
Implementation and Analysis of Covert Channel Using iBeacon
Ye-Sol Oh
1 a
, Yeon-Ji Lee
1 b
, Jiwon Jang
1 c
, Hyunwoo Choi
2 d
and Il-Gu Lee
3 e
1
Department of Future Convergence Technology Engineering, Sungshin Women’s University, Seoul, 02844, Korea
2
Korea Advanced Institute of Science and Technology, Daejeon, Korea
3
Department of Convergence Security Engineering, Sungshin Women’s University, Seoul, 02844, Korea
Keywords:
Covert Channel, BLE, iBeacon, iBeacon Payload, Advertising Interval.
Abstract:
Covert channels are typically employed to transmit information and bypass security policies and controls si-
multaneously to maintain undetected communication. Various techniques have been proposed for establishing
covert channels, including those at the network level, and for using different components. This study inves-
tigated the security implications of Apple’s iBeacon broadcast messages by focusing on the establishment
of covert channels. We introduce two Bluetooth Low Energy (BLE) covert channels: one using broadcast
payloads and the other employing broadcasting intervals. These channels can be used in a complementary
manner, balancing covertness and bandwidth. In our evaluation, the payload-based covert channel achieved a
maximum throughput of 911,600 Bytes per second (Bps) with a Packet Delivery Rate (PDR) exceeding 75%,
demonstrating its capability to transmit substantial data via iBeacon covertly. This study focuses on enhancing
the security of BLE Beacon deployment.
1 INTRODUCTION
Covert channels are concealed or unauthorized
communication methods within computer systems
and networks. These channels are typically used
to transmit information or data in a manner that
circumvents or violates security policies and con-
trols, ensuring that the communication content re-
mains undetected. Over the past few decades, nu-
merous techniques have been proposed for estab-
lishing covert channels at the network level (Tian
et al., 2020; Saenger et al., 2020; Schmidbauer et al.,
2022; Li et al., 2020). Covert channels can be es-
tablished using various components such as Blue-
tooth (Claeys et al., 2019), voltage (Gnad et al.,
2021), sound (Coyac-Torres et al., 2021), and light
(Maiti and Jadliwala, 2019). Among these, par-
ticular attention to Bluetooth-based covert channels
is essential, particularly with the increasing num-
ber of Things (IoT) devices. According to ABI Re-
search, a global technology market advisory firm,
a
https://orcid.org/0009-0004-9934-4715
b
https://orcid.org/0000-0002-0482-2381
c
https://orcid.org/0000-0002-2418-5850
d
https://orcid.org/0009-0009-9528-4002
e
https://orcid.org/0000-0002-5777-4029
over 815 million Bluetooth-enabled products (ABIre-
search, 2020). Moreover, internet companies such as
Amazon, Alibaba, Google, Baidu, and Xiaomi not
only provide Bluetooth-based services such as speech
recognition, but Bluetooth’s presence is also grow-
ing in various fields, including smart lighting, smart
appliances, door locks, and sensors (ABIresearch,
2020).
BLE technology, designed for short-range com-
munication between devices, has experienced explo-
sive growth as a technology for communication and
location-based services, particularly in the IoT con-
text. BLE has become ubiquitous worldwide and is
used in everyday life and various industrial environ-
ments owing to its high availability, low cost, low
power consumption, and ease of deployment. They
can operate on coin-cell batteries or even without bat-
teries (Mackey et al., 2020). Currently, BLE is in-
tegrated into most smartphones by default and sup-
ported by major operating systems such as iOS, An-
droid, Linux, and Windows (Hern
´
andez-Rojas et al.,
2017).
A BLE Beacon message implemented through the
Apple iBeacon (iBeacon Homepage, 2015) or Google
Eddystone (Eddystone, 2018) protocols is a small
packet of data transmitted by a BLE device. These
messages are typically designed to be broadcast at
Oh, Y., Lee, Y., Jang, J., Choi, H. and Lee, I.
Implementation and Analysis of Covert Channel Using iBeacon.
DOI: 10.5220/0012457800003648
Paper published under CC license (CC BY-NC-ND 4.0)
In Proceedings of the 10th International Conference on Information Systems Security and Privacy (ICISSP 2024), pages 861-868
ISBN: 978-989-758-683-5; ISSN: 2184-4356
Proceedings Copyright © 2024 by SCITEPRESS – Science and Technology Publications, Lda.
861
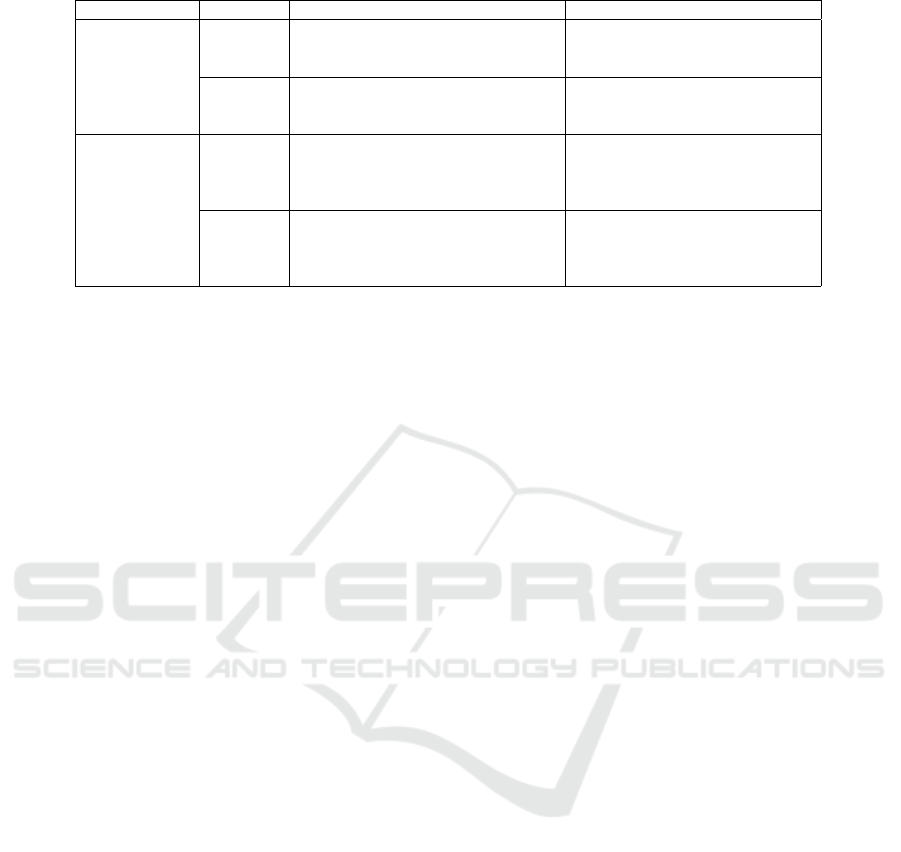
Table 1: Previous studies on covert channels.
Category Ref. Contribution Limitation
Covert Storage
Channel
Priest et
al. (2015)
- Analyze fields within the iBeacon
packet that can be used for a covert
channel
- Do not analyze the throughput
adequately across various
advertising intervals
Zhang et
al. (2020)
- Even in a highly monitored
environment, detecting the
tampering of fields is challenging
- Low transmission bandwidth
- Limited modifiable bits
Covert Timing
Channel
Seong et
al. (2022)
- Microsecond-level precision
time interval Adjustment
- Enhancing security through
encryption
- Hardware Modification Required
- Limited payload length limits
significant performance
improvements in transmission
Zhang et
al. (2018)
- Improved robustness compared
to IPD-based approaches
- Encoding messages in gray code for
channel noise mitigation
- Inefficient for large amount of
data transfer
- Prolonged messages may impact
voice quality
regular intervals and serve a specific purpose: to con-
vey information to nearby devices or applications.
The BLE Beacons are commonly used in proxim-
ity marketing, location-based services, and context-
aware applications. However, most existing beacon
systems omit protection from the transmitted BLE
beacon messages and other crucial protocol-specific
parameters, which can lead to security vulnerabilities.
This allows unauthorized devices to exploit beacons,
such as eavesdropping, spoofing, and data intercep-
tion (Kolias et al., 2017). Furthermore, the inher-
ent nature of beacons, in which devices continuously
broadcast their unique identifiers to signal their pres-
ence at specific locations, has the potential to estab-
lish covert communication through advertising with-
out establishing connections between endpoint de-
vices (Priest and Johnson, 2015; Na et al., 2021).
Therefore, ensuring the security of beacon deploy-
ment is essential for protecting user privacy, prevent-
ing unauthorized access, and maintaining the integrity
of the transmitted data.
In this study, we investigate the security implica-
tions of beacon broadcasts with a focus on Apple’s
iBeacon. Based on our analysis, we designed two
BLE covert channels using storage and timing meth-
ods: one based on broadcast payloads (similar to a
previous study (Priest and Johnson, 2015) and the
other on broadcasting intervals. The two proposed
covert channels can be used complementarily. For ex-
ample, a payload-based covert channel can be used
to transmit data when there is no monitoring or log-
ging and a need to maximize the channel capacity.
By contrast, the interval-based covert channel offers
higher concealment than the payload-based channel
but with a lower channel capacity. Among them, in
this paper, we implement and evaluate the payload-
based covert channel and evaluated its performance
in terms of Packet Delivery Ratio (PDR) and through-
put. Our experimental results reveal that the proposed
channel has a maximum throughput of 911,600 Bytes
per second (Bps), making it an efficient covert chan-
nel.
Specifically, this study makes the following con-
tributions:
- We investigated the security implications of
iBeacon’s broadcast messages with a focus on es-
tablishing covert channels.
- We designed two BLE covert channels using
storage and timing methods: broadcast payload-
and interval-based covert channels.
- We implemented and evaluated the proposed
payload-based covert channels in terms of PDR
and throughput. Our evaluation results show that
the payload-based covert channel had a maximum
throughput of 911,600 bps.
The structure of this paper is organized as follows. In
Section 2, we analyze prior research on covert chan-
nels. In Section 3, we introduce iBeacon’s back-
ground. In Section 4, we analyze the Apple iBea-
con and design two covert channels using storage and
timing channels. In Section 5, we describe the im-
plementation and evaluation of the proposed payload-
based covert channel from the perspectives of PDR
and throughput. In Section 6, we discuss the covert
timing channel case using iBeacon. Finally, Section
7 concludes the paper and proposes future research
directions.
2 RELATED WORK
In this Section, we review previous studies on covert
channels and analyze their contributions and limita-
tions. A Covert Storage Channel (CSC) uses reserved
or empty locations in legitimate packet fields (Tian
et al., 2020; Seong et al., 2022), exploiting the imper-
fections in modern network protocol designs (Zhang
et al., 2020). Covert Timing Channels (CTC) use dif-
ferences in transmission time intervals, such as inter-
packet delay (IPD) or packet retransmissions (Zhang
ICISSP 2024 - 10th International Conference on Information Systems Security and Privacy
862
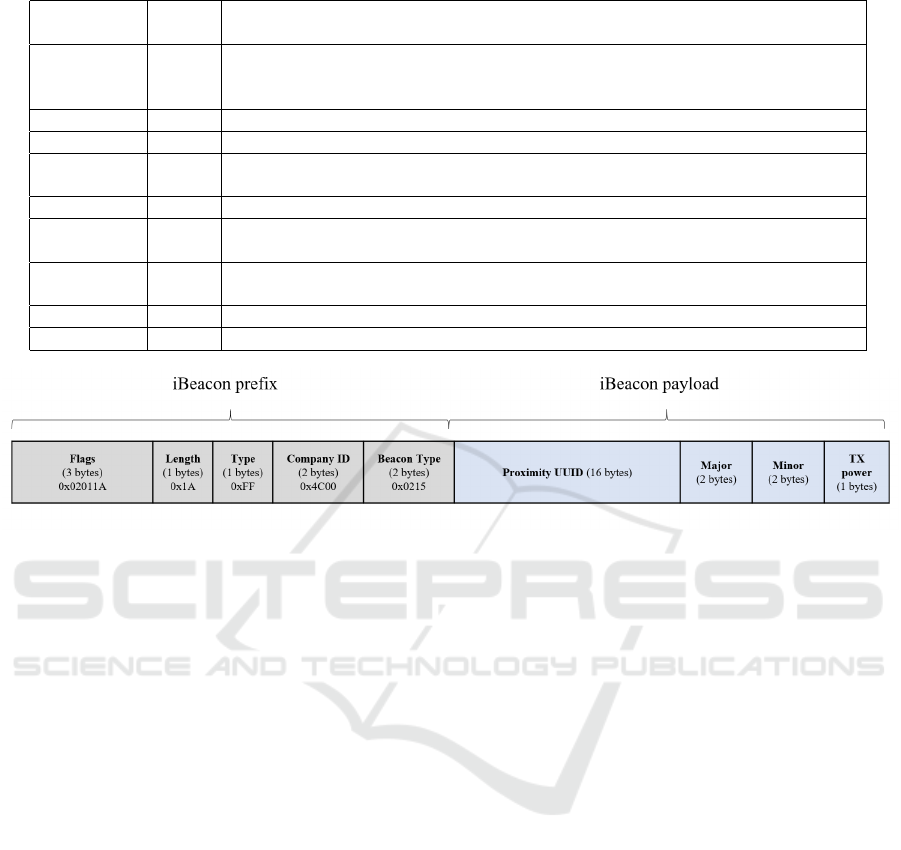
Table 2: iBeacon packet field description.
Field
Sizes
(bytes)
Description
Flags 3
Each of Length, Type, and Value is composed of 1 byte. The ’02’ serves as a length
indicator, indicating that an additional 2 bytes are present in the Flags field. The ’01’
in the Value field signifies the inclusion of flags, and ’1A’ represents the flag value.
Length 1 Displays the length of frame payload that comes after that field
Type 1 Indicates that the content of the frame is manufacturer-specific data
Company ID 2
Beginning of the manufacturer-specific advertising payload, ‘4C’ indicates the Apple
company ID number
Beacon Type 2 ‘02’ is the protocol identifier, and ‘15’ indicates the length of the subsequent payload
UUID 16
Application developers should define a UUID specific to their app and deployment use
case
Major 2
Further specifies a specific iBeacon and use case. For example, this could define a
sub-region within a larger region defined by the UUID.
Minor 2 Allows further subdivision of region or use case specified by the application developer
TX power 1 Value measured by Bluetooth device manufacturer from a 1 m distance
Figure 1: iBeacon packet structure.
et al., 2018; Tian et al., 2020; Seong et al., 2022). Ta-
ble 1 categorizes and analyzes the previous research
on CSC and CTC. Priest et al. (2015) asserted the pos-
sibility of applying a covert channel to Apple’s iBea-
con. The iBeacon prefix plays a role in identifying the
identity of the iBeacon and modifying it would pre-
vent it from being recognized as an iBeacon. There-
fore, modifiable fields were analyzed without modify-
ing the prefix to enable legitimate iBeacon receivers
to interpret a packet as an iBeacon. They confirmed
that by modifying the second byte of the Company ID,
Universally Unique Identifier (UUID), Major, Minor,
and TX power fields, a valid iBeacon could be cre-
ated. They further investigated the number of adver-
tisements a receiver could receive during the default
advertising interval using a MacBook Pro and iPad
Air 7. Priest et al. (2015) analyzed iBeacon fields
to identify the fields in which a valid covert channel
can be established. However, a limitation exists in
that the performance of the covert timing channel us-
ing iBeacon has not been fully evaluated owing to the
failure to analyze various advertising intervals. Zhang
et al. (2020) proposed a covert storage channel by
modifying the RTCP payloads in the Voice over Long
Time Evolution (VoLTE) channel. They set up an en-
vironment by installing a TCP dump on two different
mobile devices running on an Android operating sys-
tem. These devices have varying security levels, and
this study differentiates between a strictly monitored
environment and an unmonitored environment to es-
tablish a covert channel. In a strictly monitored envi-
ronment, they created a covert channel by modifying
only the lowest bit of the jitter field in the RTCP pack-
ets using the time difference between the data pack-
ets arriving at the endpoint and application processing
those packets. Conversely, they increased the trans-
mission bandwidth in a less strictly monitored envi-
ronment using the EHSNR and BLP fields to com-
pensate for the slow transmission speed. Zhang et al.
(2020) validated the difficulty of detecting tampered
fields in a constructed covert storage channel, even in
a strictly monitored environment, by using the K-S
test. However, they encountered limitations owing to
their low transmission bandwidth and limited number
of modifiable field bits.
Seong et al. (2022) has developed a covert wire-
less unidirectional communication mechanism using
the Beacon Interval (BI) of public Access Points
(APs) in an IEEE 802.11 environment. They pro-
posed a frame structure to ensure the confidential-
ity and integrity of the transmitted information and
introduced the Ping Pong Covert Timing Channel
(PPCTC) data encoding method to reduce detectabil-
ity. Although the proposed mechanism is unidirec-
tional, it ensures stable communication by providing
error recovery capabilities for consecutive 2-bit er-
rors. To implement an AP that simultaneously pro-
vides legitimate services to authorized users while
Implementation and Analysis of Covert Channel Using iBeacon
863

transmitting signals to covert receivers, Seong et al.
(2022) used OpenWiFi, following 802.11 a/b/n stan-
dards and Xilinx Zynq. They also controlled the time
differences within tens of microseconds by switch-
ing from a jiffies-based Linux kernel timer to high-
resolution kernel timer. The study by Seong et al.
(2022) significantly increased confidentiality by pre-
cisely adjusting the time intervals and implement-
ing more covert messages using SHA-1 and XOR
encryption. However, there are limitations, such as
the need for hardware modifications and restricted
payload length, which significantly hamper transmis-
sion performance. Zhang et al. (2018) proposed a
covert channel that adjusts the silence periods in the
VoLTE environment. Because the IPD of VoLTE traf-
fic is fixed and cannot be applied at the application
level, covert messages are encoded into unique sym-
bols by adjusting the silent periods and transmitting
them. Before transmission, the sender and receiver
share custom parameters, and the receiver decodes
the covert messages upon reception. They used gray
coding to encode messages to mitigate channel noise
and tested undetectability using KS and KLD tests.
Zhang et al. (2018) increased robustness compared
with IPD-based methods demonstrated undetectabil-
ity in the VoLTE environment. However, transmitting
large amounts of data is inefficient, and longer silent
periods can affect voice quality.
Previous research had limitations related to pay-
load length, making it challenging to improve the
transmission performance or transmit large amounts
of data efficiently. In addition, although numer-
ous studies have been conducted on building covert
channels in 802.11 networks or VoLTE, research on
creating covert channels in Bluetooth environments,
particularly using beacons, has not been as active.
This study aims to implement and evaluate a high-
throughput covert channel using beacons.
3 BACKGROUND
3.1 iBeacon
Bluetooth beacons are low-cost, low-power, location-
based technologies that use the BLE protocol. The
two standard communication protocols for beacons
are iBeacon, developed by Apple, and Eddystone, de-
veloped by Google (Mackey et al., 2020; Griffiths
et al., 2019). Beacons can broadcast Bluetooth sig-
nals with several bytes of information and a Univer-
sally Unique Identifier (UUID) to the surrounding en-
vironment (Griffiths et al., 2019). BLE operates in
the unlicensed 2.4 GHz ISM band and uses frequency
hopping to minimize interference with other RF de-
vices operating in the same band, making it suitable
for building covert channels (Hern
´
andez-Rojas et al.,
2017). iBeacon technology is industrially available
and has real-world applications, making it a valuable
research target (Kolias et al., 2017). The iBeacon pro-
tocol, introduced in 2013, uses a one-way discovery
mechanism to transmit small data packets at prede-
fined intervals. While Bluetooth allows for various
advertising intervals, iBeacon fixes the advertising in-
terval at 100 ms (Gast, 2014). The maximum range
of iBeacon transmission can vary depending on loca-
tion and placement, with long-range beacons capable
of reaching up to 450 m (Griffiths et al., 2019). Fig.
1 and Table 2 illustrate the structure of the iBeacon
advertising packet (Priest and Johnson, 2015; Gast,
2014; Dalkılıc¸ et al., 2017; Developer, 2014). The
fields before the UUID constitute the iBeacon prefix,
and modifying this part prevents the packet from be-
ing correctly identified by iBeacon receivers. How-
ever, modifying the UUID and major and minor parts
does not affect the transmission validity, enabling the
use of a 20-byte data payload. The distance to the bea-
con device can be estimated using the TX power and
current Received Signal Strength Indicator (RSSI) of
the received signal (Dalkılıc¸ et al., 2017). Apple’s
API provides developers with four states: immediate,
near, far, and unknown (Priest and Johnson, 2015; De-
veloper, 2014). Therefore, if the TX power byte is
modified and the distance cannot be estimated accu-
rately, the API returns an ’unknown’ descriptor, creat-
ing a valid covert channel without disrupting the iBea-
con protocol unknown (Priest and Johnson, 2015).
4 iBeacon COVERT CHANNEL
4.1 Design Overview
Payload-based Covert Channel. The payload-based
iBeacon covert storage channel model is shown in
Fig. 2. The sender and receiver agree that the ad-
vertising packet received at a particular interval in ad-
vance contains covert message. The sender adver-
tises the iBeacon packet by forging the payload ac-
cording to the agreed rules. For example, they agree
that a packet received at 500 ms contains covert mes-
sage. The sender advertises the packet by including
the covert message in the UUID, Major, and Minor
fields, the sequence number in the TX power, and set-
ting the advertising interval to 500 ms. The sender
and receiver can exchange messages without estab-
lishing a connection, and message reception is possi-
ble without hardware modifications.
ICISSP 2024 - 10th International Conference on Information Systems Security and Privacy
864
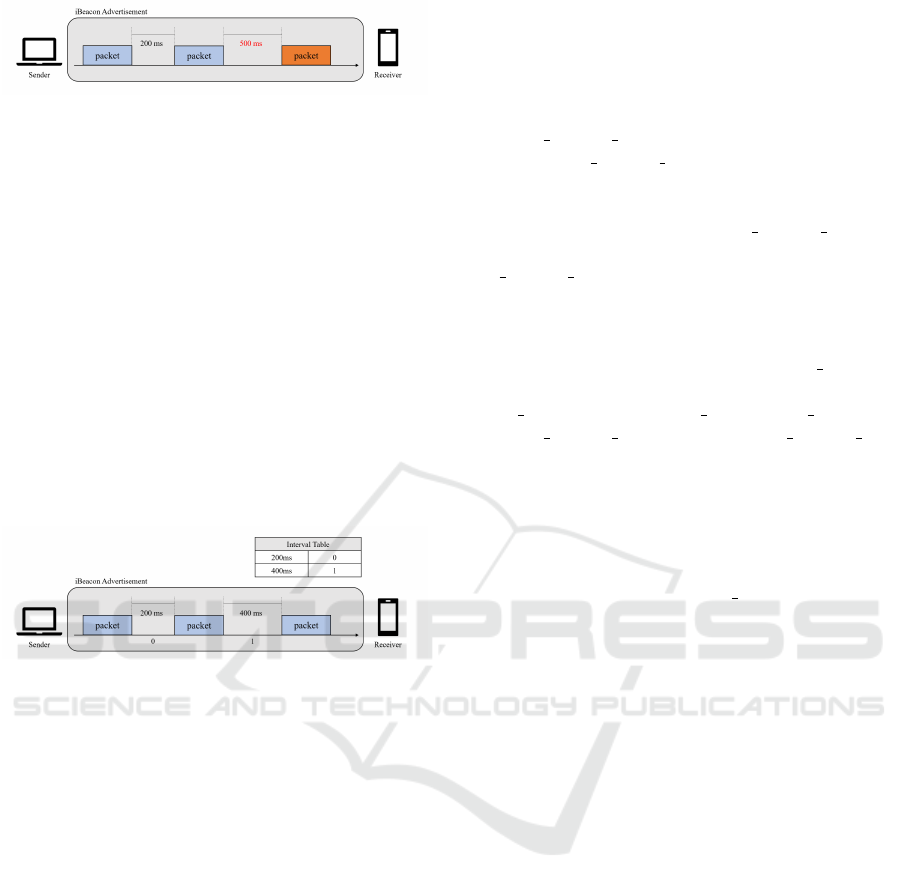
Figure 2: Payload-based covert channel (CSC-style) using
iBeacon.
Interval-Based Covert Channel. The interval-based
iBeacon covert timing channel model is shown in Fig.
3. If the sender and receiver agree on an interval rule
beforehand, the sender encodes the message and ad-
vertises the iBeacon packets according to the agreed-
upon rule. For example, if we consider Morse code ·
as 0 and - as 1, ’A’ can be converted to ‘0 1.’ Let us
assume that they agree on the rule that if the packet
arrives between 200 and 300 ms, it is interpreted as
0, and if it arrives between 400 and 500 ms, it is in-
terpreted as 1. In this scenario, the sender can trans-
mit ’A’ by advertising a packet once between 200 and
300 ms and once between 400 and 500 ms. Like
the payload-based covert channel, there is no need
for device-to-device connection or hardware modifi-
cation.
Figure 3: Interval-based covert channel (CTC-style) using
iBeacon.
4.2 Covert Channel implementation
Payload-Based Covert Channel. Based on Section
4.1, the payload-based iBeacon covert channel forges
the iBeacon’s UUID, Major, Minor, and TX power
fields. Fig. 4 shows an example of a payload where
UUID, Major, and Minor are arbitrarily set, and TX
power is used as the sequence number. Fig. 5 shows
the commands used to configure the Bluetooth inter-
face with the advertisement payload from Fig. 4. The
OGF code for the LE Controller Commands is defined
as 0x08. ‘0×0008’ corresponds to the LE Set Ad-
vertising Data Command, which allows for the con-
figuration of data used in advertising packets with
data fields (Bluetooth, 2016). The value ’1E’ repre-
sents the length of the entire payload, excluding itself
(Priest and Johnson, 2015; Bluetooth Core Specifica-
tion 5.0., 2016).
Interval-Based Covert Channel. The interval-based
covert channel encodes data within the advertising in-
tervals by modifying the advertising interval of the
iBeacon packet. The range of BLE advertising inter-
vals should be between 20 ms and 10.24 s and a mul-
tiple of 0.625 ms (Bluetooth, 2016; Shan and Roh,
2018). Fig. 6 shows the commands used to mod-
ify the advertising interval. ‘0×0006’ corresponds to
the LE Set Advertising Parameters Command, allow-
ing the configuration of advertising parameters. Ad-
vertising Interval Min should be less than or equal
to Advertising Interval Max, and it is advisable not
to set them to the same value when determining the
optimal advertising interval. The 2 bytes at posi-
tions ‘A0 00’ represent Advertising Interval Min, and
the 2 bytes at positions ‘40 01’ represent Advertis-
ing Interval Max. On multiplying 0×00A0 by 0.625
ms, 100 ms is obtained, and on multiplying 0×0140
by 0.625 ms, 200 ms is obtained, indicating that
it is configured to advertise at intervals of 100 to
200 ms. The ’03’ represents Advertising Type, in-
dicating nonconnectable advertising. When Adver-
tising Type is 0 × 03 (ADV NONCONN IND), Ad-
vertising Interval Min and Advertising Interval Max
should not be set to values less than 0x00A0 (100 ms)
(Bluetooth Core Specification 5.0., 2016). Therefore,
in this study, the advertising interval range was set
from 100 to 2000 ms in 100 ms increments for per-
formance measurement. ‘0×000A’ is the LE Set Ad-
vertise Enable Command, allowing the start of adver-
tising by setting the Advertising Enable command to
’ 0×01’ (Advertising is enabled).
5 PERFORMANCE EVALUATION
5.1 Experimental Environment
In this Section, we describe the experimental environ-
ment for implementing a covert storage channel using
iBeacon based on the commands outlined in Section
4. The experiment was conducted in a Raspberry Pi
3 B+ environment using Python 3, and the transmit-
ter and receiver codes were implemented by entering
the commands into the terminal using hcitool. Bluez
is a library that enables efficient Bluetooth modular
implementation on Linux systems (bluez Homepage,
2016), and version 5.55 was installed. The trans-
mitting Raspberry Pi advertises iBeacon packets with
packet data, as described in Section 4, whereas the re-
ceiving Raspberry Pi receives iBeacon packets from
the transmitting Raspberry Pi and outputs the recep-
tion time, raw data, and raw data converted into hex-
adecimal.
To identify successfully Received and Missing
Packets, we included sequential sequence numbers
from 1 to 60 at the end of the payload. The PDR for
each advertising interval was calculated using Equa-
tion (1) and rounded to the third decimal place.
Implementation and Analysis of Covert Channel Using iBeacon
865
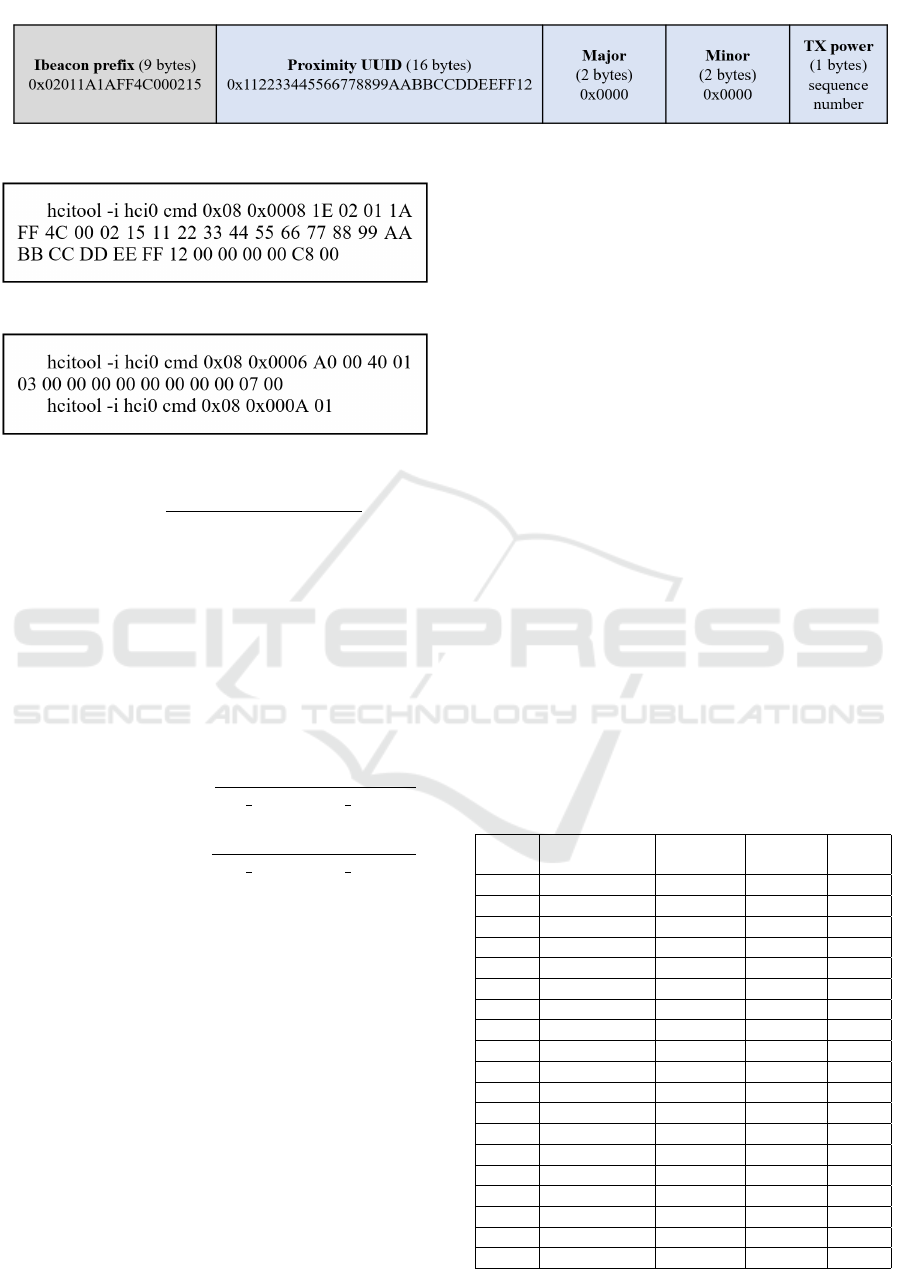
Figure 4: Payload that uses the TX power field as a sequence number.
Figure 5: Advertisement payload configuration command.
Figure 6: Advertising interval configuration command.
PDR(%) =
(Received packets) ∗ 100
(Total packets)
(1)
As shown in Fig. 1 in Section 3, the UUID, Major,
Minor, and TX power can be used as covert channel
fields in the iBeacon payload; therefore, 20 bytes of
information can be transmitted per packet. Therefore,
the Max Throughput equation and Min Throughput
equation for each advertising interval are as follows
formula (2) and (3) (Ameri and Johnson, 2017), re-
spectively, rounded from the first decimal place.
Maxthroughput (Bps) =
(Received packets) ∗ 20
min advertising interval
(2)
Minthroughput (Bps) =
(Received packets) ∗ 20
max advertising interval
(3)
5.2 Experimental Results
In this Section, PDR and throughput are used as eval-
uation indicators to verify the performance of the pro-
posed covert channel using iBeacon. We transmitted
60 packets per advertisement interval from the trans-
mitter to the receiver and repeated this process 100
times to calculate the average number of successfully
received and missing packets. Table 3 and Fig. 7 rep-
resent the PDR by Advertising Interval, while Table
4 calculates the throughput from 100 to 2000 ms with
a 100 ms difference between the min and max adver-
tising intervals. If the advertising interval is 100–200
ms, packets are sent randomly at intervals between
100 and 200 ms.
As a result of the experiment, the best PDR
was 77.1% for 1700–1800 ms, and the worst PDR
was 75.25% for 600–700 ms, showing a 1.85%p
difference, confirming that they are similar overall.
The shorter the advertising interval, the greater the
throughput, with the largest throughput of 100–200
ms. This means that no matter which advertising in-
terval is selected and sent, packets are sent constantly,
and information can be exchanged by selecting the
appropriate advertising interval according to the cir-
cumstances of the sender and receiver.
6 DISCUSSION
In this study, we designed and implemented two
types of iBeacon covert channels. The Payload-based
covert channels can be used to transfer data if there
is no monitoring or logging and the channel capac-
ity needs to be maximized; however, they have low
concealment. Interval-based covert channels offer
higher concealment than payload-based channels but
have low channel capacity and can cause delays de-
pending on the transmission environment. These two
channels can be used complementarily. For example,
data can be sent to an interval-based covert channel
Table 3: PDR per Advertising Interval.
Index
Advertising
interval (ms)
Received
Packets
Missing
Packets
PDR
(%)
1 100–200 4,558 1,442 75.97
2 200–300 4,580 1,420 76.33
3 300–400 4,585 1,415 76.42
4 400–500 4,543 1,457 75.72
5 500–600 4,578 1,422 76.3
6 600–700 4,515 1,485 75.25
7 700–800 4,613 1,387 76.88
8 800–900 4,528 1,472 75.47
9 900–1000 4,575 1,425 76.25
10 1000–1100 4,581 1,419 76.35
11 1100–1200 4,580 1,420 76.33
12 1200–1300 4,572 1,428 76.2
13 1300–1400 4,580 1,420 76.33
14 1400–1500 4,581 1,419 76.35
15 1500–1600 4,566 1,434 76.1
16 1600–1700 4,569 1,431 76.15
17 1700–1800 4,626 1,374 77.1
18 1800–1900 4,614 1,386 76.9
19 1900 - 2000 4,571 1,429 76.18
ICISSP 2024 - 10th International Conference on Information Systems Security and Privacy
866
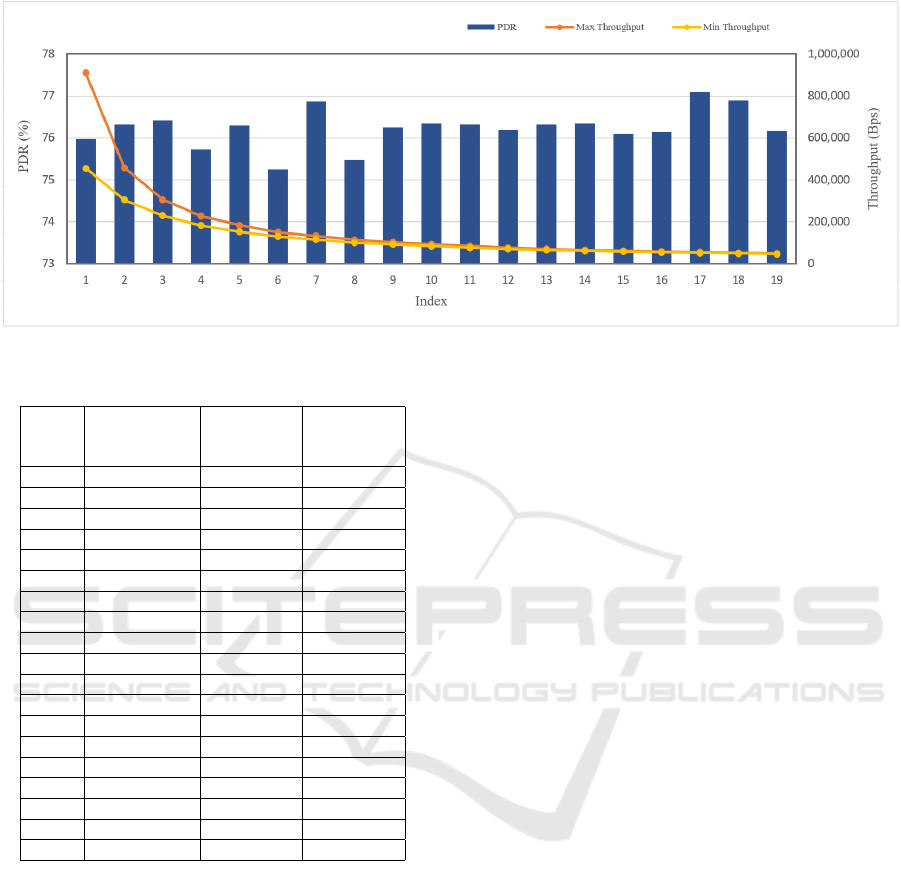
Figure 7: PDR and Throughput per Advertising Interval.
Table 4: Throughput per Advertising Interval.
Index
Advertising
interval (ms)
Max
throughput
(Bps)
Min
throughput
(Bps)
1 100–200 911,600 455,800
2 200–300 458,000 305,333
3 300–400 305,667 229,250
4 400–500 227,150 181,720
5 500–600 183,120 152,600
6 600–700 150,500 129,000
7 700–800 131,800 115,325
8 800–900 113,200 100,622
9 900–1000 101,667 91,500
10 1000–1100 91,620 83,291
11 1100–1200 83,273 76,333
12 1200–1300 76,200 70,338
13 1300–1400 70,462 65,429
14 1400–1500 65,443 61,080
15 1500–1600 60,880 57,075
16 1600–1700 57,113 53,753
17 1700–1800 54,454 51,400
18 1800–1900 51,267 48,568
19 1900 - 2000 48,116 45,710
while forging a portion of the payload to include a se-
quence number. Simply adding a sequence number to
the payload allows the receiver to recognize a packet
missing even if an error occurs during transmission.
This not only changes the advertising interval but also
involves forging the payload, allowing for achieving
a higher level of accuracy in CTC.
7 CONCLUSION
Although several covert channels have been studied,
research on covert channels using Bluetooth has not
yet been conducted. However, Bluetooth is closely
related to real life, and the possibility of abuse of
covert channels cannot be ruled out. In this study, we
designed the CSC and CTC using the iBeacon pay-
load and advertising interval. In addition, we imple-
mented the designed CSC and evaluated its PDR and
throughput. Overall, the PDR remained consistently
above 75%, and the advertising interval with the high-
est throughput relative to the PDR was in the range
of 100–200 ms. In this study, experiments were con-
ducted based on iBeacon; however, covert channels
could be established in other beacons, such as Eddys-
tone.
We have shown from experimental results that
large amounts of data can be secretly transmitted and
received using the characteristics of beacon. Future
studies will implement and evaluate the interval-based
covert channel. Also, we would like to consider coun-
termeasure to prevent beacon covert channel.
ACKNOWLEDGEMENTS
This work was partly supported by the Korea Institute
for Advancement of Technology (KIAT) grant funded
by the Korean Government (MOTIE) (P0008703, The
Competency Development Program for Industry Spe-
cialists) and MSIT under the ICAN (ICT Challenge
and Advanced Network of HRD) program (No. IITP-
2022-RS-2022-00156310), supervised by the Insti-
tute of Information Communication Technology Plan-
ning and Evaluation (IITP).
REFERENCES
ABIresearch (2020). Bluetooth iot market set to
nearly quadruple by 2024 as smart home
exceeds 800 million device shipments.
https://www.abiresearch.com/press/bluetooth-iot-
Implementation and Analysis of Covert Channel Using iBeacon
867

market-set-nearly-quadruple-2024-smart-home-
exceeds-800-million-device-shipments/.
Ameri, A. and Johnson, D. (2017). Covert channel over
network time protocol. In Proceedings of the 2017
International Conference on Cryptography, Security
and Privacy, pages 62–65.
Bluetooth, S. (2016). Proprietary : Bluetooth core specifi-
cation v5.0.
bluez Homepage (2016). http://www.bluez.org/about/.
Claeys, T., Rousseau, F., Simunovic, B., and Tourancheau,
B. (2019). Thermal covert channel in bluetooth low
energy networks. In Proceedings of the 12th Confer-
ence on Security and Privacy in Wireless and Mobile
Networks, pages 267–276.
Coyac-Torres, J. E., Rivero-Angeles, M. E., and Aguirre-
Anaya, E. (2021). Cognitive radio based system
for best effort communications in sound-based covert
channel for iot environments. Mobile Networks and
Applications, 26:1449–1460.
Dalkılıc¸, F., C¸ abuk, U. C., Arıkan, E., and G
¨
urkan, A.
(2017). An analysis of the positioning accuracy of
ibeacon technology in indoor environments. In 2017
International Conference on Computer Science and
Engineering (UBMK), pages 549–553. IEEE.
Developer, A. (2014). Getting started with ibeacon. Re-
trieved May, 10:2018.
Eddystone (2018). https://github.com/google/eddystone/.
Gast, M. S. (2014). Building applications with IBeacon:
proximity and location services with bluetooth low en-
ergy. ” O’Reilly Media, Inc.”.
Gnad, D. R., Nguyen, C. D. K., Gillani, S. H., and Tahoori,
M. B. (2021). Voltage-based covert channels using
fpgas. ACM Transactions on Design Automation of
Electronic Systems (TODAES), 26(6):1–25.
Griffiths, S., Wong, M. S., Kwok, C. Y. T., Kam, R., Lam,
S. C., Yang, L., Yip, T. L., Heo, J., Chan, B. S. B.,
Xiong, G., et al. (2019). Exploring bluetooth beacon
use cases in teaching and learning: Increasing the sus-
tainability of physical learning spaces. Sustainability,
11(15):4005.
Hern
´
andez-Rojas, D. L., Fern
´
andez-Caram
´
es, T. M., Fraga-
Lamas, P., and Escudero, C. J. (2017). Design and
practical evaluation of a family of lightweight proto-
cols for heterogeneous sensing through ble beacons in
iot telemetry applications. Sensors, 18(1):57.
iBeacon Homepage (2015).
https://developer.apple.com/ibeacon/.
Kolias, C., Copi, L., Zhang, F., and Stavrou, A. (2017).
Breaking ble beacons for fun but mostly profit. In Pro-
ceedings of the 10th European Workshop on Systems
Security, pages 1–6.
Li, Y., Zhang, X., Xu, X., and Tan, Y.-a. (2020). A ro-
bust packet-dropout covert channel over wireless net-
works. IEEE Wireless Communications, 27(3):60–65.
Mackey, A., Spachos, P., Song, L., and Plataniotis, K. N.
(2020). Improving ble beacon proximity estimation
accuracy through bayesian filtering. IEEE Internet of
Things Journal, 7(4):3160–3169.
Maiti, A. and Jadliwala, M. (2019). Light ears: Information
leakage via smart lights. Proceedings of the ACM on
Interactive, Mobile, Wearable and Ubiquitous Tech-
nologies, 3(3):1–27.
Na, X., Guo, X., He, Y., and Xi, R. (2021). Wi-attack:
Cross-technology impersonation attack against ibea-
con services. In 2021 18th Annual IEEE Interna-
tional Conference on Sensing, Communication, and
Networking (SECON), pages 1–9. IEEE.
Priest, J. and Johnson, D. (2015). Covert channel over apple
ibeacon. In Proceedings of the International Confer-
ence on Security and Management (SAM), page 51.
The Steering Committee of The World Congress in
Computer Science, Computer . . . .
Saenger, J., Mazurczyk, W., Keller, J., and Caviglione, L.
(2020). Voip network covert channels to enhance
privacy and information sharing. Future Generation
Computer Systems, 111:96–106.
Schmidbauer, T., Keller, J., and Wendzel, S. (2022). Chal-
lenging channels: Encrypted covert channels within
challenge-response authentication. In Proceedings of
the 17th International Conference on Availability, Re-
liability and Security, pages 1–10.
Seong, H., Kim, I., Jeon, Y., Oh, M.-K., Lee, S., and Choi,
D. (2022). Practical covert wireless unidirectional
communication in ieee 802.11 environment. IEEE In-
ternet of Things Journal, 10(2):1499–1516.
Shan, G. and Roh, B.-H. (2018). Advertisement interval
to minimize discovery time of whole ble advertisers.
IEEE Access, 6:17817–17825.
Tian, J., Xiong, G., Li, Z., and Gou, G. (2020). A
survey of key technologies for constructing network
covert channel. Security and Communication Net-
works, 2020:1–20.
Zhang, Q., Zhang, X., Xue, Y., and Hu, J. (2020). A stealthy
covert storage channel for asymmetric surveillance
volte endpoints. Future Generation Computer Sys-
tems, 102:472–480.
Zhang, X., Tan, Y.-A., Liang, C., Li, Y., and Li, J. (2018).
A covert channel over volte via adjusting silence peri-
ods. IEEE Access, 6:9292–9302.
ICISSP 2024 - 10th International Conference on Information Systems Security and Privacy
868
