Fuzzing Matter(s): A White Paper for Fuzzing the Matter Protocol
Marcello Maugeri
a
Department of Maths and Computer Science, University of Catania, Catania, Italy
Keywords:
Fuzzing, IoT, Security Testing.
Abstract:
IoT and smart home devices have transformed daily life, consequently raising more and more concerns about
security vulnerabilities. Robust security testing methods are essential to fortify devices against potential
threats. While dynamic analysis techniques, such as fuzzing, help identify vulnerabilities, some challenges
arise due to diverse architectures, communication channels and protocols. Testing directly on devices over-
comes difficulties in firmware emulation, but lack of protocol standardisation still poses hurdles. The recently
released Matter protocol aims to unify smart home ecosystems, thus also simplifying security testing. In par-
ticular, Matter inherits the concept of Cluster from Zigbee in its Data Model. The Data Model clearly defines
attributes, commands, status codes and events that could be leveraged to design automated security testing
techniques such as fuzzing. This paper proposes the design of a fuzzing framework for Matter-enabled smart
home devices. The framework employs stateful fuzzing to cover the inherent state-fullness of IoT devices.
Such a framework would bestow benefits upon manufacturers, researchers, and end-users.
1 INTRODUCTION
The increasing growth of smart home devices has
led to problems with competing standards and pro-
tocols. The World Economic Forum estimates that
more than 130 million households owned at least a
smart speaker – the most common smart home de-
vice – in 2022 (World Economic Forum, 2022). As
smart home technology rapidly expands, a significant
challenge arises for consumers who own devices from
multiple vendors. Integrating new devices into their
existing smart home ecosystem becomes a tedious
task. Typically, each vendor requires users to down-
load their specific app or, in the case of voice assis-
tants such as Amazon Alexa, install the corresponding
skill to enable communication with the new device.
This process not only demands considerable time and
effort but also results in a fragmented user experience.
Moreover, an additional concern emerges regard-
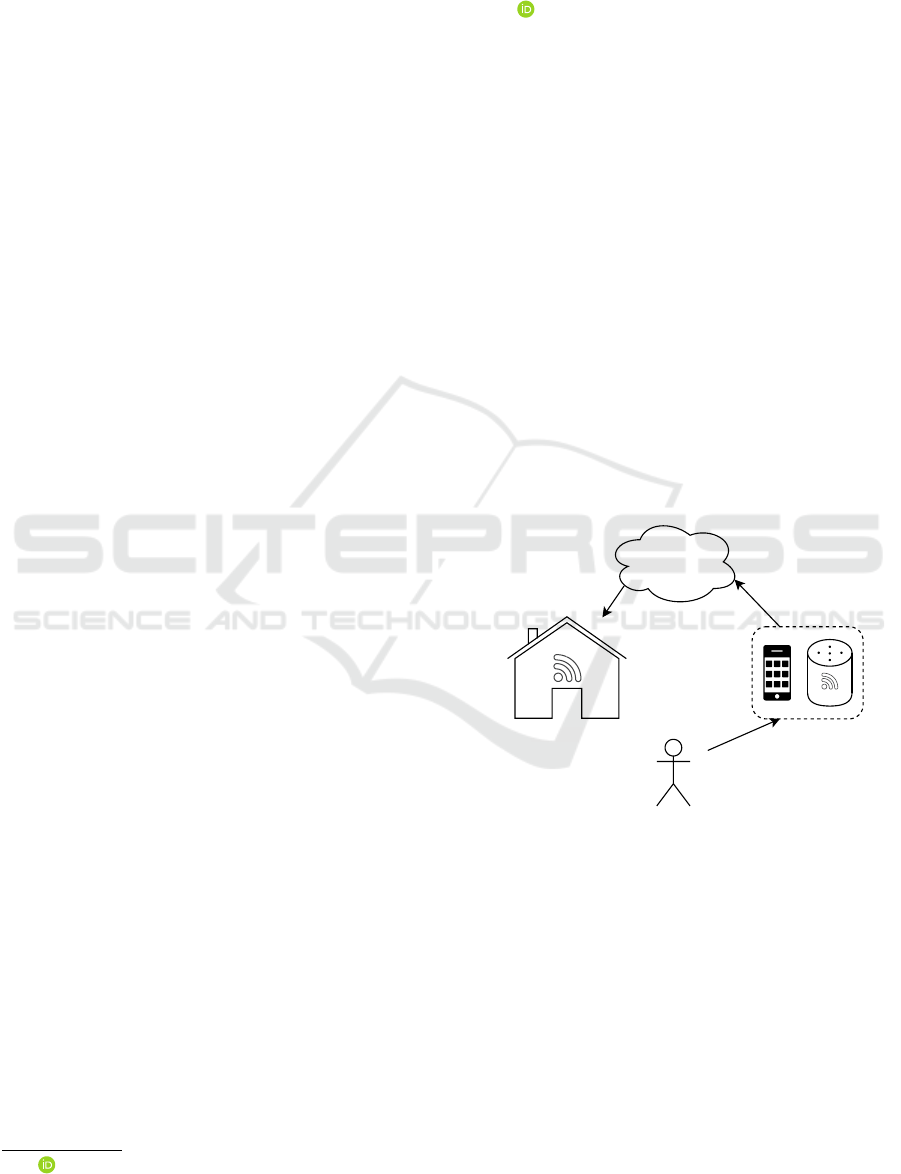
ing device usability during service disruptions. In
fact, as depicted in Figure 1, many smart home de-
vices rely on cloud services to fully function. As
a consequence, when the cloud service experiences
downtime or connectivity issues, the device’s func-
tionality may be severely affected or temporarily dis-
abled, causing inconvenience and limiting the de-
vice’s reliability.
a
https://orcid.org/0000-0002-6585-5494
Cloud Service
User
ControllersSmart Home
Figure 1: Typical usage of a smart home device.
As a solution for such issues, Matter establishes
a new smart home standard that allows devices to
be operated relying on the local network, improving
user convenience and eliminating the need for multi-
ple vendor-specific applications. To this extent, Mat-
ter (Connectivity Standards Alliance, 2023b) enables
devices to work offline without requiring continuous
access to the cloud, thus increasing the devices’ secu-
rity, especially for sensitive hardware like smart locks
and security cameras. In addition, this functionality
allows local testing, indirectly empowering end-users
and researchers.
Within the realm of security testing techniques,
446
Maugeri, M.
Fuzzing Matter(s): A White Paper for Fuzzing the Matter Protocol.
DOI: 10.5220/0012469200003648
Paper published under CC license (CC BY-NC-ND 4.0)
In Proceedings of the 10th International Conference on Information Systems Security and Privacy (ICISSP 2024), pages 446-451
ISBN: 978-989-758-683-5; ISSN: 2184-4356
Proceedings Copyright © 2024 by SCITEPRESS – Science and Technology Publications, Lda.

fuzzing has gained prominence for its automated and
effective approach to identifying vulnerabilities. The
concept is straightforward—repeatedly execute a tar-
get system with inputs designed to provoke unex-
pected behaviours.
Despite its efficacy, fuzzing encounters challenges
in the context of embedded systems (Eisele et al.,
2022), such as smart home devices, due to their
diverse architectures, communication channels, and
protocols. While testing directly on devices can over-
come issues related to firmware emulation, the lack of
protocol standardisation remains a hurdle.
However, since Matter is expected to become the
de-facto standard among smart home and IoT de-
vices, this paper relies on the necessity of develop-
ing a fuzzer specifically tailored to Matter protocol.
While adapting a pre-existing fuzzer to Matter might
appear straightforward, the intricacies inherent in the
protocol necessitate a specialised solution. Devel-
oping an effective framework involves utilising Mat-
ter’s specifics, including events and attributes for in-
ferring the state model, and leveraging the command
list knowledge for precise input generation. Hence,
this paper proposes a white paper of a possible solu-
tion.
The paper is structured as follows: Section 2 gives
a brief introduction to the state-of-the-art of embed-
ded fuzzing, followed by a brief description of the
Matter protocol. Section 3 outlines the research goals,
anticipates challenges, and provides an overview of
the proposed fuzzing framework’s design. Finally,
Section 4 concludes the paper.
2 BACKGROUND
2.1 Embedded Fuzzing
In the pursuit of robust firmware security testing,
several vulnerability-finding systems employ static
analysis (Costin et al., 2014). While static analysis
can uncover potential vulnerabilities, it often reports
false positives (Costin et al., 2016) since the target
firmware is not actually executed during the analysis.
To address this limitation and achieve more accurate
results, dynamic analysis is preferred.
Dynamic analysis methods, such as fuzzing, typ-
ically involve the emulation of the target firmware in
a controlled and efficient environment, allowing se-
curity testers and the fuzzer itself to observe the be-
haviour and interactions with various inputs. Rel-
evant emulation-based works include Firmfuzz (Sri-
vastava et al., 2019), FirmAE (Kim et al., 2020) and
Icicle (Chesser et al., 2023). Unfortunately, emulat-
ing firmware from different architectures and deal-
ing with obfuscated code still pose significant chal-
lenges (Wright et al., 2021), hindering the efficacy of
dynamic analysis. As a consequence, researchers and
security experts often resort to testing directly on ac-
tual devices to overcome the challenges of accurately
emulating firmware.
However, testing directly on devices effectively
introduces its own set of challenges due to the lack
of relevant feedback. GDBFuzz (Eisele et al., 2023)
addresses the issue effectively by monitoring the tar-
get device through the debug interface. However, it is
worth noting that not all devices have a debug inter-
face available on their shield, causing this solution to
be challenging to apply.
Then, it is preferred to use the network commu-
nication channel as an entry point. Another major
issue is the limited resources of IoT devices, which
may not be able to handle large-scale testing of nu-
merous inputs in a short amount of time. This con-
straint calls for smart and efficient testing methodolo-
gies – for example by leveraging machine learning al-
gorithms (Eceiza et al., 2021; Aichernig et al., 2021)
– to maximise the effectiveness of the testing process.
Another significant challenge is the diversity of
network communication channels used by IoT de-
vices. The devices may employ different protocols
and mechanisms for communication, leading to com-
plex communication pathways. For example, a user
might use a companion app on a smartphone to send
commands to the cloud through the use of Wi-Fi. The
cloud then relays the command to a smart hub on the
local network, and the smart hub communicates with
the actual device using a protocol such as Zigbee.
This intricate network of communication necessitates
careful consideration and testing of all communica-
tion paths to ensure comprehensive security coverage.
Additionally, the lack of standardisation in the ap-
plication protocols used to communicate with IoT de-
vices poses a significant hurdle. In some cases, de-
vices may use standard protocols such as HTTP, but
with custom payloads or unconventional implementa-
tions. Alternatively, MQTT may be used to leverage a
publish-subscribe pattern for communication. These
variations demand the development of tailored testing
tools and methodologies for each unique target under
test. As a consequence, most of the relevant works,
such as IoTFuzzer (Chen et al., 2018), DIANE (Re-
dini et al., 2021) leverage companion apps provided
by the device’s respective vendor to communicate di-
rectly with the device without inferring the underlying
protocol and cipher.
Nevertheless, these tools are tailored to the respec-
tive companion app, hence they are not easily reusable
Fuzzing Matter(s): A White Paper for Fuzzing the Matter Protocol
447

without requiring additional effort. In addition, most
apps are obfuscated, nullifying this method. As a con-
sequence, some tools such as Snipuzz (Feng et al.,
2021) and FIoTFuzzer (Xu et al., 2022) work di-
rectly by mutating previously acquired messages to
send to the target device. Both works employ guided
mutation based on feedback inferred from the re-
sponse provided by the target device. However, cer-
tain devices may not generate a detailed response
and instead prioritise providing a simplistic error
code. Also, the message acquisition phase is time-
consuming and could not cover all possible function-
alities.
To make a more comprehensive solution, Ma et
al. (Ma et al., 2023) recently developed HubFuzzer,
which leverages a device pretending to be a smart hub,
to receive allowed commands from the target device
directly. Unfortunately, HubFuzzer is not currently
open-sourced, and it is designed to work with devices
based on Zigbee and Z-Wave protocols only. In ad-
dition, Ma et al. discuss the possible re-using of this
approach with the Matter protocol. Still, this paper
foresees that it will require extensive additional work
to provide an effective solution, due to the Matter’s
specification complexity.
2.2 Matter Protocol
The Matter protocol defines a seven-layer stack as
depicted in Figure 2. At the topmost layer, the Ap-
plication Layer orchestrates the high-level business
logic, managing tasks such as turning on or off a smart
home device. Situated beneath the first layer, the Data
Model Layer serves as a fundamental component, elu-
cidating data and verb elements pivotal for the proto-
col’s delineation. Notably, this layer introduces the
concept of a Cluster: a specification that intricately
defines attributes, commands, behaviours, and depen-
dencies for a set of functionalities.
In particular, a Command is a data field set that
triggers a behaviour in the receiver. The receiver,
upon receiving a command, can respond with a suc-
cess or error status code. Alternatively, it may remain
silent (no response), or reply with a specific response
command if the initial command is not a request.
Note that the status code could be cluster-specific or a
global status code defined from the underlying Inter-
action Model.
Another integral element within a Cluster is an At-
tribute. Attributes encompass queryable or settable
states, configurations, or capabilities of the device.
For instance, a smart bulb may feature the On/Off
attribute to indicate its operational status. A more
intricate example is the AcceptedCommandList, de-
tailing the supported commands. Similar functional-
ities are achieved through AttributeList for attributes
or EventList for events.
Specifically, Events serve as records of past state
transitions. While attributes convey current states,
events function as a historical journal, equipped with
a monotonically increasing counter, timestamp, and
priority. This design enables the capture of state tran-
sitions and facilitates data modelling that extends be-
yond the capabilities of attributes.
Moving further down, the Interaction Model layer
sets the stage for communication between devices of
the same Fabric acting as a client or a server. A Fabric
is a set of nodes that interact by accessing data model
elements. For completeness, a Node is a unique ad-
dressable entity, usually a physical device, but can
also be a logical instance of it. In addition, a node
is composed of one or more endpoints adhering to a
specific device type, and the Cluster is an instance of
an endpoint.
Subsequently, the Action Framing layer is respon-
sible for encoding the message into a prescribed bi-
nary format for network transmission. Consequently,
security measures are accomplished in the Security
layer. In this layer the action frame is processed, un-
dergoing encryption and the addition of a message
authentication code using the AES-CCM mode as de-
fined in NIST 800-38C (Dworkin, 2007).
Finally, the Message Layer takes charge of con-
structing the payload format post-encryption. This
layer adds required and optional header fields, speci-
fying message properties and logical routing informa-
tion. The finalised payload is then ready for transmis-
sion via the underlying transport protocol, either TCP
or the Matter’s Message Reliability Protocol (MRP)
through UDP, for effective IP management of the data.
As the data reaches the peer device, it ascends the pro-
tocol stack, with each layer reversing the operations
performed by the sender.
3 FUZZING MATTER(S)
3.1 Research Goals
Matter offers a comprehensive definition of smart
home device functionalities through its Cluster speci-
fication. Additionally, the Matter Application Cluster
Library (MACL), curated by the Connectivity Stan-
dards Alliance, serves as a dynamic repository for
cluster functionalities, regularly updated with new
features. Essentially, the MACL comprises multiple
sets of clusters for general use. The primary research
ICISSP 2024 - 10th International Conference on Information Systems Security and Privacy
448
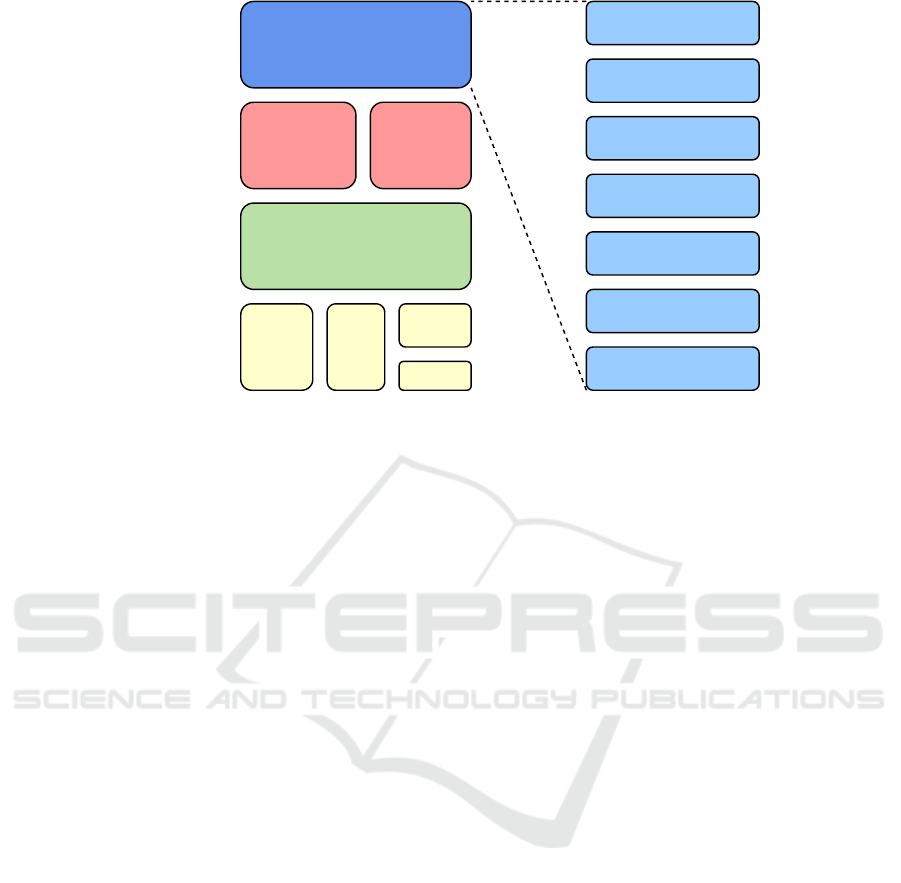
Application Layer
Data Model
Interaction Model
Action Framing
Security
Message Framing +
Routing
IP Framing +
Transport Management
Matter
TCP UDP
IPV6
Ethernet Wi-Fi
Thread
802.15.4
Transport
Network
Link
Application
Figure 2: Stack of the Matter Protocol.
goal is to develop a fuzzer capable of effectively cov-
ering all functionalities outlined in the MACL.
Moreover, smart home devices inherently possess
statefulness. In Matter, this state can be extracted
from queryable attributes and events within a Clus-
ter, laying the foundation for the design of a state-
ful fuzzer (Daniele et al., 2023). This dual-pronged
research approach aims to enhance security testing
by addressing the unique characteristics of Matter’s
Cluster functionalities and the inherent statefulness of
smart home devices.
3.2 Expected Challenges
The project expects the following challenges:
1. Benchmark – Acquiring a relevant set of real
case studies with multiple natures to build a
benchmark for the design and evaluation of the
fuzzer.
2. Information Gathering from Static Analysis of
the Firmware – Although static analysis cannot
be always applicable, existing techniques could
be tailored to obtain Matter-relevant information
from the firmware.
3. Information Gathering from Firmware Emu-
lation – Although firmware emulation is not al-
ways possible, an alternative approach could be
tailored to perform fuzzing in an emulated envi-
ronment, improving test speed and validating the
obtained results with the real device.
4. Handling Multiple Link Layers – Matter pri-
marily operates with Wi-Fi and Thread protocols,
but it also supports other protocols such as Zigbee.
Therefore, the fuzzer must be compatible with all
link layer protocols specified in Matter.
5. Stateful Fuzzing – IoT devices often have stateful
behaviour, where their actions and responses de-
pend on previous inputs. Fuzzing stateful proto-
cols can be more complicated than stateless ones.
The proposed solution will likely need to design
stateful fuzzing strategies to adequately cover all
possible device states and interactions related to
the Matter protocol.
6. Handling Vendor-Specific Implementations –
Different manufacturers may implement the Mat-
ter protocol differently, introducing variations in
the behaviour of devices. For example, a manu-
facturer could define its own Cluster specification.
The fuzzer should account for vendor-specific im-
plementations and adapt the fuzzing techniques
accordingly.
7. Validating True Positives – Fuzzing often pro-
duces numerous inputs and potential vulnerabili-
ties. The proposal requires effective methods to
validate and reproduce the obtained findings ac-
curately.
3.3 Proposed Framework
The proposed fuzzing framework consists of four
components, illustrated in Figure 3.
Initially, the Input Generator creates input fol-
lowing the Cluster specification, utilising information
such as accepted commands, queryable/settable at-
tributes, and accessible events. It is important to note
that, at the current design stage, specific input genera-
tion algorithms have not been chosen as any grammar-
Fuzzing Matter(s): A White Paper for Fuzzing the Matter Protocol
449
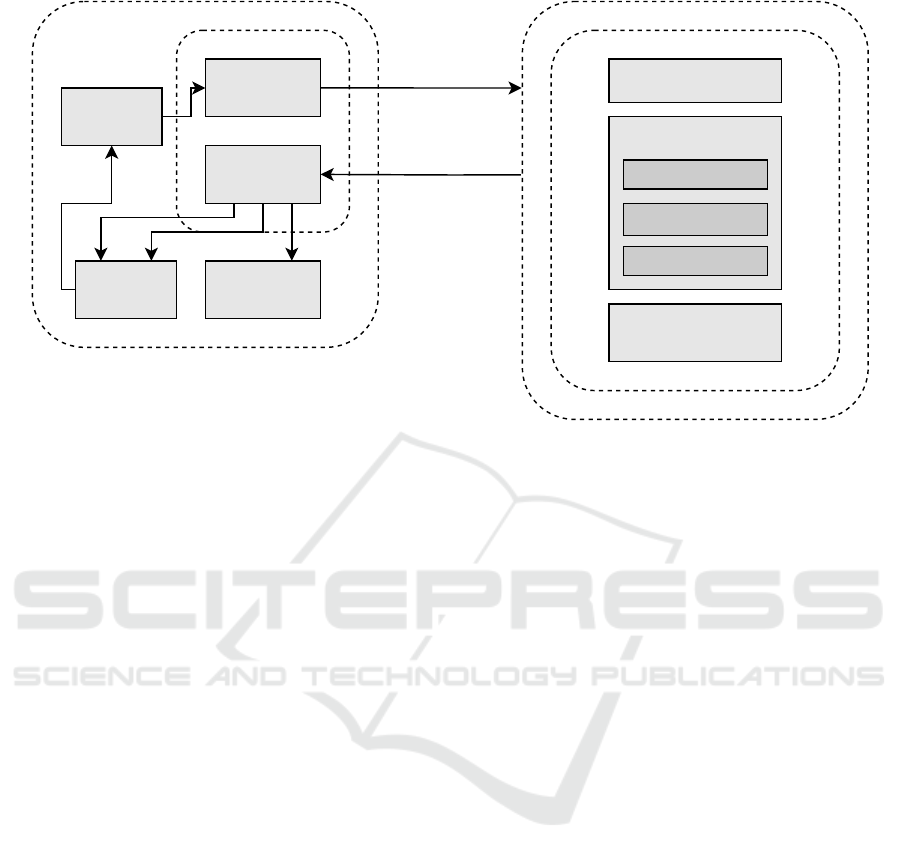
Node / Device
Cluster
Fuzzer
Connection Handler
Input
Input
Generator
State
State
Monitor
Status Code
Attributes
Events
Response
Handler
Bug Oracle
Request
Command
Sender
Response
Attributes
Commands
Events
AttributeList
EventList
AcceptedCommandList
Figure 3: Proposed Framework.
based approach adapted to the problem should fit.
However, the modular design of the framework facil-
itates easy replacement with minimal effort.
Once the input is generated, the Connection Han-
dler engages with the target node (or device), man-
aging the transmission of input generated by the In-
put Generator and receiving any corresponding re-
sponses. Given Matter’s use of Thread, Wi-Fi, and
Ethernet as networking technologies, the fuzzer must
support communication with any Matter-compliant
device, accommodating various link layer protocols.
Responses can carry diverse information. If the
request involves a command, the response should in-
clude a success or error status code, signalling poten-
tial bugs to the Bug Oracle. A bug might manifest as
an unexpected success code inappropriately granted
or an unforeseen error code in a properly formed com-
mand.
Additionally, a response may include the queried
attribute or event, updating the State Monitor on any
state transitions. The fuzzer should account for the
stateful nature of smart home devices, considering
variables such as device states (e.g., on or off). Un-
derstanding the current state proves valuable during
input generation, as the same input may trigger dif-
ferent behaviours based on the device’s state.
4 CONCLUSIONS
In conclusion, this paper has explored the neces-
sity and design of a fuzzing framework tailored for
Matter-enabled smart home devices. By leverag-
ing the inherent structure provided by Matter’s Clus-
ter specification (Connectivity Standards Alliance,
2023a) and the MACL, the proposed framework aims
to comprehensively cover all aspects of device func-
tionality. The modular nature of the framework allows
for flexibility, enabling potential advancement and ex-
tensions.
Furthermore, considering the stateful nature of
smart home devices, the framework incorporates a
State Monitor to capture state transitions during test-
ing. Also, the Connection Handler component facil-
itates interaction with Matter-compliant devices, en-
suring compatibility across different link layers.
The fuzzer aims to be open-sourced and promote
collaboration and knowledge sharing within the smart
home and fuzzing community, providing valuable
testing methods to companies, researchers, and end-
users alike. As such, the advances of this project will
be published on the web page https://fuzzingmatter.gi
thub.io/ which anyone is welcome to join.
REFERENCES
Aichernig, B. K., Mu
ˇ
skardin, E., and Pferscher, A. (2021).
Learning-based fuzzing of iot message brokers. In
2021 14th IEEE Conference on Software Testing, Ver-
ification and Validation (ICST), pages 47–58.
Chen, J., Diao, W., Zhao, Q., Zuo, C., Lin, Z., Wang,
X., Lau, W., Sun, M., Yang, R., and Zhang, K.
(2018). Iotfuzzer: Discovering memory corruptions
ICISSP 2024 - 10th International Conference on Information Systems Security and Privacy
450

in iot through app-based fuzzing. In Network and Dis-
tributed System Security Symposium.
Chesser, M., Nepal, S., and Ranasinghe, D. C. (2023). Ici-
cle: A re-designed emulator for grey-box firmware
fuzzing. In Proceedings of the 32nd ACM SIG-
SOFT International Symposium on Software Testing
and Analysis, ISSTA 2023, page 76–88, New York,
NY, USA. Association for Computing Machinery.
Connectivity Standards Alliance (2023a). Matter Applica-
tion Cluster Specification 1.2.
Connectivity Standards Alliance (2023b). Matter Core
Specification 1.2.
Costin, A., Zaddach, J., Francillon, A., and Balzarotti, D.
(2014). A Large-Scale analysis of the security of em-
bedded firmwares. In 23rd USENIX Security Sym-
posium (USENIX Security 14), pages 95–110, San
Diego, CA. USENIX Association.
Costin, A., Zarras, A., and Francillon, A. (2016). Auto-
mated dynamic firmware analysis at scale: A case
study on embedded web interfaces. In Proceedings
of the 11th ACM on Asia Conference on Computer
and Communications Security, ASIA CCS ’16, page
437–448, New York, NY, USA. Association for Com-
puting Machinery.
Daniele, C., Andarzian, S. B., and Poll, E. (2023). Fuzzers
for stateful systems: Survey and research directions.
arXiv preprint arXiv:2301.02490.
Dworkin, M. (2007). Recommendation for block cipher
modes of operation: The ccm mode for authentication
and confidentiality. Technical report, National Insti-
tute of Standards and Technology.
Eceiza, M., Flores, J. L., and Iturbe, M. (2021). Fuzzing
the internet of things: A review on the techniques and
challenges for efficient vulnerability discovery in em-
bedded systems. IEEE Internet of Things Journal,
8(13):10390–10411.
Eisele, M., Ebert, D., Huth, C., and Zeller, A. (2023).
Fuzzing embedded systems using debug interfaces. In
Proceedings of the 32nd ACM SIGSOFT International
Symposium on Software Testing and Analysis, ISSTA
2023, page 1031–1042, New York, NY, USA. Associ-
ation for Computing Machinery.
Eisele, M., Maugeri, M., Shriwas, R., Huth, C., and Bella,
G. (2022). Embedded fuzzing: a review of challenges,
tools, and solutions. Cybersecurity, 5(1):18.
Feng, X., Sun, R., Zhu, X., Xue, M., Wen, S., Liu, D.,
Nepal, S., and Xiang, Y. (2021). Snipuzz: Black-box
fuzzing of iot firmware via message snippet inference.
In Proceedings of the 2021 ACM SIGSAC Conference
on Computer and Communications Security, CCS ’21,
page 337–350, New York, NY, USA. Association for
Computing Machinery.
Kim, M., Kim, D., Kim, E., Kim, S., Jang, Y., and Kim,
Y. (2020). Firmae: Towards large-scale emulation of
iot firmware for dynamic analysis. In Annual Com-
puter Security Applications Conference, ACSAC ’20,
page 733–745, New York, NY, USA. Association for
Computing Machinery.
Ma, X., Zeng, Q., Chi, H., and Luo, L. (2023). No more
companion apps hacking but one dongle: Hub-based
blackbox fuzzing of iot firmware. In Proceedings
of the 21st Annual International Conference on Mo-
bile Systems, Applications and Services, MobiSys ’23,
page 205–218, New York, NY, USA. Association for
Computing Machinery.
Redini, N., Continella, A., Das, D., De Pasquale, G., Spahn,
N., Machiry, A., Bianchi, A., Kruegel, C., and Vigna,
G. (2021). Diane: Identifying fuzzing triggers in apps
to generate under-constrained inputs for iot devices. In
2021 IEEE Symposium on Security and Privacy (SP),
pages 484–500.
Srivastava, P., Peng, H., Li, J., Okhravi, H., Shrobe, H., and
Payer, M. (2019). Firmfuzz: Automated iot firmware
introspection and analysis. In Proceedings of the 2nd
International ACM Workshop on Security and Privacy
for the Internet-of-Things, IoT S&P’19, page 15–21,
New York, NY, USA. Association for Computing Ma-
chinery.
World Economic Forum (2022). The market for smart home
devices is expected to boom over the next 5 years.
Wright, C., Moeglein, W. A., Bagchi, S., Kulkarni, M., and
Clements, A. A. (2021). Challenges in firmware re-
hosting, emulation, and analysis. ACM Comput. Surv.,
54(1).
Xu, Z., Huang, W., Fan, W., and Cheng, Y. (2022). Fiot-
fuzzer: Response-based black-box fuzzing for iot de-
vices. In 2022 IEEE/ACIS 22nd International Con-
ference on Computer and Information Science (ICIS),
pages 239–244.
Fuzzing Matter(s): A White Paper for Fuzzing the Matter Protocol
451
