faces-hq (ffhq) dataset. https://github.com/NVlabs/
ffhq-dataset.
Petrosyan, A. (2024). Internet and social media users in the
world 2024. Accessed: 2025-01-07.
Provos, N. (2001). OutGuess steganography tool. https:
//www.outguess.org/. Accessed: 2024-07-04.
Shah, S. (2015). Stegosploit: Weaponized Polyglots
as Browser Exploits. The International Journal of
PoC||GTFo8.
Vaidya, S. (2024). OpenStego - free steganography soft-
ware. https://www.openstego.com. Accessed: 2024-
07-04.
VirusShare (2024). https://virusshare.com. Accessed:
2024-06-24.
Westfeld, A. (2001). F5—a steganographic algorithm. In
Moskowitz, I. S., editor, Information Hiding, pages
289–302, Berlin, Heidelberg. Springer Berlin Heidel-
berg.
Zuppelli, M., Manco, G., Caviglione, L., and Guarascio,
M. (2021). Sanitization of images containing stego-
malware via machine learning approaches. In Italian
Conference on Cybersecurity.
SECRYPT 2025 - 22nd International Conference on Security and Cryptography
606
