
Conceptualising an Anti-Digital Forensics Kill Chain for Smart Homes
Mario Raciti
1,2 a
1
IMT School for Advanced Studies Lucca, Lucca, Italy
2
Department of Mathematics and Computer Science, University of Catania, Catania, Italy
Keywords:
Anti-Forensics, Privacy, IoT, Cloud, Cybercrime.
Abstract:
The widespread integration of Internet of Things (IoT) devices in households generates extensive digital foot-
prints, notably within Smart Home ecosystems. These IoT devices, brimming with data about residents, inad-
vertently offer insights into human activities, potentially embodying even criminal acts, such as a murder. As
technology advances, so does the concern for criminals seeking to exploit various techniques to conceal evi-
dence and evade investigations. This paper delineates the application of Anti-Digital Forensics (ADF) in Smart
Home scenarios and recognises its potential to disrupt (digital) investigations. It does so by elucidating the
current challenges and gaps and by arguing, in response, the conceptualisation of an ADF Kill Chain tailored
to Smart Home ecosystems. While seemingly arming criminals, the Kill Chain will allow a better understand-
ing of the distinctive peculiarities of Anti-Digital Forensics in Smart Home scenario. This understanding is
essential for fortifying the Digital Forensics process and, in turn, developing robust countermeasures against
malicious activities.
1 INTRODUCTION
Locard’s exchange principle holds that “the perpe-
trator of a crime will bring something into the crime
scene and leave with something from it, and that both
can be used as forensic evidence.” (Locard, ND). This
principle also applies in crimes that involve a digital
footprint. From a cybersecurity perspective, Digital
Forensics (DF) can be considered as a posteriori type
of security measure, i.e., it is triggered after a crime
has been committed.
A peculiar and recurrent context in which crimes
happen is represented by homes. Nowadays, most do-
mestic environments have several Internet of Things
(IoT) devices ranging from voice assistants to smart
thermostats and security cameras, whose widespread
adoption presents unique challenges from a forensic
standpoint. These devices have become an integral
part of many households, offering convenience, con-
nectivity, and features so far unthinkable. Such a dig-
ital upgrade has changed house buildings into what
is defined as Smart Home, with a consequent growth
of opportunities for cybercrimes. In fact, a classical
example of cybercrime committed in a Smart Home
is given from the violation of a device, leading the
attacker to take control of it or steal private data,
a
https://orcid.org/0000-0002-7045-0213
analysing the case from a privacy perspective. In ad-
dition, criminals may also leverage the IoT devices
within a Smart Home to conduct physical crimes, e.g.,
by disabling surveillance cameras or unlocking doors.
Moreover, considering the ambivalence of their
nature, “smart” devices also provide an opportunity
for malicious actors to exploit, manipulate, or erase
the digital traces that they store, i.e., audio record-
ings, video footage, and device interaction logs, thus
obstructing the forensic process. These activities fall
under the umbrella of the unorthodox discipline of
Anti-Digital Forensics (ADF).
The objectives and implications of ADF have be-
come subjects of significant debate within the re-
search community and among experts. A prevailing
opinion tends to characterise ADF tools as inherently
malevolent in both intent and design, yet an alter-
native perspective posits them towards a more con-
structive goal. In fact, this viewpoint, argued by J.
Foster and V. Liu at the 2005 BlackHat USA Con-
ference (Foster and Liu, 2005), advocates for the use
of ADF tools as a means to highlight deficiencies in
Digital Forensics procedures and tools. According
to the authors, the exposure to Anti-Digital Forensics
prompts increased scrutiny by investigators, thus aim-
ing to improve evidence reliability, enhance forensic
tools, and elevate the overall quality of forensic edu-
cation.
Raciti, M.
Conceptualising an Anti-Digital Forensics Kill Chain for Smart Homes.
DOI: 10.5220/0012449700003648
Paper published under CC license (CC BY-NC-ND 4.0)
In Proceedings of the 10th International Conference on Information Systems Security and Privacy (ICISSP 2024), pages 831-837
ISBN: 978-989-758-683-5; ISSN: 2184-4356
Proceedings Copyright © 2024 by SCITEPRESS – Science and Technology Publications, Lda.
831

This paper explores the challenges and gaps on the
application of Anti-Digital Forensics in Smart Home
ecosystems and anticipates the conceptualisation of
an ADF Kill Chain for Smart Homes as a response.
2 BACKGROUND
The traditional definition of Digital Forensics is sum-
marised by NIST as “the application of computer sci-
ence and investigative procedures involving the exam-
ination of digital evidence – following proper search
authority, chain of custody, validation with mathemat-
ics, use of validated tools, repeatability, reporting,
and possibly expert testimony.” (NIST, ND). From
the definition, it follows the important role of Digi-
tal Evidence, which is defined as “Any probative in-
formation stored or transmitted in digital form that
a party to a court case may use at trial.” (Casey,
2011). Furthermore, Horsman and Sunde (Horsman
and Sunde, 2022) positioned Digital Forensics as a
subset of forensics science, while Abulaish and Hal-
dar (Abulaish and Haldar, 2018) defined it as “a sys-
tematic process of uncovering a crime through the in-
vestigation of digital devices”.
2.1 Smart Home Forensics
The study of IoT Security has seen Sklavos et
al. (Sklavos et al., 2017) discussing trust, security, and
privacy, emphasising the educational value and util-
ity of the concepts and protocols. At the same time,
IoT Forensics has also gained significant attention in
recent years due to the growing prevalence of IoT
devices and the increasing sophistication of cyber-
crimes. While several surveys have explored the field
of Digital Forensics in the context of IoT (Kaushik
et al., 2023), they often focus on specific aspects, such
as Network Forensics, Malware Forensics, or Mem-
ory Forensics (Alkhanafseh et al., 2019). As a result,
there is a need for a more comprehensive overview
that covers the forensics topics as a whole in the IoT
domain and, in particular, in Smart Home ecosystems.
A Smart Home ecosystem includes any device that
can be monitored or controlled via Internet access.
Typically, devices are connected to a central Smart
Home hub, i.e., a “gateway”, and have external in-
teractions with cloud services, e.g., for storage pur-
poses. For the sake of demonstration, Figure 1 il-
lustrates a typical Smart Home ecosystem, giving an
idea of the complexity and heterogeneity of the el-
ements involved. These include smart doors, smart
TVs, smart lights, smart surveillance systems, home
assistants, smart sensors, et cetera. A comprehensive
understanding of the Smart Home ecosystem serves
as a foundational basis, allowing for more targeted
and effective studies in various realms, such as Cy-
bersecurity, Privacy and, Digital Forensics.
Smart Home
Cloud Services
Figure 1: Illustration of a Smart Home Ecosystem.
Ghirardello et al. (Ghirardello et al., 2018) in-
troduced a reference architecture for smart homes
through an exploration of three distinct perspectives
within the ecosystem: (i) the functional perspective,
encompassing essential operations required for the
smart home’s regular functioning; (ii) the physical
perspective, detailing the physical elements crucial
for executing the smart home’s functions; and (iii)
the communication perspective, outlining the essen-
tial protocols for transmitting control and information
flows among these components.
Casey (Casey, 2015) emphasised the need for
digital investigators to become familiar with smart
home systems in order to understand their involve-
ment in criminal activity and the type of information
they contain. Furthermore, Kim et al. (Kim et al.,
2020) focused on obtaining, categorising, and exam-
ining Smart Home data from notable devices avail-
able on the market, i.e., Google Nest Hub, Sam-
sung SmartThings, and Kasa Cam, for forensic pur-
poses. The study scrutinised the collected Smart
Home data through companion apps, web interfaces,
and APIs to pinpoint significant information appli-
cable to forensic investigations. Also, Awasthi et
al. (Awasthi et al., 2018) presented the Almond Smart
ICISSP 2024 - 10th International Conference on Information Systems Security and Privacy
832

Home Hub as a potential goldmine for digital foren-
sics, with its centralised data collection. In addition,
Lee et al. (Lee et al., 2020) proposed a blockchain-
based Smart Home gateway architecture that ensures
data integrity and availability, in prevention of data
forgery. James (James, 2019) developed an intrusion
prevention system that can detect and protect against
cyber-attacks in Smart Home ecosystems. Anthi et
al. (Anthi et al., 2019) introduced a supervised in-
trusion detection system specifically for Smart Home
IoT devices, which can effectively distinguish be-
tween benign and malicious network activity. More-
over, Forfot and Østby (Forfot and Østby, 2021) sug-
gested a risk assessment model for Digital Forensic
Readiness in IoT.
2.2 Anti-Digital Forensics
Various studies have investigated Anti-Digital Foren-
sics techniques employed by cyber-criminals to hide
their activities, but a comprehensive analysis of the
various existing Anti-Forensics techniques is often
lacking. The discussion surrounding Anti-Forensics
(AF) has had a more pronounced impact within law
enforcement circles than in the scientific commu-
nity (Conlan et al., 2016). Harris (Harris, 2006) de-
fined Anti-Forensics as: “methods used to prevent (or
act against) the application of science [...] enforced
by police agencies.”.
Literature abounds in numerous definitions of
Anti-Digital Forensics, but one of the more widely
known and accepted comes from Rogers: “Attempts
to negatively affect the existence, amount and/or qual-
ity of evidence from a crime scene or make the anal-
ysis and examination of evidence difficult or impos-
sible to conduct.” (Rogers, 2005). Rogers also pro-
posed a widely adopted taxonomy for the categorisa-
tion of ADF techniques: data hiding, artefact wiping,
trail obfuscation and attacks against the forensic pro-
cess and tools. Figure 2 depicts Rogers’ taxonomy
and provides an example for each category: steganog-
raphy represents a method for data hiding, physical
destruction is an extreme practice for artefact wiping,
data forgery is a common method for trailing obfus-
cation, and reverse engineering of forensic tools al-
lows spotting weaknesses and/or vulnerabilities that
can lead to hinder the tool effectiveness.
In an Anti-Digital Forensics domain the primary
objective is to break the forensic process, thereby
such practices can be summarised as the dichotomous
counterpart to the “Forensic Readiness” (FR) prin-
ciple, coined by Tan (Sachowski, 2016). Forensic
Readiness was standardised within the Digital Foren-
sic Investigation Readiness Process (DFIRP) model in
ISO/IEC 27043:2015 standard. A trending approach
to FR, proposed by Rahman et al. (Ab Rahman et al.,
2016) and conceptually similar to Security-by-design,
is Forensic-by-Design (FbD), which aims to integrate
forensic requirements into every relevant phase of a
system design and development stages, ultimately to
obtain “Forensic-ready” systems by continuously re-
viewing the desired state of forensic readiness.
Alenezi et al. (Alenezi. et al., 2019) advanced
a review of challenges and future directions in IoT
Forensics, with the inclusion of Anti-Digital Foren-
sics as one of the major challenges. Furthermore,
Jean-Paul et al. (Yaacoub et al., 2022) discussed the
rise of the Anti-Anti-Forensic protection mechanism
against Anti-Forensics activities specifically in IoT
systems.
3 MOTIVATION
As Section 2.1 outlined, there has been some atten-
tion directed towards Smart Home Forensics. How-
ever, a noticeable disparity arises when consider-
ing the scarcity of studies dedicated to Anti-Digital
Forensics, especially in relation with Smart Home
ecosystems, thereby indicating a discernible gap in
the scientific community and among law enforce-
ment and forensics experts. A critical lack in the
current research landscape is given by the absence
of guidelines or standardised frameworks that incor-
porate the steps of Anti-Digital Forensics in Smart
Home scenarios. In fact, while the traditional Cyber
Kill Chain framework (Lockheed, ND), developed by
Lockheed Martin, is widely used to understand the
stages of cyber-attacks and respond effectively, it is
not specifically designed for IoT devices, thus fail-
ing to address the unique challenges and intricacies
associated with Smart Home ecosystems. The same
argument holds for the MITRE duality kill chains
ATT&CK (MITRE, NDa) and D3FEND (MITRE,
NDb). Moreover, the PEnetration Testing the Inter-
net of Things (PETIoT) (Bella et al., 2023) frame-
work advances a kill chain for IoT devices, but it fo-
cuses on cybersecurity aspects, rather than forensics.
Hence, the general motivation for this paper to raise
the problem and initiate research on the topic.
4 AN IDEAL KILL CHAIN
The term kill chain is a military concept which iden-
tifies the structure of an attack. It typically consists
of: identification of target, dispatching of (military)
forces to target, initiation of attack on target, destruc-
Conceptualising an Anti-Digital Forensics Kill Chain for Smart Homes
833
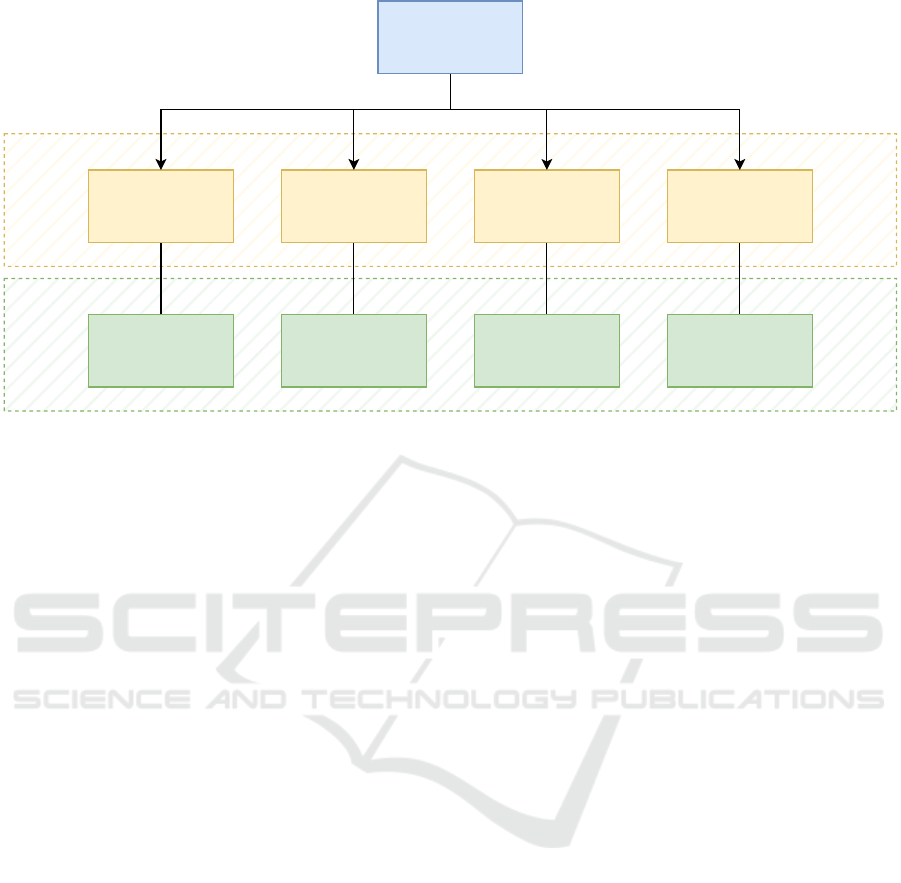
Data Hiding Artefact Wiping Trail Obfuscation
Attacks against FP
and Tools
RE of ToolsData ForgerySteganography Physical Destruction
Anti-Digital Forensics
Rogers' Categories
Examples
Figure 2: Anti-Digital Forensics Taxonomy and Examples.
tion of target. Conversely, the idea of “breaking” an
opponent’s kill chain is a method of defence or pre-
emptive action. Following our argument, we set the
following research questions:
RQ. What are the Anti-Digital Forensics steps
in a Smart Home ecosystem?
To go about such a question, we aim to conceptu-
alise an Anti-Digital Forensics Kill Chain that is tai-
lored for Smart Home ecosystems. The aim of the
ADF Kill Chain is twofold. The first is that malicious
actors can leverage it as a tool for the exploitation of
forensic vulnerabilities. Just as a smoke screen is used
in a traditional military action to obscure visibility
and confuse the enemy, the Kill Chain supports mali-
cious actors in the creation of a (virtual) veil of con-
fusion within a Smart Home. The secondary aim of
the Kill Chain relies on understanding adversary tac-
tics to empower law enforcement to counter those ef-
forts, thereby enhancing forensic investigation effec-
tiveness and ensuring the unimpeded pursuit of truth
and justice.
4.1 Research Goals
This paper tentatively outlines the following research
goals, acknowledging that they represent an initial
stage of inquiry.
Review of ADF in Smart Home. Investigate and
document existing Anti-Digital Forensics techniques
that can be specifically applied to Smart Home
ecosystems. Identify the methods malicious actors
employ to exploit vulnerabilities within the forensic
process, including tampering with evidence, identity
concealment, and misleading investigators. Under-
stand the feasibility of these techniques in the context
of Smart Home ecosystems.
Intersection of Privacy and ADF. Examine the
current regulatory landscape, with a focus on pri-
vacy, and evaluate the differences between legitimate
privacy-preserving techniques implemented in Smart
Home IoT devices and illicit ADF activities. Identify
a common ground where privacy measures can co-
exist with efforts to counteract malicious ADF tech-
niques.
Integration of AI for ADF in Smart Home. In-
vestigate the potential role of Artificial Intelligence in
support of Anti-Digital Forensics activities in Smart
Home ecosystems. Explore opportunities and limita-
tions of existing tools.
Design of ADF Kill Chain for Smart Home. De-
velop an Anti-Digital Forensics Kill Chain tailored
to Smart Home ecosystems. Identify and categorise
the key steps in the proposed ADF Kill Chain, con-
sidering the peculiar elements presented by the Smart
Home context.
Case Studies and Real-World Applications. Con-
duct case studies to illustrate real-world instances of
Anti-Digital Forensics in Smart Home ecosystems.
Analyse these cases to identify patterns, tactics, and
potential variations in ADF techniques employed by
adversaries.
ICISSP 2024 - 10th International Conference on Information Systems Security and Privacy
834

4.2 Expected Challenges
This paper anticipates the following challenges:
1. Device Heterogeneity. Smart Home ecosystems
encompass various devices with different types of
architectures, operating systems, communication
protocols, and storage mechanisms. Designing a
framework that can handle the heterogeneity of
these devices and accommodate their unique char-
acteristics poses a significant challenge.
2. Resource Constraints and Scalability. Smart
home IoT devices often have limited resources
in terms of processing power, memory, and stor-
age. Manipulating or erasing digital evidence
within these resource constraints require efficient
and scalable techniques. Developing methodolo-
gies that optimise resource usage while conduct-
ing ADF activities poses a significant challenge.
3. Forensic Readiness. Ensuring the chain of cus-
tody and integrity of digital evidence is crucial in
forensic investigations. The Kill Chain needs to
address challenges related to hinder the integrity
and reliability of evidence, striving to contrast the
potential forensic readiness of the Smart Home
ecosystem, considering the dynamic nature of its
devices.
4. Cloud Services. Smart Home IoT devices often
leverage cloud services for data storage and syn-
chronisation. The Kill Chain needs to consider
challenges for gaining illicit access to data stored
in the cloud, for the subsequent manipulation or
erasure of such digital evidence.
4.3 Development Phases
The conceptualisation of the ADF Kill Chain for
Smart Home ecosystems involves a meticulous work-
flow. This paper anticipates the main phases for the
development of the Kill Chain.
The initial phase is represented by the analysis of
a standard Smart Home ecosystem from the perspec-
tive of an individual who desires protection against a
potential digital forensic investigation. Such analysis
entails identifying potential vulnerabilities and weak
points in the ecosystem where Anti-Digital Forensics
could be employed. The malicious individual might
consider aspects such as device communication, data
storage, and user interactions as potential areas for ob-
fuscation, manipulation, or destruction of evidence to
evade forensic scrutiny. To this extent, a survey on
Anti-Digital Forensics techniques provides the appro-
priate knowledge base to elicit the malicious individ-
ual’s options.
Furthermore, the ADF Kill Chain needs to be
aware of the current status of Forensic Readiness and
Forensic-by-Design in Smart Home systems. In fact,
these embody measures that the Kill Chain must over-
come or, at least, it needs to adapt to.
The validation of the ADF Kill Chain stands as a
crucial step in establishing its efficacy and relevance
within the context of Smart Home ecosystems. This
phase involves rigorous testing and assessment to en-
sure that each stage of the Kill Chain accurately re-
flects real-world adversarial activities and their im-
pact on digital forensic investigations.
As we shall see below, the next phase involves the
practical application of the ADF Kill Chain to a de-
signed case study that mirrors realistic scenarios in
Smart Home environments.
In addition, the evaluation phase encompasses the
examination of how well the ADF Kill Chain can
be executed by adversaries seeking to manipulate or
destroy digital evidence within Smart Home IoT de-
vices. This process helps identify potential weak-
nesses and areas of improvement in the Kill Chain,
allowing for iterative refinement.
Assessments on defensive measures against the
Kill Chain conclude the flow and ensure an under-
standing of its (technical, legal, and ethical) limits.
4.4 Preliminary Conceptualisation
We anticipate that certain stages within our concep-
tualised Kill Chain may exhibit similarities with es-
tablished state-of-the-art kill chains. This expecta-
tion stems from the recognition that adversarial strate-
gies often share fundamental principles across differ-
ent cyber contexts. For instance, the well-known steps
of “Reconnaissance” and “Exfiltration” can arguably
be part of a Kill Chain tailored for Anti-Digital Foren-
sics, as fundamental aspects of Vulnerability Assess-
ment and Penetration Testing. By following this argu-
ment, in Smart Home ecosystems the Reconnaissance
step can be exemplified by the identification of the de-
vices connected, namely device discovery.
Moreover, in our current research, we have iden-
tified some steps that are peculiar to ADF scenarios
and, at the same time, differ from the classical steps
of a cybersecurity-oriented kill chain. While the de-
sign, including the detail and ordering, of these steps
have yet to be fully conjectured, an overarching con-
ceptualisation is given below.
Step A — Tampering with Digital Traces.
Objective. Manipulate or erase digital traces to ob-
struct forensic investigation.
Activities. Tampering with audio recordings, video
Conceptualising an Anti-Digital Forensics Kill Chain for Smart Homes
835

footage, and device interaction logs. Implementing
techniques to make forensic analysis challenging.
Step B — Concealing Identities.
Objective. Conceal the identity of malicious actors
involved in ADF activities.
Activities. Masking IP addresses and digital foot-
prints. Falsifying user identities associated with
Smart Home devices.
Step C — Misleading Investigators.
Objective. Introduce false information to mislead
forensic investigators.
Activities. Planting deceptive digital breadcrumbs and
manipulating timestamps and metadata.
Step D — Cloud Data Manipulation.
Objective. Manipulate data stored in cloud services
associated with Smart Home devices.
Activities. Getting remote access to cloud services
where Smart Home data is stored. Tamper with
or delete such data remotely, ensuring techniques to
avoid logging.
4.5 A Case Study
For the application of the ADF Kill Chain, we pro-
pose a case study on a Smart Home system that resem-
bles the following hypothetical scenarios. A criminal
suspect, namely Mr. X, is under investigation for a
serious crime. Whether Mr. X is guilty or not, he
is aware of the digital footprints left by Smart Home
IoT devices and is concerned about the investigation.
Therefore, Mr. X seeks to exploit these devices to
create a fabricated digital alibi that misrepresents his
presence at the crime scene. To achieve this, he de-
vises a plan to tamper with and destroy digital evi-
dence from the Smart Home IoT devices within his
residence. Mr. X believes that by evading digital
forensic detection, he can create a false narrative to
defend himself against the charges. Mr. X’s plan in-
volves leveraging the Kill Chain to carry out his dig-
ital alibi fabrication scheme. Following the outcomes
from the above scenario, we may model a second sce-
nario featuring an investigator, namely, Mrs. Y, who
wants to understand the crucial steps that Mr. X em-
ployed to hinder the investigation in the Smart Home
crime scene. Thus, Mrs. Y can leverage the Kill
Chain for Digital Forensics purposes.
5 CONCLUSIONS
This paper provided an in-depth exploration of the
challenges and gaps presented by the forensic per-
spective of Smart Home ecosystems, specifically ad-
dressing the connections with the emerging subject of
Anti-Digital Forensics. The paper advised a direc-
tion to answer the research question by arguing the
conceptualisation of an ADF Kill Chain tailored for
Smart Home ecosystems.
The ethical implication of a Kill Chain supporting
criminals (at least at a first glance) will be mitigated
by the dual product of elucidating and understand-
ing potential adversarial steps, hence providing the
knowledge to prepare appropriate countermeasures in
support of Anti-Anti-Forensics.
The endeavour to fill the void in training, aware-
ness, and knowledge-sharing within the ADF land-
scape is essential for ensuring the integrity and effi-
cacy of the Digital Forensics process applied in Smart
Home scenarios. This paper encouraged future re-
search to enhance the comprehension of Anti-Digital
Forensics, both in a general context and in its ap-
plication in Smart Home ecosystems. This will sig-
nificantly help to elucidate the boundaries of Digi-
tal Forensics, with a consequent mitigation of the so-
called “CSI effect.”, i.e., the phenomenon where peo-
ple’s perception of forensics science is influenced by
fictional portrayals in popular media, thus improving
criminal trials and court proceedings.
REFERENCES
Ab Rahman, N. H., Glisson, W. B., Yang, Y., and Choo,
K.-K. R. (2016). Forensic-by-design framework for
cyber-physical cloud systems. IEEE Cloud Comput-
ing, 3(1):50–59.
Abulaish, M. and Haldar, N. (2018). Advances in digital
forensics frameworks and tools: A comparative in-
sight and ranking. International Journal of Digital
Crime and Forensics, 10:95–119.
Alenezi., A., Atlam., H. F., Alsagri., R., Alassafi., M. O.,
and Wills., G. B. (2019). Iot forensics: A state-of-the-
art review, challenges and future directions. In Pro-
ceedings of the 4th International Conference on Com-
plexity, Future Information Systems and Risk - COM-
PLEXIS, pages 106–115. INSTICC, SciTePress.
Alkhanafseh, M., Qatawneh, M., and Almobaideen, W.
(2019). A survey of various frameworks and solu-
tions in all branches of digital forensics with a focus
on cloud forensics. International Journal of Advanced
Computer Science and Applications, 10.
Anthi, E., Williams, L., Słowi
´
nska, M., Theodorakopoulos,
G., and Burnap, P. (2019). A supervised intrusion de-
tection system for smart home iot devices. IEEE In-
ternet of Things Journal, 6(5):9042–9053.
ICISSP 2024 - 10th International Conference on Information Systems Security and Privacy
836

Awasthi, A., Read, H. O., Xynos, K., and Sutherland, I.
(2018). Welcome pwn: Almond smart home hub
forensics. Digital Investigation, 26:S38–S46.
Bella, G., Biondi, P., Bognanni, S., and Esposito, S. (2023).
Petiot: Penetration testing the internet of things. In-
ternet of Things, 22:100707.
Casey, E. (2011). Digital Evidence and Computer Crime.
Elsevier.
Casey, E. (2015). Smart home forensics. Digital Investiga-
tion, 13.
Conlan, K., Baggili, I., and Breitinger, F. (2016). Anti-
forensics: Furthering digital forensic science through
a new extended, granular taxonomy. Digital investi-
gation, 18:S66–S75.
Forfot, A. D. and Østby, G. (2021). Digital forensic readi-
ness in iot - a risk assessment model. In Yildirim Yay-
ilgan, S., Bajwa, I. S., and Sanfilippo, F., editors, In-
telligent Technologies and Applications, pages 53–64,
Cham. Springer International Publishing.
Foster, J. and Liu, V. (2005). Catch Me If You Can: Ex-
ploiting Encase, Microsoft, Computer Associates, and
the rest of the bunch. . . .
Ghirardello, K., Maple, C., Ng, D., and Kearney, P. (2018).
Cyber security of smart homes: Development of a ref-
erence architecture for attack surface analysis. In Liv-
ing in the Internet of Things: Cybersecurity of the IoT
- 2018, pages 1–10.
Harris, R. (2006). Arriving at an anti-forensics consen-
sus: Examining how to define and control the anti-
forensics problem. digital investigation, 3:44–49.
Horsman, G. and Sunde, N. (2022). Unboxing the digital
forensic investigation process. Science & Justice, 62.
James, F. (2019). Iot cybersecurity based smart home intru-
sion prevention system. In 2019 3rd Cyber Security in
Networking Conference (CSNet), pages 107–113.
Kaushik, K., Bhardwaj, A., and Dahiya, S. (2023). Smart
home iot forensics: Current status, challenges, and fu-
ture directions. In 2023 International Conference on
Advancement in Computation & Computer Technolo-
gies (InCACCT), pages 716–721.
Kim, S., Park, M., Lee, S., and Kim, J. (2020). Smart home
forensics—data analysis of iot devices. Electronics,
9(8).
Lee, Y., Rathore, S., Park, J. H., and Park, J. H. (2020).
A blockchain-based smart home gateway architecture
for preventing data forgery. Human-centric Comput-
ing and Information Sciences, 10(1):9.
Locard (N/D). Exchange Principle.
Lockheed, M. (N/D). Cyber kill chain®.
MITRE (N/Da). ATT&CK.
MITRE (N/Db). D3FEND.
NIST (N/D). Digital Forensics Definition.
Rogers (2005). Anti-forensic presentation given to lock-
heed martin, san diego.
Sachowski, J. (2016). Chapter 4 - understanding foren-
sic readiness. In Sachowski, J., editor, Implementing
Digital Forensic Readiness, pages 45–52. Syngress,
Boston.
Sklavos, N., Zaharakis, I. D., Kameas, A., and Kalapodi, A.
(2017). Security & trusted devices in the context of
internet of things (iot). In 2017 Euromicro Conference
on Digital System Design (DSD), pages 502–509.
Yaacoub, J.-P. A., Noura, H. N., Salman, O., and Chehab,
A. (2022). Advanced digital forensics and anti-digital
forensics for iot systems: Techniques, limitations and
recommendations. Internet of things, 19:100544–
100544.
Conceptualising an Anti-Digital Forensics Kill Chain for Smart Homes
837
