
Overview of the Balancing Pervasive Information Systems Project
and a Call for Research Collaborations
Sherry L. Xie
1,2,3
1
School of Information Resource Management, Renmin University of China, 59 Zhongguancun Ave., Beijing, China
2
Center for Digital Records Management Research, Beijing, China
3
Key Laboratory of Knowledge and Data Engineering, Ministry of Education of China, China
Keywords: Pervasive Information Systems, Ubiquitous Computing, Pervasive Computing, Digital Decision, Technology
Accountability, Accountability Information, Digital Records.
Abstract: The Research on Balancing Theories and Mechanisms to Pervasive Information Systems (B2P) is one of the
component studies of the Records-centered Digital Information Management Theory and Mechanisms
(DI{R}Mtm) Project, which aims pointedly at synchronizing records/information related research interests
with the evolution of information technologies and their joint impact on society. Due to the breakthroughs in
cloud computing, big data, the Internet of Things and artificial intelligence, ubiquitous/pervasive computing,
conceived in 1988, has now been rapidly advanced. As its materialization in organizations, pervasive
information systems (PISs) converges information technologies, data, digital operations and human actors
and functions as the main channel for digital decisions. Digital decisions, therefore, are autonomous,
algorithmic and penetrating, possessing influential abilities that are much greater than any single technology
in human history, including the Internet. Such abilities make it a strong force for societal advancement, yet,
at the same time, a potential hurdle – even harm – for decision recipients who are unaware of the decision-
making methods. The B2P study is conceived as a reaction to this phenomenon. This paper gives an overview
of the B2P study and calls for collaborations among researchers from the various fields relevant to the aims
of the study, i.e., archival science, records management, information science, pubic administration, law, social
sciences, and computer sciences.
1 INTRODUCTION
The Balancing Pervasive Information Systems
Project, fully entitled as Research on Balancing
Theories and Mechanisms to Pervasive Information
Systems (B2P), is one of the component studies of the
Records-centered Digital Information Management
Theory and Mechanisms (DI{R}Mtm) Project. The
DI{R}Mtm project, founded by the Fundamental
Research Funds for Central Universities and the
Research Funds of Renmin University of China
(15XNL032), is currently at its second phase (2018 –
2020), which, as suggested by the findings of the first
phase of the DI{R}Mtm project, aims more pointedly
at synchronizing research interests with the evolution
of information technology. This paper gives an
overview of the B2P study and calls for
collaborations among researchers from the various
fields relevant to the aims of the study, i.e., archival
science, records management, information science,
pubic administration, law, social sciences, and
computer sciences.
2 STUDY OBJECTS
The study objects of the B2P study include two major
topics: pervasive information systems and the issue
with digital decision accountability.
2.1 Pervasive Information Systems
Pervasive information systems (PISs) is an emerging
paradigm in the field of information systems (ISs),
which emphasizes pervasiveness. The idea of
pervasiveness is in concert with the visions of
ubiquitous computing (UbiCom) and (the later on)
pervasive computing (PerCom), all aiming at
“integrating computers seamlessly into the world”
(Weise, 1991). PISs, therefore, can be viewed as an
Xie, S.
Overview of the Balancing Pervasive Information Systems Project and a Call for Research Collaborations.
DOI: 10.5220/0007234304070416
In Proceedings of the 10th International Joint Conference on Knowledge Discovery, Knowledge Engineering and Knowledge Management (IC3K 2018) - Volume 1: KDIR, pages 407-416
ISBN: 978-989-758-330-8
Copyright © 2018 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
407
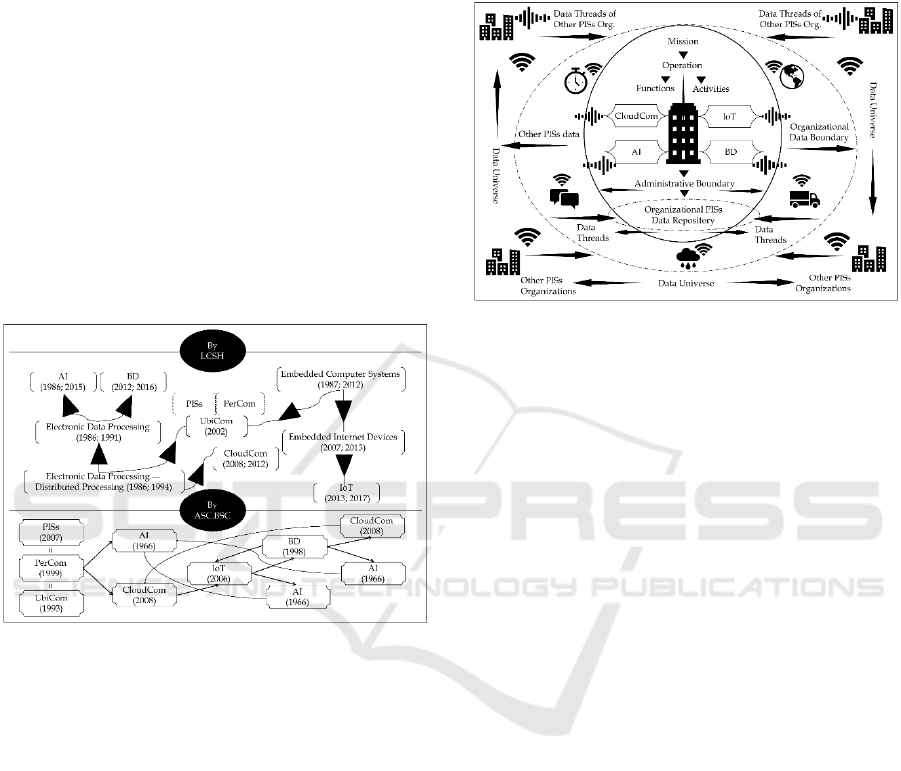
assembly of information technologies that extends
ISs from traditionally a PC network into a web of
heterogeneous cooperating/communicating objects,
both inside and outside the physical boundary of
organizations. At present, the assembly includes
technologies such as artificial intelligence (AI), big
data (BD), the Internet of Things (IoT), and cloud
computing (CloudCom), all of which – termed as
PISs component technologies in this application –
possess with each other interrelated relationships.
Relying on the entry relationships of the Library of
Congress Subject Heading (LCSH) (LC, 2018) and
the subject relationships of the databases of Academic
Search Complete and Business Source Complete
(ASC.BSC) (EBSCO, 2018), Figure 1 displays the
relationships among the PISs component
technologies (LCSH: year of entry creation; year of
revision and ASC.BSC: earliest publication year).
Figure 1: PISs and Its Component Technologies.
The application of PISs can be characterized as
personal, domestic, corporate, and public
(Kourouthanassis et al., 2010). The proposed research
limits its inquires to “corporate” and refines it as
organizations represented by government institutions
and business corporations. This is because first, the
setting of organization is the indigenous context to the
origination of ISs (Davis, 1974) and second, these
representative organizations typically have a more
influential stance than other types of organizations,
which signals research priority. Figure 2 depicts the
sitting of a PISs organization in the PISs environment,
where it
operates with both an administrative
boundary established by functions and activities and
an organizational data boundary made up by diverse
types of data threads supplied by the PISs component
technologies. By the very nature of PISs, the
organizational data boundary goes beyond the
administrative boundary and it interacts dynamically
with data flows from both within and outside. As
such, an organizational PISs data repository pulls or
receives data from other PISs organizations and at the
same time, contributes data threads to the PISs data
universe.
Figure 2: A PISs Organization in a PISs Environment PISs
and Its Component Technologies.
Deploying PISs in organizations is now believed
imperative or inevitable because of the comparative
advantages (or surviving capabilities) it offers.
Empowered by PISs defining features such as being
embedded, distributed, context-aware, portable and
real-time, organizations are becoming “smart” or
“intelligent”: their manners of handling both their
internal and external affairs are becoming more
prompt, precise and proactive. Underneath this
smartness/intelligence lies one foundation –
autonomous decision making, which outputs
decisions without human intervention. Two main
types characterize such decisions:
machine/algorithm-made decisions, which are done
by digital agent alone, and machine/algorithm-aided
decisions, which are made jointly by human and
digital agents. Digital agents here include any data
processing devices or models, large or small,
independent or as one part of a complex whole. As
Figure 3 displays, a PISs enabled smart organization
utilizes both human and digital agents in all its
decision-making processes, be they strategic or
transactional, and many of the decision-making
processes are invisible to humans, be they human
agents or human decision recipients. Indeed, being
invisible to human is the ultimate goal of PISs
deployment as the UbiCom idea indicates that “[t]he
most profound technologies are those that disappear”
(Weiser, 1991).
FR-HT 2018 - Special Session on Managing Digital Data, Information and Records: Firm Responses to Hard Technologies
408
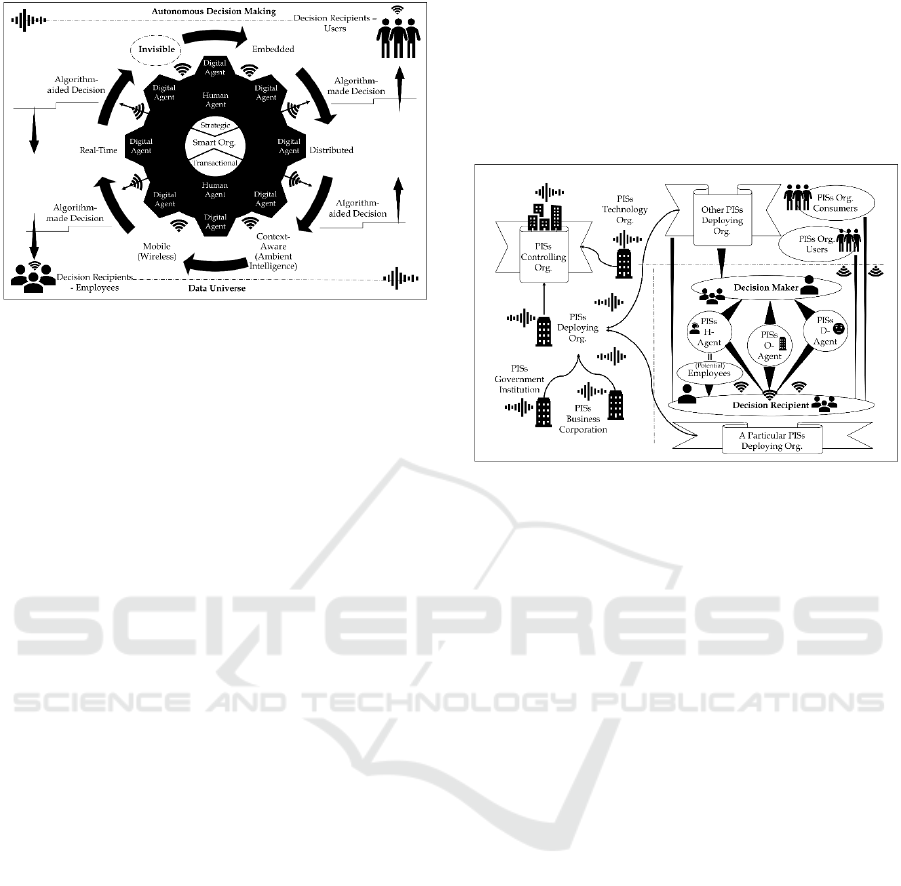
Figure 3: Characteristics of PISs Decision-Making.
As such, entities in decision making processes
exhibit relationships that are dynamic and interactive,
so do the made decisions in terms of the time of their
existence and the way they are being delivered.
Decision maker and decision recipient are two typical
types of entities in decision making processes; in
PISs, however, they function in a much more
complicated manner. As exemplified in Figure 4,
where a PISs deploying organization (dotted line) is
situated in a backdrop made up by the other types of
PISs organizations, decision maker has three types
and decision recipient has as many as seven. For
decision makers, there are PISs human agent (PISs H-
Agent), PISs digital agent (PISs D-Agent), and PISs
organization agent (PISs O-Agent), with the former
two being considered as individual or independent
unit and the later a collective whole. For decision
recipients, there are:
Potential employees of the PISs (i.e., job
applicants);
Employees of the PISs, who are also the PISs
H-Agent;
PISs users, who voluntarily make use of the
services and/or products provided by the PISs
deploying organization for work purposes;
PISs consumers, who consume the services
and/or products provided by the PISs deploying
organization for personal purposes; and
All the three types of decision makers.
Outside this particular PISs deploying organization
are other PISs deploying organizations, either of the
type of government institution or business
corporation, and PISs technology organizations. The
type of PISs deploying organizations together with
the type of PISs technology organizations constitutes
PISs controlling organization in the sense that, for the
former, they control the specific deployment of PISs
in their respective organizations, and for the latter,
they control the underlying PISs technologies of all
PISs deployments.
Figure 4: Entity Relationships in PISs Decision Making
Environment.
These decision entities are listed as 3 types below.
Type 1: Decision Maker:
PISs Organization
PISs H-Agent (individual)
PISs D-Agent (independent unit)
PISs O-Agent (the collective whole of H-Agent
and D-Agent)
Other PISs organization
Type 2: Decision Recipient:
For one PISs organization:
o PISs H-Agent
o PISs D-Agent
o PISs O-Agent
o PISs Consumers
Other PISs organization
None-PISs Organization
PISs Potential Employee
PISs Employee
Overview of the Balancing Pervasive Information Systems Project and a Call for Research Collaborations
409
Type 3: PISs Decision:
Algorithm-Aided
Work Decision: Transactional
Work Decision: Strategic and Transactional
Living Decision: Transactional
Work Decision: Recruitment
Work Decision: Performance
Work Decision: Strategical
Work Decision: Purchase
2.2 The Issue with Digital Decision
Accountability
Emerging in this PISs environment is the concern
about digital decision accountability, i.e., how PISs
enabled decision-making processes can be explained
and justified when legitimate inquiries arise.
Accountability is a concept that offers many utilities
(Jabbra and Dwivedi, 1989; Mulgan, 2000;
Lindberg, 2009; Bovens, 2010) and is entangled
with many other concepts such as responsibility,
liability, transparency, etc. (Fox, 2007; Hood, 2010;
Thompson, 2014; Castiglione, 2018). Its core,
however, can always be distilled into the notion of
accounting for actions or decisions. In this
application, “accounting for” is furthered as two
distinctive concepts, i.e., explanations and
justifications. Explanations here refer to the
information that answers the question how decisions
were made, and justifications here refer to the
information that answers the question why the
decisions were so made. Together, these two types
of information form what the proposed research
labels as (digital decision or PISs) accountability
information, which is one of the fundamental
constituents of the (digital decision or PISs)
accountability regime. Accountability information
can be described by two aspects: the way by which
it comes into existence and the way by which it
participates in decision-making processes. Tightly
associated with accountability information are the
concepts of availability and answerability.
Availability here has two forms: one from the stance
of the accountor and the other from that of the
accountee (both terms from Bovens, 2007).
Availability for an accountor means the provision of
accountability information, which is aided by the
actions of keeping, identifying and delivering
accountability information, and availability for
accountee means the obtaining of accountability
information, which requires the actions of initiating
accountability inquiry and receiving accountability
information. Answerability here means that the
provided/received information must be able to
answer the inquiry, i.e., it needs to be relevant (to
the decision being questioned), sufficient (for
covering the entire decision-making process),
understandable (by the accountee’s criteria) and
credible (by commonly accepted criteria).
3 CURRENT RESEARCH
Research dedicated to accountability in PISs,
including UbiCom and PerCom, does not currently
exist (dedicated here refers to restricting
“accountab*” in Title in databases of Web of Science
and Academic Search Complete). For its components,
a small number of dedicated articles were found: 25
in English (1 on AI, 3 on IoT, 6 on BD, and 15 on
CloudCom) and 4 in Chinese (1 on AI and 3 on BD),
and an extended search for “right to know”, a concept
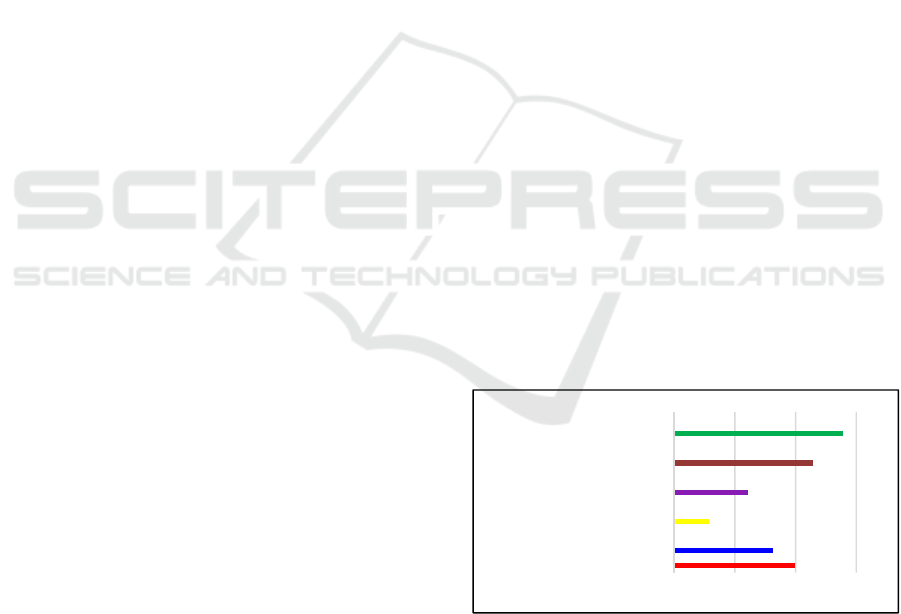
close to accountability, returned no hits. As Figure 5
shows, PISs technology and accountability are both
topics that the academia is keen about and despite the
small numbers of articles, the relationship between
the development of technology and accountability
tends to be positive, i.e., the number of articles
regarding the intersection of accountability and a
particular technology increases along with the
increase of the number of articles regarding the
technology. This demonstrates that there is increased
attention paid to technology accountability.
Figure 5: Development of PISs Technologies and Their
Relationships with Accountability.
From reviewing those dedicated articles and the
relevant ones cited by them, the following
observations can be generated:
Discussions on accountability in relation to
advanced technology started with AI in 2001
7939
6486
1
2294
0
4892
3
9160
8
11123
15
0 4000 8000 12000
Accountability
AI+Accountability
PISs+Accountability
IoT+Accountability
BD+Accountability
CloudCom+Accountability
FR-HT 2018 - Special Session on Managing Digital Data, Information and Records: Firm Responses to Hard Technologies
410

and kept accelerating with the other
components in particular cloud computing;
Most of the articles take the viewpoint of IT
(i.e., authored by IT professionals), and they
focus mainly on data privacy (Xhafa et al.,
2015; Grunwell and Sahama, 2015) and user
accountability, i.e., how users or employees
can be accountable for their actions (Boos, et
al., 2013; Gao and Iwane, 2015; Khan et al.,
2016) (labelled in this application as individual
accountability);
Others are mainly authored by sociology and
legal experts, which focus on both the concept
itself and its application to technologies (6,
2010; Vedder and Naudts, 2017) (labelled in
this application as organizational
accountability);
Information is not the focus of study, albeit it
appeared inevitably (e.g., Weber, 2011; Boos,
et al., 2013);
There are three main consensuses:
o The complexity of the issue (e.g., Ko et al.,
2011; Gao and Iwane, 2015);
o The need for accountability to be
addressed at the early stage of technology
development (e.g., Boos, et al., 2013;
Arnaboldi et al., 2017); and
o The need for further research as many of
the technologies are new or being renewed
(e.g., Arnaboldi et al. 2017).
For the four Chinese articles, only two qualify as
research articles. Neither of them identified the
meaning of accountability within their respective
research frames and both promoted technological
means for accountability insurance. Differences lie
mainly on the level of technological details, with the
one on online media suggesting not just people but
also technologies are needed to be held accountable
in a general manner (Jiang and Yang, 2016) and the
other on privacy protection outlining an
accountability strategy (Zhu et al., 2016). The core of
the strategy, however, targets only the action of
malicious leaking of user information on the part of
service providers, which does not correspond to the
proposed research in that:
The concept of PISs Controlling Organization
has a much broader coverage than service
providers;
For a particular PISs Controlling Organization,
the entirety of its decision-making activities is
under investigation – not just the action of
malicious leaking of user information. To
protect user information from breach or leaking
is readily distinguishable from the unjustifiable
use of personal information in normal business
operations.
There are research institutions internationally
concerning PISs technologies in relation to
transparency and accountability. For example:
United States: Brookings Institution
(technology, accountability and international
law); Data and Society (social and cultural
issues arising from data-centric and automated
technologies);
United Kingdom: Open Data Institute (data
identification of economic evidence and
business cases combined with social and
environmental impacts);
United Kingdom and Germany: Information
Innovation Lab (development of fundamental
rights of communities everywhere around the
world);
Canada: The Citizen Lab (“Lifting the lid off
the Internet”; intersection of information and
communication technologies, accountability
mechanisms, and global security)
Australia: Smart Cities Research Institute (the
grand challenges facing large, fast-growing
cities in Australia and around the world; new
methods of accountability and feedback);
The Information Accountability Foundation
with Americas Interest Group, Asia Discussion
Group, EU GDPR Group (data protection law
and practice through accountability-based
information governance).
The EU General Data Protection Regulation
(GDPR) (Regulation (EU) 2016/679) has included
accountability principles in its personal data
protection framework. All these efforts, however,
focus typically on one aspect albeit with much depth.
As the same as what is displayed in Figure 5, the
interplay between accountability and PISs as a whole
Overview of the Balancing Pervasive Information Systems Project and a Call for Research Collaborations
411

remains currently a gap. The produced balancing
theories and mechanisms therefore aim at
The realization of a healthy, fulfilling society,
one that cares about everyone with equality,
promotes economic prosperity with fairness,
and materializes democracy in real life events;
The optimization of corporations’ practice of
social and ethic responsibility;
The advancement of disciplinary,
interdisciplinary (i.e., integrating knowledge
from different disciplines) and
transdisciplinary (i.e., creating a unity of
intellectual frameworks beyond the
disciplinary perspectives) knowledge, as well
as the joint process of knowledge production;
and
The preparation of the next generation that is
PISs accountability ready.
4 RESEARCH QUESTIONS
The following research questions are identified as key
to the identified technology accountability issue, and
they are grouped as theory-related and mechanism-
related. For the theory-related group, two sub-groups
are further developed as theory deductive type and
theory inductive type.
Theory- related: Deductive:
To what extent can the existent accountability
theories in the field of public accountability be
instructive to the technology accountability
issue? e.g., principal-agent theory (Gailmard,
2007)? Contingency theory (Mansbridge,
2014)?.
Given the established relationship between
information and accountability (Stewart,
1984; Parkinson, 1993; GC, 2007; Obama,
2009; United Kingdom, 2009; NAA, 2017),
what kind of application of the current
development of computational archival
science and digital records management (CAS
and DRM) are suitable for building
technology accountability solutions?
Theory- related: Inductive:
In the context of equal social and economic
development, what the considerations or
criteria should be for the properness of balance
between accountability and PISs be
determined?
Among the different types of balancing forces
(i.e., PISs H-Agent type of decision recipients,
in forms of individual and aggregations), what
are the relationships between them? And what
kind of relationships can facilitate a positive
impact on developing PISs balancing power?
What should the responsibility relationships
be among all the entities in Figure 4?
What will the PISs synergetic effect be when
compared to the impact of individual PISs
technologies on accountability?
Will the relationship between PISs
deployment and PISs accountability remain
the same across industries or it will change? If
it will change, then what the most influential
factors for the change are?
Mechanism - related:
How can accountability information be
identified for a particular decision? How to
decide its ownership? When should the
identification take place? At the time of
deploying PISs? At the time of receiving
accountability inquiries? Or automatically
when a decision is made?
How can accountability information for a
particular decision be delivered? When should
the delivery take place? At the time of
receiving accountability inquiries? Or
automatically when accountability
information is identified?
How can the answerability of accountable
information be ensured?
How can the discharge of responsibilities be
evaluated?
Can PISs technologies be used to automate the
responding process to accountability inquires?
FR-HT 2018 - Special Session on Managing Digital Data, Information and Records: Firm Responses to Hard Technologies
412
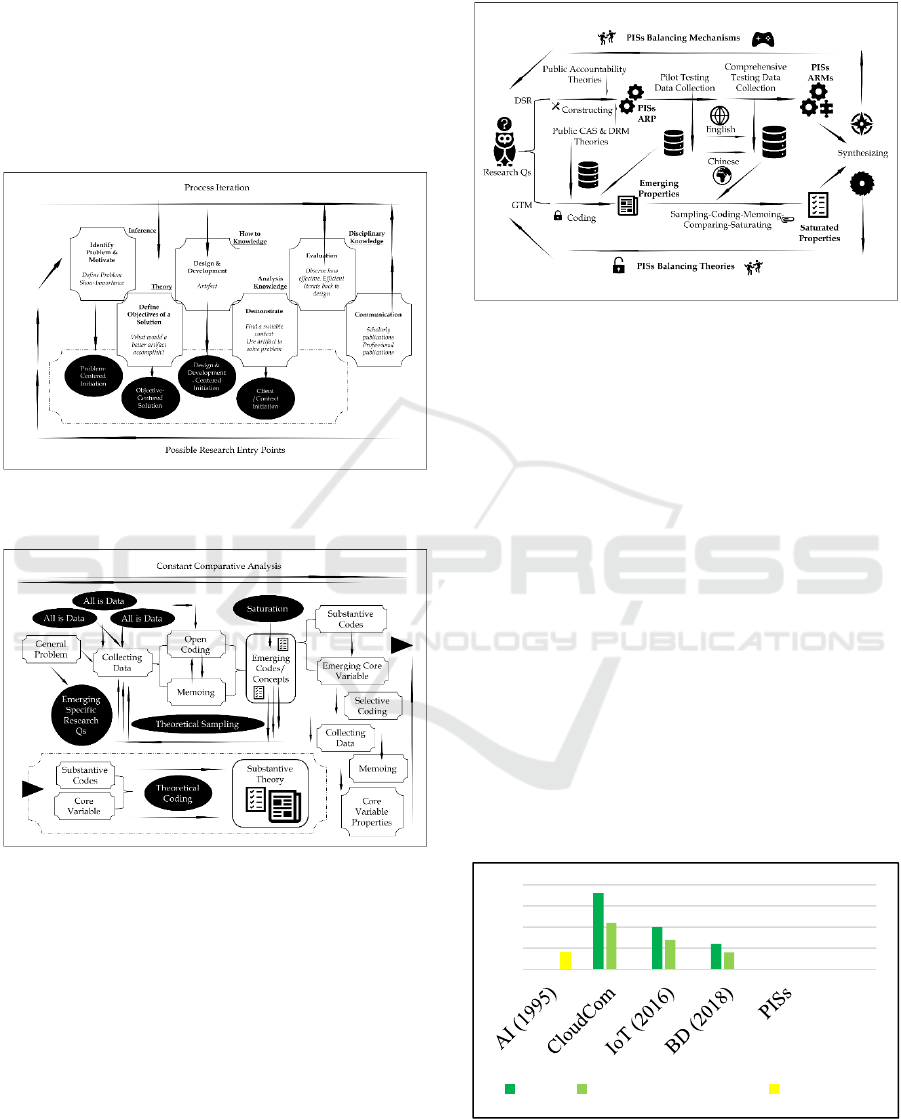
5 RESEARCH DESIGN
For investigating the above research questions, two
research methodologies were selected: design science
research (DSR) and grounded theory methodology
(GTM). Both methods have been promoted to be
employed in ISs (Gregor and Hevner, 2013; Wiesche
et al., 2017) and their investigating courses are
illustrated in Figures 6 and 7.
Figure 6: Design Science Research Methodology Process
Model (Peffers, et al., 2008).
Figure 7: Grounded Theory Methodology Process Model.
For the proposed research, DRS is responsible
for answering the research questions of the theory
deductive type and of the mechanism-related, and
GTM is responsible for answering the research
questions of theory inductive type. Data for both
methods include the types of published research,
which, as displayed in Figure 5, is sizable by now and
is constantly growing, and empirically collected data,
which will be done by the tools of questionnaires and
interviews. By integrating these two methods,
balancing theories and mechanism to PISs are
expected to be produced. Figure 8 displays the overall
process of the research:
Figure 8: PISs Balancing Theories and Mechanisms
Research Process.
6 A CALL FOR RESEARCH
COLLABORATIONS
The proposed research is considered leading
internationally in the following three aspects:
• Focusing on the impact of integrated PISs
instead of just that of PISs component
technologies (Figure 2);
• Findings to be instructive to the development
of standards by ISO, who is currently at the
initiating stage of developing relevant
standards (Figure 9);
• Enhancing the understanding and application
of PISs to the fields of social science and
humanities (Figure 10).
Figure 9: ISO Standards Re PISs Component Technologies
Currently Under Development.
18
10
6
0
11
7
4
0
4
0
5
10
15
20
Total Under Development Withdrawn
Overview of the Balancing Pervasive Information Systems Project and a Call for Research Collaborations
413
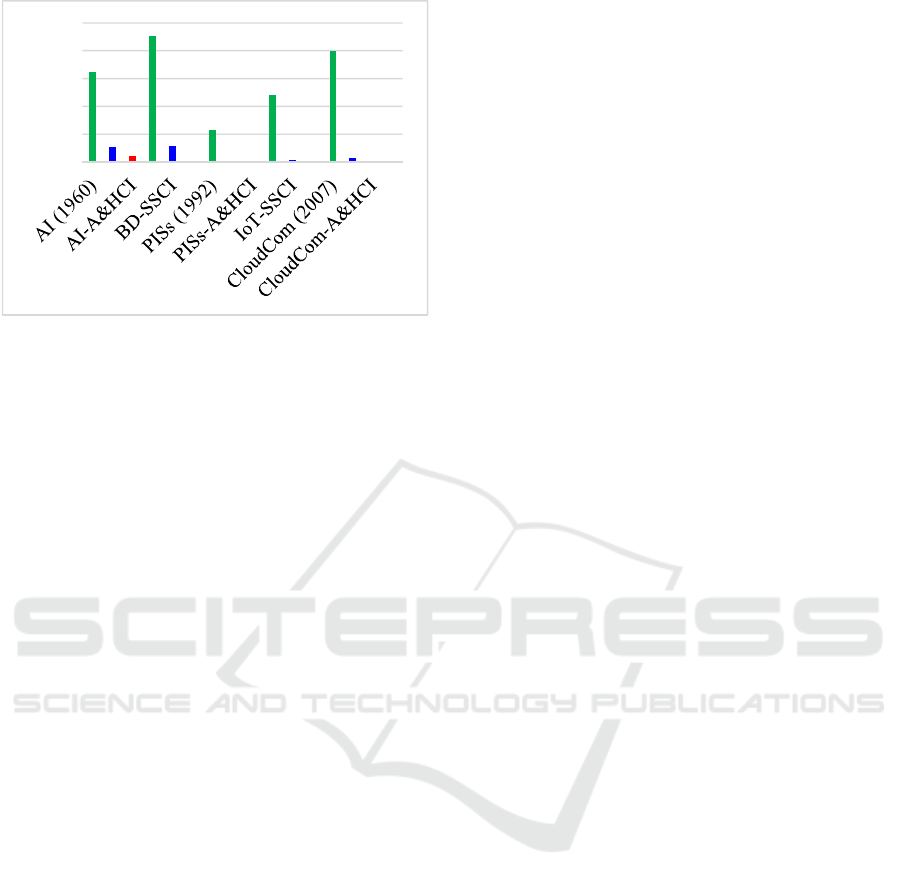
Figure 10: Current Situation of PISs Applications to fields
of Social Science and Humanities.
The proposal to timely investigate PISs
accountability takes into also the consideration that
many governments are investing massively in PISs
technologies. It is an international consensus that
these technologies are critical to the enhancement of
all-around national competitiveness; consequently,
the past couple of years see increasingly the
establishment of notional policies that strongly
encourage the racing for advancements of PISs
technologies. Enthusiasm, however, cannot be the
only condition for success. Comprehensive planning
including careful examination of side affects (or
trade-offs) must be part of this technology
development movement.
Accountability is a societal necessity because it
represents the force that aims to counter the
controlling power of decision-making authorities. As
such, it is widely acknowledged in both the
organizational types of government institutions and
business corporations. For government institutions,
accountability requires the provision of information
regarding the policies they make (Peters, 2014) and
for business corporations, the promotion of self-
discipline and code of conduct (Pava, 2008; Thorne,
2008). These accountabilities, however, do not
represent sufficiently digital decision accountability,
or in general, technology accountability. In a PISs
environment, digital decisions are being made
constantly and they are made by technologies that are
ubiquitous and invisible. These features and their
combined effects make it extremely difficult for
accountability information to be available and/or with
answerability. As a consequence, human decision
recipients, also the typical accountability force, will
find it extremely difficult to make inquiries about the
decision-making processes, let alone to understand
them. For example, in-memory processing offers
instant analytical results, however, re-examination of
the results in a later time will have to take much more
time because the participating data threads are moved
to permanent storage media after the in-time
processing and delivery. Re-examination may not
even be at all possible if the participating data threads
are not considered worthy being retained in permeant
storage media. The promise of context-aware
computing is to tailor information products and
services to user needs as much as possible, and with
the help of IoT and BD analytic thinking, such
promise is speedily becoming a reality. To
reconstruct the tailoring process, however, can be
time consuming or entirely impossible, depending on
the degree of customization, i.e., the combination of
the number of data threads used as input, the formats
in which these data threads existed, and the
complexity of the analytical tools utilized. It must be
pointed out that these examples describe only
challenges caused by individual use of technologies,
not the pervasiveness of computing as framed in PISs.
As stated above, in true PISs, all decisions, big or
small, are made based on ubiquitous technologies that
are invisible to the consumers of information,
meaning that even the decision makers do not know
where the information prompted in front of them
come from and how it is produced, let alone the
recipient of the decisions. These difficulties
accumulate with the increased number of digital
decisions and the level of integration between PISs H-
Agent and PISs D-Agent and are compounded with
the fact that accountability inquires typically take
place at times (much) later than that of decision
making.
If decision-making processes cannot be
sufficiently understood by decision recipients,
decisions will be impossible to be challenged, and
with the current situation where decision-making
powers are increasingly concentrated in the hands of
PISs technology companies, the needed balance
between decision makers and decision recipients will
be in peril and may eventually be lost. Decision-
making powers must be justly countered as a healthy,
harmonized society is one that is properly balanced.
With such balance comes along stability, yet, without
such balance, common interests can never be
identified, prosperity can hardly be sustained and the
danger of digital technology dictatorship looms. If we
are not ready to trust blindly digital decisions, if we
indeed fear to have to live in a “black box”
empowered society (Pasquale, 2015), and if we do
believe there are “weapons of math destruction”
(O'Neil, 2016), the interplays between PISs and
accountability must be investigated. Among the many
6451
1098
405
9054
1126
97
2294
89
17
4832
143
17
7957
259
3
0
2000
4000
6000
8000
10000
FR-HT 2018 - Special Session on Managing Digital Data, Information and Records: Firm Responses to Hard Technologies
414

examples, the Facebook scandal is telling us live:
digital decisions and the person(s) behind these
decisions can be invisible even to a PISs organization
itself and manipulations of user-generated data can be
unlimited. It is time for us ordinary people, the data
supplier, to be united, to take actions, and to make the
invisible visible. To that end, we need collaborations
from all fellow enthusiasts.
ACKNOWLEDGEMENTS
This study is supported by the Fundamental Research
Funds for Central Universities and the Research
Funds of Renmin University of China (15XNL032).
REFERENCES
Arnaboldi, M., Busco, C., and Cuganesan, S. (2017).
Accounting, accountability, social media and big data:
revolution or hype?. Accounting, Auditing and
Accountability Journal, 30 (4), 762-776.
Boos, D., Guenter, H., Grote, G., and Kinder, K. (2013).
Controllable accountabilities: the Internet of things and
its challenges for organisations. Behaviour and
Information Technology, 32 (5), 449-467.
Bovens, M. (2007). Public accountability. In E. Ferlie, L.
E. Lynn Jr., and C. Pollitt (eds.), The Oxford handbook
of public management (pp. 1-28). Oxford: Oxford
University Press.
Bovens, M. (2010) .Two concepts of accountability:
accountability as a virtue and as a mechanism. West
European Politics, 33(5), 946-967. DOI: 10.1080/
01402382.2010.486119.
Castiglione, D. (2018). Accountability. Retrieved 21
February 2018, from, https://www.britannica.com/
topic/accountability.
Davis, G. B. (1974). Management information systems:
conceptual foundations, structure, and development.
New York: McGraw-Hill.
Duranti, L. (2002). The Concept of electronic records. In L.
Duranti, T. Eastwood and H. MacNeil (eds.),
Preservation of the integrity of electronic records (pp.9-
20). Dordrecht; Boston: Kluwer Academic Publishers.
EBSCO (2018). Academic search complete. Retrieved 17
January 2018, from, http://resources.library.ubc.ca/?
searchtype=keywordsandsearch=academic+search+co
mplete.
Fox, J. (2007). The Uncertain relationship between
transparency and accountability. Development in
Practice, 17 (4-5), 663-671.
Gailmard, S. (2007). Accountability and principal–agent
theory. In E. Ferlie, L.E. Lynn Jr., and C. Pollitt (eds.),
The Oxford handbook of public management (pp. 1-
19). Oxford: Oxford University Press.
Gao, C., and Iwane, I. (2015). A Social network model for
big data privacy preserving and accountability
assurance. 2015 12th annual IEEE consumer
communications and networking conference (CCNC),
9-12 January 2015, Las Vegas.
Government of Canada (2018). Policy on information
management. Retrieved 16 January 2018, from
https://www.tbs-sct.gc.ca/pol/doc-eng.aspx?id=12742.
Gregor, S. and Hevner, A. R. (2013). Positioning and
presenting design science research for maximum
impact. MIS Quarterly, 37 (2), 337-355.
Hood, C. (2010) Accountability and transparency: Siamese
twins, matching parts, awkward couple?, West
European Politics, 33 (5), 989-1009. DOI: 10.1080/
01402382.2010.486122.
Grunwell, D., and Sahama, T. (2015). Information
accountability and health big data analytics: a consent-
based model. 17th International conference on e-health
networking, application and services (HealthCom),
13-17 October 2015, Boston.
InterPARES Project. (2007). Diplomatic analysis.
Retrieved 20 January 2018, from http://www.inter
pares.org/display_file.cfm?doc=ip3_template_for_dipl
omatic_analysis.pdf.
Jabbra, J. G. and Dwivedi, 0. P. (1989). Public service
accountability: a comparative perspective. Hartford,
CT: Kumarian.
Jiang, X. L., and Yang, S. (2016). Ethic accountability of
media technologies in the era of big data. Journal of
Southwest University for Nationalities (Humanities and
Social Science Edition), 7, 145-149.
Khan, M. H., Chan, G.Y., and Chua, F. F. (2016). An
Adaptive monitoring framework for ensuring
accountability and quality of services in cloud
computing. 2016 International Conference on
Information Networking (ICOIN), 13-15 January 2016,
Kota Kinabalu, Malaysia.
Ko, R. K. L., Lee, B. S., and Pearson, S. (2011). Towards
achieving accountability, auditability and trust in cloud
omputing. In A. Abraham, J. L. Mauri, J. F. Buford,
J. Suzuki, and S. M. Thampi (eds), Advances in
Computing and Communications. ACC 2011.
Communications in Computer and Information
Science, vol 193. Berlin, Heidelberg: Springer.
https://doi.org/10.1007/978-3-642-22726-4_45
Kourouthanassis, P. E., Giaglis, G. M., and Karaiskos, D.
C. (2010). Delineating ‘pervasiveness’ in pervasive
information systems: a taxonomical framework and
design implications. Journal of Information
Technology 25, 273–287.
Library of Congress (2018). Library of Congress Subject
Headings. Retrieved 23 January 2018, from
http://id.loc.gov/authorities/subjects.html.
Lindberg, S. (2009). Accountability: the core concept and
its subtypes. Retrieved 20 February 2018, from,
http://www.gsdrc.org/document-library/accountability-
the-core-concept-and-its-subtypes/.
Mansbridge, J. (2007). A Contingency theory of
accountability. In E. Ferlie, L.E. Lynn Jr., and C. Pollitt
Overview of the Balancing Pervasive Information Systems Project and a Call for Research Collaborations
415

(eds.), The Oxford handbook of public management
(pp. 1-17). Oxford: Oxford University Press.
Mulgan, R. (2000). Accountability: an ever-expanding
concept?. Public Administration, 78 (3), 555–573.
National Archives of Australia (2017). Information
governance framework. Retrieved 14 January 2018,
from http://www.naa.gov.au/about-us/organisation/
accountability/information-governance-framework/in
dex.aspx.
Obama, B. (2009). Transparency and open government.
Retrieved 15 January 2018, from https://web.archive.
org/web/20160229003506/https://www.whitehouse.go
v/the_press_office/TransparencyandOpenGovernment.
O'Neil, C. (2016). Weapons of math destruction: how big
data increases inequality and threatens democracy. New
York: Crown.
Parkinson, J. Accountability in Archival Science. MAS
Thesis. University of British Columbia. https://open.
library.ubc.ca/cIRcle/collections/ubctheses/831/items/
1.0086151
Pasquale, F. (2015). The Black box society: the secret
algorithms that control money and information.
Cambridge: Harvard University Press.
Pava, M. L. (2008). Corporate accountability. In R.W. Kolb
(ed.), Encyclopedia of business ethics and society (pp.
1-7). Thousand Oaks: SAGE Publications.
Peffers, K., Tuunanen, T., Rothenberger, M. A., and
Chatterjee, S. (2008). A Design science research
methodology for information systems research. Journal
of Management Information Systems, 24 (3), 45–77.
6, Perri. (2010). Ethics, regulation and the new artificial
intelligence, part I: accountability and power.
Information, Communication and Society, 4 (2), 199-
229. http://www.tandfonline.com/doi/abs/10.1080/713
768525.
Peters, B. G. (2014). Accountability in public
administration. In M. Bovens, R. E. Goodin, and T.
Schillemans (eds.), The Oxford handbook of public
accountability, Oxford: Oxford University Press.
Stewart, J. D. (1984). The Role of information in public
accountability. In A. G Hopwood, and C. Tomkins
(eds.) Issues in public sector accounting (pp. 13-34).
Oxford: P. Allan.
Thompson, D. F. (2014). Responsibility for failures of
government: the problem of many hands. American
Review of Public Administration, 44 (3), 259–273.
Thorne, D. M. (2008). Social accountability. In R.W. Kolb
(ed.), Encyclopedia of business ethics and society (pp.
1-4). Thousand Oaks: SAGE Publications.
United Kingdom (2009). Lord Chancellor’s code of
practice on the management of records issued under
section 46 of the Freedom of Information Act 2000.
Retrieved 18 January 2018, from http://www.national
archives.gov.uk/documents/foi-section-46-code-of-
practice.pdf.
Vedder, A., and Naudts, L. (2017). Accountability for the
use of algorithms in a big data environment.
International Review of Law, Computers and
Technology, 31 (2), 206-224.
Weber, R. H. (2011). Accountability in the Internet of
Things. Computer Law and Security Review, 41, 133-
138.
Weiser, M. (1991). The Computer for the 21st Century.
Scientific American, 265 (3, Special issue), 94-105.
Wiesche, M., Jurisch, M. C., Yetton, Y. W., and Krcmar,
H. (2017). Grounded theory methodology in
information systems research. MIS Quarterly, 41 (3),
685-701.
Xhafa, F. et al. (2015). Privacy-aware attribute-based PHR
sharing with user accountability in cloud computing.
Journal of Supercomputing, 71, 1607–1619.
Xie, S. L. (2012). The Concept of record and its revolution
in digital environments: the InterPARES perspective.
The Journal of Archival Science, 3, 46-51.
InterPARES Project. (2012). Terminology database.
Retrieved 20 January 2018, from http://interpares.org/
ip2/ip2_terminology_db.cfm.
Xie, S. L. (2012). Digital records management: the lacking
foundation for continuing accessibility. Online
Information Review, 36 (2), 299-306.
Xie, S. L. (2015). Co-design of information systems with
digital records management: a proposal for research. In
A. L. N. Fred, J. L. G. Dietz, D. Aveiro, K. Liu, and J.
Filipe (eds.), Proceedings of the 7th international joint
conference on knowledge discovery, knowledge
engineering and knowledge management, volume 3:
KMIS (knowledge management and information
Sharing) (pp. 222-238).
Xie, S. L. (2016). Retention in ‘the right to be forgotten’
scenario: a records management examination. Records
Management Journal, 26 (3), 279 – 292.
Xie, S. L., and Fan, A. (2016). Organizational records
systems - an alternative view to (enterprise) information
systems. In A. Fred, J. Dietz, D. Aveiro, K. Liu, J.
Bernardino, and J. Filipe (eds.), Proceedings of the 8th
international joint conference on knowledge discovery,
knowledge engineering and knowledge management,
Volume 3: KMIS (pp. 82-91).
Xie, S. L (2017). Records and information in the
government of Canada: a Grounded Theory study.
Hangzhou, China: Zhejiang University Press.
Zhu, G., Yang, J. Y., Feng, M. N., and Chen Y. (2016).
Research on big data privacy traceability framework in
the context of accountability. Research on Library
Science, 13, 67-73.
FR-HT 2018 - Special Session on Managing Digital Data, Information and Records: Firm Responses to Hard Technologies
416
