
Online HTN Planning for Data Transfer and Utilization Considering
Legal and Ethical Norms: Case Study
∗
Hisashi Hayashi
1
and Ken Satoh
2
1
Advanced Institute of Industrial Technology, Tokyo, Japan
2
National Institute of Informatics, Tokyo, Japan
Keywords:
Data Transfer, Legal and Ethical Norms, Online HTN Planning, Logic Programming, Application of Planning.
Abstract:
Data transfer among servers is crucial for distributed data mining because many databases are distributed
around the world. However, as data privacy is becoming more legally and ethically protected, it is necessary to
abide by the laws and respect the ethical guidelines when transferring and utilizing data. Because information
affecting legal/ethical decision-making is often distributed, the data-transfer plan must be updated online when
new information is obtained while transferring data among servers. In this study, we propose a dynamic
hierarchical task network (HTN) planning method that considers legal and ethical norms while planning multi-
hop data transfers and data analyses/transformations. In our knowledge representation, we show that data-
transfer tasks can be represented by the task-decomposition rules of total-order HTN planning. We also show
that legal norms can be expressed as the preconditions of tasks and actions, and ethical norms can be expressed
as the costs of tasks and actions where legal norms cannot be violated, but ethical norms can be violated
if necessary following the ethical theory of utilitarianism. In the middle of the plan execution, the online
planner dynamically updates the plan based on new information obtained in accordance with laws and ethical
guidelines.
1 INTRODUCTION
Because data privacy is respected worldwide, many
laws and ethical guidelines governing the transfer and
usage of collected data have been established. Some
data can only be transferred within a country or a
company. Some data can only be used for specific
purposes.
Because the laws and ethical guidelines for col-
lected data are complicated and different in each
country, some researches have been conducted on the
automated compliance check of norms in data trans-
fers. In (Agarwal et al., 2018; Bonatti et al., 2020;
Palmirani et al., 2018; Vos et al., 2019; Taheri et al.,
2021), the policy presentation of European general
data protection regulation (GDPR) is studied to au-
tomate compliance checks.
Planning for data transfer in accordance with le-
gal/ethical norms is a new field of research. In the
studies of (Satoh et al., 2021; Taheri et al., 2021),
data-transfer planners and legal/ethical checkers are
separate. These are good frameworks considering that
∗
An earlier version of this paper appeared as an infor-
mal workshop paper (Hayashi and Satoh, 2022).
the logic of legal/ethical checkers is complicated and
should be separated from the logic of planning. How-
ever, replanning was not achieved in these studies.
Considering real international data transfers
among distributed servers, replanning is crucial be-
cause the latest information necessary for planning is
also distributed and not available when initially plan-
ning. In other words, the data-transfer plan must be
dynamically checked and updated if necessary, even
in the middle of the plan execution when new infor-
mation is found on distributed servers, which may af-
fect the validity of the plan.
In this paper, we present a new knowledge for dy-
namic HTN planning on transferring and utilizing dis-
tributed data considering legal and ethical norms. We
use an extension of the Dynagent algorithm (Hayashi
et al., 2006) which is an online total-order HTN plan-
ner. Total-order HTN planning algorithms (Behnke
et al., 2018; Hayashi et al., 2006; Magnaguagno et al.,
2021; Nau et al., 1999; Schreiber, 2021) are simple,
easy to use, and used for representing the domain con-
trol heuristics by task-decomposition rules.
In our knowledge representation, we show that
data-transfer tasks can be represented by the task-
154
Hayashi, H. and Satoh, K.
Online HTN Planning for Data Transfer and Utilization Considering Legal and Ethical Norms: Case Study.
DOI: 10.5220/0011603000003393
In Proceedings of the 15th International Conference on Agents and Artificial Intelligence (ICAART 2023) - Volume 1, pages 154-164
ISBN: 978-989-758-623-1; ISSN: 2184-433X
Copyright
c
2023 by SCITEPRESS – Science and Technology Publications, Lda. Under CC license (CC BY-NC-ND 4.0)

decomposition rules of total-order HTN planning. We
also show that legal norms can be expressed as the
preconditions of tasks and actions, and ethical norms
can be expressed as the costs of tasks and actions
where legal norms cannot be violated, but ethical
norms can be violated if necessary following the eth-
ical theory of utilitarianism. Using this knowledge
and an online HTN planning algorithm, the plan of
data transfer and utilization is dynamically adapted to
the new information obtained at local servers, abiding
by the laws and following the ethical guidelines. To
the best of our knowledge, there is no study on dy-
namic replanning for data transfer considering latest
legal and ethical norms. This technology will be cru-
cial for international data transfers in the era of data
privacy protection.
The rest of this paper is organized as follows: In
Section 2, related work is discussed. In Section 3, the
problem of data transfer and utilization is defined. In
Section 4, the algorithm of online HTN planning is
explained. In Section 5, the knowledge representa-
tion method to solve the problem is shown as a case
study based on a specific scenario. In Section 6, the
knowledge representation presented in the case study
is discussed. In Section 7, the paper is summarized.
2 RELATED WORK
HTN planners create plans by decomposing abstract
tasks into more concrete subtasks. The first HTN
planners were created in the late 1970s (Sacerdoti,
1977; Tate, 1977). Other previous HTN planners
were created around 1990 (Currie and Tate, 1991;
Wilkins, 1988).
The most popular and well-established HTN plan-
ner is simple hierarchical ordered planner (SHOP)
(Nau et al., 1999), which is a simple forward-chaining
total-order planner. This forward-chaining planner
decomposes the subtasks in the same order of exe-
cution. Domain control heuristics can be expressed
easily by the task-decomposition rules (methods) in a
manner similar to the Horn clauses of the Prolog pro-
gramming language, which are used for goal/literal
decomposition.
SHOP is still standard in HTN planning. For
example, HDDL (H
¨
oller et al., 2020) was used in
the HTN planning track of the international plan-
ning competition held in 2020, however, a translator
from HDDL to (J)SHOP2 (Nau et al., 2001) was pro-
vided. (Note that SHOP2 is a partial-order-planner
version of SHOP, and that JSHOP2 is the Java ver-
sion of SHOP2.) SHOP-like total-order HTN plan-
ners are still being studied to improve computational
efficiency (Behnke et al., 2018; Magnaguagno et al.,
2021; Schreiber, 2021).
Dynagent (Hayashi et al., 2006) is a simple
SHOP-like total-order forward-chaining HTN plan-
ner. In contrast to SHOP, Dynagent is an online HTN
planner. When the current assumption is updated,
the Dynagent planner modifies the plan, even in the
middle of plan execution. Dynagent was applied to
real robot manipulation, such as online path plan-
ning (Hayashi et al., 2009) and online pick-and-place
planning (arm manipulation) (Hayashi et al., 2013;
Hayashi et al., 2015). In this study, we adopted and
slightly modified the online HTN planning algorithm
of Dynagent.
Another interesting online forward-chaining
HTN-like planning is also studied in (Patra et al.,
2019; Patra et al., 2020). This online planner never
backtracks and cannot change the plan in the middle
of execution. However, it delays the subtask de-
composition until it becomes necessary and changes
the way to decompose the subtasks according to the
current situation. Interestingly, this planner conducts
Monte Carlo tree search, which is often used for
game tree search. This technique is known to be
effective when the search space is very large, such
as in chess or Go. This planner can also represent
complicated control processes such as “if-then” and
“repetition” as in standard procedural programming
languages.
In the studies (Satoh et al., 2021; Taheri et al.,
2021), the knowledge for data-transfer planning is
expressed by logic programs that represent the sim-
plified version (Shanahan, 1989) of the event calcu-
lus (Kowalski and Sergot, 1985). These planners are
implemented by the answer set programming (ASP
(Lifschitz, 2019)) solver, which makes stable mod-
els through forward reasoning. However, they are not
online planners. The idea of using the simplified ver-
sion of the event calculus for planning was first intro-
duced in (Miller, 1997). A planner based on the event-
calculus was implemented in (Shanahan, 2000) using
the Prolog programming language. In (Berreby et al.,
2017; Berreby et al., 2018), event calculus is used for
representing causalities in computational ethics. An-
other work on ethical principles on planning is found
in (Lindner et al., 2020).
3 PROBLEM
In this section, we define the planning problem of
legally and ethically correct data transfer and utiliza-
tion.
Online HTN Planning for Data Transfer and Utilization Considering Legal and Ethical Norms: Case Study
155

Nodes (servers) are connected by arcs (network
lines). The data stored in the database at a node can
be retrieved from the same node. Data at a node can
be transferred to an adjacent node that is connected by
an arc. An analyzer at a node can analyze data for a
specific purpose at the same node. Analysis output
is also data and can be transferred to an adjacent node
connected by an arc.
There are legal and ethical norms for data trans-
fers. Some data can only be transferred within spe-
cific countries. Some data can only be transferred
within a company. Some data can only be analyzed
for specific purposes. Legal norms must be satisfied.
Ethical norms should be respected if possible.
The objective is to deliver the analysis output of
specified data to a specified node for a specific pur-
pose.
4 ONLINE HTN PLANNING
In this section, we define the syntax and sketch of
the algorithm of online total-order forward-chaining
HTN planning based on the algorithm of Dynagent
(Hayashi et al., 2006). Dynagent (Hayashi et al.,
2006) is similar to SHOP (Nau et al., 1999). However,
in contrast to SHOP, Dynagent is an online planner.
4.1 Syntax
In this subsection, we define the syntax of the belief
and planning knowledge that are used by the planner.
Because we implemented the algorithm in Prolog, the
syntax follows its representation.
In the following definition, fluents (predicates
whose truth value can change) and belief rules (corre-
sponding to Horn clauses in Prolog) are defined using
constants, variables, functions (=function symbols),
and predicates (=predicate symbols). As in Prolog,
constants, functions, and predicates, are represented
by alphanumeric characters starting with a lowercase
alphabet and Variables are represented by alphanu-
meric characters starting with an uppercase alphabet
or “ ”.
Definition 1. A term is one of the following: a con-
stant, a variable, or a complex term. A complex term
is of the following form: F(T
1
, ··· , T
n
) where n ≥ 0,
F is an n-ary function, and each T
i
(1 ≤ i ≤ n) is a
term. A fluent is of the following form: P(T
1
, · ·· , T
n
)
where n ≥ 0, P is an n-ary predicate, and each T
i
(1 ≤ i ≤ n) is a term. When P is a 0-ary predicate, the
fluent P() can be abbreviated to P. A fluent is either
derived or primitive.
In the following definition, belief rules are defined
in the same way as in Prolog. Fluents are used to
represent the states.
Definition 2. A belief rule is of the following form:
belief(F, [F
1
, · ·· , F
n
]) where n ≥ 0, F is a fluent
called the head, each F
i
(1 ≤ i ≤ n) is a fluent, and the
set of fluents F
1
, · ·· , F
n
is called the body. (This be-
lief rule can be understood as F ⇐ F
1
, · ·· , F
n
.) When
n > 0, F is a derived fluent. When n = 0, the belief rule
belief(F, []) can be expressed as belief(F) and F is
called a fact. The belief rule belief(F, [F
1
, · ·· , F
n
])
defines the fluent G if F is unifiable with G. Fluent F
is regarded as dynamic iff it is declared as dy(F). The
belief rule belief(F) can be asserted to or retracted
from the belief after observation or action execution
iff F is dynamic.
We define the syntax of tasks, actions, and (total-
order) plans as follows: task symbols are represented
by alphanumeric characters starting with a lowercase
alphabet.
Definition 3. A task is of the following form:
T(X
1
, · ·· , X
n
) where n ≥ 0, T is an n-ary task sym-
bol, and each X
i
(1 ≤ i ≤ n) is a term. When T is a
0-ary task symbol, the task T() can be abbreviated to
T. A task is either abstract or primitive. An action is
a primitive task. The cost C of the task T, where C is
a number (real number or integer), is represented as
cost(T, C).
A plan is a list of tasks of the following form:
[T
1
, · ·· , T
n
] where n ≥ 0 and each T
i
(1 ≤ i ≤ n) is
a task, which is called the i-th element of the plan.
The cost of the plan [T
1
, · ·· , T
n
] is the sum of each
cost of T
i
(1 ≤ i ≤ n).
To represent the effect of an action, we use the
following action rules.
Definition 4. An action rule is of the following form:
action(A, C, E), where A is an action, C is a list of
fluents called preconditions, E is a list of effects, an
effect is either of the following forms: initiates(F)
or terminates(F), and F is a fluent.
Intuitively, in the aforementioned definition,
initiates(F) (or terminates(F)) represents that
the truth value of F becomes true (respectively, false)
after the action execution, if all the preconditions
hold.
To represent a method to decompose a task into
subtasks, we use the following task-decomposition
rules. Note that task decomposition rules are called
methods in SHOP (Nau et al., 1999).
Definition 5. A task-decomposition rule is of the
following form: htn(H, C, B) where H is an abstract
task called the head, C is a list of fluents called pre-
conditions, and B is a plan called the body.
ICAART 2023 - 15th International Conference on Agents and Artificial Intelligence
156

Figure 1: Task Decomposition.
The planning agent has belief and planning
knowledge, which are used for planning. Further-
more, belief represents the current state, whereas
planning knowledge represents the effects of actions
and the methods to decompose tasks into subtasks.
Definition 6. Belief is of the following form: ⟨D, S⟩
where D is a set of dynamic fluents, and S is a set of
belief rules.
Planning knowledge is of the following form:
⟨AR, TDR, COST⟩ where AR is a set of action rules,
TDR is a set of task-decomposition rules, and COST
is a set of the cost of each task.
4.2 Sketch of the Algorithm
In this subsection, we show the sketch of the algo-
rithm we used in this study. We used the algorithm of
Dynagent, which is defined in detail in (Hayashi et al.,
2006). However, the replanning method after cost up-
dates is not shown in (Hayashi et al., 2006). We mod-
ified the algorithm to handle cost updates, which is
crucial for reflecting ethical norms in plan selection.
Because the algorithm is implemented in Prolog, it
can handle rules of predicate logic by unification.
4.2.1 Initial Planning
The planning agent has the belief and planning knowl-
edge defined in the previous subsection. Belief repre-
sents the current state (the truth value of each fluent)
which the planning agent believes. Planning knowl-
edge includes action rules, task-decomposition rules,
and cost information of tasks.
The planner recursively decomposes the task into
subtasks that become primitive tasks (= actions) be-
fore execution. The HTN planning algorithm is
forward-chaining and the task decomposition is con-
ducted in the same order as task execution as shown
in Figure 1.
When a task taskA in a plan is decomposed, all
the previous tasks before the task taskA are primitive.
Therefore, it is easy to evaluate the truth value of flu-
Figure 2: Multiple Subplans.
Figure 3: Protected Link.
ents in the state shortly before task execution. The
preconditions (precond2 and precond3) of the task de-
composition, which are added to the preconditions of
the first subtask (taskA1), must be satisfied before the
task execution.
In general, there are several ways to decompose
a task. For example, in the case of the data trans-
fer problem, there are several routes for data transfer.
When decomposing a task in a plan, multiple plans
are created using multiple task-decomposition rules.
For example, in Figure 2, the task t3 in a plan is de-
composed into three subplans [a1, a2, a3, a4], [b1,
b2], and [c1]. Therefore, the search space of HTN
planning is an or-search-tree of plans.
When each task has the cost information, the best-
first search can be conducted. In the algorithm of Dy-
nagent, to conduct the best-first search, the planning
agent maintains frontiers (alternative plans) in the or-
search-tree of plans, sorts the plans in ascending order
of cost, and decomposes the first abstract task in the
plan with the lowest cost. If the cost of a task is al-
ways lower than or equal to the cost of its primitive
subplans (subplans that have only actions), the first
found plan has the lowest cost.
4.2.2 Replanning after Belief Deletion
In the planning algorithm of Dynagent, each precon-
dition (a dynamic fluent) of a task in a plan is recorded
in association with the task in the plan if its truth value
is subject to change. As shown in Figure 3, this fluent
recorded as a precondition of a task serves as a pro-
tected link which must be true before the execution of
the task.
Following a belief update, if the protected link in
a plan is violated, the plan becomes invalid. Then,
the invalid plan is removed from the frontiers of the
or-search tree. As shown in Figure 4, if the current
plan becomes invalid, the planning agent changes the
current plan to the plan with the next-lowest cost, and
Online HTN Planning for Data Transfer and Utilization Considering Legal and Ethical Norms: Case Study
157
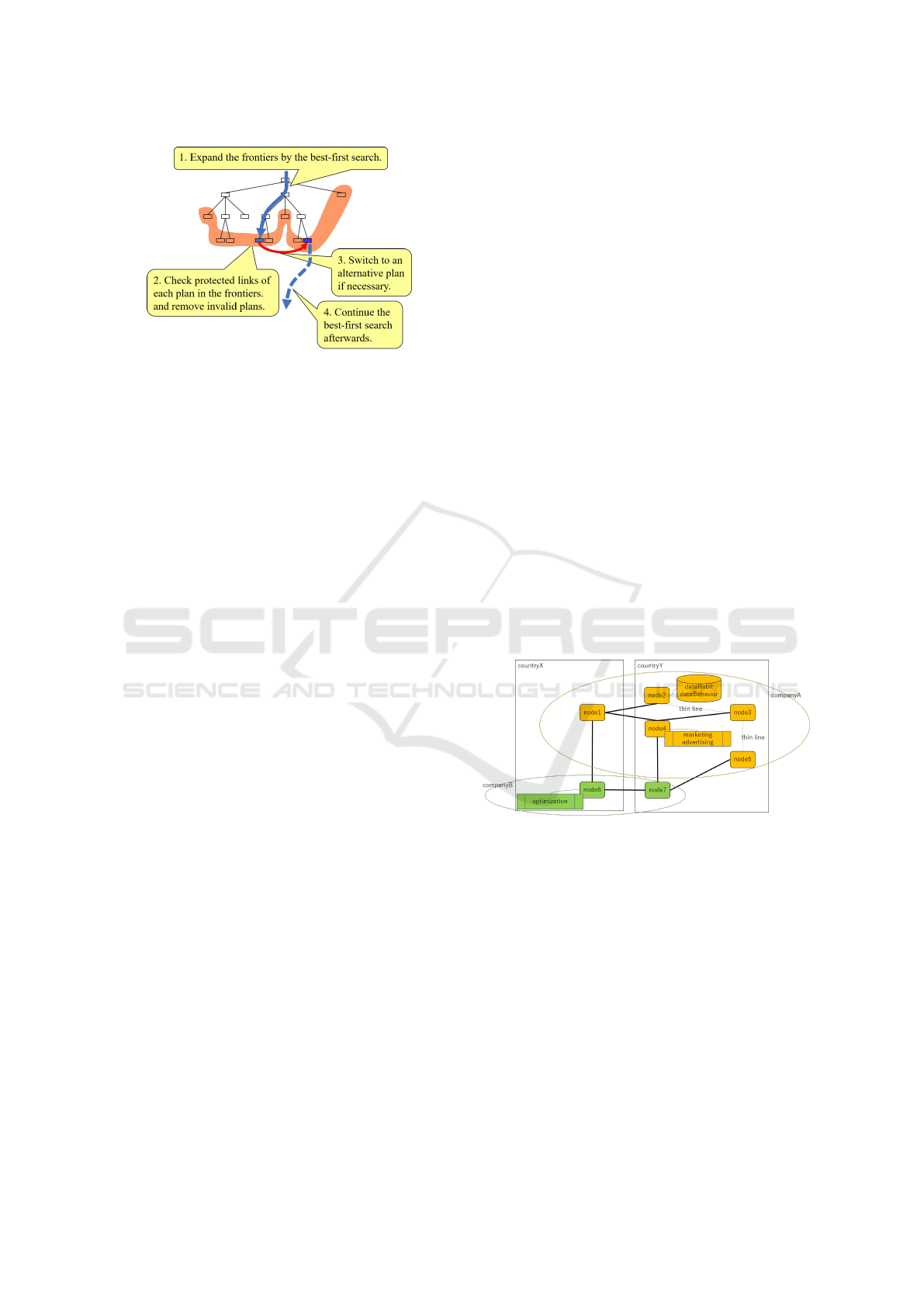
Figure 4: Switching to an Alternative Plan.
continues the best-first search using the frontiers of
valid plans.
4.2.3 Replanning after Belief Addition
When evaluating a precondition of a task in a plan
in the planning algorithm of Dynagent, if the precon-
dition is a dynamic fluent, the planning agent records
the plan separately from the frontiers even if the fluent
is false. During the plan execution, if the belief is up-
dated and the precondition becomes true, the recorded
plan is asserted to the frontiers as a new valid plan.
Because the plans in frontiers are always sorted, if the
new plan has the lowest cost, the planning agent stops
the current plan execution, switches to the new plan,
and continues the best-first search, which may lead to
a better plan.
4.2.4 Replanning after Cost Update
In the planning algorithm of Dynagent, replanning af-
ter a cost update is not explicitly shown. However,
this is crucial in our planning with an ethical checker
because the costs of unethical actions are dynami-
cally set higher after the ethical check. Therefore, we
added a new replanning procedure to the algorithm.
Following the cost update of an action (or a task),
we reevaluate the cost of each plan in the frontiers
and sort the plans in ascending order of cost. When
the current plan becomes less attractive in terms of
costs after the cost update, the planning agent stops
the plan execution, changes the plan, and continues
the best-first search, which may lead to a better plan.
4.2.5 Replanning after Action Execution
Dynagent is an online planner that updates each plan
after execution of each action. It maintains all the al-
ternative plans so that any plan can be started from the
current state.
When the execution of an action succeeds, if the
executed action is unifiable with the first action in a
plan, it is removed from the plan. Sometimes an ac-
tion execution in a plan invalidates other alternative
plans. Therefore, protected links are checked and in-
valid alternative plans are removed after a successful
action execution.
When the execution of an action fails, if the ex-
ecuted action is unifiable with the first action in a
plan, the plan is removed from the alternative plans
recorded in the frontiers. In this case, the planning
agent stops the plan execution and restarts the best-
first search using the valid plans in the frontiers until
it finds the plan.
5 CASE STUDY
In this section, we consider a specific network and
data transfer to study the feasibility of our dynamic
HTN planning framework for the planning problem
of legally and ethically correct data transfer and uti-
lization .
Figure 5 shows the whole network to be consid-
ered as a test case. This example is adopted and mod-
ified from the example written in (Taheri et al., 2021).
In the following subsections, we explain the details of
Figure 5 while showing how to express the domain
knowledge, actions, and task decomposition rules.
Figure 5: Connection of Servers.
5.1 Domain Knowledge
In this subsection, we show how to represent the do-
main knowledge that is used as a belief by the plan-
ning agent. This domain knowledge includes node
connection, location of database, location of analyz-
ers, allowed purposes for data analysis, region of
nodes, allowed regions for data transfer and analy-
sis, owners of nodes, and allowed companies for data
transfer.
5.1.1 Node Connection
In Figure 5, there are seven nodes that represent
servers. The arcs that connect nodes represent the
ICAART 2023 - 15th International Conference on Agents and Artificial Intelligence
158

network lines. These network connections are rep-
resented as follows:
belief(arc(node1,node2)). belief(arc(node1,node4)).
belief(arc(node1,node6)). belief(arc(node2,node3)).
belief(arc(node3,node4)). belief(arc(node3,node5)).
belief(arc(node4,node7)). belief(arc(node5,node7)).
belief(arc(node6,node7)).
To represent that each network connection is bidi-
rectional, we define the “connected” predicate as fol-
lows:
belief(connected(Node1,Node2),[arc(Node1,Node2)]).
belief(connected(Node1,Node2),[arc(Node2,Node1)]).
5.1.2 Location of Database and Retrieved Data
There is a database at node2 that contains data about the
habits and behaviors of people, which are represented
as follows:
belief(dbAt(dataHabit,node2)).
belief(dbAt(dataBehavior,node2)).
The location of the retrieved data from the
database is subject to change, which is represented as
follows:
dy(dataAt(_,_)).
5.1.3 Location of Analyzers
There are three analyzers of data on the habits and
behaviors of people. The analyzer at node6 is used for
optimization. The analyzer at node4 is used for market-
ing. Another analyzer at node4 is used for advertising.
This can be represented as follows:
belief(analyzableAt(dataHabit,marketing,node4)).
belief(analyzableAt(dataBehavior,marketing,node4)).
belief(analyzableAt(dataHabit,advertising,node4)).
belief(analyzableAt(dataBehavior,advertising,node4)).
belief(analyzableAt(dataHabit,optimizing,node6)).
belief(analyzableAt(dataBehavior,optimizing,node6)).
5.1.4 Allowed Purposes for Data Analysis
Initially, we assumed that all data were allowed to be
analyzed for any purpose. However, this assumption
is subject to change and may be corrected by the legal
checker. This is represented as follows:
dy(allowedPurpose(_,_)).
belief(allowedPurpose(dataHabit,marketing)).
belief(allowedPurpose(dataHabit,advertising)).
belief(allowedPurpose(dataHabit,optimizing)).
belief(allowedPurpose(dataBehavior,marketing)).
belief(allowedPurpose(dataBehavior,advertising)).
belief(allowedPurpose(dataBehavior,optimizing)).
5.1.5 Regions of Nodes
The region (country) of each node can be represented
as follows:
belief(nodeRegion(node1,countryX)).
belief(nodeRegion(node2,countryY)).
belief(nodeRegion(node3,countryY)).
belief(nodeRegion(node4,countryY)).
belief(nodeRegion(node5,countryY)).
belief(nodeRegion(node6,countryX)).
belief(nodeRegion(node7,countryY)).
5.1.6 Allowed Regions for Data Transfer
Initially, we assumed that all data were allowed to be
transferred in any region. However, this assumption
is subject to change and may be corrected by the le-
gal checker. Note that the analyzed data are also data.
This can be represented for the case of countryX as fol-
lows:
dy(allowedRegion(_,_)).
belief(allowedRegion(dataHabit,countryX)).
belief(allowedRegion(dataBehavior,countryX)).
belief(allowedRegion(
analysisOutput(dataHabit,marketing),
countryX)).
belief(allowedRegion(
analysisOutput(dataBehavior,marketing),
countryX)).
belief(allowedRegion(
analysisOutput(dataHabit,advertising),
countryX)).
belief(allowedRegion(
analysisOutput(dataBehavior,advertising),
countryX)).
belief(allowedRegion(
analysisOutput(dataHabit,optimizing)
countryX)).
belief(allowedRegion(
analysisOutput(dataBehavior,optimizing),
countryX).
The case of countryY is expressed in the same
way.
5.1.7 Owners of Nodes
The owner (company) of each node can be repre-
sented as follows:
belief(nodeOwnedBy(node1,companyA)).
belief(nodeOwnedBy(node2,companyA)).
belief(nodeOwnedBy(node3,companyA)).
belief(nodeOwnedBy(node4,companyA)).
belief(nodeOwnedBy(node5,companyA)).
belief(nodeOwnedBy(node6,companyB)).
belief(nodeOwnedBy(node7,companyB)).
5.1.8 Allowed Companies for Data Transfer
Initially, we assumed that all data were allowed to be
transferred in any company. However, this assump-
tion is subject to change and may be corrected by the
legal checker. Note that the analyzed data are also
data. This can be expressed for the case of companyA
as follows:
Online HTN Planning for Data Transfer and Utilization Considering Legal and Ethical Norms: Case Study
159

dy(allowedCompany(_,_)).
belief(allowedCompany(dataHabit,companyA)).
belief(allowedCompany(dataBehavior,companyA)).
belief(allowedCompany(
analysisOutput(dataHabit,marketing),
companyA)).
belief(allowedCompany(
analysisOutput(dataBehavior,marketing),
companyA)).
belief(allowedCompany(
analysisOutput(dataHabit,advertising),
companyA)).
belief(allowedCompany(
analysisOutput(dataBehavior,advertising),
companyA)).
belief(allowedCompany(
analysisOutput(dataHabit,optimizing),
companyA)).
belief(allowedCompany(
analysisOutput(dataBehavior,optimizing),
companyA)).
The case of companyB is expressed in the same
way.
5.2 Actions
The agent can execute three actions (primitive tasks):
one action is to retrieve the specified data from a
database, another action is to transfer the specified
data to the specified adjacent node, and the other ac-
tion is to analyze the specified data for the specified
purpose.
5.2.1 Data Retrieval from DB
The action getDataFromDB retrieves the specified data
from the DB at a node and store it at the same node.
Subsequently, the data can be transferred to another
node or analyzed for a specific purpose.
action(getDataFromDB(Data,Node),[
dbAt(Data,Node)],[initiates(dataAt(Data,Node))]).
The aforementioned rule specifies that the precon-
dition of the action is that the database of Data is at Node,
and that it initiates dataAt(Data,Node).
5.2.2 Data Transfer to an Adjacent Node
The action transfer transfers the specified data to the
specified adjacent node.
action(transfer(Data,NodeFrom,NodeTo),[
dataAt(Data,NodeFrom),
connected(NodeFrom,NodeTo),
allowedTransfer(Data,NodeTo)
],[
initiates(dataAt(Data,NodeTo)),
terminates(dataAt(Data,NodeFrom))]).
The aforementioned rule specifies that the pre-
conditions of the action are dataAt(Data,NodeFrom),
connected(NodeFrom,NodeTo), and allowedTransfer(Data,
NodeTo). It also specifies that the effects of the action
are to initiate dataAt(Data,NodeTo) and to terminate
dataAt(Data,NodeFrom).
The last precondition is defined as follows:
belief(allowedTransfer(Data,Node),[
nodeRegion(Node,Region),
allowedRegion(Data,Region),
nodeOwnedBy(Node,Company),
allowedCompany(Data,Company)]).
This indicates that the transfer of Data to Node is al-
lowed if the node is in an allowed region and is owned
by an allowed company.
5.2.3 Data Analysis
The action analyze analyzes the specified data at the
specified node for the specified purpose. The data
must be at the same location as the analyzer and the
purpose of the data analysis must be allowed. The
analysis output is obtained as new data after the data
analysis, and the original data is erased.
action(analyze(Data,Node,Purpose),[
analyzableAt(Data,Purpose,Node),
allowedPurpose(Data,Purpose),
dataAt(Data,Node)
],[
initiates(dataAt(analysisOutput(Data,Purpose),Node)),
terminates(dataAt(Data,Node))]).
The aforementioned rule specifies that the precon-
ditions of the action are Data analyzable at Node for
Purpose, Data is allowed for Purpose, and Data is at Node.
It also specifies that the effects of the action are to ini-
tiate dataAt(analysisOutput(Data,Purpose),Node), and to ter-
minate dataAt(Data,Node).
5.3 Task Decomposition
The agent needs two abstract tasks to recursively de-
compose to primitive tasks (actions) before execution.
One task is for transferring the specified data to the
specified node via multiple nodes. The other task is
the top-level task for delivering the analysis output of
the data for the specific purpose to the specified node.
5.3.1 Multi-Step Transfer
The task multiStepTransfer is a compound task for trans-
ferring data to another node via multiple nodes. This
task is recursively decomposed until the decomposed
subtasks include only the transfer actions.
htn(multiStepTransfer(Data,Node,Node),[
dataAt(Data,Node)],[]).
ICAART 2023 - 15th International Conference on Agents and Artificial Intelligence
160
htn(multiStepTransfer(Data,NodeFrom,NodeTo),[
dataAt(Data,NodeFrom),
connected(NodeFrom,Node)
],[
transfer(Data,NodeFrom,Node),
multiStepTransfer(Data,Node,NodeTo)]).
The first rule specifies that no action is required
for the transfer task multiStepTransfer(Data,Node,Node)
when Data is already at the destination (dataAt(Data,
Node)). The second rule specifies that when the data
is at NodeFrom and Node is an adjacent node, the trans-
fer task multiStepTransfer(Data,NodeFrom,NodeTo) can be ex-
ecuted by first transferring Data to the adjacent Node,
then transferring Data to the destination NodeTo via mul-
tiple steps.
5.3.2 Delivery of Analytics
The task deliverAnalytics is the top-level task for ob-
taining the specified data from a DB at a node and
delivering the analysis output for a specific purpose
to the recipient at another node.
htn(deliverAnalytics(Data,NodeFrom,NodeTo,Purpose),[
dbAt(Data,NodeFrom)
],[
getDataFromDB(Data,NodeFrom),
multiStepTransfer(Data,NodeFrom,NodeAnalysis),
analyze(Data,NodeAnalysis,Purpose),
multiStepTransfer(
analysisOutput(Data,Purpose),
NodeAnalysis,NodeTo)]).
This rule specifies that to deliver the analysis re-
sult of Data for Purpose to the destination (NodeTo), the
agent obtains Data from the DB at NodeFrom, transfers
the data to NodeAnalysis via multiple steps, analyzes the
data for the purpose, and transfer the analysis output
to the destination via multiple steps.
5.4 Costs of Tasks and Actions
We set a specific value for each task and cost. The
cost information is used for planning. The best-first
search will always find the lowest-cost plan if the cost
of each abstract task is less than or equal to the to-
tal cost of its primitive subtasks (actions), which we
obtain by task decomposition.
5.4.1 Static Cost
We assume that the costs of abstract tasks are static
and set at the minimum value of 1.
cost(deliverAnalysis(_,_,_,_),1).
cost(multiStepTransfer(_,_,_),1).
Furthermore, we assume the costs of the
getDataFromDB action and analyze action are static and the
values are set at 1.
cost(getDataFromDB(_,_),1).
cost(analyze(_,_,_),1).
5.4.2 Dynamic Cost
The data transfer costs are subject to change. We as-
sume that the agent is aware that the line between node2
and node3 and the line between node3 and node5 are nor-
mally slow. The data transfer costs become double if
these lines are used. These costs are set at 2.
cost(transfer(_,node2,node3),2).
cost(transfer(_,node3,node5),2).
cost(transfer(_,node3,node2),2).
cost(transfer(_,node5,node3),2).
The data transfer costs of the other lines are set at
1. This cost information is expressed in the same way.
5.5 Specific Task for Case Study
The specific task we consider in this case study is
deliverAnalytics(dataHabit,node2,node5,marketing). The ob-
jective of this task is to deliver the analysis output of
dataHabit, which is stored in the database at node2, to
node5. The purposed of the analysis is marketing.
5.6 Initial Planning
Considering the task, the planner creates the initial
plan as follows:
1. getDataFromDB(dataHabit,node2)
2. transfer(dataHabit,node2,node1)
3. transfer(dataHabit,node1,node4)
4. analyze(dataHabit,node4,marketing)
5. transfer(analysisOutput(dataHabit,marketing),node4,node7)
6. transfer(analysisOutput(dataHabit,marketing),node7,node5)
Figure 6: Initial Plan.
As shown in Figure 6, according to the aforemen-
tioned plan, dataHabit is retrieved from the database at
node2, transferred from node2 to node4 via node1, and an-
alyzed for the purpose of marketing at node4. The ana-
lyzed output is transferred from node4 to node5 via node3.
Online HTN Planning for Data Transfer and Utilization Considering Legal and Ethical Norms: Case Study
161
There are two data-transfer routes from node2 to
node4. Similarly, there are two data-transfer routes
from node4 to node5. The planner selects the route with
the lowest cost using the best-first search. Note that
the data-transfer cost from node2 to node3 is set higher
because the transfer speed is slow.
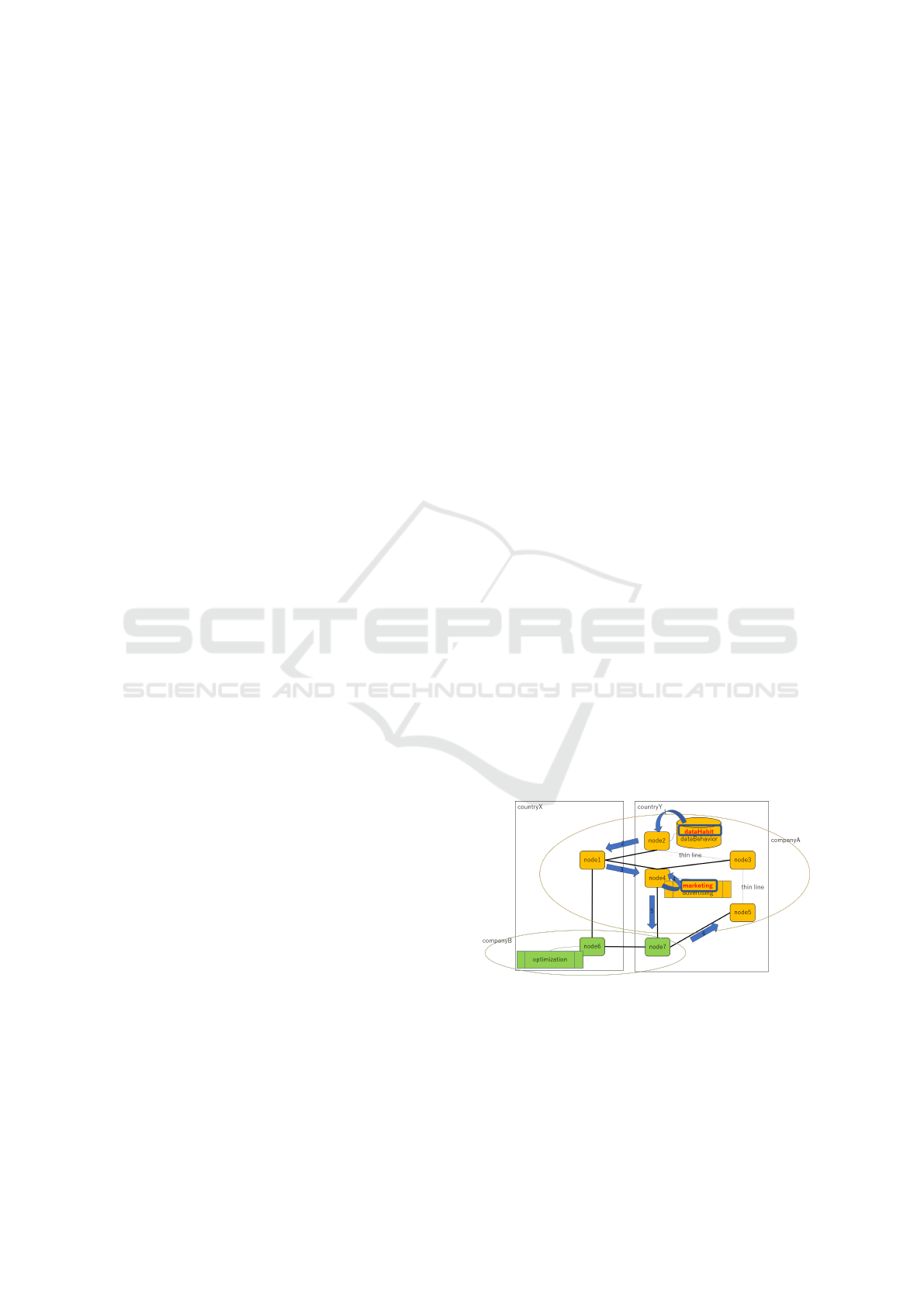
5.7 Replanning after Legal Check
We assume that dataHabit has been retrieved from the
database at node2. The next action is to transfer the
data to node1. Then, the legal checker indicates that it
is illegal to transfer dataHabit to countryX. Subsequently,
the agent removes the following from its belief:
belief(allowedRegion(dataHabit,countryX)).
Because the precondition of the next action be-
comes false, the planner modifies the plan as follows:
1. transfer(dataHabit,node2,node3)
2. transfer(dataHabit,node3,node4)
3. analyze(dataHabit,node4,marketing)
4. transfer(analysisOutput(dataHabit,marketing),node4,node7)
5. transfer(analysisOutput(dataHabit,marketing),node7,node5)
Figure 7: Legally Modified Plan.
The modified plan is shown in Figure 7. We
can confirm that dataHabit is transferred only within
countryY, rather than via countryX. This indicates that
the legal norm is satisfied. Note that the action
getDataFromDB(dataHabit,node2) is erased from the plan be-
cause it has been executed.
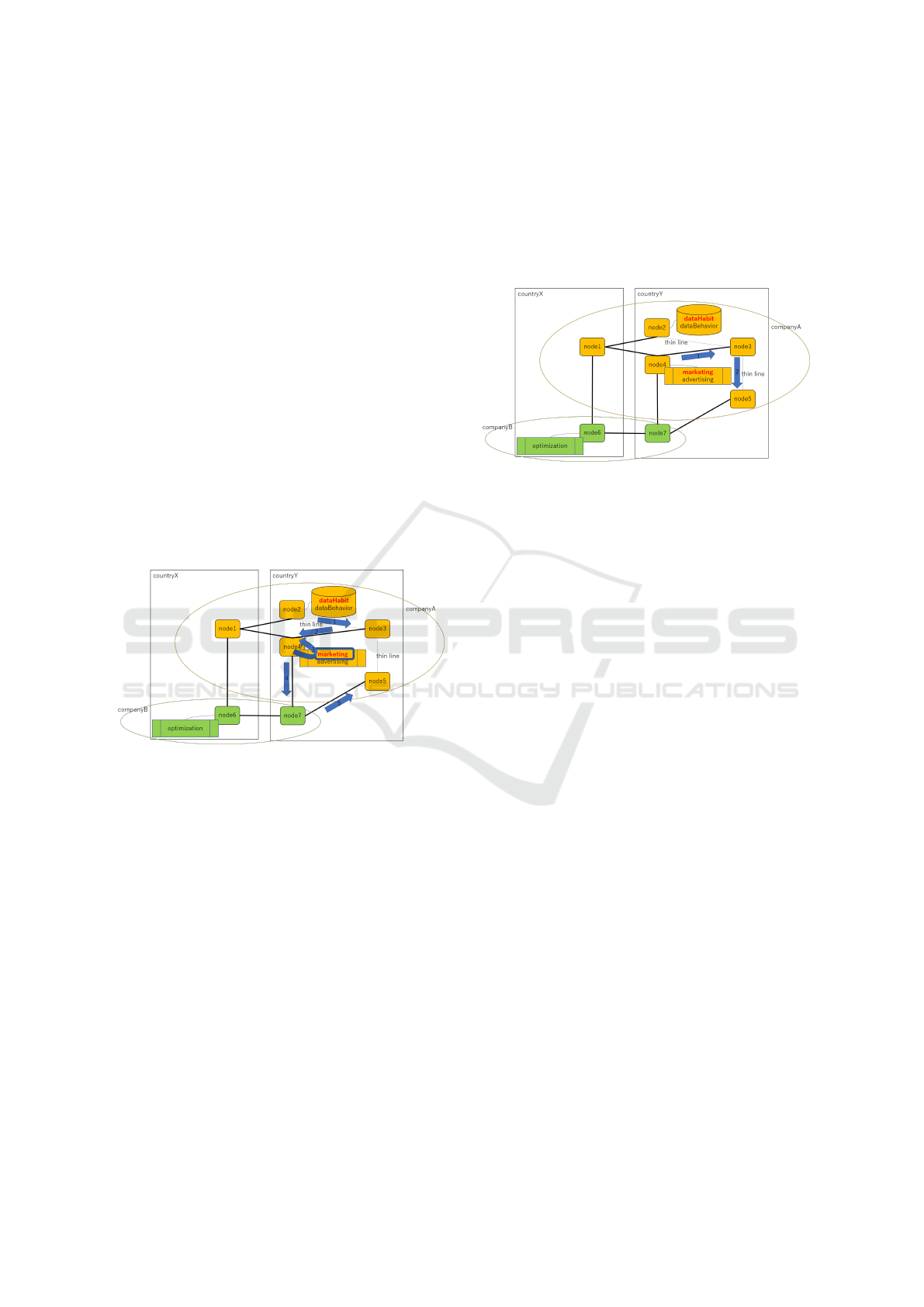
5.8 Replanning after Ethical Check
We assume that dataHabit has been analyzed at node4 for
the purpose of marketing. The next action is to transfer
the analysis output to node7. We assume that the ethical
checker indicates that it is not ethical to transfer the
analysis output to companyB. Then, the agent takes the
position of utilitarianism and updates the cost of the
next action as follows:
cost(
transfer(analysisOutput(dataHabit,marketing),node4,node7),
10).
The cost of the next action is now set at 10. Be-
cause the cost of the next action has become much
higher, the planner dynamically modifies the plan as
follows:
1. transfer(analysisOutput(dataHabit,marketing),node4,node3)
2. transfer(analysisOutput(dataHabit,marketing),node3,node5)
Figure 8: Ethically Modified Plan.
The modified plan is shown in Figure 8. We
can confirm that the analysis output (analysisOutput(
dataHabit,marketing)) is transferred within companyA,
rather than via companyB, in the modified plan. This in-
dicates that the ethical norm is respected, although it
is not illegal to transfer it via companyB. Note that the
planning agent does not abandon the plan to transfer
the analysis output via companyB. It is maintained as an
alternative plan and will be used only if there are no
other options.
5.9 Evaluation on Computation Time
We implemented the planning agent, belief, and plan-
ning knowledge in SWI Prolog for Windows 64-bit,
version 8.2.4, which was installed on the Windows
10 Home PC equipped with Intel(R) Core(TM) i7-
1065G7 CPU and the 32GB of RAM. We measured
the CPU times for initial planning, replanning after
legal check, and replanning after ethical check five
times each, and the average CPU times were 0.003,
0.006, and 0.003 seconds, respectively. Therefore,
this planner is adequate for practical use for the test
case scenario in this study.
In future, we would like to evaluate the scalabil-
ity for different types and sizes of networks. One
way to tackle the scalability problem is to use strat-
ified multi-agent HTN planning techniques (Hayashi,
2007; Hayashi et al., 2009) where the parent agent
first tries to find a rough data transfer route between
the regions, and then its child agent tries to finds a
detailed data transfer route inside the current region.
ICAART 2023 - 15th International Conference on Agents and Artificial Intelligence
162

5.10 Evaluation on Compliance with
Legal and Ethical Norms
In the test case scenario, in initial planning, nei-
ther legal norms nor ethical norms were ignored.
In other words, dataHabit was planned to be trans-
ferred to countryX, which is against the legal norm,
and analysisOutput(dataHabit,marketing) was planned to
be transferred to companyB, which is against the ethical
norm.
When the replanning algorithm was applied af-
ter legal check, dataHabit was planned to be trans-
ferred only within countryY. Therefore, the legal norm
was complied with. However, analysisOutput(dataHabit,
marketing) was still planned to be transferred to companyB,
which is against the ethical norm.
When the replanning algorithm was applied both
after legal check and ethical check, dataHabit was
planned to be transferred only within countryY, and
analysisOutput(dataHabit,marketing) was planned to be
transferred only within companyA. Therefore, not only
the legal norm was complied with but also the ethical
norm was respected.
6 DISCUSSION
From the case study, we can understand that the legal
norm of an action can be expressed as the precondi-
tion of the action. This indicates that the illegal action
cannot be executed because its legal norm (precondi-
tion) is not satisfied.
By contrast, the ethical norm of an action can be
expressed as the cost of the action. The higher the cost
is, the more unethical the action is. Even if an action
is unethical, it is still legal to execute the action. If
the planner can find the lower-cost plan, the agent can
avoid unethical action execution if possible. However,
unethical actions can still be executed if there is no
other option. Even in that case, it is possible to stop
the action execution when its cost is too high, which
means that the action is too unethical.
It is not always possible to collect all the necessary
information at the time of initial planning, especially
when the latest information is distributed across mul-
tiple servers. In the case study scenario in this paper,
the planning agent obtains new information regarding
the next action shortly before its execution. Legal and
ethical norms are checked at this time. Therefore, it is
important to dynamically check and update the plan
while executing it. Therefore, an online planning al-
gorithm is used in this paper.
7 CONCLUSION
We have shown how to represent knowledge about
legal and ethical norms using an online total-order
forward-chaining HTN planning algorithm in the do-
main of data transfer and utilization in multiagent sys-
tems. The precondition of an action was used for
its legal check, however, the cost of an action was
used for its ethical check. Dynamic adaptation to le-
gal/ethical norms was achieved by replanning after
legal/ethical check. These techniques are extremely
important when the latest information, which may af-
fect legal/ethical norms, is distributed across multiple
servers. Experiment results confirmed that this plan-
ner is adequate for practical use in terms of computa-
tion time in our case study.
ACKNOWLEDGEMENTS
This work was supported by JST, AIP Trilateral AI
Research, Grant No. JPMJCR20G4 and JSPS KAK-
ENHI, Grant No. JP19H05470 and JP21K12144.
REFERENCES
Agarwal, Steyskal, S., Antunovic, F., and Kirrane, S.
(2018). Legislative compliance assessment: Frame-
work, model and GDPR instantiation. In Annual Pri-
vacy Forum, pages 131–149.
Behnke, G., H
¨
oller, D., and Biundo, S. (2018). totSAT —
totally-ordered hierarchical planning through SAT. In
International Conference on Autonomous Agents and
Multiagent Systems, pages 6110–6118.
Berreby, F., Bourgne, G., and Ganascia, J.-G. (2017). A
declarative modular framework for representing and
applying ethical principles. In International Confer-
ence on Autonomous Agents and Multiagent Systems,
page 96–104.
Berreby, F., Bourgne, G., and Ganascia, J.-G. (2018).
Event-based and scenario-based causality for compu-
tational ethics. In International Conference on Au-
tonomous Agents and Multiagent Systems, pages 147–
155.
Bonatti, P. A., Kirrane, S., Petrova, I. M., and Sauro, L.
(2020). Machine understandable policies and GDPR
compliance checking. KI - K
¨
unstliche Intelligenz,
34(3):303–315.
Currie, K. and Tate, A. (1991). O-plan: The open planning
architecture. Artificial Intelligence, 52(1):49–86.
Hayashi, H. (2007). Stratified multi-agent htn planning in
dynamic environments. In KES International Sympo-
sium on Agent and Multi-Agent Systems: Technologies
and Applications, pages 189–198.
Online HTN Planning for Data Transfer and Utilization Considering Legal and Ethical Norms: Case Study
163

Hayashi, H., Ogawa, H., and Matsuhira, N. (2013). HTN
planning for pick-and-place manipulation. In Inter-
national Conference on Agents and Artificial Intelli-
gence, pages 383–388.
Hayashi, H., Ogawa, H., and Matsuhira, N. (2015). Com-
paring repair-task-allocation strategies in MAS. In In-
ternational Conference on Agents and Artificial Intel-
ligence, pages 17–27.
Hayashi, H. and Satoh, K. (2022). Towards legally and ethi-
cally correct online HTN planning for data transfer. In
International Workshop on Non-Monotonic Reason-
ing, pages 4–15.
Hayashi, H., Tokura, S., Hasegawa, T., and Ozaki, F.
(2006). Dynagent: An incremental forward-chaining
HTN planning agent in dynamic domains. In Declar-
ative Agent Languages and Technologies III, number
3904 in LNAI, pages 171–187. Springer.
Hayashi, H., Tokura, S., Ozaki, F., and Doi, M. (2009).
Background sensing control for planning agents work-
ing in the real world. International Journal of Intel-
ligent Information and Database Systems, 3(4):483–
501.
H
¨
oller, D., Behnke, G., Bercher, P., Biundo, S., Fiorino,
H., Pellier, D., and Alford, R. (2020). HDDL: An ex-
tension to PDDL for expressing hierarchical planning
problems. In AAAI Conference on Artificial Intelli-
gence, pages 9883–9891.
Kowalski, R. and Sergot, M. (1985). A logic-based calculus
of events. New Generation Computing, 4(1):67–95.
Lifschitz, V. (2019). Answer Set Programming. Springer.
Lindner, F., Mattm
¨
uller, R., and Nebel, B. (2020). Evalua-
tion of the moral permissibility of action plans. Artifi-
cial Intelligence, 287(103350):1–14.
Magnaguagno, M. C., Meneguzzi, F., and Silva, L. (2021).
HyperTensioN: A three-stage compiler for planning.
In 10th International Planning Competition: Planner
and Domain Abstracts – Hierarchical Task Network
Planning Track, pages 5–8.
Miller, R. (1997). Notes on deductive and abductive plan-
ning in the event calculus. In AISB Workshop on Prac-
tical Reasoning and Rationality.
Nau, D., Cao, Y., Lotem, A., and M
˜
unoz-Avila, H. (1999).
SHOP: simple hierarchical ordered planner. In Inter-
national Joint Conference on Artificial Intelligence,
pages 968–975.
Nau, D., M
˜
unoz-Avila, H., Cao, Y., Lotem, A., and
Mitchell, S. (2001). Total-order planning with par-
tially ordered subtasks. In International Joint Confer-
ence on Artificial Intelligence, page 425–430.
Palmirani, M., Martoni, M., Rossi, A., Bartolini, C., and
Robaldo, L. (2018). Legal ontology for modelling
GDPR concepts and norms. Legal Knowledge and In-
formation Systems, pages 91–100.
Patra, S., Ghallab, M., Nau, D., and Traverso, P. (2019).
Acting and planning using operational models. In
AAAI Conference on Artificial Intelligence, pages
7691–7698.
Patra, S., Mason, J., Kumar, A., Ghallab, M., Traverso, P.,
and Nau, D. (2020). Integrating acting, planning, and
learning in hierarchical operational models. In In-
ternational Conference on Automated Planning and
Scheduling, pages 478–487.
Sacerdoti, E. (1977). A Structure for Plans and Behavior.
Elsevier.
Satoh, K., Ganascia, J.-G., Bourgne, G., and Paschke,
A. (2021). Overview of RECOMP project.
In International Workshop on Computational Ma-
chine Ethics, International Conference on Prin-
ciples of Knowledge Representation and Rea-
soning. https://www.cse.unsw.edu.au/
∼
cme2021/
CME2021 paper Satoh.pdf (Accessed on 07 Feb.
2022).
Schreiber, D. (2021). Lilotane: A lifted sat-based approach
to hierarchical planning. Journal of Artificial Intelli-
gence Research, 70:1117–1181.
Shanahan, M. (1989). Prediction is deduction but explana-
tion is abduction. In International Joint Conference
on Artificial Intelligence, pages 1055–1060.
Shanahan, M. (2000). An abductive event calculus planner.
The Journal of Logic Programming, 44:207–239.
Taheri, Y., Bourgne, G., and Ganascia, J.-G. (2021). A com-
pliance mechanism for planning in privacy domain
using policies. In International Workshop on Juris-
informatics, JSAI International Symposia on AI.
Tate, A. (1977). Generating project networks. In Inter-
national Joint Conference on Artificial Intelligence,
pages 888–893.
Vos, M. D., Kirrane, S., Padget, J., and Satoh, K. (2019).
ODRL policy modelling and compliance checking. In
International Joint Conference on Rules and Reason-
ing, pages 36–51.
Wilkins, D. (1988). Practical Planning. Morgan Kauf-
mann.
ICAART 2023 - 15th International Conference on Agents and Artificial Intelligence
164
