
Blockchain for Privacy-Preserving Data Distribution in Healthcare
Amitesh Singh Rajput and Arnav Agrawal
Department of Computer Science & Information Systems, Birla Institute of Technology & Science, Pilani, Vidya Vihar,
Pilani, Rajasthan, India
Keywords:
Blockchain Technology, Healthcare Data Security, Decentralized Data Management,
Smart Contracts in Healthcare, Encryption and Key Management, Authentication Protocols.
Abstract:
As virtual transformation maintains to reshape healthcare, the security and privacy of health information
have become paramount worries. This paper delves into the novel application of blockchain generation as a
strategic technique to these urgent issues. In contrast to traditional centralized information control structures,
blockchain introduces an intensive alternate with its decentralized, immutable, and transparent nature. This
shift gives a robust alternative to comply with sensitive health data. We propose a contemporary, blockchain-
primarily based method to seamlessly integrate existing healthcare records into ledgers and share them in a
controlled way. The proposed method emphasizes enhanced data integrity, advanced security features, and a
patient-centric technique to data governance using customized smart contracts. Experimental results underline
the proposed method’s advanced performance for scalability, protection, and general machine performance,
making a compelling case for its adoption in healthcare records control.
1 INTRODUCTION
In today’s complex digital world, the healthcare sector
is particularly sensitive due to its critical nature. With
an unparalleled emphasis on the sanctity, safety, and
accessibility of facts, healthcare gives multifaceted
challenges. The very lifeblood of medical practices
and studies, patient records, is often saved in cen-
tralized databases. While these centralized structures
have long been taken into consideration as reliable
workhorses, they are being more identified for their
inherent flaws and vulnerabilities (Aslan et al., 2023).
Centralized healthcare databases, although effi-
cient in many respects, are susceptible to a variety
of challenges. These range from system failures,
cyber-attacks, unauthorized data breaches to poten-
tial data tampering (Newaz et al., 2021). Further-
more, the modern demand for seamless data flow
and integrated healthcare operations often stumbles
against the brick walls of these fragmented and iso-
lated systems. Our study addresses this problem by
providing a blockchain-based model for healthcare
data distribution. Blockchain technology offers a
promising answer to overcome the limitations of con-
ventional centralized systems (Haleem et al., 2021).
In the healthcare sector, where data sensitivity and
privacy are paramount, blockchain can revolutionize
how person’s data is stored, accessed, and shared.
A blockchain-based system can mitigate risks associ-
ated with centralized databases by means of dispens-
ing the data across a network, making it less vulnera-
ble to single points of failure and cyber assaults. This
guarantees better data integrity and protection. Addi-
tionally, blockchain’s transparent nature allows better
trust and auditability in data transactions, that is crit-
ical in healthcare wherein data accuracy and history
are important.
In recent years, several blockchain-based medical
recordkeeping systems have been developed, offer-
ing innovative solutions to the challenges in health-
care data management. For instance, MedRec (Azaria
et al., 2016a) is a notable system that uses Ethereum
blockchain for managing access to medical records.
It provides a decentralized record management sys-
tem to handle authentication, confidentiality, account-
ability, and data sharing. HealthChain (Chenthara
et al., 2020) focuses on ensuring data integrity and
access control in healthcare records. It allows for
a secure and transparent record-keeping mechanism
that patients and providers can trust. MediBlock
(Vishwa, 2021) is another significant advancement in
this space, providing a patient-centered approach. It
emphasizes patient consent and uses blockchain to se-
cure medical records.
Key Authorities (KAs) are essential in
blockchain-based healthcare data systems. They
Rajput, A. and Agrawal, A.
Blockchain for Privacy-Preserving Data Distribution in Healthcare.
DOI: 10.5220/0012470500003648
Paper published under CC license (CC BY-NC-ND 4.0)
In Proceedings of the 10th International Conference on Information Systems Security and Privacy (ICISSP 2024), pages 621-631
ISBN: 978-989-758-683-5; ISSN: 2184-4356
Proceedings Copyright © 2024 by SCITEPRESS – Science and Technology Publications, Lda.
621

are accountable for dealing with cryptographic keys,
making sure that the data is secure, maintaining
data integrity, facilitating secure transactions, and
contributing to system scalability. KAs play an
important role in protecting sensitive healthcare data,
making them essential to the security and capability
of such systems. Despite the innovative and potential
solutions for the health records, previous researches
(Azaria et al., 2016a)(Chenthara et al., 2020)(Vishwa,
2021) have not emphasized on this fundamental part.
We consider this part as utmost important along with
robust patient data sharing and propose a blockchain
based automated approach in this paper. We propose
a comprehensive set of rules, intricately designed,
showcasing how blockchain can be seamlessly
integrated into the healthcare facts pipeline involving
an extensive functioning for KAs. By examining its
core attributes, we unravel how blockchain could be
the keystone in constructing a robust healthcare data
ecosystem.
This paper aspires to make a case for a blockchain-
driven healthcare data revolution. In the follow-
ing sections, we will discover a meticulous break-
down of current challenges in section 2, our proposed
blockchain solution and its practical algorithmic de-
scriptions in section 3, followed by a thorough ex-
perimental analysis and comparison with the existing
blockchain methods in section 4. We believe that our
research not only contributes extensively to academic
discourse but additionally paves the manner for prac-
tical, tangible upgrades in the real world of healthcare
data management.
2 LITERATURE REVIEW
Data distribution, especially in an age of escalat-
ing cybersecurity threats and stringent privacy regu-
lations, is a domain of paramount importance. Ad-
dressing countless challenges in this area necessitates
a holistic understanding of both the historical context
and the forefront of current advancements. This lit-
erature review describes the landscape of data distri-
bution, particularly emphasizing the following three
pivotal facets:
1. Challenges of Traditional Data Distribution
Systems. An exploration into the pitfalls and
vulnerabilities of legacy systems, highlighting the
need for innovative solutions.
2. Blockchain’s Emergence in Privacy-Preserving
Data Distribution. Recognising blockchain’s
revolutionary potential to reimagine safe and
transparent data distribution paradigms.
3. Existing Access Control Methods Integrating
Multiple Entities in the Overall System. A
thorough examination of prior methods combin-
ing several entities to overcome current obstacles.
2.1 Challenges of Traditional Data
Distribution Systems
Traditional data distribution systems play an integral
role in various sectors, especially in the age of dig-
ital transformation. However, their inherent design
and operational characteristics present multiple chal-
lenges.
Centralized data distribution boasts ease of man-
agement, uniformity of data versions, and straightfor-
ward administrative control (Inclusion Cloud, 2023).
An attack on this system can render the entire data dis-
tribution network vulnerable resulting in irreversible
data loss (Mohammed et al., 2010).The linear scal-
ing model of infrastructure leads to longer response
times. In cases even system downtime. This nega-
tively impacts both user experience and operational
efficiency (Bertin et al., 2009). Centralized data
servers are typically located in different regions. Con-
sequently they become subject to laws that may not
align with operations or could impose restrictions
on data access. This can lead to inconsistencies in
operations (Salmon and Myers, 2019).With all data
stored in a location there is a risk of monopolization
where the controlling entity may misuse the informa-
tion (McIntosh, 2018). Without immutable record-
keeping, changes to data can go undetected. This
lack of an unalterable history can result in large com-
mercial enterprise disputes, mainly in sectors wherein
data sanctity is paramount (Pandey et al., 2020). Tra-
ditional systems might not always provide mecha-
nisms for real-time data validation, making it difficult
to immediately detect and rectify data inconsistencies
(Kumar and Bhatia, 2020).
The centralized model, in many instances, does
not maintain transparent data modification logs. Such
opacity makes it challenging to trace data changes,
leading to potential trust breaches (Abiteboul and
Stoyanovich, 2019). All decisions, including data ac-
cess, distribution rules, and dispute resolutions, are at
the discretion of a central authority. Such a system
might not always be in the best interests of all stake-
holders involved (Laoutaris, 2018). The centralized
nature necessitates regular maintenance, leading to re-
current costs and potential downtimes (Chukmaitov
et al., 2015). They consume enormous amounts of en-
ergy, leading to operational inefficiencies and larger
carbon footprints (Chukmaitov et al., 2015). Central-
ized servers, especially during peak times, can face
ICISSP 2024 - 10th International Conference on Information Systems Security and Privacy
622

bandwidth constraints, slowing down data dissemina-
tion rates (Hugoson, 2009).
Researchers and developers around the world have
been investigating alternate paradigms for data deliv-
ery in light of these difficulties. With its decentralised
structure, immutable record-keeping, and strong se-
curity features, blockchain technology has gained at-
tention as a possible solution to several of these issues
(Bhutta et al., 2021).
2.2 Blockchain’s Emergence in
Privacy-Preserving Data
Distribution
Blockchain technology stands out as a highly promis-
ing option for data distribution including built-in at-
tributes like traceability, transparency, and resistance
to tampering (Attaran, 2022). Numerous approaches
that take advantage of blockchain technology have
been put out and investigated; these have primarily
concerned healthcare and distribution while maintain-
ing anonymity. Here, we examine some of the most
significant developments in this field, shedding light
on novel approaches and their consequences.
2.2.1 Blockchain in Healthcare: A Paradigm
Shift
Blockchain, at the start conceptualized for the Bitcoin
cryptocurrency (Nakamoto, 2008), has found great
applications in healthcare, especially in protecting the
integrity, authenticity, and confidentiality of health
records (Azaria et al., 2016b). The decentralized and
immutable nature of the blockchain ensures that every
transaction, or in the case of healthcare, every data en-
try or access, is transparently recorded and verified by
a network of peers.
MedRec, introduced by Azaria et al. (Azaria
et al., 2016b), is an influential work that offers a
decentralized electronic health records system using
Ethereum’s blockchain. This system presents solu-
tions to the challenges of data interoperability, ac-
cess controls, and auditability in traditional EHR sys-
tems. By granting patients the power to grant ac-
cess to their health records and ensuring a transpar-
ent record of data access, MedRec paves the way for
improved patient-centric healthcare.
Furthermore, Yue et al. (Yue et al., 2016) pro-
posed a scheme named “Healthcare Data Gateways”,
leveraging blockchain to ensure data security, privacy,
and interoperability in health information exchange.
The framework emphasizes the role of patient con-
sent in data sharing and makes use of smart contracts
to automate and enforce data access policies.
2.2.2 Privacy-Preserving Distribution with
Blockchain
While healthcare is a predominant domain, the ex-
tensive theme of privacy preservation facilitated by
blockchain extends to various data distribution mod-
els. Zhang et al. (Zhang and Wen, 2017) intro-
duced a privacy-preserving framework which utilizes
blockchain for secure and transparent file access in
cloud environments. This framework harnesses the
decentralized consensus mechanism of blockchain to
deter unauthorized data access and modifications.
Another notable advancement is the work of Liang
et al. (Liang et al., 2017), where they propose a credit-
based scheme for privacy-preserving data sharing in
the context of the Internet of Things (IoT). Their
methodology combines the blockchain with a credit
system, ensuring that data providers and consumers
maintain a trust-based relationship, with transactions
transparently recorded and verified on the blockchain.
In addressing the challenge of non-interoperable
medical data sharing, there is a blockchain-based sys-
tem employing symmetric encryption, access con-
trol, and participant power restriction. Their sys-
tem ensures privacy by encrypting medical data, uti-
lizing a novel blockchain framework, implementing
chameleon signatures, and enabling revocable partic-
ipant privileges. Security analysis validates its ro-
bustness, and experiments demonstrate superior time
overhead compared to alternatives (Hu et al., 2023).
In response to security challenges in medical
data transmission and sharing, Chen proposed a
blockchain-based medical information system ensur-
ing data integrity and privacy. Their model employs
IoT for real-time patient health record collection and
introduces a secure, anonymous data sharing scheme
based on cloud servers and proxy re-encryption. Im-
plemented on Hyperledger Fabric, the system features
a dual-channel architecture and medical chaincode for
efficient data management and access control. (Chen
et al., 2021).
Huang presented a blockchain-based privacy-
preserving scheme addressing the challenge of bal-
ancing patient privacy with the demands of health
data research and commerce. The proposed scheme
enables secure sharing of medical data among en-
tities, including patients, research institutions, and
semi-trusted cloud servers. Utilizing zero-knowledge
proof for privacy-preserving verification and proxy
re-encryption for intermediary data decryption, the
scheme ensures data availability and consistency.
(Huang et al., 2020).
Blockchain for Privacy-Preserving Data Distribution in Healthcare
623

2.3 Existing Access Control Methods
Integrating Multiple Entities in the
Overall System
The landscape of data distribution has seen countless
techniques aimed at ensuring robustness, efficiency,
and security. A few of the previous methods (Hilde-
brandt et al., 2016)(Erkin et al., )(Rajput and Balasub-
ramanian, 2021) heavily rely with an integration of
multiple entities including KAs, transcryptors (TRs),
doctors, storage facilities, and medical researchers.
The TRs serves as intermediary entities. When a
request for data access is made, it is the TR’s role
to fetch the corresponding cryptographic key from
the KA, perform the necessary decryption operations,
and furnish the requester with the requisite decrypted
data. Other entities may encompass data providers,
end-users, or even audit entities ensuring the system’s
integrity and adherence to established protocols. The
functioning is performed with the data provider en-
crypting the data using cryptographic keys sourced
from the KAs. Once encrypted, the data is set for
distribution. Upon receipt of a valid data access re-
quest, the TR gets into action. It fetches the associated
cryptographic key, decrypts the data, and ensures its
timely delivery to the requester.
One strong challenge with these methods is their
reliance on centralized entities, i.e., the KAs. Central-
ization, while offering streamlined operations can be
a vulnerability concern. Compromising the KA could
potentially jeopardize the entire system’s data secu-
rity. Latency is another big concern which needs to be
taken care of. Given the multiple interactions between
entities, especially between TR and KAs for key re-
trieval, time-sensitive operations can be adversely af-
fected. While the algorithm integrating KAs, TRs,
and other entities showcased potential in addressing
data distribution’s challenges, it wasn’t devoid of lim-
itations. The centralization concerns, latency issues,
and scalability bottlenecks underlined the need for al-
ternative mechanisms that could offer both efficiency
and robust security. It is within this context that the
exploration for newer methods, including those har-
nessing blockchain, emerged.
3 PROPOSED METHOD
This section describes the proposed blockchain-based
method, designed to triumph over the restrictions of
traditional data distribution systems, particularly in-
side the healthcare sector. At its center, our ap-
proach leverages the decentralized, transparent, and
immutable nature of blockchain generation. The ap-
proach is multifaceted, integrating advanced crypto-
graphic strategies, smart contracts, and consensus al-
gorithms to enhance data integrity, security, and trans-
parency. We aim to decentralize data management for
getting rid of single points of failure, improving scala-
bility, and increasing resistance to cyber threats. Fur-
thermore, the proposed approach introduces a patient-
centric version for data governance, ensuring privacy
and hold over personal health records.
In the subsequent subsections, the critical compo-
nents of the proposed approach are described. Also,
the setup of blockchain-based identity management,
secure packet sharing mechanisms, and the processes
for master key generation, data request handling, and
user verification are covered. These additives col-
lectively form a cohesive and robust framework for
healthcare data management, ready to be incorporated
into current healthcare IT infrastructures. The de-
scription contains various specialized algorithms im-
portant with respect to the proposed solution. It is im-
portant to note that the functions in these algorithms
are named to clearly indicate their purpose. This nam-
ing approach helps in easily understanding what each
function does and how it fits into the overall system.
In light of the limitations encountered with the tra-
ditional data distribution techniques and the ineffica-
cies linked to the previously discussed algorithm in-
tegrating KAs, TRs, and other entities, the proposed
proposition pivots toward leveraging the capabilities
of blockchain technology. The emphasis here is not
only to decentralize the data distribution process but
also to harness the inherent security and transparency
features of blockchain. The proposed method lever-
ages customized smart contracts that play a pivotal
role to accomplish the desired tasks. Essentially,
smart contracts are self-executing contracts where the
agreement between the sender and the receiver is di-
rectly written into lines of code. In the context of our
data distribution system, the smart contracts will au-
tomate the validation of data access requests and the
distribution of decryption keys.
In the proposed method, smart contracts exe-
cute algorithms linearly for optimal functionality.
The sequence begins with Identity Registration and
Blockchain Logging (Algorithm 1), establishing veri-
fied user identities on the blockchain. Next, the Ran-
dom Selection of Key Authorities (Algorithm 2) en-
sures unbiased selection of Key Authorities. This
is followed by Secure Verification Packet Sharing
(Algorithm 3), distributing verification data to KAs.
Subsequently, Master Key Generation and Validation
(Algorithm 4) securely generates encryption keys,
and Distribution of Verification Packets (Algorithm
5) ensures secure data dissemination to KAs. Data
ICISSP 2024 - 10th International Conference on Information Systems Security and Privacy
624
Request, Verification & Blockchain Logging (Algo-
rithm 6) then manages and authenticates data re-
quests. Master Key Derivation & Decryption Process
(Algorithm 7) and Data Decryption & Sharing (Al-
gorithm 8) handle the secure decryption and distribu-
tion of data. The process concludes with Repetitive
User Verification (Algorithm 9), maintaining contin-
uous security checks. This ordered execution of al-
gorithms as smart contracts solidifies the system’s in-
tegrity and efficiency in healthcare data management.
3.1 Setting up an Identity and
Registering on the Blockchain
In this section, the algorithm describes the way of
organising a person’s identification inside the sys-
tem and securing it via blockchain technology. The
method begins with the generation of a completely
unique identifier, accompanied by the introduction of
a digital credential which is then stored in a database
for quick access. To ensure the individuality and pre-
vent duplication of identities, the credential is verified
with the prevailing facts on the blockchain. If the cre-
dential is new, it is registered at the blockchain; oth-
erwise, a duplication error is reported. This approach
as present in the algorithm 1 ensures that every person
within the machine has a distinct and verifiable digital
identification.
Algorithm 1: Identity Registration and Blockchain
Logging.
1: Input: User’s name name, blockchain BC
2: Output: Registration status
3: uniqueID ← GENERATEUNIQUEID(name)
4: credential ← (name, uniqueID)
5: STORECREDENTIALS(credential)
6: if ¬VERIFYIDENTITY(credential, BC) then
7: REGISTERONBLOCKCHAIN(credential, BC)
8: else
9: print ”Error: Duplicate identity.”
10: end if
11: function VERIFYIDENTITY(credential, BC)
12: for all block ∈ BC do
13: if block.data = credential then
14: return true
15: end if
16: end for
17: return false
18: end function
19: function STORECREDENTIALS(credential)
20: // Store credentials in the database
21: end function
22: function REGISTERONBLOCKCHAIN(credential, BC)
23: // Add new identity to the blockchain
24: end function
3.2 Secure Verification Packet Sharing
This section establishes a procedure for the secure
creation and dissemination of verification packets,
crucial for the operations of Key Authorities within
the blockchain network. It details a series of steps,
mentioned in algorithm 2, that begin with the genera-
tion of a verification packet, which is uniquely iden-
tified by a hash and timestamp to ensure its integrity.
These packets are then stored securely until they are
to be shared with eligible Key Authorities, with each
sharing event logged on the blockchain to enforce
transparency and traceability.
3.3 Random Selection by TR and
Recording on Blockchain
The selection steps in algorithm 3 operates with a
dual aim: To guarantee fairness in the selection pro-
cess of KAs and to log each selection event onto
the blockchain, thus embedding transparency and im-
mutability into the system. It begins by identifying
KAs that have not been recently active, thereby ensur-
ing an unbiased opportunity for all. A rigorous safety
check follows, verifying the temporal gap since each
KA’s last selection, thus preventing repetitive selec-
tions. Successful candidates are then recorded on the
blockchain, time-stamped to uphold the integrity and
verifiability of the process.
Algorithm 2: Random Selection of KA with Block
Addition.
1: Input: Pool of Key Authorities KA Pool, blockchain BC
2: Output: Selected Key Authority selectedKA
3: function SELECTKEYAUTHORITY(KA Pool)
4: selectedKA ← Select KA not recently chosen
5: if SAFETYCHECK(selectedKA) then
6: RECORDSELECTION(selectedKA, BC)
7: else
8: print ”Selection failed: KA chosen recently.”
9: end if
10: end function
11: function SAFETYCHECK(selectedKA)
12: timeDi f f ← Time since selectedKA’s last selection
13: return timeDi f f ≥ 24 hours
14: end function
15: function RECORDSELECTION(selectedKA, BC)
16: ADDBLOCK(BC, ”SELECTION”, selectedKA, ”current time”)
17: end function
Blockchain for Privacy-Preserving Data Distribution in Healthcare
625

Algorithm 3: Secure Verification Packet Sharing.
1: Input: Data for Verification Packet data, Key Author-
ities KA
2: Output: Status of Verification Packet Sharing
3: function CREATEANDSHAREVERPACKET(data, KA)
4: packet ← CREATEPACKET(data)
5: for all ka ∈ KA do
6: if ISELIGIBLE(ka) then
7: SHAREPACKET(packet, ka)
8: LOGPACKETSHARING(packet, ka)
9: end if
10: end for
11: end function
3.4 Master Key Generation with
Blockchain Validation
The algorithm 4 outlines a secure process for Master
Key (MK) generation, encryption, and storage, cou-
pled with blockchain logging for validation. The MK,
generated with a secure random function and times-
tamped, is encrypted for confidentiality. It’s then
stored in a secure database, with blockchain logging
ensuring transparency and validation checks main-
taining generation at safe intervals.
3.5 Distribution of Verification Packets
The secure and efficient distribution of Verifica-
tion Packets (VP) to Key Authorities (KA) within a
blockchain network is the basis of this system. The
algorithm initiates with the generation of a unique
packet ID and its subsequent encryption. KAs are
selected based on specific criteria for packet distri-
bution, with the entire process being logged onto the
blockchain for accountability. Duplicate distributions
are prevented through a verification mechanism, en-
suring the integrity of the system. All this can be ver-
ified from the Algorithm 5.
Algorithm 4: Master Key Generation and Validation.
1: Input: Security parameters, blockchain BC
2: Output: Master Key Generation and Validation
3: function GENERATEANDVALIDATEMASTERKEY
4: masterKey ← GENERATEMASTERKEY
5: encrKey ← ENCRMASTERKEY(masterKey)
6: STOREENCRYPTEDKEY(encrKey)
7: if VALIDATEKEYGENERATION then
8: LOGKEYGENERATION(encrKey, BC)
9: else
10: print ”Key generation validation failed.”
11: end if
12: end function
3.6 Data Request, Verification &
Blockchain Logging
This subsection outlines the streamlined process of re-
ceiving data requests, verifying requester authenticity,
and logging the transactions on the blockchain. The
Algorithm 6 handles requests with a security-focused
approach, ensuring data integrity and access control.
3.7 Master Key Derivation &
Decryption Process
The Algorithm 7 below starts with the derivation of a
master key (MK) which is an important step in en-
suring the security of the system. It is created us-
ing a secure function and is timestamped to guaran-
tee uniqueness. After derivation, the MK is encrypted
and stored securely. It is then utilized for decrypting
data, enforcing confidentiality. The system logs each
step involving the MK on the blockchain.
Algorithm 5: Distribution of Verification Packets.
1: Input: Verification Packet data data, Key Authorities
KA
2: Output: Distribution status
3: function DISTRIBUTEVERPACKET(data, KA)
4: packetID ← GENERATEPACKETID(data)
5: encryptedPacket ← ENCRYPTPACKET(data)
6: selectedKAs ← SELECTKASFORDISTRIBUTION
7: for ka in selectedKAs do
8: LOGDISTRIBUTIONEVENT(packetID, ka)
9: DISTRIBUTEPACKET(encryptedPacket, ka)
10: print ”Packet distributed to KA”
11: end for
12: CONFIRMFROMKA(packetID, selectedKAs)
13: end function
Algorithm 6: Data Request, Verification & Blockchain
Logging.
1: Input: Request from entity requester, data identifier
dataID
2: Output: Acknowledgment of successful data handling
3: function HANDLEDATARE-
QUEST(requester, dataID, BC)
4: isAuthentic ← VERIFYREQUESTER(requester)
5: if isAuthentic & SAFETYCHECK(requester) then
6: data ← FETCHDATA(dataID)
7: encryptedData ← ENCRYPTDATA(data)
8: TRANSMITDATA(encryptedData, requester)
9: LOGTRANSACTION(requester, dataID, BC)
10: return AWAITRECEIPT(requester)
11: else
12: print ”Request denied.”
13: return False
14: end if
15: end function
ICISSP 2024 - 10th International Conference on Information Systems Security and Privacy
626

3.8 Data Decryption & Sharing
The secure distribution of Verification Packets is a
critical characteristic in our blockchain-based system,
in particular for Key Authorities (KA) who rely upon
these packets for operational data. Each packet is
created with a completely unique identifier, encapsu-
lated securely, after which it is transmitted to a se-
lected group of KAs. This method as mentioned in the
Algorithm 8 guarantees information integrity through
encryption and maintains transparency by recording
each distribution motion at the blockchain.
Algorithm 7: Master Key Derivation and Decryption.
1: Input: inputSeed, encryptedData
2: Output: decryptedData
3: function DERIVEANDENCRYPTMK(inputSeed)
4: masterKey ← derive key using inputSeed
5: encryptedMK ← encrypt masterKey
6: Store encryptedMK securely
7: Log MK creation on blockchain
8: return encryptedMK
9: end function
10: function DECRYPTWITHMK(encryptedData, masterK)
11: decryptedData ← decrypt encryptedData with
masterKey
12: Log decryption on blockchain
13: return decryptedData
14: end function
Algorithm 8: Distribution of Verification Packets.
1: Input: Verification Packet data data, Key Authorities
KAs
2: Output: Distribution status
3: function DISTRIBUTEVERIFICATION-
PACKET(data, KAs)
4: packetID ← GENERATEPACKETID(data)
5: encryptedPacket ← ENCRYPTPACKET(data)
6: selectedKAs ← SELECTKASFORDISTRIBUTION
7: for all ka ∈ selectedKAs do
8: if SAFETYCHECK(ka) then
9: SENDPACKET(encryptedPacket, ka)
10: LOGPACKETSHARING(packetID, ka)
11: print ”Packet distributed to KA: ka”
12: else
13: print ”Distribution to KA: ka failed due to
safety check.”
14: end if
15: end for
16: return CONFIRMRECEIPT(selectedKAs)
17: end function
3.9 Repetitive User Verification
The Repetitive User Verification process mentioned
in the Algorithm 9 within the system is designed to
set up and preserve the authenticity of user identities.
By capturing user details and validating identities, the
device ensures that only legitimate users can get entry
to sensitive information. The blockchain logs each
verification attempt, providing an immutable record
of user activity. Enhanced safety features, along with
multi-factor authentication and checks for fraudulent
tries, shield against unauthorized access. Any unusual
activities are monitored and reported, underscoring
the system’s commitment to security and user trust.
Algorithm 9: Repetitive User Verification.
1: Input: User ID userID, Verification Details
userDetails
2: Output: Verification Status
3: function VERIFYUSER(userID, userDetails)
4: details ← CAPTUREUSERDETAILS(userDetails)
5: if VALIDATEUSERIDENTITY(details) then
6: LOGVERIFICATIONEVENT(userID, success)
7: INITIATEMULTIFACTORAUTHENTICA-
TION(userID)
8: print ”User verified successfully.”
9: else
10: if SAFETYCHECKFORFRAUDULENTAT-
TEMPTS(userID) then
11: LIMITUNSUCCESSFULAT-
TEMPTS(userID)
12: REPORTSUSPICIOUSACTIVITY(userID)
13: print ”User verification failed.”
14: end if
15: end if
16: end function
4 EXPERIMENTAL RESULTS
The experimental results presented here are derived
from simulations that model the overall performance
of the proposed blockchain-based system. Our com-
prehensive evaluation specializes in several key per-
formance indicators inclusive of throughput, latency,
scalability, security, and smart contract execution
metrics. The simulations have been performed on a
virtualized test network replicating a medium-scale
enterprise environment to offer a realistic evaluation
of system capabilities.
4.1 Simulation Environment
The testing environment set up specifications include
Ubuntu 20.04 LTS Operating System, Intel Xeon
CPU E5-2698 v4 @2.20GHz Processor, 64GB RAM,
Blockchain for Privacy-Preserving Data Distribution in Healthcare
627

1 TB SSD, Ethereum Testnet blockchain platform,
followed by Proof of Authority (PoA) consensus al-
gorithm, and 25 validator nodes.
The selection of Proof of Authority (PoA) as the
consensus mechanism is rooted in its suitability for
healthcare data management. PoA provides a secure
and efficient environment, crucial for handling sen-
sitive health records. Key reasons for choosing PoA
include:
• Trust and Identity Verification. PoA ensures
validators are known entities, enhancing trust and
security, essential in healthcare for regulatory
compliance.
• Efficient Transaction Processing. PoA offers
faster transaction times compared to PoW or PoS,
crucial for real-time healthcare applications.
• Energy Efficiency. Less energy-intensive than
PoW, PoA aligns with sustainable IT practices in
healthcare.
• Controlled Network Access. Restricts network
participation to verified entities, maintaining data
privacy and adhering to healthcare regulations.
• Balance of Centralization. PoA’s selective val-
idator approach mitigates risks associated with
centralization, ensuring decentralized control.
4.2 Throughput and Latency
The table showcasing throughput and latency illus-
trates how the system effectively handles growing
numbers of transactions. As the transaction count
rises from 100 to 5000, the system’s throughput, mea-
sured in Transactions Per Second (TPS), increases.
However, past a certain point (at 5000 transactions), a
slight descrease in throughput is found, probably be-
cause of the increased load. Latency, or the time taken
to complete a transaction, understandably increases
with the range of transactions, but stays inside a rea-
sonable range, showing the system’s responsiveness
even under heavy load.
Table 1: System Throughput and Latency.
Number of Trans-
actions
Throughput
(TPS)
Latency
(Seconds)
100 50 2
500 150 4
1000 200 6
5000 180 10
4.3 Scalability Analysis
The Scalability analysis table reflects the system’s
ability to maintain overall performance as the nodes
increase in number. The average transaction time
shows a slow growth as extra nodes are brought, in-
dicating a modest effect on performance. This up-
ward push is highly linear and mild, suggesting that
the device scales well. The capacity to deal with extra
nodes with only a minor increase in transaction time
is a strong indicator of the system’s scalability and its
capacity for larger-scale deployment.
Table 2: Scalability Test Results.
Number of Nodes Average Transaction
Time (Seconds)
10 2
20 2.2
30 2.5
40 2.75
50 3
4.4 Security Analysis
The security evaluation was executed to evaluate the
resilience of the proposed blockchain-based system
against various attack vectors, taking into account its
unique structure and functionalities. The evaluation
covered exclusive threat models which can be rele-
vant to the system’s operational context in healthcare
data management.
4.4.1 Threat Models and Resistance
Mechanisms
1. DDoS Attack. The system’s decentralized nature,
combined with PoA consensus, inherently resists
DDoS attacks, as attackers cannot target a single
central point. The distributed validator nodes en-
sure continuous network functionality even under
high load.
Proof. The blockchain system employs a dis-
tributed network of validator nodes. Let N be the
total number of nodes in the network. The prob-
ability P of successfully disrupting the network
is given by P =
1
N
n
, where n is the number of
nodes an attacker needs to compromise. Given the
large number of nodes in a distributed system, this
probability approaches zero, thus demonstrating
the resilience of the system against DDoS attacks.
2. Double-Spending. The blockchain’s immutable
ledger prevents double-spending by maintain-
ing a transparent and unalterable transaction his-
ICISSP 2024 - 10th International Conference on Information Systems Security and Privacy
628

tory. Each transaction is verified and recorded
across multiple nodes, making fraudulent at-
tempts highly impractical.
Proof. Assume a transaction T is initiated. For
T to be double-spent, it must be replicated as T
′
.
However, the blockchain’s consensus mechanism
requires that all transactions be verified by mul-
tiple nodes. The probability of T
′
being accepted
by all verifying nodes without detection is negligi-
bly small. Hence, the system effectively mitigates
the risk of double-spending.
3. Sybil Attack. The PoA mechanism requires val-
idators to be pre-approved, limiting the potential
for Sybil attacks. Validators are trusted entities,
reducing the risk of malicious nodes entering the
network.
Proof. Consider a network with a set of pre-
approved validators using the PoA consensus. Let
V be the set of all validators and S be the subset of
malicious validators an attacker attempts to intro-
duce. The system’s trust model and validator ap-
proval process ensure that |S| ≪ |V | that reduces
the effectiveness of any Sybil attack.
4. Insider Threats. Smart contracts use for critical
operations such as data access and identity ver-
ification minimizes human intervention, thereby
reducing the risk of insider threats.
Proof. Smart contracts in the system au-
tonomously execute predefined tasks without hu-
man intervention. Let I be the set of all poten-
tial insider attackers. The absence of direct con-
trol over data by any member of I significantly re-
duces the probability of successful insider threats,
ensuring the security of the system against such
attacks.
Each threat model was addressed through a com-
bination of blockchain’s inherent features and specific
design choices made for the system. While analysing
security breach attempts, different attack types were
rigorously examined against our systems. There were
approximately 1000 attempts of Distributed Denial
of Service (DDoS) attacks, 500 attempts of Double-
Spending attacks, 300 Sybil attacks, and 200 in-
stances of Insider Threats. These type of attempts re-
sulted in a 0% breach success rate, demonstrating the
robustness and effectiveness of our security measures.
4.5 Smart Contract Performance
Table 3 provides insights into the performance of key
smart contracts inside the system. It gives informa-
tion regarding the execution time and gas fee for ev-
ery agreement, such as Identity Registration, Data Re-
quest, and Verification Packet. The execution times
are brief, demonstrating the system’s performance in
processing these critical operations. The gas costs,
a measure of the computational resources required,
are notably low, indicating an economically feasible
model for running these contracts on the blockchain
network.
Table 3: Smart Contract Execution Metrics.
Smart Contract Execution
Time (ms)
Gas
Cost
Identity Registration 150 0.0003
Data Request 200 0.0004
Verification Packet 250 0.0002
4.6 Discussion and Comparative
Analysis with MedRec
Experimental results validate the technical and prac-
tical viability of the proposed blockchain-based sys-
tem. It successfully handles a huge quantity of trans-
actions with minimal latency, an important feature for
healthcare applications requiring real-time data pro-
cessing. The scalability evaluations show that the sys-
tem sustains performance despite increased network
size, appropriate for tremendous deployment.
The system demonstrates strong resilience to-
wards common cyber threats like DDoS attacks,
double-spending, Sybil attack and Insider threats, un-
derlining its robustness for healthcare data manage-
ment wherein safety and patient privacy are essen-
tial. Smart contracts, pivotal for automating key pro-
cesses along with identification verification and data
requests, perform successfully in terms of execution
time and useful resource usage. The experimental
outcomes suggest the machine’s readiness for health-
care implementation. Its extremely good throughput,
low latency, protection and scalability, coupled with
smart contract performance, gift it as a promising an-
swer for transforming healthcare data control.
A comparative analysis between the exist-
ing blockchain based healthcare data management
method MedRec (Azaria et al., 2016a) and the pro-
posed method is presented in Table 4. This compre-
hensive assessment aims to highlight the distinctions
and similarities in both the approaches to data protec-
tion, patient consent, interoperability, and other im-
portant aspects of healthcare data management.
The comparative analysis sheds light on the re-
spective strengths and improvement areas of both sys-
tems. While the MedRec system lays a foundational
framework using blockchain for healthcare data, our
proposed approach builds and expands upon these
Blockchain for Privacy-Preserving Data Distribution in Healthcare
629
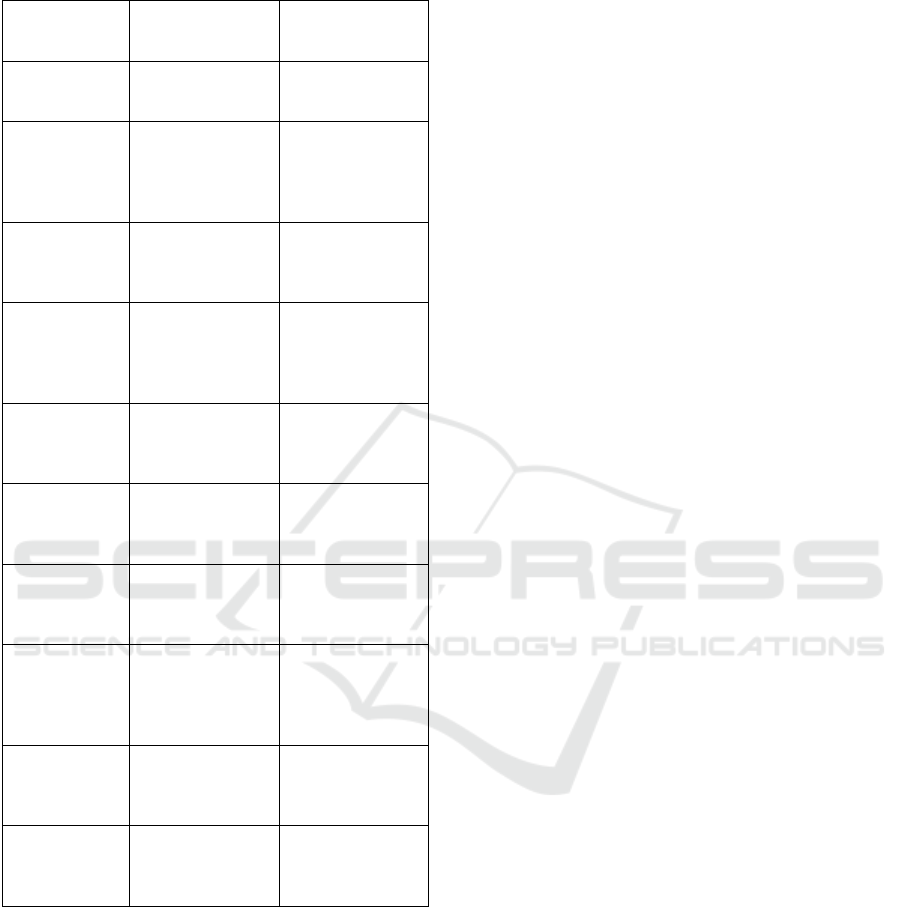
Table 4: Comparison of proposed method and MedRec
(Azaria et al., 2016a).
Feature Proposed
method
MedRec
(Azaria et al.,
2016a)
Blockchain
Platform
Utilizes a custom
blockchain archi-
tecture.
Employs
Ethereum
blockchain.
Data Security Enhanced
through ad-
vanced crypto-
graphic tech-
niques.
Relies on
Ethereum’s
inherent security
features.
Patient Con-
sent
Automated con-
sent via smart
contracts.
Patient consent
managed through
Ethereum trans-
actions.
Interoperability Designed for
seamless integra-
tion with existing
healthcare sys-
tems.
Focuses on
interoperabil-
ity within
the Ethereum
ecosystem.
Data Access
Control
Controlled by
smart contracts
for precise data
governance.
Access control is
managed through
Ethereum smart
contracts.
Scalability Addresses scala-
bility with a tai-
lored approach to
healthcare data.
Faces typi-
cal scalability
challenges of
Ethereum.
Consensus
Mechanism
Uses Proof of
Authority (PoA)
for efficiency and
security.
Dependent on
Ethereum’s
consensus mech-
anism.
Patient Data
Privacy
Prioritizes pa-
tient privacy with
decentralized
data manage-
ment.
Ensures pri-
vacy through
blockchain’s
transparent na-
ture.
Audit Trails Transparent and
immutable audit
trails for data
transactions.
Similar approach
using Ethereum’s
ledger.
Customizability High degree of
customization
for healthcare
needs.
Limited by
Ethereum’s plat-
form constraints.
concepts. By introducing enhanced scalability, cus-
tomizability, and better integration capabilities, the
proposed method demonstrates considerable advance-
ments over the MedRec system, further advancing
blockchain technology’s application in healthcare.
5 CONCLUSION
This research has considerably explored the potential
of blockchain generation in revolutionizing the data
distribution mechanisms in healthcare. Through an
intensive examination of the constraints inherent in
conventional centralized structures, we have analyzed
the transformative impact of blockchain’s decentral-
ized, transparent, and immutable nature. The pro-
posed blockchain-primarily based method not only
addresses the key worrying conditions of data in-
tegrity, security, and transparency but additionally in-
troduces advanced interoperability and patient-centric
data handling. Experimental results confirm the
prevalence of the blockchain approach in terms of
throughput, latency, scalability, and safety, indicating
its readiness for actual-world implementation. This
study reaffirms blockchain’s ability in healthcare data
control and also sets a basis for future exploration
into its broader applications in various sectors. Fu-
ture research may additionally focus on the practical
deployment challenges, integration with present sys-
tems, and exploring the synergy among blockchain
and different emerging technology which includes AI
and IoT in healthcare.
REFERENCES
Abiteboul, S. and Stoyanovich, J. (2019). Transparency,
fairness, data protection, neutrality: Data manage-
ment challenges in the face of new regulation. Journal
of Data and Information Quality (JDIQ), 11(3):1–9.
Aslan,
¨
O., Aktu
ˇ
g, S. S., Ozkan-Okay, M., Yilmaz, A. A.,
and Akin, E. (2023). A comprehensive review of cyber
security vulnerabilities, threats, attacks, and solutions.
Electronics, 12(6).
Attaran, M. (2022). Blockchain technology in healthcare:
Challenges and opportunities. International Journal
of Healthcare Management, 15(1):70–83.
Azaria, A., Ekblaw, A., Vieira, T., and Lippman, A.
(2016a). Medrec: Using blockchain for medical data
access and permission management. In 2016 2nd in-
ternational conference on open and big data (OBD),
pages 25–30. IEEE.
Azaria, A., Ekblaw, A., Vieira, T., and Lippman, A.
(2016b). Medrec: Using blockchain for medical data
access and permission management. In 2016 2nd in-
ternational conference on open and big data (OBD),
pages 25–30. IEEE.
Bertin, P., Bonjour, S., and Bonnin, J.-M. (2009). Dis-
tributed or centralized mobility? In GLOBECOM
2009-2009 IEEE Global Telecommunications Confer-
ence, pages 1–6. IEEE.
Bhutta, M. N. M., Khwaja, A. A., Nadeem, A., Ahmad,
H. F., Khan, M. K., Hanif, M. A., Song, H., Al-
shamari, M., and Cao, Y. (2021). A survey on
blockchain technology: Evolution, architecture and
security. Ieee Access, 9:61048–61073.
Chen, Z., Xu, W., Wang, B., and Yu, H. (2021). A
blockchain-based preserving and sharing system for
medical data privacy. Future Generation Computer
Systems, 124:338–350.
ICISSP 2024 - 10th International Conference on Information Systems Security and Privacy
630

Chenthara, S., Ahmed, K., Wang, H., Whittaker, F., and
Chen, Z. (2020). Healthchain: A novel framework on
privacy preservation of electronic health records using
blockchain technology. Plos one, 15(12):e0243043.
Chukmaitov, A., Harless, D. W., Bazzoli, G. J., Carretta,
H. J., and Siangphoe, U. (2015). Delivery sys-
tem characteristics and their association with quality
and costs of care. Health care management review,
40(2):92–103.
Erkin, Z., Mennink, B., Nateghizad, M., and Maulany, C.
Privacy-preserving distributed access control for med-
ical data. In Samarati, P.(ed.), Proceedings of the 15th
International Joint Conference on e-Business and
Telecommunications - SECRYPT, July 26-28, 2018,
in Porto, Portugal, pages 322–331, 2018. Setubal:
SCITEPRESS.
Haleem, A., Javaid, M., Singh, R. P., Suman, R., and Rab, S.
(2021). Blockchain technology applications in health-
care: An overview. International Journal of Intelli-
gent Networks, 2:130–139.
Hildebrandt, M., Verheul, E., Jacobs, B., Meijer, C.,
and de Ruiter, J. (2016). Polymorphic encryption
and pseudonymisation for personalised healthcare: A
whitepaper.
Hu, M., Ren, Y., and Chen, C. (2023). Privacy-preserving
medical data-sharing system with symmetric encryp-
tion based on blockchain. Symmetry, 15(5):1010.
Huang, H., Zhu, P., Xiao, F., Sun, X., and Huang, Q. (2020).
A blockchain-based scheme for privacy-preserving
and secure sharing of medical data. Computers & Se-
curity, 99:102010.
Hugoson, M.-
˚
A. (2009). Centralized versus decentral-
ized information systems: A historical flashback. In
History of Nordic Computing 2: Second IFIP WG
9.7 Conference, HiNC2, Turku, Finland, August 21-
23, 2007, Revised Selected Papers 2, pages 106–115.
Springer.
Inclusion Cloud (2023). Centralized vs. decentralized data:
Unveiling the great debate.
Kumar, R. and Bhatia, M. (2020). A systematic review of
the security in cloud computing: data integrity, confi-
dentiality and availability. In 2020 IEEE International
Conference on Computing, Power and Communica-
tion Technologies (GUCON), pages 334–337. IEEE.
Laoutaris, N. (2018). Data transparency: Concerns and
prospects [point of view]. Proceedings of the IEEE,
106(11):1867–1871.
Liang, X., Shetty, S., Tosh, D., Kamhoua, C., Kwiat, K.,
and Njilla, L. (2017). Provchain: A blockchain-
based data provenance architecture in cloud environ-
ment with enhanced privacy and availability. In 2017
17th IEEE/ACM International Symposium on Cluster,
Cloud and Grid Computing (CCGRID), pages 468–
477. IEEE.
McIntosh, D. (2018). We need to talk about data: how dig-
ital monopolies arise and why they have power and
influence. J. Tech. L. & Pol’y, 23:185.
Mohammed, N., Fung, B. C., Hung, P. C., and Lee, C.-K.
(2010). Centralized and distributed anonymization for
high-dimensional healthcare data. ACM Transactions
on Knowledge Discovery from Data (TKDD), 4(4):1–
33.
Nakamoto, S. (2008). Bitcoin: A peer-to-peer electronic
cash system. Decentralized business review.
Newaz, A. I., Sikder, A. K., Rahman, M. A., and Uluagac,
A. S. (2021). A survey on security and privacy is-
sues in modern healthcare systems: Attacks and de-
fenses. ACM Transactions on Computing for Health-
care, 2(3):1–44.
Pandey, A. K., Khan, A. I., Abushark, Y. B., Alam, M. M.,
Agrawal, A., Kumar, R., and Khan, R. A. (2020). Key
issues in healthcare data integrity: Analysis and rec-
ommendations. IEEE Access, 8:40612–40628.
Rajput, A. S. and Balasubramanian, R. (2021). Privacy-
preserving distribution and access control of personal-
ized healthcare data. IEEE Transactions on Industrial
Informatics, pages 1–1.
Salmon, J. and Myers, G. (2019). Blockchain and associ-
ated legal issues for emerging markets.
Vishwa, A. (2021). MediBlock-A Privacy-aware
Blockchain to store patients data and effective
diagnosis methods. PhD thesis.
Yue, X., Wang, H., Jin, D., Li, M., and Jiang, W. (2016).
Healthcare data gateways: found healthcare intelli-
gence on blockchain with novel privacy risk control.
Journal of medical systems, 40:1–8.
Zhang, Y. and Wen, J. (2017). The iot electric business
model: Using blockchain technology for the internet
of things. Peer-to-Peer Networking and Applications,
10:983–994.
Blockchain for Privacy-Preserving Data Distribution in Healthcare
631
