
DRANKULA: A McEliece-like Rank Metric based Cryptosystem
Implementation
Ameera Salem Al Abdouli, Mohamed Al Ali, Emanuele Bellini, Florian Caullery,
Alexandros Hasikos, Marc Manzano and Victor Mateu
DarkMatter, U.A.E.
Keywords:
Code-based Cryptography, Public Key Cryptography, Cryptosystem, Software Implementation, Post-quantum
Cryptography.
Abstract:
We present and analyze the performance of DRANKULA, a McEliece-like cryptosystem implementation us-
ing rank metric instead of Hamming distance. Namely, we use the scheme proposed by Loidreau in PQCrypto
2017 using Gabidulin codes. We propose a set of carefully selected parameters and we address several non-
trivial issues when porting this scheme into real-world systems as, for example, the generation of errors of a
given rank. We provide the pseudo-code of the core algorithms of the cryptosystem. In addition, we also show
code optimization when special instructions like Carry-less multiplications are available. Moreover, we argue
how to have a practical and side-channel resistant version of the cryptosystem. We integrated the scheme in
Open Quantum Safe and benchmarked it against the other schemes implemented there. Our results show that
DRANKULA can be a practical alternative to other well-known quantum-safe schemes.
1 INTRODUCTION
Substantial advances in quantum computing in the
past decade have re-assured the scientific community
about the necessity to build quantum-resistant cryp-
tosystems (Devoret and Schoelkopf, 2013). Recently,
Google announced Bristlecone, a new 72 qubits quan-
tum processor (Google, 2018). Post-Quantum Cryp-
tography (PQC) has raised as the preferred solution
to face the threat that quantum computers pose to
traditional public-key cryptography based on number
theory (Shor, 1997). The recent announcement by
the National Institute of Standards and Technology
(NIST) to define new standards for public-key encryp-
tion, digital signatures and key-exchange schemes has
only augmented the attention towards PQC (Chen
et al., 2016).
There exist several alternative problems to classi-
cal public-key cryptography, which is based on inte-
ger factorization or discrete logarithms. Lattice-based
cryptography, multivariate cryptography, hash-based
cryptography schemes, isogeny-based cryptography
and code-based cryptography can be used to design
cryptosystems secure against both classical and quan-
tum computers (Bernstein et al., 2008), and are thus
regarded as PQC algorithms, being candidates for be-
coming the next standards defined by NIST.
Code-based cryptography is the oldest PQC fam-
ily known and consequently is the most thoroughly
studied among the PQC candidates (Sendrier, 2017).
McEliece proposed the first code-based public-key
cryptosystem (McEliece, 1978), which is based on bi-
nary Goppa codes, and so far has withstood all crypt-
analytic efforts. Another well known cryptosystem
was proposed by Niederreiter in (Niederreiter, 1986).
Recently, Bernstein, Chou and Schwabe presented
McBits, which improved decryption time with respect
to Niederreiter (Bernstein et al., 2015). An improved
version was presented in (Chou, 2017). However, the
usage of the aforementioned schemes in real world
applications has been prohibitive because of the sig-
nificantly large key sizes (e.g., McBits requires 64KB
to achieve 2
80
classical security level). Therefore, the
most important challenge that code-based cryptogra-
phy faces is how to reduce key sizes in order to be
implemented on limited resource devices.
Two different lines have been investigated with the
purpose of reducing key sizes. On the one hand, sev-
eral works have tried to address this drawback by de-
signing McEliece variants with more compact keys
by using quasicyclic codes (Gaborit, 2005; Misoczki
et al., 2013; Chou, 2016). On the other hand, the us-
age of rank metric rather than Hamming distance has
been considered.
The rank metric was introduced by Gabidulin in
(Gabidulin, 1985) and he proposed a family of codes,
the Gabidulin codes, equivalent to Reed-Solomon
codes in Hamming distance, which can be decoded in
64
Abdouli, A., Ali, M., Bellini, E., Caullery, F., Hasikos, A., Manzano, M. and Mateu, V.
DRANKULA: A McEliece-like Rank Metric based Cryptosystem Implementation.
DOI: 10.5220/0006838100640075
In Proceedings of the 15th International Joint Conference on e-Business and Telecommunications (ICETE 2018) - Volume 2: SECRYPT, pages 64-75
ISBN: 978-989-758-319-3
Copyright © 2018 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved

polynomial time. Rank Syndrome Decoding (RSD)
is the equivalent in rank metric of the Syndrome
Decoding problem in Hamming distance. Later on,
Gabidulin et al. proposed the GPT cryptosystem,
a McEliece-like cryptosystem based on Rank metric
(Gabidulin et al., 1991). One of the advantages of us-
ing Gabidulin codes is that the complexity of the best
known attacks for solving the RSD problem have an
exponential complexity which is quadratic in the pa-
rameters of the system. As a consequence, key sizes
can be notably reduced to achieve the same security
level than a Hamming distance-based cryptosystem.
Then, Overbeck proposed a framework that dev-
astated all Gabidulin codes based encryption schemes
(Overbeck, 2005; Overbeck, 2008). Furthermore,
evolutions of the GPT cryptosystem have been shown
to be also breakable in polynomial-time (Otmani
et al., 2016). Nevertheless, Loidreau has proposed
a new McEliece-like rank metric based encryption
scheme from Gabidulin codes that is not affected by
the so-called Overbeck’s attacks (Loidreau, 2017).
In this work we carry out the first implementation
of the scheme proposed in (Loidreau, 2017), which
we have called DRANKULA. We present a set of se-
lected parameters that allow the scheme to achieve
different levels of quantum security; namely 64, 96
and 128 bit. We motivate this parameter selection
by implementation constraints and optimization pos-
sibilities. Moreover, we go through all the caveats of
the implementation of a cryptosystem based on rank
metric codes, and we provide the pseudo-code for the
main algorithms. We also discuss several counter-
measures that would make the implementation side-
channel resistant.
1.1 Organization of the Paper
The rest of the paper is structured as follows. First, in
Section 2 we outline all the code-based Key Encapsu-
lation Mechanism (KEM) and Public Key Encryption
(PKE) submissions to the NIST competition and then
in Section 3 we introduce the cryptosystem we are
implementing on this paper, and the selected parame-
ters. Section 4 is devoted to the base field arithmetic
and matrix operations that are required to implement
for running the cryptosystem. In Section 5 we present
the necessary code-blocks used to build the cryptosys-
tem, namely, (a) the key generation, (b) the encryp-
tion which includes the error generation, and (c) the
decryption. Section 6 gives an overview of the per-
formance of the scheme compared with other post-
quantum cryptography schemes. Section 7 presents
some directions to have a side-channel resistant im-
plementation. Finally, we provide the conclusions of
our proposal in Section 8.
2 RANK-METRIC NIST
SUBMISSIONS
There were four code-based KEM and PKE schemes
based on the rank metric submitted to the first round
of the NIST post-quantum cryptography standardiza-
tion competition (NIST, 2018). First, Ouroboros-R
(Deneuville et al., 2017), is a cryptosystem that inher-
its features from MDPC-McEliece (Misoczki et al.,
2013) and the rank metric quasi-cyclic family. The
security relies on decoding small weight vectors of
random quasi-cyclic codes. The advantages are the
security reduction with small public key sizes result-
ing from cyclicity, the easy evaluation of the low
decryption failure probabilities and the efficiency of
the decoding compared to MDP. Second, LAKE (Ga-
borit et al., 2013), which stands for Low rAnk parity
check codes Key Exchange, is a rank-metric scheme
for which the authors provide an efficient probabilis-
tic decoding algorithm. The quasi-cyclic family of
codes that is being used produces a public key which
is significantly smaller than MDPC codes. Similar to
LAKE, LOCKER (Aragon et al., 2017) is built on a
small variation of low rank parity check codes and
has been adapted to support low decryption proba-
bility failures with a versatile choice of parameters.
Considering the low decryption failure probabilities
the scheme is efficient in terms of key sizes and com-
putational complexity. These three schemes share the
property of a probabilistic decryption algorithms. In
contrast, DRANKULA offers a deterministic decryp-
tion procedure which makes it more suitable in sce-
narios where we cannot tolerate decryption failures.
Last, RQC (Melchor et al., 2016), is another rank-
metric scheme that is also based on the difficulty of
decoding random quasi-cyclic codes. The key-size of
the scheme is restricted to a few thousands of bytes
and has a deterministic decoding algorithm. It is also
resistant to code hidden structure recovery attacks.
Although having a bigger key size, DRANKULA re-
duces the ciphertext expansion by a factor of 2 in
comparison to RQC.
3 CRYPTOSYSTEM
DESCRIPTION
The scheme we have chosen to implement is the one
proposed in (Loidreau, 2017). It is a scheme based
on Gabidulin codes using a special sub-space for the
entries of the scrambling matrix which transforms the
private key into the public key.
The essential difference between the presented
DRANKULA: A McEliece-like Rank Metric based Cryptosystem Implementation
65

cryptosystem and traditional McEliece instantiations
is that, instead of XORing the encoded plaintext with
errors of a given Hamming weight, we do it with an
error of a specific rank weight.
Definition 1. Let e = {e
1
,...,e
n
} ∈ F
n
2
m
. The rank
weight of e is defined by
rk(
e
1,1
··· e
n,1
e
1,2
··· e
n,2
.
.
.
.
.
.
.
.
.
e
1,m
··· e
n,m
)
where e
i, j
is the jth component of e
i
seen as a vector
over F
2
.
Definition 2 (Gabidulin codes). Let k < n ≤ m be
non-negative integers and let {g
1
,...,g
n
} ∈ F
2
m
, be
linearly independent over F
2
. Let [i] = 2
i
such that
x → x
[i]
is the ith power of the Frobenius automor-
phism x → x
2
. The code Gab
k,n
(g), is the linear code
with generator matrix
G =
g
1
··· g
n
g
[1]
1
··· g
[1]
n
.
.
.
.
.
.
.
.
.
g
[k−1]
1
··· g
[k−1]
n
that is:
Gab
k,n
(g) = {xG|x ∈ F
k
2
m
}.
These codes can be decoded in polynomial-time
for errors of rank weight up to b(n−k)/2c (Gabidulin,
1985).
Gabidulin Codes are the rank-metric equivalent of
Reed Solomon Codes. The scheme’s approach is to
choose a randomly selected vector space of F
m
2
of
fixed dimension which is used to scramble the codes.
The proof of correctness of the cryptosystem is based
on the rank multiplication property, the same one used
to show that the Low Rank Parity Check (LRPC)
codes decoding procedure works.
The scheme has four parameters:
• m:= the degree of the extension of F
2
in which our
code will be defined
• n:= the length of the code
• k:= the dimension of the code
• λ:= the dimension of a randomly selected sub-
space of F
2
m
The security bounds of the scheme given in
(Loidreau, 2017) are the following:
• Decoding of the ciphertext in the public code cor-
responds to the complexity of solving Bounded
Distance binary Rank decoding BDR problem
which is NP-hard. In that setting, the decoding
complexity is equal to m
3
2
(λRk(e)−1)b(k min(m,n))/nc
binary operations for a classical computer and
to m
3
2
1
2
(λRk(e)−1)b(k min(m,n))/nc
operations for a
quantum computer.
• The lower bound on the complexity of distin-
guishability of the public code from a random
code is 2
(λ−1)m−(λ−1)
2
.
Finally, the scheme is separated into the three fol-
lowing parts:
• Key Generation:
– Private Key:
1. Select a Gabidulin code of length n and di-
mension k over F
2
m
with generator matrix
G
priv
2. Randomly generate a non-singular k × k ma-
trix S ∈ M
k
(F
2
m
)
3. Randomly select a vectorial subspace V ⊂ F
m
2
of dimension λ
4. Randomly generate a non-singular P ∈ M
n
(V )
– Public Key: The public code C
pub
has G
pub
=
SG
priv
P
−1
as a generator matrix.
• Encryption:
1. Choose a random vector e ∈ F
n
2
m
of rank weight
t := b(n − k)/(2λ)c
2. Compute y = xG
pub
+ e
3. Send y
• Decryption:
1. Compute yP = xSG + eP
2. Recover xS and eP by decoding and recover x
by multiplying xS by S
−1
We refer to (Loidreau, 2017) for the proof of work.
3.1 Parameters Selection
The parameters proposed in (Loidreau, 2017) were
not optimal for its implementation because they were
focused on reducing the size of both private and pub-
lic keys instead. For our implementation, we have
chosen a base field which is either F
2
64
or F
2
96
to
fit nicely into the words structure available on mod-
ern machines and carry out optimizations based on
special sets of instructions (e.g. carry-less multipli-
cation). We targeted 3 levels of post-quantum secu-
rity, namely 64 bit, 96 bit and 128 bit and we have
determined the following parameters. Table 1 shows
our parameter sets and their respective security lev-
els. Such values are computed following the formulas
given in (Loidreau, 2017) and are consistent with the
ones presented in that paper.
SECRYPT 2018 - International Conference on Security and Cryptography
66
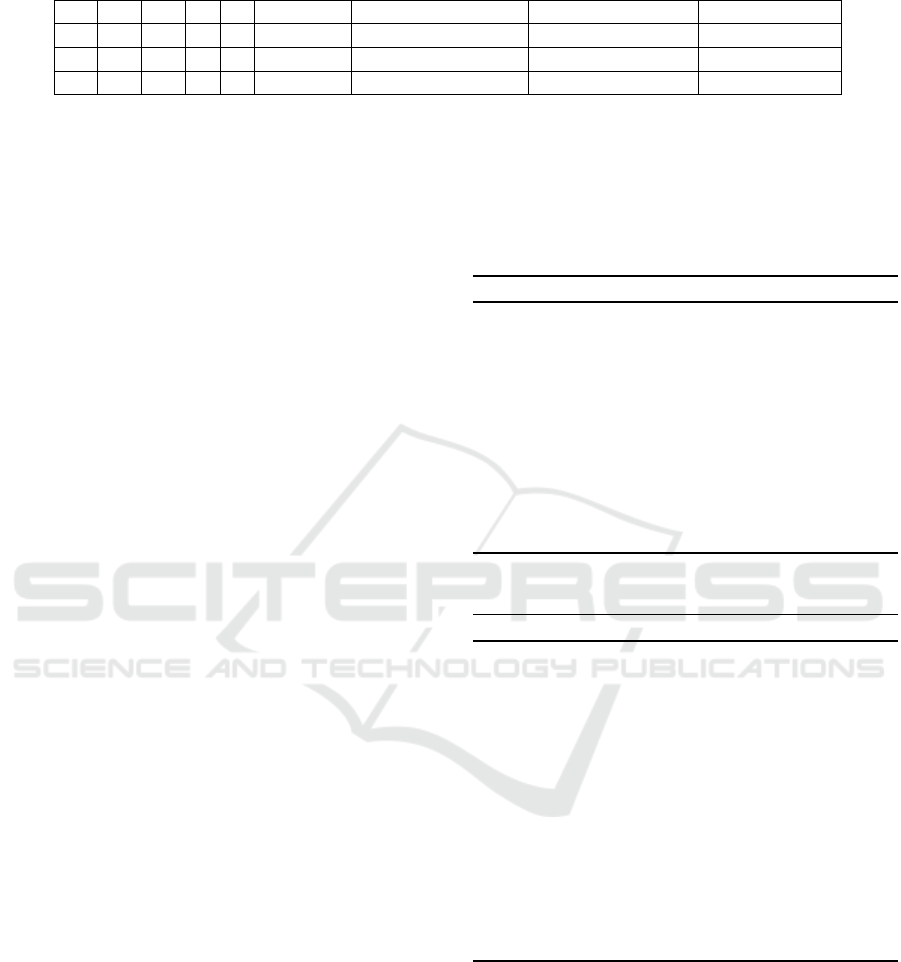
Table 1: DRANKULA security parameters.
m n k λ t dec. cplx quantum dec. cplx. key recovery cplx. public key size
64 63 31 3 5 142 78 124 7.75KB
96 71 35 3 6 194.76 104.76 188 14.77KB
96 96 48 4 6 259.75 139.75 279 27KB
4 IMPLEMENTATION OF CORE
COMPONENTS
Given the nature of the cryptosystem, the core com-
ponents are the field arithmetic and the matrix oper-
ations. Therefore, the performance of the resulting
algorithms will heavily rely on how efficient such op-
erations are.
4.1 Field Arithmetic
We implemented finite field arithmetic for the two bi-
nary fields F
2
m
, with m = 64 and m = 96, represent-
ing elements as polynomials of degree m − 1. As it
was proven in Swan’s Theorem (Swan, 1962) on fac-
torization of polynomials over finite fields, given that
64 and 96 are multiples of 8 there is no irreducible
trinomial. Therefore, we used the two following ir-
reducible pentanomial f
64
(x) = x
64
+ x
4
+ x
3
+ x + 1
and f
96
(x) = x
96
+x
10
+x
9
+x
6
+1, respectively, both
provided by the Allan Steel database incorporated
in Magma software (Bosma et al., 1997). Notice
that in the case of f
64
the pentanomial has also low-
est possible intermediate degree, allowing the short-
est shift during the reduction operations. Such irre-
ducible polynomial for the case of F
96
has 7 terms,
i.e. x
96
+ x
6
+ x
5
+ x
3
+ x
2
+ x + 1, which is not con-
venient to use compared with the pentanomial.
We stored elements in both fields using 128 unsigned
integers, with unused bits set to zero.
Addition and subtraction of two elements are a simple
XOR operation.
The multiplication of two polynomials has been per-
formed using PCLMULQDQ instruction (Gueron and
Kounavis, 2010). In the case of F
96
, three calls to such
instruction are needed, since the instruction operates
on 64 bit inputs. For this reason we split one ele-
ment of 96 bits in two elements of 32 and 64 bits re-
spectively, and then apply Karatsuba-Ofman method
(Karatsuba and Ofman, 1962). In the case of F
64
, only
one call to the instruction is needed, and there is no
need to split the element.
Since the multiplication provides polynomials of de-
gree at most 2m−2, we need to perform the reduction
of such result. The two algorithms for reduction are
presented in Algorithm 1 and Algorithm 2, where the
symbols , denote field multiplication and divi-
sion by x respectively (left and right shift operators),
⊕ is the field addition (XOR operator), and || is the
concatenation operator.
Algorithm 1: Reduction in F
2
64
.
input : A = (a
126
,...,a
0
) ∈ F
127
2
output : C = A mod f
64
∈ F
64
2
1 A
0
= (a
63
,...,a
0
) ∈ F
64
2
2 A
1
= (0,a
126
,...,a
64
) ∈ F
64
2
3 A
0
= A
0
⊕ (A
1
4) ⊕ (A
1
3) ⊕ (A
1
1) ⊕ A
1
4 A
1
= (A
1
60) ⊕ (A
1
61) ⊕ (A
1
63)
5 T = (0,...,0,a
67
,a
66
,a
65
,a
64
) ∈ F
64
2
6 A
0
= A
0
⊕(T 4)⊕(T 3)⊕(T 1)⊕T
7 return A
0
Algorithm 2: Reduction in F
2
96
.
input : A = (a
190
,...,a
0
) ∈ F
191
2
output : C = A mod f
96
∈ F
96
2
1 A
0
= (a
63
,...,a
0
) ∈ F
64
2
2 A
1
= (a
127
,...,a
64
) ∈ F
64
2
3 A
2
= (0,...,0,a
190
,...,a
128
) ∈ F
64
2
4 A
0
= A
0
⊕ (A
2
42) ⊕ (A
2
41) ⊕ (A
2
38) ⊕ (A
2
32)
5 A
1
= A
1
⊕ (A
2
22) ⊕ (A
2
23) ⊕ (A
2
26) ⊕ (A
2
32)
6 T = (0,...,0,a
127
,...,a
96
) ∈ F
64
2
7 A
0
= A
0
⊕ (T 10) ⊕ (T 9) ⊕ (T
6) ⊕ T
8 return A
1
||A
0
∈ F
96
2
To limit memory usage, the inversion on the field
relies on the Extended Euclidean Algorithm (Hanker-
son et al., 2006). An alternative requiring more mem-
ory, which we did not consider, would be Itoh-Tsujii
algorithm with precomputed powers (Itoh and Tsujii,
1988).
DRANKULA: A McEliece-like Rank Metric based Cryptosystem Implementation
67

4.2 Matrix Operations
The operations needed in our implementation are the
following:
• Matrix multiplications
• Gaussian elimination in order to perform:
– Matrix inversion for square matrices
– Assertion of linear independence
– Reduction of the generator matrix of the public
code to the systematic form (i.e. rewrite G
pub
as [Id
k
||G
0
pub
])
It has to be noted that those operations were im-
plemented with two variants. That is, one for the ma-
trices with coefficients in F
2
and one for the matrices
with coefficients in F
2
m
. As the sizes of the matrices
are quite small (96 × 96 at maximum), the naive al-
gorithms were actually faster than any optimized ver-
sion. For example, the matrix multiplication is not us-
ing Strassen’s algorithm and matrix inversion is car-
ried out using Gaussian elimination.
5 ALGORITHMS
IMPLEMENTATION
Loidreau’s proposed scheme consists of the three al-
gorithms sumarized in Section 3. Here we present our
implementation for each of them.
5.1 Key Generation
The key generation is pretty simple. It just requires to
generate random matrices with coefficients in F
2
or
F
2
m
of the right dimension and to ensure that they re-
spect the conditions given in the scheme specification.
If the randomly generated matrix does not fulfill the
conditions, then repeat the process until one suitable
candidate is found.
More precisely, the conditions are the following:
• The generators g
1
,...,g
n
of the Gabidulin code
with generator matrix G
priv
are all linearly inde-
pendent over F
2
. That is, the binary matrix
g
1,1
... g
n,1
.
.
.
.
.
.
.
.
.
g
1,m
... g
n,m
,
where g
i, j
is the j-th bit of g
i
, has a rank equal to
n.
• The λ random elements of F
2
m
which shall be seen
as the basis of V have to be linearly independent
over F
2
.
• Matrices P ∈ M
n
(V ) and S ∈ M
k
(F
2
m
) should be
non-singular.
Luckily, the density of non-singular matrices with
coefficients in finite field is high (see (Maples, 2013))
and the sample-rejection strategy is guaranteed to be
fast for the generation of P and S or even of g
1
,...,g
n
in the case where m = n.
5.2 Encryption
The encryption operation uses a matrix multiplication
and a vector addition. Nevertheless, the generation of
an error vector of a given rank is a tricky process. In-
deed, the probability that a randomly generated n × m
matrix with coefficients in F
2
has a rank equal to the
value specified in the scheme is low (see (Maples,
2013)). There is a need for a more optimized strategy.
The idea is to generate t random linearly independent
vectors of F
m
2
and then generate n random linear com-
binations of those vectors. This is the method which
is also used in (Deneuville et al., 2017). The pseudo-
code of the error generation is given in Algorithm 3.
Algorithm 3: Random error generation.
input : The binary field size m, the
length of the error n and the error
rank t
output : A random element
e := {e
1
,...,e
n
} ∈ F
n
2
m
such that
rk(e) = t
1 while not linearly independent(b
1
,...,b
t
)
do
2 b
1
,...,b
t
←generate random vectors(t,F
2
m
)
3 while rk(e) 6= t do
4 for i from 1 to n do
5 rand
$
←− {0,1}
t
6 e
i
=
∑
t
k=1
rand
k
× b
k
7 return e
Even if highly unlikely, it could happen that the
coefficient associated to one (or more) of the gener-
ating vectors is always zero. In that case, the error
vector would have a rank lower than t. This is why
the rank of the output error vector must be checked
and, in case it does not fulfill the requirements of the
scheme, another error vector must be generated.
5.3 Decryption
Given an encrypted message y = xSG
priv
P
−1
+ e, the
first step to decrypt it is to multiply y by P to ob-
tain yP = xSG
priv
+ eP. After that, the Algorithm 11
SECRYPT 2018 - International Conference on Security and Cryptography
68

might be used to obtain the corrected message which
is equal to xS. Finally, the cleartext x is computed by
multiplying xS and S
−1
. Notice that S is only needed
during the public key generation but, for decryption,
it is S
−1
the required matrix. Therefore, in our im-
plementation we store S
−1
as part of the private key
instead of S in order to avoid the computations and
memory consumption from the inversion in each de-
cryption operation.
The core component of the decryption algorithm
is the error detection and correction. In order to op-
timize this step, we use the algorithms provided in
(Puchinger and Wachter-Zeh, 2015) and (Wachter-
Zeh, 2013). Here we provide the pseudo-code of the
algorithms. We refer to the aforementioned papers
for the proof that these algorithms correctly decode
any error with rank less or equal to b(n − k)/2λc, and
an in-depth explanation of the main idea. Essentially,
this decoding procedure can be seen as the equiv-
alent of Gao’s algorithm (Gao, 2003) for decoding
Gabidulin codes. It outputs an evaluation polynomial
of the estimated message thus avoiding to solve large
linear equations systems depending on the syndrome.
To the best of our knowledge, this is the fastest de-
coding procedure for Gabidulin codes. The algorithm
takes advantage of the properties of linearized poly-
nomials to achieve a sub-quadratic complexity. Since
linearized polynomials are used in all the algorithms
for decryption, we briefly recall their definition.
Definition 3 (Linearized polynomials). A linearized
polynomial a(x) ∈ F
2
m
[x] is a polynomial of the form
d
∑
i=0
a
i
x
[i]
,
where x
[i]
= x
2
i
and d is the 2-degree of a, denoted as
deg
2
(a) in this paper.
We will denote by L
2
m
[x] the space of all lin-
earized polynomials of F
2
m
[x] and by L
2
m
[x]
≤s
the
space of all linearized polynomials of F
2
m
[x] with
maximum degree s. When embedded with the stan-
dard addition + and composition ◦, L
2
m
[x] is a left
(right) euclidean ring. Meaning that we can define a
left (right) division.
5.3.1 Algorithms Notation
Given that the algorithms required to compute the de-
coding of a message are presented next, here we in-
troduce the notation rules we have used:
• We denote as c
i
the coefficient at position i from
polynomial c.
• We denote as Frobenius(x,n) the computation of
the n-th iteration of Frobenius automorphism over
x.
• Given a linearized polynomial p, we denote as
p = 0 the assignment to p of a polynomial with
all its coefficients being 0.
• Given a linearized polynomial p, we denote as
p = x to represent that p is the linearized poly-
nomial with coefficient 1 in the lowest degree po-
sition (i.e. the coefficient of the term x) and 0s in
all others.
• We use the notation U[i] to denote that U is a vec-
tor of elements in F
2
m
where we access its ith po-
sition.
• We use —— as the concatenation operation.
• We use #U to denote the amount of elements of a
vector U.
5.3.2 Linearized Polynomial Multiplication
The first needed subroutine is the fast multiplication
of two linearized polynomials. Recall that the mul-
tiplication in the ring L
2
m
[x] is actually the standard
composition. The details of its implementation are in
Algorithm 4.
Algorithm 4: Multiplication.
input : a,b ∈ L
2
m
[x]
≤s
output: c = a ◦ b ∈ L
2
m
[x]
≤s
1 for i from 0 to deg
2
(a) + deg
2
(b) do
2 y = 0
3 for j from 0 to i do
4 if j ≤ deg
2
(a) and i − j ≤ deg
2
(b)
then
5 z = Frobenius(b
i− j
, j)
6 z = z · a
j
7 y = y + z
8 c
i
= y
9 return c
5.3.3 Linearized Polynomial Divisions
As L
2
m
[x] is a Euclidean ring, we can define a divi-
sion. As the multiplication in that ring is not com-
mutative, there exist a well-defined left and right divi-
sion. The fast algorithms for the left and right division
are given by Algorithms 5 and 6, respectively.
5.3.4 Right Linearized Extendend Euclidean
Algorithm
We can use a Linearized version of the Euclidean
Algorithm (LEEA) based on the divisions defined
DRANKULA: A McEliece-like Rank Metric based Cryptosystem Implementation
69
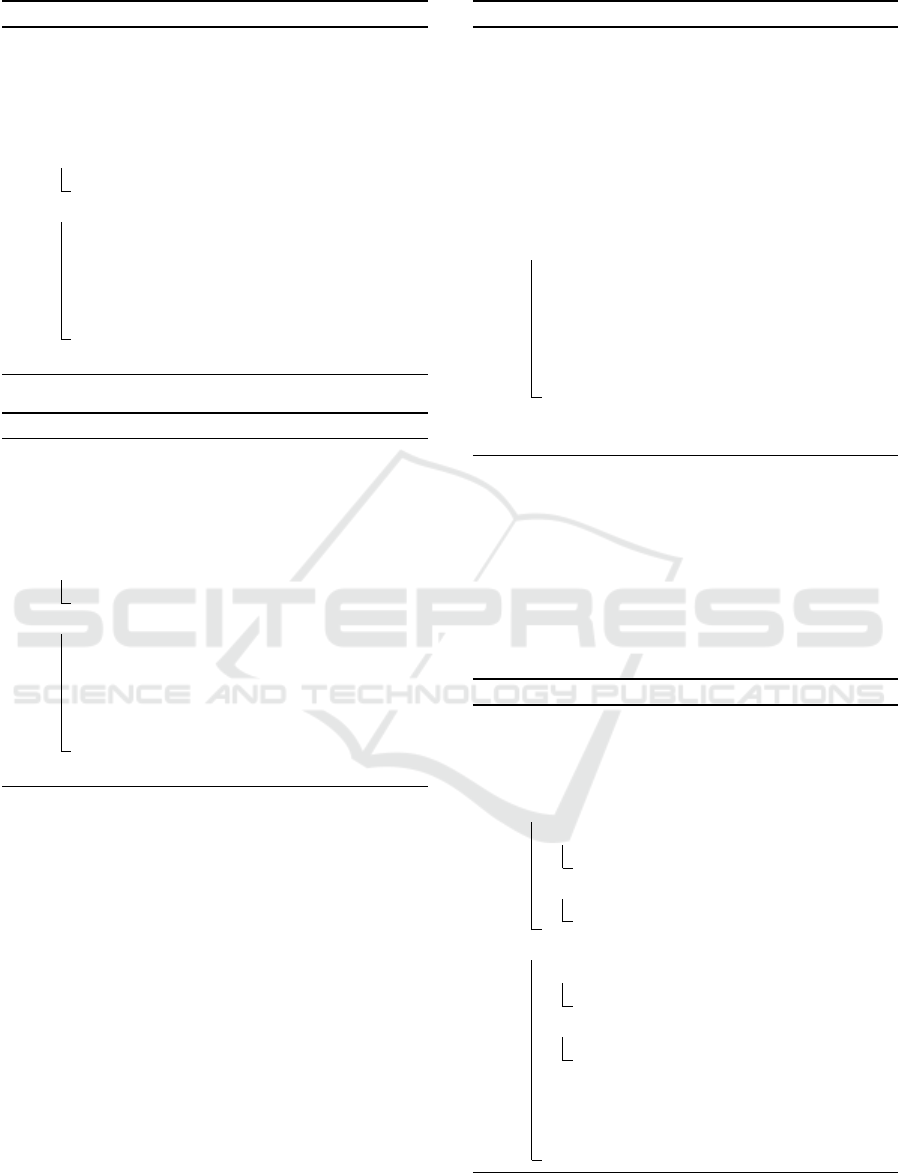
Algorithm 5: LeftDivision.
input : a, b ∈ L
2
m
[x] − {0}
output : q,r ∈ L
2
m
[x] such that
b ◦ q + r = a
initialize: r = a, db = deg
2
(b),
q = 0, di = deg
2
(r),
1 if di < db then
2 return q, r
3 while di ≥ db do
4 q
0
= 0
5 q
0
di−db
= Frobenius(r
di
/b
db
,m − db)
6 q = q + q
0
7 r = r + b ◦ q
0
8 di = deg
2
(r)
9 return q, r
Algorithm 6: RightDivision.
input : a,b ∈ L
2
m
[x] − {0}
output : q,r ∈ L
2
m
[x] such that
q ◦ b + r = a
initialize: r = a, db = deg
2
(b),
q = 0, di = deg
2
(r),
1 if di < db then
2 return q, r
3 while di ≥ db do
4 q
0
= 0
5 q
0
di−db
= r
di
/ Frobenius(b
db
,di − db)
6 q = q + q
0
7 r = r + q
0
◦ b
8 di = deg
2
(r)
9 return q, r
above. Given that only the version using right division
is required, in Algorithm 7 we show the implementa-
tion of the right LEEA algorithm.
5.3.5 Minimal Subspace Polynomial (MSP) and
Multi-Point Evaluation (MPE)
The next needed notion is the so-called Minimal Sub-
space Polynomial which is the linearized polynomial
of minimal degree which vanishes over a subspace of
F
m
2
. Its existence and uniqueness is ensured by the
following lemma.
Lemma 1 (Minimal Subspace Polynomial (MSP),
(Lidl and Niederreiter, 1997)). Let U be a linear
subspace of F
m
2
. Then there exists a unique nonzero
monic polynomial M
U
∈ L
2
m
of minimal degree such
that kerM
U
= U. Its degree is dimU.
Algorithm 7: RightLEEA.
input : a,b ∈ L
2
m
[x] with
deg
2
(a) ≥ deg
2
(b), stopping
degree d
stop
output : τ,z,y ∈ L
2
m
[x] such that
τ = z ◦ a + y ◦ b and
deg
2
(τ) < d
stop
initialize: z = 0, y = x,
v = 0, u = x,
a
0
= a, b
0
= b
1 while deg
2
(b) ≥ d
stop
and a 6= 0 do
2 q,r = RightDivision(b
0
,a
0
)
3 l = z + q ◦ u
4 i = y + q ◦ v
5 b
0
= a
0
, a
0
= r
6 z = u, y = v
7 u = l, v = i
8 τ = b
0
9 return τ, z, y
Algorithm 8 is used to find the MSP of a subspace
of F
m
2
and requires another operation called Multi-
Point Evaluation (MPE) which outputs the evaluation
of a linearized polynomial over a set of points in F
2
m
.
The algorithm to compute MPE is presented in Algo-
rithm 9. Both algorithms apply the divide and con-
quer strategy and call each other recursively.
Algorithm 8: MSP.
input : Generating set U = u
1
,...,u
s
of a
subspace U ∈ F
m
2
output: p ∈ L
2
m
[x]
≤s
such that p(u
i
) = 0
for each i ∈ {1, . . . , s}
1 if s = 1 then
2 if U[1] = 0 then
44 return p = x
5 else
6 return p = x −U[1]
7 else
8 for i from 1 to bs/2c do
9 A[i] := U[i]
10 for i from bs/2c + 1 to s do
11 B[i − bs/2c] = U[i]
12 a = MSP(A)
13 P
0
= MPE(a,B)
14 b = MSP(P
0
)
15 return p = b ◦ a
SECRYPT 2018 - International Conference on Security and Cryptography
70

Algorithm 9: MPE.
input : a ∈ L
2
m
[x]
≤s
,{u
1
,...,u
s
} ∈ F
s
2
m
output: Vector A = [a(u
1
),...,a(u
s
)] ∈ F
s
2
m
1 if a = 0 then
2 return A = [0
1
,...,0
s
];
3 if s = 1 then
4 σ = 0
5 for i from 0 to deg
2
(a) do
6 σ = σ + a
i+1
· Frobenius(U[1],i)
7 return A = [σ]
8 else
9 for i from 1 to bs/2c do
10 A[i] = U[i]
11 for i from bs/2c+ 1 to s do
12 B[i − bs/2c] = U[i]
13 w = MSP(A)
14 w
0
= MSP(B)
15 q, r = RightDivision(a,w)
16 q
0
,
0
= RightDivision(a,w
0
)
17 return A = MPE(r
0
,A)kMPE(r
0
,B)
5.3.6 Interpolation
The last subroutine is shown in Algorithm 10, and
depicts an instantiation of the interpolation algorithm
optimized for linearized polynomials which also uses
the MSP and MPE Algorithms 8, 9.
Algorithm 10: Interpolation.
input : (w
1
,y
1
),...,(w
s
,y
s
) ∈ F
2
2
m
, x
i
linearly independent over F
2
output: Interpolation polynomial p such
that p(w
i
) = y
i
for all i ∈ {1, . . . , s}
1 if s = 1 then
2 return [y[1]/w[1]]
3 else
4 for i from 1 to bs/2c do
5 A[i] = w[i]
6 for i from bs/2c+ 1 to s do
7 B[i − bs/2c] = w[i]
8 p = MSP(A)
9 p
0
= MSP(B)
10 Z = MPE(p
0
,A)
11 Z
0
= MPE(p, B)
12 I = Interpolation(Z, [y[1], . . . , y[#Z]])
13 I
0
= Interpolation(Z
0
,[y[#Z],...,y[#Z +
#Z
0
]])
14 return I ◦ M
0
+ I
0
◦ M
5.3.7 Gabidulin Decoding
Finally, we present the main decoding procedure in
Algorithm 11. One can immediately spot that the
second step of this procedure is only depending on
the generators of the chosen Gabidulin code which
is part of the private key. Hence, one can store
the MSP(
h
g
i
,...,g
n
i
) into the private key to opti-
mize the decoding speed at the price of memory con-
sumption. Notice that, the value v computed in the
RightLEEA step is the error span polynomial as de-
fined in (Wachter-Zeh, 2013).
Algorithm 11: Gabidulin Decoding.
input : Received word r ∈ F
n
2
m
and the
Gab
k,n
code generators
{g
1
,g
2
,...,g
n
}
output: Corrected codeword z, or a
decoding failure message
1 ˜r = Interpolation(g,r)
2 M = MSP(g)
3 r, u, v = RightLEEA(M, ˜r, b(n + k)/2c)
4 z, p = LeftDivision(r,v)
5 if p = 0 then
6 return z
7 else
8 return ”Decoding Failure”
6 PERFORMANCE RESULTS
Our software implementation has been designed as an
extension of the Open Quantum Safe (OQS) project
(Mosca et al., 2017). The main motivation was to be
able to compare our scheme with the other available
cryptosystems under the same conditions. We have
integrated DRANKULA in the OQS library and have
performed the automated benchmarks. The bench-
marks have been run on a MacBook Pro 2017, 2.9
GHz Intel Core i7, 16 GB 2133 MHz LPDDR3.
Table 2 presents the OQS benchmark results. As
can be observed, DRANKULA has a faster key gen-
eration than McBits as well as a significantly lower
public key size. Moreover, our scheme is faster than
SIDH for encryption and decryption, but that comes
at the price of a larger ciphertext. Same results ap-
ply to SIKE. Although RLWE BCNS15 has the best
key generation performance, its encryption is substan-
tially worse than DRANKULA with respect to both
performance and ciphertext size.
Tables 3 and Table 4 show DRANKULA’s per-
formance for the three levels of security considered
DRANKULA: A McEliece-like Rank Metric based Cryptosystem Implementation
71
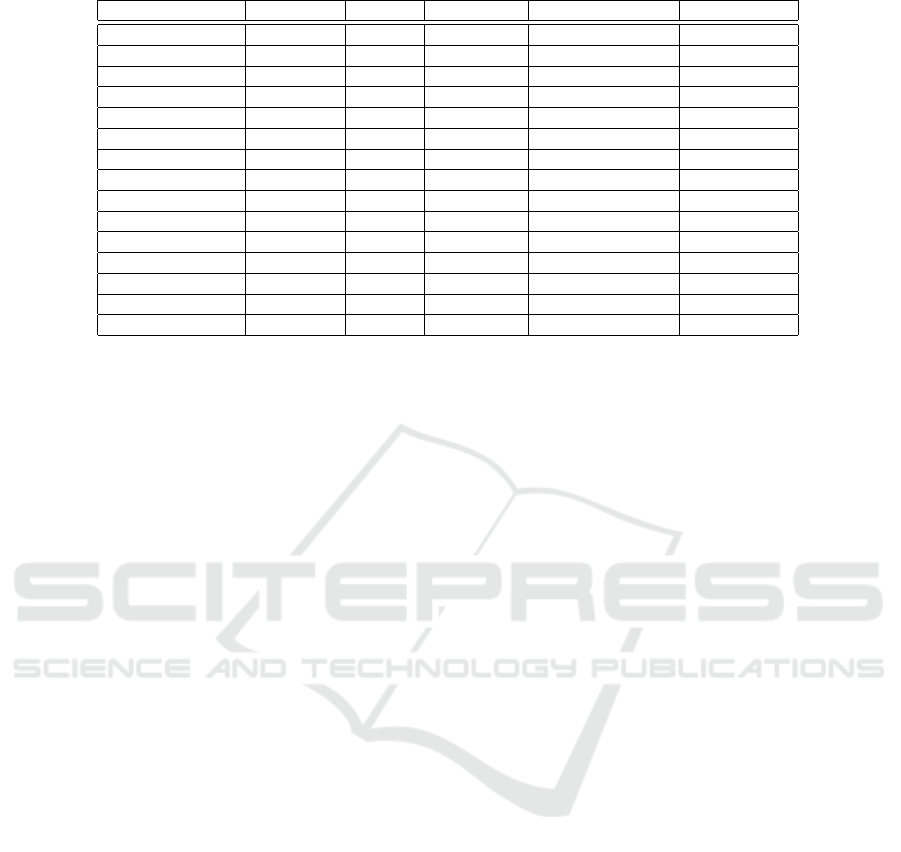
Table 2: Performance comparison between different post-quantum cryptography schemes using OQS.
Scheme Class. sec. PQ sec. operation mean CPU cycles Bytes comm.
McBits 128 - Key gen. 196,718,429 311,736
Encryption 72,952 141
Decryption 331,282
DRANKULA 128 78 Key gen. 159,808,905 7,936
Encryption 115,975 504
Decryption 7,761,451
SIDH 126 84 Key gen. 70,672,623 378
Encryption 143,629,801 378
Decryption 56,956,858
SIKE 126 84 Key gen. 77,602,053 378
Encryption 126,294,194 402
Decryption 134,851,945
RLWE BCNS15 163 76 Key gen. 1,807,319 4,096
Encryption 2,895,648 4,224
Decryption 297,673
in this work, and for an implementation without and
with carry-less multiplication optimization, respec-
tively. As observed, a simple software optimization
as is the carry-less multiplication provides a signifi-
cant performance improvement.
7 A NOTE ON A SIDE-CHANNEL
RESISTANT
IMPLEMENTATION
When implementing a new cryptosystem there is al-
ways the challenge of finding the fastest way to com-
pute each algorithm. As we detailed in the previous
sections, the approach to implement the operations re-
quired in each algorithm could be done in different
manners. A typical technique to speed up an imple-
mentation is to remove operations under certain con-
ditions or to compute the same in a different way
depending on the inputs (i.e., by means of branch-
ing). This conditional execution is usually exploited
by side-channel attackers who try to gather informa-
tion about the inputs of operations by studying the
time difference or any other physical measurement
that may lead to some information leakage.
The fact that an implementation is weak against
some side-channel attack does not mean that the cryp-
tosystem itself is not secure. It usually means that
some performance improvements must be modified
from the implementation so that secret information
remains secure. Nevertheless, nowadays performance
is such an important property for cryptosystems that
the lack of an efficient implementation may end up
with the cryptosystem becoming not used at all and
eventually obsolete.
One alternative to protect an implementation from
side-channel attacks is by means of constant-time op-
erations. This way, the operations required by each
algorithm take the same time no matter the input and,
therefore, an attacker can only extract information
about the operations, which might be public, but not
about the inputs and outputs. The main drawback of
this approach is that the cost of the algorithms is heav-
ily increased. For this reason, we propose to modify
only a subset of operations to be constant-time, and
we analyze the information leaked to check the feasi-
bility of obtaining any knowledge of the secret key, or
the error generated during encryption, from the leaked
data.
We propose to only modify some algorithms used
for the decryption procedure in order to make them
constant time, namely: the linearized polynomial ad-
dition, the linearized polynomial multiplication and
part of the Minimal Subspace Polynomial. The first
modification is simple, we just computed the addition
for all the elements and checked the degree by iter-
ating over all the positions. For the multiplication,
in Algorithm 12 we modified a little bit the previous
Algorithm 4 to avoid conditional instructions in the
loop,. We also computed the multiplication up to the
maximum degree, not only up to the degree of the
polynomials.
Finally, the changes in MSP only affected the ini-
tial conditions to return values. In Algorithm 8 we
returned either 1 or 2 values depending if the input
subspace is 0 or not. This would leak information of
the 0s in the input subspace. To prevent that from
happening we generated the same result but we fill
the polynomial with a 0 in the second position. More
precisely, we change the return value so instead of
the return statement in Algorithm 8 line 4, we return
p = x − 0.
SECRYPT 2018 - International Conference on Security and Cryptography
72
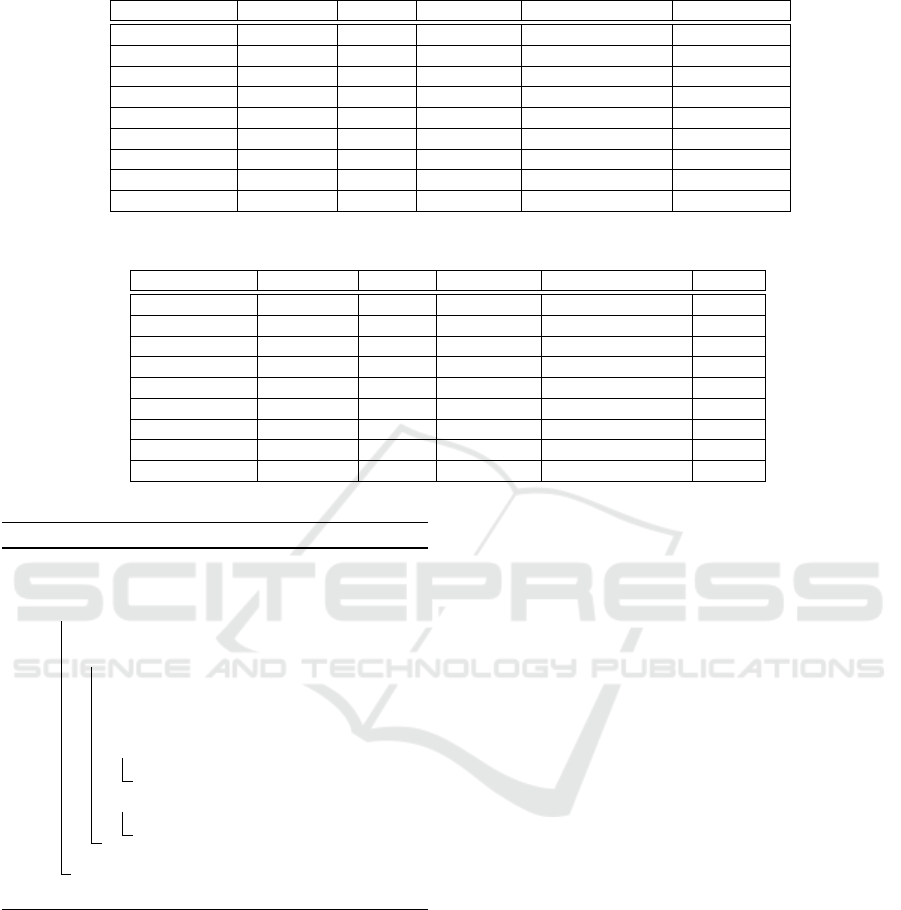
Table 3: Performance comparison for different security levels without carry-less multiplication.
Scheme Class. sec. PQ sec. operation mean CPU cycles Bytes comm.
DRANKULA 128 78 Key gen. 717,478,286 7,936
Encryption 1,167,473 504
Decryption 64,645,692
DRANKULA 192 104 Key gen. 1,405,999,903 15,120
Encryption 2,154,776 852
Decryption 131,834,096
DRANKULA 256 139 Key gen. 3,537,521,289 27,648
Encryption 3,887,225 1,152
Decryption 276,356,299
Table 4: Performance comparison for different security levels with carry-less multiplication.
Scheme Class. sec. PQ sec. operation mean CPU cycles Bytes
DRANKULA 128 78 Key gen. 159,808,905 7,936
Encryption 115,975 504
Decryption 7,761,451
DRANKULA 192 104 Key gen. 281,555,550 15,120
Encryption 209,117 852
Decryption 127,45,290
DRANKULA 256 139 Key gen. 544,649,920 27,648
Encryption 320,951 1,152
Decryption 23,559,649
Algorithm 12: Constant-Time Multiplication.
input : a,b ∈ L
2
m
[x]
≤n+1
output: c = a ◦ b ∈ L
2
m
[x]
≤n+1
1 for i from 0 to n + 1 do
2 y = 0
3 for j from 0 to i do
4 z = Frobenius(b
i− j
, j)
5 z = z · a
j
6 if j ≤ deg
2
(a) and i − j ≤ deg
2
(b)
then
7 y = y + z
8 else
9 y = y + 0
10 c
i
= y
11 return c
We have chosen only these three operations be-
cause our analysis showed that with these changes,
the decryption would not leak not enough informa-
tion to threaten the security of the cryptosystem. In-
deed, the unmodified operations are: interpolation,
rightLEEA and left / right division, which usually
take polynomials of the same degree as inputs at a
given recursion degree.
Table 5 shows the performance of our constant-
time implementation of DRANKULA for the same
three security levels that we have considered in our
work. It must be noted that our solution uses the
carry-less multiplication and, as the constant-time im-
plementation only affects the decryption, we skip the
other two operations. Results show that decryption is
heavily impacted when the countermeasures are put
in place.
The only identified cases where an attacker would
observe a timing difference are the following:
1. The interpolation polynomial ˜r is of 2-degree less
than n − 1: the attacker would be able to learn
that the point (g
n
,r
n
) is already part of the graph
of the interpolation polynomial of {(g
i
,r
i
)}
1≤i<n
.
As the attacker does not have any control on the
g
i
and neither on the r
i
s (as they are actually the
coefficients of cP where P is unknown to him), he
will not be able to extract any meaningful infor-
mation.
2. The degree controlling the number of iterations
in the loop of RightLEEA or the right division is
decreasing more than 1: the attacker would ob-
serve in the best case that the Interpolation poly-
nomial ˜r divides the MSP of the generators of the
Gabidulin code. Again, as the coefficients of ˜r are
actually depending on the coefficients of cP, then
the attacker will not gain any valuable knowledge
on the private key.
Nevertheless, a deeper analysis of the possible
leakages through timing analysis constitutes a path for
future works.
DRANKULA: A McEliece-like Rank Metric based Cryptosystem Implementation
73

Table 5: Performance comparison for different security levels of the constant-time implementation with carry-less multiplica-
tion.
Scheme Class. sec. PQ sec. operation mean CPU cycles
DRANKULA 128 78 Decryption 314,116,991
DRANKULA 192 104 Decryption 878,204,550
DRANKULA 256 139 Decryption 2,662,744,720
8 CONCLUSIONS AND FUTURE
WORK
This work is presenting a software implementation
of DRANKULA, a rank based McEliece-like cryp-
tosystem with deterministic decryption presented in
(Loidreau, 2017), and its performance results. We
address several caveats of the scheme when carry-
ing out a practical implementation, and we provide
three sets parameters targeting 64, 96 and 128 bits
of post-quantum security. In addition we provide
the pseudocode for the main subroutines of our al-
gorithms, which might be helpful to the community
to continue investigating this scheme. Results show
that DRANKULA is a viable alternative to other post-
quantum cryptography schemes and efficient in terms
of key sizes and computational complexity. We end
up providing a note on a side-channel resistant imple-
mentation of our proposal. As future work it would be
interesting to formally investigate the IND-CCA and
IND-CPA properties of DRANKULA.
REFERENCES
Aragon, N., Blazy, O., Deneuville, J.-C., Gaborit, P.,
Hauteville, A., Ruatta, O., Tillich, J.-P., and Zemor,
G. (2017). Locker - low rank parity check codes en-
cryption.
Bernstein, D. J., Buchmann, J., and Dahmen, E. (2008).
Post Quantum Cryptography. Springer Publishing
Company, Incorporated, 1st edition.
Bernstein, D. J., Chou, T., and Schwabe, P. (2015). Mcbits:
fast constant-time code-based cryptography. IACR
Cryptology ePrint Archive, 2015:610.
Bosma, W., Cannon, J., and Playoust, C. (1997). The
Magma algebra system. I. The user language. J. Sym-
bolic Comput., 24(3-4):235–265. Computational al-
gebra and number theory (London, 1993).
Chen, L., Jordan, S., Liu, Y.-K., Moody, D., Peralta, R.,
Perlner, R., and Smith-Tone, D. (2016). Report on
post-quantum cryptography.
Chou, T. (2016). Qcbits: Constant-time small-key code-
based cryptography. In Cryptographic Hardware and
Embedded Systems - CHES 2016 - 18th International
Conference, Santa Barbara, CA, USA, August 17-19,
2016, Proceedings, pages 280–300.
Chou, T. (2017). Mcbits revisited. In International Con-
ference on Cryptographic Hardware and Embedded
Systems, pages 213–231. Springer.
Deneuville, J.-C., Gaborit, P., and Z
´
emor, G. (2017).
Ouroboros: A simple, secure and efficient key ex-
change protocol based on coding theory. In Inter-
national Workshop on Post-Quantum Cryptography,
pages 18–34. Springer.
Devoret, M. H. and Schoelkopf, R. J. (2013). Supercon-
ducting circuits for quantum information: An outlook.
Science, 339(6124):1169–1174.
Gabidulin, E. M. (1985). Theory of codes with maximum
rank distance. Problems of Information Transmission
(English translation of Problemy Peredachi Informat-
sii), 21(1).
Gabidulin, E. M., Paramonov, A. V., and Tretjakov, O. V.
(1991). Ideals over a Non-Commutative Ring and
their Application in Cryptology, pages 482–489.
Gaborit, P. (2005). Shorter keys for code based cryptogra-
phy, pages 81–90.
Gaborit, P., Murat, G., Ruatta, O., and Zmor, G. (2013).
Low rank parity check codes and their application to
cryptography.
Gao, S. (2003). A New Algorithm for Decoding Reed-
Solomon Codes, pages 55–68.
Google (2018). A preview of bristlecone, googles
new quantum processor. Available at
https://research.googleblog.com/2018/03/a-preview-
of-bristlecone-googles-new.html.
Gueron, S. and Kounavis, M. E. (2010). Intel
R
carry-less
multiplication instruction and its usage for computing
the gcm mode. White Paper.
Hankerson, D., Menezes, A. J., and Vanstone, S. (2006).
Guide to elliptic curve cryptography. Springer Sci-
ence & Business Media.
Itoh, T. and Tsujii, S. (1988). A fast algorithm for com-
puting multiplicative inverses in gf (2m) using normal
bases. Information and computation, 78(3):171–177.
Karatsuba, A. and Ofman, Y. (1962). Multiplication of
many-digital numbers by automatic computers. Dok-
lady Akademii Nauk SSSR, Translation in Physics-
Doklady 7, 595-596, 1963, 145(2):293–294.
Lidl, R. and Niederreiter, H. (1997). Finite fields, volume 20
of Encyclopedia of Mathematics and its Applications.
Cambridge University Press, Cambridge, second edi-
tion.
Loidreau, P. (2017). A New Rank Metric Codes Based En-
cryption Scheme, pages 3–17.
Maples, K. (2013). Singularity of random matrices over
finite fields.
SECRYPT 2018 - International Conference on Security and Cryptography
74

McEliece, R. J. (1978). A Public-Key Cryptosystem Based
On Algebraic Coding Theory. Deep Space Network
Progress Report, 44:114–116.
Melchor, C. A., Aragon, N., Bettaieb, S., Bidoux, L.,
Blazy, O., Deneuville, J.-C., Gaborit, P., and Zmor,
G. (2016). Rank quasi-cyclic (rqc).
Misoczki, R., Tillich, J., Sendrier, N., and Barreto, P. S.
L. M. (2013). Mdpc-mceliece: New mceliece variants
from moderate density parity-check codes. In Pro-
ceedings of the 2013 IEEE International Symposium
on Information Theory, Istanbul, Turkey, July 7-12,
2013, pages 2069–2073.
Mosca, M., Stebila, D., and Contributors (2017). Open
quantum safe.
Niederreiter, H. (1986). Knapsack-type cryptosystems and
algebraic coding theory. Problems of Control and In-
formation Theory, 15:159–166.
NIST (2018). Round 1 submissions. Available
at https://csrc.nist.gov/Projects/Post-Quantum-
Cryptography/Round-1-Submissions.
Otmani, A., Kalachi, H. T., and Ndjeya, S. (2016). Im-
proved cryptanalysis of rank metric schemes based on
gabidulin codes. CoRR, abs/1602.08549.
Overbeck, R. (2005). A New Structural Attack for GPT and
Variants, pages 50–63.
Overbeck, R. (2008). Structural attacks for public-key cryp-
tosystems based on gabidulin codes. Journal of Cryp-
tology, 21(2):280–301.
Puchinger, S. and Wachter-Zeh, A. (2015). Fast opera-
tions on linearized polynomials and their applications
in coding theory. CoRR, abs/1512.06520.
Sendrier, N. (2017). Code-based cryptography: State of
the art and perspectives. IEEE Security & Privacy,
15(4):44–50.
Shor, P. W. (1997). Polynomial-time algorithms for prime
factorization and discrete logarithms on a quantum
computer. SIAM Journal on Computing, 26(5):1484–
1509.
Swan, R. G. (1962). Vector bundles and projective modules.
Transactions of the American Mathematical Society,
105(2):264–277.
Wachter-Zeh, A. (2013). Decoding of block and convolu-
tional codes in rank metric, PhD thesis.
DRANKULA: A McEliece-like Rank Metric based Cryptosystem Implementation
75
