
On the Feasibility of Fully Homomorphic Encryption of Minutiae-Based
Fingerprint Representations
Pia Bauspieß
1,2 a
, Lasse Vad
1
, H
˚
avard Myrekrok
1
, Anamaria Costache
1 b
, Jascha Kolberg
2 c
,
Christian Rathgeb
2 d
and Christoph Busch
1,2 e
1
NTNU – Norwegian University of Science and Technology, Norway
2
da/sec - Biometrics and Security Research Group, Hochschule Darmstadt, Germany
Keywords:
Fingerprint Template Protection, Minutia-Based Fingerprint Representations, Fully Homomorphic
Encryption, Post-Quantum Security.
Abstract:
Protecting minutiae-based fingerprint templates with fully homomorphic encryption has recently been recog-
nised as a hard problem. In this work, we evaluate state-of-the-art fingerprint recognition based on minutiae
templates using post-quantum secure fully homomorphic encryption that operates directly on floating point
numbers, such that no simplification or quantisation of the comparison algorithm is necessary. In a practical
evaluation on a publicly available dataset, we run a benchmark and provide directions for future work.
1 INTRODUCTION
Fingerprint patterns allow for an irrevocable and
accurate identification of individuals over several
decades (Kessler et al., 2021). Images and templates
representing such patterns have therefore, along with
other biometric data, been recognised as sensitive per-
sonal data by the European Union’s General Data Pro-
tection Regulation and the ISO/IEC 24745 (ISO/IEC
JTC1 SC27 Security Techniques, 2022) standard.
In its most recent version from 2022, the standard
places particular emphasis on Biometric Information
Protection (BIP) in the presence of quantum com-
puters. In their Quantum Manifesto (EU Parliament,
2016), the European Union expects quantum comput-
ers to pose a realistic threat within the next 15 years.
Comparing this time frame to the the retention period
for biometric systems ranging from 5 (European Data
Protection Supervisor, 2018) up to 12 years (Kessler
et al., 2021), it becomes evident that long-term pro-
tection of biometric data needs to be addressed today.
More concretely, access to a quantum computer
would allow an attacker to break the unlinkability,
a
https://orcid.org/0000-0003-0225-1674
b
https://orcid.org/0000-0001-8793-6116
c
https://orcid.org/0000-0002-3128-8049
d
https://orcid.org/0000-0003-1901-9468
e
https://orcid.org/0000-0002-9159-2923
irreversibility, and renewability assurances of classi-
cally protected BIP systems, leaving the enrolment
data vulnerable for malicious exploitation. These
three requirements are defined in ISO/IEC 24745
(ISO/IEC JTC1 SC27 Security Techniques, 2022) as
i) unlinkability, two protected templates stored in dif-
ferent applications cannot be linked to the same sub-
ject, ii) renewability, new templates can be created
from the same biometric instance without the need
to re-enrol, and iii) irreversibility, it is impossible
to retrieve original templates given only protected
templates. Considering the quantum challenge, this
work proposes a BIP system that achieves long-term
protection according to the standard’s requirements
through the use of post-quantum cryptography.
However, the lift to post-quantum security does
not come without challenges. In particular, the com-
bination of accurate minutiae-based fingerprint recog-
nition and BIP through Fully Homomorphic Encryp-
tion (FHE) has recently been recognised as a notori-
ous hard problem by leading researchers in biomet-
rics (Engelsma et al., 2019). So far, solutions have
only been proposed for fixed-length fingerprint rep-
resentations (Kim et al., 2020), or using classically
secure cryptography (Gomez-Barrero et al., 2017a).
The novelty and objective of this work is therefore to
evaluate minutiae-based fingerprint comparison with
FHE on floating point numbers, an encryption scheme
462
Bauspieß, P., Vad, L., Myrekrok, H., Costache, A., Kolberg, J., Rathgeb, C. and Busch, C.
On the Feasibility of Fully Homomorphic Encryption of Minutiae-Based Fingerprint Representations.
DOI: 10.5220/0011657100003405
In Proceedings of the 9th International Conference on Information Systems Security and Privacy (ICISSP 2023), pages 462-470
ISBN: 978-989-758-624-8; ISSN: 2184-4356
Copyright
c
2023 by SCITEPRESS – Science and Technology Publications, Lda. Under CC license (CC BY-NC-ND 4.0)

which enjoys increasing interest since its proposal in
2017 (Cheon et al., 2017). As a lattice-based FHE
scheme, its post-quantum security is provided by the
Ring-Learning with Errors (R-LWE) (Lyubashevsky
et al., 2010) hardness assumption.
This work presents post-quantum secure
minutiae-based fingerprint comparison algorithm
(Cappelli et al., 2010) using FHE, where the compar-
ison algorithm has not been simplified or quantised in
order to be compatible with the encryption scheme.
Furthermore, we highlight challenges inherent to
the application of FHE to minutiae-based fingerprint
comparison and provide an experimental benchmark
from which we draw conclusions for future work.
The rest of this paper is structured as follows:
Section 2 contextualises our contribution, before we
present our proposed system in Section 3. We give
an experimental evaluation in Section 4 and draw our
conclusions in Section 5.
2 RELATED WORK
Fingerprint recognition has historically been based
on minutiae, which are defined as ridge endings and
bifurcations of fingerprint ridges. While compari-
son algorithms with high accuracy have been devel-
oped (Cappelli et al., 2010; Va
ˇ
zan, 2021), they re-
flect the complexity inherent to comparing two sets
of minutiae such as rotation, non-linear transforma-
tion, and absence of an inherent ordering. In their
development, they have not necessarily considered
the application of encryption schemes, which offer
only a limited number of operations that can be com-
puted with feasible computational effort (Iliashenko
and Zucca, 2021). Therefore, two research directions
have emerged that approach the challenge of combin-
ing fingerprint recognition with encryption: one is to
develop fingerprint representations with simple dis-
tance functions as comparison metrics that maintain
high recognition accuracy, while the other is to apply
and adapt compatible encryption schemes to complex
minutiae-based comparators.
Indeed, FHE for fixed-length representations has
been proposed for different biometric modalities such
as face (Boddeti, 2018; Kolberg et al., 2020; Baus-
pieß et al., 2022) and iris (Kolberg et al., 2019) with
high accuracy and real-time efficiency. For fingerprint
specifically, the most prominent representation is Jain
et al.’s FingerCode (Jain et al., 2000). Notable works
on encrypting this representation include (Barni et al.,
2010; Gomez-Barrero et al., 2017b; Yang et al.,
2020). However, the encryption schemes used are
based on classical assumptions and do not hold in the
quantum age. A recent work using FHE with post-
quantum security on FingerCode templates is (Kim
et al., 2020). The FHE scheme (Chillotti et al., 2020)
applied here only tolerates binary values, which is
compatible with FingerCodes, but not with minutiae
templates.
Minutiae-based comparators share the difficulty
of finding close pairs within the sets of k reference
minutiae and l probe minutiae, the mapping between
which can be neither injective nor surjective due to
potential missing or spurious minutiae. In addition,
samples might be rotated, translated or distorted, re-
quiring either prealignment or a rotation-invariant ap-
proach. In theory, FHE allows for the evaluation
of arbitrary circuits on encrypted input data (Gentry,
2009). In practice however, both alignment and set
comparison are functions that can only be described
using conditional statements, the number of which in
prevalent approaches is high (Va
ˇ
zan, 2021; Zhang and
Koushanfar, 2016). Their combination with FHE is
therefore not straightforward, and more importantly
too costly for practical applications (Iliashenko and
Zucca, 2021). In contrast to that, the comparison
of alignment-free fixed-length representations can be
performed by computing a simple distance function
on the encrypted templates, the result of which is typi-
cally decrypted to evaluate the comparison against the
decision threshold.
Classically secure homomorphic encryption,
which is only partially or somewhat homomorphic
(Gentry, 2009), has been applied to minutiae-based
comparison (Gomez-Barrero et al., 2017a). However,
these schemes lack post-quantum security. This
is also true for a approaches based on cancelable
biometric templates constructed based on randomized
feature transformation, most recently represented
by an approach by (Rahman et al., 2022), which
do not adhere to formal secuirty proofs and are
vulnerable to unlinkability attacks. In particular, the
indistinguishability under chosen plaintext attacks
provided by (F)HE schemes, which gives formal
security in terms of ISO/IEC 24745 (ISO/IEC JTC1
SC27 Security Techniques, 2022) is not given in the
latter. Other works (Liu and Zhao, 2017; Zhang and
Koushanfar, 2016; Gilkalaye and Derakhshani, 2021)
have utilised secure multi-party computation (MPC),
which is generally speaking more flexible than FHE.
As a drawback, it introduces a communication over-
head, and practical post-quantum secure MPC has
only been explored recently (B
¨
uscher et al., 2020).
Table 1 gives a qualitative overview of the most
related works discussed in this Section and provides a
comparison against our proposed approach.
On the Feasibility of Fully Homomorphic Encryption of Minutiae-Based Fingerprint Representations
463

Table 1: Qualitative comparison of related work on cryptographic fingerprint template protection.
Reference
Template protection Cryptographic Variable-length Post-quantum
category scheme feature representation security
(Barni et al., 2010) HE
ElGamal (Elgamal, 1985)
7 7
Pailler (Paillier, 1999)
(Gomez-Barrero et al., 2017b)
HE Pailler (Paillier, 1999) 7 7
(Yang et al., 2020)
(Zhang and Koushanfar, 2016)
MPC Garbled Circuits (Yao, 1986) X 7
(Gilkalaye and Derakhshani, 2021)
(Gomez-Barrero et al., 2017a) HE Pailler (Paillier, 1999) X 7
(Kim et al., 2020) FHE TFHE (Chillotti et al., 2020) 7 X
Ours FHE CKKS (Cheon et al., 2017) X X
3 PROPOSED SYSTEM
We study a combination of the minutiae-based finger-
print comparison algorithm Minutia Cylinder-Code
(MCC) (Cappelli et al., 2010) and the state-of-the-
art FHE encryption scheme Cheon-Kim-Kim-Song
(CKKS) (Cheon et al., 2017) to illustrate the chal-
lenges that arise in the process.
3.1 Background
Before we describe our proposed system, we in-
troduce the necessary background in this Section.
Subsequently, we introduce the baseline verification
scheme without encryption, and finally, our proposed
protected system.
Throughout this work, we consider a biometric
system operating in verification mode. In a setup
phase, subjects are enrolled to the system with their
fingerprint features. During a verification transac-
tion, a fresh probe sample is captured a biometric
claim, i.e., the claimed identity of the data subject, is
transferred to the database along with the probe fea-
ture set. Then, a comparison between the probe fea-
tures and the reference template corresponding to the
claim is computed, resulting in a comparison score
in the range [0, 1], where 1 indicates highest similar-
ity. Finally, this score is compared against a prede-
termined decision threshold and the comparison trial
is accepted or rejected accordingly. In the follow-
ing section, we describe this comparison algorithm in
more detail.
3.1.1 Minutia Cylinder Code
Minutia Cylinder-Code (MCC) (Cappelli et al., 2010)
is a fingerprint comparison algorithm that takes as in-
put two minutiae-based fingerprint templates as stan-
dardized in ISO/IEC 19794-2 (ISO/IEC JTC1 SC37
Biometrics, 2011) and outputs a similarity score that
can further be used for an automated comparison.
Minutiae are significant points in the pattern of fin-
gerprint ridges: ridge endings and bifurcations, where
one ridge line splits into two. We remind the reader
of the following definition of an ISO/IEC 19794-2
(ISO/IEC JTC1 SC37 Biometrics, 2011) fingerprint
template in the notation of (Cappelli et al., 2010), Sec-
tion 3.
Definition 1 (Fingerprint Template). A fingerprint
template is an unordered set T = {m
i
}
N
i=1
of minu-
tiae m
i
, where N is the number of minutiae found in
a given fingerprint image. Each minutia is given as
a tuple m = (x
m
, y
m
, θ
m
) of its location in terms of x-
and y-coordinate (x
m
, y
m
) given in pixels from the left
upper corner of the sample together with its tangential
angle with respect to the x-axis θ
m
.
Note that the number of minutiae N varies be-
tween captures, not only between different subjects,
but also within repeated captures of the same in-
stance. This is due to noise during the capture pro-
cess: depending on the image quality and capture
conditions, minutiae can either be missed during fea-
ture extraction, or spurious minutiae can be added, re-
sulting in different length representations of the same
fingerprint. In addition, the location of the minu-
tiae are subject to fuzzyness, as their location and
angle can be distorted through rotation, translation
and non-linear transformations. Therefore, minutiae-
based fingerprint comparison comprises of the com-
plex problem of accurately comparing two unordered,
variable-sized sets of noisy points, a number of which
can be spurious.
To address the aforementioned challenges, MCC
introduces a local structure associated with each
minutiae referred to as a minutia cylinder. This
structure incorporates information about the neigh-
bourhood of each minutiae, i.e., further minutiae
ICISSP 2023 - 9th International Conference on Information Systems Security and Privacy
464

found in close proximity and their spatial and direc-
tional relationship with the center minutiae (Cappelli
et al., 2010). This approach ensures system interop-
erability as the cylinder representation is still based
on ISO/IEC 19794-2 (ISO/IEC JTC1 SC37 Biomet-
rics, 2011) fingerprint templates. In particular, the
variable-length representation is maintained, as the
number of minutia cylinders corresponds to the num-
ber of minutiae in a fingerprint template. We restate
the following definitions from (Cappelli et al., 2010),
Section 3.
Definition 2 (Minutia Cylinder). A minutia cylinder
is given by a fixed radius R and height 2π centered
around the location (x
m
, y
m
) of a minutia m. It is dis-
cretized into small cuboids, called cells, which are
orientated in the direction of the tangential angle θ
m
of the center minutiae. It can be represented as a vec-
tor c
m
∈ [0, 1]
n
, where n denotes the total number of
cells in a cylinder.
As a minutia cylinder only contains relative infor-
mation concerning the relationship between the minu-
tiae, such as distance and directonal difference, but
no global information, it can be considered transla-
tion and rotation invariant (Cappelli et al., 2010). The
same properties also make it robust against minor
non-linear transforms during capture such as differ-
ent levels of pressure applied on the fingerprint sensor.
Most importantly, the fixed-radius neighbourhood is a
key component in the handling of missing and spuri-
ous minutiae (Cappelli et al., 2010).
Definition 3 (Contribution Score). Each cell inside
a minutia cylinder is assigned a numerical value C
m
,
called contribution score, which details the likelihood
of finding another minutia in a small neighbourhood
with a compatible directional difference.
For a more technical definition along with insight-
ful figures, the reader is referred to (Cappelli et al.,
2010), Section 3.
Definition 4 (Cylinder Set). Given a fingerprint tem-
plate T , its corresponding cylinder set is defined as the
set of valid cylinders c
m
for m ∈ T . A cylinder is con-
sidered valid if it contains a sufficient number of con-
tribution scores, i.e., exeeding a pre-defined thresh-
old of a minimal number of contribution scores and a
minimal number of contributing neighbour minutiae.
Finally, a reference fingerprint template can be
compared against a probe feature set based on their
cylinder set representations. Therefore, we restate the
comparison process given in (Cappelli et al., 2010).
Definition 5 (Conditional Contribution). Let c
a
and
c
b
be cylinders corresponding to minutia a in a ref-
erence template and minutia b in a probe template.
Then, c
a|b
= c
a
where c
b
6= 0. In other words, c
a|b
contains all contributions from c
a
where c
b
has con-
tribution from corresponding cells.
Definition 6 (Candidate Pair). Two cylinders repre-
sented by c
a
and c
b
are considered a candidate pair if
and only if they satisfy the following requirements:
1. The directional difference between the two minu-
tiae a and b is not greater than
π
2
.
2. At least 60% of corresponding elements in the two
vectors c
a
and c
b
are non-zero.
3. kc
a|b
k + kc
b|a
k 6= 0.
Intuitively, it can be seen that these conditions en-
able to filter out the most relevant pairings of cylin-
ders. Firstly, the orientation of the minutiae should
be reasonably close in order to be considered as a
mated comparison trial. Secondly, there is a signifi-
cant overlap in the contribution scores associated with
each minutia cylinder, and thirdly, the contributions in
said overlap should occur at similar indices, indicat-
ing that the spacial relationships to neighbour minu-
tiae are similar. Based on valid pairings of cylinders
according to these criteria, the overall similarity be-
tween two cylinders is given by the following defini-
tion.
Definition 7 (Cylinder similarity). The cylinder simi-
larity between two cylinders represented by their vec-
tors c
a
and c
b
is given as
γ(a, b) =
(
1 −
kc
a|b
−c
b|a
k
kc
a|b
k+kc
b|a
k
, if c
a
and c
b
are candidate pairs.
0, otherwise.
(1)
The cylinder similarity allows to calculate local
similarity scores for each minutia pair. From those
local scores, a global similarity score indicating the
similarity between two fingerprints can be calculated.
The authors of (Cappelli et al., 2010) propose four dif-
ferent strategies for global score consolidation. In our
work, Local Similarity Sort (LSS) is applied, where
the top k cylinder similarity scores are averaged to
produce the global similarity score.
3.1.2 Fully Homomorphic Encryption
Fully Homomorphic Encryption (FHE) schemes al-
low for additions and multiplications of ciphertexts
that correspond directly to operations on the corre-
sponding plaintexts (Rivest et al., 1978). More for-
mally, a cryptographic scheme is homomorphic if
Enc
pk
(a ∗ b) = Enc
pk
(a) ∗ Enc
pk
(b) (2)
for an operation ∗. In partially homomorphic encryp-
tion schemes, this property is limited to either addi-
tion or multiplication. In comparison, FHE schemes
On the Feasibility of Fully Homomorphic Encryption of Minutiae-Based Fingerprint Representations
465

allow for a combination of additions and multiplica-
tions, making them applicable to a wider variety of
use cases.
The public-key encryption scheme used in this
work is the Cheon-Kim-Kim-Song (CKKS) (Cheon
et al., 2017). Historically, FHE schemes have first
been proposed for integer or binary input data. Only
more recently, (Cheon et al., 2017) have proposed a
scheme that operated on floating point numbers di-
rectly, eliminating the need for input quantisation or
significant rounding. While the scheme does come
with an approximation error, its order of mangnitude
is not significant to the application in our work.
Similarly to other FHE schemes, the security of
CKKS based on the hardness of the Ring-Learning
with Errors (R-LWE) problem (Lyubashevsky et al.,
2010). Encryption within such schemes is a prob-
abilistic operation, meaning that every encryption
uses fresh randomness. In addition, encryption in
CKKS is indistinguishable under chosen-plaintext at-
tacks (IND-CPA), such that an attacker cannot dis-
tiguish between an encryption of 0 and an encryp-
tion of 1. In particular, an attacker cannot distinguish
between two encryptions of the same input, e.g., the
biometric template of a specific data subject, and an
encryption of a different input, e.g. the biometric tem-
plate of a different subject. For more details, we refer
the reader to the original scheme (Cheon et al., 2017).
3.2 Baseline System
The baseline system operates in verification mode
on unprotected data without encryption. During en-
rolment, the reference subjects’ fingerprint samples
are captured and features are extracted as ISO/IEC
19794-2 (ISO/IEC JTC1 SC37 Biometrics, 2011) fin-
gerprint templates. From the templates, the MCC
cylinder sets are constructed as described above, and
stored in the reference database. For a verification
transaction, a probe subject’s features are extracted in
the same manner and represented as a cylinder set.
Then, the probe cylinder set is compared against the
reference cylinder set corresponding to the claimed
identitiy of the probe subject. The comparison out-
come is the global similarity score of the two cylinder
sets, which is compared against the pre-defined deci-
sion threshold to yield the comparison trial outcome.
3.3 Protected System
The protected system builds on the baseline system,
but with the addition of FHE. The reference templates
are stored in ciphertext form, and the probe features
are encrypted before comparison. Through the homo-
morphic properties of the FHE scheme, the compari-
son algorithm can be computed on the encrypted data,
ensuring privacy protection of the underlying data.
We work in an established client-server architec-
ture with a computation server (CS) controlling the
database of encrypted reference templates and an au-
thentication server (AS) controlling the secret key for
decryption in a semi-honest adversary model (Yasuda
et al., 2013). Figure 1 shows the workflow of the pro-
tected system.
In the first step, the client captures a finger-
print sample and generates a cylinder set from it.
For each minutia point m, it constructs the en-
crypted cylinder as a tuple of three CKKS ciphertexts
[Enc
pk
(θ
m
), Enc
pk
(c
m
), Enc
pk
(c
val
m
)] using coefficient
packing. The first ciphertext is the encrypted cylin-
der angle θ
m
, which inherits the minutia angle. The
second ciphertext is an encryption of the contribution
vector c
m
, while the third ciphertext stores the vector
c
val
m
, which represents the validity of each cell related
to minutia m. Even though cylinders are encrypted
individually, they cannot be utilised for hill-climbing
attacks due to the chosen plaintext security of the en-
cryption scheme. In other words, the separate encryp-
tion of multiple cylinders does not lower the privacy
protection compared to an encryption of the entire set
of cylinders.
For CS to execute the comparison between all
probe and reference cylinders, it first determines pairs
of cylinders that can be considered candidate pairs.
Following Definition 6, the first condition requires
the directional difference between two cylinders to
be lower than
π
2
. This is evaluated in the encrypted
domain by subtracting the two encrypted minutia an-
gles Enc
pk
(θ
a
) − Enc
pk
(θ
b
) = Enc
pk
(θ
a
− θ
b
). The
resulting difference is decrypted at AS and com-
pared against
π
2
by CS. The comparison is com-
puted in plaintext, as evaluating encrypted conditional
statements is complex (Iliashenko and Zucca, 2021).
However, the difference between two angles does not
reveal the orientation of the original minutiae, and
therefore, does not leak critical information.
For the second condition, CS verifies that over
60% of the corresponding elements in c
a
and c
b
are
non-zero by calculating a common validity vector as
the a homomorphic multiplication of two encrypted
validity vectors Enc
pk
(c
val
a
) and Enc
pk
(c
val
b
). The
number of elements in the resulting packed vector can
be obtained by applying the rotation technique first
introduced in (Boddeti, 2018). The resulting value is
decrypted in order to evaluate the condition. If the
amount of non-zero elements in the two vectors is be-
low 60% of the total amount of elements, the cylin-
ders are not candidate pairs and are not considered
ICISSP 2023 - 9th International Conference on Information Systems Security and Privacy
466
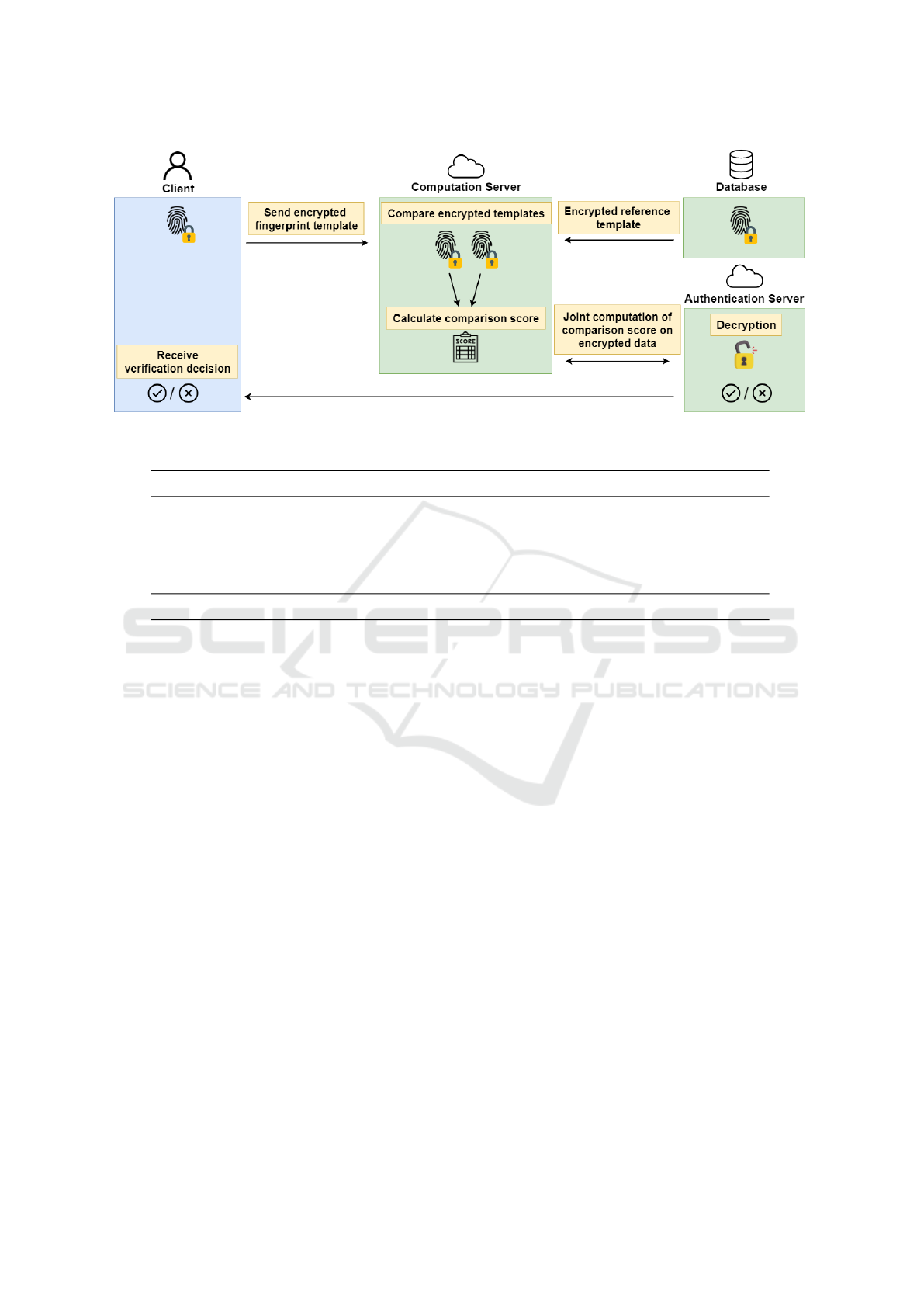
Figure 1: Simplified flowchart of the proposed solution.
Table 2: Homomorphic operations for the encrypted comparison of two minutia cylinders.
MCC operation Enc EvalAdd EvalSub EvalMult EvalAtIndex( · , 1) Dec
Cylinder encryption 3 — — — — —
Directional difference — — 1 — — 1
Common validity — n − 1 1 2 n − 1 1
Denominator — 2(n − 1) 2 2 2(n − 1) 2
Numerator — n − 1 2 1 n − 1 1
Total 3 4(n − 1) 6 5 4(n − 1) 5
further.
The third step is calculating the vectors
Enc
pk
(c
a|b
) and Enc
pk
(c
b|a
) and their norms. For this
step, CS multiplies Enc
pk
(c
a
) and Enc
pk
(c
b
) with the
common validity vector homomorphically, which fil-
ters out contributions of cells that should not be taken
into account for the cylinder similarity score. The
Euclidean norm of the resulting vectors Enc
pk
(c
a|b
)
and Enc
pk
(c
b|a
) can then again be evaluated as above.
Then, AS decrypts Enc
pk
(||c
a|b
||) and Enc
pk
(||c
b|a
||)
and CS checks that kc
a|b
k + kc
b|a
k 6= 0.
For the cylinder pairings that can be considered
candidate pairs, the final cylinder similarity score
is given in Definition 7. The denominator has al-
ready been calculated in the previous step, while the
numerator is calculated by performing one homo-
morphic subtraction of Enc
pk
(c
a|b
) − Enc
pk
(c
b|a
) =
Enc
pk
(c
a|b
−c
b|a
), and evaluating the Euclidean norm
||Enc
pk
(c
a|b
− c
b|a
)|| of the result as before. The re-
maining parts of the cylinder similarity γ(a, b) are
calculated in plaintext, and the method is repeated
m
1
· m
2
times for m
1
cylinders in the probe and m
2
cylinders in the reference template. The global com-
parison score is consolidated using local similarity
sort (Cappelli et al., 2010) and is compared against a
threshold that determines whether to accept or reject
the verification attempt.
An overview of the workload of homomorphic
operations is summarized in Table 2. Note that the
computation of one Euclidean norm requires one ho-
momorphic subtraction and multiplication as well as
n − 1 additions and rotations by one position (Bod-
deti, 2018), where n = 1536 is the fixed number of
cells in each cylinder. We account for the encryption
of the reference template during enrolment, such that
only the encryption of the probe template remains. To
complement Table 2, Table 3 gives the relative cost of
the FHE operations.
4 EXPERIMENTAL EVALUATION
In this Section, we give an experimental evaluation
of our proposed system as well as a security analysis
according to ISO/IEC 24745 (ISO/IEC JTC1 SC27
Security Techniques, 2022). Further, we compare the
performance of our system against the state of the art.
4.1 Performance
The experiments have been conducted on an Ubuntu
server version 1.13.0-1ubuntu1.1 with 4GHz CPU
and 128GB RAM. The proposed system has been
evaluated on the publicly available MYCT database
On the Feasibility of Fully Homomorphic Encryption of Minutiae-Based Fingerprint Representations
467
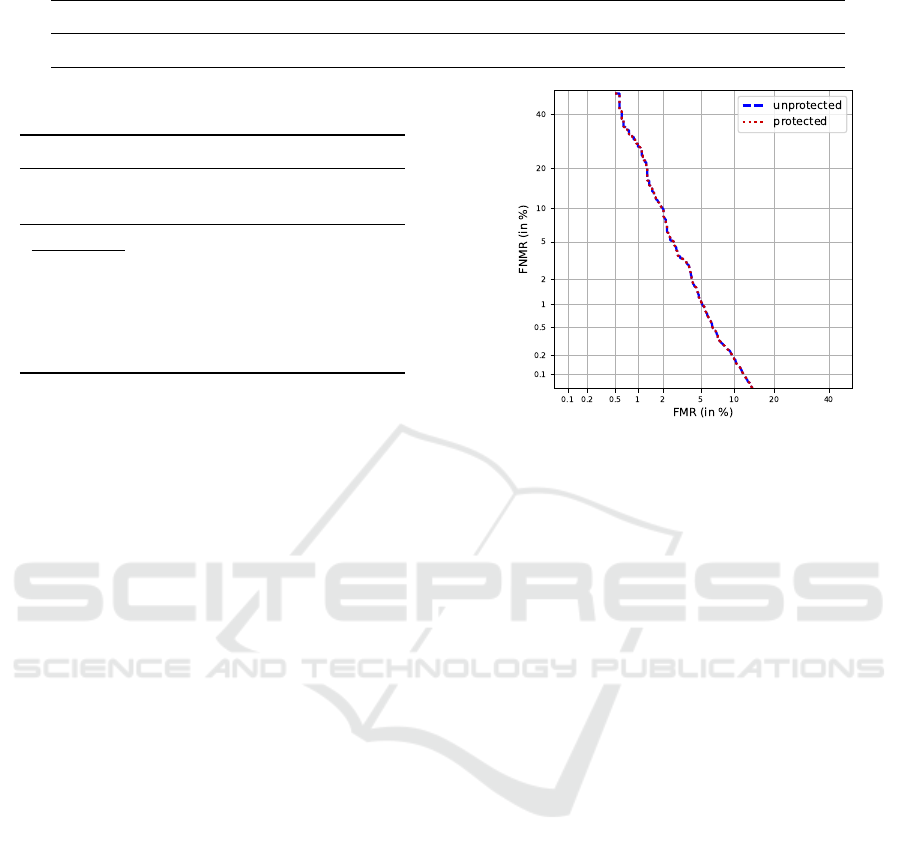
Table 3: Relative cost of CKKS (Cheon et al., 2017) operations implemented in PALISADE (Rohloff et al., 2017).
Operation on encrypted data Add Subtract Rotate Decrypt Multiply Encrypt
Relative cost 1 5 24 33 46 52
Table 4: Transaction times for the proposed system in sec-
onds.
Step Cylinder Template
Key generation — 0.08
Enrolment — 0.53
Verification
Probe encryption — 0.53
Direct. diff. 0.004 4.13
Common validity 0.017 25.12
Nom. + Denom. 3.80 11410.38
Total — 11525.03
(Ortega-Garcia et al., 2003) containing fingerprint im-
ages of 330 subjects with 12 samples of each finger
per subject. For feature extraction of the ISO/IEC
19794-2 (ISO/IEC JTC1 SC37 Biometrics, 2011)
minutiae templates, the SourceAFIS (Va
ˇ
zan, 2021)
implementation was used. The MCC (Cappelli et al.,
2010) algorithm was implemented in C++ based on
the original paper without any further optimisations
or simplifications. For the implementation of the FHE
scheme, the PALISADE library (Rohloff et al., 2017)
providing the CKKS (Cheon et al., 2017) encryption
scheme was used.
The recognition accuracy of our implementation
for the baseline system and the protected system is
shown in Figure 2. The biometric performance of
the protected system is not impacted through the ap-
plication of FHE, as all computations are carried out
in the same manner as in the baseline system, with
the difference being the computation of ciphertexts
on contrast to the unencrypted datain the baseline sys-
tem. As the FHE scheme is able to operate on floating
point numbers, no simplification or quantisation was
need for our approach. This stands in contrast to other
schemes (Kim et al., 2020; Gomez-Barrero et al.,
2017a), where accuracy loss has to be accepted in or-
der to accommodate the chosen encryption scheme.
Note that the contribution of our work is inde-
pendent of the biometric performance of the baseline
system, which could vary depending on the database
used. Instead, the contribution of our proposed sys-
tem lies in the unimpaired accuracy after the appli-
cation of BIP, as CKKS is currently the only FHE
scheme known to operate on floating point numbers
directly (Cheon et al., 2017).
Transaction times for the proposed system are pre-
sented in Table 4. Note that transaction times for the
Figure 2: Detection error trade-off curve for the evaluated
MYCT (Ortega-Garcia et al., 2003) database.
baseline system can be considered negligent in com-
parison, as they are lower than 50ms throughout all
system components on comparable hardware (Cap-
pelli et al., 2010). For the computational performance
of the protected system, the relevant metric is the
number of cylinders that need to be compared, which
corresponds to the number of minutiae in the probe
and reference template. In the evaluated database,
the median number of minutiae per template was 35,
with the lowest number of 6 and highest of 100 minu-
tiae, both of which can be traced back to poor sample
quality. The average number of cylinder comparisons
for one verification can therefore be extrapolated as
35 · 35 = 1225.
Evidently, the obtained execution times show that
the system is not practical in real-life applications,
with a verification transaction taking approximately
192 minutes. The main bottleneck is the computation
of the Euclidean norms. This has already been recog-
nised as a challenge in biometric systems (Bauspieß
et al., 2022). Within the calculation of the norms, the
most costly operation is the rotation of ciphertexts, as
can be derived from Table 3.
4.2 Security Analysis
We evaluate the protected system with respect to the
requirements defined in ISO/IEC 24745 (ISO/IEC
JTC1 SC27 Security Techniques, 2022). Firstly, un-
linkability in the protected system is given through
the chosen-plaintext security of the applied CKKS
ICISSP 2023 - 9th International Conference on Information Systems Security and Privacy
468

scheme. By the fresh random component generated
for every encryption operation, even two ciphertexts
computed from the exact same template look indistin-
guishable from a random input to an attacker. There-
fore, it is not possible for an attacker to link cipher-
texts corresponding to a certain data subjects to any
other ciphertext within our proposed system, or any
other BIP system the subject is enrolled in.
Similarly, the CKKS scheme yields renewabil-
ity, as a template from the same instance can be re-
encrypted and still be used securely in the system.
In case the template is no longer available in plain-
text form, or decryption is not possible for security
reasons, an encryption of 0 can be homomorphically
added to the previously stored reference to ensure
a newly randomized representation of the ciphertext
(Bassit et al., 2021).
Finally, irreversibility of the protected templates
is guaranteed through the hardness of the Ring-LWE
problem, which the security of the CKKS scheme
builds upon. Notably, this assumption only holds
true for correct parameter choices (Albrecht et al.,
2018), which are enforced within the PALISADE li-
brary (Rohloff et al., 2017).
5 CONCLUSION
Recent standards have placed emphasis on the long-
term protection of biometric data. Therefore, this
work has evaluated the application of post-quantum
secure FHE on minutiae-based fingerprint compari-
son. The challenge of minutiae-based comparison lies
in the variable length of the templates, absence of an
inherent order, and thereby more complex compar-
ison which requires conditional statements before a
global comparison score can be obtained. In a case
study and experimental evaluation, it has been shown
that it is not yet practical to evaluate such algorithms
using FHE. The computational overhead of FHE is
expected to decrease with further research in cryptog-
raphy, while at the same time more efficient repre-
sentations of biometric data need to be found that do
not impair the recognition accuracy. In this regard,
recent works based on deep neural networks have re-
ported significant improvements for fixed-length fin-
gerprint representation (Engelsma et al., 2019). Until
efficient post-quantum protection for high-accuracy
fingerprint representations has been developed, classi-
cally secure HE or post-quantum secure MPC should
be considered.
ACKNOWLEDGEMENTS
This research work has been funded by the German
Federal Ministry of Education and Research and the
Hessian Ministry of Higher Education, Research, Sci-
ence and the Arts within their joint support of the
National Research Center for Applied Cybersecurity
ATHENE.
REFERENCES
Albrecht, M. R., Chase, M., Chen, H., Ding, J., Goldwasser,
S., et al. (2018). Homomorphic encryption stan-
dard. Technical report, HomomorphicEncryption.org,
Toronto, Canada.
Barni, M., Bianchi, T., Catalano, D., Di Raimondo, M., La-
bati, R., et al. (2010). A privacy-compliant fingerprint
recognition system based on homomorphic encryp-
tion and fingercode templates. In IEEE Intl. Conf. on
Biometrics: Theory Applications and Systems (BTAS),
pages 1–7. IEEE.
Bassit, A., Hahn, F., Peeters, J., Kevenaar, T., Veldhuis, R.,
and Peter, A. (2021). Fast and accurate likelihood
ratio-based biometric verification secure against ma-
licious adversaries. IEEE transactions on information
forensics and security, 16:5045–5060.
Bauspieß, P., Olafsson, J., Kolberg, J., Drozdowski, P.,
Rathgeb, C., and Busch, C. (2022). Improved homo-
morphically encrypted biometric identification using
coefficient packing. In Proc. Intl. Workshop on Bio-
metrics and Forensics (IWBF).
Boddeti, V. N. (2018). Secure face matching using fully
homomorphic encryption. In Intl. Conf. on Biometrics
Theory, Applications and Systems (BTAS), pages 1–
10. IEEE.
B
¨
uscher, N., Demmler, D., Karvelas, N. P., Katzenbeisser,
S., Kr
¨
amer, J., et al. (2020). Secure two-party compu-
tation in a quantum world. In Intl. Conf. on Applied
Cryptography and Network Security, pages 461–480.
Springer.
Cappelli, R., Ferrara, M., and Maltoni, D. (2010). Minu-
tia cylinder-code: A new representation and matching
technique for fingerprint recognition. IEEE Trans. on
Pattern Analysis and Machine Intelligence.
Cheon, J. H., Kim, A., Kim, M., and Song, Y. (2017). Ho-
momorphic encryption for arithmetic of approximate
numbers. In Intl. Conf. on the Theory and Application
of Cryptology and Information Security, pages 409–
437. Springer.
Chillotti, I., Gama, N., Georgieva, M., and Izabach
`
ene, M.
(2020). TFHE: Fast fully homomorphic encryption
over the torus. Journal of Cryptology, 33(1):34–91.
Elgamal, T. (1985). A public key cryptosystem and a sig-
nature scheme based on discrete logarithms. IEEE
Trans. on Information Theory, 31(4):469–472.
Engelsma, J. J., Cao, K., and Jain, A. K. (2019). Learn-
ing a fixed-length fingerprint representation. IEEE
On the Feasibility of Fully Homomorphic Encryption of Minutiae-Based Fingerprint Representations
469

Trans. on Pattern Analysis and Machine Intelligence
(TPAMI), 43(6):1981–1997.
EU Parliament (2016). EU Quantum Manifesto: A New Era
of Technology.
European Data Protection Supervisor (2018). Report on
logging to the SIS II at national level.
Gentry, C. (2009). Fully homomorphic encryption using
ideal lattices. In Proceedings of the forty-first annual
ACM symposium on Theory of computing, pages 169–
178.
Gilkalaye, B. P. and Derakhshani, R. (2021). Secure authen-
tication using a garbled circuit variant for arithmetic
circuits. In IEEE Intl. Symposium on Technologies for
Homeland Security (HST), pages 1–7. IEEE.
Gomez-Barrero, M., Galbally, J., Morales, A., and Fier-
rez, J. (2017a). Privacy-preserving comparison of
variable-length data with application to biometric
template protection. IEEE Access, 5(1):8606–8619.
Gomez-Barrero, M., Maiorana, E., Galbally, J., Campisi, P.,
and Fierrez, J. (2017b). Multi-biometric template pro-
tection based on Homomorphic Encryption. Pattern
Recognition, 67:149–163.
Iliashenko, I. and Zucca, V. (2021). Faster homomorphic
comparison operations for BGV and BFV. Proc. on
Privacy Enhancing Technologies, 2021(3):246–264.
ISO/IEC JTC1 SC27 Security Techniques (2022). ISO/IEC
24745:2022. Information Technology - Security Tech-
niques - Biometric Information Protection. Interna-
tional Organization for Standardization.
ISO/IEC JTC1 SC37 Biometrics (2011). ISO/IEC 19794-
2:2011 Information Technology - Biometric Data In-
terchange Formats - Part 2: Finger Minutiae Data.
International Organization for Standardization.
Jain, A., Prabhakar, S., Hong, L., and Pankanti, S. (2000).
Filterbank-based fingerprint matching. IEEE Trans.
on Image Processing, 9(5):846–859.
Kessler, R., Henninger, O., and Busch, C. (2021). Finger-
prints, forever young? In Proc. Intl. Conf. on Pattern
Recognition (ICPR), pages 8647–8654.
Kim, T., Oh, Y., and Kim, H. (2020). Efficient privacy-
preserving fingerprint-based authentication system us-
ing fully homomorphic encryption. Security and Com-
munication Networks, 2020.
Kolberg, J., Bauspieß, P., Gomez-Barrero, M., Rathgeb, C.,
D
¨
urmuth, M., and Busch, C. (2019). Template pro-
tection based on homomorphic encryption: Computa-
tionally efficient application to iris-biometric verifica-
tion and identification. In IEEE Workshop on Infor-
mation Forensics and Security (WIFS), pages 1–6.
Kolberg, J., Drozdowski, P., Gomez-Barrero, M., Rathgeb,
C., and Busch, C. (2020). Efficiency analysis of post-
quantum-secure face template protection schemes
based on homomorphic encryption. In Intl. Conf.
of the Biometrics Special Interest Group (BIOSIG),
pages 175–182. Gesellschaft f
¨
ur Informatik e.V.
Liu, E. and Zhao, Q. (2017). Encrypted domain matching of
fingerprint minutia cylinder-code (MCC) with l1 min-
imization. Neurocomputing, 259:3–13.
Lyubashevsky, V., Peikert, C., and Regev, O. (2010). On
ideal lattices and learning with errors over rings. In
Annual international conference on the theory and ap-
plications of cryptographic techniques, pages 1–23.
Springer.
Ortega-Garcia, J., Fierrez-Aguilar, J., Simon, D., Gon-
zalez, J., Faundez-Zanuy, M., Espinosa, V., Satue,
A., Hernaez, I., Igarza, J.-J., Vivaracho, C., et al.
(2003). MCYT baseline corpus: a bimodal biometric
database. IEE Proceedings-Vision, Image and Signal
Processing, 150(6):395–401.
Paillier, P. (1999). Public-key cryptosystems based on com-
posite degree residuosity classes. In Intl. Conf. on
the Theory and Applications of Cryptographic Tech-
niques, pages 223–238. Springer.
Rahman, M. M., Mishu, T. I., and Bhuiyan, M. A. A.
(2022). Performance analysis of a parameterized
minutiae-based approach for securing fingerprint tem-
plates in biometric authentication systems. Journal of
Information Security and Applications, 67:103209.
Rivest, R. L., Adleman, L., Dertouzos, M. L., et al. (1978).
On data banks and privacy homomorphisms. Founda-
tions of secure computation, 4(11):169–180.
Rohloff, K., Cousins, D., and Polyakov, Y. (2017). The
PALISADE Lattice Cryptography Library. https://git.
njit.edu/palisade/PALISADE.
Va
ˇ
zan, R. (2021). Sourceafis fingerprint matcher v3.13.0.
https://sourceafis.machinezoo.com/, accessed 2022-
01-18.
Yang, W., Wang, S., Yu, K., Kang, J. J., and Johnstone,
M. N. (2020). Secure fingerprint authentication with
homomorphic encryption. In Digital Image Comput-
ing: Techniques and Applications (DICTA), pages 1–
6. IEEE.
Yao, A. (1986). How to generate and exchange secrets. In
Annual Symposium on Foundations of Computer Sci-
ence (SFCS), pages 162–167. IEEE.
Yasuda, M., Shimoyama, T., Kogure, J., Yokoyama, K., and
Koshiba, T. (2013). Packed homomorphic encryption
based on ideal lattices and its application to biomet-
rics. In Intl. Conf. on Availability, Reliability, and Se-
curity, pages 55–74. Springer.
Zhang, Y. and Koushanfar, F. (2016). Robust privacy-
preserving fingerprint authentication. In IEEE Intl.
Symposium on Hardware Oriented Security and Trust
(HOST), pages 1–6. IEEE.
ICISSP 2023 - 9th International Conference on Information Systems Security and Privacy
470
