
Enhancing Blockchain Security: An Analysis of Encryption
Technologies and Future Directions
Yefan Chang
a
Department of Computer Science, University of Liverpool, Liverpool, U.K.
Keywords: Blockchain, Encryption, Public-Key Cryptography, Quantum Computing.
Abstract: This paper provides an in-depth analysis of encryption technology within blockchain, emphasizing the pivotal
roles of public-key cryptography and hash functions in ensuring data security, integrity, and privacy. It
explores how public-key cryptography facilitates secure data transmission and user authentication, while also
highlighting the significance of hash functions in maintaining data immutability across blockchain systems.
By examining established blockchain platforms such as Bitcoin and Ethereum, the study uncovers the
practical challenges faced by these encryption technologies, including high computational complexity,
susceptibility to collision attacks, and emerging threats from quantum computing. Through experimental
evaluations, the paper identifies significant limitations in encryption technologies related to scalability,
efficiency, and resilience against quantum threats. Future research directions will prioritize the development
of more efficient encryption algorithms, particularly enhanced methods of Elliptic Curve Cryptography (ECC),
and the exploration of quantum-resistant encryption techniques. Additionally, integrating privacy-preserving
technologies such as Zero-Knowledge Proofs (ZKPs) with blockchain scalability solutions, including
sharding and sidechains, will be crucial for future advancements. The findings of this study aim to inform
strategies for enhancing the performance and security of blockchain encryption technologies, providing
valuable guidance for their application in an evolving digital economy.
1 INTRODUCTION
Blockchain technology was initially introduced as the
foundational infrastructure for cryptocurrencies like
Bitcoin. However, it has now developed into a
versatile platform that enables secure and
decentralized data handling in numerous industries,
such as finance, healthcare, and supply chain
management (Wüst and Gervais, 2018). The core
strength of blockchain lies in its reliance on
cryptographic techniques, which ensure data
integrity, privacy, and establish trust within a
distributed system (Pilkington, 2016). Through the
application of encryption methods, blockchain
eliminates the need for centralized authorities by
allowing participants to verify transactions and
exchange information securely (Zhang et.al, 2019).
This ability to establish trust in an untrusted
environment has positioned blockchain as a key
innovation in the digital economy, fostering
developments in decentralized applications (DApps)
a
https://orcid.org/0009-0001-6184-3824
and smart contracts (Casey et.al, 2018). As a result,
understanding the cryptographic methods that secure
blockchain transactions is critical for both advancing
the technology and ensuring its widespread adoption
in sensitive industries.
Over the past decade, extensive studies have been
conducted in the area of blockchain encryption, with
a particular emphasis on public-key cryptography and
hash functions. Public-key cryptography, which
depends on asymmetric encryption methods, is
commonly used to create digital signatures, ensuring
that transactions can be authenticated and validated
by participants on the network (Hellman, 1978). This
cryptography is crucial for protecting the data
exchanged within the blockchain, preventing
unauthorized access, and safeguarding user privacy
(Hellman, 2002). In parallel, hash functions play a
vital role in maintaining data integrity by producing
unique outputs (hashes) for each block of data within
the blockchain (Sobti and Geetha, 2012). These
cryptographic hashes are employed to link blocks,
506
Chang and Y.
Enhancing Blockchain Security: An Analysis of Encryption Technologies and Future Directions.
DOI: 10.5220/0013527300004619
In Proceedings of the 2nd International Conference on Data Analysis and Machine Learning (DAML 2024), pages 506-510
ISBN: 978-989-758-754-2
Copyright © 2025 by Paper published under CC license (CC BY-NC-ND 4.0)
making it computationally infeasible to modify any
previous block without detection (Preneel, 1993).
Researchers have also explored advanced
cryptographic approaches like zero-knowledge
proofs (ZKPs) and elliptic curve cryptography (ECC),
both of which enhance security and scalability for
blockchain networks (Fiege et.al, 1987). ZKPs allow
users to verify information without revealing the
actual data, offering privacy-preserving solutions for
sensitive applications. Meanwhile, ECC is well-
respected for offering an equivalent level of security
to conventional methods, but with much smaller key
sizes, which reduces the computational resources
needed for encryption (Amara and Siad, 2011).
The key aim of this study is to perform a
comprehensive evaluation of blockchain encryption,
focusing specifically on public-key cryptography and
hash functions. The research begins by examining the
foundational principles of cryptography, followed by
an in-depth discussion of the cryptographic methods
applied in blockchain systems. This study assesses
the practical performance of these methods by
providing a thorough analysis of their benefits and
limitations. Additionally, the research investigates
the future potential of blockchain encryption, taking
into account new trends and technologies that may
influence its development. By reviewing current
literature and analyzing case studies, this study seeks
to offer valuable insights into the present state of
blockchain encryption, emphasizing its role in
maintaining data integrity and security within
blockchain infrastructures. Finally, the results of this
research aim to deepen the understanding of the
cryptographic framework of blockchain technology
and propose a foundation for future advancements in
encryption techniques.
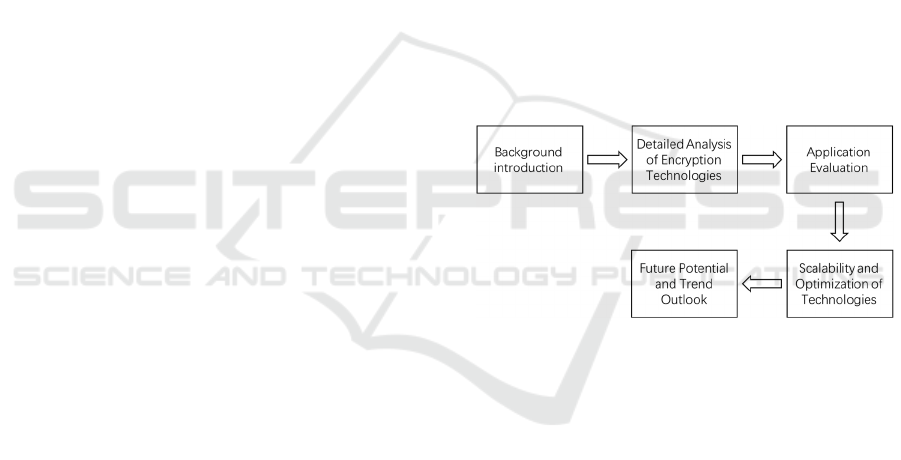
2 METHODOLOGIES
This paper begins by reviewing and summarizing the
key concepts and historical background of blockchain
encryption technologies, highlighting how they
ensure the security, privacy, and data integrity of the
network. The pipeline is shown in the Figure 1. It then
provides a detailed analysis of the cryptographic
principles underlying public-key cryptography and
hash functions. Public-key cryptography, also known
as asymmetric encryption, plays a critical role in
digital signatures, transaction verification, and
identity authentication, while hash functions maintain
data immutability by packaging, linking, and
verifying information. Next, the paper evaluates the
application of these encryption technologies within
blockchain systems such as Bitcoin and Ethereum. It
analyzes their performance across various scenarios,
including transaction verification speed, resource
consumption, and overall security. Additionally, the
scalability of these technologies for large-scale
applications will be explored, along with strategies
for optimizing encryption algorithms to enhance
blockchain processing capabilities. Following a
thorough assessment of the strengths and weaknesses
of these technologies, the paper discusses their future
potential. By examining current technological trends
and recent research developments, it predicts future
applications in blockchain and proposes potential
improvements, including the development of more
efficient encryption algorithms and solutions to
address security challenges in quantum computing
environments. Ultimately, through an in-depth
exploration of current blockchain encryption
technologies, this paper aims to provide valuable
insights into future development trends, serving as a
reference and guide for researchers and practitioners
to better understand the present state and future
trajectory of these critical technologies.
Figure 1: The research overview (Picture credit: Original).
2.1 Blockchain
Blockchain is a form of distributed ledger technology
that records and verifies transactions in a
decentralized manner. Satoshi Nakamoto first
introduced it in 2008 to facilitate the Bitcoin trading
system. Key attributes of blockchain include
decentralization, immutability, transparency, and
enhanced security. Traditional systems, which are
centralized, depend on a central authority to oversee
and validate data, whereas blockchain operates
through a global network of computers (nodes). This
distributed model removes the necessity of a central
authority, strengthening the system's resilience and
resistance to threats. In a blockchain, each transaction
is enclosed in a block, and these blocks are connected
sequentially using encryption, forming a chain. If any
block's data is altered, the hash values of all following
blocks will change, making it simple to identify and
Enhancing Blockchain Security: An Analysis of Encryption Technologies and Future Directions
507

stop tampering. Blockchain’s high transparency
enables any node to view all transaction data,
ensuring openness and accountability. Furthermore,
blockchain employs advanced cryptographic methods
such as public-key cryptography to safeguard data
transmission and verify user identities, while hash
functions guarantee the integrity and immutability of
data.
Smart contracts are another important innovation
in blockchain, consisting of self-executing code
embedded in the blockchain that automatically
enforces transaction terms based on preset conditions.
Smart contracts are widely used in decentralized
finance (DeFi) and other DApps, reducing reliance on
intermediaries and increasing automation in
transactions. Blockchain technology has shown great
potential across multiple industries, including finance
(such as cryptocurrencies and payment systems),
supply chain management, healthcare, the Internet of
Things (IoT), digital identity verification, and
government governance. Its applications are not
limited to cryptocurrencies but are gradually
expanding to more complex use cases, such as
enabling decentralized automated processes through
smart contracts. As blockchain technology continues
to evolve and improve, particularly in areas like
scalability, transaction speed, and energy efficiency,
it is anticipated to have an increasingly significant
impact on the future digital economy, driving
innovation and transformation in a wide range of
industries.
2.2 Public-Key Cryptography
Public-key cryptography, also referred to as
asymmetric encryption, is a cryptographic approach
that uses two keys for encoding and decoding data.
These keys are a public key and a private key. The
public key is distributed freely and can be shared,
while the private key is kept confidential and held by
its owner. In public-key cryptography, the public key
is responsible for encrypting the data, and the private
key handles the decryption. This ensures that while
anyone can encrypt a message using the public key,
only the person with the corresponding private key
can decrypt it. Additionally, the private key is used to
generate digital signatures, while the public key
verifies the authenticity of these signatures. This
system plays a crucial role in maintaining secure data
transmission and ensuring communication integrity.
One major benefit of public-key cryptography is
its ability to address the key distribution issue present
in symmetric encryption. In symmetric encryption,
both parties must share a single key, which
complicates secure key distribution and management.
However, with public-key cryptography, public keys
can be distributed freely without worrying about
interception, as only the corresponding private key is
able to decrypt the message. Public-key cryptography
is extensively applied in various secure
communication areas, such as network transmissions,
digital signatures, identity verification, and encrypted
payments in e-commerce. Common public-key
cryptography algorithms include Rivest-Shamir-
Adleman (RSA), ECC, and the Digital Signature
Algorithm (DSA).
2.3 Hash Function
A hash function is an essential mathematical tool that
transforms input data of any length into a fixed-size
hash value or digest using an algorithm. It plays a key
role in areas like data integrity checks, cryptography,
and blockchain. The core features of a hash function
include determinism, irreversibility, collision
resistance, and the avalanche effect. These attributes
make hash functions highly reliable for ensuring
security and processing. First, determinism ensures
that a given input will always produce the same hash
value consistently. Irreversibility implies that
reconstructing the original input from the hash value
is nearly impossible. Collision resistance reduces the
probability of two different inputs producing the same
hash value. The avalanche effect guarantees that even
a minor alteration in the input causes a significant
change in the hash value, making hash functions
extremely effective for preventing tampering with
data.
In cryptography, hash functions are commonly
applied in digital signatures, identity verification, and
encryption protocols. They produce a fixed-size hash
value by summarizing the message, ensuring the
data's integrity and authenticity while preventing any
alterations during transmission. In blockchain
technology, the application of hash functions is
particularly critical. They are used to package
transaction data into blocks and link these blocks
together in a chain structure. If any data within a
block is modified, the hash values of subsequent
blocks will also change, ensuring the immutability
and high security of the blockchain. Common hash
functions include Secure Hash Algorithm (SHA)-
256, SHA-512, and Message-digest Algorithm 5
(MD5). The efficiency and security features of hash
functions make them indispensable in modern
information security, data protection, and
decentralized systems, driving technological
DAML 2024 - International Conference on Data Analysis and Machine Learning
508

advancements in areas such as blockchain and digital
signatures.
3 RESULT AND DISCUSSION
These cryptographic technologies have significant
advantages in ensuring blockchain's decentralization,
security, and data integrity. Compared to traditional
centralized data storage and verification methods,
blockchain achieves thrustless transaction
verification and data sharing through encryption
techniques, eliminating the dependence on third-party
intermediaries, reducing operational costs, and
improving efficiency. Additionally, hash functions
ensure data immutability, thereby achieving a high
level of data reliability. Meanwhile, public-key
cryptography provides robust security for user
authentication and data transmission, preventing
unauthorized access. These advantages make
blockchain a dependable solution that boosts
transparency and security in decentralized networks,
making it applicable to a range of areas, including
finance, supply chain management, healthcare, and
digital identity verification, showcasing its significant
potential for diverse applications.
However, these encryption methods may face the
issue of high computational complexity in blockchain
applications. When processing a large number of
transactions, the decryption and signature verification
processes can result in significant computational
overhead, thereby affecting the overall system
performance. This computational overhead is
particularly prominent in large blockchain networks
such as Bitcoin and Ethereum, leading to slower
transaction confirmation speeds that cannot meet the
demands of high-frequency transactions. Moreover,
as the scale of the blockchain expands, hash functions
may face the risk of collision attacks, where attackers
could tamper with data by identifying different inputs
that yield the same hash value. More importantly, the
rapid advancement of quantum computing presents a
potential challenge to current encryption techniques,
as many conventional algorithms could become
ineffective in a quantum computing environment,
thereby compromising blockchain security. These
issues highlight that performance, scalability, and
security in existing encryption technologies still have
room for improvement, necessitating further research
and optimization.
Looking ahead, future research can focus on the
following aspects. Firstly, to address the
computational complexity issue of public-key
cryptography, more efficient encryption algorithms
can be further explored, such as improved methods
based on ECC to reduce computational resource
consumption and improve transaction processing
speed. Additionally, the application of hybrid
encryption techniques, which combine symmetric
and asymmetric encryption, is worth exploring to
achieve more efficient encryption and decryption
processes. Secondly, in terms of the security of hash
functions, researchers can investigate quantum-
resistant encryption techniques, such as lattice-based
cryptography or other post-quantum cryptographic
approaches, to ensure that blockchain remains
protected in the age of quantum computing. In terms
of hash algorithms, developing more collision-
resistant hash functions or improving existing hash
algorithms can enhance data integrity and anti-
tampering capabilities. Furthermore, privacy-
preserving technologies like ZKPs deserve further
research and application, as they can enhance
blockchain privacy in handling sensitive data,
allowing users to complete identity verification and
transaction confirmation without exposing sensitive
information.
4 CONCLUSIONS
This paper analyzed encryption technology within
blockchain, focusing primarily on public-key
cryptography and hash functions. The study explored
the critical roles these cryptographic methods play in
ensuring data security, integrity, and privacy in
blockchain systems. It highlighted how public-key
cryptography facilitates secure data transmission and
user authentication, while hash functions preserve
data immutability. Extensive research and analysis
revealed that, despite their benefits, these encryption
methods encounter challenges, including high
computational complexity, vulnerability to collision
attacks, and potential threats posed by quantum
computing. Evaluations demonstrated that current
encryption technologies exhibit limitations in
scalability, efficiency, and resilience against quantum
threats. Future research will prioritize the
development of more efficient encryption algorithms,
particularly enhanced ECC-based methods, as well as
the exploration of quantum-resistant encryption
techniques. Furthermore, integrating privacy-
preserving technologies, such as ZKPs, and
optimizing blockchain scalability through strategies
like sharding and sidechains will be essential areas for
further investigation. As research advances, the
performance and security of blockchain encryption
technologies are expected to improve, allowing them
Enhancing Blockchain Security: An Analysis of Encryption Technologies and Future Directions
509

to adapt effectively to the evolving digital economy
and laying a robust foundation for innovative
applications across diverse fields.
REFERENCES
Amara, M., & Siad, A., 2011. Elliptic curve cryptography
and its applications. In International workshop on
systems, signal processing and their applications, 247-
250.
Casey, M., Crane, J., Gensler, G., Johnson, S., & Narula, N.,
2018. The impact of blockchain technology on finance:
A catalyst for change.
Fiege, U., Fiat, A., & Shamir, A., 1987. Zero knowledge
proofs of identity. In Proceedings of the nineteenth
annual ACM symposium on Theory of computing, 210-
217.
Hellman, M. 1978. An overview of public key
cryptography. IEEE Communications Society
Magazine, 16(6), 24-32.
Hellman, M.E., 2002. An overview of public key
cryptography. IEEE Communications Magazine, 40(5),
42-49.
Pilkington, M., 2016. Blockchain technology: principles
and applications. In Research handbook on digital
transformations, 225-253.
Preneel, B., 1993. Analysis and design of cryptographic
hash functions. Katholieke Universiteit te Leuven.
Sobti, R., & Geetha, G., 2012. Cryptographic hash
functions: a review. International Journal of Computer
Science Issues, 9(2), 461.
Wüst, K., & Gervais, A., 2018. Do you need a blockchain?.
In crypto valley conference on blockchain technology,
45-54.
Zhang, R., Xue, R., & Liu, L., 2019. Security and privacy
on blockchain. ACM Computing Surveys, 52(3), 1-34.
DAML 2024 - International Conference on Data Analysis and Machine Learning
510
