
Security Analysis of an Image Encryption Scheme Based on a New
Secure Variant of Hill Cipher and 1D Chaotic Maps
George Tes¸eleanu
1,2 a
1
Advanced Technologies Institute, 10 Dinu Vintil
˘
a, Bucharest, Romania
2
Simion Stoilow Institute of Mathematics of the Romanian Academy, 21 Calea Grivitei, Bucharest, Romania
Keywords:
Image Encryption Scheme, Chaos Based Encryption, Cryptanalysis.
Abstract:
In 2019, Essaid et al. introduced a chaotic map-based encryption scheme for color images. Their approach
employs three improved chaotic maps to dynamically generate the key bytes and matrix required by the cryp-
tosystem. It should be noted that these parameters are dependent on the size of the source image. According to
the authors, their method offers adequate security (i.e. 279 bits) for transmitting color images over unsecured
channels. However, we show in this paper that this is not the case. Specifically, we present two cryptanalytic
attacks that undermine the security of Essaid et al.’s encryption scheme. In the case of the chosen plaintext
attack, we require only two chosen plaintexts to completely break the scheme. The second attack is a a chosen
ciphertext attack, which requires two chosen ciphertexts and compared to the first one has a rough complexity
of 2
24
. The attacks are feasible due to the fact that the key bits and matrix generated by the algorithm remain
unaltered for distinct plaintext images.
1 INTRODUCTION
The exponential increase in social media usage has
led to a heightened concern for the security of digital
images, particularly with regards to theft and unau-
thorized distribution. Consequently, this issue has
gained significant attention, prompting numerous re-
searchers to develop various image encryption tech-
niques. Chaotic maps have emerged as a favored
approach for encrypting images, largely due to their
high sensitivity to previous states, initial conditions,
or both. This desirable feature makes it challeng-
ing to anticipate their behavior or outputs, thus giv-
ing rise to numerous novel cryptographic algorithms
based on chaos. We refer the reader to (Zolfaghari
and Koshiba, 2022; Muthu and Murali, 2021; Hosny,
2020;
¨
Ozkaynak, 2018) for some surveys of such pro-
posals. Regrettably, due to inadequate security analy-
sis and a lack of design guidelines, a significant num-
ber of image encryption schemes based on chaos have
been found to contain critical security vulnerabilities.
To illustrate our point, we provide a list of compro-
mised schemes in Table 1. Please be aware that the
list is not exhaustive.
In (Essaid et al., 2019b) a chaos based encryp-
a
https://orcid.org/0000-0003-3953-2744
tion scheme is proposed. The authors use the En-
hanced Logistic Map (ELM), Enhanced Chebyshev
Map (ECM) and Enhanced Sine Map (ESM) as pseu-
dorandom number generators (PRNGs). Using these
three PRNGs, Essaid et al. randomly generate the
necessary key bytes. Then, the ELM PRNG is used to
generate a key matrix of size 2 × 2, such that the first
element of the matrix is invertible modulo 256. Since
ELM, ECM and ESM are simply used as PRNGs
and the scheme’s weakness is independent of the em-
ployed generators, we omit their description and sim-
ply consider the key bytes and matrix as being ran-
domly generated.
This paper presents our security analysis of the Es-
said et al. scheme. Specifically, we describe a chosen
plaintext attack and a chosen ciphertext attack, which
enables an attacker to decrypt all images of a particu-
lar size. To accomplish this, it is necessary to obtain
the ciphertexts of two chosen plaintexts or the plain-
texts of two chosen ciphertexts. Note that in the cho-
sen plaintext scenario, we reduce the scheme’s secu-
rity from 279 bits to 0 bits, while in the chosen cipher-
text scenario we reduce it to roughly 24 bits.
Structure of the Paper. We provide the necessary
preliminaries in Section 2. An alternative mathemati-
cal description of Essaid et al.’s scheme is outlined
Te¸seleanu, G.
Security Analysis of an Image Encryption Scheme Based on a New Secure Variant of Hill Cipher and 1D Chaotic Maps.
DOI: 10.5220/0012356600003648
Paper published under CC license (CC BY-NC-ND 4.0)
In Proceedings of the 10th International Conference on Information Systems Security and Privacy (ICISSP 2024), pages 745-749
ISBN: 978-989-758-683-5; ISSN: 2184-4356
Proceedings Copyright © 2024 by SCITEPRESS – Science and Technology Publications, Lda.
745
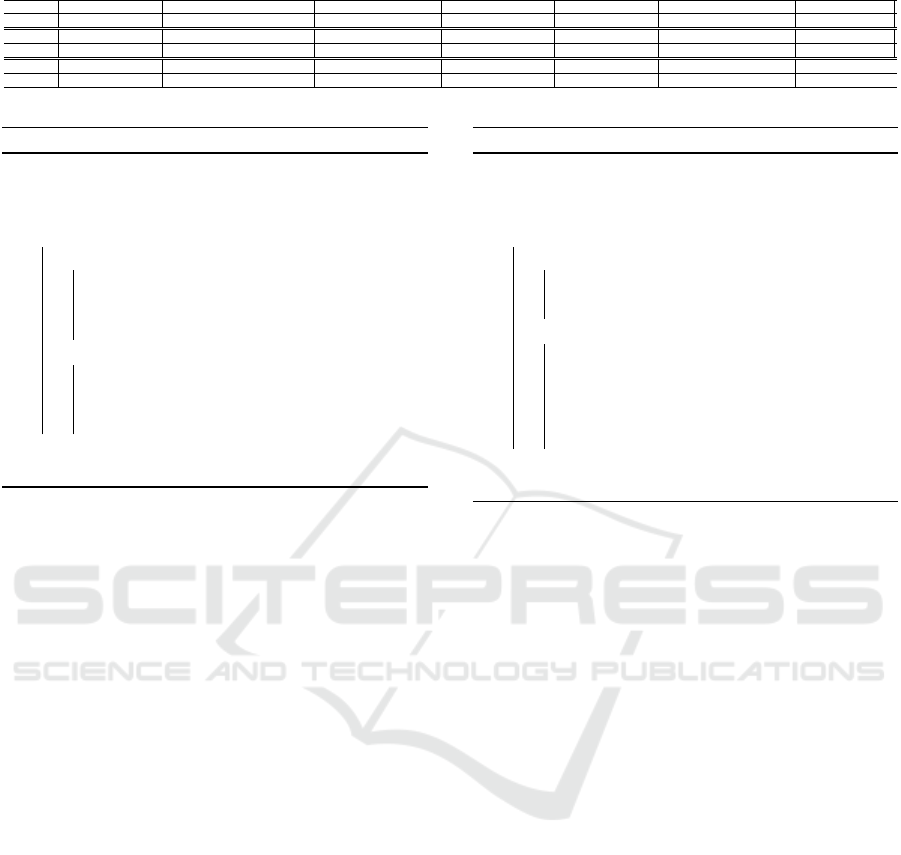
Table 1: Broken chaos based image encryption algorithms.
Scheme (Yen and Guo, 2000) (Matoba and Javidi, 2004) (Wang et al., 2012) (Huang et al., 2014) (Khan, 2015) (Song and Qiao, 2015) (Chen et al., 2015)
Broken by (Li and Zheng, 2002) (Wang et al., 2019) (Arroyo et al., 2013) (Wen et al., 2021) (Alanazi et al., 2021) (Wen et al., 2019) (Hu et al., 2017)
Scheme (Hu et al., 2017) (Niyat et al., 2017) (Hua and Zhou, 2017) (Pak and Huang, 2017) (Liu et al., 2018) (Shafique and Shahid, 2018) (Sheela et al., 2018)
Broken by (Li et al., 2019a) (Li et al., 2018) (Yu et al., 2021) (Wang et al., 2018) (Ma et al., 2020) (Wen and Yu, 2019) (Zhou et al., 2019)
Scheme (Wu et al., 2018) (Yosefnezhad Irani et al., 2019) (Khan and Masood, 2019) (Pak et al., 2019) (Mondal et al., 2021) (Essaid et al., 2019a)
Broken by (Chen et al., 2020) (Liu et al., 2020) (Fan et al., 2021) (Li et al., 2019b) (Li et al., 2021) (Tes¸eleanu, 2023)
Algorithm 1: Encryption algorithm.
Input: A plaintext P, three secret keys k
1
, k
2
and k
3
, and a secret matrix h
Output: A ciphertext C
1 for i ∈ [0, HW ) do
2 if i = 0 then
3
C
0
T
0
←
a b
c d
·
P
0
k
1,0
+
k
2,0
k
3,0
mod 256
S
1
← T
0
+ P
1
mod 256
4 else
5
C
i
T
i
←
a b
c d
·
S
i
k
1,i
+
k
2,i
k
3,i
mod 256
S
i+1
← T
i
+ P
i+1
mod 256
6 return C
7 SetAlFnt
in Section 3. In Sections 4 and 5 we show how an at-
tacker can recover the secret values in a chosen plain-
text/ciphertext scenario. We conclude in Section 6.
2 PRELIMINARIES
Notations. In this paper, the subset {1, . . . , s − 1} ∈
N is denoted by [1, s). The action of selecting a ran-
dom element x from a sample space X is represented
by x
$
←− X, while x ← y indicates the assignment of
value y to variable x. By H and W we denote an im-
age’s height and width. Hexadecimal numbers will
always contain the prefix 0x.
2.1 Essaid et al. Image Encryption
Scheme
In this section we present Essaid et al.’s encryption
(Algorithm 1) and decryption (Algorithm 2) algo-
rithms as described in (Essaid et al., 2019b). Before
the encryption/decryption process starts, the image is
always converted into a vector of size H · W . At the
end, the resulting vector is translated back into an im-
age of size H ×W. Please note that both the key bytes
k
1,i
, k
2,i
, and k
2,i
, and the matrix h values a, b, c, and
d are generated randomly. Also, a is always invertible
modulo 256.
Algorithm 2: Decryption algorithm.
Input: A ciphertext C, three secret keys k
1
,
k
2
and k
3
, and a secret matrix h
Output: A plaintext P
1 for i ∈ [0, HW ) do
2 if i = 0 then
3
P
0
← a
−1
· (C
0
− b · k
1,0
− k
2,0
) mod 256
tmp ← c · P
0
+ d · k
1,0
+ k
3,0
mod 256
4 else
5
P
i
← a
−1
· (C
i
− b · k
1,i
− k
2,i
) mod 256
P
i
← P
i
−tmp mod 256
tmp ← c · a
−1
· (C
i
− b · k
1,i
− k
2,i
) mod 256
tmp ← temp + d · k
1,i
+ k
3,i
mod 256
6 return P
7 SetAlFnt
3 A NEW LOOK AT ESSAID et al.’s
SCHEME
In this section we provide an equivalent description
of the scheme presented in (Essaid et al., 2019b). We
first start with studying Algorithm 1.
Lemma 3.1. Let C
i
and T
i
be the variables from Al-
gorithm 1. Then we can rewrite them as follows
C
i
≡ a
i
∑
j=0
c
i− j
P
j
+ α
i
mod 256,
T
i
≡ c
i
∑
j=0
c
i− j
P
j
+ β
i
mod 256,
where β
−1
= 0 and
α
i
≡ aβ
i−1
+ bk
1,i
+ k
2,i
mod 256,
β
i
≡ cβ
i−1
+ dk
1,i
+ k
3,i
mod 256.
Proof. We will prove our assertion using induction.
When i = 0 we have that
C
0
≡ aP
0
+ bk
1,0
+ k
2,0
= aP
0
+ α
0
mod 256,
T
0
≡ cP
0
+ dk
1,0
+ k
3,0
= cP
0
+ β
0
mod 256.
We assume that the assertion is true for i and we prove
ICISSP 2024 - 10th International Conference on Information Systems Security and Privacy
746

it for i + 1. Therefore, we have
C
i+1
≡ aS
i+1
+ bk
1,i+1
+ k
2,i+1
≡ a(T
i
+ P
i+1
) + bk
1,i+1
+ k
2,i+1
≡ ac
i
∑
j=0
c
i− j
P
j
+ aP
i+1
+ aβ
i
+ bk
1,i+1
+ k
2,i+1
≡ a
i+1
∑
j=0
c
(i+1)− j
P
j
+ α
i+1
mod 256
and
T
i+1
≡ cS
i+1
+ dk
1,i+1
+ k
3,i+1
≡ c(T
i
+ P
i+1
) + dk
1,i+1
+ k
2,i+1
≡ c
2
i
∑
j=0
c
i− j
P
j
+ cP
i+1
+ cβ
i
+ dk
1,i+1
+ k
3,i+1
≡ c
i+1
∑
j=0
c
(i+1)− j
P
j
+ β
i+1
mod 256,
as desired.
According to Lemma 3.1, in order to encrypt an
image using Essaid et al.’s scheme is enough to know
the secret values a, c and α
i
, for i ∈ [0, HW ). As a
consequence, we can also decrypt using these values.
Corollary 3.1.1. We can recover P
i
using
P
i
≡ a
−1
(C
i
− a
i−1
∑
j=0
c
i− j
P
j
− α
i
) mod 256.
A more efficient method for decrypting is given in
the following lemma.
Corollary 3.1.2. We can recover P
i
using
P
i
≡ a
−1
(C
i
− γ
i
− α
i
) mod 256,
where γ
0
= 0 and
γ
i
≡ acP
i−1
+ cγ
i−1
mod 256.
4 CHOSEN PLAINTEXT ATTACK
A chosen plaintext attack (CPA) is a scenario in which
the attacker A briefly gains access to the encryption
machine O
enc
and is permitted to query it with vari-
ous inputs. In this way, A generates specific plaintexts
that can facilitate his attack and uses O
enc
to obtain
the corresponding ciphertexts. We demonstrate in this
paper that Essaid et al.’s image encryption scheme is
vulnerable to such attacks.
Lets assume that we query O
enc
with two plain-
texts P and P
′
and receive C and C
′
, respectively. Ac-
cording to Lemma 3.1 we have
C
0
≡ aP
0
+ α
0
mod 256,
C
′
0
≡ aP
′
0
+ α
0
mod 256.
Therefore, if gcd(P
0
− P
′
0
, 256) = 1 then we can re-
cover a using
a ≡ (C
0
−C
′
0
)(P
0
− P
′
0
)
−1
mod 256,
and α
0
from
α
0
≡ C
′
0
− aP
′
0
mod 256. (1)
Using Lemma 3.1 we also obtain
C
1
≡ aP
1
+ acP
0
+ α
1
mod 256,
C
′
1
≡ aP
′
1
+ acP
′
0
+ α
1
mod 256,
and since we already computed a we can rewrite the
equations as
C
1
− aP
1
≡ acP
0
+ α
1
mod 256,
C
′
1
− aP
′
1
≡ acP
′
0
+ α
1
mod 256.
Therefore, we can recover c using
c ≡ (C
1
− aP
1
−C
′
1
+ aP
′
1
) · a
−1
(P
0
− P
′
0
)
−1
mod 256,
since gcd(a, 256) = gcd(P
0
− P
′
0
, 256) = 1. Also, α
1
is computed as follows
α
1
≡ C
′
1
− aP
′
1
− acP
′
0
mod 256. (2)
Once a and c are computed, the remaining α
i
are com-
puted from
α
i
≡ C
′
i
− a
i
∑
j=0
c
i− j
P
′
j
mod 256. (3)
In order to optimize the recovery of the secret val-
ues, we choose two plaintexts such that P
0
= 1 and
P
1
= . . . = P
HW −1
= P
′
0
= . . . = P
′
HW −1
= 0. There-
fore, we obtain the following relations
a ≡ C
0
−C
′
0
mod 256,
c ≡ a
−1
(C
1
−C
′
1
) mod 256,
α
i
≡ C
′
i
mod 256, for i ∈ [0, HW ).
We can easily see that the complexity of our attack
is constant and is dominated by computing an inverse
and a multiplication modulo 256. Therefore, it is very
efficient.
5 CHOSEN CIPHERTEXT
ATTACK
In contrast to a chosen plaintext attack, a chosen ci-
phertext attack (CCA) assumes that the attacker A
briefly gains access to the decryption machine O
dec
.
A then generates specific ciphertexts that can assist
his attack and uses O
dec
to obtain the corresponding
Security Analysis of an Image Encryption Scheme Based on a New Secure Variant of Hill Cipher and 1D Chaotic Maps
747

plaintexts. In this scenario, we describe an attack on
Essaid et al.’s cryptosystem.
Lets assume that we query O
dec
with two cipher-
texts C and C
′
and receive P and P
′
, respectively. Us-
ing Corollary 3.1.1 we obtain
P
0
≡ a
−1
(C
0
− α
0
) mod 256,
P
′
0
≡ a
−1
(C
′
0
− α
0
) mod 256.
Therefore, if gcd(C
0
−C
′
0
, 256) = 1 then we can re-
cover a
−1
using
a
−1
≡ (P
0
− P
′
0
)(C
0
−C
′
0
)
−1
mod 256.
Applying Corollary 3.1.1 to the second byte we obtain
P
1
≡ a
−1
(C
1
− acP
0
− α
1
) mod 256,
P
′
1
≡ a
−1
(C
′
1
− acP
′
0
− α
1
) mod 256,
and since we already computed a
−1
we can rewrite
the equations as
a
−1
C
1
− P
1
≡ cP
0
+ a
−1
α
1
mod 256,
a
−1
C
′
1
− P
′
1
≡ cP
′
0
+ a
−1
α
1
mod 256.
Note that since gcd(a, 256) = gcd(C
0
−C
′
0
, 256) = 1,
we obtain that gcd(P
0
− P
′
0
, 256) = 1. Therefore, we
can recover c using
c ≡ (a
−1
C
1
− P
1
− a
−1
C
′
1
+ P
′
1
) · (P
0
− P
′
0
)
−1
mod 256.
Once a and c are computed, the α
i
values are com-
puted using Equations (1) to (3).
In order to optimize the recovery of the secret val-
ues, we choose two ciphertexts such that C
0
= 1 and
C
1
= . . . = C
HW −1
= C
′
0
= . . . = C
′
HW −1
= 0. There-
fore, we obtain the following relations
a ≡ (P
0
− P
′
0
)
−1
mod 256,
c ≡ a(P
′
1
− P
1
) mod 256,
α
i
≡ −a
i
∑
j=0
c
i− j
P
′
j
mod 256, for i ∈ [0, HW ). (4)
Note that Equation (4) can be rewritten as
α
0
≡ −aP
′
0
mod 256,
α
i
≡ −aP
′
i
+ cα
i−1
mod 256, for i ∈ [1, HW ).
The complexity of our attack dominated by two
inverses and 2HW multiplications modulo 256. Us-
ing the fact that an inverse and a multiplication mod-
ulo 256 has constant complexity O(1), we obtain that
our attack has a complexity of O(2HW ). For exam-
ple, if we encrypt 2 megapixels
1
images we obtain a
complexity of O (2
21.87
). In the case of 12 megapix-
els
2
, we obtain O(2
24.51
).
1
W × H = 1600 × 1200
2
W × H = 4000 × 3000
6 CONCLUSIONS
The authors of (Essaid et al., 2019b) presented an im-
age encryption scheme that they claimed to have a se-
curity strength of 279 bits. However, our research
in this paper demonstrated that the actual security
strength of Essaid et al.’s scheme is essentially 0 bits.
To establish our security bound, we designed a cho-
sen plaintext attack that requires only 2 queries to the
encryption oracle. Furthermore, we outline a chosen
ciphertext attack that requires 2 queries to the decryp-
tion oracle and has a complexity of roughly O(2
24
).
REFERENCES
Alanazi, A. S., Munir, N., Khan, M., Asif, M., and Hus-
sain, I. (2021). Cryptanalysis of Novel Image Encryp-
tion Scheme Based on Multiple Chaotic Substitution
Boxes. IEEE Access, 9:93795–93802.
Arroyo, D., Diaz, J., and Rodriguez, F. (2013). Cryptanaly-
sis of a One Round Chaos-Based Substitution Permu-
tation Network. Signal Processing, 93(5):1358–1364.
Chen, J., Chen, L., and Zhou, Y. (2020). Cryptanalysis of a
DNA-Based Image Encryption Scheme. Information
Sciences, 520:130–141.
Chen, J.-x., Zhu, Z.-l., Fu, C., Zhang, L.-b., and Zhang, Y.
(2015). An Efficient Image Encryption Scheme Using
Lookup Table-Based Confusion and Diffusion. Non-
linear Dynamics, 81(3):1151–1166.
Essaid, M., Akharraz, I., Saaidi, A., and Mouhib, A.
(2019a). A New Approach of Image Encryption Based
on Dynamic Substitution and Diffusion Operations. In
SysCoBIoTS 2019, pages 1–6. IEEE.
Essaid, M., Akharraz, I., Saaidi, A., and Mouhib, A.
(2019b). Image Encryption Scheme Based on a
New Secure Variant of Hill Cipher and 1D Chaotic
Maps. Journal of Information Security and Applica-
tions, 47:173–187.
Fan, H., Zhang, C., Lu, H., Li, M., and Liu, Y. (2021).
Cryptanalysis of a New Chaotic Image Encryption
Technique Based on Multiple Discrete Dynamical
Maps. Entropy, 23(12):1581.
Hosny, K. M. (2020). Multimedia Security Using Chaotic
Maps: Principles and Methodologies, volume 884.
Springer.
Hu, G., Xiao, D., Wang, Y., and Li, X. (2017). Cryptanal-
ysis of a Chaotic Image Cipher using Latin Square-
Based Confusion and Diffusion. Nonlinear Dynamics,
88(2):1305–1316.
Hua, Z. and Zhou, Y. (2017). Design of Image Cipher Using
Block-Based Scrambling and Image Filtering. Infor-
mation sciences, 396:97–113.
Huang, X., Sun, T., Li, Y., and Liang, J. (2014). A Color
Image Encryption Algorithm Based on a Fractional-
Order Hyperchaotic System. Entropy, 17(1):28–38.
Khan, M. (2015). A Novel Image Encryption Scheme
Based on Multiple Chaotic S-Boxes. Nonlinear Dy-
namics, 82(1):527–533.
ICISSP 2024 - 10th International Conference on Information Systems Security and Privacy
748

Khan, M. and Masood, F. (2019). A Novel Chaotic Im-
age Encryption Technique Based on Multiple Discrete
Dynamical Maps. Multimedia Tools and Applications,
78(18):26203–26222.
Li, M., Lu, D., Wen, W., Ren, H., and Zhang, Y. (2018).
Cryptanalyzing a Color Image Encryption Scheme
Based on Hybrid Hyper-Chaotic System and Cellular
Automata. IEEE access, 6:47102–47111.
Li, M., Lu, D., Xiang, Y., Zhang, Y., and Ren, H. (2019a).
Cryptanalysis and Improvement in a Chaotic Image
Cipher Using Two-Round Permutation and Diffusion.
Nonlinear Dynamics, 96(1):31–47.
Li, M., Wang, P., Liu, Y., and Fan, H. (2019b). Crypt-
analysis of a Novel Bit-Level Color Image Encryp-
tion Using Improved 1D Chaotic Map. IEEE Access,
7:145798–145806.
Li, M., Wang, P., Yue, Y., and Liu, Y. (2021). Cryptanaly-
sis of a Secure Image Encryption Scheme Based on a
Novel 2D Sine–Cosine Cross-Chaotic Map. Journal
of Real-Time Image Processing, 18(6):2135–2149.
Li, S. and Zheng, X. (2002). Cryptanalysis of a Chaotic
Image Encryption Method. In ISCAS 2002, volume 2,
pages 708–711. IEEE.
Liu, L., Hao, S., Lin, J., Wang, Z., Hu, X., and Miao, S.
(2018). Image Block Encryption Algorithm Based on
Chaotic Maps. IET Signal Processing, 12(1):22–30.
Liu, Y., Qin, Z., Liao, X., and Wu, J. (2020). Cryptanaly-
sis and Enhancement of an Image Encryption Scheme
Based on a 1-D Coupled Sine Map. Nonlinear Dy-
namics, 100(3):2917–2931.
Ma, Y., Li, C., and Ou, B. (2020). Cryptanalysis of an
Image Block Encryption Algorithm Based on Chaotic
Maps. Journal of Information Security and Applica-
tions, 54:102566.
Matoba, O. and Javidi, B. (2004). Secure Holographic
Memory by Double-Random Polarization Encryption.
Applied Optics, 43(14):2915–2919.
Mondal, B., Behera, P. K., and Gangopadhyay, S. (2021). A
Secure Image Encryption Scheme Based on a Novel
2D Sine–Cosine Cross-Chaotic (SC3) Map. Journal
of Real-Time Image Processing, 18(1):1–18.
Muthu, J. S. and Murali, P. (2021). Review of Chaos De-
tection Techniques Performed on Chaotic Maps and
Systems in Image Encryption. SN Computer Science,
2(5):1–24.
Niyat, A. Y., Moattar, M. H., and Torshiz, M. N. (2017).
Color Image Encryption Based on Hybrid Hyper-
Chaotic System and Cellular Automata. Optics and
Lasers in Engineering, 90:225–237.
¨
Ozkaynak, F. (2018). Brief Review on Application of Non-
linear Dynamics in Image Encryption. Nonlinear Dy-
namics, 92(2):305–313.
Pak, C., An, K., Jang, P., Kim, J., and Kim, S. (2019). A
Novel Bit-Level Color Image Encryption Using Im-
proved 1D Chaotic Map. Multimedia Tools and Ap-
plications, 78(9):12027–12042.
Pak, C. and Huang, L. (2017). A New Color Image En-
cryption Using Combination of the 1D Chaotic Map.
Signal Processing, 138:129–137.
Shafique, A. and Shahid, J. (2018). Novel Image Encryption
Cryptosystem Based on Binary Bit Planes Extraction
and Multiple Chaotic Maps. The European Physical
Journal Plus, 133(8):1–16.
Sheela, S., Suresh, K., and Tandur, D. (2018). Image En-
cryption Based on Modified Henon Map Using Hy-
brid Chaotic Shift Transform. Multimedia Tools and
Applications, 77(19):25223–25251.
Song, C. and Qiao, Y. (2015). A Novel Image Encryption
Algorithm Based on DNA Encoding and Spatiotem-
poral Chaos. Entropy, 17(10):6954–6968.
Tes¸eleanu, G. (2023). Security Analysis of a Color Im-
age Encryption Scheme Based on Dynamic Substi-
tution and Diffusion Operations. In ICISSP 2023.
SCITEPRESS.
Wang, H., Xiao, D., Chen, X., and Huang, H. (2018). Crypt-
analysis and Enhancements of Image Encryption Us-
ing Combination of the 1D Chaotic Map. Signal pro-
cessing, 144:444–452.
Wang, L., Wu, Q., and Situ, G. (2019). Chosen-Plaintext
Attack on the Double Random Polarization Encryp-
tion. Optics Express, 27(22):32158–32167.
Wang, X., Teng, L., and Qin, X. (2012). A Novel Colour
Image Encryption Algorithm Based on Chaos. Signal
Processing, 92(4):1101–1108.
Wen, H. and Yu, S. (2019). Cryptanalysis of an Image
Encryption Cryptosystem Based on Binary Bit Planes
Extraction and Multiple Chaotic Maps. The European
Physical Journal Plus, 134(7):1–16.
Wen, H., Yu, S., and L
¨
u, J. (2019). Breaking an Image
Encryption Algorithm Based on DNA Encoding and
Spatiotemporal Chaos. Entropy, 21(3):246.
Wen, H., Zhang, C., Huang, L., Ke, J., and Xiong, D.
(2021). Security Analysis of a Color Image Encryp-
tion Algorithm Using a Fractional-Order Chaos. En-
tropy, 23(2):258.
Wu, J., Liao, X., and Yang, B. (2018). Image Encryption
Using 2D H
´
enon-Sine Map and DNA Approach. Sig-
nal processing, 153:11–23.
Yen, J.-C. and Guo, J.-I. (2000). A New Chaotic Key-Based
Design for Image Encryption and Decryption. In IS-
CAS 2000, volume 4, pages 49–52. IEEE.
Yosefnezhad Irani, B., Ayubi, P., Amani Jabalkandi, F.,
Yousefi Valandar, M., and Jafari Barani, M. (2019).
Digital Image Scrambling Based on a New One-
Dimensional Coupled Sine Map. Nonlinear Dynam-
ics, 97(4):2693–2721.
Yu, F., Gong, X., Li, H., and Wang, S. (2021). Differ-
ential Cryptanalysis of Image Cipher Using Block-
Based Scrambling and Image Filtering. Information
Sciences, 554:145–156.
Zhou, K., Xu, M., Luo, J., Fan, H., and Li, M. (2019).
Cryptanalyzing an Image Encryption Based on a
Modified Henon Map Using Hybrid Chaotic Shift
Transform. Digital Signal Processing, 93:115–127.
Zolfaghari, B. and Koshiba, T. (2022). Chaotic Image
Encryption: State-of-the-Art, Ecosystem, and Future
Roadmap. Applied System Innovation, 5(3):57.
Security Analysis of an Image Encryption Scheme Based on a New Secure Variant of Hill Cipher and 1D Chaotic Maps
749
