
Operator-dependent Modifiers in Nilpotent Logical Systems
J. Dombi
1
and O. Csisz
´
ar
2,3
1
University of Szeged, Institute of Informatics, Szeged, Hungary
2
Hochschule Esslingen, University of Applied Sciences, Faculty of Basic Sciences, Esslingen, Germany
3
´
Obuda University, Institute of Applied Mathematics, Budapest, Hungary
Keywords:
Linguistic Modifier, Modality, Hedge, Unary Operator, Nilpotent Logic, Bounded System, Possibility,
Necessity, Sharpness.
Abstract:
The purpose of the current study is to consider the main unary operators of a nilpotent logical system in an
integral framework and to reveal the underlying general structure of all the previously examined operators
in nilpotent logical systems. The unary operators are obtained by repeating the argument in multivariable
operators. This enables us to provide a widely applicable system, where all the operators are connected to
each other, and where the modalities and hedges are operator-dependent. It becomes possible to describe all
the operators by using a generator function and a few parameters. The possibility, necessity and sharpness
operators are thoroughly examined and it is also shown how the multivariable operators can be derived from
the unary ones.
1 INTRODUCTION
Among other preferable properties, the fulfillment of
the law of contradiction and the excluded middle, and
the coincidence of the residual and the S-implication
(Trillas and L. Valverde, 1981) make the application
of nilpotent operators in logical systems feasible. In
their pioneer work (Dombi and Csisz
´
ar, 2015), Dombi
and Csisz
´
ar examined connective systems instead of
operators themselves. It was shown that a consis-
tent connective system generated by nilpotent opera-
tors is not necessarily isomorphic to the Łukasiewicz-
system. Using more than one generator function, con-
sistent nilpotent connective systems (so-called boun-
ded systems) can be obtained in a significantly dif-
ferent way with three naturally derived negation ope-
rators. Due to the fact that all continuous Archime-
dean (i.e. representable) nilpotent t-norms are isomor-
phic to the Łukasiewicz t-norm (Grabisch et al., 2009;
Klement et al., 2000), the previously studied nilpo-
tent systems were all isomorphic to the well-known
Łukasiewicz-logic.
In the last few years, the most important multivari-
able operators of general nilpotent systems have been
thoroughly examined. In (Dombi and Csisz
´
ar, 2014)
and in (Dombi and Csisz
´
ar, 2016), Dombi and Csisz
´
ar
examined the implications and equivalence operators
in bounded systems. In (Dombi and Csisz
´
ar, 2017),
a parametric form of the generated operator o
ν
was
given by using a shifting transformation of the ge-
nerator function. Here, the parameter can be inter-
preted semantically as a threshold of expectancy (de-
cision level). This means that nilpotent conjunctive,
disjunctive, aggregative (where a high input can com-
pensate for a lower one) and negation operators can
be obtained by changing this parameter.
Negation operators were also studied thoroughly
in (Dombi and Csisz
´
ar, 2015), as they play a signi-
ficant role in logical systems by building connecti-
ons between the main operators (De Morgan law) and
characterising their basic properties. Despite their
significance, about other unary operators (compared
to the multivariable ones) there are only limited litera-
ture available. In fuzzy theory, modalities (like possi-
bly, necessarily, ...) and hedges (like very, quite, extre-
mely, ...) are the most studied unary operators, which
modify the linguistic variables (Zadeh, 1975c; Zadeh,
1975a; Zadeh, 1975b; Huynh et al., 2002; T
¨
urken,
2004; Banks, 1994; Jang et al., 1997; De Cock et al.,
2000). In this study, the focus is on the unary opera-
tors of a nilpotent logical system. They perform vari-
ous operations such as incrementing or decrementing
a value and they can be widely used for expressing
modalities and hedges in human thinking (Liu et al.,
2001).
In this paper, our main purpose is to consider the
main unary operators of a nilpotent logical system in
an integral framework and to reveal the underlying ge-
126
Dombi, J. and Csiszár, O.
Operator-dependent Modifiers in Nilpotent Logical Systems.
DOI: 10.5220/0006894701260134
In Proceedings of the 10th International Joint Conference on Computational Intelligence (IJCCI 2018), pages 126-134
ISBN: 978-989-758-327-8
Copyright © 2018 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved

neral structure of all the operators considered so far.
This enables to provide a widely applicable system,
where all operators are connected to each other, and
the modalities and hedges are operator-dependent. In
such a system, only a few parameters are to be gi-
ven. By fitting the parameter values, the system can
be used to model real life problems.
The article is organized as follows. After recalling
some basic preliminaries in Section 2, unary operators
in nilpotent logical systems are examined in Section
3. First, in Section 3.1, a possible way of constructing
unary operators is considered: repeating the argument
in multivariable operators; i.e. by choosing x
i
= x
j
(∀i, j) for the arguments of the many-variable opera-
tors. This is how it can be ensured that the opera-
tors are connected. In Section 3.2, our focus is on the
drastic unary operators, in Section 3.3 on the compo-
sition rules and then in Section 3.4, it is shown how
the multivariable operators can be derived from unary
ones. This result underlines the importance of the
unary operators in a logical system. In Section 3.5,
a general framework is given for all the operators dis-
cussed so far.
In Section 4, a future research direction is sugge-
sted that could provide the next steps along the path to
a practical and widely applicable system (e.g. in neu-
ral networks). The main disadvantage of the nilpotent
operator family, namely the lack of differentiability
can be eliminated by using a continuously differenti-
able approximation of the cutting function.
Finally, in Section 5, the main results are summa-
rized.
2 PRELIMINARIES
To construct a logical system, we need to define
the appropriate logical operators. As in (Dombi
and Csisz
´
ar, 2015), we consider connective systems
where the conjunction and disjunction operators are
special types of t-norms and t-conorms, respectively.
A triangular norm (t-norm for short) T is a bi-
nary operation on the closed unit interval [0, 1] such
that ([0, 1], T ) is an abelian semigroup with neutral
element 1 which is totally ordered, i.e., for all x
1
,
x
2
, y
1
, y
2
∈ [0, 1] with x
1
≤ x
2
and y
1
≤ y
2
we have
T (x
1
, y
1
) ≤ T (x
2
, y
2
), where ≤ is the natural order on
[0, 1].
Standard examples of t-norms are the minimum
T
M
, the product T
P
, the Łukasiewicz t-norm T
L
given
by T
L
(x, y) = max(x + y − 1, 0), and the drastic pro-
duct T
D
with T
D
(1, x) = T
D
(x, 1) = x, and T
D
(x, y) = 0
otherwise.
A triangular conorm (t-conorm for short) S is a bi-
nary operation on the closed unit interval [0, 1] such
that ([0, 1], S) is an abelian semigroup with neutral
element 0 which is totally ordered. Standard exam-
ples of t-conorms are the maximum S
M
, the probabi-
listic sum S
P
, the Łukasiewicz t-conorm S
L
given by
S
L
(x, y) = min(x + y, 1), and the drastic sum S
D
with
S
D
(0, x) = S
D
(x, 0) = x, and S
D
(x, y) = 1 otherwise.
A continuous t-norm T is said to be Archimedean
if T (x, x) < x holds for all x ∈ (0, 1). A continuous
Archimedean T is called strict if T is strictly mono-
tone; i.e. T (x, y) < T (x, z) whenever x ∈ (0, 1] and
y < z , and nilpotent if there exist x, y ∈ (0, 1) such
that T (x, y) = 0.
From the duality between t-norms and t-conorms,
we can easily derive the similar properties for t-
conorms as well.
As it is well-known, t-norms and t-conorms can be
expressed by means of a single real generator function
with the following specific properties.
Proposition 1. (Baczy
´
nski, (Baczy
´
nski and Jayaram,
2009), Ling, (C. Ling, 1965)) A function T : [0, 1]
2
→
[0, 1] is a continuous Archimedean t-norm if and only
if it has a continuous additive generator, i.e. there
exists a continuous strictly decreasing function t :
[0, 1] → [0, ∞) with t(1) = 0, which is uniquely deter-
mined up to a positive multiplicative constant, such
that
T (x, y) = t
−1
(min(t(x) + t(y), t(0)), x, y ∈ [0, 1].
(1)
Proposition 2. (Grabisch et al., 2009)
A t-norm T is strict if and only if t(0) = ∞ holds for
each continuous additive generator t of T.
A t-norm T is nilpotent if and only if t(0) < ∞ holds
for each continuous additive generator t of T.
Due to the duality, additive generators of t-
conorms (s(x)) can be obtained from the additive ge-
nerators of their dual t-norms.
Since the generator functions of nilpotent t-norms
and t-conorms are bounded and determined up to
a multiplicative constant, they can be normalized
(Dombi and Csisz
´
ar, 2015). Let us use the following
notations for the uniquely defined normalized genera-
tor functions:
f
c
(x) :=
t(x)
t(0)
, f
d
(x) :=
s(x)
s(1)
. (2)
In order to simplify the notations, we recall the
definition of the so-called cutting function.
Definition 1. (Dombi and Csisz
´
ar, 2015; Sabo and
Strezo, 2005) Let us define the cutting operation [ ]
by
[x] =
0 i f x < 0
x i f 0 ≤ x ≤ 1
1 i f 1 < x
(3)
Operator-dependent Modifiers in Nilpotent Logical Systems
127

and let the notation [ ] also act as brackets when wri-
ting the argument of an operator. Then we can write
f [x] instead of f ([x]).
Definition 2. (Dombi and Gera, 2005) Let a, b ∈
[0, 1], a < b and let us define the generalized cutting
operation [ ]
b
a
by
[x]
b
a
=
0 i f x < a
x−a
b−a
i f a ≤ x ≤ b
1 i f b < x
(4)
and let the notation [ ] also act as brackets when wri-
ting the argument of an operator. Then we can write
f [x] instead of f ([x]).
Proposition 3. (Dombi and Csisz
´
ar, 2015) With the
help of the cutting operator, we can write the con-
junction and disjunction operators in the following
form, where f
c
(x) and f
d
(x) are decreasing and incre-
asing normalized generator functions, respectively.
c(x, y) = f
−1
c
[ f
c
(x) + f
c
(y)], (5)
d(x, y) = f
−1
d
[ f
d
(x) + f
d
(y)]. (6)
From now on, the notations c(x, y) and d(x, y)
above will be used for the conjunction and disjunction
to emphasize the use of the normalized generator
functions.
Next, we recall the definition of a nilpotent logical
system.
Definition 3. (Dombi and Csisz
´
ar, 2015) The triple
(c, d, n), where c is a continuous Archimedean t-norm,
d is a continuous Archimedean t-conorm and n is a
strong negation, is called a connective system.
Definition 4. (Dombi and Csisz
´
ar, 2015) A con-
nective system is nilpotent if the conjunction c is a
nilpotent t-norm, and the disjunction d is a nilpotent
t-conorm.
It was shown in (Dombi and Csisz
´
ar, 2015) that
to construct a logical system, more than one genera-
tor functions can be used without losing consistency.
In these systems, n
c
(x) and n
d
(x), the negations ge-
nerated by f
c
and f
d
respectively (also called as the
natural negations) do not coincide with the negation
operator; i.e. n
c
(x) 6= n
d
(x) 6= n(x).
Definition 5. A nilpotent connective system is called
a bounded system if f
c
(x)+ f
d
(x) > 1, or equivalently
n
d
(x) < n(x) < n
c
(x) holds for all x ∈ (0, 1), where f
c
and f
d
are the normalized generator functions of the
conjunction and disjunction, and n
c
, n
d
are the natu-
ral negations.
The associativity of t-norms and t-conorms per-
mits us to consider their extensions to the multivari-
able case. Dombi and Csisz
´
ar (Dombi and Csisz
´
ar,
2017) examined a general parametric operator o
ν
(x)
of nilpotent systems, where the parameter has an im-
portant semantic meaning as the threshold of expec-
tation. Nilpotent conjunctive, disjunctive, aggregative
and negation operators can be obtained by changing
the parameter value.
Definition 6. Let f : [0, 1] → [0, 1] be an increasing
bijection, ν ∈ [0, 1], and x = (x
1
, . . ., x
n
), where x
i
∈
[0, 1] and let us define the general operator by
o
ν
(x) = f
−1
"
n
∑
i=1
( f (x
i
) − f (ν)) + f (ν)
#
=
= f
−1
"
n
∑
i=1
f (x
i
) − (n − 1) f (ν)
#
.
(7)
Remark 1. Note that the general operator for ν = 1
is conjunctive, for ν = 0 it is disjunctive and for ν =
ν
∗
= f
−1
1
2
it is self-dual.
On the basis of Remark 1, the conjunction, the dis-
junction and the aggregative operator can be defined
in the following way.
Definition 7. Let f : [0, 1] → [0, 1] be an increa-
sing bijection. Let us define the conjunction, the dis-
junction and the aggregative operator by
c(x) := o
1
(x) = f
−1
"
n
∑
i=1
f (x
i
) − (n − 1)
#
, (8)
d(x) := o
0
(x) = f
−1
"
n
∑
i=1
f (x
i
)
#
, (9)
a(x) := o
ν
∗
(x) = f
−1
"
n
∑
i=1
f (x
i
) −
(n − 1)
2
#
, (10)
respectively, where ν
∗
= f
−1
1
2
.
Remark 2. A conjunction, a disjunction and an ag-
gregative operator differ only in one parameter of the
general operator in (7). The parameter ν has the se-
mantic meaning of the level of expectation: maximal
for the conjunction, neutral for the aggregation and
minimal for the disjunction.
Definition 8. Let w = (w
1
, . . ., w
n
) and w
i
> 0 be real
parameters, f : [0, 1] → [0, 1] an increasing bijection
with ν ∈ [0, 1]. The weighted general operator is defi-
ned by
a
ν,w
(x) := f
−1
"
n
∑
i=1
w
i
( f (x
i
) − f (ν)) + f (ν)
#
. (11)
Definition 9. The operator
a
w
(x) = f
−1
"
w
n
∑
i=1
f (x
i
) −
n
2
!
+
1
2
#
, (12)
where w > 0, is called the weighted aggregative ope-
rator.
IJCCI 2018 - 10th International Joint Conference on Computational Intelligence
128

Proposition 4. The weighted general operator
a
ν,w
(x) satisfies
1. The boundary condition a
ν,w
(0) = 0, if and only if
ν = 0 or
n
∑
i=1
w
i
≥ 1 (for a commutative operator:
w ≥
1
n
);
2. The boundary condition a
ν,w
(1, . . ., 1) = 1, if and
only if ν = 1 or
n
∑
i=1
w
i
≥ 1 (for a commutative ope-
rator: w ≥
1
n
);
3. Both of the above-mentioned boundary conditi-
ons, if and only if
n
∑
i=1
w
i
≥ 1 (for a commutative
operator: w ≥
1
n
);
4. a
ν,w
(ν, . . ., ν) = ν.
3 UNARY OPERATORS IN
NILPOTENT LOGICAL
SYSTEMS
In the early 1970’s, Zadeh (L. A. Zadeh, 1972) intro-
duced a class of powering modifiers, which defined
the concept of linguistic variables and hedges (like
very, quite, extremely, ...). He proposed computing
with words as an extension of fuzzy sets and logic the-
ory and introduced modifier functions of fuzzy sets
called linguistic hedges, which change the meaning
of the primary terms. As pointed out by Zadeh, lin-
guistic variables and terms are closer to human thin-
king and therefore, words and linguistic terms can be
used to model human thinking systems (L. A. Zadeh,
1971). Hedges and also modalities (like possibly, ne-
cessarily, ...) are the most examined unary operators.
From a semantic viewpoint, these unary operators can
also be viewed as a part of a logical system. In this
section, two possible ways of extending a nilpotent
logical system by defining the necessity and possibi-
lity operators are examined. The novelty of these two
methods lies in the fact that they provide a logical sy-
stem, where all the operators are connected to each
other.
The possibility and neccessity operators have to
satisfy the following equations.
impossible(x) = necessity(not(x)) (13)
and
possible(x) = not(impossible(x)). (14)
3.1 Possibility and Necessity as Unary
Operators Derived from
Multivariable Operators
A possible way of obtaining unary operators is by
choosing x
i
= x
j
(∀i, j) for the arguments of the many-
variable operators. Based on the De Morgan property
of the conjunction and the disjunction, the unary ope-
rators derived from them satisfy the equations above.
Definition 10. Let k ∈ N, λ ∈ R
+
, λ > 1, f : [0, 1] →
[0, 1] be an increasing bijection and let us define the
so-called necessity operator, τ
(k)
N
(x) : [0,1] → [0, 1] in
the following way:
τ
(k)
N
(x) := c[x, x, ...x
| {z }
k−times
] = f
−1
[k( f (x) − 1) + 1], (15)
and the generalized necessity operator τ
(λ)
N
(x) :
[0, 1] → [0, 1] as
τ
(λ)
N
(x) := f
−1
[λ( f (x) − 1) + 1] =
= f
−1
[λ f (x) − (λ − 1)],
(16)
where c is the conjunction generated by f
c
(x) = 1 −
f (x).
Similarly, the so-called possibility operator can
also be defined by means of the disjunction operator.
Definition 11. Let k ∈ N, λ ∈ R
+
, λ > 1, f : [0, 1] →
[0, 1] be an increasing bijection and let us define the
so-called possibility operator, τ
(k)
N
(x) : [0, 1] → [0, 1]
in the following way:
τ
(k)
P
(x) := d[x, x, ...x
| {z }
k−times
] = f
−1
[k f (x)], (17)
and the generalized possibility operator τ
(λ)
P
(x) :
[0, 1] → [0, 1] as
τ
(λ)
P
(x) := f
−1
[λ f (x)], (18)
where d is the disjunction generated by f (x).
Next, the so-called sharpness operator is defined,
based on the self-duality of the aggregative operator.
Definition 12. Let k ∈ N, λ ∈ R
+
, λ > 1, f : [0, 1] →
[0, 1] be an increasing bijection and let us define the
so-called sharpness operator, τ
(k)
S
(x) : [0, 1] → [0, 1]
in the following way:
τ
(k)
S
(x) := a[x, x, ...x
| {z }
k−times
] = f
−1
k f (x) −
k − 1
2
, (19)
and the generalized sharpness operator τ
(λ)
S
(x) :
[0, 1] → [0, 1] as
τ
(λ)
S
(x) := f
−1
λ f (x) −
λ − 1
2
, (20)
Operator-dependent Modifiers in Nilpotent Logical Systems
129

where a is the aggregative operator generated by
f (x).
The three definitions above can be summarized in
a unified formula.
Definition 13. Let λ ∈ R
+
, λ > 1, ν ∈ [0, 1], f :
[0, 1] → [0, 1] be an increasing bijection. Let us de-
fine the unary operator τ
(λ)
ν
(x) in the following way.
τ
(λ)
ν
(x) := f
−1
[λ( f (x) − f (ν)) + f (ν)]. (21)
Remark 3. For ν = 1, ν = 0 and ν = ν
∗
(i.e. f (ν) =
1
2
), we get the necessity, the possibility and the sharp-
ness operators, respectively.
The above-defined unary operators fulfill the fol-
lowing De Morgan identities (see equations 13 and
14).
Proposition 5. Let f : [0,1] → [0, 1] be an increasing
bijection and let n(x) be the negation generated by
f (x).
n
τ
(λ)
N
(x)
= τ
(λ)
P
(n(x)), (22)
n
τ
(λ)
P
(x)
= τ
(λ)
N
(n(x)), (23)
n
τ
(λ)
S
(x)
= τ
(λ)
S
(n(x)). (24)
Proof. The proof is similar in all three cases. Let us
prove the first statement.
Taking into account the fact that 1 − [x] = [1 − x],
n
τ
(λ)
N
(x)
= f
−1
[1 − [λ f (x) − (λ − 1)]] =
f
−1
[λ(1 − f (x))] = τ
(λ)
P
(n(x)).
Proposition 6. τ
(λ)
ν
(x) is for ∀ν ∈ [0, 1] increasing.
Let x = x
1
be the greatest value, for which τ
(λ)
ν
(x) = 0,
and let x = x
2
be the lowest value, for which τ
(λ)
ν
(x) =
1. In this case
x
1
= f
=1
λ − 1
λ
f (ν)
(25)
and
x
2
= f
=1
λ − 1
λ
f (ν) +
1
λ
. (26)
Proof. The monotonicity follows from the monoto-
nicity of f (x). To find x
1
and x
2
, the following two
equations need to be solved:
λ( f (x) − f (ν)) + f (ν) = 0,
and
λ( f (x) − f (ν)) + f (ν) = 1.
The solution follows from a direct calculation.
The values x
1
and x
2
in Proposition 6 for ν =
1, ν = 0 and ν = ν
∗
can be found in Table 1.
Table 1: x
1
and x
2
values for ν = 1, ν = 0 and ν = ν
∗
.
ν x
1
x
2
τ
(λ)
N
(x) 1 f
−1
1 −
1
λ
1
τ
(λ)
P
(x) 0 0 f
−1
1
λ
τ
(λ)
S
(x) ν
∗
f
−1
λ−1
2λ
f
−1
λ+1
2λ
Table 2: x
1
and x
2
values for f (x) = x.
ν x
1
x
2
τ
(λ)
N
(x) 1 1 −
1
λ
1
τ
(λ)
P
(x) 0 0
1
λ
τ
(λ)
S
(x) ν
∗
λ−1
2λ
λ+1
2λ
Proposition 7. Let ν
∗
= f
−1
1
2
.
τ
(λ)
N
(ν
∗
) = f
−1
1 −
λ
2
, (27)
τ
(λ)
P
(ν
∗
) = f
−1
λ
2
(28)
and
τ
(λ)
S
(ν
∗
) = ν
∗
. (29)
Proof. The statements follow from direct calculati-
ons.
Remark 4. Note that ν
∗
is a fixpoint of the sharpness
operator τ
(λ)
S
(x).
Next, let us consider the case f (x) = x.
Remark 5. In particular for f (x) = x,
τ
(λ)
N
(x) = min (1, max (0, λx − (λ − 1))) , (30)
τ
(λ)
P
(x) = min (1, max (0, λx)), (31)
τ
(λ)
S
(x) = min
1, max
0, λx −
λ − 1
2
. (32)
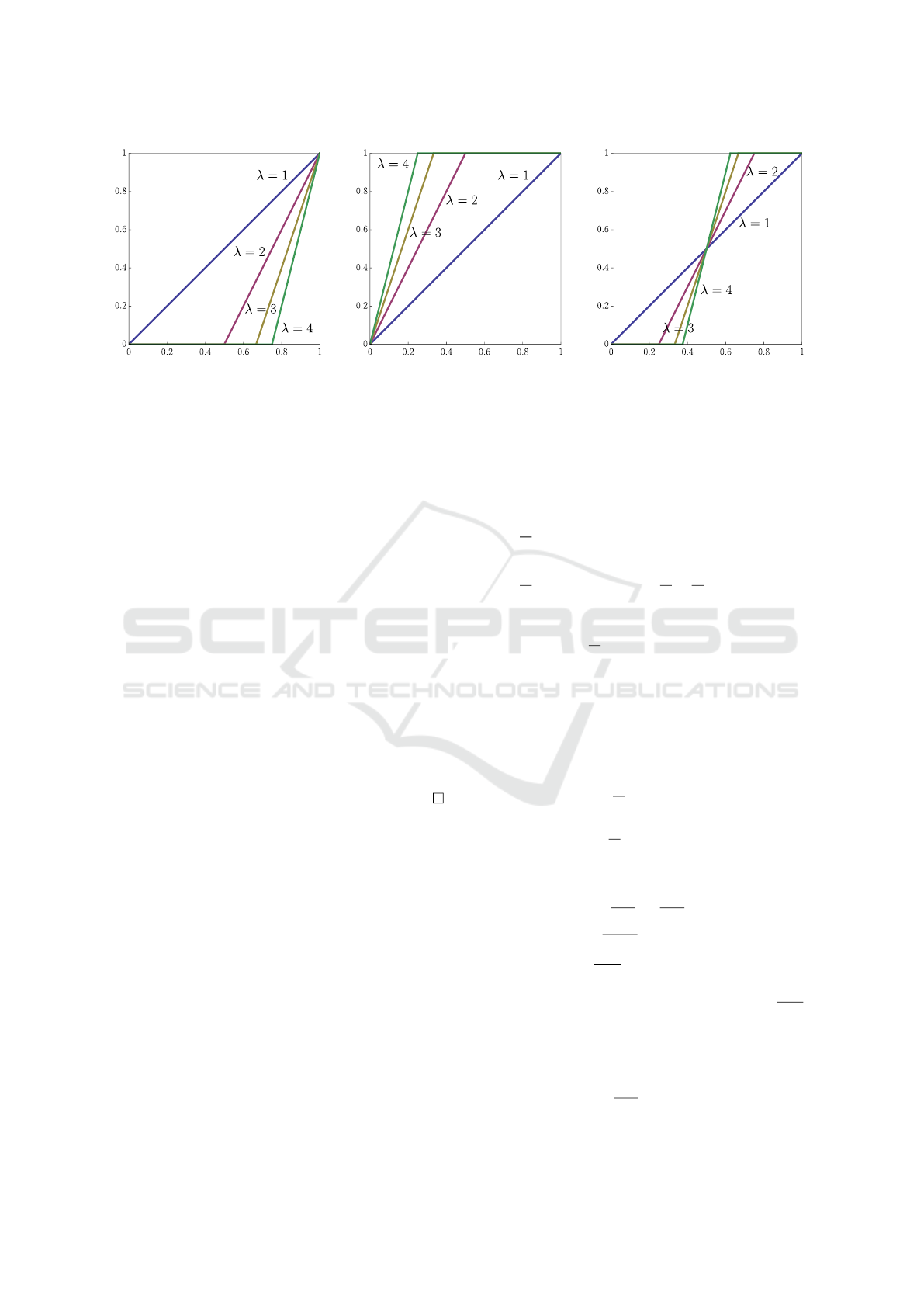
In Figure 1, unary operators generated by f (x) = x
are shown. For the values x
1
and x
2
, see Table 2.
Remark 6. As can be seen, for f (x) = x, the unary
operators τ
(λ)
I
(x) (I ∈ {N, P, S}), have a value in (0, 1)
if and only if x ∈ (x
1
, x
2
). Note that the length of this
interval, x
2
− x
1
=
1
λ
.
3.2 Drastic Unary Operators
Let us now define the so-called drastic unary opera-
tors in the following way.
Definition 14. Let f : [0, 1] → [0, 1] be an increasing
bijection. Let
τ
(∞)
N
(x) := lim
λ→∞
τ
(λ)
N
(x), (33)
IJCCI 2018 - 10th International Joint Conference on Computational Intelligence
130
(a) Necessity operators τ
(λ)
N
for λ =
1, 2,3, 4
(b) Possibility operators τ
(λ)
P
for λ =
1, 2,3, 4
(c) Sharpness operators τ
(λ)
S
for λ =
1, 2,3, 4
Figure 1: Unary operators generated by f (x) = x.
τ
(∞)
P
(x) := lim
λ→∞
τ
(λ)
P
(x), (34)
and
τ
(∞)
S
(x) := lim
λ→∞
τ
(λ)
S
(x). (35)
τ
(∞)
N
(x), τ
(∞)
P
(x) and τ
(∞)
S
(x) are called drastic unary
operators.
Proposition 8.
τ
(∞)
N
(x) =
0 i f x < 0
1 i f x = 1,
(36)
and
τ
(∞)
P
(x) =
0 i f x = 0
1 i f x > 0,
(37)
and
τ
(∞)
S
(x) =
0 i f x < ν
ν i f x = ν
1 i f x > ν.
(38)
Proof. The statement follows from a direct calcula-
tion.
3.3 Composition Rules
In human thinking and languages, emphasis is often
expressed by repeating modalities and hedges, such
as ”very-very”. The following proposition shows that
the necessity, possibility and sharpness operators are
all closed under composition. The parameter of the
compositon is the product of the input parameters.
Proposition 9. Let f : [0,1] → [0, 1] be an increasing
bijection and let n(x) be the negation generated by
f (x).
τ
(λ
1
)
N
τ
(λ
2
)
N
(x)
= τ
(λ
1
λ
2
)
N
(x), (39)
τ
(λ
1
)
P
τ
(λ
2
)
P
(x)
= τ
(λ
1
λ
2
)
P
(x), (40)
τ
(λ
1
)
S
τ
(λ
2
)
S
(x)
= τ
(λ
1
λ
2
)
S
(x). (41)
Proof. 1. It has to be shown that τ
(λ
1
)
N
τ
(λ
2
)
N
(x)
=
f
−1
λ
1
f
f
−1
[λ
2
f (x) − (λ
2
− 1)]
− (λ
2
− 1)
=
f
−1
[λ
1
[λ
2
f (x) − (λ
2
− 1)] − (λ
2
− 1)] .
(a) For λ
2
f (x) − (λ
2
− 1) ≤ 0; i.e. for f (x) ≤ 1 −
1
λ
2
, we obtain τ
(λ
1
)
N
τ
(λ
2
)
N
(x)
= 0. In this case,
τ
(λ
1
λ
2
)
N
(x) = 0 as well, since from f (x) ≤ 1 −
1
λ
2
follows f (x) ≤ 1 −
1
λ
2
−
1
λ
1
; i.e. λ
1
λ
2
f (x) −
((λ
1
− 1)(λ
2
− 1) − 1) ≤ 0.
(b) For 0 < λ
2
f (x) − (λ
2
− 1) ≤ 0 < 1; i.e. for
f (x) > 1 −
1
λ
2
, the cutting function can be omit-
ted and the statement follows from a direct cal-
culation.
(c) Taking into account the fact that λ
2
> 1 and 0 ≤
f (x) ≤ 1, λ
2
f (x) − (λ
2
− 1) > 1 is impossible.
2. It has to be shown that τ
(λ
1
)
P
τ
(λ
2
)
P
(x)
=
f
−1
[λ
1
[λ
2
f (x)]] = f
−1
[λ
1
λ
2
f (x)].
(a) If f (x) ≥
1
λ
2
, then f
−1
[λ
1
[λ
2
f (x)]] =
f
−1
[λ
1
λ
2
f (x)] = 1.
(b) If 0 < f (x) <
1
λ
2
, then the cutting function can
be omitted and the statement is trivial.
3. It has to be shown that τ
(λ
1
)
S
τ
(λ
2
)
S
(x)
=
f
−1
h
λ
1
h
λ
2
f (x) −
λ
2
−1
2
i
−
λ
1
−1
2
i
=
f
−1
h
λ
1
λ
2
f (x) −
λ
1
λ
2
−1
2
i
.
(a) If λ
2
f (x) −
λ
2
−1
2
≤ 0, then taking into account
the fact that λ
i
> 1, the left hand side of the
equation is 0. Since in this case f (x) ≤
λ
2
−1
2λ
2
,
2λ
1
λ
2
f (x) ≤ λ
1
λ
2
− 1 ≤ λ
1
λ
2
− 1. Therefore,
the value in the cutting function on the right
hand side is less than or equal to 0, which me-
ans that the equation holds.
(b) If 0 ≤ λ
2
f (x) −
λ
2
−1
2
≤ 1, then the cutting func-
tion can be omitted and the statement is trivial.
Operator-dependent Modifiers in Nilpotent Logical Systems
131

(c) If λ
2
f (x) −
λ
2
−1
2
> 1, then f (x) >
λ
2
+1
2λ
2
> 1,
which means that the left hand side of the equa-
tion is 1. Since in this case
1+λ
1
λ
2
2
<
λ
1
λ
2
+λ
1
2
<
λ
1
λ
2
f (x), the value in the cutting function on
the right hand side is greater than 1, which me-
ans that the equation is valid.
Proposition 10. 1. For the drastic operators
τ
(∞)
I
τ
(∞)
J
(x)
= τ
(∞)
J
(x), (42)
where I, J ∈ {N, P, S}.
Proof. This statement follows from a direct calcula-
tion.
3.4 Multivariable Operators Derived
from Unary Operators
Proposition 11 tells us how the conjunction and the
disjunction can be expressed in terms of the unary
operators and the arithmetic mean operator.
First, let us recall the definition of the arithmetic
mean operator.
Definition 15.
m(x) := f
−1
1
k
k
∑
i=1
( f (x
i
))
!
, (43)
where f : [0, 1] → [0, 1] is an increasing bijection.
Proposition 11. The unary operators satisfy the fol-
lowing equation:
τ
(k)
ν
(m(x)) = o
ν
(x). (44)
In particular,
1. τ
(k)
P
(m(x)) = d(x),
2. τ
(k)
N
(m(x)) = c(x),
3. τ
(k)
S
(m(x)) = a(x).
Proof. The statements follow from a direct calcula-
tion.
Proposition 12. The necessity and the possibility
operator have the following property:
1. d
τ
(k)
P
(x
1
), τ
(k)
P
(x
2
), ...τ
(k)
P
(x
k
)
= τ
(k)
P
(d(x)) .
2. c
τ
(k)
N
(x
1
), τ
(k)
N
(x
2
), ...τ
(k)
N
(x
k
)
= τ
(k)
N
(c(x)),
Proof. 1. The following statement has to be pro-
ven: f
−1
k
∑
i=1
[λ f (x
i
)]
= f
−1
λ
k
∑
i=1
[ f (x
i
)]
. If
λ f (x
i
) ≤ 1 for ∀i, then the statement is trivial. If
∃i, for which λ f (x
i
) > 1, then both sides of the
equations have the same value (i.e. a value of 1).
2. This follows from the first statement by applying
the De Morgen law.
3.5 A General Framework: The α, β, γ-
Model
All basic operators discussed so far can be handled in
a common framework, since they all can be described
by the following parametric form.
Definition 16. Let x, y ∈ [0, 1], α, β, γ ∈ R and let f :
[0, 1] → [0, 1] be a strictly increasing bijection. Let
the general parametric operator be
o
α,β,γ
(x, y) := f
−1
[α f (x) + β f (y) + γ]. (45)
The most commonly used operators for special va-
lues of α, β and γ are listed in Table 3.
Now let us focus on the unary (1-place) case.
Definition 17. Let x ∈ [0, 1], α, γ ∈ R and let f :
[0, 1] → [0, 1], a strictly increasing bijection. Then
o
α,γ
(x) := f
−1
[α f (x) + γ]. (46)
For special γ values, see Table 4.
In this framework it becomes possible to define all
the operators by a single generator function and a few
parameters.
4 FUTURE WORK AND
APPLICATION
The main disadvantage of the Łukasiewicz operator
family is the lack of differentiability, which would be
necessary for numerous practical applications. Alt-
hough most fuzzy applications (e.g. embedded fuzzy
control) use piecewise linear membership functions
owing to their easy handling, there are areas where
the parameters are learned by a gradient-based opti-
mization method. In this case, the lack of continuous
derivatives makes the application impossible. For ex-
ample, the membership functions have to be differen-
tiable for each input in order to fine-tune a fuzzy cont-
rol system by a simple gradient-based technique. This
problem could be easily solved by using the so-called
squashing function (see Dombi and Gera (Dombi and
Gera, 2005)), which provides a solution to the above-
mentioned problem by a continuously differentiable
approximation of the cut function. This approxima-
tion could be the next step to realizing a practical and
widely applicable system.
The squashing function defined below is a conti-
nuously differentiable approximation of the generali-
zed cutting function (see Definition 2) by means of
sigmoid functions (see Figure 2).
IJCCI 2018 - 10th International Joint Conference on Computational Intelligence
132
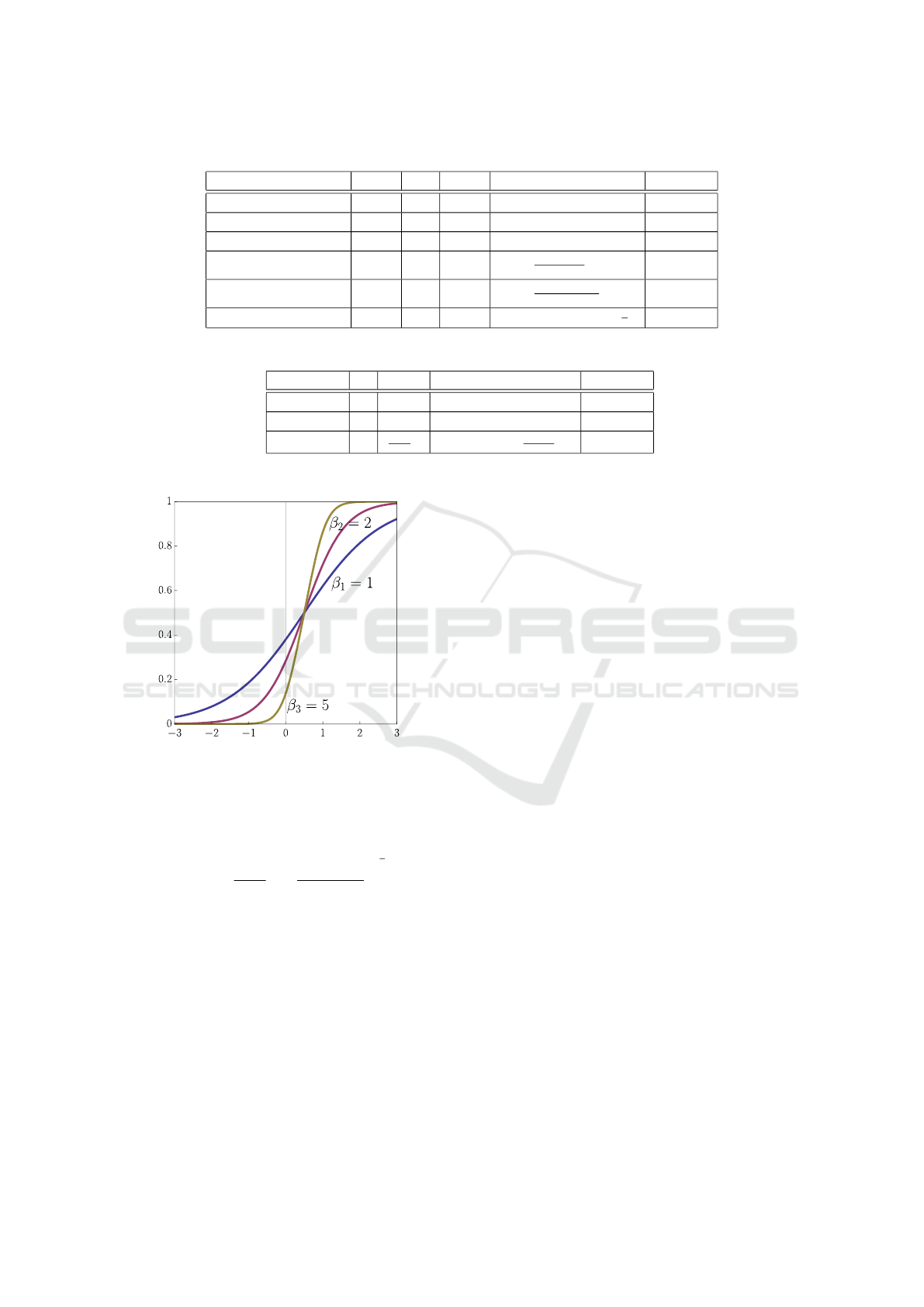
Table 3: Special values for α, β and γ.
α β γ o
α,β,γ
(x, y) Notation
disjunction 1 1 0 f
−1
[ f (x) + f (y)] d(x, y)
conjunction 1 1 −1 f
−1
[ f (x) + f (y) − 1] c(x, y)
implication −1 1 1 f
−1
[ f (y) − f (x) + 1] i(x, y)
arithmetic mean 0.5 0.5 0 f
−1
h
f (x)+ f (y)
2
i
m(x, y)
preference −0.5 0.5 0.5 f
−1
h
f (y)− f (x)+1
2
i
p(x, y)
aggregative operator 1 1 −0.5 f
−1
f (x) + f (y) −
1
2
a(x, y)
Table 4: Special values for γ.
α γ o
α,γ
(x, y) Notation
possibility α 0 f
−1
[α f (x)] τ
P
(x)
necessity α 1 − α f
−1
[α f (x) − (α − 1)] τ
N
(x)
sharpness α
α−1
2
f
−1
[α f (x) −
(α−1)
2
] τ
S
(x)
Figure 2: Squashing functions for b = 1, a = 0, for different
β values (β
1
= 1, β
2
= 2 and β
3
= 5).
Definition 18. (Dombi and Gera, 2005) Let the
squashing function over the interval [a, b] be
S
β
a,b
(x) =
1
b − a
ln
1 + e
β(x−a)
1 + e
β(x−b)
!
1
β
(47)
where a, b ∈ R, a < b, β ∈ R
+
.
The parameters a and b affect the placement of the
squashing function, while the parameter β drives the
precision of the approximation.
The reason for choosing the sigmoid function is its
significant role in applications such as artificial neural
networks, optimization methods, economic and biolo-
gical models.
In Figure 3, ”squashed” unary operators are il-
lustrated; i.e. unary operators, in which the cutting
function is approximated with a squashing function.
5 CONCLUSIONS
The main purpose of this paper was to examine the
main unary operators of a nilpotent logical system.
An integral framework was introduced to reveal the
underlying structure of all the operators considered
so far. As a result, a nilpotent logical system can be
obtained, in which all operators are connected to each
other, and the modalities and hedges are operator-
dependent. This is how it becomes possible to define
all the operators via a single generator function and a
few parameters. By fitting the parameter values, the
system can be used to model real-life problems.
ACKNOWLEDGEMENTS
The research was supported by GINOP-2.1.7-15-
2016-01782. The authors also gratefully acknow-
ledge the financial support by the Faculty of Basic
Sciences, Hochschule Esslingen, University of App-
lied Sciences.
REFERENCES
Baczy
´
nski, M. and Jayaram, B. (2009). On the distributivity
of fuzzy implications over nilpotent or strict triangu-
lar conorms. IEEE Transactions on Fuzzy Systems,
17(3):590–603.
Banks, W. (1994). Mixing crisp and fuzzy logic in appli-
cations. Idea/Microelectronics, WESCON/94, pages
94–97.
C. Ling (1965). Representation of associative functions.
Operator-dependent Modifiers in Nilpotent Logical Systems
133
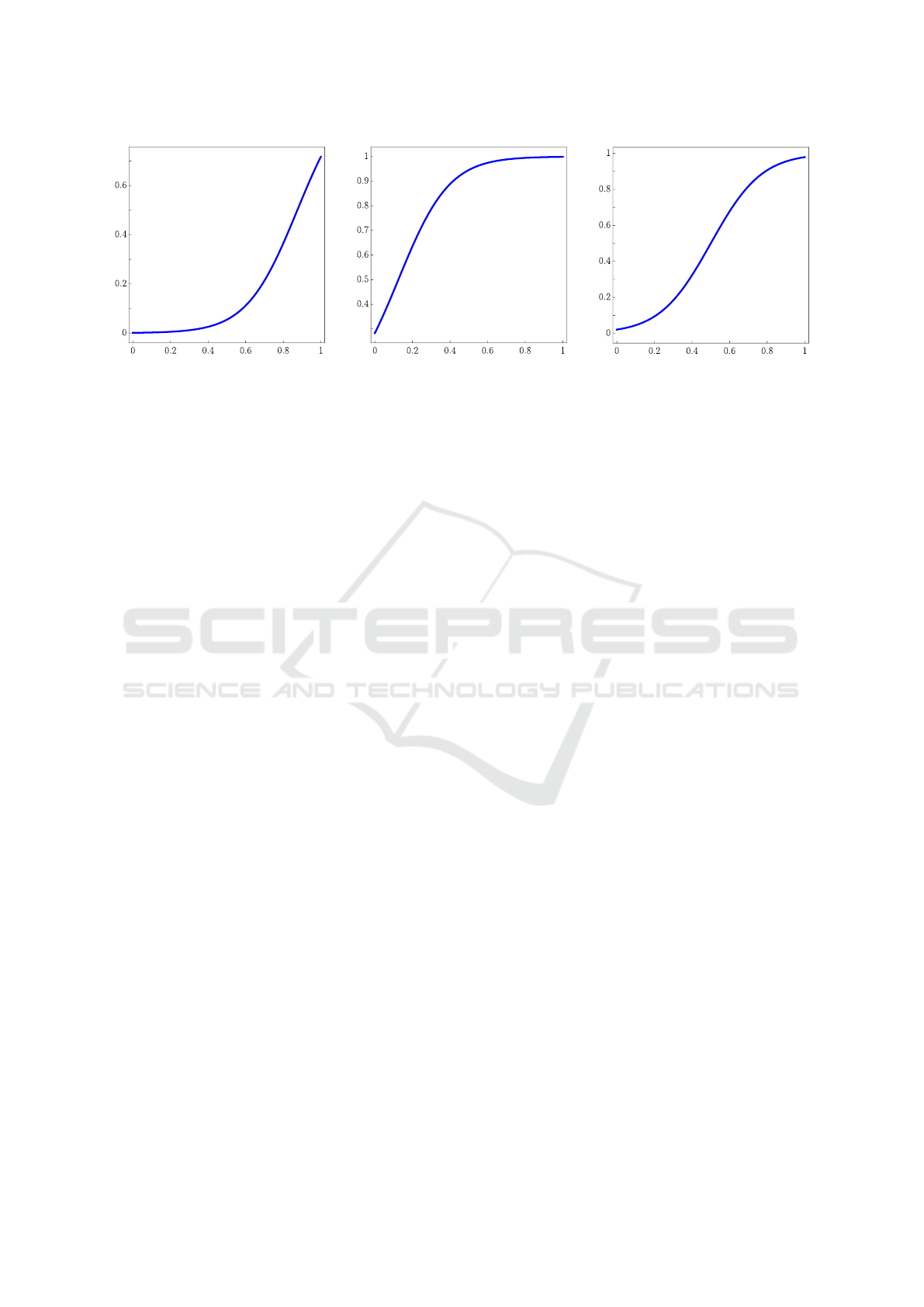
(a) necessity (b) possibility (c) sharpness
Figure 3: Unary operators approximated with the squashing function, a = 4, β = 2.
Publicationes Mathematicae, Debrecen, 12:189—-
212.
De Cock, M., Bodenhofer, U., and Kerre, E. E. (2000). Mo-
delling linguistic expressions using fuzzy relations.
Proc. 6th Int. Conf. on Soft Computing (IIZUKA2000),
2(Iizuka 2000):353–360.
Dombi, J. and Csisz
´
ar, O. (2014). Implications in bounded
systems. Information Sciences, 283:229–240.
Dombi, J. and Csisz
´
ar, O. (2015). The general nilpotent
operator system. Fuzzy Sets and Systems, 261:1–19.
Dombi, J. and Csisz
´
ar, O. (2016). Equivalence operators in
nilpotent systems. Fuzzy Sets and Systems, 299:113–
129.
Dombi, J. and Csisz
´
ar, O. (2017). Self-dual operators and
a general framework for weighted nilpotent opera-
tors. International Journal of Approximate Reasoning,
81:115–127.
Dombi, J. and Gera, Z. (2005). The approximation of pie-
cewise linear membership functions and Lukasiewicz
operators. Fuzzy Sets and Systems, 154:275–286.
Grabisch, M., Marichal, J. L., Mesiar, R., and Pap, E.
(2009). Aggregation Functions.
Huynh, V. N., Ho, T. B., and Nakamori, Y. (2002). A pa-
rametric representation of linguistic hedges in Zadeh’s
fuzzy logic. International Journal of Approximate Re-
asoning, 30(3):203–223.
Jang, J., Sun, C., and Mizutani, E. (1997). Neuro-Fuzzy and
Soft Computing-A Computational Approach to Lear-
ning and Machine Intelligence [Book Review].
Klement, E. P., Mesiar, R., and Pap, E. (2000). Triangular
norms.
L. A. Zadeh (1971). Quantitative fuzzy semantics. Infor-
mation Sciences, 3:159–176.
L. A. Zadeh (1972). A fuzzy-set-theoretic interpretation of
linguistic hedges. Journal of Cybernetics, 2(3):4–34.
Liu, B.-d., Member, S., Chen, C.-y., Member, S., and Tsao,
J.-y. (2001). Design of Adaptive Fuzzy Logic Control-
ler Based on Linguistic-Hedge Concepts and Genetic
Algorithms. 31(1):32–53.
Sabo, M. and Strezo, P. (2005). On Reverses of Some Bi-
nary Operations. Kybernetika, 41:425–434.
Trillas, E. and L. Valverde (1981). On some functionally
expressable implications for fuzzy set theory. pages
173–190.
T
¨
urken, I. B. (2004). A foundation for CWW: Meta-
linguistic axioms. Annual Conference of the North
American Fuzzy Information Processing Society - NA-
FIPS, 1:395–400.
Zadeh, L. (1975a). The concept of a linguistic variable and
its applications to approximate reasoning II. Informa-
tion Sciences, 8(4):199–249.
Zadeh, L. (1975b). The concept of a linguistic variable and
its applications to approximate reasoning III. Infor-
mation Sciences, 8(4):199–249.
Zadeh, L. A. (1975c). The concept of a linguistic variable
and its application to approximate reasoning I. Infor-
mation Sciences, 8(3):199–249.
IJCCI 2018 - 10th International Joint Conference on Computational Intelligence
134
