
Machine to Machine Automatic Housing Area Security System
Prototype Using MQTT IoT Communication Protocol
Imam Sutrisno
1a
, Moh. Farras Raihan
1
, Mukhammad Jamaludin
1
, Vandy Achmad
1
,
Rendy Rizkananda
1
, Urip Mudjiono
1
, Tri Mulyatno Budhi Hartanto
2
, Muhammad Khalil
3
,
Muhammad Fuad Alharis
4
and Monika Retno Gunarti
5
1
Politeknik Perkapalan Negeri Surabaya, Indonesia
2
Balai Pendidikan dan Pelatihan Transportasi Laut, Indonesia
3
Politeknik Negeri Tanah Laut, Indonesia
4
Politeknik Negeri Banyuwangi, Indonesia
5
Politeknik Pelayaran Surabaya, Indonesia
Keywords: IoT, Security, MQTT, Housing Area, Emergency Button.
Abstract: Environmental security is a shared responsibility between the community and officers who are specifically
authorized to maintain the security of an area. For this reason, the role of the community in informing actions
that interfere with safety is important. This study aims to create a prototype of an environmental security
system using an emergency button application for security to inform certain security conditions. This research
was developed using the Research and Development model approach by conducting a needs analysis, then it
was designed and implemented in the form of hardware which was then tested for its functionality. Functions
offered in this model include emergency hazard buttons, stranger alert, out-of-town, and assistance. The sys-
tem is connected to each guard post in the housing. The prototype has been tested for functionality and works
well according to its function.
1 INTRODUCTION
The comfort of the living environment is one of the
basic needs in social life. This is based on a finding
that environmental comfort is the dominant factor in
choosing a place to live (A. Syafrina, 2018). Housing
developers have a challenge so that the housing envi-
ronment is designed in such a way that it meets the
environmental comfort requirements as regulated by
the government. Public and social facilities are
needed by the community in a residential area
(Nuryasin, 2021). Some of them, are security facili-
ties, worship, health, education, and others. However,
some housing estates do not yet have complete sup-
porting facilities. One of them is a one-gate system.
The problem due to the non-enforcement of the one-
gate system is that it opens up opportunities for crime
to enter from unofficial doors. Several cases of crime
occur in housing, such as theft, in addition, some
criminals are good at disguises so they are not recog-
a
https://orcid.org/0000-0002-7053-8004
nized when they act (Okezone, 2020). Crimes also oc-
cur by individuals who disguise themselves as scav-
engers and buskers (Liputan6, 2017). Based on the
above background the author intends to develop a
prototype emergency button on a housing. The proto-
type was developed based on a website that is con-
nected to the security guard post. Several researchers
have researched similar topics. These studies have
their characteristics, such as an emergency button to
maintain campus security (A. Wijayanto, 2019). This
study aims to respond to security disturbances in the
campus environment. Another study resulted in the
application of emergency buttons in hospitals. This
study aims to make it easier to make emergency calls
to the hospital for emergency cases (M. Anike, 2019).
Meanwhile, several other studies have also produced
similar systems such as emergency button applica-
tions implemented by the police (M. Afdal, 2020) and
the development of emergency button applications in-
stalled in crowded places that are integrated at the
central security post (A. I. Afolabi, 2018). In this
Sutrisno, I., Raihan, M., Jamaludin, M., Achmad, V., Rizkananda, R., Mudjiono, U., Har tanto, T., Khalil, M., Alhar is, M. and Gunarti, M.
Machine to Machine Automatic Housing Area Security System Prototype Using MQTT IoT Communication Protocol.
DOI: 10.5220/0011863200003575
In Proceedings of the 5th International Conference on Applied Science and Technology on Engineering Science (iCAST-ES 2022), pages 703-707
ISBN: 978-989-758-619-4; ISSN: 2975-8246
Copyright © 2023 by SCITEPRESS – Science and Technology Publications, Lda. Under CC license (CC BY-NC-ND 4.0)
703

study, the authors focus on making a prototype of an
emergency button on housing by integrating it at a se-
curity post using the MQTT Protocol whose output
can be displayed via DMD P10 at each related secu-
rity post, besides that this prototype is accompanied
by an alarm notification if there is an emergency mes-
sage from residents. The prototype offers emergency
button functions for alerts, stranger alerts, out-of-
town notifications, and requests for assistance to
health workers.
Several researchers have produced similar sys-
tems such as applications for emergency buttons on
housing and campus security systems that are inte-
grated with the main security post through the inte-
gration using the HTTP protocol. However, this is not
efficient because it requires a good and stable connec-
tion. Besides that, it takes a long process of sending
messages from the incident location to the security
post. When compared with previous research, there
are several advantages of the tools that we developed,
namely the system tools are easy to install, maintain,
and operate. Other than that, it is also cheaper in terms
of the total cost of these tools namely installation and
maintenance costs. This means it is more efficient
than the previously researched applications. There are
also additional benefits, that this tool is also more ef-
fective than the one using the HTTP protocol. Be-
cause it is using the widely used lightweight commu-
nications MQTT protocol that doesn't require a good
and stable connection. The operation of this tool is
easy, it only needs to press the emergency button, and
the tool will directly send a message to all security
guards in the area.
1.1 Housing Area
Housing is a building where humans live and carry
out their lives, besides that a house is also a place
where the socialization process takes place in which
an individual is introduced to the norms and customs
that apply in a society. As a place for human life, it is
not only about technical and physical aspects but also
social, economic, and cultural aspects of its inhabit-
ants. (Budiharjo, 1998).
1.2 MQTT
The MQTT protocol is one of the IoT's application
protocols. This is the most widely adopted protocol
for developing IoT applications compared with the
other application protocols (N. Naik, 2017). MQTT
was developed by Andy Stanford-Clark of IBM (U.
Hunkeler, 2008) and Arlen Nipper of Arcom in 1999
and standardized in 2013 by the Organization for the
advancement of structured information standards
(OASIS) (A. Banks, 2014). It's suitable for IoT appli-
cations due to its simple model and low bandwidth
usage. Furthermore, it guarantees the reliability of
packet delivery. Some features of the MQTT proto-
col: It's a published/subscribe protocol and runs over
TCP/IP. It's suitable for constrained environments
due to its simplicity and open source code. It also sup-
ports three levels of quality of service (QoS).
In MQTT, the publish-subscribe model men-
tioned below in Figure 1, the publisher sends the data
to the broker for publishing in the 'Publish' message;
a subscriber authenticates and subscribes to the bro-
ker for a certain topic on the 'Subscribe' message, and
the broker sends the data to the specifics subscribers
that are subscribed to the specific topic on 'Publish'
message.
1.3 Emergency Button
The emergency button device is a manual control de-
vice. It is the method of initiating the emergency
function. An Emergency button is an electronic de-
vice designed to assist in alerting somebody in emer-
gencies where a threat to persons or property exists.
These buttons can be connected to a monitoring cen-
ter or locally via a silent alarm or an audible bell/si-
ren. The alarm can be used to request emergency as-
sistance from local security, police, or emergency ser-
vices.
1.4 Security
From such a perspective, the general definition of se-
curity is usually thought to be encountered in the ab-
sence – or at least unlikeliness – of threats to a certain
object. For example, David Baldwin has defined se-
curity astutely as a low probability of damage to ac-
quired (Baldwin, 1997). Similarly, for Lawrence
Krause and Joseph Nye, it was the absence of acute
threats to the minimally acceptable levels of the basic
values that a people consider essential to its survival
(Krause, 1975).
1.5 DMD P10
Dot Matrix Display P10 Running text or also known
as writing walking is one of the electronic media
which is very useful for conveying messages and in-
formation that can also be used as advertising means.
In its development, displaying running text is now
present not only in showing a series of running texts
but also for display images or logos (Simanjuntak,
2019).
iCAST-ES 2022 - International Conference on Applied Science and Technology on Engineering Science
704
2 METHOD
In the process of making a prototype, it is necessary
to design and flow to be able to know the develop-
ment and progress of the prototype as follows.
Figure 1: Prototype flow drawing.
The formulation of the problem is obtained based
on real events that often occur in the community, es-
pecially in the housing complex area.
Literature studies on research take sources from
various journals and the internet about wireless home
security, MQTT protocol, IO platform, Internet of
Things, DMD P10, and microcontroller (Imam Su-
trisno et.al., 2014).
2.1 Analysis
a. Functional Needs Analysis
1. Designing a P10 control system circuit using
MQTT.
2. Designing a data transmission system using
MQTT
3. Design a series of tools to support the DMD P10.
control system
b. Non-Functional Needs Analysis
1. Hardware (Hardware)
- Computer/Laptop
- DMD P10. control circuit board
- Jumper Cable
- USB cable
- DC5V adapter
2. Software
- MQTT Explorer app
- Platform IO
- Visual Studio Code
- Eagle
- Fritzing App
2.2 Design
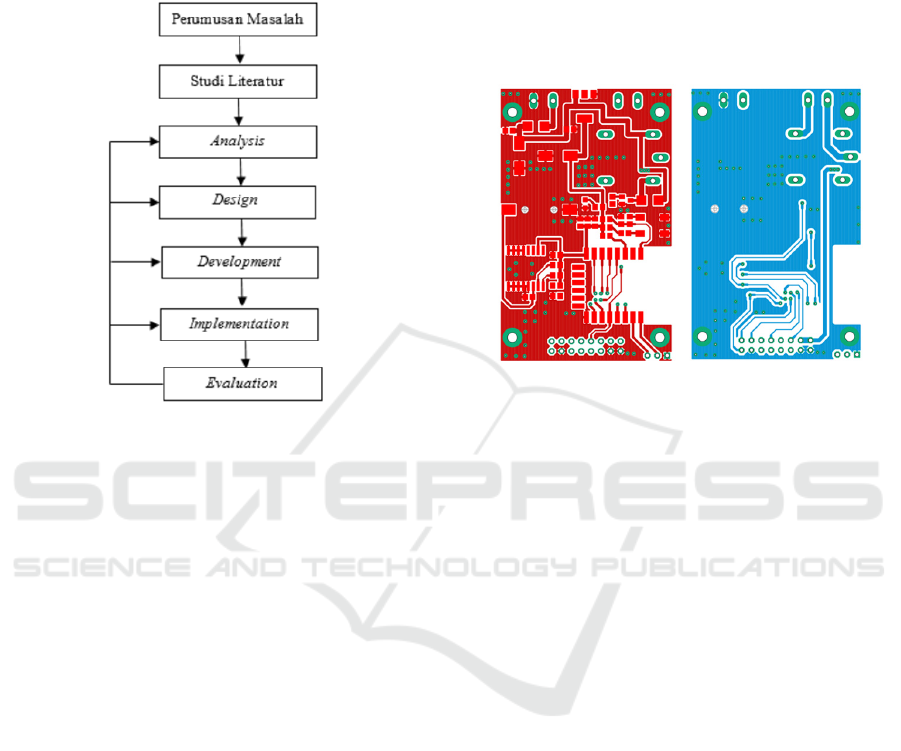
a. Hardware Design
The hardware design is carried out for the ESP 12-e
IC as well as other modules and devices.
Figure 2: Custom PCB Design.
b. Software Design
In the software design, the process of making a pro-
gram on the IO platform is carried out for sending
data from the MQTT explorer to DMDP10 (Sutrisno,
2012).
2.3 Development
Hardware and Software development is carried out as
follows.
- Define components
- Designing the board on the eagle, printing the
board, assembling the board to DMDP10, checking
the board and wiring board
- Upload programs and define efficient algorithms
- Test the tool to make sure the tool works well
2.4 Implementation
At this stage, testing the tool and checking the data
transmission via MQTT explorer to the board and dis-
playing the results on DMDP10 (Jami'in M.A.,2014).
2.5 Evaluation
Evaluation is the stage where the author sees the level
of success of the tool after passing the trial and is used
as input for the next stage of development (Sutrisno,
2014).
Machine to Machine Automatic Housing Area Security System Prototype Using MQTT IoT Communication Protocol
705

3 RESULT AND DISCUSSION
3.1 Circuit Results
The series of control systems that we developed to
control DMDP10 can work well. This circuit is
equipped with a buzzer that can be used to turn on the
speaker. Of course, this system is quite effective
when developed for security in homes and housing.
3.2 Prototype Work
Our prototype can send messages from MQTT ex-
plorer to the p10 control system board and display
text on DMDP10. In its development, an emergency
button will be added which will be connected wire-
lessly with the dmdp10 circuit located at the security
post.
3.3 How Prototypes Work
The way this tool works is quite simple but func-
tional. MQTT explorer will send a message to the p10
control system board. Then, from the control system,
P10 will display the results of writing on DMDP10.
Various forms of writing can be displayed. Starting
from numbers, a combination of letters, and others ac-
cording to the DMDP10 specification itself (Jami'in
M.A.,2015)..
3.4 Program Code
The following figure shows the program used to pro-
gram the p10 control system, board.
Figure 3: Image of program code on vscode.
The program that we created is centered on a messag-
ing system that uses MQTT to go to the p10 control
system board. Messages from MQTT explorer will be
sent and received by the esp12-e chip which is on the
p10 control system board. The message will be re-
ceived by the void callback function. This function
will accept the topic and payload sent by the MQTT
explorer. The topic will contain the payload. The pay-
load itself will contain the message that we send. This
message will be converted from a string to a char. Af-
ter being converted to char, the string copy or str copy
function will duplicate the value of this message and
send it to the display.drawstring function so that the
text can be displayed in dmdp10.
3.5 Improving Security System
Effectiveness
With this system, the level of security in residential
areas can be further increased and allows the commu-
nity to become closer to Society 5.0. Because this sys-
tem can facilitate prevention and handling of criminal
acts in residential areas by directly connecting all se-
curity posts which are usually located far from each
other. So that the security officers who are guarding
each post can monitor the overall situation in the
housing area without being limited by the monitoring
area of the security post.
3.6 Comparison with Conventional
Technology
When compared to conventional technology used to-
day, such as Handie Talkie, this system is far supe-
rior. Because Handie Talkie only conveys messages
directly which will then disappear when the message
is broadcasted. The gap lies in this, where sometimes
the message that has been broadcasted is not received
by the security officers due to various factors, such as
unclear message transmission or the officer is not
holding the Handie Talkie.
Meanwhile, when using this system, the message
can be maintained until the situation is under control.
So that it can be ensured that all officers at each secu-
rity post receive the message conveyed and act in ac-
cordance with their respective security procedures
(Sutrisno, 2019).
4 CONCLUSIONS
This system brings people closer to Society 5.0.
Where all social activities can be improved effective-
ness and efficiency with the Internet of Things, in-
cluding the security sector. With this increase, it can
iCAST-ES 2022 - International Conference on Applied Science and Technology on Engineering Science
706

create an ideal social environment by minimizing
criminal acts that occur. Prevention and handling of
criminal acts can also be done more precisely and
quickly than before. This prototype system has many
development possibilities. It is hoped that in the fu-
ture this system can be developed further. Starting
from input devices that can be upgraded with various
sensor modules such as cameras, infrared, and Li-
DAR, Main Processing Units that can be programmed
with Machine Learning-based Artificial Intelligence
that can be trained to recognize suspicious objects,
and Output Devices that can be added with motors
that can controlling instrumentation that can block the
way in and out of residential areas.
REFERENCES
A.Banks and R. Gupta, (2014), “MQTT Version 3.1.1,” Jt.
Pap. Open Group OASIS OMG.
A.I.Afolabi, O. Moses, M. S. Opeyemi, B.-O. A. Abraham,
and A.-Z. P. Temidayo, (2018), “Design and Construc-
tion of A Panic Button Alarm System for Security
Emergencies,” Int. J. Eng. Tech., vol. 4, no. 3, pp. 3–7,
[Online]. Available: http://www.ijetjournal.org
A.Syafrina, A. C. Tampubolon, Suhendri, N. Hasriyanti,
and H. E. Kusuma, (2018), “Preferensi Masyarakat ten-
tang Lingkungan Perumahan yang Ingin Ditinggali,” J.
RUAS, vol. 16, no. 1, pp. 32–45.
A.Wijayanto, (2019), “Penerapan Emergency System Ber-
basis Mobile (Study Kasus Institut Teknologi Telkom
Purwokerto),” J. Informatics, Inf. Syst. Softw. Eng.
Appl., vol. 1, no. 2, pp. 1–8, doi: 10.20895/inista.v1i
2.29.
Baldwin, David A. (1997). The Concept of Security. Re-
view of International Studies 23: 5–26.
Budiharjo, Eko. (1998). Sejumlah masalah permukiman
kota, Alumni: Bandung.
Certified Alarm Technician Level 1 Manual (1 April 2001)
NTS (10 October 2007)
Krause, Lawrence, and Joseph Nye. (1975). Reflections on
the Economics and Politics of International Economic
Organisations. In: Bergsten and Krause (eds.) World
Politics and International Economics. Washington
D.C.: The Brookings Institute.
Liputan6.com, (2017), “Awas, Maling Berkedok Pemulung
di Bone Jadi Modus Baru,”. https://www.liputan6.com/
regional/read/2854618/awas-maling-berkedok-pemulu
ng-di-bone-jadi-modus-baru.
M. Afdal and Y. P. Putra, (2020), “Rancang Bangun Panic
Button System Terintegrasi Menggunakan LBS pada
Kepolisian Resor Kota Pekanbaru,” J. Ilm. Rekayasa
dan Manaj. Sist. Inf., vol. 6, no. 1, pp. 83–92.
M. Anike, (2019), “Application Emergency panic Button
(AEPB) Berbasis Android Application Emergency
Panic Button (AEPB) Berbasis Android (Studi Kasus
RS St. Carolus Boromeus-Bello),” Sistemasi, vol. 8, no.
3, p. 367, doi: 10.32520/stmsi.v8i3.499.
N. Naik, (2017), “Choice of effective messaging protocols
for IoT systems: MQTT, CoAP, AMQP and HTTP,” in
2017 IEEE International Systems Engineering
Symposium (ISSE), Vienna, Austria, Oct. 2017, pp. 1–
7, doi:10.1109/SysEng.2017.8088251.
Nuryasin, Ilyas. (2021). Pengembangan Prototipe Tombol
Darurat Perumahan Berbasis Website. Jurteksi (Jurnal
Teknologi dan Sistem Informasi). 7.213-218. 10.33330/
jurteksi.v7i2.918.
Okezone.com, (2020), “Terekam CCTV, Pencuri Santai
Lewati Satpam Perumahan,”. https://news.oke
zone.com/read/20 20/10/10/519/2291496/terekamcctv-
pencuri-sepeda-santailewati-satpam-perumahan.
Simanjuntak, Imelda U.V. & Suhendar, Asep. (2018).
Jurnal Ilmiah Teknologi Informasi Terapan. Rancang
Bangun Running Text P10 16x32 Berbasis Arduino
Uno Dengan Komunikasi Sms (Short Message
Service). ISSN: 2407 - 3911
U. Hunkeler, H. L. Truong, and A. Stanford-Clark, (2008),
“MQTT-S — A publish/subscribe protocol for
Wireless Sensor Networks,” in 2008 3rd International
Conference on Communication Systems Software and
Middleware and Workshops (COMSWARE ’08),
Bangalore, India, Jan. 2008, pp. 791–798, doi:
10.1109/COMSWA.2008.4554519.
Imam Sutrisno, Mohammad Abu Jami’in, Jinglu Hu.
(2014). Modified fuzzy adaptive controller applied to
nonlinear systems modeled under quasi-ARX neural
network, Artificial Life and Robotics, vol. 19, issue 1,
pp. 22-26.
Sutrisno, Imam. (2012). Neural predictive controller of
nonlinear systems based on quasi-ARX neural network,
ICAC 12 - 18th International Conference on
Automation and Computing.
Jami'in M.A., Sutrisno I. (2014). An adaptive predictive
control based on a quasi-ARX neural network model.
13th International Conference on Control Automation
Robotics and Vision, ICARCV
Sutrisno, Imam. (2014). An improved adaptive switching
control based on quasi-ARX neural network for
nonlinear systems. Artificial Life and Robotics
Jami'in M.A., Sutrisno I. (2015). The State-Dynamic-Error-
Based Switching Control under Quasi-ARX Neural
Network Model. The Twentieth International
Symposium on Artificial Life and Robotics 2015
(AROB 20th 2015)
Sutrisno, Imam. (2019). Design of Pothole Detector Using
Gray Level Co-occurrence Matrix (GLCM) And Neural
Network (NN), IOP Conference Series: Materials
Science and Engineering
Machine to Machine Automatic Housing Area Security System Prototype Using MQTT IoT Communication Protocol
707
