
Toward an Understanding of Government Cloud Acceptance
A Quantitative Study of G-Cloud Acceptance by Saudi Government Agencies using
Extended UTAUT
Maha A. Al Rashed and Mutlaq B. Alotaibi
Department of Computer and Information Sciences, Al-Imam Muhammad Ibn Saud University, Riyadh, Saudi Arabia
Keywords: Cloud Computing, Government Cloud, Technology Acceptance, Unified Theory of Acceptance and Use of
Technology (UTAUT), Trust.
Abstract: With today’s rapid advances in Information and Communication Technologies (ICT), an increasing number
of governments worldwide are seeking solutions to enhance their IT infrastructures and services, and
reshape their e-government systems to meet public needs of providing easily accessible, cost-effective, high
quality, and reliable e-services. In recent years, government cloud (G-Cloud) has emerged as a new and
innovative computing paradigm with a promising opportunity for many governments to rationalize the way
they manage their services and resources. Government cloud’s potential benefits has been recognized by
many governments around the world. This paper will study the acceptance of cloud computing technologies
and services in Saudi government agencies by investigating the significant and influential factors that affect
the behavioral intentions to use G-Cloud. Moreover, in light of the rising concerns over trust issues in cloud
computing which have been reported to be one of the major barriers to the adoption of the cloud, the study
proposes an extended Unified Theory of Acceptance and Use of Technology (UTAUT) model by
incorporating trust as a key factor in the acceptance of G-Cloud.
1 INTRODUCTION
Over the last decade, the adoption of ICT solutions
in the public sector has been recognized as a
strategic tool to enable governmental reforms
(Charalabidis et al., 2010). E-government systems
and applications are now increasingly leveraging
new technological developments and this trend
seems to continue at a great pace in the future. It has
been noted that e-government initiatives are aimed
beyond providing citizens with government
information and services into providing permanent
access with transparency in government activities
and services (Kurdi et al., 2011). Furthermore, there
is a need for e-government systems to be redesigned
and revised to meet public needs and governments’
own demands. It is mainly due to the inflation of the
data in e-government systems, complexity in
operation flows, and difficulties in business
collaboration (Liang, 2012). With regard to this
issue, cloud computing has emerged at the right time
to solve these challenges by promoting economies of
scale to increase business agility and lower IT costs.
To this extent, governments are considering the real
value of incorporating the cloud into their practices
and making full use of cloud computing potentials
for higher working efficiency and better public
services (Liang, 2012). This new initiative involves
applying cloud computing model to the business
processes of e-government and building government
cloud (G-Cloud) (Zhang and Chen, 2010).
The Government of Saudi Arabia has recognized
the tremendous potentials of the cloud and accorded
it a considerable amount of attention. According to
the Communications and Information Technology
Commission (CITC), the spending on cloud services
in Saudi Arabia has been increased enormously
between 2011and 2014 by 373%. Moreover, it is
expected that cloud services market will expand at a
CAGR of 36.6% through 2019, surpassing SAR 898
million; making the cloud one of the fastest growing
segments in the Saudi ICT market (CITC, 2015).
This paper aims to study the acceptance of G-
Cloud among government agencies. Specifically, it
will examine the acceptance of cloud computing
technologies and services in Saudi government
agencies by studying the key factors that influence
the behavioral intention to use G-Cloud which, in
turn, affect the actual use.
Rashed, M. and Alotaibi, M.
Toward an Understanding of Government Cloud Acceptance - A Quantitative Study of G-Cloud Acceptance by Saudi Government Agencies using Extended UTAUT.
In Proceedings of the 6th International Conference on Cloud Computing and Services Science (CLOSER 2016) - Volume 1, pages 239-244
ISBN: 978-989-758-182-3
Copyright
c
2016 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
239

A relatively extensive amount of research has
been done to study the factors that influence
organizations’ decisions to adopt cloud computing
technologies. However, there is a limited research on
cloud adoption and usage in the context of e-
government. Moreover, as governmental operations
involve sensitive and critical data, and as cloud
computing implies risky conditions and uncertainty
about data security and safety due to the lack of
control and confidence in entrusting sensitive
information to cloud service providers, trust has
been reported to be a major concern (Kanwal et al.,
2013). Indeed, scholars agree that lack of users’ trust
is a key inhibitor to the adoption of cloud services
especially in domains where confidential and
sensitive information is involved (Ko, Lee and
Pearson, 2011). To the best of our knowledge there
is limited research on the acceptance of government
cloud, and no studies have considered trust as a key
factor when investigating G-Cloud acceptance
among government agencies. While the focal point
of the majority of studies in the relevant literature
was on the benefits and concerns of G-Cloud, other
studies focused on finding approaches and models to
build trust in the cloud. This issue presents a gap in
the research field which this study is addressing by
proposing an extended UTAUT model to account for
trust as a main construct.
2 LITERATURE REVIEW
2.1 Government Cloud Computing
Government Cloud (G-Cloud) is an emerging
paradigm, in which cloud computing is utilized to
redesign the business processes of e-government
system for allocation, management, distribution and
maintenance of IT resources of governments via the
internet (Liang, 2012). It has revolutionized how
governments operate; governments are leveraging
the cloud for its flexibility, scalability, accessibility,
elasticity, and substantial cost savings. Thus, this
innovative step of moving to the cloud can lead to
improved government transparency, accountability,
and service value (Zhang and Chen, 2010).
The G-Cloud model can help governments to
dramatically cut costs associated with large and
expensive IT infrastructures required to support
government agencies’ work. It also reduces the
burden of IT administration, maintenance, and
upgrades as it shifts to cloud providers (Khan et al.,
2011). G-Cloud provides government organizations
with greater ability to focus on core business and
mission-critical processes and outsource non-critical
applications to service providers (Wyld, 2010).
Moreover, it supports resource and information
sharing and business collaboration among different
departments and agencies within the government
which has been perceived as one of the biggest
benefits of moving to the cloud (Wyld, 2009).
The cloud movements in the public sector are
spreading all around the world; the literature
highlights many early government cloud computing
initiatives that have been undertaken by
governments in a number of worldwide countries.
The USA, UK, Thailand, China, New Zealand and
Germany have introduced and used cloud computing
in the public sector, and realized budget reductions
and high-efficiency green IT implementation (Shen,
Yang and Keskin, 2012). Australia, Singapore, and
Japan are among the most active countries for
government-led implementation of the cloud model.
These countries are leveraging cloud computing as a
solution for e-government efficiency, business
innovation, IT development, and cost reduction
(Seo, Min and Lee 2014).
2.2 The Unified Theory of Acceptance
and use of Technology (UTAUT)
Several models and theories have been developed
and surfaced over the last three decades to help
explain users’ acceptance and use of IT. Such
models include the Theory of Reasoned Action
(TRA), the Theory of Planned Behavior (TPB), the
Technology Acceptance Model (TAM), and the
Diffusion of Innovation (DOI). Central to this study
is the Unified Theory of Acceptance and Use of
Technology (UTAUT), a comprehensive and widely
accepted framework that had been formulated by
Venkatesh et al. (2003) by integrating the findings
of eight prominent technology acceptance models. It
addresses the limitations and shortcomings identified
in previous models by combining determinants from
various acceptance theories, and thereby providing
superior advantage. Venkatesh et al. (2003) argued
that this model is able to explain variance in IT
behavioral intention and usage behavior better than
the previous ones. The theory holds that four key
constructs: performance expectancy, effort
expectancy, social influence, and facilitating
conditions are direct determinants of usage intention
and behavior; along with four moderating variables
of gender, age, experience, and voluntariness of use
are posited to moderate the impact of the core
constructs on use intention and behavior (Venkatesh
et al., 2003). The UTAUT model validity, reliability
CLOSER 2016 - 6th International Conference on Cloud Computing and Services Science
240

and comprehensiveness in technology adoption have
been tested and proven on large real world data sets
in various contexts (Im, Hong and Kang, 2011). It
has been featured prominently in studies concerning
IT acceptance such as cloud based e-government
services (Lian, 2015). Accordingly and given the
robust theoretical background of this model and its
suitability for the context of the study, this study
adopt UTAUT as the primary theoretical framework
to examine users’ acceptance of G-Cloud.
2.3 Trust as an Extension to the
UTAUT Model
As cloud computing involves third parties storing
and processing sensitive data, and it requires
individuals and organizations to transfer some or all
control of their data and computing resources to
cloud service providers, trust-related concerns arise
(Khan and Malluhi, 2010). Indeed, trust is widely
perceived as a key concern for cloud consumers,
whether they are end users or organizations; they are
worried about who have access to their data and how
it will be shared and used (Pearson, 2013). It has
been reported that the fear of loss of control over
data is a major inhibitor to the adoption of the cloud
in Saudi Arabia (CITC, 2015). However, according
to CITC, as Saudi organizations develop trusting
relationships with their service providers, this will
boost adoption and usage.
Scholars from various research disciplines
believe that trust is crucial in enabling relations and
exchanges that involve uncertainty, interdependence,
or fear of opportunism (Bradach and Eccles, 1989).
That is, it is most needed in risky situations (Kim,
Ferrin and Rao, 2008). Mayer, Davis and
Schoorman (1995) define trust as “the willingness of
a party to be vulnerable to the actions of another
party”. Consistent with this conceptualization of
trust and related literature, this study defines trust as
the user’s willingness to accept vulnerability based
on his/her beliefs and positive expectations that the
cloud provider will perform fairly and reasonably as
expected, and that using the cloud will result in
positive outcomes due to the provider’s integrity and
competences.
Scholars believe that the adoption of IT can
involve high levels of uncertainty, especially when
challenged with the emergence of a new technology
(Kirs and Bagchi, 2012). Therewith, trust has been
recognized as a key driver for adoption due to its
relevance to deal with uncertainty and the risk of
vulnerability which are present mostly in online
contexts (Gefen, Karahanna and Straub, 2003). The
abstract and distributed nature of the cloud
technology besides the associated uncertainty pose a
considerable obstacle for the acceptance of cloud
based solutions (Martucci et al., 2012). Thus, this
study has expanded upon the UTAUT model by
incorporating trust as a key factor to better
comprehend the acceptance of G-Cloud.
Extant research that has examined trust in online
environments with respect to consumer–vendor
relationships has suggested a generic model of trust
that, in essence, concerns two targets: the entity or
vendor providing the online service and the
technology itself through which the service is
provided (Schaupp, Carter and McBride, 2010).
Pavlou (2003) argued that when consumers willingly
become vulnerable to online vendors, they consider
both the characteristics of the e-vendors due to
behavioral uncertainty, as well the characteristics of
the related technology due to environmental
uncertainty. Consistent with related scholarly
research, this study defines trust in terms of trust in
Cloud Service Providers (CSPs) as well as trust in
the reliability and integrity of the cloud technology.
In that sense, trust in government cloud can be
viewed as the user’s confidence in using the cloud,
and that the CSPs will fulfill obligations set forth in
an exchange. This conceptualization of trust implies
that users must have a certain level of confidence in
that cloud providers will behave capably
(competence), fairly (benevolence), and ethically
(integrity) (Adjei, 2015). These three dominantly
cited beliefs have been identified as key
characteristics for assessing trustees’ trustworthiness
(Burda and Teuteberg, 2014).
3 RESEARCH MODEL AND
HYPOTHESES
3.1 Research Model
As previous research has proved the validity of the
UTAUT framework in explaining a wide range of IT
acceptance and usage behavior, this study adopt the
UTAUT as the baseline model. However, in this
study, G-Cloud is a specific context that calls for
additional variables to extend the original UTAUT
to better explain variances. Thus, the study proposes
a modified UTAUT model that incorporates other
constructs for a better explanation of G-Cloud
acceptance. Figure 1 shows the research model and
associated hypotheses investigated under this study.
Toward an Understanding of Government Cloud Acceptance - A Quantitative Study of G-Cloud Acceptance by Saudi Government Agencies
using Extended UTAUT
241
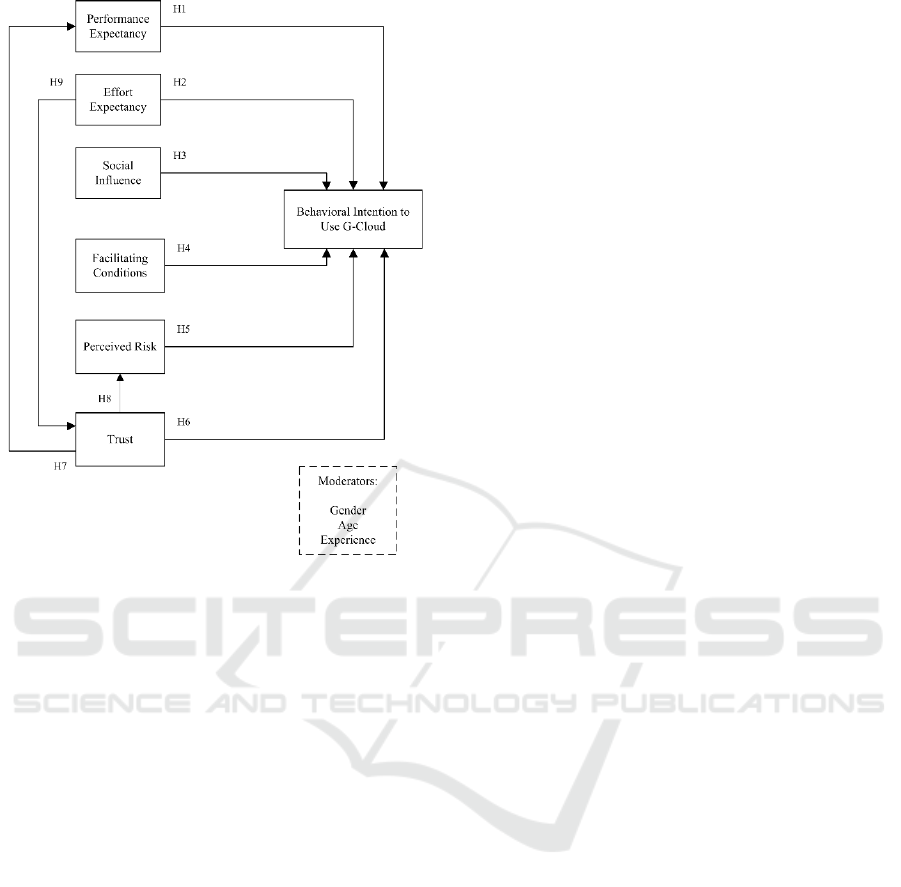
Figure 1: Research Model.
3.2 Hypothesis Development
Performance expectancy (PE) has been constantly
found to be a significant predictor, if not the
strongest predictor, of intention to use IT (Venkatesh
et al., 2003). That is, users who perceive the
usefulness of a particular technology will be more
likely to adopt it. Prior cloud adoption studies have
shown the direct and positive effect of perceptions
of usefulness on the behavioral intention toward
using the cloud (Opitz et al., 2012). It has been
argued that increasing the awareness of users
towards the usefulness of using cloud services is
most likely to increase the acceptance of such
technology (Alharbi, 2012). Therefore, this study
has hypothesized that:
H1: Performance expectancy has a significant
positive effect on the behavioral intention to use G-
Cloud.
Effort expectancy (EE) refers to “the degree of
ease associated with the use of the system”
(Venkatesh et al., 2003). A system that is perceived
to be easier to use is more likely to induce the
behavioral intention of usage. Lian (2015) has found
that effort expectancy significantly affects user’s
behavioral intention toward using a cloud-based e-
government service. Opitz et al. (2012), in their
study on the acceptance of cloud computing by CIOs
and IT managers, have found that both perceptions
of usefulness and ease of use explained 66.4 % of
the variance in the behavioral intention to use cloud
based services. Thus, it is hypothesized that:
H2: Effort expectancy has a significant positive
effect on the behavioral intention to use G-Cloud.
Social influence (SI), in this study, revolved
around users’ beliefs that the behavior (using G-
Cloud services) is accepted, encouraged, and
promoted by their circle of influencers which in turn
tends to affect their behavioral intentions. The effect
of SI on intention to use technology has been shown
to be significant in several previous adoption
studies. Park and Ryoo (2013) have validated the
significant role of SI on users’ intention to use cloud
computing services. Alotaibi (2014) has pointed out
on the need to investigate the effect of social
influence on the intention to use the cloud in Saudi
Arabia as Saudis rely heavily on social models to
make decisions. Therefore, it is hypothesized that:
H3: Social influence has a significant positive
effect on the behavioral intention to use G-Cloud.
Consistent with Venkatesh et al. (2003)
definition, facilitating conditions (FC) refers to the
degree to which users believe that organizational as
well technical infrastructure supports the use of
government cloud and removes barriers to adoption.
The influence of facilitating conditions on IT usage
behavior has been investigated and validated in
several prior adoption studies. AlAwadhi and Morris
(2008) believe that the use of a new system is
expected to increase as users find support in using
the system. Lian (2015) argues that since cloud
based e-government services are relatively new and
innovative, unfamiliarity may hinder usage. Hence,
according to Lian (2015), the better the facilitating
conditions, the more likely people will be to use the
service. Thus, it has hypothesized that:
H4: Facilitating conditions has a significant
positive effect on the behavioral intention to use G-
Cloud.
In light of the inherent risks and uncertainties
surrounding the cloud environment, it is expected
that perceived risk would affect users’ intentions to
use cloud services. This study defines perceived risk
(PR) as the user’s belief of the potential and
uncertain negative outcomes of using the cloud. This
definition covers both forms of PR, behavioral and
environmental uncertainty, that have been identified
in the literature (Pavlou, 2003). According to
Pavlou, (2003), both behavioral and environmental
uncertainty involve privacy risks. In cloud
computing environment, scholars argue that the
cloud raises risks of security and privacy (Chi, Yeh
CLOSER 2016 - 6th International Conference on Cloud Computing and Services Science
242

and Hung, 2012). CITC has suggested that Saudi
organizations are generally reluctant to risks of data
security and privacy which are considered major
concerns and inhibitors to cloud services adoption
(CITC, 2015). Chi, Yeh and Hung (2012), in their
study of the effect of perceived risk on intentions to
use cloud services, has found that perceived risk
significantly and negatively affects usage intentions.
Therefore, it is hypothesized that:
H5: Perceived risk has a significant negative
effect on the behavioral intention to use G-Cloud.
The role of trust on IT adoption has been
investigated in many prior studies that consistently
found trust to exert a positive and direct effect on
behavioral intentions (Burda and Teuteberg, 2014;
Wu and Chen, 2005). Previous cloud adoption
studies have recognized trust to be a key predictor of
behavioral intention to use cloud services (Wu, Lan
and Lee, 2013). Thus, it is hypothesized that:
H6: Trust in G-Cloud has a significant positive
effect on the behavioral intention to use G-Cloud.
Prior empirical adoption studies have shown that
trust exerts an indirect influence on intention to use
via perceived usefulness and perceived risk. Gefen,
Karahanna and Straub (2003) argued that when
consumers initially trust e-vendors and believe that
adopting an online service is beneficial to their job
performance and productivity, they will perceive the
online service as useful. Burda and Teuteberg (2014)
have recognized trust to be a major determinant of
cloud adoption decisions that significantly reduces
perceived risk on the one hand, and increases
usefulness perceptions of cloud services on the other
hand. Kim, Ferrin and Rao (2008) have shown that a
consumer’s trust has a strong negative influence on
perceived risk; that is as trust increases, consumers
are likely to perceive less risk than if trust were
absent. Drawing from these findings, this study has
hypothesized that:
H7: Trust in G-Cloud has a significant positive
effect on performance expectancy.
H8: Trust in G-Cloud has a significant negative
effect on perceived risk.
Extant research has suggested that perceived
ease of use (PEOU) has a positive effect on trust
since it helps promoting consumers’ favorable
impressions on the e-vendor in the initial adoption of
an online service (Wu and Chen, 2005). This
argument is supported by the cognition-based trust
which is built upon first feelings and impressions
toward a certain behavior rather than through
experiences, which is relevant to the initial stages of
adoption (Gefen, Karahanna and Straub, 2003). Wu
and Chen (2005) provided empirical evidence that
PEOU influences trust and explains 19% of the
variance in trust. Thus, it is hypothesized that:
H9: Effort expectancy has a significant positive
effect on trust in G-Cloud.
4 CONCLUSIONS
Today, governments, due to the complexity of their
processes and massive data records and the need for
a powerful infrastructure, are almost obligated to
turn to new technological innovations to provide
better public information and services with lower IT
costs. Therefore, many government organizations
tend to exploit advanced technology trends such as
government cloud. Despite the appealing benefits of
the cloud, the adoption of such technology raises
various challenges including trust that has been
reported as one of the major barriers to the
widespread growth and uptake of the cloud. This
paper, as an attempt to address the gap in the
literature, proposes an extended UTAUT model that
accounts for trust as a key construct to investigate
the acceptance of G-Cloud by government agencies
in Saudi Arabia. Approaching this issue would be an
added value to the literature of e-government
practices, as well the literature of cloud computing.
Furthermore, understanding the factors affecting G-
Cloud acceptance through validated theoretical
foundation, is critical for effective and successful
implementation of this technology. As a matter of
fact, the understanding of these factors is useful to
both cloud computing adopters and providers.
REFERENCES
Adjei, J. K. (2015) ‘Explaining the role of trust in cloud
computing services’, info, 17(1), pp. 54-67.
AlAwadhi, S. and Morris, A. (2008) ‘The Use of the
UTAUT Model in the Adoption of E-government
Services in Kuwait’, in Hawaii International
Conference on System Sciences, Proceedings of the
41st Annual, Waikoloa, HI, pp. 219-219.
Alharbi, S. T. (2012) ‘Users’ acceptance of cloud computing
in Saudi Arabia: an extension of technology acceptance
model’, International Journal of Cloud Applications and
Computing (IJCAC), 2(2), pp. 1-11.
Alotaibi, M. B. (2014) ‘Exploring Users’ Attitudes and
Intentions toward the Adoption of Cloud Computing
in Saudi Arabia: An Empirical Investigation’, Journal
of Computer Science, 10(11), pp. 2315-2329.
Bradach, J. L. and Eccles, R. G. (1989) ‘Price, authority,
and trust: From ideal types to plural forms’, Annual
review of sociology, 15, pp. 97-118.
Toward an Understanding of Government Cloud Acceptance - A Quantitative Study of G-Cloud Acceptance by Saudi Government Agencies
using Extended UTAUT
243

Burda, D. and Teuteberg, F. (2014) ‘The role of trust and
risk perceptions in cloud archiving-Results from an
empirical study’, The Journal of High Technology
Management Research, 25(2), pp. 172-187.
Charalabidis, Y., Markaki, O., Lampathaki, F., Mantzakou, I.
and Sarantis, D. (2010) ‘Towards a scientific approach to
e-government research’, in tGov Workshop.
Chi, H., Yeh, H. and Hung, W. C. (2012) ‘The moderating
effect of subjective norm on cloud computing users’
perceived risk and usage intention’, International
Journal of Marketing Studies, 4(6), pp. 95.
Communications and Information Technology
Commission (CITC) (2015) ‘ICT Report’.
Gefen, D., Karahanna, E. and Straub, D. W. (2003) ‘Trust
and TAM in online shopping: An integrated model’,
MIS quarterly, vol. 27(1) pp. 51-90.
Im, I., Hong, S. and Kang, M. S. (2011) ‘An international
comparison of technology adoption: Testing the UTAUT
model’, Information & Management, 48(1), pp. 1-8.
Kanwal, A., Masood, R., Ghazia, U. E., Shibli, M. A. and
Abbasi, A. G. (2013) ‘Assessment Criteria for Trust
Models in Cloud Computing’, in Green Computing
and Communications (GreenCom), 2013 IEEE and
Internet of Things (iThings/CPSCom), IEEE
International Conference on and IEEE Cyber, Physical
and Social Computing, Beijing, pp. 254-261.
Khan, F., Zhang, B., Khan, S. and Chen, S. (2011)
‘Technological leap frogging e-government through
cloud computing’, in Broadband Network and
Multimedia Technology (IC-BNMT), 2011 4th IEEE
International Conference, Shenzhen, pp. 201-206.
Khan, K. M. and Malluhi, Q. (2010) ‘Establishing trust in
cloud computing’, IT professional, 12(5), pp. 20-27.
Kim, D. J., Ferrin, D. L. and Rao, H. R. (2008) ‘A trust-based
consumer decision-making model in electronic commerce:
The role of trust, perceived risk, and their antecedents’,
Decision support systems, 44(2), pp. 544-564.
Kirs, P. and Bagchi, K. (2012) ‘The impact of trust and
changes in trust: A national comparison of individual
adoptions of information and communication
technologies and related phenomenon’, International
Journal of Information Management, 32(5), pp. 431-441.
Ko, R. K., Lee, B. S. and Pearson, S. (2011) ‘Towards
achieving accountability, auditability and trust in cloud
computing’, in Advances in Computing and
Communications, Springer Berlin Heidelberg, pp. 432-444.
Kurdi, R., Taleb-Bendiab, A., Randles, M. and Taylor, M.
(2011) ‘E-Government Information Systems and
Cloud Computing (Readiness and Analysis)’, in
Developments in E-systems Engineering (DeSE),
2011, Dubai, pp. 404-409.
Lian, J. W. (2015) ‘Critical factors for cloud based e-
invoice service adoption in Taiwan: An empirical
study’, International Journal of Information
Management, 35(1), pp. 98-109.
Liang, J. (2012) ‘Government Cloud: Enhancing
Efficiency of E-Government and Providing Better
Public Services’, in Service Sciences (IJCSS), 2012
International Joint Conference, pp. 261-265.
Martucci, L., Zuccato, A., Smeets, B., Habib, S. M.,
Johansson, T. and Shahmehri, N. (2012) ‘Privacy,
security and trust in cloud computing: The perspective
of the telecommunication industry’, in Ubiquitous
Intelligence & Computing and 9th International
Conference on Autonomic & Trusted Computing
(UIC/ATC), 2012 9th International Conference on,
Fukuoka, pp. 627-632.
Mayer, R. C., Davis, J. H. and Schoorman, F. D. (1995)
‘An integrative model of organizational trust’,
Academy of Management Review, 20(3), pp. 709-734.
Opitz, N., Langkau, T. F., Schmidt, N. H. and Kolbe, L. M.
(2012) ‘Technology acceptance of cloud computing:
empirical evidence from German IT departments’, in
System Science (HICSS), 2012 45th Hawaii International
Conference on IEEE, Maui, HI, pp. 1593-1602.
Park, S. C. and Ryoo, S. Y. (2013) ‘An empirical
investigation of end-users’ switching toward cloud
computing: A two factor theory perspective’,
Computers in Human Behavior, 29(1), pp. 160-170.
Pavlou, P. A. (2003) ‘Consumer acceptance of electronic
commerce: Integrating trust and risk with the
technology acceptance model’, International journal
of electronic commerce, 7(3), pp. 101-134.
Pearson, S. (2013) ‘Privacy, security and trust in cloud
computing’, in Privacy and Security for Cloud
Computing, Springer London, pp. 3-42.
Schaupp, L. C., Carter, L. and McBride, M. E. (2010) ‘E-
file adoption: A study of US taxpayers’ intentions’,
Computers in Human Behavior, 26(4), pp. 636-644.
Seo, J. H., Min, J. S. and Lee, H. (2014) ‘Implementation
Strategy for a Public Service Based on Cloud Computing
at the Government’, International Journal of Software
Engineering & Its Applications, 8(9), pp. 207-220.
Shen, Y., Yang, J. and Keskin, T. (2012) ‘The evolution of
IT towards cloud computing in China and US’, in
Computational Problem-Solving (ICCP), 2012
International Conference on, Leshan, pp. 224-235.
Venkatesh, V., Morris, M. G., Davis, G. B. and Davis, F.
D. (2003) ‘User acceptance of information technology:
Toward a unified view’, MIS Quarterly, 27(3), pp.
425-478.
Wu, L. and Chen, J. L. (2005) ‘An extension of trust and
TAM model with TPB in the initial adoption of on-
line tax: an empirical study’, International Journal of
Human-Computer Studies, 62(6), pp. 784-808.
Wu, W. W., Lan, L. W. and Lee, Y. T. (2013) ‘Factors
hindering acceptance of using cloud services in
university: a case study’, The Electronic Library,
31(1), pp. 84-98.
Wyld, D. C. (2009) ‘Moving to the cloud: An introduction
to cloud computing in government’, IBM Center for
the Business of Government.
Wyld, D. C. (2010) ‘Risk in the clouds?: Security issues
facing government use of cloud computing’,
Innovations in Computing Sciences and Software
Engineering, pp. 7-12.
Zhang, W. and Chen, Q. (2010) ‘From E-government to
C-government via cloud computing’, in E-Business
and E-Government (ICEE), 2010 International
Conference, pp. 679-682.
CLOSER 2016 - 6th International Conference on Cloud Computing and Services Science
244
