
Towards Interoperable Data Spaces: Comparative Analysis of Data
Space Implementations Between Japan and Europe
Shun Ishihara
a
and Taka Matsutsuka
b
Fujitsu Limited, Kawasaki, Kanagawa 211-8588, Japan
Keywords:
Trust, Analysis, Data Space, Interoperability, DATA-EX, Catena-X.
Abstract:
Data spaces are evolving rapidly. In Europe, the concept of data spaces, which emphasises the importance
of trust, sovereignty, and interoperability, is being implemented as a platform such as Catena-X. Meanwhile,
Japan has been developing its approach to data sharing, in line with global trends but also to address unique
domestic challenges, resulting a platform such as DATA-EX. Achieving interoperability between European
and Japanese data spaces remains a critical challenge due to the differences created by these parallel advances.
Although interoperability between data spaces has several aspects, compatibility of trust in the participating
entities and the data exchanged is a significant aspect due to its influence on business. This paper undertakes a
comparative analysis of DATA-EX and Catena-X while focusing on aspect of trust, to explore the challenges
and opportunities for achieving interoperability between Japanese and European data spaces. By examining
common data exchange processes, key objects such as datasets, and specific evaluation criteria, the study
identifies gaps, challenges, and proposes actionable solutions such as inter-exchangeable topology. Through
this analysis, the paper aims to contribute to the ongoing discourse on global data interoperability.
1 INTRODUCTION
The rapid evolution of data spaces is transforming
the landscape of secure and interoperable data sharing
across industries and regions. In Europe, the concept
of data spaces, supported by initiatives such as the
European Data Strategy, emphasises the importance
of trust, sovereignty, and interoperability. Mean-
while, Japan has been developing its approach to data
sharing, in line with global trends but also address-
ing unique domestic challenges. Despite these paral-
lel advancements, achieving interoperability between
European and Japanese data spaces remains a critical
challenge due to differences in governance, technol-
ogy standards, and authentication frameworks. Inter-
operability between data spaces has various aspects
such as compatibility of technologies like connectors,
compatibility of objects handled in data spaces, and
compatibility of trust on participating entities and the
data exchanged. Compatibility of trust is a signifi-
cant issue among these aspects, because actual data
exchange is never established without trustworthiness
between participants.
a
https://orcid.org/0009-0005-4584-2695
b
https://orcid.org/0000-0002-2673-6708
This paper undertakes a comparative analysis of
DATA-EX and Catena-X to explore the challenges
and opportunities for achieving interoperability be-
tween Japanese and European data spaces. The anal-
ysis is focusing on trust. By examining common data
exchange processes, key objects such as participants,
datasets, and data catalogs, and specific criteria for
evaluation, the study identifies gaps and proposes ac-
tionable solutions. The findings are based on a thor-
ough analysis of relevant documentation, highlighting
areas for alignment and improvement.
Through this analysis, the paper aims to contribute
to the ongoing discourse on global data interoperabil-
ity. It proposes an inter-exchangeable topology that
bridges regional differences while addressing com-
mon challenges.
The rest of the paper is structured as follows. Sec-
tion 2 reviews the development of data spaces in Eu-
rope and Japan, and examines the role of trust anchors
and interoperability challenges. Section 3 describes
the analysis method, including key evaluation crite-
ria and data sources. Section 4 presents the analy-
sis results, comparing participants, devices, datasets,
and other key elements of the two platforms. Sec-
tion 5 discusses identified gaps, proposes an inter-
exchangeable topology, and addresses specific chal-
318
Ishihara, S., Matsutsuka and T.
Towards Interoperable Data Spaces: Comparative Analysis of Data Space Implementations Between Japan and Europe.
DOI: 10.5220/0013460600003967
In Proceedings of the 14th International Conference on Data Science, Technology and Applications (DATA 2025), pages 318-328
ISBN: 978-989-758-758-0; ISSN: 2184-285X
Copyright © 2025 by Paper published under CC license (CC BY-NC-ND 4.0)

lenges. Section 6 reviews related works, and Section
7 concludes with findings and future directions.
2 BACKGROUND
In recent years, the importance of the data economy
has been steadily increasing, with data spaces evolv-
ing through unique approaches in different regions
and countries. Data spaces refer to infrastructures or
frameworks that enable the sharing and integration of
data, allowing participating organisations and individ-
uals to maintain data sovereignty while securely shar-
ing information. This section provides an overview of
the development of data spaces in Europe and Japan,
highlights their characteristics, and identifies chal-
lenges for the future.
2.1 Development of Data Spaces in
Europe
Europe has been accelerating its efforts to maximise
the potential of the data economy. Central to these
efforts are the European Data Strategy
1
and the con-
cept of data sovereignty. The European Data Strat-
egy aims to foster data sharing within and beyond
the region, positioning Europe as a global leader in
the data economy. This strategy is rooted in the be-
lief that data should be managed and utilised fairly,
without being disproportionately controlled by a few
companies or nations. Data sovereignty refers to the
principle that entities owning and managing data have
the exclusive right to determine its usage. For ex-
ample, this includes the control over the data, even
if the data is shared with other parties. Europe has
reinforced this principle through stringent data pro-
tection regulations such as General Data Protection
Regulation (GDPR), ensuring that individuals and or-
ganisations can safeguard their rights while contribut-
ing to the data economy. Initiatives like Interna-
tional Data Spaces Association (IDSA) and Gaia-X
exemplify Europe’s approach to data spaces. IDSA
focuses on creating secure and standardised frame-
works for data sharing across various industries, en-
suring that data sovereignty is maintained. Mean-
while, Gaia-X, a European initiative for cloud infras-
tructure and data sharing, aims to establish an interop-
erable ecosystem where data and services can be se-
curely exchanged while adhering to European values
such as transparency and privacy. Together, these ini-
1
https://commission.europa.eu/strategy-and-policy/
priorities-2019-2024/europe-fit-digital-age/
european-data-strategy en
tiatives highlight Europe’s commitment to fostering a
trusted data economy by addressing technical, legal,
and ethical challenges inherent in cross-border data
exchanges. With this multipronged strategy, Europe
seeks to establish itself as a leader in the development
of a robust, scalable, and ethical data ecosystem.
2.2 Development of Data Spaces in
Japan
Similarly, Japan has pursued its own approach to de-
veloping data spaces, centerd on the concepts of So-
ciety 5.0
2
and Data Free Flow with Trust (DFFT)
3
.
Society 5.0 is a national strategy that envisions a
super-smart society where cyberspace and physical
space are seamlessly integrated to address societal
challenges through data utilisation. Within this con-
cept, DFFT emphasises the importance of trust in data
flow, enabling secure data sharing across national and
organisational boundaries. The second phase of the
Strategic Innovation Promotion Program (SIP) and its
subsequent evolution into DATA-EX (Koshizuka and
Mano, 2022) have constituted significant advances in
Japan’s data space endeavours, spearheaded by gov-
ernmental initiatives. In the context of SIP, a con-
nector called Connector Architecture for Decentral-
ized Data Exchange (CADDE)
4
has been developed
with the objective of enabling secure and efficient
data sharing between organisations. This founda-
tional technology constituted the basis for the subse-
quent establishment of the DATA-EX initiative, which
was launched within Data Society Alliance (DSA).
The objective of this initiative is to expand the ca-
pabilities of CADDE into a broader data exchange
infrastructure, thereby promoting interoperability and
trust in data sharing across sectors. Another notable
effort is the Ouranos Ecosystem (Ministry of Econ-
omy, Trade and Industry, 2023) project, which began
in 2022 under the leadership of Information Process-
ing Agency’s Digital Architecture Design Center (IPA
DADC). The project’s objective is to enhance battery
traceability within the automotive manufacturing sup-
ply chain as well as ensure compliance with Euro-
pean battery regulations. This addresses the critical
need for transparency and accountability in tracking
battery production and usage. In 2023, the imple-
mentation phase was completed, establishing a tech-
nical foundation for real-world application. By 2024,
the operational body, Automotive and Battery Trace-
ability Center Association (ABtC), was established,
2
https://www8.cao.go.jp/cstp/english/society5 0/
3
https://www.digital.go.jp/en/policies/dfft
4
https://sip-cyber-x.jp/en/
Towards Interoperable Data Spaces: Comparative Analysis of Data Space Implementations Between Japan and Europe
319

marking the transition to full-scale operation and con-
tributing to the advancement of sustainable supply
chain management.
2.3 The Importance of Trust Anchors in
Data Spaces
Trust anchors are critical for ensuring the security, au-
thenticity, and reliability of data spaces, enabling par-
ticipants to confidently share data while maintaining
sovereignty. Key technologies include digital identity
systems like decentralised identifiers (DIDs), which
allow entities to manage their own digital identities
securely, and verifiable credentials (VCs), which pro-
vide proof of attributes or certifications without ex-
posing unnecessary information. Governance frame-
works, like those from IDSA, establish common rules
for interoperability and trust. Together, these tech-
nologies and standards build a secure and reliable
foundation, fostering participation and unlocking the
full potential of global data spaces.
2.4 Challenges of Interoperability
Between Japan and Europe
Currently, data spaces in Japan and Europe are built
on different technological bases, making interoper-
ability challenging. In Europe, standardisation of data
space and trust is being pursued in IDSA and Gaia-X
respectively. In Japan, meanwhile, the DATA-EX and
Ouranos Ecosystem are pursuing their own individ-
ual standardisation agendas. However, the need for
interoperability between these data spaces is becom-
ing increasingly critical, particularly for addressing
global issues such as carbon footprint transparency
and international supply chain management. Inter-
operability between data spaces has various aspects
such as compatibility of technologies which means
connectors or related components can connect each
other seamlessly beyond a data space, compatibility
of objects which means expression of objects han-
dled in data spaces can be interpreted uniquely, and
compatibility of trust which means trustworthiness of
participating entities and the data exchanged is simi-
lar among data spaces. A significant challenge lies in
the compatibility of trust. Without robust mechanisms
to guarantee trust, resistance to data sharing may in-
crease, stalling the flow of data and hindering the data
economy. Therefore, creating systems that integrate
or harmonise the technological foundations of Japan
and Europe is essential. Addressing this challenge
will pave the way for a sustainable and interconnected
data economy in the future.
3 ANALYSIS METHOD
As a first step towards solving the challenge men-
tioned above, we undertake a comparative analysis of
two prominent data space platforms in Japan and Eu-
rope from a trust perspective. We selected DATA-EX
in Japan and Catena-X in Europe as the representa-
tive data space platforms due to substantial number
of analysable documents and the past maturity evalu-
ation (Dam et al., 2023) (Bacco et al., 2024).
In this section, we examine a common data ex-
change process, key objects such as participants,
datasets, and data catalogs, and specific criteria for
evaluation, and available documents used for analy-
sis.
3.1 Common Data Exchange Process
First, we decided on a common data exchange process
to make a fair comparison between the two platforms.
We researched principal whitepapers written in Japan
and Europe to compare regional differences.
A whitepaper from Data Society Alliance (DSA,
2022) described processes, functions and elements
when data providers and data consumers who were
in different organisations or departments plan to han-
dle data across existing systems or applications. The
paper attempted to define the data exchange process.
Six phases below were extracted as the data exchange
process in the paper.
• Planning: A data provider prepares the data to be
transferred. A data consumer designs a new ser-
vice or application to use the data and defines data
requirements.
• Discovery: The data provider describes and pub-
lishes the catalog of the data. The data consumer
searches for the data to meet requirements through
a catalog search service.
• Contract: The data provider and the data con-
sumer negotiate terms and conditions of the data
exchange and conclude a contract.
• Transfer: The data provider makes the data avail-
able in an accessible location. The data consumer
obtains the data from the provider and uses it
within scope of the contract.
• Payment: The data consumer pays for the data
based on the contract.
• Verification: The data provider and the data con-
sumer verify the status of the contract fulfilment
(e.g., progress of data delivery or payment).
A whitepaper from International Data Spaces As-
sociation (IDSA, 2023) defined a reference architec-
ture model to generalise concepts, functionality, and
DATA 2025 - 14th International Conference on Data Science, Technology and Applications
320

overall processes for creating a secure network of
trusted data. Their reference architecture model de-
fined five layers: business layer, functional layer, in-
formation layer, process layer, and system layer. The
process layer defined five phases below as the inter-
actions that take place between the different com-
ponents (e.g., connectors) of the international data
spaces.
1. Onboarding, i.e. what to do to
be granted access to the International Data
Spaces as a Data Provider or Data Consumer.
2. Data Offering, i.e. offering data or
searching for a suitable data.
3. Contract Negotiation, i.e. accept data
offers by negotiating the usage policies.
4. Exchanging Data, i.e. transfer data be-
tween IDS Participants.
5. Publishing and using Data Apps, i.e. in-
teracting with an IDS App Store or using IDS
Data Apps.
There are some overlaps between the phases of
DSA and IDSA. Table 1 shows the correspondence
between DSA and IDSA phases.
Table 1: Correspondence between DSA and IDSA phases.
DSA IDSA
- Onboarding
Planning -
Discovery Data Offering
Contract Contract Negotiation
Transfer Exchanging Data
Publishing and using Data Apps
Payment -
Verification -
Considering this correspondence, we extract the
onboarding phase from IDSA’s process and all six
phases from the DSA’s process as a common data ex-
change process.
3.2 Target Objects
Based on the common data exchange process, we
identified objects which are generated in a data ex-
change as a target for our analysis. (The term “object”
here means a digital entity that requires some kind of
trust.) As a result, six objects shown in Table 2 were
identified.
In the onboarding phase, a data space operating
company validates an applicant organisation and then
creates a user account. We defined this account as
a “Participant” object. Following the acquisition of
the user account, the applicant organisation prepares
Table 2: Generated objects in the common data exchange
process.
Phase Generated object
Onboarding Participant (data consumer or
provider account)
Device (server and endpoint on
which connector works)
Planning Dataset
Data catalog
Discovery - (only refer data catalogs)
Contract Contract
Transfer Sending & Receiving Log
Payment
Verification - (only refer previously generated
log)
servers and endpoints on which the connectors op-
erate. We defined these servers and endpoints as
“Device” objects. During the planning phase, a data
provider prepares datasets to provide and data cata-
logs to advertise their datasets. We defined these two
as “Dataset” and “Data catalog” objects. In the con-
tract phase, the data provider and consumer conclude
a contract about a data exchange. A record of the con-
tract is stored as a paper or a digital data. We defined
these records as “Contract” objects. In the transfer
and payment phases, actual data and money are trans-
ferred in accordance with the contract. The records of
these transactions are stored as a digital log to prove
fulfilment of the contract. We defined these logs as
“Sending & Receiving Log” objects.
3.3 Analysis Criteria
We have developed an analysis criteria on trust based
on six analysis target objects.
In order for an object to be considered trustworthy,
trust needs to be satisfied at two steps: when gener-
ated and when verified. The first step is to ensure trust
of the object when it is generated. In the case of the
participant object, an applicant is validated by a sys-
tem administrator in a certain aspect (e.g., existence,
eligibility, agreement to rules). The second step is to
verify whether trust is ensured during the operation
of the data space. In the case of the participant object,
after the validation, the system administrator issues a
credential (e.g., user id and password), and the system
verifies the credential on login. Considering these two
steps, we created two analysis perspectives.
• p1) How to ensure trust in the object generation
• p2) How to verify trust in operation
The final analysis criteria using identified objects
and analysis perspectives is shown in Table 3.
Towards Interoperable Data Spaces: Comparative Analysis of Data Space Implementations Between Japan and Europe
321
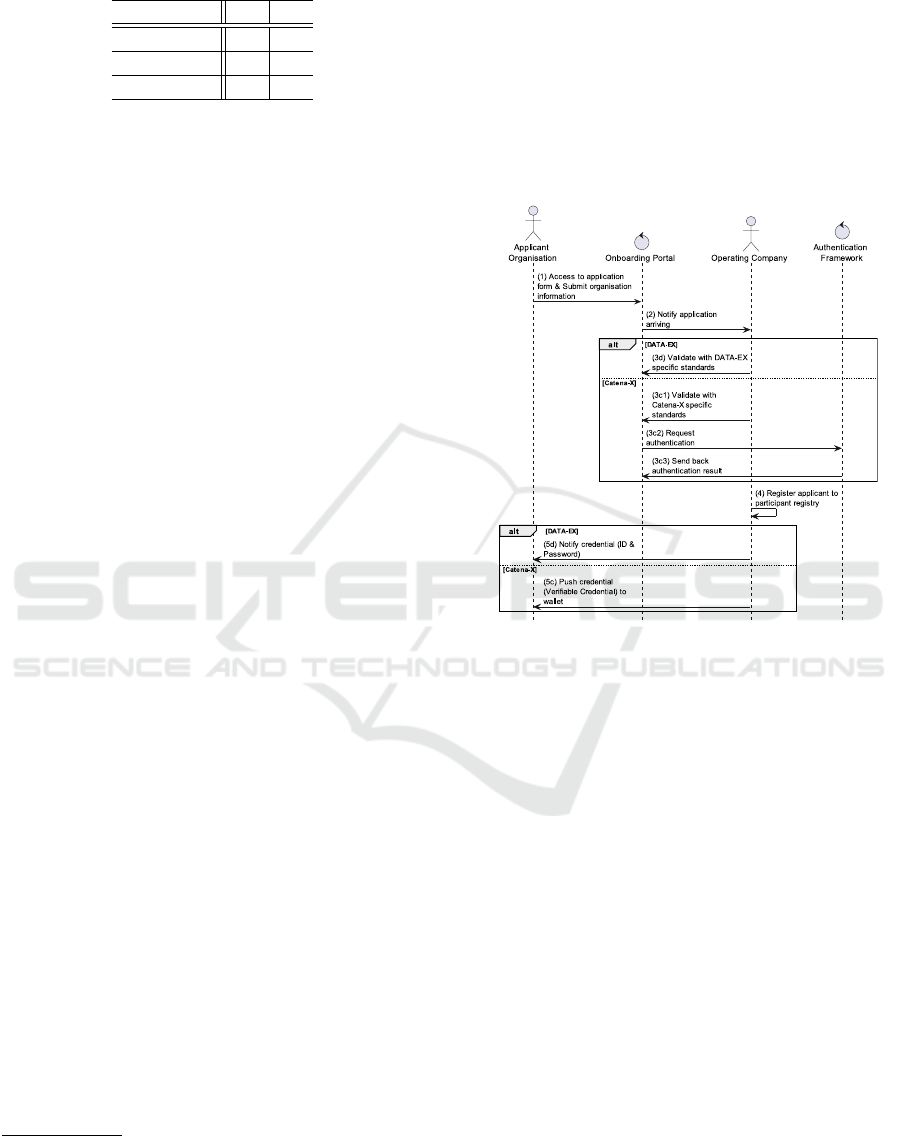
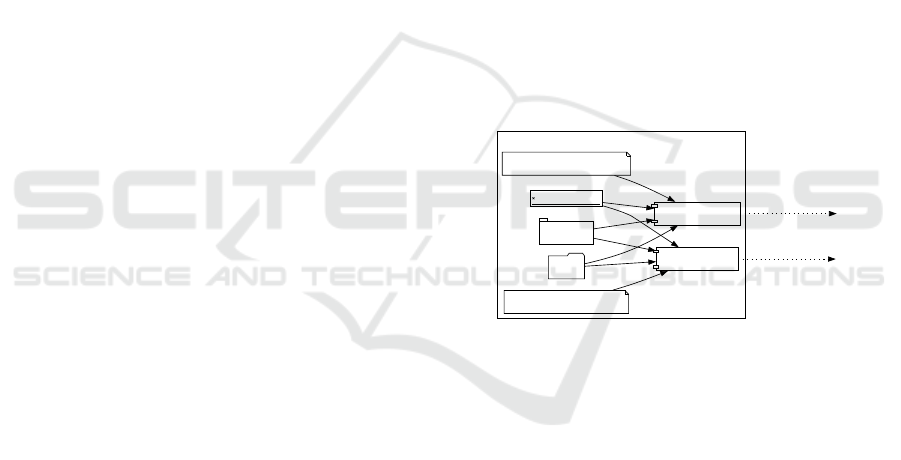
Table 3: Analysis criteria.
p1 p2
Participant
Device
. . .
The horizontal axis represents analysis perspec-
tives, while the vertical axis represents identified ob-
jects. Employing these criteria facilitates comprehen-
sive analysis.
3.4 Documents Used for Analysis
Finally, we selected the technical documents to be
used in the analysis.
With regard to DATA-EX, we selected technical
documents in both the industrial data linkage infras-
tructure
5
and CADDE documents
6
. Digital Agency is
facilitating its implementation as industrial data link-
age infrastructure and publishing its basic design doc-
uments. Note that some documents are not included
in the industrial data linkage infrastructure’s publica-
tion but in the CADDE publication because indus-
trial data linkage infrastructure is an enhancement of
CADDE.
With regard to Catena-X, we selected technical
documents in both the technical standards (Catena-
X, 2024) and deliverables of the Eclipse Tractus-X
project
7
. Catena-X Automotive Network e.V. is pub-
lishing technical standards, but it doesn’t cover all
specifications of Catena-X. Eclipse Tractus-X is an
open-source project to develop reference implementa-
tions of Catena-X and providing some technical docu-
ments (not comprehensive) and source code. The ver-
sion of the selected documents was adhered to CX-
Jupiter release as Catena-X is under continuous de-
velopment.
4 ANALYSIS RESULT
Summary of the analysis result is shown in Table 4.
In this summary, function or method of each data
space is described. N/A means that there is no func-
tion or method. There is N/A in the dataset, data
catalog, and contract, because the trust of these ob-
jects should be ensured by the participant in princi-
ple. Therefore, described function or method of these
objects is not comprehensive solution but solution to
5
https://www.digital.go.jp/en/policies/
industrial-data-integration
6
https://github.com/CADDE-sip
7
https://github.com/eclipse-tractusx
complement the trust ensured by the participant. De-
tails of the analysis results for each object are shown
below.
4.1 Participant
About p1, both platforms validate the applicant or-
ganisation through an onboarding portal. A validation
process of each platform is shown in Figure 1.
Figure 1: Validation process of the participant.
In both platforms, the applicant organisation sub-
mits organization information to the operating com-
pany through onboarding portal, but there are two dif-
ferences.
The first difference is the validation method and
standard (illustrated in Figure 1 as 3d,3c1,3c2,3c3).
The operating company in both platforms validates
similarly submitted information, but the validation
standards are not the same. In addition, partici-
pant authentication is performed by an authentica-
tion framework in Catena-X. This framework is called
as Gaia-X Digital Clearing House (Sprenger, 2024),
which automatically validates an organisation from
different perspectives (e.g., notarisation check with
LEI code). This framework can be used commonly
by multiple data spaces. By using this framework,
one data space can obtain compatibility about trust of
the participant with another data space.
The second difference is a credential which the ap-
plicant organisation receives (illustrated in Figure 1
as 5d,5c). In DATA-EX, a participant registry is an
identity provider, or IdP, so the applicant organisation
is registered in form of an account and receives the
id and password of the account as a credential. In
DATA 2025 - 14th International Conference on Data Science, Technology and Applications
322
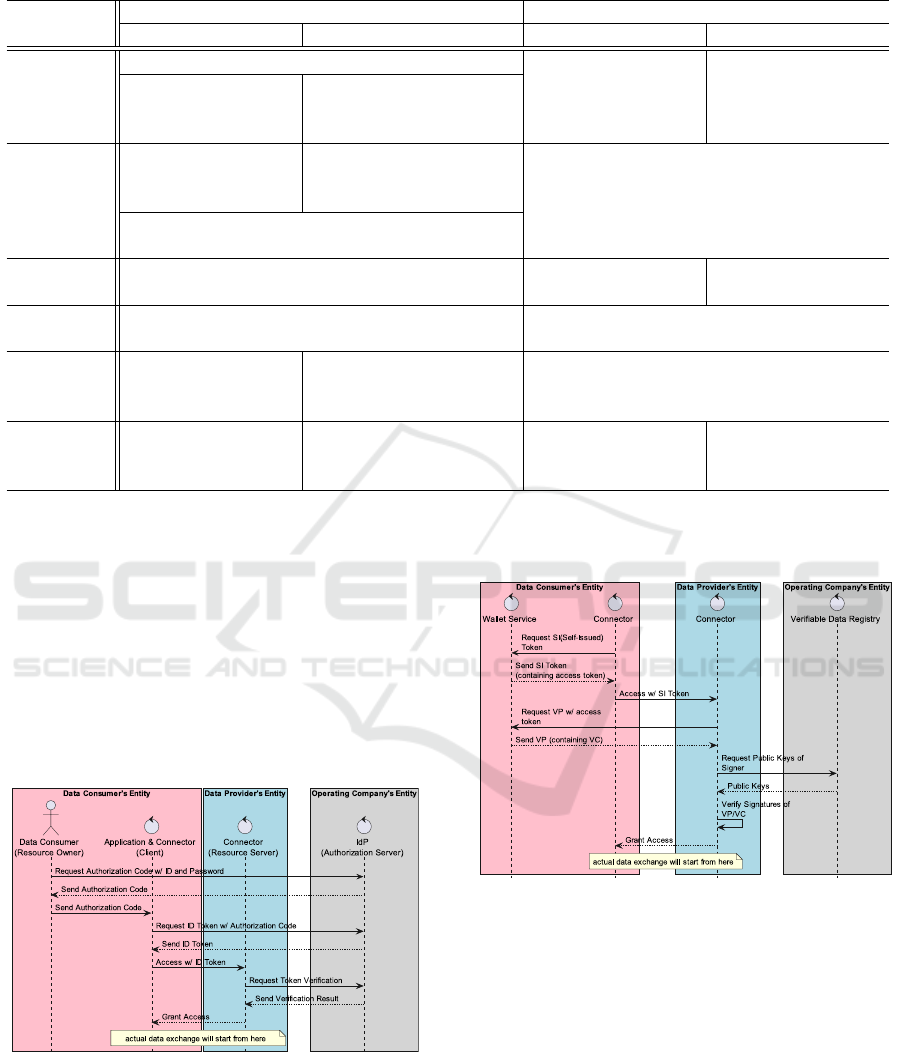
Table 4: Summary of the analysis result.
p1) How to ensure trust in the object generation p2) How to verify trust in operation
DATA-EX Catena-X DATA-EX Catena-X
Participant
Onboarding Portal JWT (issued via
OIDC protocol &
presented via
original protocol)
VC (issued &
presented via
original protocol)
Validation with
DATA-EX specific
standards
Validation with
Catena-X specific
standards
Device
Validation with
DATA-EX specific
standards
Validation with
Catena-X specific
standards
Connector endpoint resolver and
general HTTPS verification based on
X.509 certificate
Validation with CA’s common standards
(e.g., Extended Validation)
Dataset Data model & vocabulary repository Signable data pack-
age
N/A
Data cata-
log
Modified DCAT v2 format catalog cre-
ation function
N/A
Contract N/A Connector’s con-
tract negotiation
API
N/A (External contract brokering ser-
vice is recommended, and connector
can work with it)
Sending &
Receiving
Log
Centralized log
management ser-
vice
N/A (local log) Centralized log
management ser-
vice
N/A (local log)
Catena-X, on the other hand, the participant registry
is a verifiable data registry (VDR), so the applicant
organisation is registered in form of a DID document
which holds a public key and receives a verifiable cre-
dential signed by a private key of the operating com-
pany.
The difference in the credential affects function or
method on p2. In DATA-EX, the credential is handled
via the OpenID Connect (OIDC) protocol shown in
Figure 2.
Figure 2: Verification process of the participant in DATA-
EX.
On OIDC protocol, the verification is performed
by the authorisation server managed by the operating
company. In Catena-X, on the other hand, the creden-
tial is handled via the Decentralized Claims Protocol
(DCP) (Andrea et al., 2024), shown in Figure 3.
Figure 3: Verification process of the participant in Catena-
X.
On DCP, the verification is performed by the data
provider, who is a verifier. The operating company
only provides an issuer’s public key through the VDR.
The role of the operating company in the verification
is a major difference.
4.2 Device
As a first step on p1, both platforms validate the de-
vice against platform specific standards and register
device’s endpoint into a connector endpoint resolver.
The connector endpoint resolver provides the con-
Towards Interoperable Data Spaces: Comparative Analysis of Data Space Implementations Between Japan and Europe
323

nector endpoint to the data consumer according to
given search keys (e.g. identifiers representing the
data provider or its connector). The available search
keys are different on each platform, but the endpoint
provided by the resolver has assurance that has been
validated by the operating company.
As a second step on p1, external Certification Au-
thority (CA) validates the device against common
standards (e.g., Extended Validation) and issues a
SSL certificate. This SSL certificate includes domain
information used by the endpoint, so it can prove
ownership of the endpoint.
In terms of p2, consistency between the endpoint
and the device showed by the endpoint can be verified
by an SSL certificate.
4.3 Dataset
The trust of the dataset depends on the data provider
in principle because the dataset is generated by the
data provider. Thus, in terms of p1, both platforms do
not have any validation function or method but sup-
porting function to improve portability of the dataset
across participants. Portability of the dataset here
means that one participant can use the dataset from
another participant without any conversion. For en-
suring portability of the dataset, all participants must
adopt same semantics on their dataset. In order to
standardise semantics of the dataset in a data space,
both platforms have a repository (called as vocabu-
lary repository in DATA-EX, semantic hub in Catena-
X) of data models and vocabularies. This reposi-
tory manages the vocabularies and models expressing
datasets in the data space. The data provider organiza-
tion can use this repository as a reference or propose
new vocabularies and models if existing data models
do not fit the purpose. On Catena-X also has over
100 pre-defined models and vocabularies with exter-
nal reference to ECLASS
8
.
In terms of p2, only DATA-EX supports a signable
format of datasets, called as Data Distribution Pack-
age (DDP). DDP allows the data consumer to verify
the creator’s authenticity of the dataset.
4.4 Data Catalog
In terms of p1, for the same reason as the dataset, the
trust of the data catalog depends on the data provider
and both platforms have a function to keep the data
catalogs interoperable in a data space. Both plat-
forms basically restrict the catalog to the DCAT Ver-
sion 2 (W3C, 2024) format by this function (data cat-
8
https://eclass.eu/en/
alog creation tool do in DATA-EX, connector do in
Catena-X).
In terms of p2, both platforms have no functions
to support.
4.5 Contract
The trust in the contract should be ensured by both
data consumers and providers, as the contract is an
object created by both participants. In terms of p1,
Catena-X supports the communication between both
participants through the connector’s contract negotia-
tion API, which is defined in the dataspace protocol
(IDSA, 2024). Using this API, the data provider can
propose a contract candidate and the data consumer
can send the confirmation result (agree or disagree).
DATA-EX doesn’t have this functionality.
In terms of p2, however, the contract should be
concluded in a commonly used manner because the
contract has legal requirements. For this reason, both
platforms recommend concluding the contract outside
of the platform (e.g., via an external contract broker-
ing service such as DocuSign). The connectors on
both platforms can work with the external contract
brokering service.
4.6 Sending & Receiving Log
On both platforms, the sending and receiving log is
basically generated by the connector and managed in
the participant’s device. Only DATA-EX has an op-
tional centralised management service (Provenance
Management Service). This service stores the send-
ing and receiving logs to construct the proof of origin,
which has the structures shown in Figure 4.
Type: Sent
URL: https://aa.com/bb.zip
Date: 2024/03/12T02:34:21
Provider: 302bd3
Consumer: dji30x
Signature: (by Provider)
Type: Received
URL: https://aa.com/bb.zip
Date: 2024/03/12T02:34:53
Provider: 302bd3
Consumer: dji30x
Signature: (by Consumer)
Type: Sent
URL: https://aa.com/bb.zip
Date: 2024/04/02T14:21:02
Provider: dji30x
Consumer: nc923o
Signature: (by Provider)
...
...
...
...
...
...
Figure 4: An example of provenance.
The provenance consists of a repetition of a sent
and received log. In terms of p1, by holding digital
signatures by both the data provider and consumer in
logs, the consistency of the sent and received logs can
ensure the occurrence of the data transfer. In terms of
p2, the provenance is verifiable as each log is signed
by the creator of the log.
DATA 2025 - 14th International Conference on Data Science, Technology and Applications
324
5 DISCUSSION
Based on the analysis results above, we discuss the
challenges of the international connectivity of data
spaces. First, we review the gaps identified as shown
in Table 4. Second, we discuss an inter-exchangeable
topology based on the review. Third, we discuss two
challenges based on the topology. Finally, we discuss
possible policy alignment for addressing two chal-
lenges.
5.1 Review of Gaps
5.1.1 Participant
It is difficult to close the gap because of the differ-
ent ways in which trust is ensured and verified. The
trust of participants on each platform is not the same,
because participants are validated with platform spe-
cific standards at generation time. In addition, the
difference of verification method makes it difficult to
standardise data exchange protocols. Catena-X can-
not adopt DATA-EX’s OIDC protocol as verification
method because Self Sovereign Identity (SSI) is an
essential requirement in Europe. Similarly, adopting
Catena-X’s DCP as a verification method on DATA-
EX could take a long time because there are no laws
or government guidelines such as eIDAS2.0 on digital
identity wallet in Japan.
5.1.2 Device
In both platforms, the device is validated in two steps.
The first step is the validation at the time of registra-
tion with the endpoint resolver. The second step is the
validation performed by CA at the time of getting de-
vice’s SSL certificate. In the second step, the device
is validated with common standards (e.g., Extended
Validation) by CA, so certain compatibility will be
ensured in trust of the device.
5.1.3 Dataset
Semantics of the dataset are different on each plat-
form, so it may spoil portability of the dataset across
multiple data spaces. Except for this portability issue,
however, exchange of the dataset itself is possible be-
cause each platform does not limit semantics of an
acceptable dataset to certain one.
5.1.4 Data Catalog
Both platforms adopt the same format as a basis and
restrict an acceptable catalog format. Principal prop-
erties of the catalog are common in both platforms, so
it is interoperable to a certain extent.
5.1.5 Contract
Both platforms recommend concluding the contract
outside of the platform, so trust of the contract is not
scope of assurance by platforms.
5.1.6 Sending & Receiving Log
Only DATA-EX assures trust of the sending and re-
ceiving log by enabling these logs verifiable in cen-
tralised management service. Verifiable sending and
receiving logs can be also used to proof transferred
path of the dataset across three or more participants
and this may contribute to ensure trust of the dataset.
However, this gap does not disturb data exchange be-
cause use of centralised management service is not
mandatory.
5.2 Inter-Exchangeable Topology
Figure 5 shows the possible inter-exchangeable topol-
ogy between DATA-EX and Catena-X based on our
gap analysis.
Participant’s Entity
Dataset
DATA-EX Connector
Catena-X Connector
Data catalog
Device certificate
Exchange Data with
Participant in JP
Exchange Data with
Participant in EU
Account as DATA-EX Participant
Account as Catena-X Participant
Figure 5: Inter-exchangeable topology between DATA-EX
and Catena-X.
To discuss inter-exchangeable topology, we
judged each gap whether it interferes interoperability
or not. For an object which has the former gap, we
thought that we should use the function or method on
each platform as they are. In our judgement, only the
participant has the former gap, so a connector, which
is a component to verify the participant, and an ac-
count, which acts as a participant’s credential, should
be prepared for both platforms like a dual-stack inter-
face. Fast and economic way to prepare the connector
and account will be desired because there is large bur-
den in preparation against two platforms.
For the rest objects, we thought that we may make
it to be common or omit it. In our judgement, the
dataset, data catalog, and the device certificate can
be used commonly in both connectors with tiny con-
version. The contract and logs can be omitted be-
cause these are managed outside of data spaces or not
mandatory.
Towards Interoperable Data Spaces: Comparative Analysis of Data Space Implementations Between Japan and Europe
325

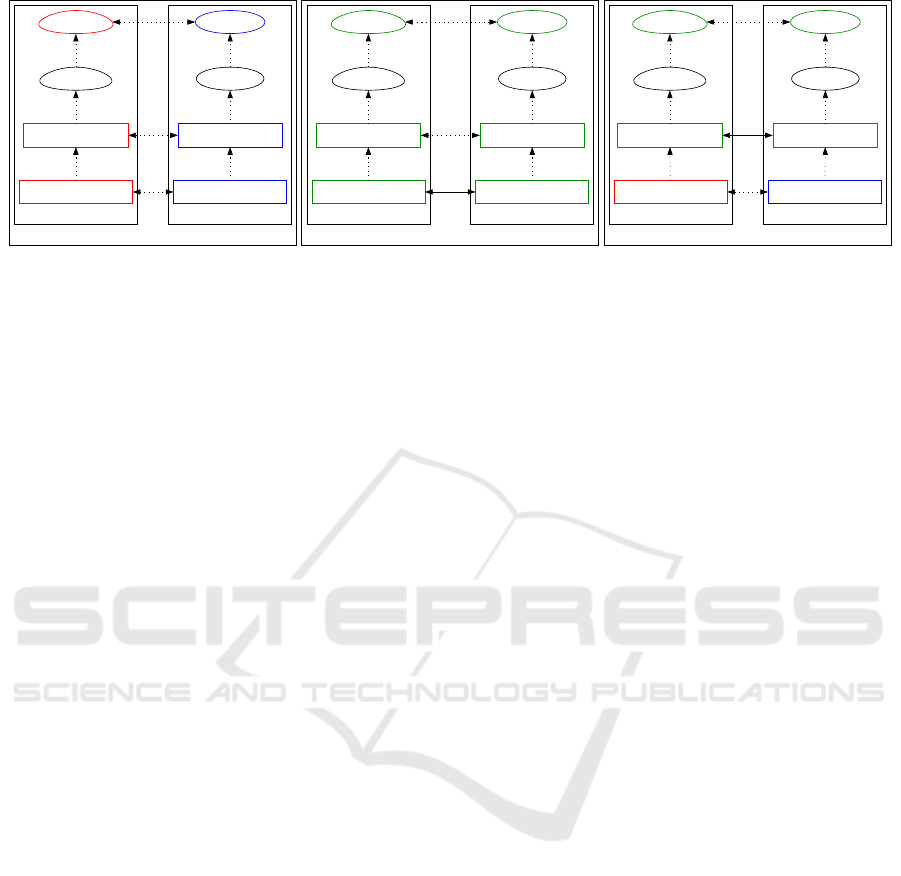
5.3 A Challenge on the Participant
Enabling interoperability of the participant trust be-
tween data spaces is a high priority challenge, as the
trust of other objects depends on the participant trust.
Figure 6 shows the current state (left), the ideal state
(center), and a realistic solution (right) in terms of the
participant trust.
On the current state, laws or government guide-
lines about digital trust are different in Japan and Eu-
rope. Especially, there is no comprehensive one like
eIDAS2.0 in Japan. This difference is reflected in the
difference of the authentication framework. The au-
thentication framework is used by the operating func-
tions of the data space, so the trust of the registered
participants will be different as a result.
In the ideal state, laws and government policies
are mutually recognised. Mutual recognition of pub-
lic (i.e., governmental) leads to compatibility of the
authentication framework. As a result, the trust of
registered participants will be compatible in some ex-
tent. However, this model is difficult to implement at
an early stage, as it could take a long time establish
mutual recognition. In fact, even electronic authen-
tication and electronic signature, which has been al-
ready used in various systems, is not mutually recog-
nised completely among each country (Tezuka et al.,
2024).
Figure 6 (right) shows our proposal as a realis-
tic solution. We recommend that the mutual recog-
nition of private authentication frameworks should
precede the mutual recognition of public to achieve
early adoption. While this approach needs to contin-
uously adapt to the latest developments in legislation
or government policy, it is advantageous for partici-
pants who wish to communicate to other participants
beyond a country or region.
5.4 A Challenge on the Dataset
Another challenge is the semantics of the dataset be-
yond the single data space. Although the trust of the
dataset depends on largely the participant, as men-
tioned in a previous section, the data space applies
governance to the data models and vocabularies by
providing the repository and pre-defined models. The
repository does not cover a data space in other coun-
tries, and the pre-defined models are not mutually
recognised between countries. This situation makes
it difficult for the participant to trust the dataset in an-
other data space.
To address this problem, we consider two solu-
tions. The first solution is to create an international
repository. Although it is an ideal solution, it takes
a long time to proceed mutual recognition between
countries or regions. The second solution is to cre-
ate an index repository to show correspondence of se-
mantics among existing repository in each data space.
It is more realistic than the first solution because reg-
istration and maintenance of the index can be led
by the participant. To implement index repository,
some existing semantic technologies such as knowl-
edge graphs (Theissen-Lipp et al., 2023) may be use-
ful. Automation of registration or maintenance using
technologies such as a name identification method is
also suitable for this solution. Thus, we believe the
second solution should be proceeded ahead of the first
one.
5.5 Possible Policy Alignment
For address two challenges above in an ideal way, pol-
icy alignment and mutual recognition between coun-
tries or regions is essential. There are two approaches
to achieving it. The first is standardization. While
the IDSA standardise the data space itself and related
technologies in the data space protocol, Gaia-X stan-
dardise trust required to join the data space ecosystem
in the Gaia-X compliance document (Gaia-X, 2024).
The Gaia-X compliance document defines trust stan-
dards to be satisfied as some levels and laws or reg-
ulations to be followed to be certified at each level.
Gaia-X itself is a European organization, so approach
to develop trust standards applicable internationally
through international and neutral standardization or-
ganizations is necessary.
The second approach is discussion in the interna-
tional committee. At G7 Hiroshima 2023, the estab-
lishment of the Institutional Arrangement for Partner-
ship (IAP)
9
was endorsed by G7 leaders to opera-
tionalise DFFT. The IAP can provide opportunities
for discussion utsing existing committees or organs of
international organisations, so discussing challenges
here can be another approach.
6 RELATED WORKS
A basic survey against data space connectors was
carried out (Dam et al., 2023) (Bacco et al., 2024).
A total of eight connectors including EDC used in
Catena-X were surveyed and evaluated, but Japanese
connectors are not included in the surveyed connec-
tors. Moreover, it didn’t discuss the interoperability
issues between connectors, while they explains IDS
RAM (IDSA, 2023) as a common specification for
9
https://www.digital.go.jp/en/policies/dfft/dfft-iap
DATA 2025 - 14th International Conference on Data Science, Technology and Applications
326
Current State
Data Space in Japan Data Space in Europe
Ideal State
Data Space in Japan Data Space in Europe
Realistic Solution
Data Space in Japan Data Space in Europe
Participants Participants
cannot trust
Data Space
affect
Data Space
affect
Authentication Framework
used
Authentication Framework
different
used
Laws, Goverment Guidelines
affect
Laws, Goverment Guidelines
different
affect
Participants Participants
can trust
Data Space
affect
Data Space
affect
Authentication Framework
used
Authentication Framework
compatible
used
Laws, Goverment Guidelines
affect
Laws, Goverment Guidelines
mutual
recognition
affect
Participants Participants
can trust
Data Space
affect
Data Space
affect
Authentication Framework
used
Authentication Framework
mutual
recognition
used
Laws, Goverment Guidelines
affect
Laws, Goverment Guidelines
different
affect
Figure 6: States of a challenge on the participant.
data spaces. Our work is to compare European con-
nectors in accordance with IDS RAM and Japanese
connectors not in accordance with IDS RAM and to
consider interoperability among them.
Attempts to create design options for data spaces
by analysis of published papers or interview were
conducted (Gieß et al., 2023) (Gieß et al., 2025). This
paper also conducted a frequency analysis of design
options against existing data spaces. Their design op-
tions include a perspective of trust. They emphasise
the dataset and log as objects to consider trust, how-
ever, many other objects, such as contracts, are gen-
erated in an actual data exchange process. Our work
is to conduct an analysis with comprehensive criteria
covering a whole data exchange process.
Consideration of interoperability between data
spaces was carried out (Schinke and Roßmann, 2024).
They investigated and analysed various technologies
(including the data space) that can be used to increase
data sharing. They proposed six ways to enable trust-
worthy data sharing using the technologies they re-
searched. One of six ways included an architecture
that combines multiple data spaces. They stated that
handling of a dataset for multiple data spaces is a chal-
lenge in this architecture and this challenge should be
solved by data trustee (Schinke et al., 2023) (Steinert
et al., 2024). The data trustee can hide a layer of con-
nectors from the participants by creating intermediary
layer, so the participant does not have to consider in-
teroperability issues. While our work is to discuss
an inter-exchangeable topology without any trust in-
termediary like the data trustee, the data trustee can
be another solution towards achievement of interop-
erability.
Another consideration of interoperability between
data spaces was carried out (Hutterer and Krumay,
2024). They surveyed and analysed the scopes of gov-
ernance in data spaces from published papers. As
a result of the analysis, three types of governance
were identified: ecosystem governance, technologi-
cal governance, and operational governance. In the
technological governance, the authors argues that the
federated data space architecture (Schleimer et al.,
2023) can achieve interoperability across different
data spaces. The federated data space architecture ex-
presses the architecture to realise global data avail-
ability across multiple data spaces as three logical
layers, local foundation layer, federation layer, and
global presentation layer. This architecture was eval-
uated with a circular economy example, but designs
for each layer were abstract because no actual con-
nectors were described. Our work is to discuss an
inter-exchangeable topology at a more concreate level
by comparing and analysing actual connectors.
An experimental environment (called as Interna-
tional Testbed for Dataspace Technology, or ITDT)
to try interoperability measures was proposed (Mat-
sunaga et al., 2023). The ITDT aims to enable re-
searchers or developers to test connectivity or inter-
operability among connectors which built on different
technological bases. The ITDT can be an adequate
environment for us to implement and test our propos-
als in future, although a DATA-EX connector has not
provided yet in the ITDT.
7 CONCLUSION
In this paper, we analysed DATA-EX and Catena-X as
a representative data space platform in Japan and Eu-
rope from the perspective of trust. In order to make a
fair comparison between two platforms, we decided a
common data exchange process and identified six ob-
jects that are generated in the decided process and cre-
ated analysis criteria over the identified objects. Us-
ing the analysis criteria, we analysed two platforms
and identified gaps on all objects.
Then, we reviewed the identified gaps and con-
cluded that the trust of participant to be the most
significant challenge. Based on the review, we dis-
cussed inter-exchangeable topology between two data
spaces and two challenges. As the first challenge, we
Towards Interoperable Data Spaces: Comparative Analysis of Data Space Implementations Between Japan and Europe
327

identified compatibility of participant trust across data
spaces and a realistic solution to it. As a second chal-
lenge, we stated the semantics of the dataset beyond
single data space and a brief solution of it.
Our study is, naturally, subject to several limita-
tions that must be considered. Because of the anal-
ysis method focusing on trust, our solutions do not
cover all aspect of interoperability but focus on com-
patibility of trust on participating entities and the data
exchanged. Especially, issues like how to assure
compatibility between different connectors is not dis-
cussed. Continuous discussion is needed for it consid-
ering each standardization activities, although multi-
stack topology we proposed can be one solution for a
while.
Ideally, both two challenges we stated should be
addressed by each other’s government and interna-
tional standardisation organisation, but a work of
them takes time to reach consensus. Therefore, in the
perspective of immediacy, we believe that private trust
initiatives are just as important as public initiatives.
We hope this paper contributes to further efforts to-
wards a sustainable and interconnected data economy
in the future.
REFERENCES
Andrea, B. et al. (2024). Eclipse Decentralized Claims
Protocol. https://eclipse-dataspace-dcp.github.io/
decentralized-claims-protocol/v1.0-RC1/, v1.0-rc1
edition.
Bacco, M., Kocian, A., Chessa, S., Crivello, A., and Bar-
socchi, P. (2024). What are data spaces? systematic
survey and future outlook. Data in Brief, 57:110969.
Catena-X (2024). Standards. Catena-X Automo-
tive Network e.V., https://catenax-ev.github.io/docs/
standards/overview, cx-jupiter edition.
Dam, T., Klausner, L. D., Neumaier, S., and Priebe, T.
(2023). A survey of dataspace connector implementa-
tions. arXiv preprint arXiv:2309.11282.
DSA (2022). Data Exchange System Overview. Data
Society Alliance, https://data-society-alliance.org/
survey-research/data-exchange-system-overview/,
v1.0 edition.
Gaia-X (2024). Gaia-X Compliance Document. Gaia-
X, https://gaia-x.eu/wp-content/uploads/2024/09/
Compliance-Document 24.06.pdf, 24.06 edition.
Gieß, A., M
¨
oller, F., Schoormann, T., and Otto, B. (2023).
Design options for data spaces. In ECIS.
Gieß, A., Schoormann, T., M
¨
oller, F., and G
¨
ur, I. (2025).
Discovering data spaces: A classification of design
options. Computers in Industry, 164:104212.
Hutterer, A. and Krumay, B. (2024). Scopes of governance
in data spaces. In ACIS.
IDSA (2023). IDS-RAM 4. International Data Spaces
Association, https://docs.internationaldataspaces.org/
ids-knowledgebase/ids-ram-4.
IDSA (2024). Dataspace Protocol. Interna-
tional Data Spaces Association, https://docs.
internationaldataspaces.org/ids-knowledgebase/
dataspace-protocol, 2024-1 edition.
Koshizuka, N. and Mano, H. (2022). Data-ex: Infrastruc-
ture for cross-domain data exchange based on feder-
ated architecture. In 2022 IEEE International Confer-
ence on Big Data (Big Data), pages 6145–6152.
Matsunaga, I., Michikata, T., and Koshizuka, N. (2023).
Itdt: International testbed for dataspace technology.
In 2023 IEEE International Conference on Big Data
(BigData), pages 4740–4747. IEEE.
Ministry of Economy, Trade and Industry (2023). Japan’s
initiatives for interoperable data infrastructures offi-
cially named “ouranos ecosystem”. https://www.meti.
go.jp/english/press/2023/0429 001.html.
Schinke, L., Hoppen, M., Atanasyan, A., Gong, X., Heinze,
F., Stollenwerk, K., and Roßmann, J. (2023). Trustful
data sharing in the forest-based sector-opportunities
and challenges for a data trustee. In VLDB Workshops.
Schinke, L. and Roßmann, J. (2024). Enabling trustful data
sharing in industry 4.0-a comparison between data
spaces, data markets and other related concepts. Au-
thorea Preprints.
Schleimer, A. M., Jahnke, N., and Otto, B. (2023). Archi-
tecture design options for federated data spaces. In
HICSS.
Sprenger, T. (2024). Gaia-x digital clearing houses
(gxdch). https://gaia-x.eu/wp-content/uploads/2024/
08/GXDCH Gatekeeper-Digital-Economy.pdf.
Steinert, M., Tebernum, D., and Hupperz, M. (2024). De-
sign features for data trustee selection in data spaces.
In International Conference on Data Science, Tech-
nology and Applications 2024.
Tezuka, S. et al. (2024). Comparison report of international
mutual recognition for trust services infrastructure.
Technical report, Keio University, https://d-trust.
sfc.wide.ad.jp/assets/pdf/JP-EU-India Comparison
Report International Mutual Recognition r9.pdf.
Theissen-Lipp, J., Kocher, M., Lange, C., Decker, S.,
Paulus, A., Pomp, A., and Curry, E. (2023). Seman-
tics in dataspaces: Origin and future directions. In
Companion Proceedings of the ACM Web Conference
2023, pages 1504–1507.
W3C (2024). Data Catalog Vocabulary (DCAT). W3C,
https://www.w3.org/TR/vocab-dcat-2/, version 2 edi-
tion.
DATA 2025 - 14th International Conference on Data Science, Technology and Applications
328
