
A Resilient Randomization Technique Against ML-Driven Timing Side
Channel Attack on Mobile Location
Abdeslam El-Yahyaoui
1
and Mohammed Erradi
2
1
CID Development, Rabat, Morocco
2
ENSIAS, Mohammed V University of Rabat, Morocco
Keywords:
User Privacy, Mobile User Location, Timing Side Channel Attack, Random Delays.
Abstract:
Delivery status notifications are a standard feature of mobile instant messaging applications. They inform
users about the successful delivery of their sent messages. However, this common feature opens up a timing
side channel attack compromising user location privacy. This attack exploits variations in Round Trip Times
(RT T s) across locations, allowing the training of machine learning models for location inference. Recent
work proposed a solution based on randomly delaying the RTTs (RDR) on the messenger server side using
uniformly sampled perturbations between 0 and a maximum value.
I this work, we have shown that the timing side channel attack still persists with significant accuracy even
with the aforementioned randomly delaying RT T countermeasure. We then propose a resilient client side
randomization technique involving a distribution with randomly varying parameters across RT T s (RV PR).
We have shown that the suggested approach (RV PR) is resilient against this attack and has less impact on user
experience than the existing RDR approach.
1 INTRODUCTION
Mobile messaging applications like WhatsApp have
become the primary mode of mobile communications
(Schnitzler et al., 2023). They are widely used in:
sending and receiving messages, exchanging audio
and video calls, informal communication among
working colleagues (Loch, 2019), to social interac-
tions among elderly people (Miller et al., 2021). In
some cases, messengers are also used for official cor-
respondence with government entities (Purz, 2020),
thus composing large and heterogeneous sets of
contacts in one application per user. One notable fea-
ture of these messaging applications is the real-time
status updates provided after delivery and reception
of messages. Users can easily track the progress
of their messages through the checkmarks received
after delivery and read receipt (Ariano, 2020). While
this functionality enhances user experience, it also
introduces potential privacy issues. As highlighted in
(Schnitzler et al., 2023), recipient geolocation could
be compromised through this tracking mechanism.
This issue is critical because it is simple, rather un-
suspicious, and hard to mitigate. Users lack effective
means to prevent messages from individuals in their
contact list, other than permanently blocking them.
A similar vulnerability was revealed in Short Mes-
sage Services (SMS) (Bitsikas et al., 2023). Despite
the prevalence of smartphones and various messaging
apps, SMSs remain an essential communication chan-
nel for sending and receiving text messages. They
are widely used in diverse applications such as ap-
pointment reminders, two-factor authentication, and
identity verification(Peeters et al., 2022; Reaves et al.,
2016; Reaves et al., 2019). However, as demonstrated
in (Bitsikas et al., 2023), SMSs can be exploited to
infer a receiver location. The attack works by lever-
aging SMS Delivery Reports, which are transmitted
back to the sender when the network delivers the SMS
to the recipient. The sender can request these reports,
and there is no way for the recipient to prevent them
(the recipient cannot prevent the sender from request-
ing and getting the Delivery Reports of the sent mes-
sages). By measuring RT T s between sending an SMS
and receiving the corresponding Delivery Report, the
attacker can distinguish various locations of the tar-
get recipient and determine their location area after a
training phase. Imagine the scenario of a person (the
victim) conducting a press conference from a partic-
ular location, such as their official residence. Despite
public knowledge of the victim’s current location and
El-Yahyaoui, A., Erradi and M.
A Resilient Randomization Technique Against ML-Driven Timing Side Channel Attack on Mobile Location.
DOI: 10.5220/0013457900003979
In Proceedings of the 22nd International Conference on Security and Cryptography (SECRYPT 2025), pages 61-71
ISBN: 978-989-758-760-3; ISSN: 2184-7711
Copyright © 2025 by Paper published under CC license (CC BY-NC-ND 4.0)
61

phone number, the adversary initiates the collection
of round-trip time measurements by sending silent or
regular SMS messages to the victim. These measure-
ments create timing signatures specific to the location.
Later, when the attacker seeks to determine if the vic-
tim has returned to their residence, they simply send
a silent SMS and compare the timing signatures. The
attacker can always contact the victim and collect the
round-trip time measurements at any time with just
their mobile phone number. This is possible because
Delivery Reports are inherent to protocol specifica-
tions across all mobile network generations and can-
not be disabled.
An existing solution (Schnitzler et al., 2023; Bit-
sikas et al., 2023) consists of obfuscating the RT T s by
adding random delays sampled from a uniform dis-
tribution on the messenger server side or within the
core network for SMS. This is not sufficient to avoid
this timing side channel attack and adversely affects
server and core network resources.
In this paper, we propose a more resilient client
side distribution where the parameters exhibit random
variation across RT T measurements. We will show
that this randomization technique renders the compu-
tation of the RT T s more challenging. The main con-
tributions of this work are:
1. Proofing the persistence of the timing side channel
attack even with the existing approach.
2. The design of a randomization technique resilient
against location inference attack.
3. Proofing the usefulness of implementing the solu-
tion on the client side rather than the server side
to avoid its high resource consumption.
4. The experiments of the suggested solution outper-
form the existing one.
The subsequent sections of the paper are organized as
follows: Section 2 discusses related works, followed
by preliminaries in Section 3. Section 4 presents the
threat model. Section 5 elaborates on the proposed
solution. Section 6 provides the experimental results.
Finally, Section 7 concludes the paper.
2 RELATED WORK
The most related works to our research are those con-
ducted in (Schnitzler et al., 2023) and (Bitsikas et al.,
2023). The former focused on messenger applications
and demonstrated a location inference attack based on
the RT T s generated by delivery status notifications.
They proposed various solutions, including randomly
delaying these notifications by a uniformly sampled
random delay between 0 and 5 seconds. The latter
demonstrated the existence of a similar side-channel
attack in SMS services. This attack uses RT T s as-
sociated with delivery reports received post-sending
an SMS. They also suggested different solutions, in-
cluding randomly delaying the delivery reports. In
our study, we propose a novel approach more resilient
against location inference attacks.
Several research works have extensively explored
the relationship between timing and distance, inte-
grating the Internet’s topology to enhance localiza-
tion techniques (Candela et al., 2019; Du et al., 2020;
Katz-Bassett et al., 2006; Kohls and Diaz, 2022).
These studies collectively contribute to advancing the
understanding and application of timing-based local-
ization and distance estimation on the Internet. Other
studies (Hong et al., 2018; Hussain et al., 2019; Lak-
shmanan et al., 2021) worked on localizing cellular
network users either actively or passively through the
capture of identifiers. Kotuliak et al. (Kotuliak et al.,
2022) showcased enhanced localization accuracy of
up to 20 meters using Timing Advance and leverag-
ing overshadowing techniques (Erni et al., 2021; Yang
et al., 2019).
Authors in (Michalevsky et al., 2015) investi-
gated a side channel vulnerability allowing applica-
tions to access aggregate power usage data. By an-
alyzing short-term power consumption, these appli-
cations could infer the user location, since the phone
location affects the power consumption of its cellular
radio. Oberhuber et al. (Oberhuber et al., 2025) con-
ducted another study on sensor-based side-channel at-
tacks targeting Android smartphones. Their research
specifically explored the exploitation of power-related
signals through the Android sensor framework. The
findings demonstrated how commonly available sen-
sors, such as the geomagnetic rotation vector sensor,
can be used to leak sensitive information in realistic
attack scenarios.
The security threats posed by in-app advertise-
ments on mobile devices were studied in (Diaman-
taris et al., 2021). The study highlighted the ability of
in-app ads to access mobile sensors without specific
permissions. This critical issue exposes sensitive user
data like the geographical location. Han et al. (Han
et al., 2022) studied a location spoofing attack target-
ing Wi-Fi positioning systems. The attack involves
crafting a Location Lookup Table containing esti-
mated Wi-Fi access point locations based on cell tow-
ers and Wi-Fi nodes. This attack enables adversaries
to infer users’ daily activities and monitor their move-
ments. Researchers in (Pourali et al., 2022) investi-
gated existing privacy analysis tools for mobile apps,
noting their focus on standard HTTP and HTTPS
SECRYPT 2025 - 22nd International Conference on Security and Cryptography
62

channels while potentially overlooking vulnerabilities
in non-standard ones like TCP/UDP and custom en-
cryption. Their research revealed widespread GPS
data leakage in mobile apps.
Several studies have explored side-channel attacks
in cryptography. Nassi et al. (Nassi et al., 2023) in-
troduced optical cryptanalysis, a novel side-channel
attack where secret keys are extracted by measuring
light emitted from a device’s power LED using a pho-
todiode and analyzing subtle fluctuations during cryp-
tographic operations. Erata et al. (Erata et al., 2023)
introduced Pascal, a tool designed to detect power
side-channel vulnerabilities in constant-time crypto-
graphic code using symbolic register analysis tech-
niques. Ahmed et al. (Ahmed et al., 2024) provided
a review of deep learning use for enhancing encryp-
tion techniques against side-channel attacks between
2018 and 2024. They discussed the vulnerabilities
in cryptographic algorithm implementations, partic-
ularly through power analysis and explores how deep
learning methods such as Convolutional Neural Net-
works and Recurrent Neural Networks can be em-
ployed to mitigate these threats.
In their work, Zhang et al. (Zhang et al., 2024)
examined micro architectural timing side-channel at-
tacks and their countermeasures. They focused on
vulnerabilities arising from performance optimiza-
tions like simultaneous multi-threading and out-of-
order execution. Maar et al. (Maar et al., 2025) in-
troduced KernelSnitch, a novel side-channel attack
based on timing differences in kernel data structures
to leak sensitive information. The data structures,
such as hash tables and trees, exhibit timing variances
depending on their occupancy levels, which can be
exploited by an unprivileged attacker to infer infor-
mation about kernel operations or activities in other
user processes.
Cristiano et al. (Rodrigues et al., 2024) intro-
duced a novel class of side-channel attacks on mi-
crocontrollers. These attacks exploit subtle timing
differences in the bus interconnect arbitration logic.
The authors presented BUSted, a method that exploits
these timing differences to bypass memory protec-
tion mechanisms and leak sensitive data from iso-
lated memory regions. Bognar et al. (Bognar et al.,
2023) proposed enhancing an instruction set architec-
ture with micro architectural leakage traces obtained
through profiling. This approach facilitates the devel-
opment of tools to detect and mitigate side-channel
vulnerabilities.
3 PRELIMINARIES
Round Trip Time (RT T ) is the time in milliseconds
(ms) it takes for a network packet to go from a start-
ing point to a destination and back to the starting
point. Authors in (Schnitzler et al., 2023) and (Bit-
sikas et al., 2023) demonstrated the existence of a
timing side channel vulnerability in mobile messag-
ing applications and SMSs based on RT T s. In this
section, we will provide some background on side
channels as well as the concept of the considered side
channel attack.
3.1 Side Channels and User Privacy
On a computing system, the occurrence of any event
will inevitably produce side effects which could be
observed by the party not supposed to know anything
about the event (Wang et al., 2023). These side effects
are channels from which protected information can be
inferred, which can compromise users privacy. User
privacy refers to an individual’s right to control how
their personal data is used (Bateman, 2023). It should
be collected and used according to their choices, and
in a way that helps them remain anonymous. Accord-
ing to the General Data Protection Regulation, the Eu-
ropean Union regulation on information privacy, per-
sonal data covers users location (Bateman, 2023). A
user could be profiled based on the places that he vis-
its, albeit at a low frequency. He might not be will-
ing to reveal that he is visiting a particular church,
a health clinic, or some hotel. Revealing these places
might enable an entity with access to the user location
to profile him (Fawaz and Shin, 2014).
3.2 Messaging Applications RTT-Based
Side Channel Attack
In the context of messaging applications (Schnitzler
et al., 2023), the involved RT T s are derived from
the delivery status notifications shown in Figure 1.
The sent message initially reaches a messenger server,
which then acknowledges receipt by sending a deliv-
ery notification to the sender. The server forwards the
message to the ultimate receiver, subsequently receiv-
ing confirmation of successful reception. Upon re-
ceiving this notification, the server dispatches a con-
firmation of successful delivery back to the sender.
This process is simplified since sender and receiver
can be connected to different messenger servers.
Based on these exchanges, the adversary cal-
culates RTT (S, M) between Sender and Messenger
server as the time difference between sending the
message and receiving the first notification from the
A Resilient Randomization Technique Against ML-Driven Timing Side Channel Attack on Mobile Location
63
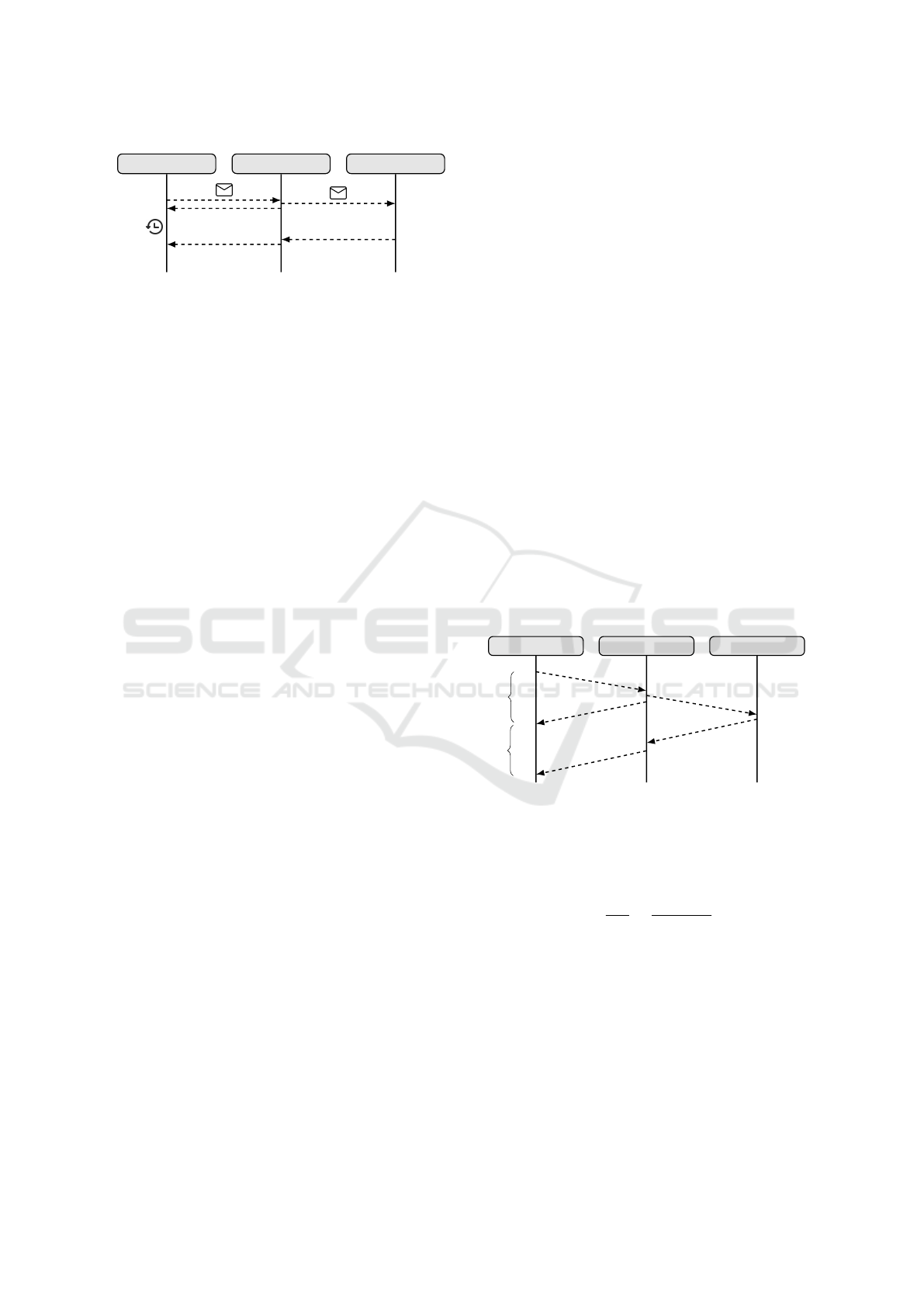
(S)ender
(M)essenger Server
(R)eceiver
✓
✓
✓✓
Figure 1: Message flow scenario.
server. Likewise, RT T (S,R) between Sender and
Receiver as the duration between sending the mes-
sage and receiving the second notification confirm-
ing successful delivery to the intended receiver. From
the two obtained RT T s, the adversary calculates the
RT T (M, R) between Messenger and Receiver as fol-
lows:
RT T (M, R) = RT T (S,R) − RT T (S,M) (1)
For a specific location A, the calculated RT T
can be expressed as τ(A) + ε. Here, ε accounts for
the measurement’s fluctuation around a constant
value τ(A), influenced by factors such as varying
network and messenger server loads. This is why
the authors opted for a sequence of 5 RT T mea-
surements to construct their timing dataset, as this
improves accuracy in accounting for these variations.
After training a model on this dataset, the adversary
can predict locations based on newly measured RT T s.
The variability in Round-Trip Times (RT T s) is not
solely affected by distance; rather, it is influenced by a
multitude of factors. For instance, fluctuations in net-
work traffic affect how long it takes to send messages
and receive delivery confirmations. Additionally, the
specific network path traversed by packets can differ
based on the Internet service providers involved, lead-
ing to distinct timing characteristics for each location.
Consequently, locations exhibit different timing sig-
natures, consisting of the distribution of RT T (M, R)
considering these diverse factors. Notably, even loca-
tions equidistant from the server might have different
timing patterns.
3.3 SMS RTT-Based Side Channel
Attack
A similar study on the Short Message Service (SMS)
(Bitsikas et al., 2023) demonstrated that delivery re-
ports of sent SMSs lead also to a timing side-channel
vulnerability. Receiving an SMS inevitably generates
Delivery Reports whose reception bestows a timing
attack vector at the sender. The high-level idea of this
attack is as follows: The time elapsed between send-
ing an SMS and receiving the corresponding Deliv-
ery Report differs depending on the receiver location.
Therefore, one can distinguish different receiver loca-
tions by observing the elapsed time.
The attack is based on SMS Delivery Reports,
which are transmitted back to the sender when the
network delivers the SMS to the recipient. The sender
can request these reports, and there is no way for the
recipient to prevent them. By measuring the round-
trip time, i. e., the time elapsed between sending an
SMS and receiving the corresponding Delivery Re-
port, the attacker can distinguish various locations of
the target recipient and determine their location area
after a training phase.
As depicted in Figure 2, SMS transmissions
prompt acknowledgment notifications from the core
network and Delivery Reports from the recipient.
This Delivery Report indicates the SMS delivery sta-
tus. To calculate the fingerprint for location identifi-
cation, the attacker uses three timestamps: the SMS
transmit time (t
txt
) when the attacker sends the SMS,
the SMS sent time (t
sent
) when the attacker receives
the “ACK” notification, and the SMS delivery time
(t
del
) when the attacker receives the Delivery Report
notification. From these timestamps, the real sent du-
ration (T
sent
), real delivery duration (T
del
), total de-
livery duration (T
tot
), and delivery ratio (P) are com-
puted. These features are calculated for each individ-
ual SMS transmission.
Sender Core Network Receiver
SMS
ACK
SMS
Delivery Report
Delivery Report
T
sent
t
txt
t
sent
T
del
t
del
Figure 2: SMS timing features.
T
sent
= t
sent
− t
txt
(2)
T
del
= t
del
− t
sent
(3)
T
tot
= T
del
+ T
sent
(4)
P =
T
del
T
tot
=
t
del
− t
sent
t
del
− t
txt
(5)
Additionally, to generate robust location signatures,
the attacker considers two consecutive SMS transmis-
sions (i − 1 and i) and estimates the differences in
real sent duration (T
∆sent
) and real delivery duration
(T
∆del
).
T
∆sent
= (T
i
sent
− T
i−1
sent
)/T
i−1
sent
(6)
T
∆del
= (T
i
del
− T
i−1
del
)/T
i−1
del
(7)
The location signature comprises the six features:
(T
sent
, T
del
, T
tot
, P, T
∆sent
, T
∆del
).
SECRYPT 2025 - 22nd International Conference on Security and Cryptography
64

4 THREAT MODEL
The attacker’s goal is to locate the victim receiver’s
whereabouts, specifically, whether the victim’s
mobile is in a specific geographic area of interest.
We have two different scenarios to perform the con-
sidered attack; using either messenger applications or
SMSs:
Messenger Application Scenario:
• Both the attacker and the victim have regular de-
vices supporting the considered messaging appli-
cation.
• The attacker can access and analyze his own net-
work traffic to extract timing information.
• Adversary and victim must be in each other’s con-
tact lists in the messenger (the threat is limited to
parties who likely know each other).
• The involved devices have network connection.
• The adversary does not require physical access to
mobile devices, or any network entities.
SMS Scenario:
• The considered SMSs can be regular private
SMSs, marketing SMSs, or silent SMSs.
• The adversary knows the victim’s mobile number
and can send it SMSs.
• The adversary can target any valid mobile number
attached to a cellular provider.
• The adversary does not require physical access to
mobile devices, or any network entities.
In the next section, we will elaborate on our suggested
solution.
5 A RANDOMLY VARYING
PARAMETERS DISTRIBUTION
APPROACH
Our solution is based on enhancing the existing ap-
proach that consists of randomizing the RT T s using
a standard uniform distribution. In this section, we
highlight this approach weaknesses, then we present
our suggested one.
5.1 Existing Approach
The existing approach consists of delaying the RT T s
using samples from the uniform distribution U(a, b)
having a and b as parameters. The added delays are
implemented on the messenger server for messaging
applications and core network for SMSs. We will
show that even with this solution, the attack can still
be performed. Additionally, we will examine the im-
pact of implementing this solution on the messenger
server or the core network side.
Persistence of the Attack. The considered distribu-
tion exhibits static properties such as min, max, and
mean values corresponding to a, b, and (b − a)/2, re-
spectively. Statistically estimating these features is
easy based on a sequence of a relatively small num-
ber n of samples. For example, if an adversary is
interested in a location A with an RT T of τ(A) + ε,
a sequence of n measurements at this location will
produce values like τ(A) + ε + u
1
, τ(A) + ε + u
2
, ...,
τ(A) + ε + u
n
. u
1
, u
2
, ..., u
n
are sampled from U(a,b)
and ε is the the fluctuation of the RT T around τ(A).
The adversary can select the minimum value of this
sequence, which is τ(A) + ε + min(u
1
,u
2
,...u
n
), ap-
proximately τ(A) +ε + a. Consequently, they can de-
duce τ(A) + ε if a is known. They repeat this pro-
cess five times to construct a sequence of five approx-
imated RT T s that the model requires to predict the lo-
cation. Algorithm 1 shows this attack procedure when
a is known. The same process applies to the mean and
max values. If a and b are unknown, the adversary
can’t directly deduce the RT T s. Thus they will need
to construct a shifted dataset based on RT T + a, RT T
+ b, or RT T + (b − a)/2 to carry out the attack. We
will further discuss the effectiveness of the attack in
such scenarios in section 6. It’s important to note that
performing the attack based on min, max, or mean
values makes the dataset construction more complex
since it requires more measurements.
Impact on the Messenger Server. Implementing
the solution on the messenger server side would
degrade its resources since it is designated to handle
a large number of messages. The same constraint
applies to the core network for SMSs. Thus, we
will focus our reasoning only on the messaging
applications scenario.
The dynamics of the server can be modeled like a
system with an inflow and an outflow. The balance of
inflow and outflow determines the state of the server.
We consider a server with:
• Capacity (K): Maximum number of messages the
server can hold.
• Incoming Speed (s
i
): Rate at which messages ar-
rive at the server.
A Resilient Randomization Technique Against ML-Driven Timing Side Channel Attack on Mobile Location
65

Algorithm 1: Min value based attack process for a given
location A.
Input: Model M trained to classify a set of
locations including a location A
Input: The lower bound a of the uniform
distribution U(a,b) used to
randomize the RTTs
Input: A list RTT sequences of five
sequences of n randomized RTTs at
location A using U(a,b)
Output: Prediction of the location
Initialize an empty list estimated RTTs;
for i ← 1 to 5 do
RTT sequence ← RTT sequences[i];
min sequence ← min(RTT sequence);
estimated RTT ← (min sequence − a);
Append estimated RTT to
estimated RTTs;
prediction ← M(estimated RTTs) ;
// Use M to predict location
return prediction;
• Outgoing Speed (s
o
): Rate at which messages are
processed.
The server is saturated when it reaches its maximum
capacity and cannot accept new messages until some
are processed.
Saturation Condition. For the sake of simplic-
ity, we consider (s
i
) and (s
o
) constants. Saturation
occurs when the incoming rate exceeds the outgoing
rate. In such scenario, the net flow rate into the server
is given by:
NetFlowRate = s
i
− s
o
(8)
The Formula for Saturation Time: The number
of messages in the server at time t is approximately
given by:
n(t) = n
0
+ (s
i
− s
o
) · t (9)
where n
0
is the initial number of messages in the
server. This formula shows a linear growth of
messages over time.
The server reaches its capacity K at t
sat
:
K = n
0
+ (s
i
− s
o
) · t
sat
(10)
For s
i
> s
o
, the time until saturation t
sat
is given by:
t
sat
=
K − n
0
s
i
− s
o
(11)
This formula is applicable under the condition that
s
i
> s
o
and n
0
≤ K. If s
i
≤ s
o
, the server will not
reach saturation as the outflow is sufficient to man-
age or exceed the inflow. Implementing the solution
on the server side would significantly reduce s
o
, as
each message handling duration will be delayed by
(b−a)/2 in average. For a = 0 and b = 5 as suggested
in (Schnitzler et al., 2023), the messages will be de-
layed by 2.5 seconds in average. During peak hours,
when the server receives a high volume of messages,
s
i
would exceed s
o
, leading to server saturation.
5.2 The Suggested Solution
We propose using a client side uniform distri-
bution with parameters randomly varying across
RT T measurements. These parameters are sam-
pled from uniform distributions at each RTT mea-
surement. Specifically, this client side distribution
has the form: U(u(a
1
,b
1
),u(a
2
,b
2
)), with a
1
, b
1
,
a
2
and b
2
appropriately chosen. The distribution
U(u(a
1
,b
1
),u(a
2
,b
2
)) is characterized by its diffi-
culty in capturing its minimum, maximum, and mean
values. This makes it more difficult for attackers to
remove randomness by repeatedly sending messages.
We considered only uniform distributions since
they offer the highest entropy (MacKay, 2003),
thus, a significant level of randomness in the sam-
pled values.
Implementing the solution on the client side
wouldn’t cause significant issues on the client device.
In fact, a typical client device is expected to handle
a very limited number of messages. However, in this
case, we recommend implementing an anti-Denial of
Service (anti-DOS) mechanism to protect the device.
This is crucial, as an attacker could flood the device
that implements the random delays with a high vol-
ume of messages, causing resource exhaustion. This
scenario is similar to server saturation under heavy
load conditions and the application of random delays
(as demonstrated in Section 5.1).
We compare the behaviors of the two distributions
U(0,5) suggested in (Schnitzler et al., 2023) and
U(u(0,2),u(3,5)) having the same minimal, maxi-
mal, and mean values. Figure 3 shows the values of
100 samples from both distributions. Notably, we ob-
serve that our proposed distribution seldom reaches
values close to its real minimum and maximum com-
pared to the other one. For deeper insights Figures 4,
5, and 6 depict the minimum, maximum, and mean
values of varying size samples from both distribu-
tions. Each round of measurements involves sam-
pling a new set of values, without accumulation with
the previous ones. These plots show the large dif-
ference between the required sample size to obtain
values near the min, max, and mean of the two dis-
SECRYPT 2025 - 22nd International Conference on Security and Cryptography
66
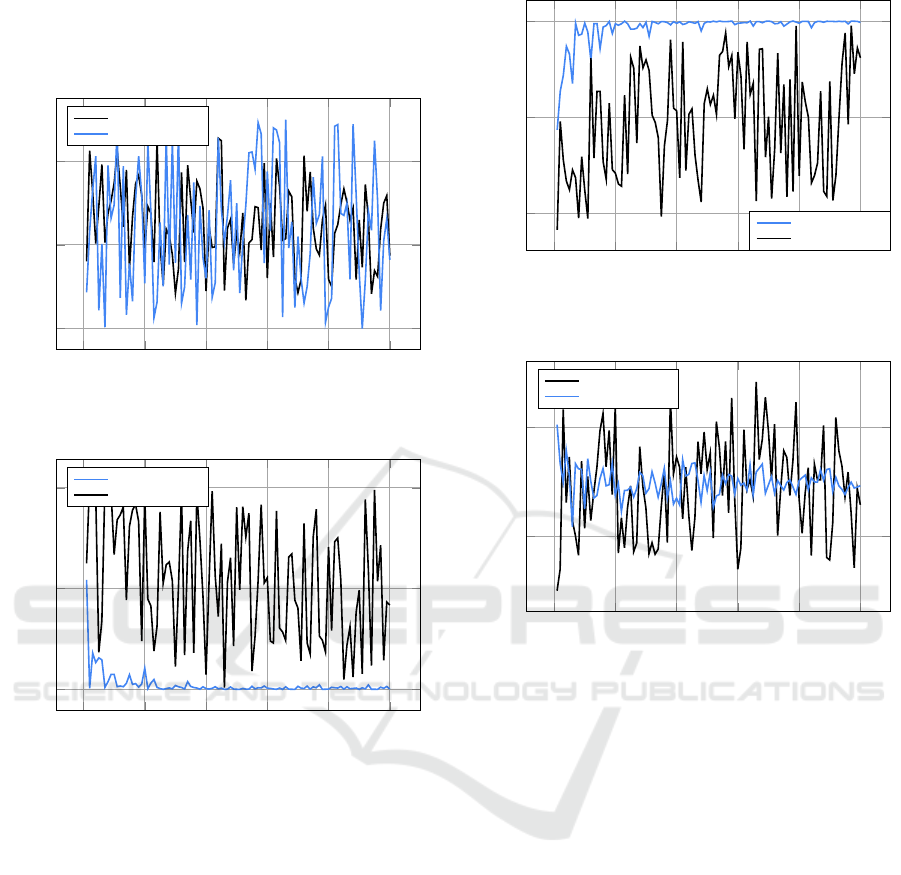
tribution. For instance, Figure 4 shows that U(0, 5)
attained values near 0 for samples of size almost 10,
whereas U(u(0, 2), u(3,5)) necessitated nearly a 230-
size sample.
0 20 40
60
80 100
0
2
4
Experience number
Generated values
U(u(0,2), u(3,5))
U(0,5)
Figure 3: Behavior of the two distributions.
0 100 200 300 400
500
0
1
2
Number of generated samples
Minimum
U(0,5)
U(u(0,2), u(3,5))
Figure 4: Min values comparison.
Table 1 shows the number of obtained values in
the window [0,0.1] for different sample sizes. For the
distribution U(u(0,2),u(3,5)), we didn’t obtain any
value between 0 and 0.1 for sample sizes less than
400. We then observed one value in the interval for
the sizes 600 and 1000 and two values with the sam-
ple size 5000. For the distribution U(0, 5), we ob-
tained 1 value between 0 and 0.1 for sample sizes 10
and 50. This number increased significantly along
the increasing sample sizes until reaching 217 for a
sample size of 10000. In summary, as the sample
size increases, the number of values near 0 also in-
creases for both distributions, but the rate of increase
is much higher for the distribution U(0,5) compared
to U(u(0, 2),u(3,5)). This is expected as the sup-
port of U(0, 5) covers the interval [0, 5] uniformly,
whereas U(u(0,2),u(3, 5)) is constrained by the dis-
tributions U(0,2) and U(3,5).
0 100 200 300 400
500
3
4
5
Number of generated samples
Maximum
U(0,5)
U(u(0,2), u(3,5))
Figure 5: Max values comparison.
0 100 200 300 400
500
2
3
Number of generated samples
Mean
U(u(0,2), u(3,5))
U(0,5)
Figure 6: Mean values comparison.
Impact on User Experience: Figure 3 presenting
the behavior of the two distributions shows that
the distribution, U(0,5), exhibits greater fluctua-
tions between its min and max values compared to
U(u(0,2),u(3,5)). This entails that for the first one,
a sender may receive message notifications either
promptly or significantly delayed, leading to potential
drawbacks in user experience. However, in the second
scenario, notifications of message reception are less
time dispersed, offering a more consistent experience
for the sender.
In the next section, we will conduct experimental
validation of the theoretical results.
6 EVALUATION
In this section we aim to experimentally evaluate the
effectiveness of our approach and compare it to the
existing one.
A Resilient Randomization Technique Against ML-Driven Timing Side Channel Attack on Mobile Location
67
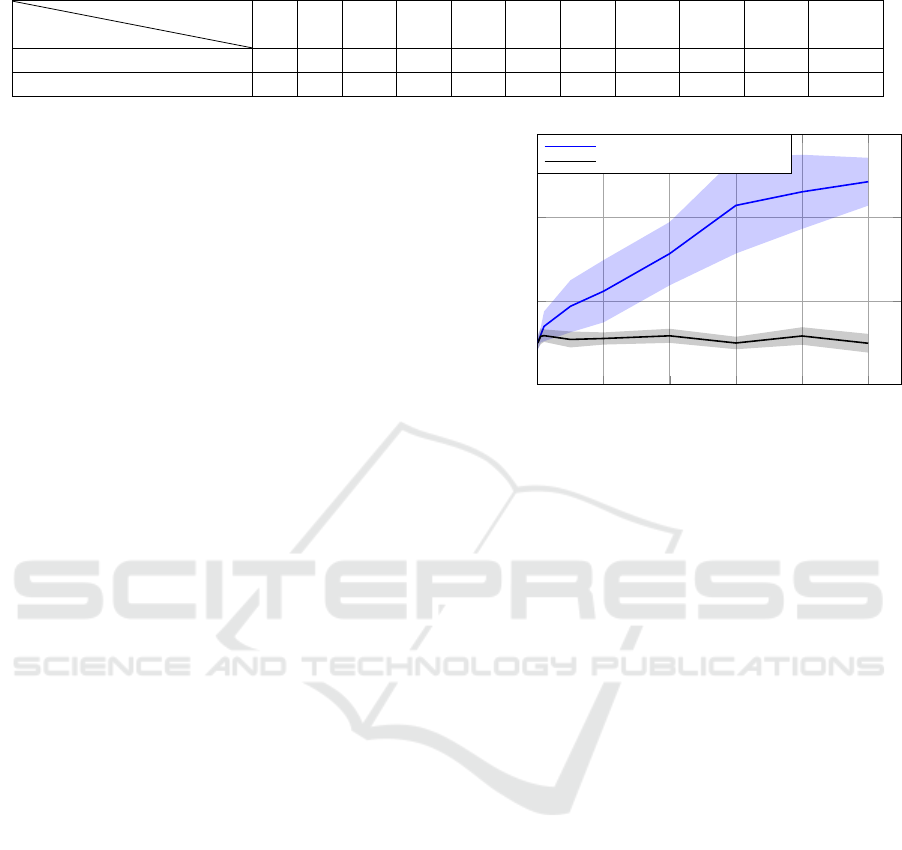
Table 1: Number of values between zero and 0.1 for different sample sizes.
Distribution
Sample size
10 50 100 200 300 400 600 1000 2000 5000 10000
U(u(0,2),u(3,5)) 0 0 0 0 0 0 1 1 2 2 7
U(0,5) 1 1 2 5 5 7 13 22 33 92 217
6.1 Dataset Construction
For the dataset collection, we calculated sequences of
RT T s based on ping replay timings between a sender
located in Morocco and two distant servers. The two
servers are respectively located in Rabat, Morocco
and California, spanning a significant distance of al-
most 9,645km. We focused exclusively on these two
locations to construct a dataset serving as a proof
of concept for the attack. We conducted measure-
ments at three different moments of the day: at 10:00,
12:00, and 16:30. During these measurements, we al-
ternated between Ethernet and cellular connections.
Similar to (Schnitzler et al., 2023), we accounted for
sequences of 5 RT T measurements. The dataset com-
prises 15,386 rows in total.
6.2 Minimum Value Based Attack
In our initial dataset, there are no random delays, re-
sulting in an accuracy of over 97% when training an
LST M model on it. From this dataset, we used a sub-
set containing 400 homogeneous data points for test-
ing purposes. We simulated the implementation of
the two randomization techniques and evaluated the
resulting accuracy of the attack.
For each RT T in the testing dataset, we sampled
a sequence of delays from U(u(0, 2),u(3,5)) (respec-
tively U(0,5)), and added their minimum to the RT T .
This process mimics an adversary attacking the solu-
tions using the min value. Subsequently, we trained
the LST M model on the non randomized dataset por-
tion and evaluated its accuracy on the randomized
portion. We conducted 20 rounds of training and pre-
diction for different sample sizes and represented the
mean accuracy along with the standard deviation in
Figure 7.
For U(0, 5), increasing the sample size signifi-
cantly enhances the attack accuracy. This is because,
with a larger number of samples, the probability of
obtaining minimum values closer to the real RT T s
becomes higher. Essentially, with more data points,
the likelihood of accurately estimating the RTT s, and
thus inferring the correct locations, increases. In sce-
narios where there are no restrictions on the num-
ber of messages that can be sent, such as with silent
SMSs, the attack can achieve an accuracy exceeding
90%. However, the situation is totally different when
0 200 400
600
800 1,000
40
60
80
100
Number of samples per location
Accuracy (%)
Mean Accuracy for U (0, 5)
Mean Accuracy for U (u(0, 2),u(3, 5))
Figure 7: Mean accuracy of minimum-based attack.
considering the distribution U(u(0,2),u(3, 5)). De-
spite increasing the sample size, the attack accuracy
remains close to 50%. Consequently, the attacker is
essentially making a binary decision, choosing be-
tween two potential locations with an accuracy being
near 50%. This indicates that the attack is no better
than random guessing.
6.3 Case of Unknown Distribution
Parameters
Previously, we demonstrated the difficulty in accu-
rately capturing the min, max, and mean values of
U(u(0,2),u(3,5)). Consequently, the accuracy of at-
tacks relying on these values is notably low, as ex-
emplified by the attack based on the minimum value.
Thus, conducting such an attack with this distribution
is unfeasible, especially when the parameters are un-
known beforehand. In this subsection, we will focus
on evaluating the feasibility of the attack when the
parameters of U(a,b) are unknown. As mentionned
before, the attacker can construct a dataset based on
RT T + cte, where cte is a, b, or (b − a)/2.
Initially, we shifted the dataset RT T s by the same
constant, and computed the accuracy for 20 rounds of
model training. We varied the shifting constant value
and plotted the mean accuracy along with its standard
deviation in Figure 8. The experimental results in-
dicate a notable decrease in accuracy as the shifting
constant increases demonstrating that even slight vari-
ations in dataset shifting can degrade performance.
SECRYPT 2025 - 22nd International Conference on Security and Cryptography
68
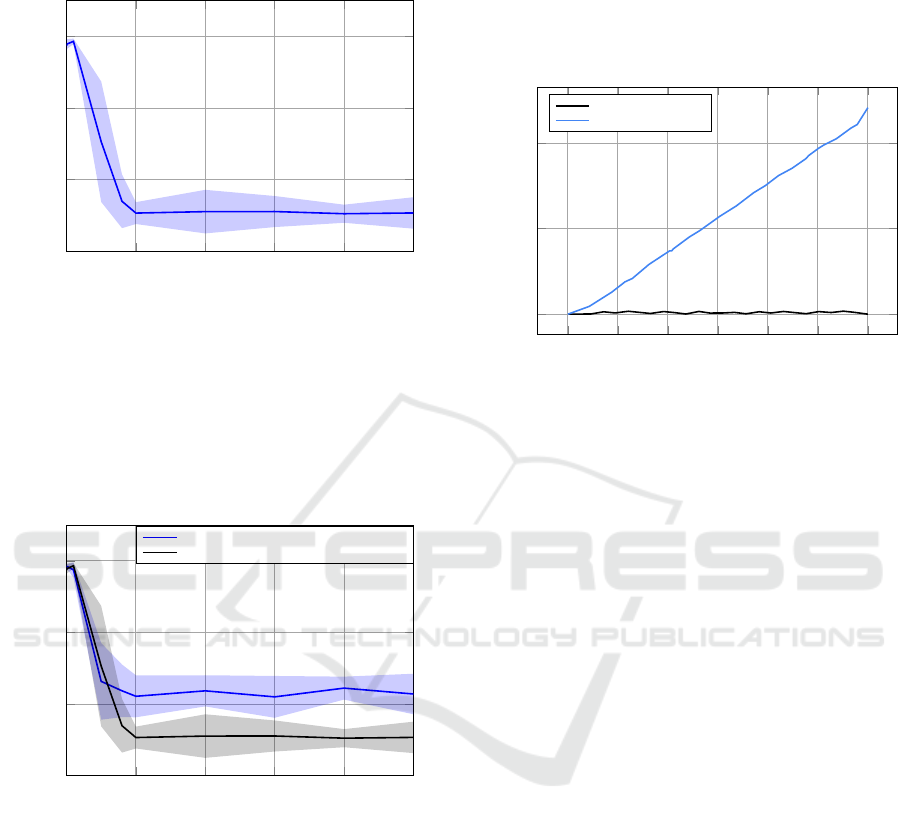
Particularly, the accuracy approaches approximately
50% when the shifting constant exceeds 1s (1000ms).
0 1,000 2,000 3,000 4,000
5,000
40
60
80
100
The shift constant in ms
Accuracy
Figure 8: Shift effect on accuracy.
We then normalized and standardized the shifted
dataset and re-evaluated the resulting accuracy. The
outcomes in Figure 9 reveal that this improves accu-
racy, stabilizing at approximately 64% for larger shift-
ing constants. This indicates that the attack is also fea-
sible in this scenario. However, the accuracy is lower
than conducting the attack with known parameters.
0 1,000 2,000 3,000 4,000
5,000
40
60
80
100
The shift constant in ms
Accuracy
Normalized and standardized datasets
Non-normalized and non-standardized datasets
Figure 9: Normalization and standardization.
6.4 Impact on the Messenger Server
As we theoretically demonstrated in Section 5.1, im-
plementing the solution on the server side would lead
to a degradation of server resources. To test this,
we created a server with a queue and simulated 1000
clients sending messages to this server. The clients
send messages and wait for a random duration be-
tween messages to mimic user behavior. This wait-
ing duration is sampled from a Poisson distribution
with the parameter 5. This indicates an average of
5 seconds between two consecutive messages. The
sent messages are placed into the server queue. We
considered two configurations: one where the server
introduces a random delay sampled from U(0,5), and
one without these delays. We recorded the evolu-
tion of the server queue size over one minute and
plotted the results in Figure 10. In the normal case,
0
10 20 30 40
50 60
0
0.5
1
·10
4
Time (s)
Queue size
Without random delays
With delays
Figure 10: Server queue size variation over time.
the server queue size fluctuates around zero, indicat-
ing efficient handling of incoming messages without
overhead. This means that the server processes mes-
sages at a rate that is equal to or greater than the arrival
rate, preventing any accumulation. However, when
random delays are introduced, the situation changes
significantly. The queue size increases linearly due to
message accumulation. This result is compatible with
Equation 9 with n
0
= 0 (n
0
is the initial number of
messages in the server). In this scenario, the reception
rate exceeds the server’s processing rate, causing mes-
sages to arrive faster than they can be handled, result-
ing in a continuously growing queue. This observa-
tion validates our theoretical findings, demonstrating
that the introduction of random delays substantially
affects server performance.
7 CONCLUSIONS AND FUTURE
WORK
This paper addresses the privacy concerns associated
with timing side-channel attacks on mobile messag-
ing applications and SMS services. Existing solu-
tions propose using uniform random delays to obfus-
cate Round Trip Times on the messenger server and
SMS core network sides. Our evaluation demonstrates
the persistence of the attack with significant accuracy
with this solution in place and showed the signifi-
cant impact it has on the messenger server and SMS
core network resources. We proposed a more resilient
client side randomization technique using a distribu-
A Resilient Randomization Technique Against ML-Driven Timing Side Channel Attack on Mobile Location
69

tion with randomly varying parameters across RT T
measurements. Through experimental validation, we
highlighted the effectiveness of our proposed solution
compared to the existing one.
However, we could not use the original dataset due
to privacy restrictions. Our illustrative dataset com-
prises RT T s derived from ping reply timings to con-
struct a POC of the attack. Therefore, the obtained
results may vary slightly if we were to use data based
on RT T s from messenger notifications or SMS deliv-
ery reports. Furthermore, our study has limitations
in the exploration of machine learning algorithms, as
we solely opted for an LST M model to demonstrate
the feasibility of the attack. Additionally, we only
focused on two locations in our work to construct a
Proof of Concept of the attack. As a future work, we
aspire to investigate the potential existence of timing
side-channel vulnerabilities in video and voice calls.
REFERENCES
Ahmed, A. A., Hasan, M. K., Aman, A. H., Safie, N., Islam,
S., Ahmed, F. R. A., and Rzayeva, L. (2024). Review
on hybrid deep learning models for enhancing encryp-
tion techniques against side channel attacks. IEEE Ac-
cess.
Ariano, R. (2020). ’what do the check marks mean on what-
sapp?’: How to determine the status of your message
on whatsapp. Accessed March 12, 2024.
Bateman, R. (2023). Privacy practices for user
location. https://www.termsfeed.com/blog/
user-location-privacy-practices/, as of April 2024.
Bitsikas, E., Schnitzler, T., P
¨
opper, C., and Ranganathan, A.
(2023). Freaky leaky sms: Extracting user locations
by analyzing sms timings. In 32nd USENIX Security
Symposium (USENIX Security 23), pages 2151–2168.
Bognar, M., Winderix, H., Bulck, J. V., and Piessens, F.
(2023). Microprofiler: Principled side-channel miti-
gation through microarchitectural profiling. In 2023
IEEE 8th European Symposium on Security and Pri-
vacy (EuroS&P), pages 651–670. IEEE.
Candela, M., Gregori, E., Luconi, V., and Vecchio, A.
(2019). Using ripe atlas for geolocating ip infrastruc-
ture. IEEE Access, 7:48816–48829.
Diamantaris, M., Moustakas, S., Sun, L., Ioannidis, S., and
Polakis, J. (2021). This sneaky piggy went to the an-
droid ad market: Misusing mobile sensors for stealthy
data exfiltration. In Proceedings of the 2021 ACM
SIGSAC Conference on Computer and Communica-
tions Security (CCS), pages 1065–1081.
Du, B., Candela, M., Huffaker, B., Snoeren, A. C., and
claffy, k. (2020). Ripe ipmap active geolocation:
Mechanism and performance evaluation. ACM SIG-
COMM Computer Communication Review, 50(1):4–
10.
Erata, F., Piskac, R., Mateu, V., and Szefer, J. (2023).
Towards automated detection of single-trace side-
channel vulnerabilities in constant-time cryptographic
code. In 2023 IEEE 8th European Symposium on Se-
curity and Privacy (EuroS&P), pages 687–706. IEEE.
Erni, S., Leu, P., Kotuliak, M., R
¨
oschlin, M., and Capkun,
S. (2021). Adaptover: Adaptive overshadowing of lte
signals. ArXiv, abs/2106.05039.
Fawaz, K. and Shin, K. G. (2014). Location privacy protec-
tion for smartphone users. In Proceedings of the 2014
ACM SIGSAC Conference on Computer and Commu-
nications Security, pages 239–250.
Han, X. et al. (2022). Location heartbleeding: The rise of
wi-fi spoofing attack via geolocation api. In Proceed-
ings of the 2022 ACM SIGSAC Conference on Com-
puter and Communications Security (CCS).
Hong, B., Bae, S., and Kim, Y. (2018). Guti reallocation
demystified: Cellular location tracking with chang-
ing temporary identifier. In 25th Annual Network and
Distributed System Security Symposium (NDSS 2018),
San Diego, California, USA.
Hussain, S. R., Echeverria, M., Chowdhury, O., Li, N., and
Bertino, E. (2019). Privacy attacks to the 4g and 5g
cellular paging protocols using side channel informa-
tion. Network and distributed systems security (NDSS)
symposium2019.
Katz-Bassett, E., John, J. P., Krishnamurthy, A., Wether-
all, D., Anderson, T., and Chawathe, Y. (2006). To-
wards ip geolocation using delay and topology mea-
surements. In ACM Internet Measurement Conference
(IMC ’06), pages 71–84, Rio de Janeiro, Brazil.
Kohls, K. and Diaz, C. (2022). Verloc: Verifiable local-
ization in decentralized systems. In USENIX Security
Symposium (USENIX ’22), Boston, MA, USA.
Kotuliak, M., Erni, S., Leu, P., R
¨
oschlin, M., and Capkun,
S. (2022). Ltrack: Stealthy tracking of mobile phones
in lte. In 31st USENIX Security Symposium (USENIX
Security 22), pages 1291–1306.
Lakshmanan, N., Budhdev, N., Kang, M. S., Chan, M. C.,
and Han, J. (2021). A stealthy location identifi-
cation attack exploiting carrier aggregation in cellu-
lar networks. In 30th USENIX Security Symposium
(USENIX Security 21), pages 3899–3916.
Loch, P. (2019). Whatsapp in the workplace. Accessed
April 2024.
Maar, L., Juffinger, J., Steinbauer, T., Gruss, D., and Man-
gard, S. (2025). Kernelsnitch: Side-channel attacks
on kernel data structures. In Network and Distributed
System Security Symposium 2025: NDSS 2025.
MacKay, D. J. (2003). Information theory, inference and
learning algorithms. Cambridge University Press.
Michalevsky, Y. et al. (2015). Powerspy: Location tracking
using mobile device power analysis. In 24th USENIX
Security Symposium (USENIX Security 15).
Miller, D., Abed Rabho, L., Awondo, P., de Vries, M.,
Duque, M., Garvey, P., Haapio-Kirk, L., Hawkins, C.,
Otaegui, A., Walton, S., et al. (2021). The global
smartphone: Beyond a youth technology. UCL Press.
Nassi, B., Vayner, O., Iluz, E., Nassi, D., Jancar, J., Genkin,
D., and Elovici, Y. (2023). Optical cryptanalysis: Re-
covering cryptographic keys from power led light fluc-
tuations. In Proceedings of the 2023 ACM SIGSAC
SECRYPT 2025 - 22nd International Conference on Security and Cryptography
70

Conference on Computer and Communications Secu-
rity, pages 268–280.
Oberhuber, M., Unterguggenberger, M., Maar, L., Kogler,
A., and Mangard, S. (2025). Power-related side-
channel attacks using the android sensor framework.
In Network and Distributed System Security Sympo-
sium 2025: NDSS 2025.
Peeters, C., Patton, C., Munyaka, I. N. S., Olszewski, D.,
Shrimpton, T., and Traynor, P. (2022). Sms otp secu-
rity (sos): Hardening sms-based two factor authenti-
cation. In ASIA CCS’22: ACM Asia Conference on
Computer and Communications Security, pages 2–16,
Nagasaki, Japan. ACM.
Pourali, S., Samarasinghe, N., and Mannan, M. (2022).
Hidden in plain sight: exploring encrypted channels
in android apps. In Proceedings of the 2022 ACM
SIGSAC Conference on Computer and Communica-
tions Security (CCS).
Purz, M. (2020). How governments world-
wide are using messaging apps in times of
covid-19. https://www.messengerpeople.com/
governments-worldwide-covid-19/, as of April 2024.
Reaves, B., Scaife, N., Tian, D., Blue, L., Traynor, P., and
Butler, K. R. B. (2016). Sending out an sms: Charac-
terizing the security of the sms ecosystem with public
gateways. In IEEE Symposium on Security and Pri-
vacy (SP), pages 339–356, San Jose, CA, USA. IEEE
Computer Society.
Reaves, B., Vargas, L., Scaife, N., Tian, D., Blue, L.,
Traynor, P., and Butler, K. R. B. (2019). Character-
izing the security of the sms ecosystem with public
gateways. ACM Transactions on Privacy and Secu-
rity, 22(1):2:1–2:31.
Rodrigues, C., Oliveira, D., and Pinto, S. (2024). Busted!!!
microarchitectural side-channel attacks on the mcu
bus interconnect. In 2024 IEEE Symposium on Se-
curity and Privacy (SP), pages 3679–3696. IEEE.
Schnitzler, T., Kohls, K., Bitsikas, E., and P
¨
opper, C.
(2023). Hope of delivery: Extracting user locations
from mobile instant messengers. In Network and
Distributed System Security Symposium (NDSS), San
Diego, CA, USA. The Internet Society.
Wang, Z., Guan, J., Wang, X., Wang, W., Xing, L., and
Alharbi, F. (2023). The danger of minimum expo-
sures: Understanding cross-app information leaks on
ios through multi-side-channel learning. In Proceed-
ings of the 2023 ACM SIGSAC Conference on Com-
puter and Communications Security, pages 281–295.
Yang, H., Bae, S., Son, M., Kim, H., Kim, S. M., and Kim,
Y. (2019). Hiding in plain signal: Physical signal
overshadowing attack on lte. In 28th USENIX Secu-
rity Symposium (USENIX Security 19), pages 55–72,
Santa Clara, CA. USENIX Association.
Zhang, J., Chen, C., Cui, J., and Li, K. (2024). Timing side-
channel attacks and countermeasures in cpu microar-
chitectures. ACM Computing Surveys, 56(7):1–40.
A Resilient Randomization Technique Against ML-Driven Timing Side Channel Attack on Mobile Location
71
