Quantum-Resilient IoT: Integrating Hardware-Based Post-Quantum
Cryptography for Robust Device Security
Stephan Spitz
1
, Alexander Lawall
1
and Michal Andrzejczak
2
1
IU International University of Applied Science, Juri-Gagarin-Ring 152, 99084 Erfurt, Germany
2
Resquant, Narutowicza 40 / 1, 90-135 Lodz, Poland
Keywords:
Silicon-Integrated Post-Quantum Cryptographic Cores, Applied Post-Quantum Cryptography, Internet of
Things (IoT) Security, Industrial Internet of Things (IIoT) Security.
Abstract:
The evolution of quantum computers necessitates the reevaluation of cryptographic standards, especially
within the Internet of Things (IoT) infrastructures, where long-term security is critical. Current cryptographic
algorithms, such as RSA, are vulnerable to quantum attacks, highlighting the need for post-quantum crypto-
graphic (PQC) solutions. This paper explores the integration of PQC Cores into System-on-a-Chip (SoC) ar-
chitectures to enhance the security of IoT devices. The foundation is a crypto-agile Root-of-Trust (RoT), these
integrated PQC solutions provide robust lifecycle management, secure boot processes, and protection against
quantum-based threats. The paper discusses the architectural considerations for integrating PQC, including se-
cure boot, lifecycle management, and the role of RoT in ensuring device integrity and secure communications.
The research findings emphasize the importance of PQC in safeguarding IoT infrastructures from emerging
quantum threats and demonstrate how hardware-based PQC implementations offer superior security compared
to software-based counterparts, particularly in the context of side-channel attack mitigation.
1 INTRODUCTION
The evolution of quantum computers will demand
an update of security mechanisms, which are funda-
mental in communication protocols and IT processes.
This is especially valid for mechanisms built on cryp-
tographic primitives (Tiwari et al., 2024). There
exists, for example, the Shor-Algorithm (Skosana,
2021) for the factorization of large primes that solves
the foundational challenge on which the RSA (Rivest
Shamir Adleman) algorithm (Rivest et al., 1978) has
been built. Similarly, currently used asymmetric
ciphers are affected once quantum computers offer
sufficient computing capabilities that are based on
qubits. For breaking the RSA cipher with the Shor-
Algorithm, at least 4000 qubits are required for a
2048-bit key (Roetteler et al., 2017) whereas topi-
cal quantum computers have just surpassed the 1000
qubits (Quantum, 2023). For this reason, RSA ciphers
with 512-bit key length can no longer be considered
secure.
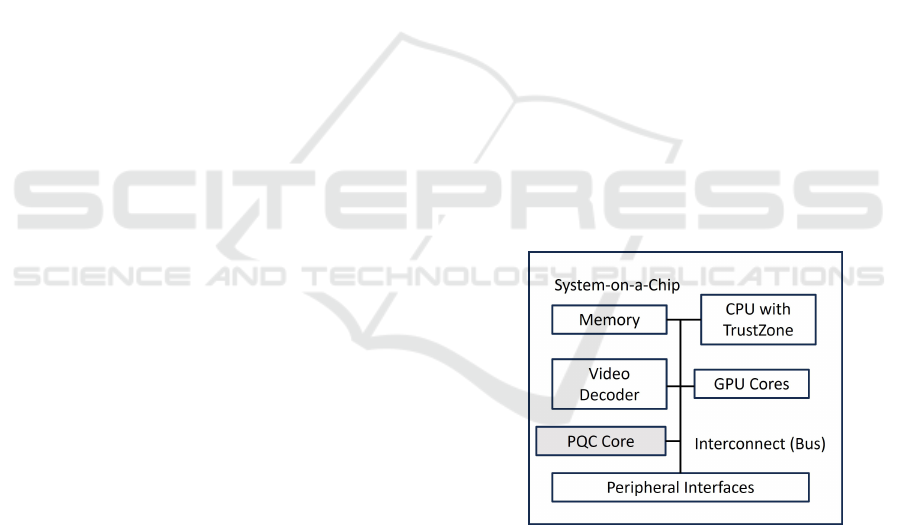
Figure 1: Integration of a Post-Quantum Cryptographic
Core in a System-on-a-Chip.
2 THE TECHNOLOGY STACK
This section describes the foundation for linking se-
curity services on the application level to an inte-
grated Post-Quantum Cryptographic (PQC) Core (Za-
gala and Andrzejczak, 2024) in a System-on-a-Chip
(SoC). A dedicated technology stack is required link-
ing the PQC Core via a processor bus to security ser-
vices running in a TrustZone (Arm, 2018) or another
Spitz, S., Lawall, A. and Andrzejczak, M.
Quantum-Resilient IoT: Integrating Hardware-Based Post-Quantum Cr yptography for Robust Device Security.
DOI: 10.5220/0013091100003899
In Proceedings of the 11th International Conference on Information Systems Security and Privacy (ICISSP 2025) - Volume 2, pages 419-424
ISBN: 978-989-758-735-1; ISSN: 2184-4356
Copyright © 2025 by Paper published under CC license (CC BY-NC-ND 4.0)
419
Security Enclave on the main CPU, cf. Figure 1.
An integrated PQC Core needs to interact with
secure software that is executed in a protected envi-
ronment such as TrustZone. This ensures that only
a higher privileged and protected process can use the
PQC algorithms and that cryptographic keys are suf-
ficiently protected.
2.1 Crypto Support of Secure Services
Concurrency of the security services is necessary be-
cause services executed in the richOS or Real-Time
OS (RTOS) require parallel access to PQC crypto
routines and cryptographic keys (Spitz, 2012). Con-
sequently, the new security subsystem including the
PQC Core must support high bandwidth commu-
nication, multitasking and multithreading. Secure
concurrent communication over the Internet Protocol
(IP), e.g. Transport Layer Security (TLS) demands
the handshake asynchronous encryption and signa-
ture verification processes performed in the Secure
OS. Large vendors such as IBM and Google are al-
ready working on PQC-enabled TLS Cipher Suites
(Pursche et al., 2024), (Westerbaan, 2024) in their
products. In contrast, the Internet Engineering Task
Force (IETF) is currently working on standardizing
TLS with hybrid modes (Stebila et al., 2024), where
classical cryptography is used in combination with
post-quantum algorithms.
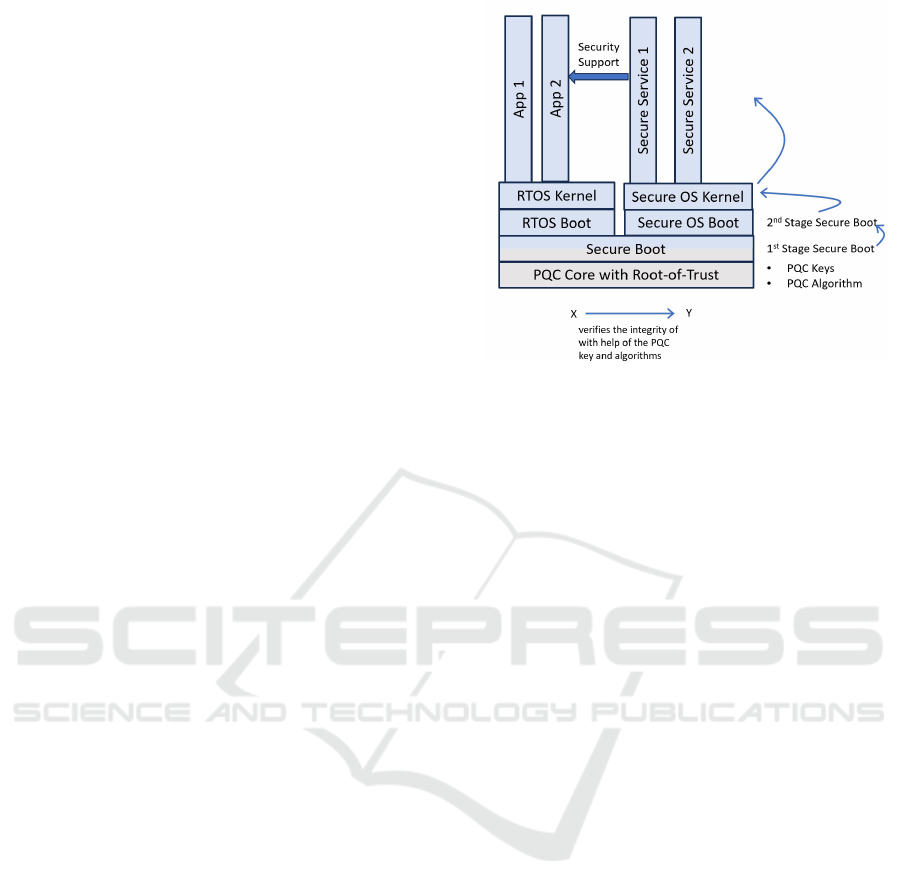
2.2 Secure Boot
Another important aspect is the PQC Core integration
in the boot process, cf. Figure 2. The SoC-integrated
PQC Core is booted together with the SoC firmware
before the richOS/RTOS starts execution. This re-
sults in a security-critical dependency of the entire
boot process on the PQC Core. The authenticity of
the firmware and communication stack must be vali-
dated during the SoC’s Secure Boot process to ensure
that no altered or compromised software or firmware
is loaded by a potential attacker. Moreover, the verifi-
cation procedure must be reliable and verified. Thus,
a full hardware implementation (based only on ded-
icated circuits without any program) of PQC algo-
rithms used in Secure Boot for signature verification
must be performed. The circuit responsible for this
part is verified with formal methods in the pre-silicon
stage and is the security foundation for Secure Boot.
The involved keys and code require the following
protection:
• Integrity protection of the PQC public keys for
code integrity verification
Figure 2: Staged Verification during the Boot with the PQC
Core providing the Foundation.
• Integrity protection of the code doing the verifica-
tion, which is part of the first stage bootloader
• Monotonic Counters which are used to invalidate
old firmware and allow updates of the second-
stage bootloader code
The entire SoC must exhibit tamper resistance, with
particular emphasis on the cryptographic core. Sim-
ilar to Smart Card semiconductors, security-critical
components must be safeguarded through active
countermeasures such as metal shielding, scrambled
data buses, or sensors designed to detect attacks.
These requirements introduce significant challenges
to chip architecture and standard silicon fabrication
processes.(Arm, 2018). A challenge for PQC is
side-channel protection where additional leakage (e.g.
thermal, timing and power) can be used to compro-
mise used keys. To face this threat, several addi-
tional countermeasures are adopted, slowing down al-
gorithms up to several times (Migliore et al., 2019).
However, hardware implementations of PQC offer
more ways to implement countermeasures compared
to software implementations and are also more effi-
cient. The generic SoC manufacturing processes must
be enhanced to establish the necessary cryptographic
and security infrastructure, particularly for the Secure
Boot mechanism (IAR, 2018). The establishment of
the Root-of-Trust (RoT) serves as the foundational se-
curity element for Secure Boot and all subsequent se-
curity processes, including the deployment and load-
ing of the Secure OS, as well as individualization and
penalization procedures. As personal devices like a
wearable or smartphone get into the hands of users at
a later stage, accounts are personalized in an insecure
environment. The RoT ensures a reliable device iden-
tity and enables attestation services to bootstrap user
identities and user authentication in the field.
ICISSP 2025 - 11th International Conference on Information Systems Security and Privacy
420

3 ARCHITECTURAL CONCEPTS
3.1 Considerations on PQC Integration
SoC-integrated security solutions have an impact on
the whole technology stack, which is built in bare
metal (Spitz and Lawall, 2024). One important aspect
is the reentrance of the PQC Core to support mul-
tiple cryptographic operations on the software layer.
In the operating system, multitasking enables se-
cure encrypted and authenticated asynchronous high-
bandwidth communication (Safe, 2024). There are
different possibilities to connect an IoT device se-
curely to the Internet. The operating system archi-
tecture must account for the integration of the PQC
Core, providing appropriate drivers and protocols to
facilitate its interaction. At higher software layers,
asynchronous communication is managed through a
mailbox mechanism, enabling the exchange of large
volumes of data between security-critical and non-
critical processes within a designated memory space.
Another security-critical piece of functions closely
linked to the PQC Core is system calls, which are
mapped to the cryptographic support in hardware.
The entry point is the OS Kernel which contains
the necessary routines for accessing the PQC Core
e.g. for verifying the integrity of applications that are
scheduled for execution by the OS Kernel. An exam-
ple of such a service is the Samsung TIMA (Trusted
Integrity Management Architecture) (Snyder, 2019)
on Android smartphones. TIMA issues system calls
to the services that are securely executed by the Se-
cure OS running in the TrustZone of the SoC. One
reason for such system calls is the run-time integrity
protection of the OS Kernel itself and security-critical
applications to avoid fraudulent modifications in the
code, e.g. to bypass rights management. Typically,
the Secure OS is loaded from flash memory in an early
boot stage and initialized with the cryptographic keys
stored in the PQC Core. Especially with Dilithium the
key length of up to 4864 bytes for the private key has
to be considered when storing keys in the secret mem-
ory of the PQC Core. Nevertheless, sufficient flash
memory seems not to be an issue on modern SOCs
whereas the SRAM (i.e. Cortex-M4) reaches in some
cases its limitations during the execution of Dilithium
with these key lengths. Large key sizes can be a chal-
lenge for more constrained devices. Long-term stor-
age techniques for generating keys from master seed
might be applied, but this won’t solve issues with a
lack of MCU’s internal memory. In that case, specific
implementation techniques or dedicated hardware cir-
cuits should be developed. The main OS Kernel is
booted after the complete security subsystem consist-
ing of the Secure OS, Secure Services and the PQC
Core have been initialized. Thus, attacks on the OS
Kernel can hardly circumvent the Secure OS or tam-
per the PQC Core in hardware. The essential mas-
ter keys, integrity protection and verification mech-
anisms are part of the PQC Core because this of-
fers protection in hardware (Zagala and Andrzejczak,
2024).
3.2 Overall SoC Security Architecture
A single PQC Core is insufficient for ensuring the
security of an SoC. Strong hardware-based isolation
mechanisms are crucial, such as Arm TrustZone or a
dedicated secure processor core like the ARC SEM
(Synopsys, 2016). Additionally, security-critical SoC
components, including memory and I/O peripherals,
can be isolated from standard processing elements
and accessed exclusively in a secure execution mode.
Countermeasures against fault injection and side-
channel attacks are essential in any hardware secu-
rity solution. Since generic silicon fabrication pro-
cesses offer limited support for such protections, the
security features embedded in hardware and firmware
become increasingly critical. Firmware plays a key
role in safeguarding access to the PQC Core with se-
curity boundaries established during platform boot.
Integrity checks must be performed for all low-level
drivers and firmware components, particularly for the
driver interfacing with the PQC Core. A staged secure
boot process is needed to initialize all secure process-
ing elements before activating standard components,
ensuring that standard operations do not compromise
security settings or access to critical cryptographic
keys and functions.
4 LIFECYCLE MANAGEMENT
OF INTEGRATED SECURITY
SOLUTIONS
4.1 The Role of a Root-of-Trust
A robust RoT, integrated with the PQC Core, serves
as the foundational security anchor for software
lifecycle management and update processes (IAR,
2018). Lifecycle management encompasses the de-
ployment, modification, and complete removal of
security-critical code and data, particularly informa-
tion related to device identity and access control roles.
This identity-related data may pertain to the device it-
self or the roles governing access management.
Furthermore, a RoT is essential for establishing a
Quantum-Resilient IoT: Integrating Hardware-Based Post-Quantum Cryptography for Robust Device Security
421
secure communication channel with the device, en-
abling the provisioning of identities even when the
device operates in an untrusted environment. Lever-
aging the RoT, an authenticated and secure channel
can be established, facilitating the secure download
of sensitive data, such as during maintenance opera-
tions, even when the device is already deployed in the
field. The RoT provides the cryptographic foundation
required for securely binding the device to an external
trusted entity through a cryptographic handshake. A
RoT can be based on the following asymmetric and
symmetric keys:
• Crypto-Agility with a symmetric master key pre-
seeded for exchange of the asymmetric keys and
algorithms
• XMSS/LMS or SPHINCS+ public key for boot
chain integrity verification
• CRYSTALS-Dilithium private key for Remote
Attestation
• CRYSTALS-Dilithium public key for Remote
Authentication. XMSS is best suited for BLOB
updates.
• CRYSTALS-Kyber public key for a secure key
exchange of a temporary symmetric key for Data
Confidentiality
The RoT can be also located outside the PQC Core
in the protected memory of the SoC. The RoT must
be established in a secure process in a secure envi-
ronment. At least, the AES256 (National Institute of
Standards and Technology, 2001) secret must be pre-
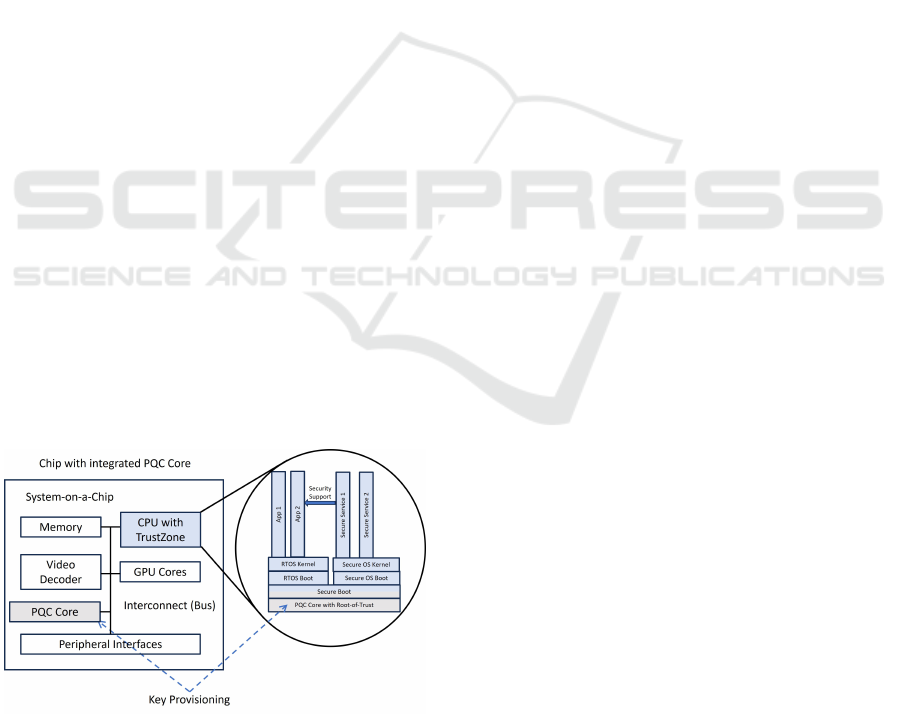
seeded with the first part of the bootloader. A staged
secure bootloader incorporating the RoT is respon-
sible for the integrity of the whole SoC and all the
software executed on the device. Such a bootloader
is typically organized in a first and second stage, cf.
Figure 3.
Figure 3: Key Provisioning for seeding a Root-of-Trust.
The PQC Cores have the necessary capabilities to
protect the PQC master keys and at least one symmet-
ric secret, preferably an AES256 symmetric key. This
symmetric key has to be protected in the best possi-
ble way in the device and the infrastructure for device
management. Furthermore, it should be device indi-
vidual, because it allows the exchange of the other
asymmetric PQC keys in the PQC Core. Lattice-
base cryptography is relatively new in the field and
first attacks on implementations have already been
discovered(IAR, 2018). Utilizing a symmetric key
allows for the exchange of a compromised key or
a transition from lattice-based algorithms, such as
CRYSTALS-Dilithium or Kyber, to SPHINCS+, a
hash-based asymmetric algorithm. It is worth it to
recap that the public PQC keys just require integrity
protection because this information needs not to be
kept confidential. Private and symmetric keys should
be device individual and highly confidentiality pro-
tected.
4.2 Lifecycle Management Operations
For the secure lifecycle management of an IT system,
the following aspects matter:
• Integrity verification including remote identity
proof, cf. (Sundar et al., 2019)
• Protection of the code and data during loading and
runtime, especially protection of the Secure OS,
from fraudulent modifications cf. (Wang et al.,
2019)
• User and Access Management including the op-
tion to assign individual rights to selected users.
This starts with the establishment of initial user
accounts with the necessary authentication meth-
ods.
• AA-functionality (Authentication/Authorization)
of configuration changes, code updates, especially
security-relevant settings
• Delegation of control to third parties, especially
with the change of ownership
• Secure disabling of single accounts or the com-
plete system e.g. for end-of-life, over-production
control, and grey market prevention
• Initial setup of secure communication channels
for different kinds kind of lifecycle operations, es-
pecially updates or configuration changes
The processes mentioned above contain all the fol-
lowing basic cryptographic routines:
• a) Identification of the IoT device
• b) Authorisation of a lifecycle action e.g. software
update
• c) Authentication of a user or even an individual
task
ICISSP 2025 - 11th International Conference on Information Systems Security and Privacy
422
• d) Ensuring secrecy of code or data in transit and
rest
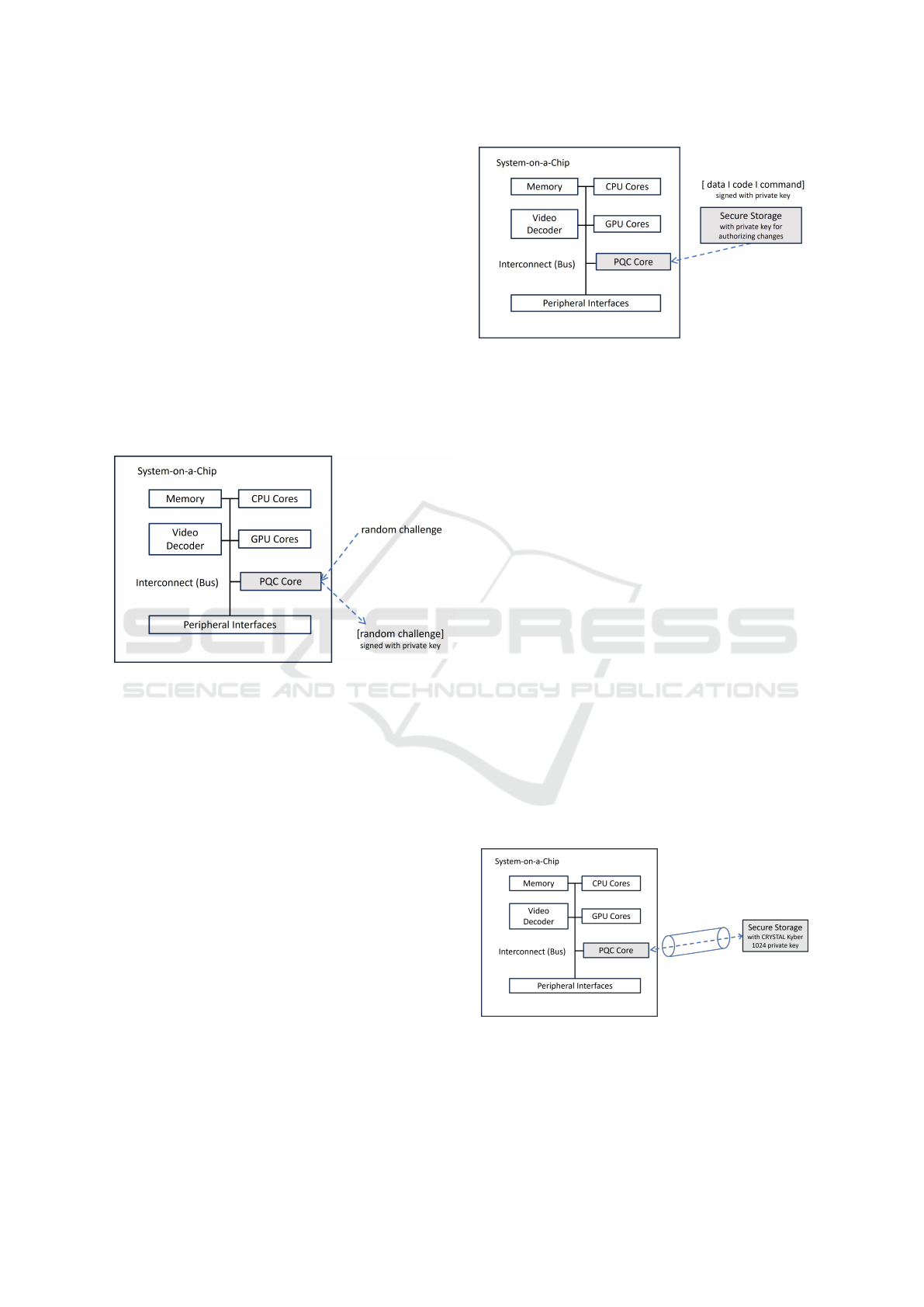
4.2.1 Identification of a System-on-a-Chip
In scenario a), the RoT may include an identity and
a private key, which are securely stored in the PQC
Core during the manufacturing process, as illustrated
in Figure 4. Subsequently, the Secure OS within the
device receives a request to authenticate the device
and attest its identity. This request is accompanied by
a random number which the Secure OS signs using
the private key stored in the RoT. The verifying entity
external to the device can then decrypt the response
utilizing the corresponding public key. The device
successfully demonstrates its identity if the decrypted
result matches the initial random challenge.
Figure 4: Device Identity Verification.
4.2.2 Authorisation and Authentication of an
Administrative Action
In scenarios b) and c), the roles are reversed, with the
RoT containing a public key, as depicted in Figure 5.
In this case, the external entity possesses a private key,
enabling it to authorize administrative actions, deploy
code, or perform read/write operations within the Se-
cure OS. The issuer of the administrative action is au-
tomatically identified in this scenario, as the private
key can be uniquely associated with an individual, le-
gal entity, or IT system. This association is estab-
lished through a Public Key Infrastructure (PKI). It is
important to note that, in this context, the public key
on the device must be protected against modifications
and unauthorized exchanges, although confidentiality
protection is not a requirement. The RoT must ensure
integrity protection, allowing only the Secure OS on
the device to have read access to this public key.
4.2.3 Confidentiality Protection of Data
Scenario d) necessitates the use of a hybrid encryption
scheme, which combines both symmetric and asym-
Figure 5: Authorisation of Remote Management.
metric encryption methods. This is due to the perfor-
mance limitations of asymmetric algorithms, which
are not well-suited for encrypting large volumes of
data, as illustrated in Figure 6. In this hybrid ap-
proach, a symmetric key is temporarily generated and
transmitted alongside the encrypted data to the de-
vice. The symmetric key itself is further encrypted
using the public key of the device, ensuring its confi-
dentiality during transmission. The Secure OS, which
has access to the device’s private key stored within
the RoT, performs two critical operations: first, it de-
crypts the encrypted symmetric key using its private
key, and second, it employs the decrypted symmetric
key to encrypt and decrypt the data. This scenario is
particularly pertinent when transmitting personaliza-
tion data to the device, such as subscriber profiles for
integrated SIM cards (ETSI, 2017) or payment cre-
dentials for Integrated Secure Elements (iSEs). The
use of a hybrid encryption scheme enhances secu-
rity while maintaining efficiency for scenarios requir-
ing the secure handling of sensitive information. By
leveraging the strengths of both encryption methods,
this approach not only safeguards data confidential-
ity but also ensures that the process remains compu-
tationally feasible, thus enabling seamless operations
in resource-constrained environments.
Figure 6: Confidentiality Protection.
Quantum-Resilient IoT: Integrating Hardware-Based Post-Quantum Cryptography for Robust Device Security
423

5 CONCLUSION
Due to the advances of quantum computers, System-
on-a-Chip manufacturers need to consider designing
a Post-Quantum Cryptographic Core that offers long-
term sustainability for the security of the lifecycle
management of the whole IoT device. It is important
to implement crypto agility with exchangeable PQC
keys and algorithms which can be leveraged to pro-
tect for a long-term all relevant services running on
the IoT device. The PQC Core forms the foundation
of a modern Root-of-Trust which protects the IoT de-
vices against many kinds of attacks. To fully leverage
protection capabilities, it is essential to integrate the
PQC Core across the entire chain, from hardware to
the software services running on the IoT device’s op-
erating system and within the supporting infrastruc-
ture. There should be no weak element in this chain
and integrity verification is an important aspect to en-
sure this. Last but not least, PQC is more vulnera-
ble to sophisticated side-channel attacks than the out-
dated classical asymmetric ciphers such as RSA and
ECC. However, recent developments show that it is
possible to implement mechanisms to achieve tamper
resistance also with PQC Cores (Zagala and Andrze-
jczak, 2024).
REFERENCES
Arm (2018). Cortex-m35p a tamper-resistant
cortex-m processor with optional software
isolation using trustzone for armv8-m. In
https://developer.arm.com/products/processors/cortex-
m/cortex-m35p. Arm.
ETSI (2017). iuicc poc group primary plat-
form requirements, approved release.
In https://www.gsma.com/newsroom/wp-
content/uploads/UIC.03 v1.0.pdf. ETSI.
IAR (2018). Building a supply chain of
trust: Understanding secure mastering. In
https://www.iar.com/support/resources/articles/secure-
mastering. IAR.
Migliore, V., G
´
erard, B., Tibouchi, M., and Fouque, P.-A.
(2019). Masking dilithium. In Deng, R. H., Gauthier-
Uma
˜
na, V., Ochoa, M., and Yung, M., editors, Applied
Cryptography and Network Security, pages 344–362,
Cham. Springer International Publishing.
National Institute of Standards and Technology (2001). Ad-
vanced encryption standard (aes). FIPS Publication
197, U.S. Department of Commerce.
Pursche, M., Puch, N., Peters, S. N., and Heinl, M. P.
(2024). SoK: The engineer’s guide to post-quantum
cryptography for embedded devices. Cryptology
ePrint Archive, Paper 2024/1345.
Quantum, I. (2023). The quantum decade: Ibm’s quantum
roadmap to 2033. Accessed: 2024-08-19.
Rivest, R. L., Shamir, A., and Adleman, L. (1978). A
method for obtaining digital signatures and public-
key cryptosystems. Communications of the ACM,
21(2):120–126.
Roetteler, M., Naehrig, M., Svore, K. M., and Lauter, K.
(2017). Quantum resource estimates for computing el-
liptic curve discrete logarithms. In International Con-
ference on the Theory and Applications of Cryptology
and Information Security (ASIACRYPT 2017), pages
241–270. Springer.
Safe, O. Q. (2024). Tls. In
https://openquantumsafe.org/applications/tls.html.
Resquant.
Skosana, T. (2021). Demonstration of shor’s factoring algo-
rithm for n=21 on ibm quantum processors. In 2021
Scientific Article number: 16599, pages 1–4. Springer.
Snyder, J. (2019). Samsung trusted boot and trust-
zone integrity management explained. In
”https://insights.samsung.com/2019/09/04/samsung-
trusted-boot-and-trustzone-integrity-management-
explained/”. Samsung.
Spitz, S. (2012). Mobicore® secure os for arm® trustzone®
soc. In https://prezi.com/rgrvv8vv-t4s/mobicore-
secure-os-for-arm-trustzone-soc/. Prezi.
Spitz, S. and Lawall, A. (2024). Silicon-integrated secu-
rity solutions driving iot security. In Proceedings of
the 10th International Conference on Information Sys-
tems Security and Privacy - Volume 1: ICISSP, pages
398–402. INSTICC, SciTePress.
Stebila, D., Fluhrer, S., and Gueron, S. (2024). Hybrid
key exchange in TLS 1.3. Internet-Draft draft-ietf-tls-
hybrid-design-10, Internet Engineering Task Force.
Work in Progress.
Sundar, S., Yellai, P., Sanagapati, S. S. S., Pradhan, P. C.,
et al. (2019). Remote attestation based software in-
tegrity of iot devices. In 2019 IEEE International
Conference on Advanced Networks and Telecommu-
nications Systems (ANTS), pages 1–4. IEEE.
Synopsys (2016). Designware arc sem security processors.
In https://www.synopsys.com/dw/ipdir.php?ds=arc-
sem. Synopsys.
Tiwari, A., Chauhan, R., Joshi, N., Devliyal, S., Aluvala,
S., and Kumar, A. (2024). The quantum threat: Impli-
cations for data security and the rise of post-quantum
cryptography. 2024 IEEE 9th International Confer-
ence for Convergence in Technology (I2CT), pages 1–
7.
Wang, W., Zhang, X., Hao, Q., Zhang, Z., Xu, B., Dong,
H., Xia, T., and Wang, X. (2019). Hardware-enhanced
protection for the runtime data security in embedded
systems. Electronics, 8(1):52.
Westerbaan, B. (2024). The state of the post-quantum inter-
net. Accessed: 2024-09-05.
Zagala, S. and Andrzejczak, M. (2024). Post-Quantum
Cryptography IP Cores.
ICISSP 2025 - 11th International Conference on Information Systems Security and Privacy
424
