
Assessment of the Cultivation and Protection of College Students'
Information Security Consciousness in the Era of Big Data
Rui Su
1,2 a
, Qianqian Wang
1b
, Lixian Xu
3,* c
and Caixia He
1d
1
Shandong Institute of Commerce and Technology, Tourist road, Jinan City, China
2
Angeles University Foundation, Metro Manila, Angeles City, Philippines
3
Department of Computing, Shandong Jianzhu University, Fengming Road, Jinan City, China
Keywords: Information Security, College Students, Cultivation, Protection.
Abstract: The development of information technology brings great convenience to our living environment, but also
brings the problem of information leakage, which has the same impact on the campus environment.The
development of network technology brings a lot of convenience to the campus life of contemporary college
students, but also brings a lot of hidden dangers of information security. Every year, many cases of
information leakage cause losses to college students. Therefore, it is very important to enhance the awareness
of information security of college students. This paper first introduces the importance of carrying out research
on the cultivation and protection evaluation of college students' information security awareness, and sorts out
the relevant research status. This study in order to more than 500 students with different levels of education
as the research object, and using the likert scale method to design the questionnaire, we understand the student
evaluation in self safety awareness, in the face of emergency handling capacity and existing security
awareness training for schools and the relevant work satisfaction and Suggestions to protect the situation, and
the research results on the reliability analysis, The experimental results are good. Finally, according to the
analysis results of the questionnaire, this paper puts forward four suggestions on the cultivation and protection
of college students' information security consciousness, which can provide reference for the relevant work of
colleges and universities.
1 INTRODUCTION
The information technology in the era of big data has
stronger interaction, which brings us a lot of
convenience in daily life and work, but also brings the
problem of information security leakage. With the
development of information technology, the Internet
will produce a lot of data every day, the traditional
information security processing technology has been
unable to meet the information age people's demand
for efficient data information processing, in order to
improve the quality and efficiency of information
security processing, information security processing
technology based on big data emerged at the historic
moment. Of course, the application of these
technologies is based on data. This paper will start
a
https://orcid.org/0000-0001-8562-0134
b
https://orcid.org/0000-0001-8562-0134
c
https://orcid.org/0000-0002-1633-1766
d
https://orcid.org/0000-0001-8585-4352
with the investigation of the research object and the
acquisition of basic data, analyze the current situation
of information security research of college students,
and lay a foundation for the subsequent research on
computer big data information security processing
technology.
College students are a relatively special group in
China. Most of them are adults with independent
thinking and strong sense of individuality. Although
many college students still need to get living expenses
from their parents, quite a large number of students
can get living subsidies through part-time jobs. In
short, they have a greater degree of control over their
money. However, most college students have not had
in-depth contact with the society, so their thoughts are
relatively simple. They are more used to making
Su, R., Wang, Q., Xu, L. and He, C.
Assessment of the Cultivation and Protection of College Students’ Information Security Consciousness in the Era of Big Data.
DOI: 10.5220/0012069700003624
In Proceedings of the 2nd International Conference on Public Management and Big Data Analysis (PMBDA 2022), pages 35-41
ISBN: 978-989-758-658-3
Copyright
c
2023 by SCITEPRESS – Science and Technology Publications, Lda. Under CC license (CC BY-NC-ND 4.0)
35

judgments on things with emotional thinking rather
than rational thinking. In their view, the social level
is more tolerant and righteous, and some negative
information, such as fraud and theft, is often ignored.
As a result, many criminals treat college students as
targets for their fraud.
In fact, it is a very important duty of colleges and
universities to help college students establish
information security protection awareness. However,
surprisingly, even the teachers often take classes or
class meeting to pass on his knowledge to protect the
safety of personal information, still can't completely
make sure that all the students away from danger,
almost a week at least one will still occur due to
personal information disclosure by fraud case, even,
almost all the universities are facing this problem. For
students to encounter fraud in this matter, in addition
to bring pecuniary loss, more dangerous is likely lead
to distrust and dislike of society, which for the
personality cultivation of college students in the key
period is a bad thing, it can also bring negative factors
to the society as a whole, it is against the direction of
the university for the cultivation of college students.
These facts make me seriously reflect: why college
students' awareness of personal information security
is relatively weak? How should teachers guide
students to establish information security
consciousness more effectively? How do students
need help from schools and teachers?
The answers to these questions need to be based
on in-depth study and analysis of objective data. In
order to further explore the cultivation and protection
of college students' information security awareness
and other related issues, and give teachers better work
suggestions, better help students establish
information security awareness, to ensure that they
stay away from harm, I think it is of very important
practical significance to carry out relevant research.
2 RELATED STUDIES
2.1 Research Status of Information
Security
The concept of "information security" is often
equated with "network security" in some studies.
Although we cannot live without the network now,
and many information security risks are indeed
related to the network, it is not rigorous to directly
regard these two concepts as the same. Some scholars
believe that information security should meet the
requirements of five aspects, specifically, the
information is confidential, the information is real,
the information is complete, the information cannot
be copied illegally, and the information storage
environment is safe. Some scholars believe that
information security refers to the protection of data
storage system and data processing system through
technical means or management means to prevent
them from being infringed.
It can be seen that most definitions of information
security are based on technology and science (Da
Veiga 2015), and the author believes that
"information security" is not just a technical concept,
but should be defined from a wider range, including
ethical and legal levels. Especially for college
students, the establishment and protection of personal
information security consciousness should be paid
more attention to.
2.2 Research Status of Information
Security of College Students in
China
Since 2010, with the increasing popularity of the use
of the Internet in China, the status quo of college
students' information security has gradually received
more and more attention, and many investigations
and papers are based on this (Feng 2020).
Liu Xinyi, a scholar, believes that most of the
domestic research is conducted through the
information security awareness and behavior of
college students. Although there are many research
results, they lack pertinency of problems, so the
application of research results is not good (Liu 2020).
Li Zhiping, a scholar, has analyzed and evaluated the
formulation and implementation effect of relevant
laws and regulations based on the current situation of
network security of College students in China. He
believes that the legal system of information security
in China is not perfect enough, which will have a
negative impact on the information security
protection of college students (Li 2021).
2.3 Foreign Research Status
Abroad for information security research carried out
earlier, the use of the results is better, for example, the
countries of the European Union by information
security related courses, help students to establish
information security protection consciousness, and
the teaching content and social practice, and mental
health, combining the help of information security
related courses has become a comprehensive
discipline, It can get better teaching effect and better
practical application effect (Menard 2017).
PMBDA 2022 - International Conference on Public Management and Big Data Analysis
36
However, most foreign studies on the cultivation
and evaluation of information security awareness take
primary and middle school students as the research
object, and the cultivation and evaluation of
information security awareness of college students
are relatively few.
3 METHODOLOGY
3.1 The Design of Research Process
This paper will combine the current situation of
college students' information security, and on the
basis of detailed analysis of factors affecting college
students' information security consciousness, put
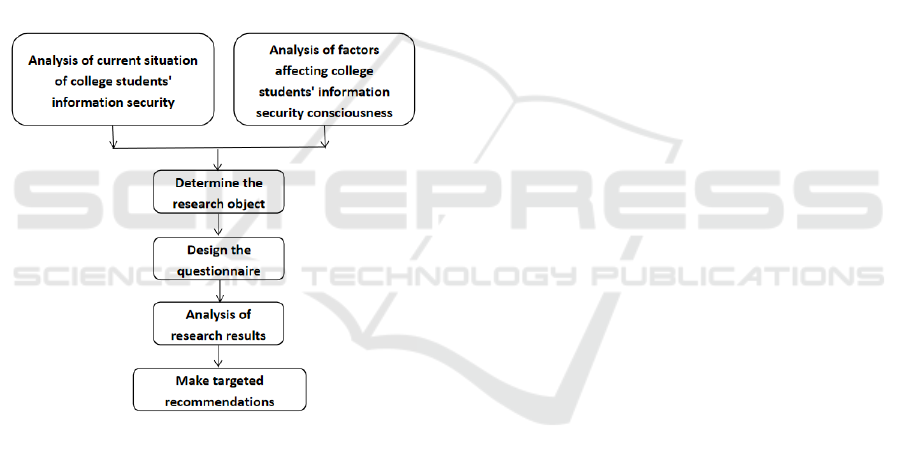
forward the research ideas: determine the survey
object → design the questionnaire → analysis of the
survey results → put forward targeted suggestions.
Figure 1: This caption has one line so it is centered.
3.2 Sample Selection and Sample Size
Design
This research will be carried out from different
dimensions and levels.
First, in order to better to analyze and compare the
education environment of universities on the student
information security awareness training, the author
will be carried out in two different education levels
school related research, finally selected the Shandong
Jianzhu university undergraduates and Shandong
institute of Commerce and Technology students as
the research sample. Second, in order to analyze and
compare the possible differences of information
security awareness among students of different
grades, the author sets questions about the grades in
the questionnaire, which is helpful for the analysis
and comparison of the research results in the later
stage. Thirdly, in order to compare and analyze the
possible differences between male and female college
students in their sensitivity to information security,
the author sets questions in the questionnaire that can
distinguish the gender of the survey samples.
3.3 Questionnaire Design
The survey questionnaire can help us understand the
most real information security status of college
students. For the relevant research work, the survey
questionnaire is a reliable and convenient tool.
Therefore, the reasonable design of the survey
questionnaire is a very key link in the relevant
research.
In this study, likert scale was used to design the
questionnaire. The questionnaire includes 38
questions, which cover four dimensions of the
research content: 1. College students' self-
information security awareness evaluation (including
10 questions); 2. College students' ability to deal with
problems related to information security (including
16 questions); 3. College students on the
effectiveness of information security awareness
training work evaluation (including 7 questions); 4.
College students' evaluation and suggestions for
strengthening information security awareness
channels (including 5 questions). Five options are set
for each question. The questionnaire will be released
to the respondents through the online research
platform, and the surveyed college students can
answer the questionnaire through mobile phone or
computer. This very convenient way of participation
can ensure that we can collect more effective
questionnaires.
3.4 Research and Analysis Methods
Although the author roughly determined the sample
size at the initial stage of the survey, in order to obtain
enough effective questionnaires, the survey scope
was expanded during the actual distribution of
questionnaires. This time, the author sent a total of
540 questionnaires to the two universities and
collected 522 valid questionnaires, with an effective
rate of 96.7%.
Next, the author will analyse the results of the
survey questionnaire from different dimensions,
mainly using quantitative analysis method.
Assessment of the Cultivation and Protection of College Students’ Information Security Consciousness in the Era of Big Data
37
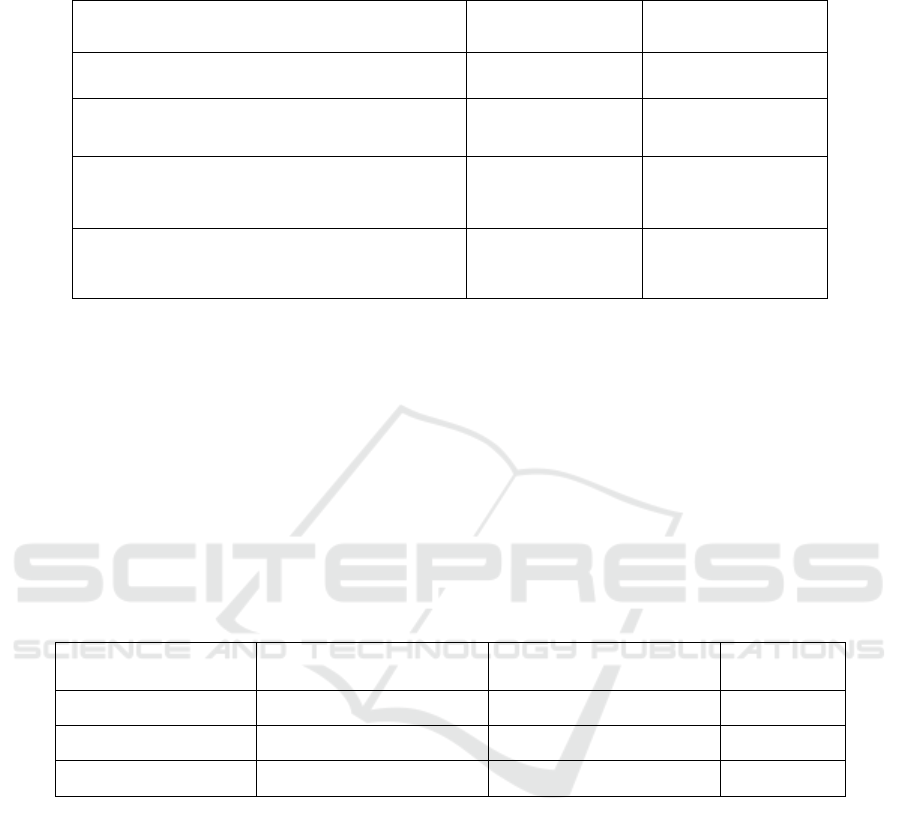
Table 1: The Design of the Assessment of the cultivation and protection of college students' information security
consciousness.
Dimensional variables
Number of
questions
Percentage
College students' self-information security
awareness evaluation
10 26.3%
College students' ability to deal with problems
related to information security
16 42.1%
College students on the effectiveness of
information security awareness training work
evaluation
7 18.4%
College students' evaluation and suggestions for
strengthening information security awareness
channels
5 13.2%
4 RESULTS AND ANALYSIS
4.1 Survey Object Composition and
Questionnaire Validity Analysis
A total of 540 online questionnaires were distributed
to two different universities, including 330 for
undergraduates and 210 for junior college students.
From the perspective of the effectiveness of the
questionnaires, the total number of valid
questionnaires collected was 522, with a total
effective rate of 96.7%. Among them, 325 valid
questionnaires were collected for undergraduates,
with an effective rate of 98.5%. There were 197 valid
questionnaires for junior college students, and the
effective rate was 93.8%. In this survey, a total of 18
questionnaires were judged to be invalid, mainly due
to short answer time and the same answers. The
remaining 522 questionnaires were of high quality
and could be used as the original data for this survey.
Table 2: Statistical table of education level composition and validity of questionnaire.
Investigated object
Number of questionnaires
issued
Number of valid
questionnaires
Perce-ntage
Undergradu-ates 330 325 98.5%
Junior college student
210 197 93.8%
In total 540 522 96.7%
4.2 Reliability Analysis of Survey
Questionnaire Results
Reliability analysis is generally used to measure the
reliability of survey questionnaire results and is also
an important basis for evaluating the design quality of
survey questionnaire. We usually require the
Cronbach reliability coefficient to be above 0.8.
In this study, we use online SPSS analysis tool to
analyze the reliability of the questionnaire from the
whole and different dimensions. The analysis results
show that the reliability coefficient of Cronbach is
0.93 for the questions related to the "self-information
security awareness evaluation of college students". In
dimension 2, the related questions of "college
students' processing ability assessment in the face of
information security-related problems", Crombach
reliability coefficient is 0.916; In dimension 3, the
Cronbach reliability coefficient is 0.935. For the
questions related to dimension 4, "Evaluation and
suggestions of College students on strengthening
information security awareness channels", the
Cronbach reliability coefficient is 0.856.
PMBDA 2022 - International Conference on Public Management and Big Data Analysis
38
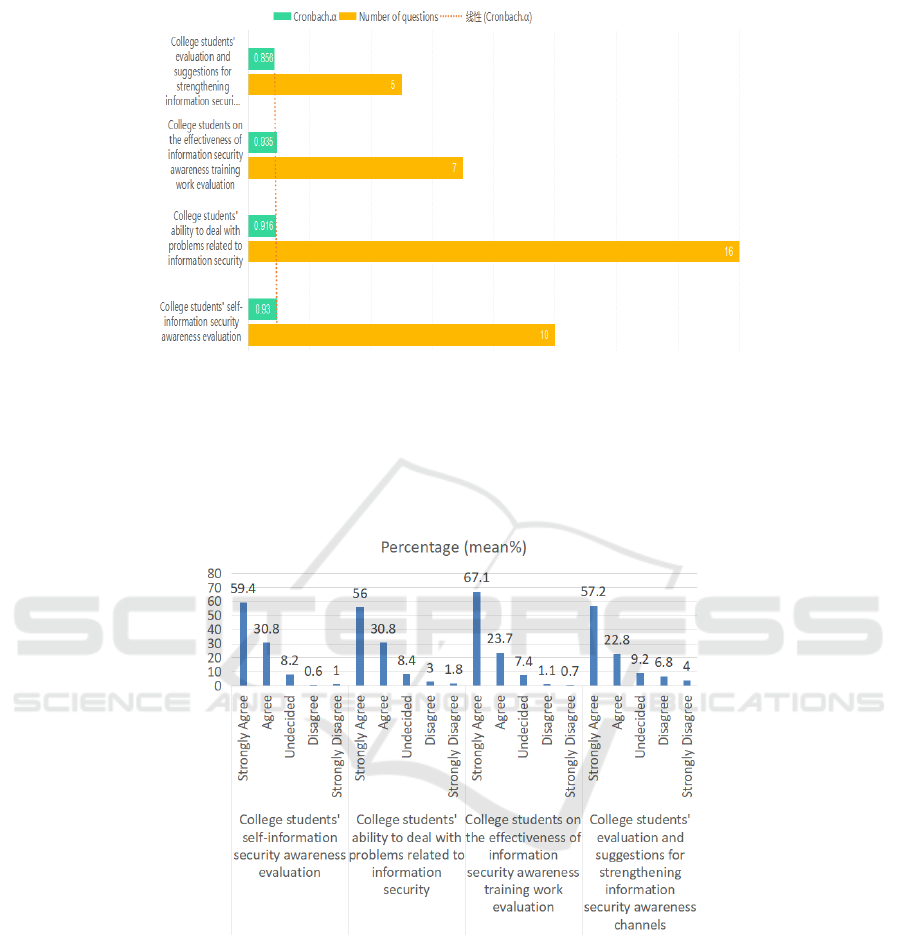
Figure 2: Reliability analysis of survey results.
4.3 Statistics of Frequency Analysis
Results
Frequency analysis can usually objectively and
directly reflect the real opinions of the respondents.
In this survey, frequency analysis method was used to
conduct classified statistics on the answers to
questions of different dimensions, as shown in Figure
3.
Figure 3: Statistical table of frequency analysis results.
The data in Table 4 make statistics on the
investigation of questions from four dimensions.
Taking the analysis of questions related to
dimension 1 in the table "Evaluation of self-
information security consciousness of college
students" as an example, the data means that the
average proportion of "Strongly Agree" is 59.4%, the
average proportion of "Agree" is 30.8%, and the
average proportion of "Neutral" is 8.2%. The average
number of respondents who answered "Disagree" was
0.6 percent, while the average number who answered
"Strongly Dissagree" was 1 percent.
5 DISSCUSSION
Through cross-analysis of the research results of
"information security awareness" and "normative
behavior", it is found that "personal information
security awareness" is closely related to information
protection behavior, as shown in Figure 4.
Assessment of the Cultivation and Protection of College Students’ Information Security Consciousness in the Era of Big Data
39
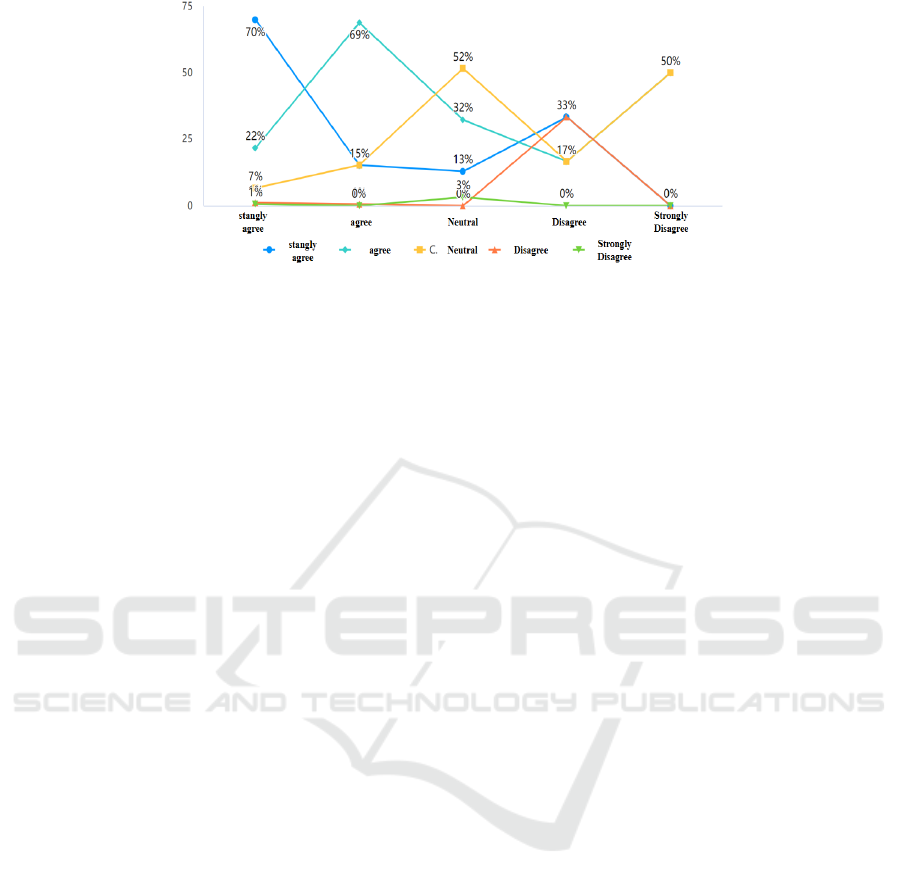
Figure 4: Cross analysis results.
And it can be found that in the survey questions of
dimension 1, the proportion of "Strongly Agree" and
"Agree" is as high as 90.2%, which indicates that
college students are very concerned about "self-
information security", and most of them think they
have a good sense of self-information security
protection.
In the survey questions of dimension 2, the
proportion of "Strongly Agree" and "Agree" is as high
as 86.8%. These data show that college students can
make correct decisions in most cases when facing
questions related to information security. Of course,
these answers are obtained when they remain calm. In
many cases, people's minds will be tense and
confused when facing unexpected situations. That is
to say, college students may not perform so well in
dealing with practical problems as they do in
answering questionnaires.
In the survey question of dimension 3, the
proportion of "Strongly Agree" and "Agree" is as high
as 90.8%, indicating that they highly Agree with the
current work carried out by schools to protect and
cultivate students' awareness of information security,
which also provides reference suggestions for the
future efforts of colleges and universities.
In the survey question of dimension 4, the
proportion of "Strongly Agree" and "Agree" is 80%,
which indicates that most students are still
psychologically dependent on the relevant measures
of the school for their personal information security
protection, and they have more expectations for the
work of the school to help them stay away from the
hidden dangers of information security.
From the survey also found that the overall level
of analysis, academic level and the reading grade for
the understanding of the information security
problem almost no difference, but the boys and girls
has significant differences on some issues of
understanding, such as "what do you think of personal
information protection is entirely your own thing and
has nothing to do with school" problem of answer,
The proportion of male students who answered
"Strongly Agree" and "Agree" was 71.12%, while
female students only answered 54.22%. In the answer
to the question "Do you think the security of students'
information should be protected by the school and
there is no need for individuals to do anything",
47.59% of male students answered "Strongly" and
"Agree", while only 68.98% of female students. This
shows that girls have higher requirements for self-
information security awareness, while boys are
worse.
Based on the above analysis, I think it is very
important for universities to find a good way to
cultivate students' personal information security
awareness and protection education. Based on my
own work experience, specific suggestions are as
follows:
(1) Strengthen top-level coordination mechanism
and design clear and complete educational content.
Undertake to the student information security
education is in fact a systems engineering, and if you
want to do it well, the university's management
should stand at a higher level thinking some
problems, for example, combined with the actual
situation of school teachers and students, to design a
personalized, concrete, feasible about "information
security awareness cultivation and protection of"
education content, These should ensure the right
environment for the university and its students.
(2) Formulate supervision and management rules
and master the effects obtained in the education
process.
In order to ensure that the educational links we
design can be well implemented and achieve good
results, there must be a corresponding supervision
mechanism, which can help us quickly find some
good educational methods and experience, and
promote them to more people and schools. In the
same way, we can also quickly discover some bad
PMBDA 2022 - International Conference on Public Management and Big Data Analysis
40

aspects in the education process through the
supervision mechanism, which can help us adjust the
direction and focus of work in time.
(3) strengthen teachers' awareness of information
security, and guide teachers to do a good job in
cultivating students' awareness of information
security.
In the education process for students, teachers are
very important participants, because teachers are the
people closest to students. For students, teachers are
the transmitters of school education concepts and can
represent the school. In fact, teachers pass some
information to students through the teaching process
is very direct, and the effect is very good. Therefore,
it is very important to strengthen teachers' awareness
of information security.
(4) Improve and enrich the campus culture to
achieve a good effect of "using environment to
educate students".
In China, there is a very famous word, called
"moistens everything silently", it mean good
environment can bring people a lot of good changes,
these changes happened secretly, no one can be found,
but in the long run, a good change of this man will be
more and more obvious, like spring rain will bring
many plants moist, no one can find to begin with, But
the plants will gradually become very vigorous, the
flowers will become very beautiful, let people feel
surprised. Just like people, they are more likely to
become a kind and gentle person in a nice
environment.
So, we should pay attention to shaping a good
campus environment, such as through "information
security related events, let more students know the
knowledge of the information security, and by his
own strength to knowledge of the students passed
around, if everyone can turn into" information
security "the spread of the messenger, I think it must
be a very good thing.
6 CONCLUSION
The cultivation and protection of college students'
information security consciousness is a systematic
project. As the main body of this task, college
students' sensitivity to information security is very
important. In addition, because they are still living on
campus, the school and teachers for their influence is
very big, schools and teachers to their influence is
very big, as the main management and training of the
students, the college managers should strengthen the
mechanism of the top design, we hope to find a good
method to guide students to strengthen their
information security awareness at the same time, Also
create a better information security campus
environment. In addition, there is a very important
aspect, that is to improve the teacher information
security education ability, inside and outside the
classroom for students to carry out information
security education, and strive to ensure that all
students away from information security risks.
REFERENCES
Da Veiga A, Martins N. Information security culture and
information protection culture: A validated assessment
instrument[J]. Computer Law & Security Review,
2015, 31(2): 243-256.
Feng HOU. Research on Information Security and
Protection Strategy of Computer Network[J].
International Journal of Computational and
Engineering,2020,5(1).
Li Zhiping, Xie Jiagui, Gao Likun, Nie Fanjie. Data Privacy
Protection in Data Fusion[J]. Journal of Physics:
Conference Series,2021,2033(1). Zhang Yue, Sun
Qian. Information Security Protection Strategy Based
on Computer Big Data Technology[J]. Journal of
Physics: Conference Series,2021,1744(4).
Liu Xinyi. Research on Information Security Awareness
Education of College Students in the Micro Era [D].
Tianjin Polytechnic University, 2020. DOI: 10.
27357/d. CN ki. Gtgyu. 2020. 000907.
Menard P, Bott G J, Crossler R E. User motivations in
protecting information security: Protection motivation
theory versus self-determination theory[J]. Journal of
Management Information Systems, 2017, 34(4): 1203-
1230.
Assessment of the Cultivation and Protection of College Students’ Information Security Consciousness in the Era of Big Data
41
