
From Plant to Lab: Industrial Emulation Tools for
Real-World Security Testing in Industrial Control Systems
Argiro Anagnostopoulou
1a
, Thomas Papaloukas
2
, George Stergiopoulos
2b
and Dimitris Gritzalis
1c
1
Dept. of Informatics, Athens University of Economics and Business, 76 Patision Ave, Athens, Greece
2
Dept. of Information and Communication Systems Engineering, University of the Aegean, GR-83200 Samos, Greece
Keywords: Industrial Control System, Industrial Process, Emulation Software, Comparative Analysis.
Abstract: The industry and research communities have introduced a variety of approaches and algorithms that require
evaluation of their security and safety in industrial settings. However, conducting such assessments is chal-
lenging, given the need to maintain operational availability of these infrastructures. Consequently, scientists
often capture datasets from authentic industrial environments, but assess attacks on such data in emulated or
simulated environments. To replicate proper industrial conditions within controlled and simulated environ-
ments, testbeds need to be able to assess the effectiveness of implemented attacks and provide results usable
to real-world systems. In this study, we present and compare such tools that aim to emulate or simulate in-
dustrial control systems by establishing eight criteria. The objective of our work is to address concerns sur-
rounding the selection of an appropriate emulation tool based on specific needs.
1 INTRODUCTION
Industrial Control System (ICS) is a term used to de-
scribe industrial automation systems that are usually
responsible for visualization and control of industrial
processes and data acquisition. These systems are
mainly used in industrial sectors or critical infrastruc-
tures (Mattioli and Moulinos, 2015). Indicative exam-
ples of ICS are the Supervisory Control and Data Ac-
quisition (SCADA), the Programmable Logic Con-
trollers (PLC), the Distributed Control Systems
(DCS), and the Industrial Automation Systems (IAS).
These systems are employed in environments where
automation and monitoring are required, such as pow-
erplants, water facilities, nuclear plants etc. (Stouffer
and Falco, 2006), (Drias et al., 2015).
There is an increased interest of both research
community and industries to reduce the attack surface
on industrial environments. Researchers are constant-
ly proposing algorithms and models to secure the in-
dustrial sector. However, these approaches cannot be
evaluated on real-time industrial environments since
a
https://orcid.org/ 0000-0003-4199-6257
b
https://orcid.org/ 0000-0002-5336-6765
c
https://orcid.org/ 0000-0002-7793-6128
such infrastructures must be always up and running.
For this reason, there are alternatives that may assist
in the testing of the approaches. The first option is to
develop, physically or virtually, a testbed in order to
emulate the business processes of such infrastructu-
res. However, in this alternative there is a dilemma:
whether someone chooses an emulation software in-
stead of physically designs a testbed on a research lab.
The answer is not clear and depends on the purposes
that the testbed need to be designed. Additional fac-
tors to consider may be the cost of equipment, the
scale of the testbed, the downtime, or the risk of fai-
lure. A great advantage of preferring the emulation
tools is that they are able at a great extend to emulate
the conditions and setup of industrial sector at a low
or even zero cost.
Another option is to find a publicly available data-
set, and evaluate an approach using these data. This is
a difficult task, since information regarding the busi-
ness processes and transmitted values are quite pro-
tected. Sources that drive to real-wolrd datasets are
limited, because such information describe the opera-
tion of a critical infrastructure. Moreover, using a da-
Anagnostopoulou, A., Papaloukas, T., Stergiopoulos, G. and Gritzalis, D.
From Plant to Lab: Industrial Emulation Tools for Real-World Security Testing in Industrial Control Systems.
DOI: 10.5220/0012710700003767
Paper published under CC license (CC BY-NC-ND 4.0)
In Proceedings of the 21st International Conference on Security and Cryptography (SECRYPT 2024), pages 13-25
ISBN: 978-989-758-709-2; ISSN: 2184-7711
Proceedings Copyright © 2024 by SCITEPRESS – Science and Technology Publications, Lda.
13

taset limits the researcher's capabilities, since it would
not be able to launch an attack scenario.
In this work, we present nine available tools that
emulate industrial environments. We compare these
tools regarding specific factors, such as complexity,
pricing, accessibility of documentation, ease of confi-
guration, and scalability.
1.1 Motivation and Contribution
There is a plethora of software available for emulat-
ing a SCADA system. The question is why a resear-
cher chooses to use an emulation software instead of
physically design and implement a testbed. There are
multiple factors that we should consider before we
decide, including pricing, downtime, flexibility, or
risk of failure (Queiroz et al., 2011).
The primary obstacle for physically developing a
testbed is its cost. An industrial environment is a quite
complex infrastructure with various types of equip-
ment. For example, SCADA is composed of multiple
distributed devices. Each device may be included to a
different type. Regarding the aim and the type of the
device, there is a different cost and effort for its con-
figuration. Thus, when we decide which device will
be included in our testbed, for instance PLC or RTU,
we should bare in mind the cost and the expertise
needed (Queiroz et al., 2011).
In case that someone wants to launch attacks on
the infrastructure, it is crucial such action not to hap-
pen in productive environment. Attacks like distrib-
uted denial of service (DDoS) cause downtime issues,
because attackers overwhelm the resources of the in-
fected system which is not designed to handle such
amount of traffic. Such activities can either increase
the response time, or even shutdown the whole servi-
ce. Impacting the provided services for testing purpo-
ses, especially in SCADA systems, is not tolerable
(Queiroz et al., 2011). Moreover, testing malevolent
scenarios in real-time systems raises a great risk since
the tested attacks aim to bypass any security measures
that are in place. This may have a great impact on the
business processes of the critical infrastructure (Quei-
roz et al., 2011).
In order to tackle such issues, the option of devel-
oping a testbed using an emulation software is quite
appealing. Despite the fact that some emulation tools
may be an expensive choice, on average we can re-
duce the implementation cost. Moreover, we can be
more flexible since we are able to load saved projects,
revert a virtual machine to a previous state, or elimi-
nate the risk factor of causing impact on the operation
of a real-world critical infrastructure. Our work aims
to help research community to pinpoint which of the
available emulation tools can be suitable for corres-
ponding purposes, budget and we attempt to address
any concerns researchers may have.
1.2 Structure of the Work
The remainder of the paper is structured as follows.
In Section 2 we outline the methodology used to carry
out this work. In Section 3 we provide an overview of
the industrial control systems, protocols and stand-
ards. In Section 4 we present nine tools used for the
emulation of an ICS, while in Section 5 we thorough-
ly compare these tools. Finally, the paper ends with a
few concluding remarks.
2 RESEARCH METHODOLOGY
For conducting a transparent and reproducible over-
view of the scientific literature regarding emulation
tools for industrial environments, we utilize certain
features of the PRISMA statement (Page et al., 2021).
PRISMA approach is consisted of four steps: (a) de-
fine the work protocol, (b) identify studies based on
targeted searches, (c) evaluate the selected studies,
and (d) extract data, synthesize the main findings, and
report the results.
2.1 Research Objectives and Strategy
As mentioned earlier, during the first phase of our
study we defined our research questions, that helped
us find publicly available information about emula-
tion tools for industrial environments. Based upon our
properly formulated research questions (see Table 1),
Table 1: Research questions and objectives of the work.
Research Question Objectives
RQ1: What are the
reasons to support
the use of emulati-
on software tools?
The objective here is to better
understand the problem and
identify why it will be helpful
for research community to use
emulation software tools.
RQ2: What are the
available software
tools that emulate
ICS systems?
The aim is to identify the emula-
tion software that focus on ICS
systems.
RQ3: What are the
emulation tools that
can be used for re-
search
p
ur
p
oses?
The objective is to identify and
present this software that can be
used by research community.
SECRYPT 2024 - 21st International Conference on Security and Cryptography
14
we conducted a systematic literature review from Jan-
uary 2023 to August 2023. To retrieve relevant scien-
tific literature, we used widely known academic
search systems, including Google Scholar, Scopus,
and Web of Science. Moreover, Google's search en-
gine was used to extract relevant standards and best
practices (grey literature). Table 2 shows the queries
we used at all search systems.
Table 2: Keywords used during the search phase.
Scientific literature Grey literature
("ICS" OR "SCADA") AND ("emu-
lation software" OR "emulation
tool") AND ("free of charge" OR
"free" OR "open source") AND
("SCADA" OR "PLC" OR "RTU")
SCADA emulation,
ICS emulation, in-
dustrial environment
emulation
After evaluating the initial 200 results obtained
from Google, we identified the available grey litera-
ture. We limited the inclusion to this number because,
beyond this threshold:
a) the Google query produced numerous irrelevant
and low-quality results with minimal impact, as out-
lined in our exclusion criteria;
b) not all actual results were accessible due to bro-
ken or inactive hyperlinks.
Google searches served as a supplementary search
strategy, while Scopus was our main source. The quan-
tity of documents retrieved from Google was relatively
small compared to the bibliography obtained from Sco-
pus. In order to effectively handle the vast volume of
relevant literature and ensure that our review is thor-
ough and conforms to the high standards of academic
integrity, we created a list of inclusion and exclusion
criteria which are applied at several sta-ges.
The inclusion criteria on the first stage referred to
whether the title is aligned with the research focus,
while on the second stage we focused on how useful
and relevant each study was regarding on both the ab-
stract and the introduction. At the final stage we con-
sidered how applicable each publication was after
comprehensive full-text reading.
The exclusion criteria on the first stage referred to
research papers, book chapters and scientific articles
that lacked peer review, publications not written in
English, and studies lacking abstracts or introducti-
ons. On the second stage we eliminated articles that
seemed relevant but were out-of-scope upon closer
review, reports from organizations lacking recogniz-
ed national or international status, and publications by
authors not affiliated with reputable scientific com-
munities or lacking citations and references.
Papers from repositories like arXiv are not exclu-
ded, because even though they may not meet all pub-
lication standards, some studies are considered credi-
ble (Xarhoulacos, 2021).
2.2 Selection of Studies and Analysis
According to PRISMA statement (Page et al., 2021),
the four stages for the selection of literature are: (a)
identification, (b) screening, (c) eligibility, and (d) in-
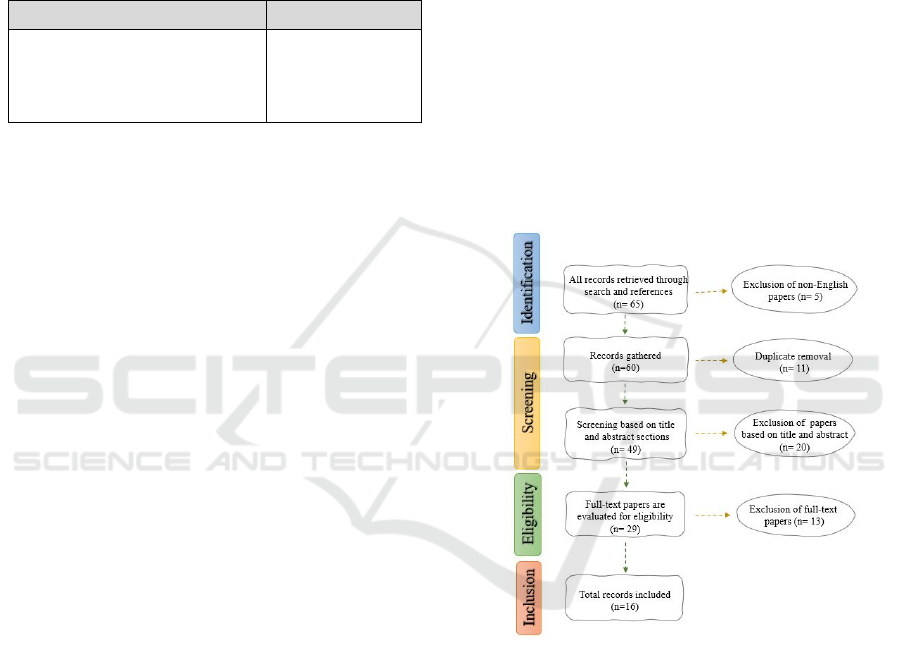
clusion. In Figure 1 we present the number of docu-
ments we retained on each stage. On the identification
stage, we gathered 65 documents in the academic
field. However, we excluded 13 of them since those
were written in languages we could not parse. During
the screening stage, we removed duplicates, and af-
terwards we evaluated the rest documents. A total of
20 papers were removed based on their title and ab-
stract. Finally, on the eligibility stage 13 papers were
rejected after reading the complete text body.
Figure 1: Flowchart of the search strategy.
Overall, in the main body of our literature review
we included 16 papers. We also used additional liter-
ature for peripheral information presented in the man-
uscript, but they were not considered on the total
number of included files as they did not address our
research questions. The predominant challenge we
faced was that the majority of the Google search re-
sults directed us to the websites of companies which
sell emulation software.
From Plant to Lab: Industrial Emulation Tools for Real-World Security Testing in Industrial Control Systems
15

3 INDUSTRIAL CONTROL
PROTOCOLS & STANDARDS
We provide an overview of the ICS, along with the
available communication protocols and standards that
such systems utilize.
3.1 ICS Overview
ICS is mostly used for the mechanism of data gather-
ing from various endpoint devices, in order to parti-
ally or fully automate the production process. Indica-
tive types of ICS include the Process Control Systems
(PCS), DCS, and SCADA (Macaulay and Singer,
2011). SCADA systems are mainly found in critical
infrastructures and industrial sectors, such as water
distribution systems, waste-water collection systems,
or oil and gas pipelines (Macaulay and Singer, 2011).
SCADA collects data from remote devices and con-
trollers and send this information to a centralized sys-
tem (Control Center), where an authorized user can
connect, physically or remotely, in order to monitor
and control the values in real-time.
The main components of SCADA are the control
center, the distributed devices (e.g. PLC, RTU, etc.),
the Human-Machine Interface (HMI), and the Master
Terminal Unit (MTU). In details, HMI is located in
the Control Center, along with the Data Historian, and
MTU. HMI provides user with an environment that
displays the monitored values, and the available ac-
tions for the configuration and control of the remote
devices. MTU is the server that processes and stores
the acquired data from the RTUs and PLC. The Data
Historian provides a centralized database located in
the control system, that supports analytics based on
statistical process control techniques. Finally, Remo-
te Terminal Unit (RTU) and Programmable Logic
Controller (PLC) collect data, monitor and control
sensors and actuators (Macaulay and Singer, 2011).
3.2 Communication Protocols
3.2.1 RS-485
RS-485 bus standard is used in the physical layer. It
transfers small blocks of data over long distances (up
to 1219m) at high speeds (≤10Mbps) (Marais, 2008)
(Axelson, 1999). The main advantage of this standard
is the ability for communication in electrically noisy
environments, and the support of multiple devices on
the same bus (CUI Devices, 2020). The protocol was
designed years before the development of Ethernet,
and thus the security aspect was not a priority.
3.2.2 Modbus
Modbus is a publicly available protocol. A central
master sequentially requests status information from
each connected device (Modbus Organization, 2006),
(OPS Telecom, 2023). Modbus is implemented in ap-
plication layer, used for real-time communication and
monitoring. Modbus was designed for serial commu-
nication and was later extended to run over TCP
(Drias et al., 2015). Modbus provides two types of
communication: (1) query/response between a master
and a slave, and (2) broadcast communication, where
the master sends a command to its slaves (Fovino et
al., 2009). Its main advantage is that it can be included
in a wide range of device types from any equipment
vendor (OPS Telecom, 2023). The drawback of Mod-
bus is the lack of security features, as it was originally
developed without considering security aspects
(Stouffer, 2006).
3.2.3 DNP3
Distributed Network Protocol (DNP3) is another pro-
tocol implemented in application layer. It is primarily
designed to simplify the communication across vari-
ous types of data acquisition and control systems.
Three types of communications are defined in DNP3
protocol: i) unicast transaction, ii) broadcast transac-
tion, and iii) unrequested responses from remote de-
vices (East et al., 2009). In unicast transaction, the
master can make a request to a targeted destination
slave, and the slave device responds back with a mes-
sage. In broadcast transaction, the master broadcasts
a request towards all its slaves within the network,
and in this instance, the slaves do not reply. The last
type of communication is typically periodic, unreque-
sted (by the master) updates or alerts are sent from the
remote devices to the master (East et al., 2009).
3.2.4 HART
Highway Addressable Remote Transducer (HART)
protocol is mostly applied to transmitters located in
hazardous environments (petrochemical, pharmaceu-
tical, chemical industries). Some of the published pro-
ducts provide a Bluetooth HART modem for the
transmitters to connect, in order to remotely configure
the transmitters while being in a dangerous environ-
ment, without the need of physical access to configure
them (Yu et al., 2018). HART is a combination of an-
alog and digital industrial automation protocol.
WirelessHART was later released to enhance wi-
reless capabilities to HART technology while main-
taining compatibility with pre-existing HART devi-
SECRYPT 2024 - 21st International Conference on Security and Cryptography
16

ces. WirelessHART is designed to use mesh network-
ing technology. In a mesh network, each device can
serve as a router for messages coming from other de-
vices. Thus, a device can forward a message to the
next closest one instead of communicating directly
with a gateway. This extends the range of the network
and provides redundant communication routes to in-
crease reliability (Song et al., 2008).
3.2.5 ICCP/TASE 2.0
Inter-control Center Communications Protocol, also
referred as Tele-control Application Service Element
(TASE 2.0), is a protocol that allows communication
and data exchange between different control centers
over Local Area Networks and Wide Area Networks
(Cunha et al., 2004), (Ilgner et al., 2021). TASE 2.0
relies on Manufacturing Message Specifications in
order to transfer data and monitor network nodes.
TASE 2.0 does not support authentication or encryp-
tion; instead, it implements an ingrained security suite
of underlying TCP/IP stack (Ilgner et al., 2021).
3.2.6 CIP
Common Industrial Protocol (CIP) is an object-ori-
ented protocol that transfers data between communi-
cation objects. An object is consisted of attributes,
services, connections, and behaviors. The protocol
also includes an extensive library that supports (a)
typical automation functions (e.g. analog and digital
input/output devices, HMI, motion control and posi-
tion feedback etc.), (b) general purpose network com-
munications, and (c) network services (e.g. file trans-
fer etc.) (Weehuizen et al., 2007), (ODVA, 2006).
3.2.7 BACnet
Building Automation & Control Network (BACnet)
is a protocol that was initially designed for heating,
ventilation, and air conditioning (HVAC) systems,
and was later extended to support further functionali-
ties (Esquivel-Vargas et al., 2017). BACnet solves in-
teroperability issues among devices from different
vendors, by modelling exchanged information with
object-oriented representations (Tang et al., 2020).
An object in BACnet is defined as a collection of
information related with the functionality of a BAC-
net device (Newman, 2013). Although BACnet was
not primarily designed with security in mind, there
are a-vailable options to secure BACnet, such as
through IP security solutions, IPsec, etc. (Peacock et
al., 2017), (Peacock, 2019).
3.3 Communication Standards
We introduce the standards encountered during the
communication of different components within an In-
dustrial Control System (ICS).
3.3.1 IEC 60870-5-104 (IEC 104)
IEC 104 was developed on top of the serial commu-
nication standard IEC 60870-5-101 (IEC 101).
Standard IEC was originally developed to enable
ba-sic tele-control messages between a control station
and outstations, over a communication link between
them (e.g. telephone network, modem circuit) (Mai et
al., 2019). IEC 104 is implemented in application lay-
er and is based on TCP/IP. However, this makes it
prone to attacks since it carries all the security issues
of TPC /IP. Moreover, the lack of encryption on the
transmitted data in the application layer is another se-
curity concern, making it vulnerable to Man-in-the-
Middle (MITM) attacks (Radoglou, et al., 2019).
3.3.2 IEC 61850
IEC 61850 is an international standard that defines a
comprehensive framework for communication bet-
ween devices and systems used in substations (e.g.,
control systems). One of its goals is to improve the
interoperability and integration of devices and sys-
tems in substation automation systems. It can support
both Ethernet and serial communication protocols,
and thus it provides an easier integration between var-
ious devices across different vendors. It is commonly
implemented in electric power industries (Mackie-
wicz, 2006). An important aspect of IEC 61850 is the
security guidelines that are included and focus on: i)
authentication and access control, ii) data integrity
and confidentiality, iii) network security, and iv) risk
assessment and management (Hussain et al., 2019).
On the other hand, IEC 61850 proposed SNTP proto-
col that has less accuracy, while in time-critical appli-
cations (such as in industrial sector) there is need for
accurate protocols to be applied (Sidhu et al., 2008).
3.3.3 ISO 15745
ISO 15745 proposes a framework for the develop-
ment of communication profiles for industrial auto-
mation systems. The standard outlines the conditions
for the creation and application of communication
profiles, which are used in industrial automation envi-
ronments to guarantee interoperability between devi-
ces and systems. A communication profile is a set of
rules and protocols in order to describe how devices
communicate in a system (Kosanke, 2006). Although
From Plant to Lab: Industrial Emulation Tools for Real-World Security Testing in Industrial Control Systems
17

this standard provides rules and profiles as a frame-
work for the development of communication proto-
cols (which could be designed to meet security re-
quirements), it does not explicitly deal with security
requirements of industrial automation systems.
3.3.4 EN 62443
EN 62443 is a set of industrial cybersecurity stand-
ards developed by the International Electro-technical
Commission (IEC) and the International Society of
Automation (ISA). EN 62443 was designed to provi-
de a comprehensive framework for securing indust-
rial automation and control systems against cyber
threats. The standard includes criteria for cybersecu-
rity management systems, risk assessment, and inci-
dent response plans, along with a list of recommen-
dations and best practices for safeguarding the net-
work and devices of industrial automation and control
systems. Due to restrictions on cost and resources, it
is difficult to effectively address all security issues as
required by IEC 62443 (Maidl et al., 2018).
4 EMULATION SOFTWARE
In this section we make an analysis of nine software
tools that can be used to realistically emulate complex
industrial processes or entire plants.
4.1 IEC Server & QTester104
IEC Server is a software, written in Java, that emu-
lates field devices (such as an RTU) and SCADA, im-
plementing a telecontrol message protocol specified
in the IEC 60870-5 (Parcharidis, 2018). The software
is free of charge, and it is simple to operate. The tool
comes as a portable executable and does not need to
be installed, reducing the configuration time compar-
ed to the other emulation tools. A drawback of this
software is that the documentation is not publicly
available because it is hosted on a website that is cur-
rently unavailable. Despite the lack of a manual, the
tool includes several interesting actions, such as add
IEC a 60870-5-104 command from a short list, pause
or resume the emulation, start or stop the server that
listens to a specified port, or even save a preset of a
given configuration.
QTester104 is a software designed to receive data
from a field device, based on the IEC 60870-5-104
communication protocol, in a SCADA system (Par-
charidis, 2018). This software is also free of charge and
can be compiled on Linux and Windows platforms.
There is adequate documentation that explains both the
tool functionalities and the user interface.
4.2 OMNeT++
OMNeT++ (Objective Modular Network Testbed in
C++) is an extensible, modular, component-based
C++ simulation framework. It is primarily used for
building network simulations. OMNeT++ is an open-
source tool with extensive documentation. It can be
used for free and for non-commercial purposes, such
as for academic institutions or teaching (Ahmad and
Durad, 2019). The OMNeT++ simulation kernel is
standard C++ and runs on all platforms where C++
compiler is available. The simulation IDE requires
Windows, Linux, or macOS. A project in OMNeT++
consists primarily of three files. A NED file that con-
tains the topology of the network, an INI file that con-
tains the configuration of the simulation, and the
source code file which is written in C++ and manages
the simulation (Ahmad and Durad, 2019). The project
is compiled using the NEDC compiler, included in the
OMNeT++ (Varga, 2005).
The greatest advantage of this software is its ex-
tensive documentation, provided both by researchers
and the community. One negative point is that the
configuration needed for the creation of a new project
can be overwhelming, since there are many compo-
nents that have to be included and users must have
adequate knowledge of the C++ language.
4.3 RINSE
RINSE (Real-time Immersive Network Simulation
Environment) is used to conduct real-time emulation
for network-security purposes (Liljenstam et al.,
2005). RINSE can emulate large networks, along with
a great number of attacks and defensive measures
(Davis et al., 2006). RINSE is composed of five basic
elements: i) iSS FNet network simulator, ii) simulator
database manager, iii) database, iv) data server, and
v) client-side network viewers. The iSSFNet is a net-
work simulator that runs over the Scalable Simulation
Figure 2: RINSE architecture.
SECRYPT 2024 - 21st International Conference on Security and Cryptography
18

Framework (iSSF), an Application Programming
Interface (API) which is responsible for the synchro-
nization and the functionality support. The iSSFNet
is running on parallel machines and supports the sim-
ulation of large-scaled networks. The simulator data-
base manager is responsible for supervising the data
gathering from the simulation nodes, in order to store
them in the database. These data are later delivered to
the simulator. The data server allows users to monitor
and control the simulated network. Finally, the net-
work viewers are running on the clients, allowing us-
ers to gain a local view of the network (Liljenstam et
al., 2005). RINSE architecture is depicted in Figure 2.
Through the network view clients, the users can
execute basic commands that modify the simulation.
Such commands can be categorized, based on their
functionality:
Attack: Commands used for launching attacks
(such as DDoS, worms).
Defense: Commands used for applying counter-
mea-sures (such as packet filters).
Diagnostic networking tools: Commands for basic
networking communication.
Device control: Commands for the control of the
devices (such as restart, reboot).
Simulator data: Commands sent to the simulator
in order to modify the output.
Although RINSE appears to be a promising simu-
lation software tool (highly scalable, with multiple
functionalities etc.), it has limited options to the com-
mands that can be used for attacks. Most of the attack
commands revolve around denial of service.
4.4 GRFICS
GRFICS (Graphical Realism Framework for Indus-
trial Control Simulations) is a simulation tool de-
signed specifically for ICS. It can be customized to
meet user needs. GRFICS helps users understand ICS
protocols through virtual network environments. This
accessibility aims to improve community knowledge
in ICS security. Users can simulate and observe cy-
bersecurity attacks like command injection, man-in-
the-middle attacks, and buffer overflows through 3D
visualizations. Finally, the tool offers the chance of
practicing defensive strategies by deploying proper
firewall and intrusion detection rules within the vir-
tual network. (Slatman H).
GRFICS allows users to swap components (such
as PLCs, HMI and any I/O module) with real ICS de-
vices. In order to emulate its physical processes, the
software utilizes: i) the emulation backend, ii) the e-
mulation API, iii) the 3D visualization, and iv) the I/O
modules (Formby et al., 2018). In regard to the visu-
alization of the PLC, developers used a modified ver-
sion of the OpenPLC. OpenPLC is an open-source
software for virtualizing controllers, which supports
multiple communication protocols (e.g., IEC 61131-
3, Modbus/TCP or DNP3). For the HMI’s visualiza-
tion, developers implemented Advanced HMI, an
open-source software allowing HMI virtualization.
Figure 3: SCADAVT architecture.
Overall, GRFICS is a great framework that com-
bines all the essential components: a virtualized net-
work of PLC, HMI, router, and a workstation.
It is an ideal tool for researchers that want to con-
duct basic security attacks and defensive counter-
measures at no cost. GRFICS can be downloaded
from the GRFICS Git-Hub repository. Also, there is
available an adequ-ate documentation, as well as
video tutorials on how to configure the virtual ma-
chines.
4.5 SCADAVT
SCADAVT is a security framework that is targeted to
security experts of SCADA systems (Almalawi et al.,
2013). It was developed on top of the CORE emulator
(Ahrenholz, 2010). CORE is a network emulator, si-
milar to OMNET++, OPNET, QualNet, NetSim, SSF
Net, NS2 (NetWork Simulator 2) and NS3 (Network
Simulator 3) (Ahmad and Durad, 2019), (Pan and
Jain, 2008). Since the CORE emulator does not sup-
port the commonly used SCADA protocols, the crea-
tors of the testbed developed three essential compo-
nents, which were integrated as services within the
CORE emulator. These components are:
Modbus/TCP Simulators of Master/Slave: Uti-
lizes the master-slave architecture essential for
SCADA systems. SCADAVT supports the Mod-
bus protocol, and the modes of master-slave are
integrated into the CORE emulator, using the
Modbus library and python scripts.
Modbus/TCP Simulator of HMI Server: Acts as
the communication medium between the HMI cli-
ent and MTU, facilitating a two-way communica-
tion for command exchanges.
From Plant to Lab: Industrial Emulation Tools for Real-World Security Testing in Industrial Control Systems
19
I/O modules Simulator: Acts as a server, and is
charge of receiving input data, from the external
environment, and sending it to the requesting
nodes.
In order to utilize the SCADAVT framework, the
user should install the following components: i) the
CORE emulator, ii) a third party publicly accessible
Modbus library, iii) a Python interpreter, iv) a securi-
ty tool (such as hping3), and v) the integration Python
scripts, developed by the creators (Ahrenholz, 2010).
The architecture of SCADAVT is shown in Figure 3.
Because the CORE emulator is a GUI-friendly solu-
tion that does not require code to configure a network
topology, the absence of the python scripts used to
implement the required SCADA components into the
emulator shifts the burden of developing new python
scripts to end-users.
4.6 TASSCS
TASSCS (Testbed for Analyzing Security of SCADA
Control Systems) is a testbed developed at the NSF
Center for Autonomic Computing at the University of
Arizona, aiming to help the security research, by pro-
viding innovative protection techniques for SCADA
systems (Mallouhi et al., 2011). TASSCS uses three
tools: (i) OPNET, a long-used by the industry com-
mercial network simulator (Pan and Jain, 2008), (ii)
PowerWorld that simulates the operations of the elec-
trical power grid, and (iii) Autonomic Software Pro-
tection System (ASPS) whose role is to protect SCA-
DA system and its network from the tested attacks
(Mallouhi et al., 2011). Modbus RSim is a tool that
helps users emulate PLC devices (Modbus server).
The Modbus server is combined with the Power-
World server and OPNET in order to listen incoming
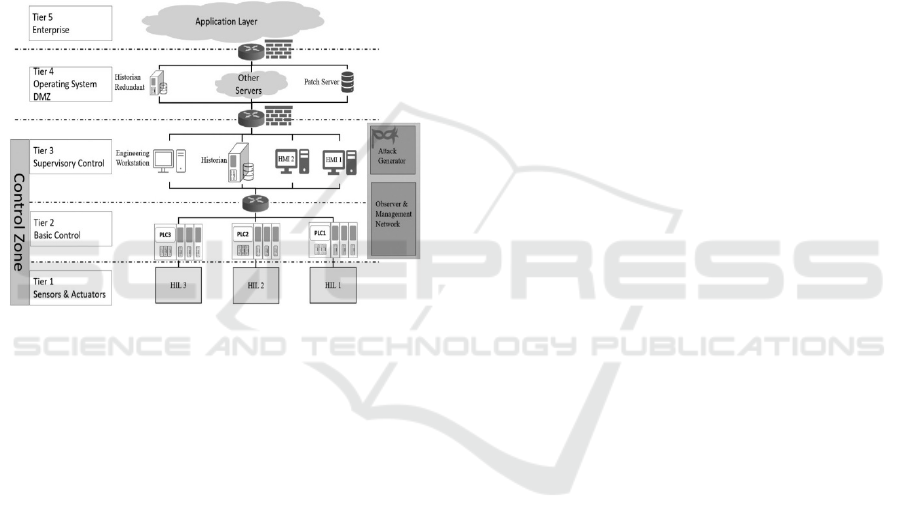
requests (Mallouhi et al., 2011). In Figure 4 we depict
how the components of TASSCS are connected.
Figure 4: TASSCS architecture.
The TASSCS architecture has three components:
(i) Control HQ, (ii) WAN, and (iii) Energy Field.
Through the Control HQ, users can control all the
available resources within the emulated environment,
along with the provided services. This component al-
lows the presentation and storage of the collected data
(e.g. historical data from the devices and sensors).
Moreover, through Control HQ the end-users can ma-
nage the grid’s resources. The WAN component con-
sists of multiple emulated sensors, such as PLC, RTU
etc. These devices provide SCADA with the required
data and execute the requested commands from the
control center through the HMI. Finally, the Energy
Field serves as the electrical grid controlled by the
SCADA system. Through this component, develop-
ers would showcase the effectiveness of the ASPS, as
it prevents the launched attacks, and minimizes the
impact on the operations of the grid.
TASSCS has a great potential as it allows users to
test various attack scenarios and has defensive capa-
bilities which permit users to study the detection and
prevention aspect, through the ASPS.
4.7 SCADASim
SCADASim is a framework used for emulating SCA-
DA systems, developed at the Royal Melbourne Insti-
tute of Technology in Australia. SCADASim is an all-
in-one, plug and go emulator, that utilizes the OM-
NET++ discrete event simulation engine (Qassim et
al., 2017). SCADASim was developed with three key
requirements (Queiroz et al., 2011): (a) no need for
programming skills, (b) connectivity to multiple ex-
ternal devices (both hardware and software), and (c)
support of multiple industry standard protocols (e.g.
Modbus/TPC, DNP3).
Figure 5: SCADASim architecture.
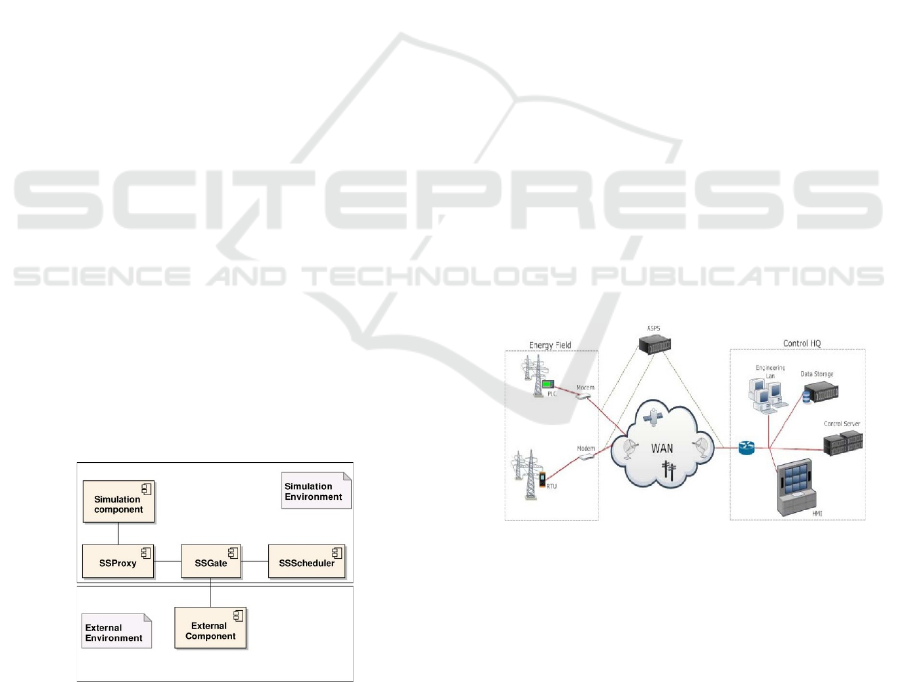
As depicted in Figure 5, SCADASim’s architec-
ture consists of three essential components: i) SSS-
cheduler, ii) SSGate, and the iii) SSProxy. The SSS-
cheduler is a real-time scheduler, that allows users to
add new schedulers to the OMNET++ simulator. Us-
ers can control and synchronize the messages that re-
ceive from the external environment. SSScheduler
manages the SSGate instances, which are responsible
to send and receive messages from the external envi-
ronment. SSGate is the communication link to the ex-
SECRYPT 2024 - 21st International Conference on Security and Cryptography
20
ternal environment, where external SCADA compo-
nents are allowed to connect, through a supported
communication protocol.
Currently SCADA Sim supports three types of
gates: ModbusGate, DNP3Gate, and HTTPGate. SS-
Proxy is a representation of a real device or an exter-
nal application with-in the emulated environment,
and it communicates with the emulated objects (e.g.
PLC, RTU, MTU) through the SSGate which routes
their messages (Queiroz et al., 2011). SCADASim al-
lows many attacks to be launched on the emulated en-
vironment, such as: Denial of Service, Man in the
Middle, Spoofing, and Eavesdropping etc. Overall,
SCADA Sim has an easy configuration, with adequ-
ate documentation provided.
Figure 6: ICSSIM reference architecture.
4.8 ModbusPal & Rodbus
ModbusPal is a free, open-source emulation software
written in Java, which supports both natively TCP/IP
communication and serial communication as well.
The user can include up to 247 slaves, and each slave
can hold both registers and coils. ModbusPal can dy-
namically generates missing resources (slaves, regis-
ters and coils) as it receives requests from the master.
ModbusPal supports automations, where an automa-
tion is defined as a generator that creates the values
(through Linear, Random, and Sine generators) with
a predefined step, and these values can be bound with
a register or a coil. ModbusPal by default listens on
port 502, which can be easily changed through the
user interface. A slave can have its own IP address in
order to be identified in the network. Finally, a project
can be saved in an XMPP format so that the user can
load it again on the emulator.
Rodbus (Rust and Modbus) is a Rust implementa-
tion of the Modbus protocol. It is a command-line tool
written in Rust and can be easily installed using Car-
go. Rodbus provides in simple syntax all the essen-
tials commands that could be used by the master, such
as reading coils and registers, writing both single and
multiple coils or registers, etc.
4.9 ICSSIM
ICSSIM is a python-based emulation testbed, created
for security-research purposes. Several components
of the emulation are created as Docker containers that
may either share resources (such as a shared SQLite
database for “hardwired” communication) or commu-
nicate across the network using configurable, private
IP addresses. It supports Modbus TCP and includes
classes that might be extended to support new proto-
cols. The ICSSIM is capable of supporting both hard-
ware and emulated ICS components, such as a PLC
(Dehlaghi-Ghadim et al., 2023). Figure 6 presents the
ICSSIM reference architecture.
The Attack Generator, a key component of this
testbed, enables for the emulation of an adversary
within the environment, assuming that the attacker al-
ready has a foothold. Because this Attack Generator
is a Docker running Kali Linux, attackers can launch
a variety of attacks. This emulation software does not
require highly technical skills to operate, but basic
containerization understanding is required. Finally,
programming skills would help end-users to increase
the emulation capabilities of the tool.
5 EMULATION SOFTWARE
COMPARISON
In this section, we undertake a comparison of the
emulation tools based on the criteria outlined in Table
3. Due to the software's modularity, most emulation
tools can model any protocol as needed by research-
ers. The term "modularity" here refers to a software
design approach that divides the program's function-
ality into independent, interchangeable modules. As
indicated in Table 4, half of the tools have the capa-
bility to simulate any protocol requested by the user.
Specifically, SCADAVT, TASSCS, ModbusPal
& Rodbus, and ICSsim are dedicated to the Mod-
bus/TCP protocol, with TASSCS also incorporating
DNP3. On the other hand, IEC Server & QTester104
exclusively support the IEC 60870-5 protocol.
From Plant to Lab: Industrial Emulation Tools for Real-World Security Testing in Industrial Control Systems
21
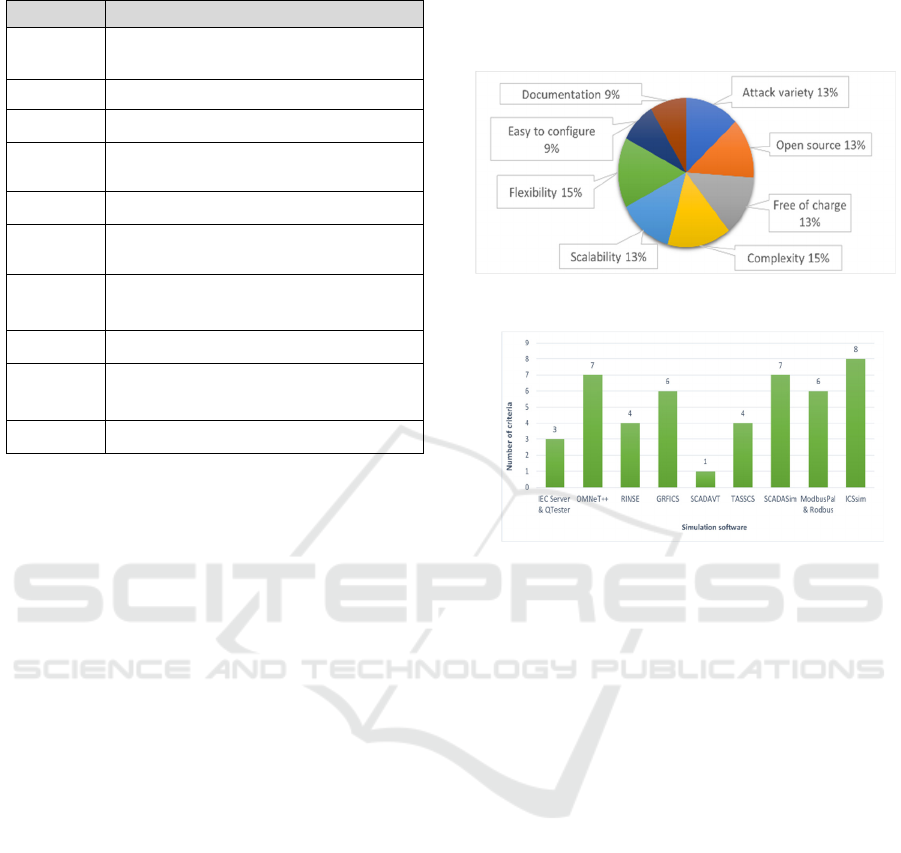
Table 3: Description of comparison criteria.
Criterion Description
Modularity
Modularity of the software defines whether an emu-
lation software could model any protocol that a re-
searcher desires.
Sector The sectors that an emulation tool is focused.
Attack vari-
et
y
How flexible is to emulate several attacks or is spec-
ified to a sin
g
le attack.
Open source
The capability of a tool and its source code to be
used, altered, or distributed to anyone and for any
p
ur
p
ose.
Free of
char
g
e
Whether a researcher should purchase the emulation
tool.
Complexity
Whether the use of an emulation tool requires higher
technical knowledge (e.g. programming skills) from
users.
Scalability
Factors that indicate scalability of a tool: number of
emulated devices, whether Firewalls, Intrusion De-
tection Systems etc., could be used in the emulation.
Easy to con-
fi
g
ure
How easy is for a researcher, may not be familiar in
a
g
reat extend with
p
ro
g
rammin
g
and en
g
ineerin
g
Flexibility
The degree of flexibility is determined by how con-
figurable the environment is, the variety of attacks
that can be launched.
Documenta-
tion
A tool offers a good experience if the user can easily
find the details of how to confi
g
ure and use it.
Pricing and accessibility of software are crucial
aspects in comparison. Some tools are proprietary and
intended for use by specific organizations. Fortunate-
ly, a significant number of tools are freely available
and open-source. As shown in Table 4, IEC Server &
QTester104, OMNeT++, GRFICS, SCADASim,
ModbusPal & Rodbus, and ICSsim are all examples
of tools that are both free of charge and open-source.
Additionally, we considered specific sectors applic-
able by these tools. According to Table 4, most tools
are not sector-specific. Only two tools have a con-
centrated focus on specific areas. GRFICS targets the
chemical sector, while TASSCS is designed for use
in the chemical and energy sectors.
A feature that is beneficial to users is the presence
of adequate documentation. Unfortunately, only four
tools have accessible documentation, which are OM-
NeT++, RINSE, ModbusPal & Rodbus, and ICSsim.
Furthermore, it is important the tools to be kept up to
date. This is because when the tools integrate updates,
then enhance existing features, fix bug issues, or im-
prove their performance. Based on Table 5, the most
up-to-date tools are the IEC Server, the OMNeT++,
the Rodbus, and the ICSsim. The GRFICS, SCA-
DAVT, and TASSCS are no longer available.
Researchers aim to emulate environments not on-
ly for testing but also for launching attacks and draw-
ing conclusions without impacting real-world infrast-
ructures. Therefore, we evaluate the presented soft-
ware based on the criterion of attack variety. Most of
the tools meet this criterion, except IEC Server &
QTester104, RINSE, and SCADAVT. In terms of fle-
xibility and scalability, as indicated in Table 4, IEC
Server & QTester104, SCADAVT, and ModbusPal &
Rodbus are identified as less scalable tools. Specifi-
cally, IEC Server & QTester104 and SCADAVT are
noted as the least flexible among the tools.
Figure 7: Number of criteria per emulation software.
Figure 8: % of tools that incorporate each criterion.
Figure 7 indicates how many emulation tools in-
corporate a particular criterion. We notice that the lar-
ger percentage is attributed to complexity and flexibi-
lity. Conversely, the lowest percentage suggests that
developers are not concerned with the ease of config-
uration and the documentation provision. Based on
the above observations, we can assume that software
developers focus enough on adding new features, but
they sacrifice the ease of configuring the tool. Have
in mind that the user, in our case a researcher, may
not be familiar to a great extend with programming
and engineering and customization adds complexity
to execution.
Figure 8 depicts the number of criteria that each
of the presented tools incorporates. We notice that on-
ly the ICSsim meets all the requirements. The second
place, with 7 out of 8 incorporated criteria, belongs to
the OMNeT++ and the SCADASim. The tool that sat-
isfies only one requirement is SCADAVT.
Researchers are flexible to choose emulation soft-
ware based on their expertise, specific emulation
needs, and budget constraints. This analysis suggests
ICSsim as a recommended choice that meets all speci-
fied criteria. Alternatively, researchers may consider
either OMNeT++ or SCADASim, both satisfying 7 out
of 8 criteria. The choice between these two tools de-
pends on individual needs. OMNeT++ offers extensive
SECRYPT 2024 - 21st International Conference on Security and Cryptography
22
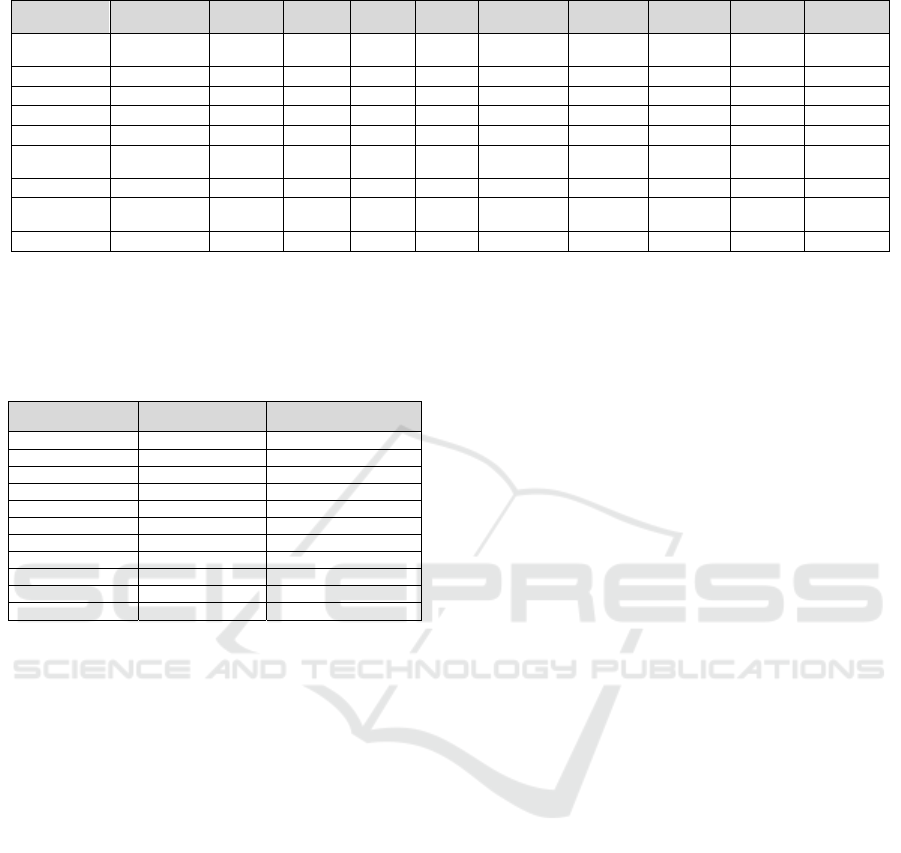
Table 4: Emulation Software Comparison.
Emulation
software
Modularity Sector
Attack
variet
y
Open
source
Free of
char
g
e
Complexity Scalability Flexibility
Easy to
confi
g
ure
Documen-
tation
IEC Server &
QTester104
IEC 60870-5 Generic -
✓
✓
- - -
✓
-
OMNeT++ Any protocol Generic
✓
✓
✓
✓
✓
✓
-
✓
RINSE Any protocol Generic - - -
✓
✓
✓
-
✓
GRFICS Any protocol Chemical
✓
✓
✓
✓
✓
✓
- -
SCADAVT Modbus/TCP Generic - - -
✓
- - - -
TASSCS
Modbus/TCP,
DNP3
Energy,
Chemical
✓
- -
✓
✓
✓
- -
SCADASim Any protocol Generic
✓
✓
✓
✓
✓
✓
✓
-
ModbusPal
& Rodbus
Modbus/TCP Generic
✓
✓
✓
- -
✓
✓
✓
ICSsim Modbus/TCP Generic
✓
✓
✓
✓
✓
✓
✓
✓
documentation despite being challenging in configura-
tion, while SCADASim is easy to configure but lacks
accompanying documentation.
Table 5: Software Latest Updates.
Emulation software Release date Latest update
IEC Serve
r
February, 2018 June 27, 2023
QTeste
r
A
p
ril, 2016 Novembe
r
10, 2022
OMNeT+
+
Decembe
r
2018 Jul
y
5, 2023
GRFICS N/
A
N/
A
RINSE Ma
y
, 2018 Decembe
r
14, 2020
SCADAVT N/
A
N/
A
TASSCS N/
A
N/
A
SCADASi
m
December, 2018 Novembe
r
9, 2020
ModbusPal March, 2009 Februar
y
20, 2018
Rodbus Au
g
ust, 2019 A
p
ril 27, 2023
ICSsi
m
A
p
ril, 2022 Februar
y
2, 2023
6 CONCLUSIONS
Our work aimed to identify and present tools that can
be used for the emulation of complex ICS infrastruc-
tures and systems, such as SCADA. We made a thor-
ough analysis and comparison among these tools bas-
ed on a number of criteria regarding the accessibility
to the tool, flexibility in terms of the emulation com-
ponents, configuration complexity, latest updates of
the software, pricing, scalability, as well as the acces-
sibility to documentation and manuals.
For an effective tool selection, a user should first
define requirements per use-case and specific needs
of the facility that requires the emulation tool. This
includes understanding the type of ICS in use (e.g.,
SCADA, PLC, DCS), critical processes and compo-
nents that must be emulated, along with the overall
objectives of using the tool (e.g., training, vulnerabil-
ity testing, system analysis).
At a minimum, plant users should choose based
on (i) protocol support regarding the communication
protocols used in the existing ICS (e.g., Modbus, IEC
61850), (ii) actuator and sensor emulation support to
simulate the types of equipment used in the system,
and (iii) material mapping capabilities to be relevant
to the processes (e.g., chemical properties in a pro-
cessing plant).
Some of the simulation software provide high fle-
xibility regarding the simulation components. This
may cost the ease of using and configuring the soft-
ware and leads to an increased level of complexity,
requiring higher technical knowledge (e.g. program-
ming skills) from users. For example, OMNeT++, of-
fers simulation of any desired component within an
industrial control system, supporting any communi-
cation protocol, due to its modularity. However, it re-
quires considerably higher technical skills, compared
to other simulation solutions. The pricing is another
concern that we have in mind. Most of the emulation
software is free of charge, where others are either not
publicly available, or require a license.
Finally, we aimed at addressing the challenging
dilemma of whether someone chooses an emulation
software instead of physically designs a testbed on a
research lab. The objective of our analysis is to help
research community identify which of the existing
emulation tools can be suitable for corresponding pur-
poses and budget.
REFERENCES
Ahmad, Z., Durad, M. (2019). Development of SCADA
simulator using omnet++. In 2019 16
th
International
Bhurban Conference on Applied Sciences and Tech-
nology, pg. 676–680. IEEE.
Ahrenholz, J. (2010). Comparison of core network emula-
tion platforms. In 2010 Military Communications Con-
ference, pg. 166–171. IEEE.
Almalawi, A., Tari, Z., Khalil, I., Fahad, A. (2013). Sca-
davt-a framework for scada security testbed based on
virtualization technology. In 38
th
Annual IEEE Confer-
ence on Local Computer Networks, pg. 639–646.
Axelson, J. (1999). Designing rs-485 circuits. Circuit Cel-
lar, 107:20–24.
From Plant to Lab: Industrial Emulation Tools for Real-World Security Testing in Industrial Control Systems
23

Coffey, K., Smith, R., Maglaras, L., Janicke, H. (2018).
Vulnerability analysis of network scanning on SCADA
systems. Security and Communication Networks, 2018.
CUI Devices (2020). RS-485 serial interface explained.
Cunha, C., Rein, O., Jardini, J., Magrini, L. (2004). Electri-
cal utilities control center data exchange with iccp and
cim/xml. In 2004 IEEE Transmission and Distribution
Conference & Exposition, pg. 260–265. IEEE.
Davis, C., Tate, J., Okhravi, H., Grier, C., Overbye, T.,
Nicol, D. (2006). SCADA cyber security testbed devel-
opment. In 2006 38
th
North American Power Sympo-
sium, pg. 483–488. IEEE.
Dehlaghi-Ghadim, A., Balador, A., Moghadam, M., Hans-
son, H., Conti, M. (2023). Icssim - a framework for
building industrial control systems security testbeds.
Computers in Industry, 148:103906.
Drias, Z., Serhrouchni, A., Vogel, O. (2015). Taxonomy of
attacks on industrial control protocols. In 2015 Interna-
tional Conference on Protocol Engineering, pg. 1–6.
IEEE.
East, S., Butts, J., Papa, M., Shenoi, S. (2009). A taxonomy
of attacks on the dnp3 protocol. In Internatio-nal Con-
ference on Critical Infrastructure Protection, pg. 67–81.
Springer.
Esquivel-Vargas, H., Caselli, M., Peter, A. (2017). Au- to-
matic deployment of specification-based intrusion de-
tection in the bacnet protocol. In Proc. of the 2017
Workshop on Cyber-Physical Systems Secuity and Pri-
vacy, pg. 25–36.
FieldComm Group. Wirelesshart.
Formby, D., Rad, M., Beyah, R. (2018). Lowering the bar-
riers to industrial control system security with
{GRFICS}. In 2018 USENIX Workshop on Advances
in Security Education.
Fovino, I., Carcano, A., Masera, M., Trombetta, A. (2009).
Design and implementation of a secure mod- bus pro-
tocol. In International conference on critical infrastruc-
ture protection, pg. 83–96. Springer.
Hussain, S., Ustun, T., Kalam, A. (2019). A review of iec
62351 security mechanisms for iec 61850 message ex-
changes. IEEE Transactions on Industrial Informatics,
16(9):5643–5654.
Ilgner, P., Cika, P., Stusek, M. (2021). Scada-based mes-
sage generator for multi-vendor smart grids: Distribut-
ed integration and verification of tase. 2. Sensors,
21(20):6793.
Incorporated, A. (2005). BusWorks® 900EN Series: 10/
100M Industrial Ethernet I/O Modules w/Modbus.
Kosanke, K. (2006). Iso standards for interoperability: A
comparison. In Interoperability of enterprise software
and applications, pg. 55–64. Springer.
Liljenstam, M., Liu, J., Nicol, D., Yuan, Y., Yan, G., Grier,
C. (2005). Rinse: The real-time immersive network si-
mulation environment for network security exercises.
In Workshop on Principles of Advanced and Distribu-
ted Simulation, pg. 119–128. IEEE.
Macaulay, T., Singer, B. L. (2011). Cybersecurity for indu-
strial control systems: SCADA, DCS, PLC, HMI, and
SIS. CRC Press.
Mackiewicz, R. E. (2006). Overview of iec 61850 and ben-
efits. In 2006 IEEE Power Engineering Society General
Meeting, pg. 8–10. IEEE.
Mai, K., Qin, X., Silva, N., Cardenas, A. (2019). Iec 60870-
5-104 network characterization of a large-scale opera-
tional power grid. In 2019 IEEE Security and Privacy
Workshops, pg. 236–241. IEEE.
Maidl, M., Kroselberg, D., Christ, J., Beckers, K. (2018). A
comprehensive framework for security in engineering
projects-based on iec 62443. In 2018 IEEE Interna-
tional Symposium on Software Reliability Engineering
Workshops, pg. 42–47. IEEE.
Mallouhi, M., Al-Nashif, Y., Cox, D., Chadaga, T., Hariri,
S. (2011). A testbed for analyzing security of SCA-DA
control systems. In ISGT 2011, pg. 1–7. IEEE.
Marais, H. (2008). Rs-485/rs-422 circuit implementation
guide. AN-960 Analog Devices.
Mattioli, R., Moulinos, K. (2015). Analysis of ICS-SCADA
cyber security maturity levels in critical sec-tors.
Modbus Organization (2006). Modbus messaging on TCP/
IP Implementation Guide V1.
Journal on Wireless Communications and Networking,
2012(1):1–17.
Newman, H. (2013). Bacnet explained. ASHRAE Journal.
ODVA (2006). Common Industrial Protocol (CIP).
OPS Telecom (2023). Understanding modbus protocol - rtu
vs tcp vs ascii.
Page, M., et al. (2021). The Prisma 2020 statement: An
updated guideline for reporting systematic reviews. 88:
105906.
Pan, J., Jain, R. (2008). A survey of network simulation to-
ols: Current status and future developments. 2(4):45.
Parcharidis, M. (2018). Simulation of cyber-attacks against
scada systems.
Peacock, M. (2019). Anomaly detection in bacnet/ip
managed building automation systems.
Peacock, M., Johnstone, M., Valli, C., Camp, O., Mori, P.,
Furnell, S. (2017). Security issues with bacnet value
handling. In ICISSP, pg. 546–552.
Qassim, Q., et al., (2017). A survey of SCADA testbed imp-
lementation approaches. Indian Journal of Science and
Technology, 10(26):1–8.
Queiroz, C., Mahmood, A., Tari, Z. (2011). Scada-sim - A
framework for building scada simulations. IEEE
Transactions on Smart Grid, 2(4):589– 597.
Radoglou-Grammatikis, P., Sarigiannidis, P., Giannoula-
kis, I., Kafetzakis, E., Panaousis, E. (2019). Attacking
iec-60870-5-104 SCADA systems. In 2019 IEEE
World Congress on Services, vol. 2642, pg. 41–46.
IEEE.
Slatman H. A curated list of resources related to Industrial
Control System (ICS) security.
Sidhu, T., Kanabar, M., Parikh, P. (2008). Implementation
issues with iec 61850 based substation automation
systems. In 15
th
National Power Systems Conference,
pg. 473–478.
Song, J., Han, S., Mok, A., Chen, D., Lucas, M., Nixon, M.,
Pratt, W. (2008). Wirelesshart: Applying wireless
technology in real-time industrial process control. In
SECRYPT 2024 - 21st International Conference on Security and Cryptography
24

2008 IEEE Real-Time and Embedded Technology and
Applications Symposium, pg. 377–386. IEEE.
Stouffer, K., Falco, J. (2006). Guide to supervisory control
and data acquisition (SCADA) and industrial control
systems security. NIST.
Tang, S., Shelden, D. R., Eastman, C. M., Pishdad-Bozorgi,
P., Gao, X. (2020). Bim assisted building automation
system information exchange using bacnet and ifc. Au-
tomation in Construction, 110:103049.
Varga, A. (2005). Omnet++ discrete event simulation sys-
tem, ver. 3.2, User Manual.
Weehuizen, F., Brown, A., Sunder, C., Hummer, O. (2007).
Implementing IEC 61499 communication with the cip
protocol. In 2007 IEEE Conference on Emerging Tech-
nologies and Factory Automation, pg. 498–501. IEEE.
Xarhoulacos, C. G., Anagnostopoulou, A., Stergiopoulos,
G., & Gritzalis, D. (2021). Misinformation vs. situa-
tional awareness: The art of deception and the need for
cross-domain detection. Sensors, 21(16), 5496.
Yu, Y.-S., Chen, C.-H., Cheng, K. (2018). Design and im-
plementation of a remote hart configurator. In 2018
IEEE International Conference on Applied System In-
vention, pg. 510–512. IEEE.
From Plant to Lab: Industrial Emulation Tools for Real-World Security Testing in Industrial Control Systems
25
