
How to Design a Blue Team Scenario for Beginners on the Example of
Brute-Force Attacks on Authentications
Andreas Eipper and Daniela P
¨
ohn
a
Universit
¨
at der Bundeswehr M
¨
unchen, Neubiberg, Germany
Keywords:
Cyber Range, Scenario Design, Brute-Force Attack, Training Scenario.
Abstract:
Cyber attacks are ubiquitous and a constantly growing threat in the age of digitization. In order to protect
important data, developers and system administrators must be trained and made aware of possible threats.
Practical training can be used for students alike to introduce them to the topic. A constant threat to websites
that require user authentication is so-called brute-force attacks, which attempt to crack a password by system-
atically trying every possible combination. As this is a typical threat, but comparably easy to detect, it is ideal
for beginners. Therefore, three open-source blue team scenarios are designed and systematically described.
They are contiguous to maximize the learning effect.
1 INTRODUCTION
The world is becoming more and more connected
through digital systems. According to (Lord, 2020),
users have between 80 and 150 online accounts, in-
cluding social media, online banking, and many more.
With the help of publicly available information and
basic hacking skills, many authentication systems can
be infiltrated or compromised, giving attackers access
to users’ personal information. Each user should pro-
tect their accounts with individual secure passwords.
In practice, users tend to use single passwords for
multiple services. This increases the impact of a se-
curity incident. Simple passwords, such as 123456,
test1, qwerty, iloveyou and others in wordlists
like rockyou.txt, can be easily cracked. Social en-
gineering and online research, also called open source
intelligence (OSINT), help hackers figure out valid
passwords. The information obtained can automate
brute-forcing as the attack progresses. As a result of
various incidents and attacks (e. g., data leaks, brute-
force attacks, and phishing), lists of user names and
passwords can be found on the Internet. Credential
stuffing is, for example, an attack that automatically
tries these stolen credentials for other services.
The aim of this paper is to impart knowledge and
skills in the field of detection and countermeasures to
participants in cyber range training courses by design-
ing and implementing open-source blue team scenar-
a
https://orcid.org/0000-0002-6373-3637
ios with the topic of brute-force attacks on authentica-
tion in a web application. Three subsequent scenarios
each cover a specific part of the learning content and
lay the foundation for beginners and those interested
in protection against brute-force attacks.
Therefore, this paper contributes 1) the design
process for beginner scenarios; 2) a description of the
overall training setting and each scenario in a generic
way; 3) an evaluation based on a training session.
The paper is structured as follows: Related work is
introduced in Section 2. Next, the concept of the three
beginner scenarios is outlined. This is the basis for the
practical implementation in Section 4, which is then
tested with students, as described in Section 5, and
discussed in Section 6. Last but not least, the paper is
concluded and future work is given in Section 7.
2 RELATED WORK
This chapter evaluates related work to brute-force de-
tection and prevention as well as cyber training and
training scenarios. To the best of our knowledge,
there is no training for learning about brute-force de-
tection and prevention.
Brute-Force Detection and Prevention: Applying
detection techniques is important to detect anoma-
lous behavior early and minimize its impact on the
network. One such application is Wireshark, as de-
Eipper, A. and Pöhn, D.
How to Design a Blue Team Scenario for Beginners on the Example of Brute-Force Attacks on Authentications.
DOI: 10.5220/0011667300003405
In Proceedings of the 9th International Conference on Information Systems Security and Privacy (ICISSP 2023), pages 477-484
ISBN: 978-989-758-624-8; ISSN: 2184-4356
Copyright
c
2023 by SCITEPRESS – Science and Technology Publications, Lda. Under CC license (CC BY-NC-ND 4.0)
477

scribed by (Mohammed et al., 2017). The authors rea-
son that the automatic ban function of FileZilla is not
enough to stop a brute-force attack. Therefore, they
recommend deactivating the targeted account. This
is possible if only single or selected accounts are un-
der attack. Other important sources for detection are
log files. Apache hypertext transfer protocol (HTTP)
server offers different log files, including error.log
(diagnosis information and errors) and access.log
(processed requests). Based on these log files, dif-
ferent attacks can be noticed by personnel if the at-
tacks are known (Meyer, 2021; Simic, 2019). How-
ever, it also requires training to detect attacks, either
manually or with the aid of tools. (Lopez-Araiza and
Cankaya, 2017) describe tools for network security
and forensics including Fail2Ban, which provides de-
tection and ban functionalities.
Cyber Training: To achieve pedagogical added
value, it is important to design the training compe-
tently. (G
´
alikov
´
a et al., 2021) provide guidelines on
how training can be effectively designed using the
principle of serious games. The training is intended to
reproduce realistic environments that require strategic
and adversarial thinking. (Kn
¨
upfer et al., 2020) cate-
gorize cyber training. (Kaschow et al., 2017) exam-
ined several training courses to determine their added
value for network defense. The authors conclude that
the representation of realistic and comprehensible at-
tack scenarios with different patterns leads to a high
learning effect. The training should be accompanied
by specialist staff. A high proportion of practical
exercises can reduce the duration of training while
achieving higher learning goals. In addition, different
online learning platforms provide gamified real-world
labs as evaluated by (Stu et al., 2022).
Training Scenarios: (Al-Mohannadi et al., 2016)
specify cyber attacks by applying the diamond model,
consisting of an adversary, capability, infrastructure,
and victim. These categories can be applied for train-
ing scenarios as well, but are not specific enough.
(Nagarajan et al., 2012) give an overview of game
design for cyber security training, whereas (Kout-
souris et al., 2021) analyze evaluation metrics for cy-
ber security training. (Subas¸u et al., 2017) propose
amongst other things a workflow diagram for training
exercises, describing the main steps objectives; envi-
ronment configuration; design and deploy; train test
score; and analyze evaluate adjust. Although these
steps can be applied, they are rather generic. The
design and use cases of the KYPO cyber ranges are
presented by (Vykopal et al., 2017). In their docu-
mentation, (Masaryk University, 2022) state how to
use their patterns to design use cases and workflows.
Even though it is a systematic approach, it is fo-
cused on their environment. Similarly, (Arshad et al.,
2021) propose a domain-specific language based on
the MITRE ATT&CK framework for dynamic train-
ing in cyber range environments. The authors de-
scribe the classification, environment, execution, and
evaluation in a systematic, but also high-level way.
Summary: Skills in network analysis is a core task
for blue teams. Training designed for beginners is
hardly described. We did not find any training on
brute-force attacks related to authentication. There-
fore, we provide a step-by-step guide and a generic
description of the scenarios, which can be repurposed
for other training settings.
3 CONCEPT
This chapter outlines the theoretical composition and
structure of the designed beginner scenarios. The de-
scription of the structure of the three subsequent sce-
narios is based on (Kn
¨
upfer et al., 2020). Thereby, the
audience, training environment, training setup, and
technical setup are defined in general. In addition, the
scenario, goals, and resources are explained in more
detail. This is supplemented with a possible proce-
dure based on related work, described in Section 2.
Based on the received feedback, see Section 5, pre-
requisites are necessary to pre-access.
3.1 Overview
Audience: The target audiences are students and
other interested persons with basic cyber security
knowledge. Thereby, the prerequisite consists of the
knowledge gained in a bachelor’s program. Hence,
the sector is described as universities and the pro-
ficiency level is the related audience. The training
has the purpose to increase the ability to detect brute-
force attacks on authentication of websites, thereby,
using log files and Wireshark, resp. understanding of
intrusion prevention.
Training Environment: The training is carried out
in dedicated computer rooms or in our cyber range.
With the goal to understand brute-force attacks on au-
thentication, their detection, and prevention, the mate-
rial is divided into three distinct scenarios. Each sce-
nario covers a certain aspect to learn basic knowledge:
1. Wireshark: As a visual instrument for analyzing
and graphically processing data logs (Usha et al.,
ICISSP 2023 - 9th International Conference on Information Systems Security and Privacy
478
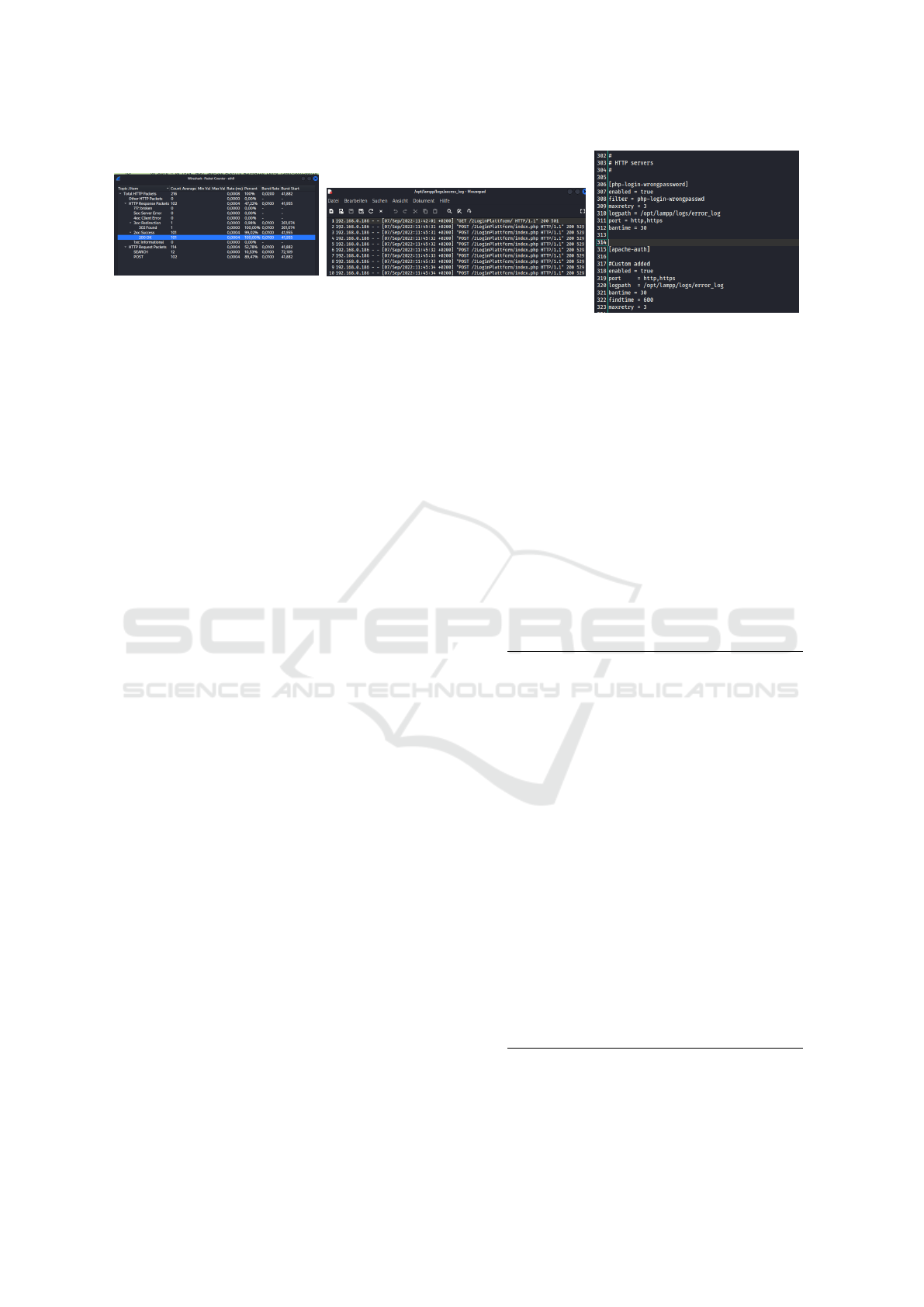
(a) Scenario 1: Package analysis in
Wireshark.
(b) Scenario 2: Excerpt of log files.
(c) Scenario 3: Rules in Fail2Ban.
Figure 1: Scenarios.
2010; Mohammed et al., 2017). In addition, Wire-
shark could be used in advanced scenarios with no
suitable log files.
2. Log Files: As a system-related and fast source of
information and supplement to Wireshark. Log
files are utilized in more advanced tools. (Meyer,
2021; Simic, 2019)
3. Fail2Ban: As a simple tool for intrusion preven-
tion (Lopez-Araiza and Cankaya, 2017).
The first two scenarios cover intrusion detection. In
the last scenario, Fail2Ban is presented as an intru-
sion prevention system (IPS) for blue teams. Thereby,
the participants first see the malicious traffic graphi-
cally, before analyzing the in-going traffic with the
command line. Last but not least, a prevention possi-
bility is explained. The topics are coherent and can,
therefore, be dealt with in one go for maximum learn-
ing effect. For added pedagogical value, the diamond
framework (Al-Mohannadi et al., 2016) and the cyber
kill chain can be used as an aid. In addition, follow-on
topics can be discussed.
Training Setup: No scoring is set up in these three
basic scenarios as the primary goal is to introduce the
participants to the concepts and handling of Kali and
its tools. Scoring can be applied in advanced scenar-
ios to challenge the participants. The participants act
as a blue team in single mode at a general level.
Technical Setup: The scenarios try to rebuild a
simplified realistic environment structure. The de-
ployment is on-premise with a resp. several virtual
machines (VMs) due to the architecture of our TAME
range, as outlined by (Shin et al., 2019). Although
VMware is the primary installation, VirtualBox or
other products could be imported.
Description: The training concept can be summa-
rized as in Listing 1. First, a description of the scenar-
ios (name, goal, scoring, and environment) is given
(Lines 3-7). Then the set of scenarios with each sce-
nario, intended tool, and goal are generally stated
(Lines 8-20). This description language is based on
related work in Section 2. It tries to balance detailed
information and generic representation. The descrip-
tion utilizes JavaScript Object Notation (JSON) as a
prominent candidate for descriptions on the Internet,
similar to the related work. Depending on the cyber
range, either automated provisioning with tools such
as Vagrant and Puppet or VMs are set up (Shin et al.,
2019). In consequence, the descriptions either result
(with translation) in automated provisioning or can be
used to build the VMs. The scenarios and the techni-
cal setup need to be detailed in further descriptions.
Listing 1: Training description.
1 {
2 " training ": {
3 " desc r i p t i o n ": {
4 " nam e " : " Brute - F o rce AuthN ",
5 " goa l " : " analyze ",
6 " scoring ": " n one ",
7 " envi r o n m e n t ": " c y ber range ",
8 " scenarios " : [
9 {
10 " scenario ": " network traffic ",
11 " too l " : " Wires h a r k " ,
12 " goa l " : " un d e r s t a n d " ,
13 }, {
14 " scenario ": " logging ",
15 " too l " : " log f i les ",
16 " goa l " : " apply " ,
17 }, {
18 " scenario ": " I PS ",
19 " too l " : " Fail 2 Ban " ,
20 " goa l " : " analyze ",
21 }
22 ]
23 },
24 }
25 }
How to Design a Blue Team Scenario for Beginners on the Example of Brute-Force Attacks on Authentications
479

3.2 Scenario 1: Wireshark
Training Environment: The scenario provides the
participants with a VM to work on. The aim is to
discover abnormalities in the packet capture (PCAP)
files. The following learning objectives are aimed for
in this scenario.
• Wireshark basics:
– Operation of the tool.
– Filter application.
– Statistics creation and evaluation.
• Detection of simple brute-force attacks.
• Awareness of log files.
Training Setup: The lecturer discusses the basics
of Wireshark and brute-force attacks, in order to
create a theoretical understanding. The participants
search for and open the PCAP file in Wireshark and
try to recognize the attack, shown in Figure 1a. Then,
mitigation strategies are discussed.
Technical Setup: The participants use a stored
PCAP file.
3.3 Scenario 2: Log Files
Training Environment: The aim is to discover
anomalies in the log files and to include them in the
analysis results of scenario 1. The following learning
objectives are aimed for in this scenario.
• Basics Log Files:
– Types of log files.
– Locations of log files on Debian distributions.
– Evaluation of log files.
• Detection of brute-force attacks.
• Awareness of log files.
Training Setup: After an introduction to log files,
the participants search for and open the log files and
analyze them accordingly (pattern, IP addresses, in
combination with the PCAP file).
Technical Setup: The participants use the accord-
ing log files access.log and error.log.
3.4 Scenario 3: Fail2Ban
Training Environment: The goal is to activate the
Fail2Ban configuration and demonstrate the capabili-
ties of the tool in a practical demonstration. This sce-
nario has the following learning objectives.
• Intrusion Prevention Basics:
– Functionality.
– Areas of application.
• Basics Fail2Ban:
– Theoretical functionality.
– Practical implementation.
Training Setup: The lecturer summarizes the re-
sults from the previous scenarios to create a basis for
discussions on ways to combat brute-force attacks.
After collecting and evaluating ideas and suggestions,
Fail2Ban and intrusion prevention, in general, are pre-
sented. Once the theoretical basis has been created,
Fail2Ban is installed and configured. The proper-
ties of the local.jail file and the necessary com-
mands for activation are shown here, see Figure 1c.
The functionality is demonstrated using an example
attack. Finally, possible errors and weaknesses of
Fail2Ban are discussed with the participants.
Technical Setup: The participants use Fail2Ban
with its configuration and log files.
4 IMPLEMENTATION
The implementations and technical precautions re-
quired to carry out the training are described in this
section. The implementation can be summarized as in
Listing 2. First, a description of the implementation is
given (Lines 3-5). Then the environment featuring the
different teams, i. e., blue team (Lines 7-19), red team
(Lines 20-23), and yellow team (Lines 24-27), is sum-
marized. This especially includes platforms, tools, IP
addresses, and resources.
Listing 2: Implementation description.
1 {
2 " training ": {
3 " desc r i p t i o n ": {
4 " nam e " : " Brute - F o rce AuthN ",
5 " scenario s " : " 3 " ,
6 }, " environm e n t " : {
7 " blueteam ": {
8 " platform " : " Kal i L i nux ",
9 " tools " : [ " W i r e s h ark ", " log
files " , " Fail 2 Ban " ] ,
10 " ip ": "19 2 . 168 . 1 .1 0 " ,
11 " in f r a s tructur e " : {
12 " nam e " : " WebApp ",
13 " goa l " : " web appli c a t i o n " ,
14 " tools " : [ " PHP " , " A p ache ", "
phpMyA d m i n " ],
15 " sources ": [" P HP pages " ,
ICISSP 2023 - 9th International Conference on Information Systems Security and Privacy
480

16 "/ v ar / log /*" ,
17 "/ o pt / lam p p / logs /*" ,
18 "/ e tc / f a il 2 ban / jai l . local " ]
,
19 },
20 }, " redteam " : {
21 " platform " : " Kal i L i nux ",
22 " tools " : [ " F i r e f o x " , " Burp
Suite " , " F o x y P r o x y " ],
23 " ip ": "19 2 . 168 . 2 .1 - 1 00" ,
24 }, " yellowteam " : {
25 " platform " : " Windows 1 1 " ,
26 " tools " : [ " C h rome " , " Selenium "]
,
27 " ip ": "19 2 . 168 . 2 .1 - 1 00" ,
28 },
29 }
30 }
31 }
As a basis for the blue and red team platforms,
VMs are created with Oracle VM VirtualBox and Kali
Linux as the operating system. Alternatively, Debian
could be used for blue teams.
The web application of the infrastructure is cre-
ated with the LAMPP/XAMPP framework (PHP,
Apache, MariaDB, and phpMyAdmin) by (Adobe,
2023). It consists of five PHP files: a login page,
homepage, registration page, logout page, and a con-
nection page to the database. The data required for
the web application is stored in the database. The log
files can be found at the default location. In addition,
several tools for the analysis are available or can be
installed, such as Fail2Ban.
In order to simulate the attacks (red team), the
Burp Suite (Port Swigger, 2022) is utilized. Burp
Suite is a tool developed by Portswigger Web Security
with the ability to act as a proxy for manual testing
of web applications. Other applications such as THC
Hydra, Medusa, and Patator as shown by (Offensive
Security, 2023a) could be used instead but Burp Suite
provides a graphical interface and is often applied
for website testing. Burp Suite is triggered by the
browser plugin (FoxyProxy, 2023). Burp Suite Proxy
and Intruder (tryhackme, 2021) catch the request to
the target. The attacker then can modify it to start the
brute-force attack as shown in Figure 2a. With chang-
ing IP addresses through the usage of proxies, Tor, or
virtual private networks (VPNs), a distributed attack
can be imitated, if no distributed setting is available.
Alternatively, editing files is possible.
The tool selected to generate ordinary network
traffic is Selenium (Ramya et al., 2017). Origi-
nally, Selenium is a portable testing framework pri-
marily focused on testing web-based applications.
It provides a record-playback feature that helps in
recording test case executions and allows testers to
play them back at a later time as shown in Fig-
ure 2b. Thereby, simple user behavior can be sim-
ulated (Tanaka et al., 2020; Srinivasa Rao and Pais,
2017). A new test is first started and then a login pro-
cess is recorded. These and other tests can be run
as often as you like at later times, thereby, simulat-
ing regular user behavior. This has the advantage of a
simple generation. On the other hand, it replays with-
out much variation.
5 EVALUATION BASED ON
TRAINING SESSION
We evaluate the training scenarios and their descrip-
tion through a small-scale training session with stu-
dents. In order to test the learning effects of the
scenarios, a training session was conducted. The
participants were predominantly male, young, and
technical-savvy. They had a rudimentary knowledge
of cyber security. The following criteria were evalu-
ated during the training and subsequent assessment:
Sources of Information: The participants had mate-
rial about brute-force attacks. The material was
described as comprehensive and intuitive in terms
of structure and writing style. During the train-
ing, it turned out that the amount of information
material becomes confusing for beginners due to
the complexity and the missing knowledge about
Linux and the command line.
Training Structure: The structuring was empha-
sized positively. However, the training revealed
slower learning progress than expected. Neverthe-
less, all participants successfully completed the
training within the allocated and some buffer time.
One possible option could be to separate the sce-
narios based on their properties. Another option
would be to add an informative session before-
hand to explain the theory. This though would
extend the training time in total (Kaschow et al.,
2017). Last but not least, the Linux OS Kali and
the command line could be introduced in another
session. Several courses about Kali can be found
online, including the official course PEN-103 by
(Offensive Security, 2023b).
Training Process: The guide was positively received
and was effective according to all participants.
Here too, however, the beginner-typical deficits
came clear. Basics such as operating the OS Kali,
in particular using the command line to configure
Fail2Ban, also had to be explained.
In summary, the training was positively received by
all. The learning effect and awareness of cyber secu-
How to Design a Blue Team Scenario for Beginners on the Example of Brute-Force Attacks on Authentications
481

(a) Data in Burp Suite Intruder.
(b) Recorded sessions in Selenium.
Figure 2: Implementation.
rity were evident. Due to the lack of basic understand-
ing, it is advisable to verify the required knowledge
and locate time accordingly. The preferred option for
our training session is to include a pre-session about
Linux and Kali in particular, where the students can
familiarize themselves with the command line.
6 DISCUSSION
Based on the concept and practical implementation
of the subsequent training sessions, we discuss major
elements of our beginner training.
Design of Beginner Scenarios: By applying the
cyber taxonomy (Kn
¨
upfer et al., 2020), we used a sys-
tematic approach to design and describe our begin-
ner scenarios. Based on the goals and learning skills,
three subsequent scenarios were created. Whereas
several cyber range architectures and the usage of cy-
ber training for educating students are published, we
found no beginner scenarios in the literature. This
workflow can be applied to future scenarios. Al-
though it suited our purpose, a refined version might
be required for advanced cyber range scenarios. In
addition, prerequisites need to be verified.
Network Traffic: Realistic synthetic network traf-
fic is an important element of cyber training. (Adeleke
et al., 2022) provide a categorization of different tools
and methodologies applied. The overview shows that
there is no standard solution so far. We applied Se-
lenium, which is not included in the overview, as we
focused on web application authentication and the re-
play of recorded sessions suits the purpose. Never-
theless, it is not realistic enough for more advanced
scenarios.
Structured Description Language: The designed
subsequent scenarios target beginners and, therefore,
do not consist of a complicated setting such as in
(Masaryk University, 2022). Even though the first ap-
proaches presented structured description languages,
no standard has been established yet. In contrast to the
examples accompanying these structured description
languages, our scenarios are comparably easy and,
therefore, do not fit. We tried to adapt them to our
scenarios. Contrary, our description language fits our
purpose but is not suited for complex settings. There-
fore, further work is required toward an advanced de-
scription language for different scenarios.
Content: According to (Walden, 2008), web appli-
cation security should be integrated into IT curricu-
lum. Our subsequent scenarios cover selected topics
around authentication and operational security and re-
quire web application input. With the increasing num-
ber of digital identities and different identity manage-
ment protocols, this is also true for identity manage-
ment security. Our scenarios provide the first step. In
order to teach web application security resp. identity
management, additional scenarios are necessary.
Summary: In summary, our three consecutive sce-
narios provide a first step towards detecting and mit-
igating brute-force attacks on authentication in web
applications. It utilizes basic functionalities and
tools for a better understanding and an easier start.
Thereby, the participants see the effects of brute-force
attacks by Wireshark and log files and simple pre-
vention by Fail2ban. This knowledge helps to apply
and evaluate tools for better discovery and prevention.
This setting can be transferred to different environ-
ments by utilizing the description language. Depend-
ing on the organization and infrastructure, other tools,
such as security information and event management
(SIEM), and Windows OS may be available. For fur-
ther training, more scenarios are required.
ICISSP 2023 - 9th International Conference on Information Systems Security and Privacy
482

7 CONCLUSIONS
The number of digital accounts is ever-increasing.
The same is the case with attacks on them, ranging
from brute-force attacks to sophisticated supply chain
attacks targeting active directory environments. In or-
der to train beginners, we designed a series of blue
team scenarios with the topic of brute-force attacks
on authentication in a web application. In the first
step, we evaluated related work. With the help of the
results obtained, three consecutive scenarios for the
cyber range were designed and implemented. These
scenarios each cover a specific part of the learning
content and lay the foundation for beginners and those
interested in protection against brute-force attacks.
Nonetheless, more scenarios are required to train fu-
ture system administrators. Finally, the open-source
scenarios were assessed in a small-scale training and
a discussion.
In future work, we plan to extend the scenarios to
cover different attacks on identities and identity man-
agement systems, such as the more advanced attacks
of Kerberoasting, Golden Ticket, and Golden SAML,
and other OSs, in particular Windows. In addition, we
will evaluate and improve our description language
with these scenarios and discuss it with other experts.
For the brute-force scenarios, regular traffic was gen-
erated with Selenium. We want to investigate other
techniques and represent the traffic more realistically
for a better training setup in future work.
REFERENCES
Adeleke, O. A., Bastin, N., and Gurkan, D. (2022). Network
Traffic Generation: A Survey and Methodology. ACM
Comput. Surv., 55(2).
Adobe (2023). XAMPP Apache + MariaDB + PHP + Perl.
https://www.apachefriends.org/index.html. accessed
January 11, 2023.
Al-Mohannadi, H., Mirza, Q., Namanya, A., Awan, I.,
Cullen, A., and Disso, J. (2016). Cyber-Attack Mod-
eling Analysis Techniques: An Overview. In Proceed-
ings of the 4th International Conference on Future In-
ternet of Things and Cloud Workshops (FiCloudW),
pages 69–76. IEEE.
Arshad, S., Alam, M., Al-Kuwari, S., and Khan, M. H. A.
(2021). Attack Specification Language: Domain
Specific Language for Dynamic Training in Cyber
Range. In Proceedings of the 12th Global Engineering
Education Conference (EDUCON), pages 873–879.
IEEE.
FoxyProxy (2023). FoxyProxy. https://getfoxyproxy.org.
accessed January 11, 2023.
G
´
alikov
´
a, M.,
ˇ
Sv
´
abensk
´
y, V., and Vykopal, J. (2021). To-
ward Guidelines for Designing Cybersecurity Serious
Games. In Proceedings of the 52nd Technical Sympo-
sium on Computer Science Education (SIGCSE), page
1275. Association for Computing Machinery.
Kaschow, R., Hanka, O., Kn
¨
upfer, M., and Eiseler, V.
(2017). Cyber Range: Netzverteidigung trainieren
mittels Simulation. In Proceedings of the D•A•CH Se-
curity 2017, pages 126–137. syssec.
Kn
¨
upfer, M., Bierwirth, T., Stiemert, L., Schopp, M., See-
ber, S., P
¨
ohn, D., and Hillmann, P. (2020). Cyber
Taxi: A Taxonomy of Interactive Cyber Training and
Education Systems. In Hatzivasilis, G. and Ioanni-
dis, S., editors, Model-driven Simulation and Training
Environments for Cybersecurity, pages 3–21, Cham.
Springer International Publishing.
Koutsouris, N., Vassilakis, C., and Kolokotronis, N. (2021).
Cyber-Security Training Evaluation Metrics. In Pro-
ceedings of the 1st International Conference on Cyber
Security and Resilience (CSR), pages 192–197. IEEE.
Lopez-Araiza, C. and Cankaya, E. (2017). A Comprehen-
sive Analysis of Security Tools for Network Foren-
sics. Journal of Medical - Clinical Research & Re-
views, 1(3):1–9.
Lord, N. (2020). Uncovering Password Habits: Are
Users’ Password Security Habits Improving?
https://digitalguardian.com/blog/uncovering-
password-habits-are-users-password-security-
habits-improving-infographic. accessed January 11,
2023.
Masaryk University (2022). KYPO Cyber Range Platform.
https://docs.crp.kypo.muni.cz. accessed January 11,
2023.
Meyer, R. (2021). Detecting Attacks on Web Applications
from Log Files. techreport, SANS Institute.
Mohammed, M. A., Degadzor, A. F., Effrim, B. F., and
Appiah, K. A. (2017). Brute Force Attack detection
and prevention on a network using wireshark analy-
sis. International Journal of Engineering Sciences &
Research Technology, 6(6):26–37.
Nagarajan, A., Allbeck, J. M., Sood, A., and Janssen,
T. L. (2012). Exploring game design for cyberse-
curity training. In Proceedings of the International
Conference on Cyber Technology in Automation, Con-
trol, and Intelligent Systems (CYBER), pages 256–
262. IEEE.
Offensive Security (2023a). All Kali Tools. https://www.
kali.org/tools/all-tools/. accessed January 11, 2023.
Offensive Security (2023b). PEN-103 Modules.
https://portal.offensive-security.com/courses/pen-
103/books-and-videos/modules. accessed January
11, 2023.
Port Swigger (2022). Burp Suite documentation. https:
//portswigger.net/burp/documentation. accessed Jan-
uary 11, 2023.
Ramya, P., Sindhura, V., and Sagar, P. V. (2017). Testing us-
ing selenium web driver. In Proceedings of the 2nd In-
ternational Conference on Electrical, Computer and
Communication Technologies (ICECCT), pages 1–7.
IEEE.
Shin, S., Seto, Y., Kasai, Y., Ka, R., Kuroki, D., Toyoda,
S., Hasegawa, K., and Midorikawa, K. (2019). De-
How to Design a Blue Team Scenario for Beginners on the Example of Brute-Force Attacks on Authentications
483

velopment of Training System and Practice Contents
for Cybersecurity Education. In Proceedings of the
8th International Congress on Advanced Applied In-
formatics (IIAI-AAI), pages 172–177. IEEE.
Simic, S. (2019). How to View Apache Access & Error
Logs. https://phoenixnap.com/kb/apache-access-log.
accessed January 11, 2023.
Srinivasa Rao, R. and Pais, A. R. (2017). Detecting Phish-
ing Websites Using Automation of Human Behav-
ior. In Proceedings of the 3rd Workshop on Cyber-
Physical System Security (CPSS), page 33–42. Asso-
ciation for Computing Machinery.
Stu, S., Ananth, J., and de Leon Daniel, C. (2022). A Survey
of Cloud-hosted, Publicly-available, Cyber-ranges for
Educational Institutions. Journal of Computing Sci-
ences in Colleges, 38.
Subas¸u, G., Ros¸u, L., and B
˘
adoi, I. (2017). Modeling And
Simulation Architecture For Training In Cyber De-
fence Education. In Proceedings of the 9th Interna-
tional Conference on Electronics, Computers and Ar-
tificial Intelligence (ECAI), pages 1–4. IEEE.
Tanaka, T., Niibori, H., Shiyingxue, L., Nomura, S., Nakao,
T., and Tsuda, K. (2020). Selenium based Testing Sys-
tems for Analytical Data Generation of Website User
Behavior. In Proceedings of the 13th International
Conference on Software Testing, Verification and Val-
idation Workshops (ICSTW), pages 216–221. IEEE.
tryhackme (2021). Burp Suite: Intruder. https://tryhackme.
com/room/burpsuiteintruder. accessed January 11,
2023.
Usha, B., Ashutosh, V., and Saxena, M. (2010). Evaluation
of the Capabilities of WireShark as a tool for Intrusion
Detection. International Journal of Computer Appli-
cations, 6(7):1–5.
Vykopal, J., Oslejsek, R., Celeda, P., Vizvary, M., and
Tovarnak, D. (2017). KYPO Cyber Range: Design
and Use Cases. In Proceedings of the 12th Inter-
national Conference on Software Technologies (IC-
SOFT), pages 310–321. INSTICC, SciTePress.
Walden, J. (2008). Integrating Web Application Security
into the IT Curriculum. In Proceedings of the 9th SIG-
ITE Conference on Information Technology Education
(SIGITE), page 187–192, New York, NY, USA.
ICISSP 2023 - 9th International Conference on Information Systems Security and Privacy
484
