
A Lightweight Authentication Protocol
for V2G Networks in Smart Grid
Luis Fernando Arias Roman
1
, Paulo R. L. Gondim
1
and Jaime Lloret
2
1
Departamento de Engenharia Elétrica, Universidade de Brasília (UnB), Brasília, Brazil
2
Integrated Management Coastal Research Institute, Universitat Politecnica de Valencia (UPV), Valencia, Spain
Keywords: Authentication, Security, Electric Vehicles, Aggregator, Vehicle-to-Grid, V2G, Smart Grid.
Abstract: In a Smart Grid, a Vehicle to Grid (V2G) network aims to provide mobile distributed capacity of battery
storage, helping to minimize the dependency of non-renewable energy sources. In this network, the privacy
and anonymity of users’ identity, confidentiality of the transmitted data and location of the Electric Vehicle
(EV) must be guaranteed. This article proposes a lightweight authentication protocol devoted to the
protection of EV identities, prevention against the tracking of the vehicle and confidentiality of transmitted
data. In a performance comparison with other protocols, the results from computing and communications
performance analyses are better. The lower consumption of resources allows contributing for reducing
signalling congestion and saving bandwidth. The protocol protects from various known attacks and security
analysis shows that the protocol achieves the security goals.
1 INTRODUCTION
Smart grid (SG) is based on the overlaying of
communications and control system onto the power
delivery infrastructure. The integration of electric
vehicles (EVs) into electricity load is based on a
Vehicle-to-Grid (V2G) network, able to provide
mobile distributed capacity of battery storage.
There are several security holes in V2G
communications. Among the several security needs
to be attended, it is necessary to guarantee the
privacy and confidentiality of the user's sensitive
information (user identity, loading and unloading
schedules, location, etc.) that can be acquired by an
attacker using various attack techniques such as:
spoofing / sniffing, Denial of Service (DoS) and
Man-in-the-Middle attacks.
An authentication protocol is one of the most
important parts in V2G networks to ensure the
confidentiality and privacy of data (Jie et al. 2015;
Saxena et al. 2015; Yaqoob and Shon, 2016; J.
Lloret et al, 2012), in order to efficiently protect
identities and control access to resources. These
protocols need to be resistant to attacks and efficient,
so some authors use different techniques to lower
costs; among these techniques, group authentication
has been used (Wang et al., 2015; Li, 2016; Shao et
al. 2016) in order to offer optimum performance.
Group based systems are widely used to improve the
performance of the network (Lloret, 2011).
This paper proposes a group authentication
protocol for the administration and distribution of
keys in a V2G architecture. The protocol is based on
groups to manage secret keys, Elliptic Curve - Diffie
Hellman (ECDH) to share secrets and bilinear
pairing to provide simultaneous and efficient session
key generation and authentication for EVs grouped
in aggregators. The protocol achieves very good
performance in terms of computing and
communication costs, and provides protection
against various attacks.
The remainder of the manuscript is organized as
follows: Section 2 describes some works related to
the authentication of EV in the V2G network;
Section 3 introduces the proposed protocol; Section
4 reports on a performance analysis of the protocol
and describes the characteristics of the security
properties; Section 5 provides the conclusions and
suggests some future work.
2 RELATED WORK
Several protocols have been proposed for
authenticating EVs in a V2G network (e.g., (Jie et al.
2015; Saxena et al. 2015; Braeken et al. 2017; Guo
et al, 2011; Liu et al, 2013; Liu et al. 2014; Menezes,
Arias Roman, L., Gondim, P. and Lloret Mauri, J.
A Lightweight Authentication Protocol for V2G Networks in Smart Grid.
DOI: 10.5220/0007231702050212
In Proceedings of the 8th International Joint Conference on Pervasive and Embedded Computing and Communication Systems (PECCS 2018), pages 205-212
ISBN: 978-989-758-322-3
Copyright
c
2020 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
205

2005). We selected two proposals for the sake of
comparison, as presented below.
(Jie et al. 2015) designed an authentication
protocol that preserves the privacy of users´ data in
the connection of their electric vehicles for the
charging or discharging of batteries in the V2G
network. It also optimizes communications through
aggregators and dynamically manages the system. It
uses group signatures and a partially blind signature
restrictive technique based on identity. The
architecture comprises five entities, namely Central
Aggregator (CAG), LAG, Charging/discharging
station (ST), Plug-in electric vehicle (PEV) and a
trusted authority (TA). The protocol consists three
phases: a) Initial Configuration; b) Generation of
group blind certificate for each PEV; c) Access of
PEV to the V2G network through ST.
(Saxena et al. 2015) proposed authentication
protocols for the access of EVs in the Smart Grid
and the recharge and discharge of their batteries
considering five entities: EVs, Charging Station
(CS), LAG, Certification/Registration Authority
(CA/RA) and Control Center (CC). The protocol
consists of four parts: Initial configuration, where all
entities generate a pair of public and private keys;
Registration of EVs: each EV sends information to
CA/RA and returns a temporary identity to the EV;
LAG - CA/RA communication: all LAG must have
the register of the temporary identities of all EVs
registered in CA/RA, therefore, the communication
between LAG - CA/RA occurs for updating the
register of such entities; Protocol execution: when an
EV must charge or discharge (sell) part of its energy,
it approaches a CS, establishes communication with
LAG and generates a session key that guarantees a
mutual authentication between EV and LAG. The
EV calculates an identity verification parameter and
sends an encrypted message to the LAG with the
session key. The LAG decrypts the researched
message, adds information for the verification of the
EV identity, and sends all parameters to the CA/RA
in a message encrypted with the CA / RA digital
signature generated by the LAG. Finally, CA/RA
checks the EV identity and returns a message of
commands to the EV. The remaining messages
exchanged between the EV and CA/RA are
encrypted under asymmetrical encryption based on
blind digital firms.
3 PROTOCOL PROPOSAL
For the proposal of the protocol, a V2G network
architecture is considered, involving EVs
recharging/discharging their batteries;
Charge/Discharge Stations (CDS); Aggregators
(AGs) --- Local AG’s, and a Central AG;
Authentication Servers (AS), including a Central
Authentication Server (CAS) and several Substation
Authentication Servers (SAS), used in large SG
networks; Control Center (CC).
Three phases are considered:
1
st
. phase: Initialization of the System
Two cyclic groups G and G
T
of order q and P, and a
generator element of group G are chosen. G and G
T
are supposedly related to a non-degenerative pairing
and a bilinear map that can be efficiently computed:
ê : G × G → G
T
such that ê(P, P) ≠ 1G
T
and
ê(aP
1
,bQ
1
) = ê(b P
1
,a Q
1
) = ê(P
1
, Q
1
)
ab
∈ G
T
for
every a, b ∈
∗
and every P
1
, Q
1
∈ G (Menezes,
2005). Moreover, the hash functions of the system
are defined:
:
{
0,1
∗
→,
:→ℤ
∗
and
:
{
0,1
∗
→ℤ
∗
.
Finally, the central authentication server (AS)
and all aggregators (AG) define an elliptical curve
on a finite field E (Fq) and parameters {G, G
T
, ê, P,
H
1
, H
2
, H
3
} are published. AS then chooses a private
key
,∈
∗
and calcultates its public key
=
∗ to be published.
2
nd
. phase: Registration
All EVs and must register on-site in the energy
supplier´s system. An identity (
) must be
chosen for the registration of AGs. The aggregator
then chooses a random number
∈Z
∗
to be its
private key and calculates a public key
=
∗
. sends AS a message containing the public key
and the identity of the device {
,ID
}. CAS
stores the data received
andID
, and
calculates group private key
=
|
|
∗
(1)
and temporary group identity
=
∗
(
)
(2)
where LAI (local area identifier) identifies the area
where the aggregator is located and
∗
are
random numbers.
The registration of an EV is initialized when it
chooses an
identity and an
∈
∗
private
key. It calculates
=
∗ public key. The
user sends a message containing the public key and
PEC 2018 - International Conference on Pervasive and Embedded Computing
206

the user´s identity {y
,ID
} to AS through a safe
channel. CAS saves the data received, i.e., y
andID
, associates the EV attributes, as model,
make, owner, chassis number and telephone
numbers related to the vehicle and choose random
numbers
∗
. It then calculates
group private key
=
(
||
||
||
ℎ
)
∗
(3)
a temporary identity
=
∗
(
) (4)
and temporal visitor Identity
=
(
)
∗
(
) (5)
The system creates a user account for a web
service in the cloud for the sending of data necessary
for the authentication phase. The web service will
store the hash of the user's identity ℎ
=
(
),
and require the user to change the password on the
first access.
CAS initializes the group by: defining the EVs
and AG that will be part of the group and its identity
; generating a binary tree where leaves are the
private group keys (
,
) of each entity in
the group; computes group key
.
Finally the CAS sends the group private key
(
,
) and a list of the blinded keys of its
siblings ( =
,
,…,
) to calculate the group
key
, the random numbers
and
for each
of the EVs and the random number
for the AG in
order to calculate the temporary identifications. In
the sequence, CAS sends all necessary data
(,_,
,
,
,
) for SAS for
authenticating group members.
3
rd
. phase: Authentication of EV and AG
In this phase, 4 messages are exchanged:
A) When an EV is going to charge / discharge
energy into a CDS, it generates a temporary identity
=
∗
(
) (6)
a verification message
=
||
(7)
where LAI is the location area identifier of EV, and
together with a message authentication code
(MAC), generates the message 1
({
||
||
}), and sends it to the
aggregator
.
B) After receiving message 1 the
checks the
of message. If the comparison is
satisfactory,
adds message
and
to a group message
, Otherwise, if comparison
isn’t satisfactory, the connection with EV is
terminated. The aggregator chooses value
∈
∗
,
calculates a temporary identity
=
∗
(
) (8)
a verification message
={
|
|
(9)
a temporary group identity
=
∗
(10)
and a message authentication code of the aggregate
authentication information
=ℎ
||
(11)
The
and
are added to the
, then the
message is encrypted with the group key
. last
message 3: {{
||
||
} is sent to
SAS, where the
=
⨁
⨁…⨁
(12)
C) AS decrypt the message with the group key and
calculates
and all
and the total
of the message
=
´
⨁´
⨁…⨁´
(13)
and compares with the
of the received
message, If the verification fails, sends a
failure message to the group. Otherwise, decrypts
A Lightweight Authentication Protocol for V2G Networks in Smart Grid
207

the messages with the group private keys of each of
the EVs and AG, and verifies the identities and
location. After, it chooses as random numbers
,
,∈
∗
and calculates a temporary
identity
=
∗
(14)
and a temporary key for the group
=ℎ
(
||
)
(15)
The
is sent to the cloud web service with an
account associated with the user. The user can join
the cloud service through an application on the cell
phone, computer, or with a user interface installed in
the CDS; this latter feature is important to ensure
that the EV owner could join their account to acquire
, in a situation where, for some reason, he does
not have a device with Internet access to join the
cloud service in the cloud.
Then, once the
were obtained, the AS sends a
broadcast message 3: {φ,X
,X
,t
}, where
=∗
(16)
=∗
(17)
=
(
||
)⨁(
|
|
)
;=
(ℎ+
+
) (18)
ℎ=
(
|
|
) (19)
=
∗
∗
(20)
=∗
(
)∗
(21)
=∗
∗
(22)
and t
is a timestamp. in parallel the SAS does the
calculation the session keys and the hash of each
:
´
=ê
,ê
,
∗
∗
(23)
and
:
´
=ê
,ê
,
∗
∗
(24)
D) When and
receive the message from
, they calculate: ´
=
(
)∗
; ´
=
∗
. Then the EVs and the AG perform an Xor
operation to extract the parameters:
φ⨁H
(w
|
|
w
)
=(
||) (25)
With ,
,
and F values found in the
message, EV and AG do the following actions:
• Verification of the message:
To check the message sent by SAS, the EVs and the
AG must calculate
′=
||
(26)
and
ℎ′ =
(
|
|
) (27)
where
and
are the values received in the
message and
is the group key found in the
message. EV must then verify
=
(ℎ′+
′+
). If the verification succeeds,
and
calculate the session key; otherwise, they close
communication.
• Session key
The EVs and the AG must use the following
calculations to obtain a session key: private keys;
EV:
=ê
+
, (28)
and AG:
=ê
+
, (29)
Once the session key is generated, the EVs and AG
calculate a hash of that key (
=
=
(
)
) and form a
message that contains the temporal identity (EVs or
AG) and the session key hash. This message is
encrypted by an XOR operation with the group key
(
=(
||TID
)⨁
and
=
(
||TID
)⨁
) and are sent to the SAS for
verification.
In the sequence, immediately receives the
messages from each
and
, groups them
and calculates their ´
, groups them and
calculates
of the keys and temporal
identity’s calculated by :
PEC 2018 - International Conference on Pervasive and Embedded Computing
208

=´
=
´
||´
||´
||…||´
⨁
(30)
If M´
=M
are the same, all group
members have the correct session key, therefore,
communication is established. On the other hand, if
the verification fails, checks, one by one, the
Hash of the keys sent.
4 SECURITY AND
PERFORMANCE ANALYSES
This section reports on an analysis of the security
and performance of the proposed protocol and a
comparison with the other protocols used for
authentication of a V2G system.
4.1 Security Analysis
Below is a description of the processes related to
authentication, preservation of privacy and integrity
and resistance of the proposed protocol to attacks.
Mutual Authentication: Mutual Authentication is
established among , and .
authenticates and EVs through the use in the
authentication phase of the pre-shared keys (
,
,
) in the registration phase.
authenticate and by means of token
in
the calculation phase of the group´s temporal key
through a pairing operation of the message sent by
.
Preservation of privacy: The identity of the EV is
kept confidential by the authentication servers; the
other entities of the V2G network know only the
temporary identity of EV (
). The location
privacy is also guaranteed in both residential and
guest modes. The use of encrypted messages in the
residential mode ensures only SAS can decipher the
location of the vehicle. Such a location is important
for the tracking and establishment of responsibilities
in case of security incidents.
Protection to integrity: The integrity of the
messages exchanged is maintained with the MAC
generation. An adversary cannot make changes to an
intercepted message without the MAC value
changing, so the system would identify if a message
was manipulated.
Prevention against attacks: we will describe the
different types of attacks that can affect the V2G
network and how the proposed protocol can resist
them:
- Impersonating: an attacker that aims at
impersonating a valid EV must know its the
identity and secret key. However, parameter
TID
or TID
cannot be obtained
without the secret keys of the involved
entities. A session key is generated whenever
an
is authenticated for the avoidance of
use of old parameters in other devices;
- MITM: after receiving a message from ,
sends to EVs an One Time Password
(OTP) through another channel to check the
identity of towards protecting the system
from such an attack. EV
must perform
operations with both the values contained in
the message received and the OTP (
)
sent by the server for obtaining the session
key and validating the identity of
and
;
- Replay and Injection: an attacker can
intercept a message to carry out a repetition
attack and inject data in the message.
Therefore, random numbers chosen for each
session, as TKG,,
,are implemented
and hash functions check the integrity of the
message;
- -Redirectioning: whenever a new tries to
access the system, it is associated with a
group attended by an
. If the same user
tries a second access to either the same group,
or a different one, rejects the second
connection;
- Known key: the proposed protocol generates
temporary identities and sends an OTP
(
) to the EV to calculate a key for each
session, so that an attacker cannot use old
keys or data to establish a communication.
- DoS: The Server will enable a valid EV to
access the V2G network by calculating the
TID
. If more than one session is
requested, the server checks the location of
the request and if differences between
of
the requests sent by the same user are
detected, the system rejects the
communication of this user to avoid even
DDoS attacks
A Lightweight Authentication Protocol for V2G Networks in Smart Grid
209
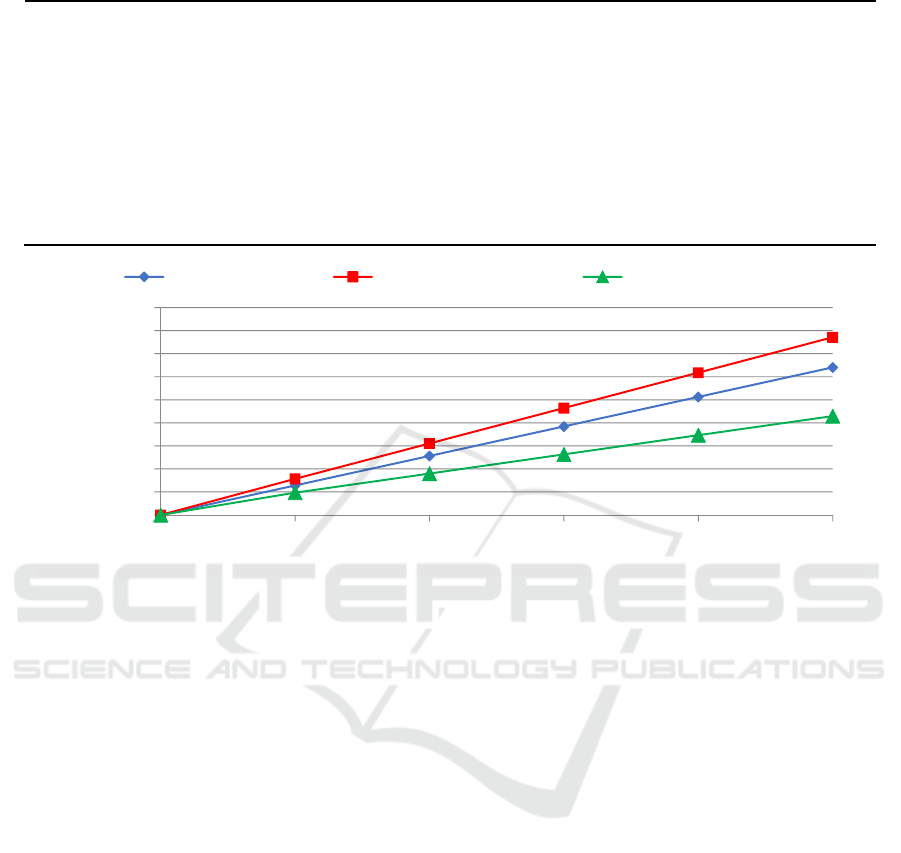
Table 1: Communication Costs in bits per message.
M1 M2 M3 M4 M5 M6 M7 M8 TOTAL
(Jie et al.,
2015)
257n 64n 128n 256n 128n 128n 128n 192n
1281n
(Saxena et
al., 2015)
384n 704n 320n 128n+320 - - - -
1536n+320
Proposed
Protocol
376n 312n+376 704 192n+192 - - - -
880n+1272
Figure 1: Communication Costs of the Protocols.
Analysis of Communication and Computational
Costs
Communication Costs
Due to severe resource limitations, especially those
related to bandwidth (spectrum scarcity), it is very
important to evaluate the communication cost
imposed by a protocol. This evaluation is commonly
based on the number of bits transmitted by a
network during the execution of the protocol, thus
allowing inferring about bandwidth consumption.
Table 1 shows a comparison of the communica-
tion costs by entities for a group of n EVs connected
to an AG.
According to Table 1, the protocol achieves
better communication performance than the protocol
designed by (Jie et al., 2015) for a number of EVs
higher than 4, and better performance than the
protocol of (Saxena et al., 2015) for a number of
EVs higher than or equal to 1.45.
Figure 1 shows graphs of the communication
costs of the proposed protocol and the protocols
proposed by (Jie et al. 2015; Saxena et al. 2015).
The communication costs of all protocols increase
linearly according to the number of EVs. The
superior performance of our protocol in aggregators
with medium or high number of EVs is clearly
demonstrated.
Computing Costs
In terms of computational costs, the run-time values
of the Multiplication (
), Exponentiation (
)
and Bilinear Pairing (
) functions are based on
(Tao et al., 2017). Other operations, as XOR and
hashing, have negligible computational cost
(Roman, 2018).
Figure 2 shows a comparison of the total
computational cost of the authentication phase of the
proposed protocol and the protocols of (Jie et al.
2015; Saxena et al. 2015). Our protocol also provides
better computational performance than the protocols
designed by (Jie et al. 2015; Saxena et al. 2015).
It is possible to verify (as in (Roman, 2018)) that
the largest number of operations of the proposed
protocol is concentrated on the entity of best
computational properties, i.e., AS. Such a
characteristic offers better performance and
flexibility to the V2G network and avoids the
overload of operations in elements of limited
resources.
0
10000
20000
30000
40000
50000
60000
70000
80000
90000
0 1020304050
Communication Coste (bits)
Number for EV per AG
Jie et al. [12] Saxena et al. [13] Proposed Protocol
[1]
[2]
PEC 2018 - International Conference on Pervasive and Embedded Computing
210
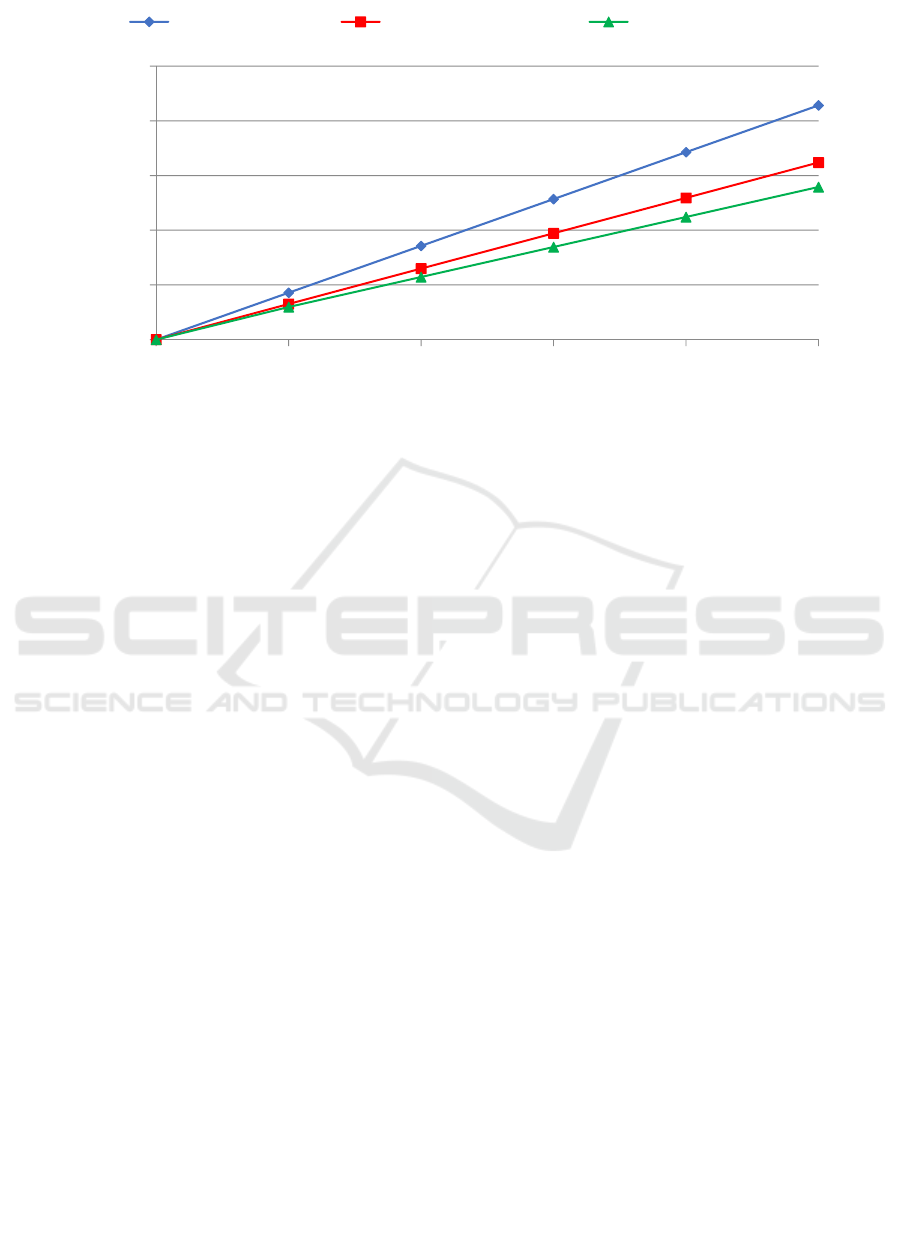
Figure 2: Comparison of Computational Costs among Protocols.
5 CONCLUSIONS
Due to the worldwide interest in reducing air
pollution, research in the field of green technologies
is very necessary to create alternatives that help
reduce air contamination. Part of the research has
been related to the integration of EVs into V2G
networks, and the different functions that can be
developed by EVs to assist the power plants in the
demand / supply of energy.
Among the several security challenges, it has
been treated the need for secure and efficient
authentication of the EVs to enter and use the V2G
network.
In the literature, several authentication protocols
have been proposed, but their performance and
security analyzes should be improved.
In this paper, we proposed a group-based
protocol that considers a distributed architecture for
authentication services, thus avoiding problems
related to centralization; it allows a better
distribution of the computational processing of the
operations in the devices.
The protocol is based on techniques which
include ECDH and bilinear pairing, which shows
better computational and communication costs than
the proposals of (Jie et al. 2015; Saxena et al. 2015),
and provides better results in relation to security
analysis.
Future work has considered the simulation of the
protocol and its adaptation for the integration in a
V2G network based on cloud. The inclusion of
access control functions based on RBAC / ABAC /
RABAC models has also been scheduled for future
work.
REFERENCES
Braeken, A.; Touhafi, A., “AAA autonomous
anonymous user authentication and its application in
V2G” Special Issue Paper Wiley, 2017.
Guo, H., Wu, Y., H. Chen, Ma, M., “A batch
authentication protocol for V2G communications”,
2011 4th IFIP International Conference on New
Technologies, Mobility and Security, Paris, France,
February 2011.
Jie, C.; Yueyu1, Z.; Wencong, S., “An anonymous
authentication scheme for plug-in electric vehicles
joining to charging-discharging station in V2G
networks” China Communication, v.12, pp. 9-19,
2015.
Li, H., “privacy-preserving authentication and billing for
dynamic charging of electric vehicles”, Doctor
Dissertation, University of Illinois at Urbana-
Champaign, 2016.
Liu, H.; Ning, H.; Zhang, Y.; Guizani, M.; “Battery
Status-aware Authentication Scheme for V2G
Networks in Smart Grid”, IEEE Transactions on
Smart Grid, v.4, p.p 99-110, 2013.
Liu H., et al., "Role-Dependent Privacy Preservation for
Secure V2G Networks in the Smart Grid", IEEE
Trans. Inf. Forensics Security, vol. 9, no. 2, pp. 208-
20, Feb. 2014.
Lloret, J.; Gilg, M.; Garcia, M.; Lorenz, P., “A group-
based protocol for improving energy distribution in
smart grids”, Communications (ICC), 2011 IEEE
0
500
1000
1500
2000
2500
0 1020304050
Computational Cost (ms)
Number of EV per AG
Jie et al. [12] Saxena et al. [13] Proposed Protocol
[1]
[2]
A Lightweight Authentication Protocol for V2G Networks in Smart Grid
211

International Conference on, pp. 1-6, Paris, France,
May 2011.
Lloret, J.; Lorenz, P.; Jamalipour, A.; “Communication
protocols and algorithms for the smart grid”, IEEE
Communications Magazine 50 (5). 2012.
Menezes, A. (2005) “An Introduction to Pairing-Based
Cryptography”, Recent Trends in Cryptography, v.
477, p. 47-65.
Roman, L.F.A., “Proposal and Evaluation of
Authentication Protocols for Smart Grid Networks”,
Master’s Degree Dissertation, Universidade de
Brasilia, UnB, 2018.
Saxena, N.; Choi, B. J.; Cho, S., “Lightweight Privacy-
Preserving Authentication Scheme for V2G Networks
in the Smart Grid” IEEE Trustcom/BigDataSE/ISPA,
v.1, pp. 604-611, 2015.
Shao, J.; Lin, X.; Lu, R.; Zuo, C.; “A Threshold
Anonymous Authentication Protocol for VANETs”,
IEEE Transactions on Vehicular Technology, v.65, pp.
1711-1721, 2016.
Tao, M.; Ota, K.; Dong, M.; Qian, Z., “AccessAuth:
Capacity-aware security access authentication in
federated-IoT-enabled V2G networks”, Journal of
Parallel and Distributed Computing, Vol. 118, Part 1,
August 2018, Pages 107-117.
Wang, F.; Chang, C.; Chou, Y. “Group Authentication and
Group Key Distribution for Ad Hoc Networks”,
International Journal of Network Security, v.17, pp.
199-207, 2015.
Yaqoob S., and Shon, T., “A Hybrid EV Authentication
Approach in Smart Grid Based Distributed Network”,
Ad Hoc and Sensor Wireless Networks, Vol. 31,
Number 1-4, pp. 89-99, 2016.
PEC 2018 - International Conference on Pervasive and Embedded Computing
212
