
Covid-19 Spread Prevention System on Campus based on Student
Population Monitoring
Rachmad Imbang Tritjahjono
1
, Moch Bilal Zaenal Asyikin
2
, Noor Cholis Basjaruddin
3
and Andriyanto Setyawan
4
1
Department of Mechanical Engineering, Politeknik Negeri Bandung, Bandung, Indonesia
2
Department of Refrigeration, Air Conditioning, and Energy Engineering, National Chin-Yi University of Technology,
Taichung, Taiwan
3
Department of Electrical Engineering, Politeknik Negeri Bandung, Bandung, Indonesia
4
Department of Refrigeration and Air Conditioning Engineering, Politeknik Negeri Bandung, Bandung, Indonesia
Keywords: Monitoring, Base64, MQTT, HTTP.
Abstract: Various efforts have been made by the government in controlling the spread of covid-19, such as social
restrictions of various scales, restrictions on community activities, social assistance, to vaccination. One of
the sectors affected is education. This research aims to create a system to prevent the spread of virus covid-
19 from monitoring the number of student populations on campus. Thus, phisical teaching can still be
implemented. Every student who will access the campus area must scan the QR code on the mobile
application. Algorithms are designed to access QR codes based on course schedules and based on permission.
The system is also equipped with sanctions features for students late in or out of campus area. All section
systems, namely mobile applications, scanners, virtual servers and web platforms, are successfully created
according to the designed algorithm. The web platform can display the student population on campus in real-
time. In addition, base64 encryption is used to secure the converted data in QR codes.
1 INTRODUCTION
The covid-19 pandemic is a primary concern that is
being resolved around the world. The number of
deaths worldwide reached more than two million
(WHO Coronavirus Disease (COVID-19)
Dashboard, 2021). Indonesia became one of the
countries with a very high number of cases reaching
more than one million people with the number of
deaths of more than 32 thousand people (World
Health Organization, 2021). The covid-19 virus can
spread from an infected person's mouth or nose in the
form of tiny particles (aerosols) when they cough,
sneeze or talk. A person can contract this virus if the
aerosol enters his mouth or nose (Centers for Disease
Control and Prevention, 2020). In preventing the
spread of the covid-19 virus, the Indonesian
government has done various ways both at the central
level and at the regional level, such as closing access
to arrivals and departures to and from abroad (Satuan
Tugas Penanganan Covid-19, 2020), the imposition
of large-scale social restrictions (Kementerian
Sekretariat Negara Republik Indonesia, 2020), to the
enactment of restrictions on micro-based community
activities (Menteri Dalam Negeri, 2021). Many
sectors are affected by this policy. One of them is
teaching and learning activities of various levels of
education that have to be temporarily diverted online.
The Ministry of Education, Culture, Research and
Technology had announced that there would be a
return to in physical teaching. However, the plan was
delayed after the covid-19 delta variant spread and
became a significant focus for the current
government. In the face of a situation that continues
to develop dynamically, various efforts continue to be
made by multiple parties to innovate in offering
solutions to diverse problems. In this research,
innovation was carried out by creating a system to
monitor the student population on campus. This
research aims to succeed in management policies in
limiting or controlling the number of daily students
on campus to prevent the spread of covid-19. By
preparing the system, it is expected to be still able to
control the spread of covid-19 when phisical teaching
begins to be implemented.
Tritjahjono, R., Asyikin, M., Basjaruddin, N. and Setyawan, A.
Covid-19 Spread Prevention System on Campus based on Student Population Monitoring.
DOI: 10.5220/0010956100003260
In Proceedings of the 4th International Conference on Applied Science and Technology on Engineering Science (iCAST-ES 2021), pages 889-895
ISBN: 978-989-758-615-6; ISSN: 2975-8246
Copyright
c
2023 by SCITEPRESS – Science and Technology Publications, Lda. Under CC license (CC BY-NC-ND 4.0)
889
2 LITERATURE REVIEW
Research on student population monitoring systems
on campus includes engineering in terms of both
hardware and software. The use of minicomputers
and quick response (QR) readers from the hardware
side and encryption algorithms and QR codes from
the software side becomes one of the support in
running the system.
2.1 QR Code
This research will use QR code as student access in
and out of campus. QR code is a type of two-
dimensional symbol developed by Denso Wave in
1994. QR stands for “Quick Response”, indicating
that the code contents should be decoded very quickly
at high speed (Tiwari, 2016). Compared with 1-D
Codes, 2- D Codes can hold more data in a smaller
space. In Bar Codes, information is coded in one
direction or one dimension only (Saranya, Reminaa,
& Subhitsha, 2016). Table 1 shows the
comparative study of QR code and Bar code. The QR
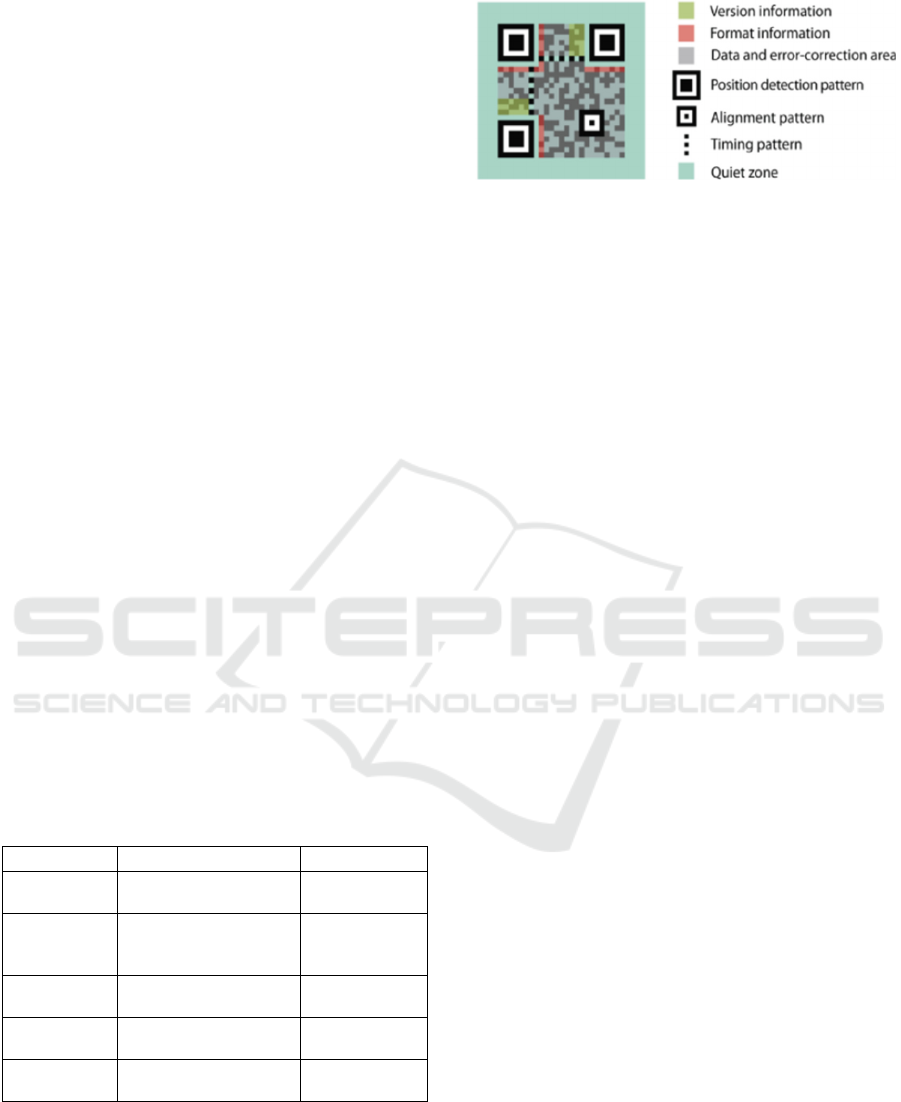
code structure can be seen in
Figure 1
. Each QR code
symbol is arranged in a square shape and consists of
function patterns and encoding regions. A quiet zone
boundary surrounds the entire symbol on all four
sides. There are four types of function patterns,
including finder patterns, separators, timing patterns,
and alignment patterns. The encoding region contains
data representing version information, information
format, and error correction (Priyambodo,
Novamizanti, & Usman, 2020).
Table 1: Comparison of QR code and barcode (Tiwari,
2016).
Features QR Code Bar Code
High
ca
p
acit
y
Upto 7089 numeric
di
g
its
10-20 digits
Durability
against
damage
Reading is possible
(upto 30% damaged)
Reading is
impossible
Reduced
Space
40 digits numeric
10 digits
numeric
360°
Supports 360°
reading
Horizontal
reading
Language
Su
pp
orte
d
Numeric,Alphanum
eric,Kan
j
i,Kana etc
Numeric,Alph
anumeric
Figure 1: QR code structure (Priyambodo, Novamizanti, &
Usman, 2020).
QR code will be built on the android application
that every student must enter the campus area. The
QR reader device is used to read QR codes in mobile
applications.
2.2 Base64 Encryption Algorithm
Real-time monitoring systems involve the use of
information between the user and the system.
Information encryption technology can meet the
security requirements of confidentiality of the
information and avoid the leakage of critical
information security threats. Therefore, encryption
technology is the base of authentication technology
and other security technology, and it is also the core
technology of information security (Yu, Wang, &
Wang, 2012). The base64 algorithm is used for
encoding and decoding data before it becomes a QR
code. The base 64 algorithm works to convert data
into an ASCII format based on the base number 64.
The resulting character in this base64 transformation
consists of A. Z, a. z and 0..9, plus the symbols "+"
and "/" and one character equal to (=) in the last two
characters used for pad charging or in other words
adjusting and completing binary data. The character
of the symbol to be generated will depend on the
process of the algorithm running. The stage in convert
a string with base64 algorithm are as follows (Yu,
Wang, & Wang, 2012):
• Break the bytes string to 3 bytes.
• Combine 3 bytes into 24 bits. with a record of 1
bytes = 8 bits, so 3 x 8 = 24 bits.
• Then 24 bits stored in-buffer (put together)
devided into 6 bits, and it will produce four
fractions
• Each fraction is converted into a decimal value,
where the maximum value of 6 bits is 63.
• Finally, make the decimal values into an index to
choose
And so on until the end of the bytes string that will
undergo conversion. If there is a remaining divider in
the encoding process, then add the character pad (=)
iCAST-ES 2021 - International Conference on Applied Science and Technology on Engineering Science
890
as the remaining sucker. Therefore, sometimes at
base64 will appear one or two characters (=). Base64
table index can be seen in Table 2.
Table 2: Base64 index table (Wen & Dang, 2018).
Val Char Val Char Val Char
Val Char
0 A
1 B
2 C
3 D
4 E
5 F
6 G
7 H
8 I
9 J
10 K
11 L
12 M
13 N
14 O
15 P
16 Q
17 R
18 S
19 T
20 U
21 V
22 W
23 X
24 Y
25 Z
26 a
27 b
28 c
29 d
30 e
31 f
32 g
33 h
34 i
35 j
36 k
37 l
38 m
39 n
40 o
41 p
42 q
43 r
44 s
45 t
46 u
47 v
48 w
49 x
50 y
51 z
52 0
53 1
54 2
55 3
56 4
57 5
58 6
59 7
60 8
61 9
62 +
63 /
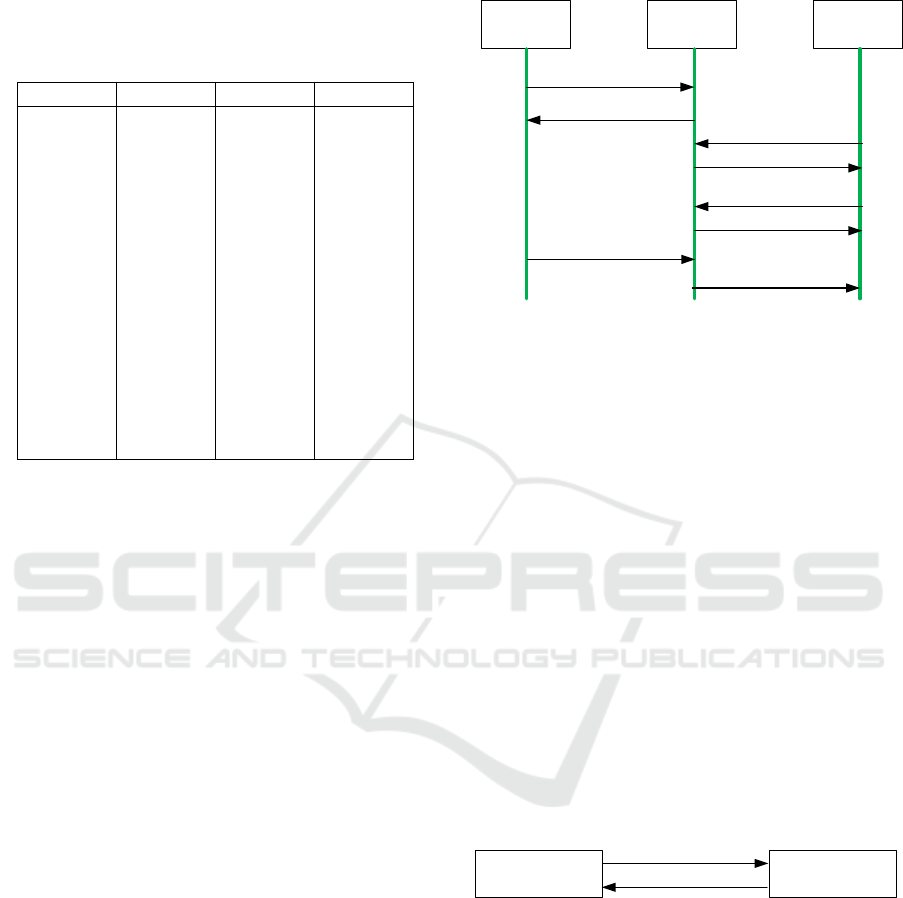
2.3 Message Queuing Telemetry
Transport (MQTT)
MQTT was invented by Andy Standford-Clark and
Arlen Nipper. The communication model used is
publish and subscribe and provide quality of service
(QoS) support. The publish mechanism is usually
used to send the data to the broker and the subscribe
mechanism is used to get the data from the broker
(Vyas, Rudani, & Student, 2018). The MQTT
structure can be seen in
Figure 2. With QoS, the
MQTT protocol can ensure higher delivery
capabilities than HTTP. There are three levels of QoS
(Shinde, Nimkar, Singh, Salpe, & Jadhav, 2016):
• QoS – 1 (at most once): guarantees the best
delivery efforts.
• QoS – 2 (at least once): Messages are sent at
least once, but it could be more.
• QoS – 3 (exactly once): guarantees that a
message sent is received once.
Publisher Broker Subscriber
(Source)
(Public
Server)
(Sink)
connect
connect Ack
connect
Connect Ack
Subscribe (topic)
Subscribe Ack
Publish (topic, data)
Publish (topic, data)
Figure 2: MQTT structure (manmeetjuneja5, 2020).
2.4 Hyper Text Transfer Protocol
(HTTP)
HTTP was initially designed as a protocol for web
browsing (Jin & Choi, 2012). HTTP is used by the
world wide web (www) to determine how its
messages will be sent and formatted. HTTP
formulates the specifications for messaging between
Web servers and clients. Since 1990, HTTP has been
in usage by the Worldwide Web global information
initiative (Huang, Xia, Sun, & Xue, 2015). This
protocol is responsible for the actions that servers
must take when sending information over the
network. When the URL is being entered into the
browser, this protocol sends an HTTP request to the
server, and then the HTTP response is sent back to the
browser. The protocol is also responsible for
controlling web pages on the World Wide Web to
format and represent data. The HTTP structure can be
seen in
Figure 3.
HTTP Client HTTP Client
HTTP Request
Message
HTTP Response
Message
Figure 3: HTTP structure (manmeetjuneja5, 2020).
3 SYSTEM DESIGN
3.1 Block Diagram
The system is designed to limit the number of
students in the campus area. The designed system
consists of several builder components: mobile
applications, scanners, virtual servers, and web
Covid-19 Spread Prevention System on Campus based on Student Population Monitoring
891
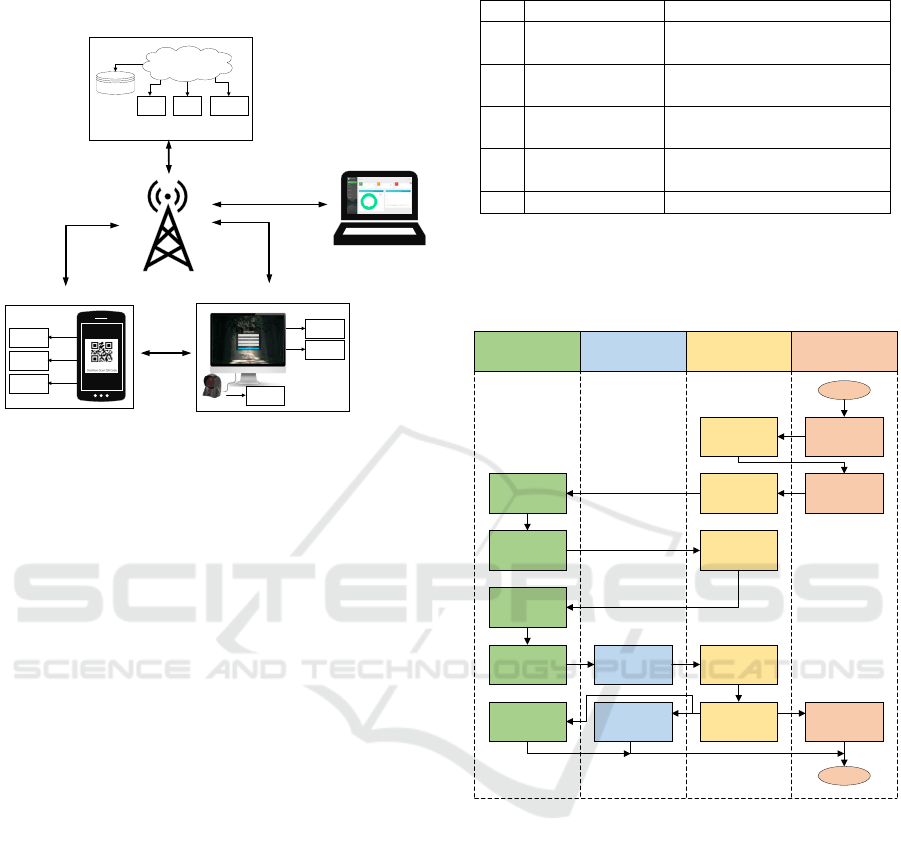
platforms. The block diagram of the system can be
seen in Figure 4 below.
Database
QR Code
HTTP Client
Notification
Mobile Application
HTTP Client
Scanner
MQTT
QR Scanner
Internet
Virtual Server
Server
API
MQTT
Broker
Web Platform
HTTP
Scanning
Figure 4: Block diagram system.
The Mobile Application block consists of an
HTTP client that plays a role in retrieving or
requesting data from the server using the http
protocol. Furthermore, a QR code is an image
generated by the mobile application to be scanned by
the QR code scanner in the scanner block section. The
scanner section consists of a QR Code Scanner to
scan the QR code of the mobile application to be
processed by the Mini PC and then verified to the
virtual server by making http requests through the
Internet Provider. A virtual server section is a
component that governs all needs. This block consists
of servers that play a role in capturing requests from
other sections, processing data to the database,
integrating requests with APIs and providing
responses to requests received. A web platform
section is a block that runs on a computer or mobile
device to view the combined data of all sections with
the role of administrator.
3.2 System Algorithm
System algorithm is designed in such a way as to
accommodate the needs of students greeting the
campus area but still meet the goals to be achieved.
There are 5 types of users in the system as a whole
with their respective functions. The following Table
3 is an explanation of each user.
Table 3: Users role.
No User Descri
p
tion
1
Administrator
The administrator of the
entire management syste
m
2 Head of
De
p
artment
Permit applicant verifier
3 Head of Study
Pro
g
ram
Permit applicant verifier
4 Department
Technician
Sanction verifier
5 Student Target use
r
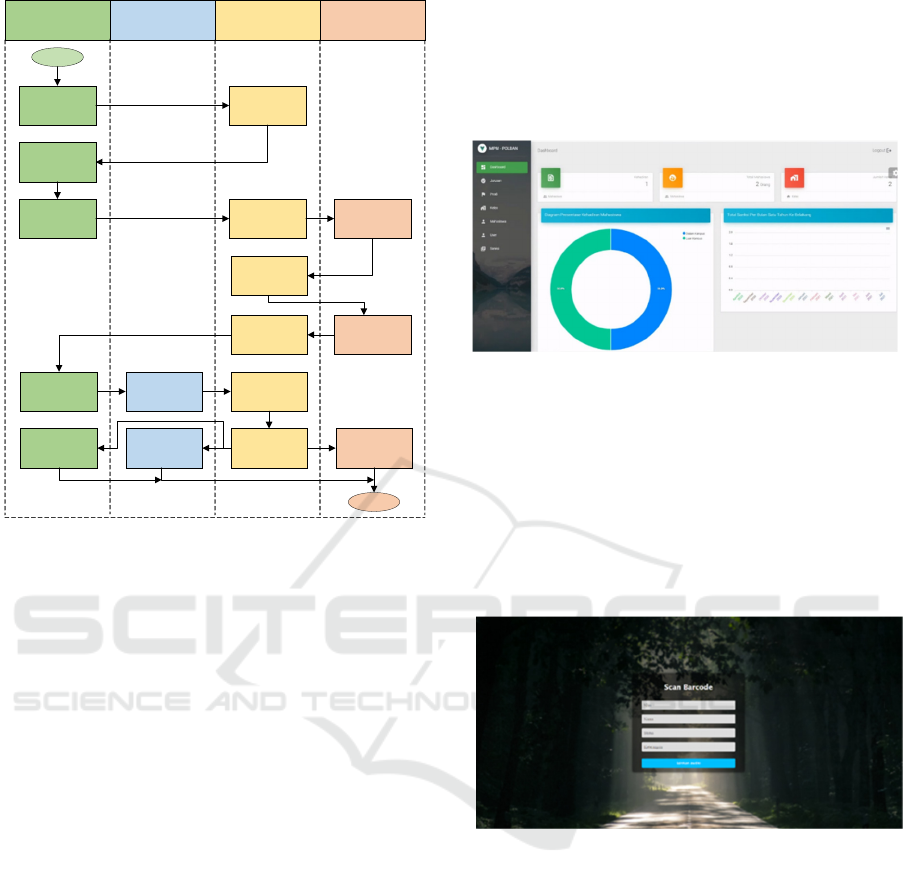
Each student can access the campus area in only
two conditions, when there is a schedule of courses
and if they have urgent needs. The system algorithm
for the first condition can be seen in
Figure 5.
Mobile
Application
Scanner Virtual Server Web Platform
Users
registration
Save on
databse
Get user login
through email
Login
User
verification
Show user
informations
Get QR code
through course
schedule
Scan the QR
code
User verification
Update the
information
data
Update the
database
Start
Finish
Show user
informations
Update the
information
data
Login as admin
User
verification
Figure 5: An algorithm based on courses schedule.
Each student will be registered by the user
administrator and get an account to log in to the
mobile application via email. Based on Fig. 6 above,
the system algorithm generally describes the system's
flow in each section. In addition, there will be a
notification in each mobile application every 15
minutes before the beginning of the course as a
reminder to every registered student user. Notices
will also appear 15 minutes before the student must
leave the campus area. This reminder system is used
so that every student user can obey all the rules
applied. The following condition system algorithm is
based on permission when students have an urgent
need by applying for approval on the mobile
application. The system algorithm designed for the
second condition can be seen in
Figure 6.
iCAST-ES 2021 - International Conference on Applied Science and Technology on Engineering Science
892
Mobile
Application
Scanner Virtual Server Web Platform
Login
User
verification
Show user
informations
Ask QR code
thr ough
perm ission
Update the
database
Start
Login as
Verifier
User
verification
Give
permission
Update the
database
Get QR code
thr ough
perm ission
Scan the QR
code
User verification
Update the
information
data
Update the
database
Finish
Show user
informations
Update the
information
data
Figure 6: An algorithm based on permission.
Students who apply for permission to visit the
campus area will only get a QR code on the mobile
application when the verifier obtains approval. Two
users must permit the applicant, namely:
• Head of the applicant's study program
• Head of the applicant department
In addition, sanctions are also applied to every student
user who is late, either entering the campus area or
leaving the campus area. Sanctions are converted into
sanction points where every minute of delay is
interpreted as one point of sanctions. The sanction
points will appear on the main page of the student user
mobile application. A compensation system is
implemented to pay for the sanctions where students
can submit them to registered technician users. User
technicians will reduce the value of points per
appropriate compensation.
4 RESULT
4.1 Platform
The realization of the design results at this stage has
been done. The creation of a web platform as in
Figure
7
named MPM - Pollan. The web-based platform has
several features, including :
• Real-time monitoring dashboard
• Users management
• Courses schedule management
• Class management
• Sanction management
Figure 7: Web platform dashboard.
4.2 Scanner
Student access using QR code makes it easier for
security to conduct supervision. The scanner
dashboard can be seen in
Figure 8
. The application is a local web-based
platform that will be installed on a mini PC and
installed on the entrance and exit gates of the campus.
Figure 8: Scanner dashboard.
4.3 Mobile Application
Students obtain access in and out of campus through
the android application, as in
Figure 9
. Features
contained in the android application include the
following.
• User management
• Course information
• QR code builder with base64 data
encryption
• Notification
• Sanction information
• Permission form
Covid-19 Spread Prevention System on Campus based on Student Population Monitoring
893
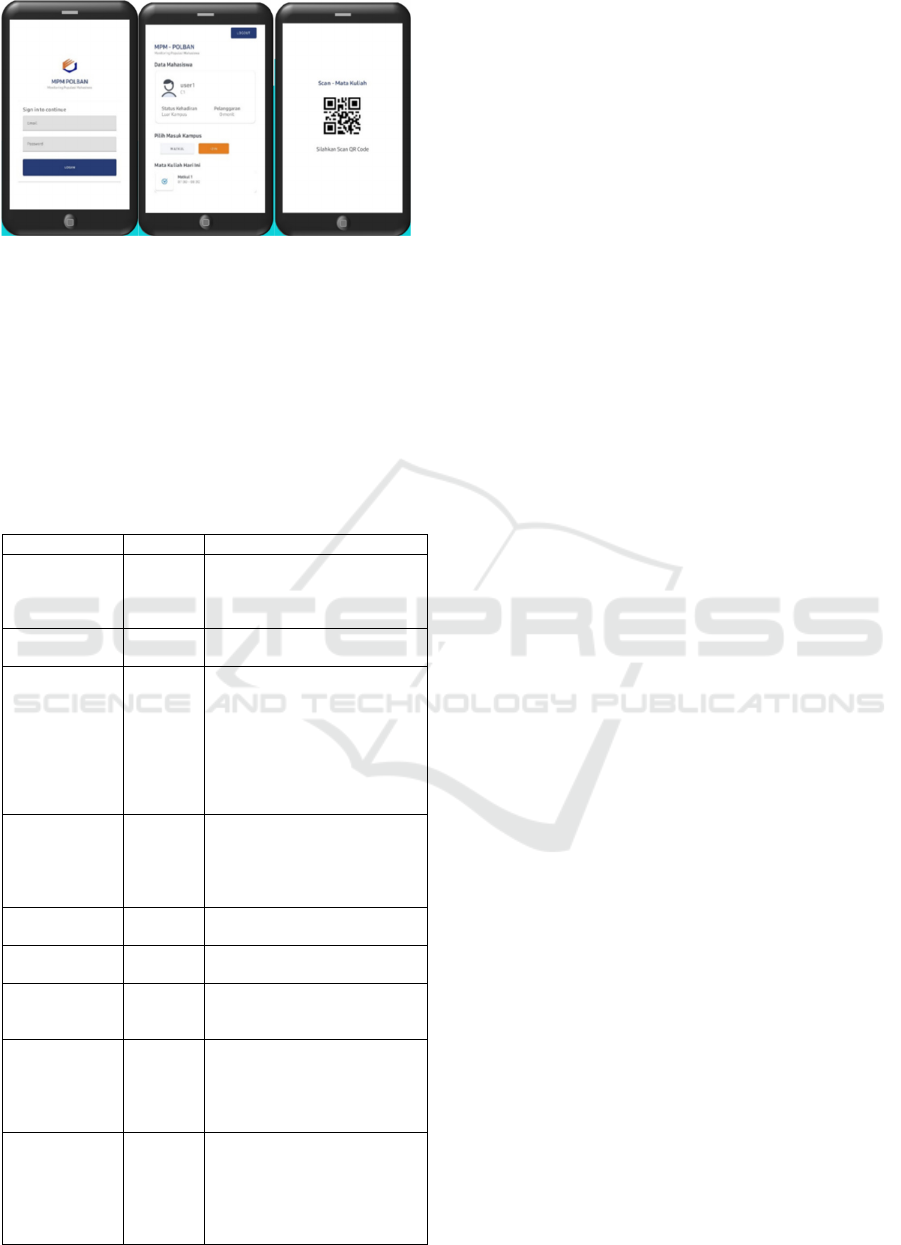
Figure 9: Mobile application.
4.4 Overall Testing
The overall testing is done by integrating the entire
system section. Testing is also done on the algorithm
based on the course schedule and based on
permission. The overall test results can be seen in
Table 4
below. All the commands that are parameters
in the test work well.
Table 4: Overall function testing.
Command Worked Output
User Account
Registration
9
User account is added to the
database, and email account
information is sent to the
user.
User Account
Login
9
Display the main page of the
application.
Notification
9
Generate notifications on
smartphones that have been
logged in in the mobile
application. Notifications
appear 15 minutes before the
initial course schedule and
15 minutes before the user
has to leave campus area.
QR code
based on
course
schedule
9
QR code access appears if
the user has a course
schedule. The mobile
application can display QR
codes.
Ask QR based
on permission
9
QR code access appears when
the verifie
r
gives permission.
Scan QR code
9
QR readers can read QR codes
from the mobile application.
Scanner UI
9
User information can be
displayed on a web-based
dashboard scanner.
Sanction
9
Sanction points appear on each
user's mobile application page.
User technicians can reduce
the value of points through the
web platform.
Realtime
monitoring
9
User status, sanction points,
and the number of student
populations on campus can
be displayed on the
dashboard of the web
platform in real-time.
5 CONCLUSIONS
The system of monitoring the student population to
prevent the covid-19 from spreading has been
successfully developed. All sections systems, namely
mobile applications, scanners, virtual servers and web
platforms, are successfully created according to the
designed algorithm. The Web Platform can display
the student population on campus in real-time. In
addition, base64 encryption is used to secure the
converted data in QR codes.
ACKNOWLEDGEMENTS
The authors would like to thank Pusat Penelitian dan
Pengabdian kepada Masyarakat Politeknik Negeri
Bandung for financial support with contract number
B/76.3/PL1.R7/PG.00.03/2021.
REFERENCES
Centers for Disease Control and Prevention. (2020, 10 28).
Retrieved from How covid spread:
https://www.cdc.gov/coronavirus/2019-ncov/prevent-
getting-sick/how-covid-spreads.html
Huang, Z., Xia, C., Sun, B., & Xue, H. (2015). Analyzing
and summarizing the web server detection technology
based on HTTP. 6th IEEE International Conference on
Software Engineering and Service Science (ICSESS),
1042-1045. doi:10.1109/ICSESS.2015.7339231
Jin, C.-G., & Choi, M.-J. (2012). Integrated Analysis
Method on HTTP Traffic. 14th Asia-Pacific Network
Operations and Management Symposium (APNOMS),
1-6. doi:10.1109/APNOMS.2012.6356056
Kementerian Sekretariat Negara Republik Indonesia.
(2020, 3 31). Retrieved from Peraturan Pemerintah
Republik Indonesia Nomor 21 Tahun 2020:
https://peraturan.bpk.go.id/Home/Download/125896/P
P%20Nomor%2021%20Tahun%202020.pdf
manmeetjuneja5. (2020, 07 06). Retrieved 08 03, 2020,
from GeeksforGeeks:
www.geeksforgeeks.org/difference-between-mqtt-and-
http-protocols/
Menteri Dalam Negeri. (2021, 02 05). Retrieved from
Instruksi Menteri Dalam Negeri Nomor 03 Tahun 2021:
https://covid19.go.id/p/regulasi/instruksi-menteri-
dalam-negeri-nomor-03-tahun-2021
Nasional, K. P.-1. (2021, 02 11). Penguatan 3M dan 3T
Kunci Pengendalian Pandemi. Retrieved from
https://covid19.go.id/p/berita/penguatan-3m-dan-3t-
kunci-pengendalian-pandemi
Priyambodo, A., Novamizanti, L., & Usman, K. (2020).
Implementasi QR Code Berbasis Android pada Sistem
iCAST-ES 2021 - International Conference on Applied Science and Technology on Engineering Science
894

Presensi. Jurnal Teknologi Informasi dan Ilmu
Komputer, 7, 1011-1020.
Sadeq, A. S., Hassan, R., Al-rawi, S. S., Jubair, A. M., &
Aman, A. H. (2019). A Qos Approach For Internet Of
Things (Iot) Environment Using Mqtt Protocol.
International Conference on Cybersecurity (ICoCSec),
59-63. doi:10.1109/ICoCSec47621.2019.8971097
Saranya, K., Reminaa, R. S., & Subhitsha, S. (2016).
Modern applications of QR-Code for security. IEEE
International Conference on Engineering and
Technology (ICETECH), 173-177.
doi:10.1109/ICETECH.2016.7569235
Satuan Tugas Penanganan Covid-19. (2020, 12 28).
Retrieved from Surat Edaran Nomor 4 Tahun 2020:
https://www.imigrasi.go.id/uploads/covid/regulasi/12-
11-29-SE_Kasatgas_No_4_Tahun_2020_(1).pdf
Shinde, S. A., Nimkar, P. A., Singh, S. P., Salpe, V. D., &
Jadhav, Y. R. (2016). MQTT - Message queuing
telemetry transport. Int. J. Res, 3, 240-244.
Suwito, B. (2006). Konsep Enkripsi dan Dekripsi.
Surabaya.
Tiwari, S. (2016). An Introduction to QR Code Technology.
International Conference on Information Technology
(ICIT), 39-44. doi:10.1109/ICIT.2016.021
Vyas, D. J., Rudani, N. N., & Student, M. T. (2018). MQTT
& IOT Based Control and Monitoring of Smart Green
House. IJEDR Int. J. Eng. Dev, 6.
Wen, S., & Dang, W. (2018). Research on Base64
Encoding Algorithm and PHP Implementation. 26th
International Conference on Geoinformatics, 1-5.
doi:10.1109/GEOINFORMATICS.2018.8557068
WHO Coronavirus Disease (COVID-19) Dashboard.
(2021, 02 11). Retrieved from World Health
Organization: https://covid19.who.int/
World Health Organization. (2021, 02 11). Retrieved from
https://covid19.who.int/table
Yu, L., Wang, Z., & Wang, W. (2012). The Application of
Hybrid Encryption Algorithm in Software Security.
Fourth International Conference on Computational
Intelligence and Communication Networks, 762-765.
doi:10.1109/CICN.2012.195
Covid-19 Spread Prevention System on Campus based on Student Population Monitoring
895
