
Anonymous Multi-Receiver Certificateless Hybrid Signcryption for
Broadcast Communication
Alia Umrani
∗ a
, Apurva K Vangujar
∗ b
and Paolo Palmieri
c
Department of Computing & IT, University College Cork, Cork, Ireland
Keywords:
mKEM-DEM, Hybrid Signcryption, Certificateless, Multireceiver, Pseudo-Identity, Confidentiality,
Authentication, Anonymity.
Abstract:
Confidentiality, authentication, and anonymity are fundamental security requirements in broadcast communi-
cation achievable by Digital Signature (DS), encryption, and Pseudo-Identity (PID) techniques. Signcryption,
particularly hybrid signcryption, offers both DS and encryption more efficiently than “sign-then-encrypt”, with
lower computational and communication costs. This paper proposes an Anonymous Multi-receiver Certifi-
cateless Hybrid Signcryption (AMCLHS) scheme for secure broadcast communication. AMCLHS combines
public-key cryptography and symmetric key to achieve confidentiality, authentication, and anonymity. We pro-
vide a simple and efficient construction of a multi-recipient Key Encapsulation Mechanism (mKEM) to create
a symmetric session key. This key, with the sender’s private key, is used in Data Encapsulation Mechanism
(DEM) to signcrypt the message, ensuring confidentiality and authentication. The scheme generates identical
ciphertext for multiple recipients while maintaining their anonymity by assigning a PID to each user. Secu-
rity notions are demonstrated for indistinguishability against chosen-ciphertext attack using the elliptic curve
computational diffie-hellman assumption in the random oracle model and existential unforgeability against
chosen message attack under elliptic curve diffie-hellman assumption. The AMCLHS scheme operates in a
multireceiver certificateless environment, preventing the key escrow problem. Comparative analysis shows
that our scheme is computationally efficient, provides optimal communication cost, and simultaneously en-
sures confidentiality, authentication, anonymity, non-repudiation, and forward security.
1 INTRODUCTION
Confidentiality, authentication, and anonymity are the
basic security requirements in broadcast communica-
tion (Peng et al., 2020). The current solution to pro-
vide for these security requirements are encryption
and Digital Signature (DS). However, the traditional
”sign-then-encrypt” approach results in high compu-
tational costs. Signcryption, on the other hand, al-
lows both the encryption and DS operations to be per-
formed simultaneously, providing both the confiden-
tiality and authentication more efficiently. Signcryp-
tion was first proposed by Zhang et al. as a novel
cryptographic primitive (Zheng, 1997). Malone-Lee
proposed the first Identity (ID)-based signcryption
a
https://orcid.org/0000-0003-1885-3629
b
https://orcid.org/0000-0002-8194-4593
c
https://orcid.org/0000-0002-9819-4880
∗
Alia Umrani and Apurva Vangujar are supported by
PhD scholarships funded by the Science Foundation Ireland
Centre under Grant No. SFI 18/CRT/6222
scheme that provides forward security and public ver-
ifiability (Malone-Lee, 2002). However, in ID-based
schemes, the public key generator generates the user’s
private key, leading to the issue of private key es-
crow. To solve the key escrow problem, Al-Riyami
et al. proposed a Certificateless Public Key Cryptog-
raphy (CLPKC) (Al-Riyami and Paterson, 2003). In
CLPKC, the Key Generation Center (KGC) only gen-
erates a partial private key (ppk) of the user. The
user then combines ppk and a secret value to gen-
erate the actual private and public key pair. There-
fore, the KGC does not have knowledge of the user’s
complete private key. Following that, Barbosa and
Farshim proposed the first certificateless signcryption
scheme (Barbosa and Farshim, 2008). The signcryp-
tion methods mentioned above are designed for single
receiver, which are not suitable for broadcast commu-
nication. When sending the same message to multi-
ple recipients, the user encrypts a message for each
individual recipient, increasing computation time and
communication lag. To address this, Selvi et al. pro-
Umrani, A., Vangujar, A. and Palmieri, P.
Anonymous Multi-Receiver Certificateless Hybrid Signcryption for Broadcast Communication.
DOI: 10.5220/0012353400003648
Paper published under CC license (CC BY-NC-ND 4.0)
In Proceedings of the 10th International Conference on Information Systems Security and Privacy (ICISSP 2024), pages 733-744
ISBN: 978-989-758-683-5; ISSN: 2184-4356
Proceedings Copyright © 2024 by SCITEPRESS – Science and Technology Publications, Lda.
733

posed the first multireceiver certificateless signcryp-
tion scheme (Selvi et al., 2008). Generally, the con-
struction of signcryption can be achieved through two
methods: (i) Public key signcryption: With public
key signcryption, both message encryption and sign-
ing take place in a public key setting (Selvi et al.,
2008). (ii) Hybrid signcryption: Hybrid signcryption
provides the advantages of combining symmetric key
encryption with asymmetric key signature while en-
suring integrity, authentication, and non-repudiation
(Selvi et al., 2009). Hybrid signcryption is generally
efficient in resource constrained environments than
pure asymmetric signcryption because, in asymmet-
ric signcryption alone, large messages are sent with
the large public key values. For more reading, we
refer to Dent’s work (Dent, 2005b; Dent, 2005a) on
Hybrid signcryption schemes.
In this paper, we propose a multi-receiver anony-
mous certificateless hybrid signcryption based on
multi-recipient Key Encapsulation Mechanism-Data
Encapsulation Mechanism (mKEM-DEM) for broad-
cast communication. For confidentiality, we prove
Indistinguishability against Chosen-Ciphertext At-
tack (ind-cca2-I) for Type-I adversary, and (ind-
cca2-II) for Type-II adversary using Elliptic Curve
based Computational Diffie-Hellman (ECCDH) as-
sumption. For unforgeability, we prove Existen-
tial Unforgeability against Chosen Message Attack
(euf-cma-I) for Type-I adversary, and (euf-cma-II)
for Type-II adversary, respectively, based on Elliptic
Curve Discrete Logarithm (ECDL) assumption. Ad-
ditionally, to ensure anonymity, each user is assigned
a Pseudo-Identity (PID) and we further demonstrate
the security for non-repudiation and forward secu-
rity. Finally, we compare our scheme with exist-
ing multireceiver certificateless hybrid signcryption
schemes, demonstrating its efficiency in terms of
computation cost, communication cost, and security
requirements. In comparison to existing schemes, our
scheme demonstrates higher efficiency, with the sign-
cryption cost increasing linearly with the number of
designated receivers, while the unsigncryption cost
remains constant. Our scheme simultaneously satisfy
all the security requirements in terms of confidential-
ity, unforgeability, anonymity, non - repudiation, and
forward security.
1.1 Our Contributions
The objective of this paper is to provide an anony-
mous certificateless hybrid signcryption scheme by
utilizing mKEM and DEM. Our main contributions
are as follows:
1. We propose an Anonymous Multireceiver Certifi-
cateless Hybrid Signcryption (AMCLHS) scheme
based on mKEM-DEM. The AMCLHS scheme
uses a combination of PKC and symmetric key to
signcrypt a message in broadcast communication.
2. The AMCLHS scheme achieves anonymity for
each receiver by assigning a PID to each user
(sender and receiver) and enables the sender to
signcrypt an identical message for multiple re-
ceivers while keeping their real identities anony-
mous from each other.
3. The scheme operates in a multireceiver certifi-
cateless environment, preventing the key escrow
problem. We achieve confidentiality by demon-
strating security against ind-cca2-I and ind-cca2-
II and unforgeability by demonstrating euf-cma-
I and euf-cma-II, respectively. The security is
proven using ECCDH and ECDL assumptions un-
der the Random Oracle Model (ROM).
The remainder of the paper is as follows: The related
work is provided in Sec. 2. Sec. 3 describes the
mathematical assumptions and definitions. In Sec. 4,
we introduce the AMCLHS framework and security
model of the scheme in Sec. 5. Sec. 6 introduces the
proposed AMCLHS scheme and in Sec. 7, we pro-
vide the security analysis under the hard assumption.
Sec. 8 provide the performance analysis and compar-
ison of the proposed scheme. Lastly, in Sec. 9, we
conclude the work.
2 RELATED WORK
2.1 Certificateless Signcryption
Signcryption was first introduced by Zheng et al.
in 1997 combining the signature and encryption to
provide authentication and confidentiality more effi-
ciently than sign-then-encrypt (Zheng, 1997). Several
ID-based signcryption schemes have been proposed,
however, the key issue is the presence of a key es-
crow problem. To address this, Barbosa and Farshim
proposed the first certificateless signcryption scheme
that provides both confidentiality and authentication
and is secure under the ROM (Barbosa and Farshim,
2008). Chen et al. and Cui et al. proposed a certifi-
cateless signcryption scheme for the Internet of Med-
ical Things without pairings and the Internet of Vehi-
cles (IoVs), respectively. The schemes provides con-
fidentiality and authentication and proves security un-
der ECDL and Computational Diffie-Hellman (CDH)
assumptions (Chen et al., 2023; Cui et al., 2022).
Similarly, a certificateless signcryption scheme with-
out ROM was proposed by ZHOU et al. that achieves
ICISSP 2024 - 10th International Conference on Information Systems Security and Privacy
734

confidentiality and unforgeability however, does not
provide anonymity (ZHOU, 2018). Kasyoka et al.
proposed a certificateless signcryption for wireless
sensor networks (Kasyoka et al., 2021). Addition-
ally, Cui et al. presented a pairing-free certificate-
less signcryption scheme for the IoVs (Cui et al.,
2022). Li et al. proposed a signcryption scheme
for resource-constrained smart terminals in cyber-
physical power systems (Li et al., 2022). However, all
the aforementioned schemes are designed for single
receivers, which are not suitable for broadcast com-
munication. Yu et al. introduced the first multire-
ceiver signcryption scheme based on ID-based PKC,
enabling message encryption for n designated re-
ceivers (Yu et al., 2007). The security of the scheme
is based on CDH assumption under the ROM. Later
on, several multireceiver certificateless signcryption
schemes were proposed. In 2022, Niu et al. proposed
a privacy-preserving mutual heterogeneous signcryp-
tion scheme based on 5G network slicing, where the
sender is in a public key infrastructure environment,
and the receiver is in a certificateless environment
(Niu et al., 2022a). The proposed scheme is secure
against ind-cca2 and euf-cma under the hardness as-
sumptions of CDH and Discrete Logarithm (DL). In
addition, numerous multireceiver certificateless sign-
cryption schemes have been introduced in edge com-
puting, Internet of Things (IoT), and IoT-enabled mar-
itime transportation systems (Peng et al., 2020; Qiu
et al., 2019; Yang et al., 2022; Yu et al., 2022).
The above schemes based on large and resource-
constrained environment are proven secure in pub-
lic key settings, however, they may become computa-
tionally expensive when dealing with large messages,
compared to hybrid settings. On the other hand, hy-
brid signcryption is generally more efficient than pub-
lic key signcryption alone because it uses the com-
bination of symmetric key and PKC. A message is
encrypted using a symmetric key algorithm, which is
faster and more efficient (Dent, 2005b; Dent, 2005a).
2.2 Certificateless Hybrid Signcryption
Dent et al. proposed the first hybrid signcryption
scheme with insider and outsider security (Dent,
2005a; Dent, 2005b). Following that, Li et al.
proposed the first certificateless hybrid signcryption
scheme (Li et al., 2009). Wu et al. proposed a cer-
tificateless hybrid signcryption scheme for IoT (Wu
et al., 2022). The scheme utilizes PKC to gener-
ate a symmetric key and is used to signcrypt the
message. While the scheme provides confidential-
ity, authentication, forward security, and public ver-
ification under CDH and Decisional Bilinear Diffie-
Hellman (DBDH) assumptions, it incurs high com-
putational cost due to Bilinear Pairing (BP) opera-
tion. Yin et al. proposed a certificateless hybrid sign-
cryption scheme for wireless sensor network (WSN)
(Yin and Liang, 2015). Similarly, Gong et al. pre-
sented a lightweight and secure certificateless hybrid
signcryption scheme for the IoT (Gong et al., 2022).
It ensures data confidentiality, integrity, and authen-
ticity. The scheme utilizes BP for initialization and
key construction and proves security under CDH and
DBDH assumptions. Hongzhen et al. presented cer-
tificateless signcryption scheme for Vehicular Ad hoc
Networks (VANETs) without BP (Hongzhen et al.,
2021). Moreover, Zhang et al. introduced a certifi-
cateless hybrid signcryption scheme suitable for the
IoT (Zhang et al., 2022). The scheme is constructed to
achieve both confidentiality and unforgeability under
DL, CDH, DBDH, and BDH assumptions. In 2017,
Niu et al. proposed a heterogeneous hybrid sign-
cryption for multi-message and multi-receiver (Niu
et al., 2017). The scheme proves security against
ind-cca and euf-cma attacks under the ROM based
on the hardness assumptions of DBDH and variants
of DBDH and Computational BDH. In 2022, Niu et
al. presented a broadcast signcryption scheme based
on certificateless cryptography for WSN (Niu et al.,
2022b). The scheme aims to ensure the confidential-
ity and integrity of the data transmitted, while protect-
ing by the privacy of the receiver’s ID under ECDH
and ECDL assumptions. The scheme uses a trusted
third party to outsource the encryption operation and
assumes that the trusted third party is always avail-
able. However, it may not be realistic in some scenar-
ios, for instance, if the trusted third party is offline,
the scheme may not work properly. Moreover, the
scheme incurs higher computational costs compared
to the AMCLHS scheme.
3 PRELIMINARIES AND
ASSUMPTIONS
1. Elliptic Curve Based Computational
Diffie-Hellman (ECCDH) Assumption. The
security assumption of ECCDH is according to
(Cohen et al., 2005).
Definition 3.1. The ECCDH assumption holds
given (P,xP,yP) ∈ G, where x,y ∈ Z
∗
q
, it is
computationally infeasible for any Probabilis-
tic Polynomial-Time (PPT) algorithm to compute
xyP.
2. Elliptic Curve Discrete Logarithm (ECDL)
Assumption. The security assumption of ECDL
Anonymous Multi-Receiver Certificateless Hybrid Signcryption for Broadcast Communication
735

is adopted from (Cohen et al., 2005).
Definition 3.2. Given P and Q ∈ G, it is hard to
find an x ∈ Z
∗
q
for any PPT algorithm with non-
negligible probability such that Q = xP.
3. The Multi-Recipient Key Encapsulation
Mechanism (mKEM) and Data Encapsulation
Mechanism (DEM). The notion of mKEM was
first proposed by N.P Smart (Smart, 2004) and
has a KEM like construction which takes multiple
receiver’s public keys pk
r
i
where 1 ≤ i ≤ t and
t < n as input and generates a single symmetric
session key K and an encapsulation C of K.
Definition 3.3. The mKEM construction below is
according to the (Smart, 2004):
(a) mKEM. It consists of four algorithms defined
as follows (Setup, KeyGen, mKEM.Encaps,
mKEM.Decaps):
• Setup. On input the security parameter 1
λ
,
the algorithm outputs PP.
• KeyGen. Taking PP as input, the algorithm
outputs (pk,sk) for each user.
• mKEM.Encaps. On input PP and a set of re-
ceiver public keys pk
r
i
where 1 ≤ i ≤ t, this
algorithm outputs a symmetric session key K
and an encapsulation C
1
of K where K is used
in DEM.
• mKEM.Decaps. Taking PP, receiver’s private
key sk
r
i
, and an encapsulation C
1
as input, this
algorithm outputs K. The correctness holds if
K = mKEM.Decaps(PP,sk
r
i
,C
1
).
(b) DEM: It consists of two algorithms
(Enc
K
,Dec
K
) (Niu et al., 2017) defined as
follows:
• Enc
K
. On input (K,m), this algorithm outputs
a ciphertext C
2
.
• Dec
K
. Taking (K, C
2
) as input, this algorithm
outputs m
′
. The correctness of DEM holds if
m
′
= m.
4. KEM-DEM Hybrid Signcryption Scheme.
Definition 3.4. The construction of KEM-
DEM hybrid signcryption scheme is given
by (Dent, 2005a). It consists of four al-
gorithms (Setup,KeyGen,Gen − Enc, Dec − Ver)
defined as follows:
(a) Setup. It takes as input a security parameter 1
λ
and outputs PP.
(b) KeyGen. Taking PP as input, this algorithm
outputs a public and private key pair for sender
(pk
s
,sk
s
) and receiver (pk
r
,sk
r
).
(c) Gen − Enc. In Gen − Enc, the sender runs fol-
lowing algorithms:
• Encaps. On input (PP,sk
s
,pk
r
,m), it outputs
a symmetric session key K and an encapsula-
tion C
1
.
• Enc
K
. It takes K as input and outputs C
2
. The
receiver outputs ciphertext CT = (C
1
,C
2
).
(d) Dec − Ver. In this phase, the receiver runs fol-
lowing algorithms:
• Decaps. On input (sk
r
,C
1
), it outputs K. If
K =⊥, the sender stops. Otherwise, the re-
ceiver runs next algorithmic step.
• Dec
K
. On input (C
2
,K), outputs m. If m =⊥,
the receiver stops. Else, it runs next step.
• Ver. Taking (pk
s
,m,C
1
) as input, it outputs
either valid or not. If valid, outputs m, else ⊥.
4 AMCLHS FRAMEWORK
4.1 Framework
The framework of the AMCLHS scheme
consists of four entities: KGC, a Registra-
tion Authority (RA), and n users such as
n = (PID
s
,{PID
1
,... ,PID
r
i
,... ,PID
r
t
}). As-
sume, a sender with PID
s
sends an arbitrary length
message m to t designated receivers with PID
r
i
where
1 ≤ i ≤ t. The role of each entity is defined below:
• KGC. The KGC is a trusted authority that is re-
sponsible for generating public parameters (PP),
master secret key (msk) of KGC, master public
key (mpk) of KGC, and partial private key (ppk)
for each user taking part in communication.
• RA. The RA is a semi-trusted authority that gen-
erates its private key sk
RA
and public key pk
RA
.
RA is also responsible for user registration, ID
verification, and PID assigning.
• Sender. The sender with PID
s
encrypts a m us-
ing the set of designated receiver’s public key pk
r
i
,
signs with its private key sk
s
and sends the sign-
crypted ciphertext CT to t designated receivers.
• Receiver. The designated receiver with PID
r
i
and
sk
r
i
, decrypt the CT, and verify the signature using
sender’s public key pk
s
.
4.2 Definition of AMCLHS
The AMCLHS scheme represents a hybrid approach,
leveraging both mKEM and DEM components. Be-
fore signcrypting the message, RA verifies user’s real
identity ID
R
, registers, and assigns a PID to each cor-
responding user. For signcryption, this framework
firstly utilizes mKEM that takes a set of receiver’s
ICISSP 2024 - 10th International Conference on Information Systems Security and Privacy
736

public keys as input, and generates a symmetric ses-
sion key K and an encapsulation C
1
of that key. The
mKEM also takes a sender’s private key to generate
the signature S which is encapsulated in C
1
and veri-
fies in the unsigncryption phase as given in Def. 4.1.
Following this, the DEM and session key K are jointly
used to symmetrically encrypt m, producing a cipher-
text C
2
. This ciphertext is then represented as a sign-
crypted ciphertext pair CT = (C
1
,C
2
). For decryp-
tion, the process starts with the decapsulation of C
1
using mKEM and the receiver’s private key to retrieve
K. After this, the message m is decrypted from C
2
us-
ing K. Once the m is decrypted, the receiver verifies
the signature S using Ver algorithm by taking sender’s
public key and C
1
as input. Hence, the AMCLHS
scheme introduces an effective and secure mechanism
for data signcryption and unsigncryption, employing
both symmetric and asymmetric key strategies in a
unique hybrid methodology.
Definition 4.1. In the AMCLHS scheme, the sender
with PID
s
sends an arbitrary length m to t designated
receivers denoted with PID
r
i
where 1 ≤ i ≤ t. The
AMCLHS scheme follows the Defs. 3.3 and 3.4. The
proposed scheme consists of eight polynomial time al-
gorithms as follows:
1. Setup. On input the security parameter 1
λ
, the
KGC generates (PP, msk,mpk). Next, RA gen-
erates sk
RA
and pk
RA
.
2. Pseudo-Identity. Takes Real Identity (ID
R
) and
pk
RA
as input and outputs a PID.
3. Partial Private Key. For each PID, the KGC
takes (mpk,msk) as input, it outputs the partial
private key (ppk).
4. Secret Value. On input the PID, each user gener-
ates a secret value (sv).
5. Private Key. Taking (ppk,sv) as input, each user
generates the sk.
6. Public Key. On input the sv, each user outputs the
pk.
7. Signcryption. To signcrypt the m and generate the
CT, the sender runs this algorithm in two phases.
In Phase 1, the sender runs mKEM.Encaps and in
Phase 2, the sender runs Enc
K
according to the
Def. 3.3. The phases are defined as follows:
• Phase 1 (mKEM.Encaps) Taking PP, sk
s
, a
plaintext m and a set pk
r
i
for 1 ≤ i ≤ t, this al-
gorithm outputs C
1
and K
• Phase 2 (Enc
K
) On input (K,m), this algo-
rithm outputs C
2
and sets signcrypted cipher-
text CT = (C
1
,C
2
).
8. Unsigncryption. To unsigncrypt the CT and re-
trieve m, the receiver runs this algorithm in three
phases. Phase 1 consists of mKEM.Decaps, Phase
2 consists of Dec
K
, and Phase 3 consists of Ver al-
gorithm according to the Def. 3.3.
• Phase 1 (mKEM.Decaps). Taking (sk
r
i
,C
1
) as
input, this algorithm outputs K.
• Phase 2 (Dec
K
). On input (K,C
2
), this algo-
rithm outputs m
′
. If m
′
̸= m, the receiver rejects
the m. If m
′
= m, the receiver verifies the sig-
nature in Phase 3.
• Phase 3 (Ver). Taking (m
′
,C
1
,pk
s
) as input,
this algorithm verifies the signature S. If it is
valid, accept the m, or else return ⊥.
5 SECURITY MODEL
We define the security Game-I for ind-cca2-I and ind-
cca2-II in Sec. 5.1, to evaluate the security against
Type-I adversary (A
I
) and Type-II adversary (A
II
),
respectively. Moreover, in Sec. 5.2, we introduce
the security Game-II for euf-cma-I and euf-cma-II to
evaluate the security against A
I
and A
II
and are de-
fined as follows:
1. A
I
. A
I
is an honest-but-curious user who cannot
access msk but can replace the pk of any ID with
the value of his/her own choice. A
I
is not allowed
to ask a ppk query q
ppk
for any of the target ID.
2. A
II
. A
II
, also known as malicious KGC, cannot
make public key replace query q
pr
for the target
ID. A
II
is not allowed to make sv extract queries
q
sv
. If the q
pr
has been done for the target ID, then
the q
sv
is not allowed for the same ID.
5.1 Game-I
The Game-I is interaction between the Challenger C
and A in three phases. In each phase, the A asks
a polynomially bounded number of hash and public
and private key queries. Finally, A provides a target
plaintext pair (m
0
,m
1
) to C . C picks β ∈ {0,1}
∗
ran-
domly and responds with a challenge CT
∗
. A returns
β
′
∈ {0,1}
∗
and wins the Game-I if β = β
′
.
Definition 5.1. The ind-cca2 requires that there exists
no PPT Adversary A which could distinguish cipher-
texts. The advantage of A is defined as the probability
that A wins the game.
1. Phase-1. The A asks polynomially bounded num-
ber of hash queries q
H
l
where l = {1,2,3}. The C
keeps a list L
l
of q
H
l
to record the responses.
Anonymous Multi-Receiver Certificateless Hybrid Signcryption for Broadcast Communication
737

• Setup. C generates (PP,msk,mpk, sk
RA
,pk
RA
)
and passes to A . Then A selects t target PID
r
i
where 1 ≤ i ≤ t.
2. Phase-2. The A proceeds to make a series of
queries, subject to the restrictions defined in Sec.
5. The queries include public key retrieve query
q
pk
, partial private key query q
ppk
, secret value ex-
tract query q
sv
, public key replace query q
pr
, sign-
cryption query q
sc
, and unsigncryption query q
usc
.
An initially empty list L
pk
is maintained by the C
to store public and secret information. The C re-
sponds to each query as follows:
• q
pk
. Upon receiving such query for PID, the C
searches L
pk
for pk. If it does not exist, C runs
the secret value algorithm to generate a sv for
PID, and performs the public key algorithm to
return the pk to A.
• q
ppk
. Given PID, the C checks if PID = PID
∗
.
If it does, the C aborts. Otherwise, it fetches
the ppk from L
pk
. If it does not exist, C runs a
partial private key algorithm to return ppk and
updates L
pk
.
• q
sv
. Upon q
sv
, the C checks L
pk
for sv. If it
does not exist, C runs a secret value algorithm
and returns sv to A.
• q
pr
. Given PID as input, the C replaces pk with
pk
′
and updates L
pk
.
• q
sc
. On input (m, PID
s
,PID
r
i
), the C checks if
PID
r
i
= PID
∗
. If it is not, C performs normal
signcryption operation by taking values from
L
pk
. Otherwise, it performs the signcryption al-
gorithm to generate CT.
• q
usc
. Upon receiving (CT, PID
s
,PID
r
i
) as in-
put, the C checks if PID
r
i
= PID
∗
. If it is not,
C performs normal unsigncryption operation.
Otherwise, C performs the unsigncryption al-
gorithm to answer m.
3. Challenge. The A outputs a target plaintext
(m
0
,m
1
). The C picks β ∈ {0,1}
∗
at random, sets
challenge CT
∗
, and sends CT
∗
to A.
4. Phase-3. The A can make further queries except
that the CT
∗
is not allowed to appear in the q
usc
.
5. Guess. Finally, A responds with its guess β
′
∈
{0,1}
∗
. If β = β
′
, A wins the Game-I. The advan-
tage of A
I
is defined as:
Adv
IND−CCA2
A
I
=| Pr
β = β
′
− 1/2 | (1)
The advantage of A
II
is defined as:
Adv
IND−CCA2
A
II
=| Pr
β = β
′
− 1/2 | (2)
5.2 Game-II
Game-II consists of two phases. In each phase, the A
asks a polynomially bounded number of hash, pk and
sk queries. In the end, A outputs the forged cipher-
text. A wins if unsigncryption does not return ⊥.
Definition 5.2. An AMCLHS scheme is euf-cma se-
cure if every PPT A has a negligible advantage in
winning the Game-II.
1. Phase-1. Phase-1 remains same as in Def. 5.1
except that A selects a target identity as PID
∗
s
2. Phase-2. The A asks a number of queries with the
restrictions defined in Sec. 5. The queries include
q
pk
, q
ppk
, q
pr
, q
sv
, q
sc
, and q
usc
and are defined
in Phase-2 in Def. 5.1. C maintains an initially
empty list L
pk
to store the pk and sk information.
3. Forgery. A outputs the forged CT under a tar-
geted PID
∗
s
. A wins if unsigncryption does not
return ⊥.
6 THE PROPOSED AMCLHS
SCHEME
In this section, we focus on the construction of the
proposed AMCLHS scheme, built upon the mKEM-
DEM framework, according to the Def. 4.1. The
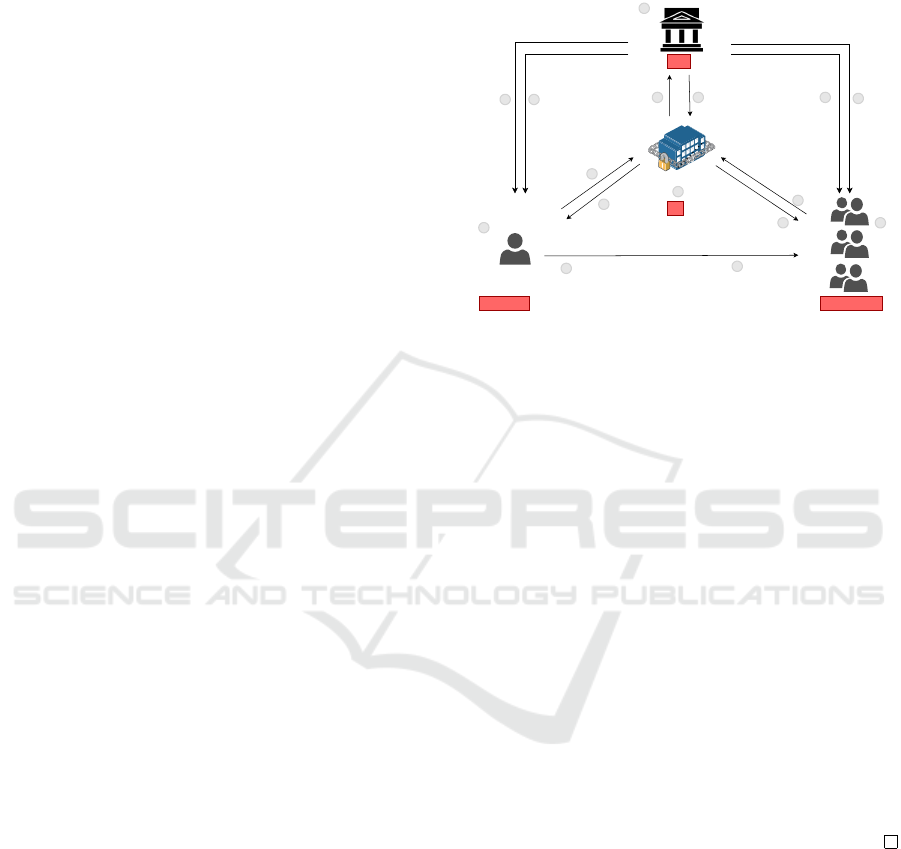
structure of the scheme is shown in Fig. 1.
1. Setup. The KGC initializes the system by tak-
ing the security parameter 1
λ
as input. It chooses
a group G of large prime order q, derived from
an elliptic curve E over a finite field F
q
. The
KGC selects a generator point P ∈ G and gener-
ates four hash functions. The first hash function
is H
0
: {0, 1}
ℓ
−→ G, where ℓ is a positive inte-
ger. The second is H
1
: {0,1}
∗
× G −→ G. The
third hash function is H
2
: G −→ {0, 1}
k
, where k
denotes the plaintext box length. The fourth is
H
3
: {0,1}
∗
× G × G × G −→ Z
∗
q
. The KGC gen-
erates PP = {G, E, P,q,H
0
,H
1
,H
2
,H
3
}, randomly
selects x
0
∈ Z
∗
q
as the master secret key msk, and
calculates the master public key mpk = x
0
P. It
then publish PP and mpk, while keeping msk se-
cret. Subsequently, the RA selects v ∈ Z
∗
q
at ran-
dom as its secret key sk
RA
and calculates its pub-
lic key pk
RA
= vP. The RA publicizes pk
RA
and
keeps sk
RA
as a secret.
2. Pseudo-Identity. This algorithm is run by each
user and RA as follows:
• User. Each user chooses a random ID
R
∈ {0,1}
ℓ
and computes R = αP where α ∈ Z
∗
q
. Tak-
ICISSP 2024 - 10th International Conference on Information Systems Security and Privacy
738
ing (ID
R
,α) as input, it computes PID = ID
R
⊕
H
0
(αpk
RA
) and sends (PID
I
,R) to RA.
• RA. On input (PID,R), RA verifies ID
R
=
PID ⊕ H
0
(Rv). If it holds, RA accepts the reg-
istration request, confirms and assigns PID =
ID
R
⊕ H
0
(αpk
RA
) to each corresponding user
ID. Else, RA discards the PID and cancels the
registration request.
3. Partial Private Key. Taking (PID,mpk,msk) as
input, the KGC computes Q
PID
= H
1
(PID∥mpk)
as a public component. Taking Q
PID
, the KGC
computes ppk as d = x
0
Q
PID
.
4. Secret Value. Each user with PID chooses a ran-
dom x ∈ Z
∗
q
randomly as a sv.
5. Private Key. On input (d,x), each user with PID
sets sk = (d,x).
6. Public Key. Taking x as input, each user with PID
computes pk = xP.
7. Signcryption. The sender with PID
s
and sk
s
runs
following phases to signcrypt a m and sends CT
to receivers with PID
r
i
and pk
r
i
1 ≤ i ≤ t:
• Phase 1 (mKEM-Encaps).
(a) Randomly chooses r ∈ Z
∗
q
and computes U =
rP.
(b) Taking pk
r
i
and Q
PID
r
i
as input, computes
Z
1
i
= d
s
Q
PID
r
i
and Z
2
i
= x
s
pk
r
i
.
(c) Computes ψ
i
= (Z
1
i
Z
2
i
) and K = H
2
(ψ
i
).
(d) Computes a hash f
i
= H
3
(m,ψ
i
,pk
s
,pk
r
i
) and
Signature S
i
= r
−1
( f
i
∥wd
s
x
s
) where w =
x
U
mod q which is the x-coordinate of U.
(e) Sets C
1
i
= ( f
i
,S
i
) and outputs (C
1
i
,K).
• Phase 2 (Enc
K
).
(a) Computes C
2
i
= Enc
K
(m). Sets CT
i
=
(C
1
i
,C
2
i
) and sends to t designated receivers.
8. Unsigncryption. Each designated receiver with
PID
r
i
takes (sk
r
i
,pk
s
) as input for i
th
receiver and
runs the following phases to unsigncrypt the CT
i
and generate m:
• Phase 1 (mKEM-Decaps).
(a) Taking (x
r
i
,d
r
i
) as input, computes Z
′
1
i
=
d
r
i
Q
PID
s
and Z
′
2
i
= pk
s
x
r
i
.
(b) Computes ψ
′
i
= (Z
′
1
i
Z
′
2
i
) and K = H
2
(ψ
′
i
). If
K =⊥, the receiver aborts else, decrypts m as
follows:
• Phase 2 (Dec
K
).
(a) Calculates m
′
= Dec
K
(C
2
i
). If m
′
= m, verifies
the S
i
else rejects.
• Phase 3 (Ver).
(a) Inputs (C
1
i
,pk
s
), outputs f
′
i
=
H
3
(m
′
,ψ
′
i
,pk
s
,pk
r
i
).
(b) If f
′
i
= f
i
, verifies S
i
by checking if U = rP
and w
′
= x
U
mod q. If w
′
= w, the receiver
will accept the signcrypted m else returns ⊥
and aborts.
PP, msk, mpk
sk
RA
, pk
RA
PP
ID
R
PID
s
PID
r1
, . . .,PID
rt
d
r1,
. . . ,d
rt
sk
s,
pk
s
RA
PP
PP
ID
R1
, . . . , ID
Rt
sk
r1,
pk
r1
sk
ri,
pk
ri
sk
rt,
pk
rt
d
s
pk
RA
CT = C
1,
C
2
If K is valid,
decrypts m and verifies S
i
1
1 2
2
2
3
3
4
4
5
5
6
6
7
8
KGC
SENDER RECEIVERS
1
Figure 1: Our Proposed AMCLHS Scheme.
7 SECURITY ANALYSIS
The security analysis of the proposed AMCLHS
scheme is based on the security model defined in Sec.
5. The message confidentiality is based on Theorems
7.1 and 7.2 which demonstrates that the scheme
is secure against ind-cca2 A
I
and A
II
in Def. 5.1.
Similarly, unforgeability is based on Theorems 7.3
and 7.4 and follows that the scheme is secure against
euf-cma A
I
and A
II
in Def. 5.2.
Confidentiality
Theorem 7.1. Suppose that the ind-cca2-I has a non-
negligible advantage ε in winning the game then,
there is C that can solve the ECCDH with the non-
negligible advantage ε
′
.
Proof. Given a random instance (P,xP,yP) ∈ G of the
ECCDH assumption, the C has to compute xyP as
Def. 3.1 by interacting with the A
I
as follows:
1. Phase-1. A polynomially bounded number of
queries q are made by an A
I
. The C keeps a list L
l
of q
H
l
to record the responses.
• Setup. The C runs this algorithm to generate
PP = {G,E,P,q,H
0
,H
1
,H
2
, H
3
}. The C sets
new value for the mpk = θP and sends PP and
mpk to the A
I
. The A
I
selects t target identities
denoted by PID
∗
i
where 1 ≤ i ≤ t.
• H
1
-Query. Upon H
1
query, C determines if the
tuple (Q
PID
i
,mpk,PID
i
) exists in L
1
or not. If
it already exists, C returns Q
PID
i
to A
I
. Else,
if PID
i
̸= PID
∗
i
, C sets Q
PID
i
= H
1
(PID
i
∥mpk).
Anonymous Multi-Receiver Certificateless Hybrid Signcryption for Broadcast Communication
739

If PID
i
= PID
∗
i
, C chooses γ ∈ Z
∗
q
, computes
Q
PID
i
= γP, adds in L
1
and sends Q
PID
i
to A
I
.
• H
2
,H
3
-Query. Upon H
2
and H
3
queries,
the C determines if the tuple (K,ψ
i
,Z
1
i
,Z
2
i
),
(m,ψ
i
, f
i
) exists in L
2
and L
3
. If it does, C
returns K and f
i
to A
II
. Else, the C chooses
K ∈ {0, 1}
k
and f
i
∈ Z
∗
q
randomly, updates both
tuples. The C sends ψ
i
and f
i
to A
I
.
2. Phase-2. The A
I
asks queries including q
pk
, q
ppk
,
q
pr
, q
sv
, and q
usc
. The C maintains an initially
empty list L
pk
to store the public and secret infor-
mation. The C responds to the queries as follows:
• q
pk
. Upon pk
i
query for PID
i
, C checks if pk
i
exists in L
pk
. If it exists, C returns pk
i
to A
I
.
Otherwise, C chooses x
i
∈ Z
∗
q
and computes
pk
i
= x
i
P, adds the tuple (PID
i
,−,pk
i
,x
i
) in L
pk
and returns pk
i
to A
I
.
• q
ppk
. Upon q
ppk
, if PID
i
= PID
∗
i
, the C aborts.
Otherwise, if it exists in L
pk
, C sends d
i
to A
I
,
if it does not, C randomly chooses Q
PID
i
= γP
from L
1
and return d
i
= mpkQ
PID
i
to A
I
. The C
then updates the tuple (PID
i
,d
i
,pk
i
,x
i
) in L
pk
.
• q
sv
. Upon receiving q
sv
, C checks if it exists
in L
pk
, if it does, C sends x
i
to A
I
. If not, C
performs the q
pk
and return x
i
to A
I
.
• q
pr
. Upon q
pr
, C replaces the pk
i
with pk
′
i
for
PID
i
and updates the tuple (PID
i
,d
i
,pk
′
i
,−).
• q
sc
. Upon receiving the query with PID
s
, PID
r
i
and m, the C checks if PID
r
i
= PID
∗
i
. If not, the
C performs the normal signcryption operation
by taking values from L
pk
. Otherwise, the C
performs the signcryption as follows:
– If pk
i
is replaced, A
I
provides another value.
– Chooses r ∈ Z
∗
q
and computes U = rP.
– Gets Q
PID
r
i
from L
1
and computes Z
1
i
=
d
s
Q
PID
r
i
, Z
2
i
= x
s
pk
r
i
, ψ
i
= (Z
1
i
Z
2
i
), K =
H
2
(ψ
i
), and updates L
2
.
– Computes f
i
= H
3
(m,ψ
i
,pk
s
,pk
r
i
) and up-
dates L
3
.
– Computes S
i
, C
1
i
= ( f
i
,S
i
), C
2
i
= Enc
K
(m)
and returns CT
i
= (C
1
i
,C
2
i
) to A
I
.
• q
usc
. Upon q
usc
with PID
s
, PID
r
i
and a CT, the
C checks whether PID
r
i
= PID
∗
i
. If not, the C
performs the normal unsigncryption operation.
Otherwise, the C unsigncrypts m as follows:
– If pk
i
is replaced, A
I
provides another value.
– Searches the lists L
2
and L
3
for (K,ψ
′
i
,Z
′
1
i
,Z
′
2
i
)
and H
3
(m,ψ
′
i
, f
′
i
).
– If the record does not exist, C returns ”fail-
ure”. If it exists, the C computes K ̸=⊥ and
m
′
= Dec
K
(C
2
i
).
– Checks if f
′
i
= f
i
, if it holds then checks if U =
rP and w
′
= x
U
mod q holds or not. If yes, the
C answers m else, returns ⊥.
3. Challenge. The A
I
chooses equal length plaintext
message pair (m
0
,m
1
) and sends the target plain-
text to the C . The A
I
takes a sender PID
s
and a
target PID
r
i
. Moreover, the A
I
can not ask for the
sk of the target PID
r
i
. If PID
r
i
̸= PID
∗
i
, the C re-
turns ⊥. Otherwise, it chooses β ∈ {0,1}
∗
and
performs the following steps to generate a CT
∗
i
:
• Chooses r
∗
∈ Z
∗
q
and computes U
∗
= r
∗
P
• Computes Z
∗
1
i
= d
s
Q
PID
r
i
, Z
∗
2
i
= x
s
pk
r
i
, and
ψ
∗
i
= (Z
∗
1
i
Z
∗
2
i
). Computes K
∗
= H
2
(ψ
∗
i
).
• f
∗
i
= H
3
(m,ψ
∗
i
,pk
s
,pk
r
i
). Computes S
∗
i
=
r
∗−1
( f
∗
i
∥wd
s
x
s
) and C
∗
1
i
= ( f
∗
i
,S
∗
i
).
• C
∗
2
i
= Enc
K
∗
(m) and computes CT
∗
i
=
(C
∗
1
i
,C
∗
2
i
).
4. Phase-3. A
I
may issue further polynomially
bounded queries as in Phase-1, however, A
I
can-
not send the q
ppk
of the target PID
r
i
, or the unsign-
cryption query for CT
∗
i
.
5. Guess. The A
I
will respond with the guess bit
β ∈ {0,1}
∗
. A
I
wins the game if β
′
= β. The C
will win the game by evaluating
θZ
1
i
−d
i
r
(d
s
−U)
= θγP
using mpk = θP, Q
PID
i
= γP which is the solution
to the ECCDH assumption.
Next, we evaluate the advantage of C winning the
Game-I (ind-cca2-I) by calculating the probability of
aborting the game during the following events:
1. In q
ppk
, the game aborts for PID
i
= PID
∗
i
. The
probability is Pr(E
q
ppk
) = 1/q
ppk
.
2. In q
usc
, the game aborts due to invalid m. The
probability is Pr(E
q
usc
) = q
usc
/2
k
.
3. In the challenge phase, C aborts if the adversary
queries against the identity PID
r
i
̸= PID
∗
i
. The
probability is Pr(E
q
H
1
) = (1 − 1/qH
1
).
Moreover, the C fetches L
1
to retrieve Q
PID
i
and L
2
to
retrieve Z
1
i
and evaluates
θZ
1
i
−d
i
r
(d
s
−U)
= θγP with proba-
bility (1/q
H
1
+ 1/q
H
2
). Therefore, the probability of
the C winning the game with advantage ε
′
is:
ε
′
≥ ε
1
qH
1
+
1
qH
2
1
qH
1
1 −
1
q
ppk
1 −
q
usc
2
k
(3)
Theorem 7.2. Suppose that the ind-cca2-II has a
non-negligible advantage ε in winning the game then,
there is a C that can solve the ECCDH assumption
with the non-negligible advantage ε
′
.
ICISSP 2024 - 10th International Conference on Information Systems Security and Privacy
740

Proof. Given a random instance (P,xP,yP) ∈ G of the
ECCDH assumption, the C has to compute xyP as
Def. 3.1 by interacting with A
II
as follows:
1. Phase-1. A polynomially bounded number of
queries q are made by an A
II
.
• Setup. The C generates PP and mpk as in The-
orem 7.1 and sends PP and mpk to the A
II
.
• H
1
-Query. The response of H
1
query to A
II
is
same as in Theorem 7.1.
• H
2
,H
3
-Query. This query remains the same as
in Theorem 7.1 and the C sends ψ
i
and f
i
to A
II
.
2. Phase-2. A
II
asks a number of queries including
q
pk
, q
sv
. The C responds as follows:
• q
pk
. Upon pk
i
for PID
i
, the C checks if pk
i
ex-
ists in the L
pk
as (PID
i
,d
i
,pk
i
,x
i
). If it exists, C
returns pk
i
to C . Otherwise, C chooses x
i
∈ Z
∗
q
,
pk
i
= x
i
P, adds the tuple (PID
i
,−,pk
i
,x
i
) in L
pk
and returns pk
i
to A
II
.
• q
sv
. Upon q
sv
, C checks if PID
i
= PID
∗
i
. If it
holds, the C aborts because, in this case, the
PID
i
is a target ID. Otherwise, it checks if x
i
already exists in the L
pk
. If it exists, the C re-
turns x
i
to A
II
. Otherwise, C runs q
pk
, computes
pk
i
= x
i
P, adds the tuple (PID
i
,d
i
,pk
i
,x
i
) in L
pk
and returns x
i
to A
II
.
• q
sc
. The q
sc
query from A
II
and the response
from C will be similar to the Theorem 7.1.
• q
usc
. The q
usc
query from A
II
and the response
from C will be same as in Theorem 7.1.
3. Challenge. The A
II
chooses target plaintext
m
0
,m
1
and sends to the C . A
II
takes a PID
s
and a
target PID
r
i
. Moreover, the A
II
can not ask for the
sk of the receiver PID
r
i
. If PID
r
i
̸= PID
∗
i
, the C
returns ⊥. Otherwise, it chooses β ∈ {0,1}
∗
and
performs the following steps to generate a chal-
lenge CT
∗
:
• Chooses r
∗
∈ Z
∗
q
and computes U
∗
= r
∗
P.
• Computes Z
1
i
= d
s
Q
PID
r
i
, Z
2
i
= x
s
pk
r
i
, and
ψ
∗
i
= (Z
∗
1
i
Z
∗
2
i
). Computes K
∗
= H
2
(ψ
∗
i
).
• Computes f
∗
i
= H
3
(m,ψ
∗
i
,pk
s
,pk
r
i
). Computes
S
∗
i
= r
∗−1
( f
∗
i
∥wd
s
x
s
) and C
∗
1
i
= ( f
∗
i
,S
∗
i
).
• C
∗
2
i
= Enc
∗
K
(m) and CT
∗
i
= (C
∗
1
i
,C
∗
2
i
).
4. Phase-3. The A
II
may issue further queries as in
Phase-1 however, A
II
cannot send the q
sv
for the
target PID
∗
r
i
and the q
uns
for CT
∗
i
.
5. Guess. The A
II
will respond with the guess bit
β ∈ {0,1}
∗
. The adversary wins the game if
β
′
= β. The C will win the game by obtaining
θγP, which is the solution to the ECCDH assump-
tion. The C obtains it by evaluating
θZ
1
i
−d
i
r
(d
s
−U)
= θγP
since mpk = θP, Q
PID
i
= γP.
Next, we will analyse the advantage of the C in win-
ning the game. The C advantage is based on the oc-
currence of the events in which the game aborts. The
C aborts under the following events:
• The q
sv
where the game aborts for PID
i
= PID
∗
i
.
The probability is Pr(E
q
sv
) = 1/q
sv
.
• The q
usc
where the game aborts due to invalid m.
The probability is Pr(E
q
usc
) = q
usc
/2
k
.
• In the challenge phase, A
II
queries
for PID
∗
r
i
̸= PID
∗
i
. The probability is
Pr(E
q
H
1
) = (1 − 1/qH
1
).
Moreover, the C fetches L
1
to retrieve Q
PID
i
and
L
2
to retrieve Z
1
i
and evaluates θγP with probability
(1/q
H
1
+ 1/q
H
2
). Therefore, the probability of the C
winning the game with advantage ε
′
is:
ε
′
≥ ε
1
qH
1
+
1
qH
2
1
qH
1
1 −
1
q
sv
1 −
q
usc
2
k
(4)
Unforgeability
Theorem 7.3. Suppose that the euf-cma-I adversary
A
I
has a non-negligible advantage ε in winning the
game then, there is C that can solve the ECDL with
the non-negligible advantage ε
′
.
Proof. Given a generator point P ∈ G and a new gen-
erator Q = φP in the same group, the C has to find φ
by interacting with A
I
.
1. Phase-1. A
I
makes same queries as in the Phase-1
of Theorem 7.1.
• Setup. The C runs setup algorithm to generate
PP = {G,E,P,q,H
0
,H
1
,H
2
, H
3
}. The C sets
mpk = θP and sends PP and mpk to the A
I
.
The A
I
selects a target identity as PID
∗
s
.
2. Phase-2. The queries and responses are the same
as in Phase-2 of Theorem 7.1 except the response
to q
ppk
is as follows:
• q
ppk
. Upon q
ppk
, if PID = PID
∗
s
, the C aborts.
Otherwise, if it exists in L
pk
, the C sends d
i
to
A
I
, if it does not, the C randomly chooses φ ∈
Z
∗
q
and computes d
i
= φQ
PID
i
. The C returns
d
i
= φQ
PID
i
to A
I
and updates L
pk
.
3. Forgery. Taking the targets PID
∗
s
and PID
r
i
, A
I
outputs a forged CT
∗
i
= (C
∗
1
i
,C
∗
2
i
) on m
∗
where
C
∗
1
i
= ( f
∗
i
,S
∗
i
) and C
∗
2
i
= Enc
∗
K
(m) which is the
valid signcrypted ciphertext and is not the result
of signcryption oracle.
Anonymous Multi-Receiver Certificateless Hybrid Signcryption for Broadcast Communication
741

• Case-1 (PID ̸= PID
∗
s
): The C returns ⊥.
• Case-2 (PID = PID
∗
s
): The C extracts the L
pk
for the record (PID
∗
i
,d
∗
i
,pk
∗
i
,x
∗
i
) and L
3
for the
record (m
∗
,ψ
∗
i
, f
∗
i
).
According to Forking Lemma, C replays the
A
I
with the same random tape but distinct at-
tributes from H
1
and H
3
. It implies that, h
∗
1
=
H
1
(mpk,PID
∗
i
) and h
′∗
1
= H
1
(mpk,PID
∗
i
), and
h
∗
1
̸= h
′∗
1
i.e. Q
∗
PID
s
̸= Q
′∗
PID
s
. Similarly, h
∗
3
=
H
3
(m
∗
,ψ
∗
i
, pk
∗
s
,pk
∗
r
i
), h
′∗
3
= H
3
(m
∗
,ψ
∗
i
,pk
∗
s
, pk
∗
r
i
)
and h
∗
3
̸= h
′∗
3
i.e. f
∗
i
̸= f
′∗
i
. Finally, the A
I
out-
puts another forged CT
′∗
i
= (C
∗
1
i
,C
∗
2
i
) on the same
m
∗
where C
∗
1
i
= ( f
′∗
i
,S
′∗
i
) and C
∗
2
i
= Enc
∗
K
(m). Fi-
nally, C will have two valid signatures:
S
∗
i
= r
∗−1
( f
∗
i
∥wd
∗
s
x
s
) (5)
S
′∗
i
= r
′∗−1
( f
′∗
i
∥wd
′∗
s
x
s
) (6)
where r
∗
= r
′∗
and d
∗
s
= d
′∗
s
. From the Equations
8 and 9 above, C can extract φ as follows:
φ = r
∗−1
( f
′∗
i
− f
∗
i
) + (S
∗
i
−
S
′∗
i
)(r
∗−1
(wx
s
(Q
∗
PID
s
− Q
′∗
PID
s
))
−1
Given that, the C solves the ECDL assumption
Q = φP with the advantage ε
′
:
ε
′
≥ ε
1
qH
1
+
1
qH
2
1
qH
1
1 −
1
q
ppk
1 −
q
usc
2
k
(7)
Theorem 7.4. Suppose that the euf-cma-II adversary
A
II
has a non-negligible advantage ε in winning the
game then, there is C that can solve the ECDL as-
sumption with the non-negligible advantage ε
′
.
Proof. Given a P ∈ G and a new generator Q = πP in
the same group where π ∈ Z
∗
q
. The C has to find π by
interacting with the A
II
such that Q = πP.
1. Phase-1. The queries are similar to Theorem 7.2.
• Setup. The C generates (PP, mpk) as in Theo-
rem 7.3 and sends to the A
II
.
2. Phase-2. The queries and responses are same as
in Phase-2 of Theorem 7.2, except the response to
q
sv
is as follows:
• q
sv
. Upon q
sv
, the C checks if PID = PID
∗
s
.
If it holds, C aborts because, in this case, the
PID is a target ID. Otherwise, it checks if x
i
exists in L
pk
. If it exists, the C returns x
i
to A
II
.
Otherwise, computes pk
i
= πP where x
i
= π ∈
Z
∗
q
and adds in L
pk
and returns x
i
to A
II
.
3. Forgery. Taking the target PID
∗
s
and PID
r
i
, A
II
outputs a forged CT
∗
i
= (C
∗
1
i
,C
∗
2
i
) on m
∗
where
C
∗
1
i
= ( f
∗
i
,S
∗
i
) and C
∗
2
i
= Enc
∗
K
(m) which is the
valid signcrypted ciphertext and is not the result
of signcryption oracle.
• Case-1 (PID ̸= PID
∗
s
). The C returns ⊥.
• Case-2 (PID = PID
∗
s
). The C extracts the L
pk
for the record (PID
∗
i
,d
∗
i
,pk
∗
i
,x
∗
i
) and L
3
for the
record (m
∗
,ψ
∗
i
, f
∗
i
).
According to the Forking Lemma, the C replays
the A
II
with the same random tape but distinct at-
tributes from H
1
and H
3
. It implies that, h
∗
1
=
H
1
(mpk,PID
∗
i
) i.e. , h
′∗
1
= H
1
(mpk,PID
∗
i
) and
h
∗
1
̸= h
′∗
1
i.e. Q
∗
PID
s
̸= Q
′∗
PID
s
. Similarly, h
∗
3
=
H
3
(m
∗
,ψ
∗
i
,pk
∗
s
,pk
∗
r
i
), h
′∗
3
= H
3
(m
∗
, ψ
∗
i
,pk
∗
s
,pk
∗
r
i
),
and h
∗
3
̸= h
′∗
3
i.e. f
∗
i
̸= f
′∗
i
. In the end, the A
II
out-
puts another forged CT
′∗
i
= (C
∗
1
i
,C
∗
2
i
) on the same
m
∗
where C
∗
1
i
= ( f
′∗
i
,S
′∗
i
) and C
∗
2
i
= Enc
∗
K
(m). Fi-
nally, C will have two valid signatures:
S
∗
i
= r
∗−1
( f
∗
i
∥wd
∗
s
x
∗
s
) (8)
S
′∗
i
= r
′∗−1
( f
′∗
i
∥wd
∗
s
x
′∗
s
) (9)
where r
∗
= r
′∗
and x
∗
s
= x
′∗
s
. From the Eq. 8 and 9
above, the C can extract π as follows:
π = r
∗−1
( f
′∗
i
− f
∗
i
) + (S
∗
i
−
S
′∗
i
)(r
∗−1
(wmpk(Q
∗
PID
s
− Q
∗
PID
s
′
))
−1
Given that, the C solves the ECDL assumption
Q = πP with the advantage ε
′
:
ε
′
≥ ε
1
qH
1
+
1
qH
2
1
qH
1
1 −
1
q
sv
1 −
q
usc
2
k
(10)
Anonymity. Each user utilizes the PID to communi-
cate instead of the ID
R
where the sender sends same
m to multiple receivers while ID
R
of the receiver re-
mains private from each other. The PID is assigned
by RA after verifying each user’s ID
R
using its private
key v. If ID
R
is not verified, then the corresponding
PID will be discarded. Additionally, since only RA
knows its private key, no else could falsely verify the
ID
R
. In case of a dispute, RA can expose the ID
R
.
Non-Repudiation. In our scheme, message m
is signed by the sender with its sk
s
as S
i
=
r
−1
( f
i
∥wd
s
x
s
). The receiver verifies m using pk
s
as
R
i
= S
−1
i
( f
i
P∥wpk
s
Z
1
i
Q
−1
PID
r
i
). Since the sender signs
m with its sk
s
that only the sender knows, it cannot
deny sending m, thus proving non-repudiation.
Forward Security. In the proposed AMCLHS
scheme, the symmetric session key K and its encap-
sulation C
1
i
is generated using the (sk, pk) using a
randomly generated secret value x ∈ Z
∗
q
and a ppk.
In this case, even if the sk is exploited, the A cannot
extract the past sessions since the x is randomly gen-
erated and updated for each session.
ICISSP 2024 - 10th International Conference on Information Systems Security and Privacy
742
8 PERFORMANCE ANALYSIS
We compare the computational cost, communica-
tion cost, and security requirements of the AM-
CLHS scheme with existing multireceiver signcryp-
tion schemes. M shows point multiplication opera-
tion, E shows exponentiation in Z
∗
q
, and n represents
the number of users. The computational overhead is
compared with (Niu et al., 2017; Niu et al., 2022b;
Peng et al., 2020) as shown in Table 1. The over-
head for signcryption is calculated for multiple recip-
ients as outlined in our scheme, whereas the overhead
for unsigncryption is determined on a per-receiver ba-
sis. Among the multireceiver signcryption schemes,
Niu et al. have the highest computational overhead,
utilizing a total of (2n + 4)BP + 1M + (2n + 2)E op-
erations (Niu et al., 2017). Peng at al. require to-
tal (2n + 5)M operations (Peng et al., 2020) and Niu
et al. require a total of (4n + 6)M operations (Niu
et al., 2022b). Contrasting with existing solutions, our
proposed scheme delivers high efficiency with only
(2n + 5)M total operations. It uniquely pairs a lin-
ear signcryption cost with a constant unsigncryption
cost per receiver, regardless of scale. This optimal
combination results in a predictable, scalable system
and setting a new performance standard. Given its
scalability and robustness, our scheme emerges as a
compelling choice for larger, more complex broadcast
communication scenarios, providing a significant up-
grade over existing schemes.
Table 1: Comparison of Computational Overhead.
Schemes Signcryption Unsigncryption Total
Niu et al. (Niu et al., 2017) (2n)BP + 1M +(2n)E 4BP + 2E (2n + 4)BP + 1M + (2n + 2)E
Peng et al. (Peng et al., 2020) (2n + 1)M 4M (2n + 5)M
Niu et al. (Niu et al., 2022b) (2n + 4)M (2n + 2)M (4n + 6)M
Our scheme (2n + 2)M 3M (2n + 5)M
Table 2: Comparison of Communication Cost.
Schemes Ciphertext Length
Complexity of Communication
Signcryption Unsigncryption
Niu et al. (Niu et al., 2017) n|m| + |G| + 2n|G| O(n
2
) O(n)
Peng et al. (Peng et al., 2020) n|m| + (n + 2)|Z
∗
q
| O(n
2
) O(n)
Niu et al. (Niu et al., 2022b) n|(m + 2)| + 2|G| + 2|Z
∗
q
| O(n) O(n)
Our scheme n|m| + |Z
∗
q
| + |G| + |K| O (n) O(1)
The Table 2 shows the communication cost in
terms of the size of the ciphertext generated by each
scheme (Niu et al., 2017; Niu et al., 2022b; Peng
et al., 2020). The proposed AMCLHS scheme has the
optimal communication cost among the four schemes,
as it only requires n|m| + |Z
∗
q
|+ |G| +|K| bits to sign-
crypt a message. Moreover, our scheme has linear
communication cost in signcryption while the un-
Table 3: Comparison based on Security Requirements.
Schemes Confidentiality Unforgeability Anonymity Non-repudiation Forward Security
Niu et al. (Niu et al., 2017) ✓ ✓ ✓ ✓ ✓
Niu et al. (Niu et al., 2022b) ✓ ✓ ✓ × ×
Peng et al. (Peng et al., 2020) ✓ ✓ ✓ × ×
Our scheme ✓ ✓ ✓ ✓ ✓
signcryption cost remains constant. In Table 3, we
present a comparative analysis of the security re-
quirements between our scheme and existing multire-
ceiver hybrid signcryption schemes (Niu et al., 2017;
Niu et al., 2022b; Peng et al., 2020). The com-
parison parameters are confidentiality, unforgeabil-
ity, anonymity, non-repudiation, and forward security.
Our proposed scheme successfully achieves all secu-
rity requirements as shown in Table 3, offering supe-
rior efficiency with lower computational costs, setting
it apart from the others.
9 CONCLUSION
Our paper introduces a novel mKEM-DEM based
AMCLHS scheme for broadcast communication. The
proposed scheme generates a symmetric key using the
public and private key pair of the users. The mes-
sage is then signcrypted with the previously gener-
ated symmetric key and the private key of the sender.
We provide a detailed security analysis using EC-
CDH and ECDL assumptions and demonstrate that
the scheme is secure against ind-cca2 and euf-cma at-
tacks for Type-I and Type-II adversaries. Moreover,
in this scheme, each user is assigned a PID to en-
sure user anonymity. Lastly, we compare our scheme
with existing single receiver and multireceiver cer-
tificateless hybrid signcryption schemes in terms of
computation cost, communication cost, and security
requirements. We show that the proposed scheme
has less communication cost and is computationally
more efficient, with the signcryption cost linear with
the number of designated receivers while the unsign-
cryption cost remains constant and simultaneously
achieves confidentiality, unforgeability, anonymity,
non-repudiation, and forward security.
REFERENCES
Al-Riyami, S. S. and Paterson, K. G. (2003). Certificateless
public key cryptography. In Advances in Cryptology
- ASIACRYPT 2003, 9th International Conference on
the Theory and Application of Cryptology and Infor-
mation Security, Taipei, Taiwan, November 30 - De-
cember 4, 2003, Proceedings, volume 2894 of LNCS,
pages 452–473. Springer.
Barbosa, M. and Farshim, P. (2008). Certificateless sign-
cryption. In Proceedings of the 2008 ACM Sympo-
sium on Information, Computer and Communications
Security, ASIACCS 2008, Tokyo, Japan, March 18-20,
2008, pages 369–372. ACM.
Chen, X., He, D., Khan, M. K., Luo, M., and Peng, C.
(2023). A secure certificateless signcryption scheme
Anonymous Multi-Receiver Certificateless Hybrid Signcryption for Broadcast Communication
743

without pairing for internet of medical things. IEEE
Internet Things J., 10(10):9136–9147.
Cohen, H., Frey, G., Avanzi, R., Doche, C., Lange, T.,
Nguyen, K., and Vercauteren, F. (2005). Handbook
of elliptic and hyperelliptic curve cryptography. CRC
press.
Cui, B., Lu, W., and He, W. (2022). A new certificateless
signcryption scheme for securing internet of vehicles
in the 5g era. Security and Communication Networks.
Dent, A. W. (2005a). Hybrid signcryption schemes with in-
sider security. In Boyd, C. and Nieto, J. M. G., editors,
Information Security and Privacy, 10th Australasian
Conference, ACISP 2005, Brisbane, Australia, July 4-
6, 2005, Proceedings, volume 3574 of LNCS, pages
253–266. Springer.
Dent, A. W. (2005b). Hybrid signcryption schemes with
outsider security. In Zhou, J., L
´
opez, J., Deng, R. H.,
and Bao, F., editors, Information Security, 8th Inter-
national Conference, ISC 2005, Singapore, Septem-
ber 20-23, 2005, Proceedings, volume 3650 of LNCS,
pages 203–217. Springer.
Gong, B., Wu, Y., Wang, Q., Ren, Y., and Guo, C. (2022).
A secure and lightweight certificateless hybrid sign-
cryption scheme for internet of things. Future Gener.
Comput. Syst., 127:23–30.
Hongzhen, D., Qiaoyan, W., Shanshan, Z., and Mingchu,
G. (2021). A pairing-free certificateless signcryption
scheme for vehicular ad hoc networks. Chinese Jour-
nal of Electronics, 30(5):947–955.
Kasyoka, P. N., Kimwele, M. W., and Mbandu, A. S.
(2021). Efficient certificateless signcryption scheme
for wireless sensor networks in ubiquitous healthcare
systems. Wirel. Pers. Commun., 118(4):3349–3366.
Li, F., Shirase, M., and Takagi, T. (2009). Certificateless
hybrid signcryption. In Bao, F., Li, H., and Wang,
G., editors, Information Security Practice and Expe-
rience, 5th International Conference, ISPEC, Xi’an,
China, April 13-15, 2009, Proceedings, volume 5451
of LNCS, pages 112–123. Springer.
Li, X., Jiang, C., Du, D., Wang, S., Fei, M., and Wu,
L. (2022). A novel efficient signcryption scheme
for resource-constrained smart terminals in cyber-
physical power systems. CoRR, abs/2212.04198.
Malone-Lee, J. (2002). Identity-based signcryption. IACR
Cryptol. ePrint Arch., page 98.
Niu, S., Niu, L., Yang, X., Wang, C., and Jia, X. (2017).
Heterogeneous hybrid signcryption for multi-message
and multi-receiver. PloS one, 12(9):e0184407.
Niu, S., Shao, H., Hu, Y., Zhou, S., and Wang, C. (2022a).
Privacy-preserving mutual heterogeneous signcryp-
tion schemes based on 5g network slicing. IEEE In-
ternet Things J., 9(19):19086–19100.
Niu, S., Zhou, S., Fang, L., Hu, Y., and Wang, C. (2022b).
Broadcast signcryption scheme based on certificate-
less in wireless sensor network. Comput. Networks,
211:108995.
Peng, C., Chen, J., Obaidat, M. S., Vijayakumar, P., and He,
D. (2020). Efficient and provably secure multireceiver
signcryption scheme for multicast communication in
edge computing. IEEE Internet Things J., 7(7):6056–
6068.
Qiu, J., Fan, K., Zhang, K., Pan, Q., Li, H., and Yang, Y.
(2019). An efficient multi-message and multi-receiver
signcryption scheme for heterogeneous smart mobile
iot. IEEE Access, 7:180205–180217.
Selvi, S. S. D., Vivek, S. S., and Rangan, C. P. (2009). Cer-
tificateless KEM and hybrid signcryption schemes re-
visited. IACR Cryptol. ePrint Arch., page 462.
Selvi, S. S. D., Vivek, S. S., Shukla, D., and Rangan,
C. P. (2008). Efficient and provably secure certificate-
less multi-receiver signcryption. In Provable Secu-
rity, Second International Conference, ProvSec 2008,
Shanghai, China, October 30 - November 1, 2008.
Proceedings, volume 5324 of LNCS, pages 52–67.
Springer.
Smart, N. P. (2004). Efficient key encapsulation to multiple
parties. In Blundo, C. and Cimato, S., editors, Se-
curity in Communication Networks, 4th International
Conference, SCN 2004, Amalfi, Italy, September 8-10,
2004, Revised Selected Papers, volume 3352 of LNCS,
pages 208–219. Springer.
Wu, Y., Gong, B., Zhang, Y., et al. (2022). An improved ef-
ficient certificateless hybrid signcryption scheme for
internet of things. Wireless Communications and Mo-
bile Computing, 2022.
Yang, Y., He, D., Vijayakumar, P., Gupta, B. B., and Xie,
Q. (2022). An efficient identity-based aggregate sign-
cryption scheme with blockchain for iot-enabled mar-
itime transportation system. IEEE Trans. Green Com-
mun. Netw., 6(3):1520–1531.
Yin, A. and Liang, H. (2015). Certificateless hybrid
signcryption scheme for secure communication of
wireless sensor networks. Wirel. Pers. Commun.,
80(3):1049–1062.
Yu, X., Zhao, W., and Tang, D. (2022). Efficient and prov-
ably secure multi-receiver signcryption scheme using
implicit certificate in edge computing. J. Syst. Archit.,
126:102457.
Yu, Y., Yang, B., Huang, X., and Zhang, M. (2007). Effi-
cient identity-based signcryption scheme for multiple
receivers. In Autonomic and Trusted Computing, 4th
International Conference, ATC, Hong Kong, China,
July 11-13, 2007, Proceedings, volume 4610 of LNCS,
pages 13–21. Springer.
Zhang, W., Zhang, Y., Guo, C., An, Q., Guo, Y., Liu, X.,
Zhang, S., Huang, J., et al. (2022). Certificateless hy-
brid signcryption by a novel protocol applied to inter-
net of things. Computational Intelligence and Neuro-
science.
Zheng, Y. (1997). Digital signcryption or how to achieve
cost(signature) + cost(encryption). In Advances in
Cryptology - CRYPTO ’97, 17th Annual International
Cryptology Conference, Santa Barbara, California,
USA, August 17-21, 1997, Proceedings, volume 1294
of LNCS, pages 165–179. Springer.
Zhou, C. (2018). Certificateless signcryption scheme with-
out random oracles. Chinese Journal of Electronics,
27:1002–1008.
ICISSP 2024 - 10th International Conference on Information Systems Security and Privacy
744
