
The Impact of IOT Cybersecurity Testing in
the Perspective of Industry 5.0
Tauheed Waheed
a
and Eda Marchetti
b
CNR-ISTI Pisa, Italy
Keywords:
Industry 4.0, IoT Cybersecurity, Industry 5.0.
Abstract:
The continuous advancements in IoT (Internet of Things) have various benefits. It has opened new horizons
for the industrial revolution in the 21st century. Industry 4.0 and Industry 5.0 also promote using IoT devices
to build better and more productive autonomous systems. The behaviour of these complex software systems
evolves as they are augmented with the physical and security of IoT devices. IoT-security security and privacy
benchmark systems have recently caused a financial loss in various industrial sectors. More importantly, it
has damaged the trust of people in technology and IoT systems and people’s distrust towards IoT, motivating
rediscovering IoT cybersecurity from a brother perspective. The paper aims to enhance security and privacy
by design methodology and provides an overview of the issues and challenges in cybersecurity testing. We
also proposed a Cybersecurity Testing Framework (CTF) to enhance IoT cybersecurity that will help to resolve
significant security and privacy challenges related to Industry 5.0.
1 INTRODUCTION
Recently, the Security and Privacy by Design (SPbD)
approach has been proposed to target these two im-
portant attributes and ensure that IoT systems by de-
sign comply with their principles. Thus, the software
industry and academia promote the concept of SPbD
to build a proactive security-based culture rather than
bearing the additional cost of security testing later in
the development process. Even if they leverage en-
terprise architecture methods to improve the imple-
mentation of security during development, SPbD is
still not fully implemented, and various questions and
undiscovered challenges are still unsolved.
Recent research revealed that 90% of consumers
need more confidence regarding the IoT cybersecurity
of their systems or applications (Gem, ). Solutions for
reducing uncertainty and increasing overall reliability,
cybersecurity and trustworthiness must move in two
technological and societal directions.
Considering the former, past solutions adopted
by Industry 4.0 focused on using legacy or embed-
ded systems to isolate them from the Internet (Casola
et al., 2020), even if with a significant impact on the
business and benefits. It is evident that Industry 4.0
a
https://orcid.org/0009-0006-0489-7697
b
https://orcid.org/0000-0003-4223-8036
and automation brought various business benefits, but
going into Industry 5.0 our modern industrial systems
will require more efficient, trusted, and secure ways of
communication. Indeed, pressure from time to market
often forces industries and developers towards mas-
sive use of available third-party or open-source com-
ponents that could increase cybersecurity risks if not
adequately tested. Additionally, if, from one side, the
commonly adopted cloud solutions and data analyt-
ics (like, Google Cloud (Security, 2020), Microsoft
Azure (Andrade, 2022) and Amazon (Infastructure,
2022) improve the IOT integrability (Andrade et al.,
2020), for the other still requires robust trustable and
reliable solutions and components. Finally, as evi-
denced by the many focused call-for-proposals at the
European level, one of the most effective means for
preventing main criticalities and breaches is to pro-
mote the by-design adoption of cybersecurity from
a broader perspective (Casola et al., 2020) (Chhetri
et al., 2022)
Thus, guidelines and methodologies and specific
tools for integrating cybersecurity into the entire life
cycle of software development, from conception to
dismantlement, have been the focus of the last year’s
research activity (Tahaei and Vaniea, 2023) with par-
ticular attention to tools and techniques support Agile
(Bonorchis, 2022) and DevOps (Atlassian, 2023) ap-
proaches.
480
Waheed, T. and Marchetti, E.
The Impact of IOT Cybersecurity Testing in the Perspective of Industry 5.0.
DOI: 10.5220/0012235800003584
In Proceedings of the 19th International Conference on Web Information Systems and Technologies (WEBIST 2023), pages 480-487
ISBN: 978-989-758-672-9; ISSN: 2184-3252
Copyright © 2023 by SCITEPRESS – Science and Technology Publications, Lda. Under CC license (CC BY-NC-ND 4.0)

Among them, an important role has been taken by
proposals focused on testing, analysis and verifica-
tion of potentially vulnerable, insecure hardware and
software components because they are considered the
most effective ways to prevent, detect and control vul-
nerability and failures (Garousi et al., 2020).
However, considering that the overall cost of test-
ing is around 40% of the total development costs of a
typical software project (Garousi et al., 2020), in IoT
and Industry 4.0, verification, validation, and assess-
ment procedures are the first to be reduced or skipped
to save cost and time if not strictly connected to safety
risks.
From the societal point of view, and in line with
the Internet of trust (European, 2022) principles, a
human-centred and ethical development of digital and
industrial technologies is currently recognised as the
most effective way for improving the overall trustwor-
thiness and supporting social innovation (European,
2022). Indeed, by 2030, 80% of citizens will use dig-
ital solutions. A two-way engagement of citizens in
developing and testing technologies will assure more
sustainable and secure infrastructures, systems and
components.
In this paper, following the message of (Bravos
et al., 2022), we focus on improving the IoT cyberse-
curity testing for the next generation of our industrial
development processes and integrating it with human
capabilities.
Considering both technological and societal direc-
tions, the proposal of this paper focuses on several ar-
eas, such as: evaluating present cybersecurity testing
solutions, working in line with the intelligent itera-
tive processes, promoting a practical IoT cybersecu-
rity testing approach, supporting user-centric testing,
improving and assessing technological development
in line with social and ethical values, sustainability
and user trustworthiness, adoption of standards to in-
crease transparency and openness.
The cybersecurity market is expected to grow to
170.4 billion dollars in the coming years (Zaghloul
et al., 2021). In this light, one main target of the In-
ternet of Things is to promote connectivity between
devices and objects. Recent estimations show that the
number of devices connected to the Internet has in-
creased abruptly from 0.08 to 6.58% per person, with
an overall increase of 8225% in the last seven years
(G
´
omez et al., 2021)
Indeed, this massive growth of services and possi-
bilities certainly improves digital lives, allowing peo-
ple to be connected whenever and wherever, but it
calls for specific attention to security and privacy.
With the new paradigm proposed by Industry 5.0,
which focuses on the collaboration between robots
and humans (Adel, 2022), the emphasis on technolo-
gies will be reduced. However, security and privacy
criticalities are not entirely solved (Straub, 2020) due
to a lack of user involvement in IoT cybersecurity
testing. The primary purpose of this paper is to de-
velop a comprehensive cybersecurity testing frame-
work while ’user’ or ’human’ should be center of fo-
cus.
In particular, in Section 2, we present the current
perspectives about cybersecurity and we analyse the
currently available solutions considering the impact
of IOT cybersecurity testing in Industry 4.0 to move
a first step from the perspective of Industry 5.0. Then
we first overview the security and privacy threats and
their impact on cybersecurity testing Section 4).
Then, Section 4 analyses cybersecurity from dif-
ferent perspectives considering various domains util-
ising IoT infrastructure and exploring paramount fac-
tors regarding the need for cybersecurity testing in the
present era. Section 4 discusses the importance of
cybersecurity testing and later proposed CTF. More-
over, it is a human-centric or user-centric cybersecu-
rity testing framework appropriate for Industry 5.0.
2 BACKGROUND AND RELATED
WORK
Cyber assaults (Rajabion, 2023) play a critical role
in safeguarding software and hardware against intru-
sion and unauthorized access. Nowadays, security
measures use various security strategies like access
control systems, cybersecurity software, antivirus and
malware, intrusion detections, firewalls, raising secu-
rity awareness for system users and process optimiza-
tion.The intelligent access to resources (Srujana et al.,
2022) can be possible through cybersecurity appropri-
ately. However, these transformations have made cy-
bersecurity the most robust modern-day defence strat-
egy against various digital threats and attacks. There-
fore, various sectors are investing in enhancing se-
curity mechanisms and cybersecurity to prevent data
theft, maintain regulatory compliance, secure trade
secrets, and protect critical information while facil-
itating and improving organization operations. Ex-
ploring and understanding cybersecurity from various
perspectives is essential, as cyber-attackers do not al-
ways follow the same attack strategy. In the follow-
ing, some of these aspects will be discussed.
1. As reported in (Jaber and Fritsch, 2022), cy-
bersecurity’s primary focus is on defence strate-
gies that detect, mitigate and prevent the system
The Impact of IOT Cybersecurity Testing in the Perspective of Industry 5.0
481

from cyber-attacks, but the technology and dig-
italization environment is becoming more com-
plex. Therefore, regularly updating an organiza-
tion’s security strategy to enhance its cybersecu-
rity defences is essential.
2. In recent years, emerging technologies like Ar-
tificial Intelligence (AI) have been applied to
solve some cybersecurity criticalities, but AI fea-
tures have also been used by cyber-attacks too.
Indeed, AI-driven cyber-attacks create complex
challenges for cybersecurity experts, impacting
overall system trustworthiness. Nowadays, cyber-
security (Pearlson and Huang, 2022) issues are
detected and resolved mainly through quality-
control testing, vulnerability testing and penetra-
tion testing.
3. Considering the Small and Medium-sized enter-
prise perspective, it has been observed that the
number of hackers is increasing as they are ex-
ploiting SMEs limited resources and outdated cy-
bersecurity infrastructure. SMEs should improve
their cybersecurity approach efficiently and ap-
propriately. a recent study demonstrates that
(Varma et al., 2023) that several undiscovered
cybersecurity vulnerabilities were due to lack of
technical skills and knowledge in using the avail-
able facilities. Thus guidelines and roadmap
should be provided to to aid SMEs in adequately
implementing the proper defence.
4. European Union Cybersecurity Agency (ENISA)
and American National Institute of Technology
(NIST) (Chiara, 2022) recognise cybersecurity
certifications as one of the effective means for en-
suring the right level so trust. The IoT based cer-
tifications can have a role in Industry 5.0 and be-
come paramount for user trustworthiness as ven-
dors must meet cybersecurity requirements before
launching and selling their products (Trustmark,
2021). Additionally, as highlighted in (White-
House, 2021) federal government should support
the recognition of cybersecurity vulnerabilities
and persistent network threats by providing proac-
tive and visionary measures to modernize its cy-
bersecurity strategy, including by maximizing the
federal government’s visibility into cybersecurity
threats while protecting user privacy and rights.
Even if not exhaustive, the above examples evi-
dence that only integrated quality-control testing pro-
cess, associated with certification procedures, guide-
lines and round-breaking to conduct collaborative re-
search, can be the solution for facing cybersecurity
criticalities (Heiding et al., 2023).
3 WHY DO WE NEED
CYBERSECURITY TESTING?
As highlighted before, cybersecurity testing will aid
in further maturing the predictable security mecha-
nisms for ensuring that the product performs its func-
tions as intended and more securely. Cybersecurity
testing will become more vital than ever for maintain-
ing the integrity and security of critical software sys-
tems for several reasons. Cybersecurity testing can
protect organizations from cyber-attacks and, more
important, able to disrupt business continuity from a
broader perspective (Athanasopoulos and et al., 2022;
Daoudagh and Marchetti, 2023) and provide them
with the level of robustness of their security strategy
and efficacy of their countermeasures. Cybersecu-
rity testing can improve the integrity and security of
the software supply chain, enhancing user trustwor-
thiness in critical software systems. In Figure 1, for a
better focus on the issue, a schema of the main reasons
why cybersecuity testing is important is provided.
1 Achieving Auditable and verifiable Products:
The massive portion of the software components that
aid in developing software services or products are
extracted from third parties and, therefore can contain
vulnerabilities that could compromise the overall de-
sired security requirements. Cybersecurity testing can
help to achieve verifiable and auditable products.
2 Improving the continuous Inspections of
Software: The software system or application re-
quires frequent updates due that could impact secu-
rity, privacy, General Data Protection and Regula-
tion (GDPR) policies and, importantly user/consumer
needs. Cybersecurity testing and regression, in par-
ticular, can be used to update the software systems
efficiently and improve its continuous inspections.
3 Achieving Better Implementation of SPbD
for Agile Software Development: As we men-
tioned in the introduction, SPbD still needs com-
prehensive strategies to build a proactive security-
based culture in the software industry. Therefore, spe-
cific SPbD cybersecurity testing techniques and tools
should be provided to prevent cyber-attackers and in-
truders from compromising security requirements.
4 Enhancing Software Reliability: Even if in the
last decade, various security measures and guidelines
have been implemented to improve the reliability of
industrial systems, more effort is required to meet a
certain level of quality . Therefore, cybersecurity test-
ing will be significant to pave the way to improve the
reliability of our modern-day cyber-physical systems
and various complex AI-driven software systems.
5 Improving Decentralized Software Gover-
nance: The blockchain technologies, smart contracts
WEBIST 2023 - 19th International Conference on Web Information Systems and Technologies
482
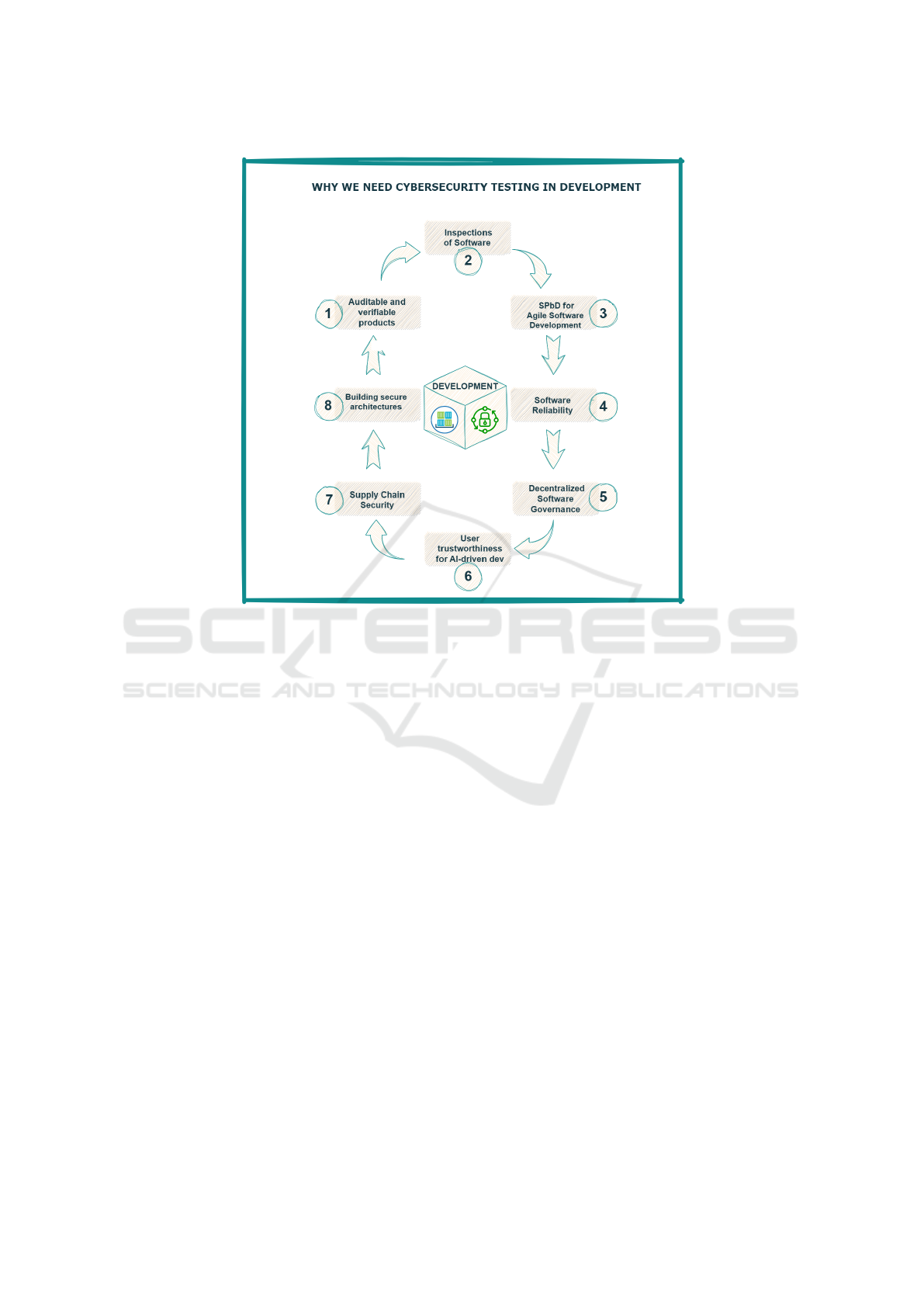
Figure 1: Cybersecurity needs.
and crypto-assets are prominent examples of software
with decentralized governance in which cybersecurity
testing can identify vulnerabilities and evaluate the
impact of the recovery actions on the overall consen-
sus.
6 Exploring new Challenges and Improving
user Trustworthiness in AI-driven Software Devel-
opment: In the near future, particularly going into
Industry 5.0, most of the software life cycle activi-
ties will be carried out by intelligent agents increasing
productivity but also cybersecurity risks. Therefore,
cybersecurity testing (Pawlicka et al., 2022) will be
needed to improve user trustworthiness in AI-driven
software development and ultimately enhance our se-
curity strategy from a broader perspective.
7 Improving Supply chain Security: The in-
tegration of components and code from third par-
ties, whose development and testing are considered
outside the control, can be a risk for the overall
system. During the recent pandemic, they encoun-
tered various attacks, such as the SolarWind cyber-
attack(Athanasopoulos and et al., 2022). Methodol-
ogy to improve supply chain security and cyberse-
curity testing has excellent potential to guarantee the
trustworthiness of these third-party components.
8 Building more Secure Architectures and Plat-
forms: It’s essential to understand that a trusted
supply chain is insufficient to develop and maintain
security-critical systems. Secure architectures start-
ing from the hardware and operating system level
should be developed and cybersecurity testing applied
(Athanasopoulos and et al., 2022) to validate commu-
nication between components and the overall security.
As a practical example, we refer to the software
system developed (Kirk et al., 2023) for modern au-
tonomous vehicles is more advanced and complicated
than desktop-based software due to increased depen-
dencies or interconnectivity to perform various criti-
cal functions. However, these dependencies and com-
plexities increase attack-surface area while ultimately
aiding cyber-attackers. In this regard, researchers
have introduced Over-The-Air (OTA) updates to mit-
igate and prevent cyber-attacks. The same OTA up-
dates have also been utilized for both Android and
desktop systems. Uptane is the current OTA secu-
rity system for autonomous vehicles. It is designed
to address the special issues vehicles must face. The
working mechanism of the Uptane system particu-
larly needs to possess a secure method for updating;
if not, hackers will exploit it regularly.
Researchers have developed model-based and
comprehensive security testing approaches by trans-
The Impact of IOT Cybersecurity Testing in the Perspective of Industry 5.0
483
forming Uptane and attack models into formal mod-
els for Communicating Sequential Processes (CSP) in
broader perspectives (Kirk et al., 2023). The results
achieved by security testing provided the benchmark
to validate some paramount vulnerabilities and se-
curity design of Uptane.Furthermore,the researchers
tested Uptane system with 25 specifically conceived
test cases to simulate attacks. The OTA system was
stressed with a continuous bombardment of security
tests during its live implementation, demonstrating
unexpected vulnerabilities.
4 CYBERSECURITY
FRAMEWORK
The cybersecurity domains directly impact industrial
technologies like smart manufacturing, the Internet of
Things (IoT), cyber-physical systems, cloud comput-
ing and Artificial Intelligence. Therefore, all these in-
dustrial technologies demand updated cybersecurity
measures and utilizing cybersecurity testing to build
user trustworthiness is the appropriate direction to
protect the environment from being attacked.
It has been evident that cybersecurity essentials
for Industry 5.0 emphasize risk management and busi-
ness continuity. As we move towards Industry 5.0,
more white and grey hat hackers are needed.The user-
centric cybersecurity testing approach will collabo-
rate with white hat hackers to reduce vulnerability and
cyber-attacks on
Cybercriminals are the first cybersecurity essen-
tial threat for Industry 5.0. Cyber-criminals are ei-
ther internal, such as employees, or external, such as
organized attackers (Hacktivist, state-sponsored) and
hackers (black, white, grey). Moreover, their moti-
vation is financial gain; they practice cracking pass-
words while sending malware and viruses to steal crit-
ical financial assets, such as credit cards or any infor-
mation that can be of high value. The countermeasure
for cyber crimes varies as it is based on the value of
data and its sensitivity.
The continuous and proactive updating of cyberse-
curity testing techniques are needed to counter skill-
ful hackers, but a solution could be to ask for the help
of users that are the final and most impacted by this
annoying situation. Users have enormous manpower,
and in the proper condition, they can work together
with testers and developers for a more secure and safe
life in every application domain. Our proposal is,
therefore, to develop a human-centric testing that can
be suitable also for Industry 5.0. We propose a con-
tinuous and hybrid cybersecurity testing framework
to protect the system from cyber-attacks and increase
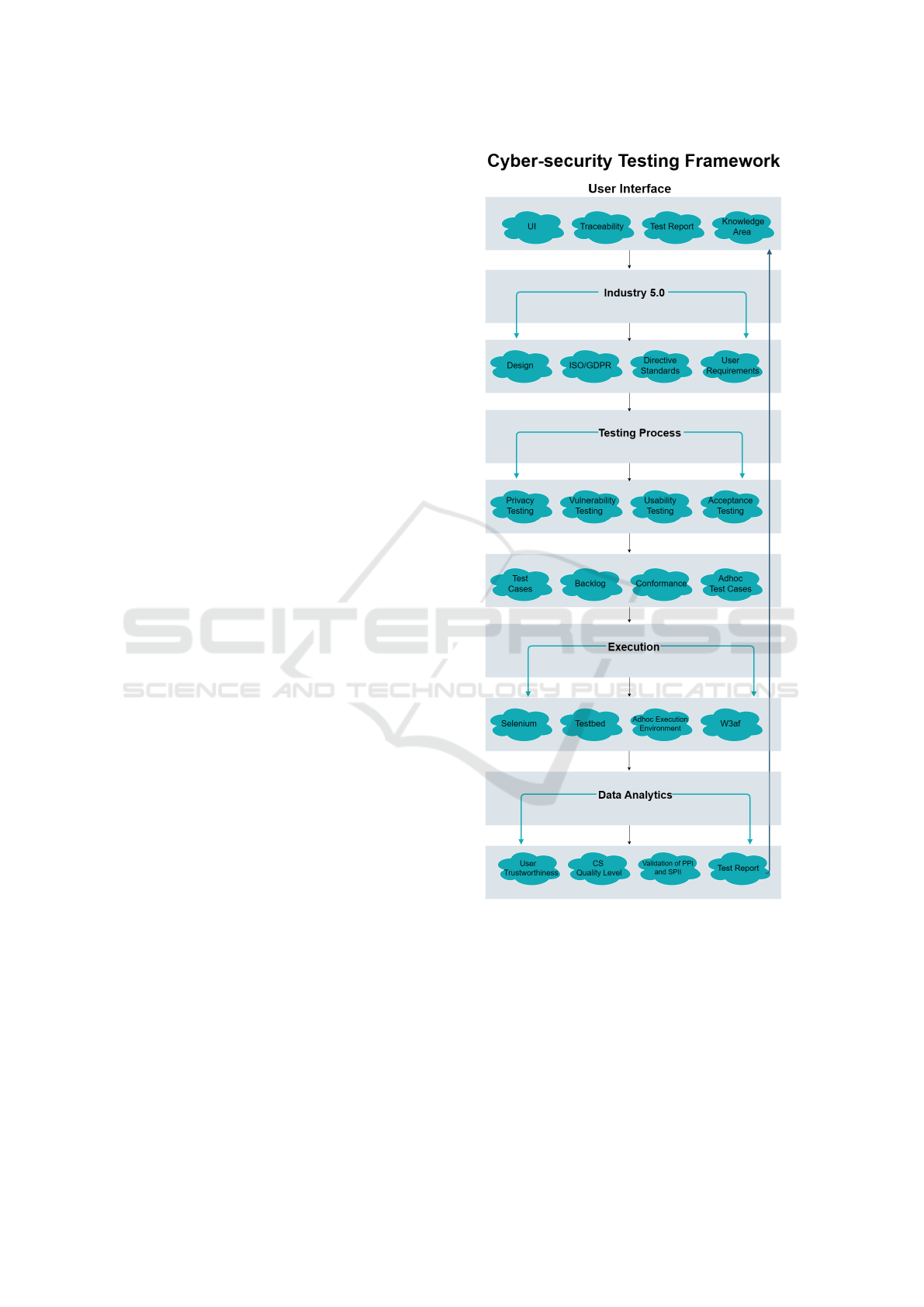
Figure 2: Conceptual Model.
user trustworthiness as schematized in Figure 2.
As in the figure our proposal comprises various
layers, ad different elements in each of them, to let the
user be completely involved in testing and ultimately
enhancing user trustworthiness.
User Interface: The first layer i is the user inter-
face where the users can find facilities for expressing
their requirements, needs and desired functions. In
this layer, there can be, but not limited to, the follow-
ing elements:
WEBIST 2023 - 19th International Conference on Web Information Systems and Technologies
484

• UI: It allows the user to interact with the system
depending upon the scope and legitimacy of the
user to perform some tasks.
• Traceability: Traceability in the user interface al-
lows all kinds of users to be proactive while per-
forming cybersecurity testing in every iteration.
• Test Report: It is generated based on testing ac-
tivities and is a fundamental document for man-
aging founded threats or bugs or future improve-
ments.
• Knowledge Area: The knowledge area reports
the lessons learned from previous iterations and
provides a collaborative knowledge-sharing plat-
form to all users/stakeholders interested in im-
proving cybersecurity.
Industry 5.0: Represent the target domain of this
paper and the proposed human-machine collabora-
tion. The objective is to boost industrial productiv-
ity and open new horizons in technological advance-
ments. The element we included in this layer are:
• Design: The design specification describes the
environment, the systems, its components and
how the user interacts with the system. This can
guide the cybersecurity testing.
• ISO/GDPR: It is paramount to keep track of up-
dates in International Organization of Standard-
ization (ISO) and General Data Protection and
Regulation (GDPR), while going into require-
ments elicitation.
• Directive Standards: The directive standards
will also be considered because they provide ba-
sic safety management strategies and legal work-
ing mechanisms for various domains, e.g., health
care.
• User Requirements: The user requirements elic-
itation phase provides an opportunity to under-
stand user needs better and focus on the cyber-
security testing process.
Testing Process: The intention is to provide a
unified platform to perform various types of cyber-
security testing to improve the security strategy from
broader perspectives and with specific user facilities.
It includes two sub-layer definitions of the test target
and the selection of the test strategy. In particular, as
reported in the figure, we considered:
• Privacy Testing: If focus on user privacy require-
ments and their implementation. It is essential for
different domains and, in particular, for the health-
care systems.
• Vulnerability Testing: It evaluates the security
by recognizing and resolving application short-
comings. It is helpful to understand system be-
haviour for the identification of risks.
• Usability Testing: It focuses on system behavior
while interacting with the user to detect vulnera-
bilities that malicious attackers can exploit.
• Acceptance Testing: Also referred to as pre-
production testing, checks whether the software
system or application satisfies the user acceptance
criteria. Moreover, acceptance testing is carried
out to ensure that the software developed is con-
venient to release by performing formal testing of
user/customer requirements and business motives.
• Test Cases: The test cases are usually formulated
and documented by software testers to fulfil all
acceptance criteria requirements. The test cases
can be prioritized based on their importance in ac-
ceptance criteria. This prioritization of test cases
ensures that the most critical and paramount func-
tionalities are tested first. Moreover, it must sim-
ulate the real-world scenario to test all software
functionalities.
• Backlog: The backlog comprises a prioritized list
of tasks for the cybersecurity testing team. It is ex-
tracted from the test cases and user requirements.
The most critical tasks are shown at the top of the
testing backlog, so the tester delivers them first. It
also documents the meetings among developers,
testers, users and various stakeholders.
• Conformance: The purpose o is to review and
validate test cases to ensure they are adequate and
correct. As mentioned above, test cases are docu-
mented in the testing backlog and kept in a cen-
tralized position for further verification. More-
over, when all the test cases are executed, the cy-
bersecurity testing team must review the test re-
sults to resolve the defects.
• Adhoc Test Cases: The purpose is to check for
the completeness of the testing process and to find
more defects before going into the execution pro-
cess. It is an unstructured approach that doesn’t
follow formal documentation and test design tech-
niques to formulate adhoc test cases. The tester
should have adequate knowledge of the system
under test to create quality adhoc test cases.
Execution: The execution of our cybersecurity
testing framework will be done through various state-
of-the-art testing techniques and tools such as;
• Selenium: Selenium is an open-source automated
testing framework for web applications across dif-
ferent platforms and browsers. It is utilized to au-
tomate web applications for testing, it is supported
The Impact of IOT Cybersecurity Testing in the Perspective of Industry 5.0
485

by vendors. The selenium will always be rele-
vant in the perspective of our cybersecurity test-
ing framework execution because cyber-attackers
mostly prefer web applications as these are fragile
and comprised of users that are newbies in terms
of using technology securely.
Test-bed: The term test bed is more like an
umbrella activity, as it captures everything from
hardware equipment, and prototype machines to
virtual investigative environments integrated with
user requirements for continuous optimization.
The test-bed environments are supported by a
comprehensive network of stakeholders and do-
main experts. In envisaging to involve users in
the testing process, the test bed should let them
collaborate with various stakeholders like domain
experts for keep on developing innovative solu-
tions to adapt to Industry 5.0 effectively.
Adhoc Execution Environment: The purpose of
adhoc execution environment is to allow the exe-
cution of the test cases without creating or going
through a formal test plan. This execution envi-
ronment has been widely utilized in agile testing
environments and development because iterative
testing is essential to deliver the product timely.
The adhoc execution environment plays a massive
role in ensuring quality and identifying defects in
our products.
W3af: The W3af (Web Application Attack and
Audit Framework) is basically open-source secu-
rity scanner for web applications.The main pur-
pose of W3af is to provide a framework or plat-
form that helps us to secure our web applications
by exploiting and identifying various vulnerabil-
ities. It aids in penetration testing and provides
important information about security vulnerabili-
ties.
Data Analytic: The purpose of data analytics in
our CTF is to extract data from our testing results after
its execution and perform analysis to achieve various
benefits. It a clear picture to improve the quality of
our test suite and improves collaboration among var-
ious stakeholders. Moreover,it aids in exploring the
causes of test failures and documenting them in the
shape of cybersecurity test reports. It includes the fol-
lowing elements:
• User Requirements: It organizes and helps to
improve user requirements for optimizing organi-
zational cybersecurity strategy.
• Cybersecurity Quality Level: The purpose of
cybersecurity testing framework is to achieve
some adequate quality level. Industry 5.0 needs
quality risk management strategies to understand
user/customer demands and to improve its secu-
rity policies. Through the cybersecurity testing
process, evidence can be collected and used for
deriving the quality level provided. This mea-
sure provides the user with the data for increasing
his/her trustworthiness in the tested system.
• Validation of PII and SPII: Another advantage
data analytics will provide is validating PII (Per-
sonally Identifiable Information) and SPII ( Sensi-
tive Personally Identifiable Information) that can
be utilized to distinguish one individual from an-
other. The security and validation of these essen-
tial assets play a massive role to achieve user trust-
worthiness, as the consistent validation of these
assets protects our users from financial theft and
identity theft.
• Test Report: .The test report achieved from
our CTF is really vital for everyone, includ-
ing users, security experts and various stakehold-
ers.As schematised in Figure 2, the test report en-
hances the knowledge area of various users per-
forming cybersecurity testing in the next itera-
tions. Furthermore, the test report will help our
stakeholders to analyze the errors and security
loopholes efficiently.
5 CONCLUSION
Cybersecurity is evolving rapidly, and it’s essential to
understand the need for user involvement to formulate
an efficient and robust cybersecurity strategy. This
paper aims to enhance user trustworthiness by giving
them equal opportunity to be part of the system in the
tester’s shape. As the number of IoT users is increas-
ing and bringing complex challenges for cybersecu-
rity. We tried to resolve these challenges through our
CTF and its user-centricity. It will help us to educate
and motivate users to take responsibility for security.
We have a long road ahead in terms of building ubiq-
uitous testing platforms to achieve adequate quality
and user trustworthiness, but user-centric Cybersecu-
rity Testing Frameworks, as the one presented here,
have excellent potential to resolve cybersecurity chal-
lenges.
ACKNOWLEDGEMENTS
This work was partially supported by the project SER-
ICS (PE00000014) under the NRRP MUR program
funded by the EU - NGEU.
WEBIST 2023 - 19th International Conference on Web Information Systems and Technologies
486

REFERENCES
Gemalto 2023: State of iot security. Network Security,
2019(2):4–4.
Adel, A. (2022). Future of industry 5.0 in society: Human-
centric solutions, challenges and prospective research
areas. J. of Cloud Computing, 11(1):1–15.
Andrade (20 December 2022). Azure identity & ac-
cess security best practices microsoft learn. in
azure security fundamentals documentations.
https://learn.microsoft.com, Retrieved(July 14,2023).
Andrade, R. O., Yoo, S. G., Tello-Oquendo, L., and Ortiz-
Garc
´
es, I. (2020). A comprehensive study of the iot
cybersecurity in smart cities. IEEE Access, 8:19.
Athanasopoulos, E. and et al. (December 2022). Cy-
bersecurity for europe. In Markatos, E. and Ran-
nenberg, K., editors, Blue book, pages 70–91.
https://cybersec4europe.eu.
Atlassian, J. (7 May 2023). Jira security issues. atlas-
sian community. https://community.atlassian.com/,
Retrieved(July 14,2023).
Bonorchis (20 October 2022). Jira-issue & project tracking
software. atlassian. https://www.atlassian.com, Re-
trieved(July 14,2023).
Bravos, G., Cabrera, A. J., Correa, C., Danilovi
´
c, Vasiliadis,
G., and Vukobratovic, D. (2022). Cybersecurity for
industrial internet of things: Architecture, models and
lessons learned. IEEE Access, 10:124747–124765.
Casola, V., De Benedictis, A., and Rak (2020). A novel
security-by-design methodology: Modeling and as-
sessing security by slas with a quantitative approach.
J. of Systems and Software, 163:110537.
Chhetri, M. B., Liu, X., Grobler, M., Hoang, T., Renaud,
K., and McIntosh, J. (2022). Report on the 2nd work-
shop on human centric software engineering & cyber
security (hcse&cs 2021). SIGSOFT Softw. Eng. Notes,
47(2):12–14.
Chiara, P. G. (2022). The iot and the new eu cybersecurity
regulatory landscape. Int.Review of Law, Computers
& Technology, 36(2):118–137.
Daoudagh, S. and Marchetti, E. (2023). Breakthroughs in
testing and certification in cybersecurity: Research
gaps and open problems. In Proc. of the 7th Italian
Conference on Cyber Security, Bari, Italy, February
2nd to 5th, 2023, CEUR Workshop Proceedings.
European, U. (15 December 2022). European digital-
ization vision. https://www.europarl.europa.eu, Re-
trieved(July 14,2023).
Garousi, V., Rainer, A., Lauv
˚
as Jr, P., and Arcuri, A. (2020).
Software-testing education: A systematic literature
mapping. J. of Systems and Software, 165:110570.
G
´
omez, G., Espina, E., and Armas-Aguirre, J. M. M.
(2021). Cybersecurity architecture functional model
for cyber risk reduction in iot based wearable devices.
In 2021 Congreso Internacional de Innovaci
´
on y Ten-
dencias en Ingenier
´
ıa, pages 1–4. IEEE.
Heiding, F., S
¨
uren, E., Oleg
˚
ard, J., and Lagerstr
¨
om, R.
(2023). Penetration testing of connected households.
Computers & Security, 126:103067.
Infastructure, A. S. (22 November 2022). Ama-
zon cloud security – amazon web services (aws).
https://aws.amazon.com, Retrieved(July 14,2023).
Jaber, A. and Fritsch, L. (2022). Towards ai-powered cyber-
security attack modeling with simulation tools: Re-
view of attack simulators. In Int. Conf. on P2P, Paral-
lel, Grid, Cloud and Internet Computing, pages 249–
257. Springer.
Kirk, R., Nguyen, H. N., Bryans, J., and Shaikh (2023). A
formal framework for security testing of automotive
over-the-air update systems. J.of Logical and Alge-
braic Methods in Programming, 130:100812.
Pawlicka, A., Pawlicki, M., Kozik, R., and Chora
´
s, M.
(2022). Human-driven and human-centred cybersecu-
rity: policy-making implications. Transforming Gov-
ernment: People, Process and Policy, 16(4):478–487.
Pearlson, K. and Huang, K. (2022). Design for cybersecu-
rity from the start. MIT Sloan Management Review,
63(2):73–77.
Rajabion, L. (2023). Industry 5.0 and cyber crime security
threats. In Advanced Research and Real-World Appli-
cations of Industry 5.0, pages 66–76. IGI Global.
Security, G. C. (2 August 2020). Google cloud blogs.
google cloud solutions. https://cloud.google.com, Re-
trieved(July 14,2023).
Srujana, S., Sreeja, P., Swetha, G., and Shanmugasundaram,
H. (2022). Cutting edge technologies for improved
cybersecurity model: A survey. In 2022 International
Conference on Applied AI and Computing (ICAAIC).
Straub, J. (2020). Software engineering: The first line of
defense for cybersecurity. In 2020 IEEE 11th Int.
Conf. on Software Engineering and Service Science
(ICSESS), pages 1–5. IEEE.
Tahaei, M. and Vaniea (2023). Embedding privacy into de-
sign through software developers: Challenges and so-
lutions. IEEE Security & Privacy, 21(1):49–57.
Trustmark, I. S. (2 December 2021). Baseline iot cyberse-
curity requirements. https://trustmark.tech/baseline/,
Retrieved(July 14,2023).
Varma, A. J., Taleb, N., Said, R. A., Ghazal, T. M., Ahmad,
M., Alzoubi, H. M., and Alshurideh, M. (2023). A
roadmap for smes to adopt an ai based cyber threat in-
telligence. In The Effect of IT on Business and Market-
ing Intelligence Systems, pages 1903–1926. Springer.
WhiteHouse, N. C. (12 May 2021). Executive
order on improving the nation’s cybersecurity.
https://www.whitehouse.gov, Retrieved(July 14 2023).
Zaghloul, Z. S., Elsayed, N., Li, C., and Bayoumi, M.
(2021). Green iot system architecture for applied au-
tonomous network cybersecurity monitoring. In 2021
IEEE 7th World Forum on IoT (WF-IoT), pages 628–
632. IEEE.
The Impact of IOT Cybersecurity Testing in the Perspective of Industry 5.0
487
