
Cloud Provider Transparency
A View from Cloud Customers
Daniela S.
Cruzes and Martin Gilje Jaatun
SINTEF – ICT, Postboks 4760 Sluppen, 7465 Trondheim, Norway
Keywords: Cloud, Provider, Customer, Security, Privacy, Accountability, Transparency.
Abstract: A major feature of public cloud services is that data are processed remotely in unknown systems that the users
do not own or operate. This context creates a number of challenges related to data privacy and security and
may hinder the adoption of cloud technology. One of these challenges is how to maintain transparency of the
processes and procedures while at the same time providing services that are secure and cost effective. This
paper presents results from an empirical study in which the cloud customers identified a number of
transparency requirements to the adoption of cloud providers. We have compared our results with previous
studies, and have found that in general, customers are in synchrony with research criteria for cloud service
provider transparency, but there are also some extra pieces of information that customers are looking for.
1 INTRODUCTION
Cloud computing, which allows for highly scalable
computing and storage, is increasing in importance
throughout information technology (IT). Cloud
computing providers offer a variety of services to
individuals, companies, and government agencies,
with users employing cloud computing for storing
and sharing information, database management and
mining, and deploying web services, which can range
from processing vast datasets for complicated
scientific problems to using clouds to manage and
provide access to medical records (Paquette, 2010).
Several existing studies emphasize the way
technology plays a role in the adoption of cloud
services, and most of these studies conclude that the
most important challenges are related to security,
privacy and compliance (Kuo, 2011), (Gavrilov and
Trajkovik, 2012), (AbuKhousa et al., 2012),
Rodrigues et al. 2013), (Ahuja et al. 2012). Cloud
service users may hand over valuable and sensitive
information to cloud service providers without an
awareness of what they are committing to or
understanding of the risks, with no control over what
the service does with the data, no knowledge of the
potential consequences, or means for redress in the
event of a problem.
In the European A4Cloud research project
(http://a4cloud.eu), our focus is on accountability as
the most critical prerequisite for effective governance
and control of corporate and private data processed by
cloud-based IT services. We want to make it possible
to hold cloud service providers accountable for how
they manage personal, sensitive and confidential
information in the cloud, and for how they deliver
services. This will be achieved by an orchestrated set
of mechanisms: preventive (mitigating risk),
detective (monitoring and identifying risk and policy
violation) and corrective (managing incidents and
providing redress). Used individually or collectively,
they will make the cloud services in the short- and
longer-term more transparent and trustworthy for:
• users of cloud services who are currently not
convinced by the balance of risk against
opportunity
• their customers, especially end-users who do not
understand the need to control access to
personal information
• suppliers within the cloud eco-system, who need
to be able to differentiate themselves in the
ultimate commodity market.
In this paper we report on the results of an
elicitation activity related to transparency
requirements from the perspective of cloud
customers. A Cloud Customer in our context is an
entity that (a) maintains a business relationship with,
and (b) uses services from a Cloud Provider;
correspondingly, a Cloud Provider is an entity
responsible for making a [cloud] service available to
Cloud Customers.
Transparency is the property of an accountable
system that is capable of ‘giving account’ of, or
30
Cruzes D. and Jaatun M..
Cloud Provider Transparency - A View from Cloud Customers.
DOI: 10.5220/0005439000300039
In Proceedings of the 5th International Conference on Cloud Computing and Services Science (CLOSER-2015), pages 30-39
ISBN: 978-989-758-104-5
Copyright
c
2015 SCITEPRESS (Science and Technology Publications, Lda.)
providing visibility of, how it conforms to its
governing rules and commitments (Felici et. al,
2013). Transparency involves operating in such a way
as to maximize the amount of and ease-of-access to
information which may be obtained about the
structure and behavior of a system or process. An
accountable organization is transparent in the sense
that it makes the policies on treatment of personal and
confidential data known to relevant stakeholders, can
demonstrate how these are implemented, provides
appropriate notifications in case of policy violation,
and responds adequately to data subject access
requests. In an ideal scenario, the user knows the
information requirements and is able to communicate
that clearly to the provider, and in return, the provider
is transparent and thus willing to address the
regulatory and legislative obligations required with
regard to the assets.
The rest of the paper is organized as follows.
Section 2 presents some background from the
literature. Section 3 explains the methodology that we
used to elicit the views of the stakeholders. In section
4 we present the results, and in section 5 we discuss
our findings compared to related work. We draw our
conclusions in section 6.
2 RELATED WORK
Transparency is closely connected to trust (Yang and
Tate, 2012). Onwubiko (2010) affirms that trust is a
major issue with cloud computing irrespective of the
cloud model being deployed. He says that cloud users
must be open-minded and must not whole-heartedly
trust a provider just because of the written-down
service offerings without carrying out appropriate due
diligence on the provider; where certain policies are
not explicit, users should ensure that missing policies
are included in the service contract. By understanding
the different trust boundaries, each cloud computing
model assists users when making decision as to which
cloud model they can adopt or deploy.
Khorshed et al. highlight the gaps between cloud
customers' expectations and the actually delivered
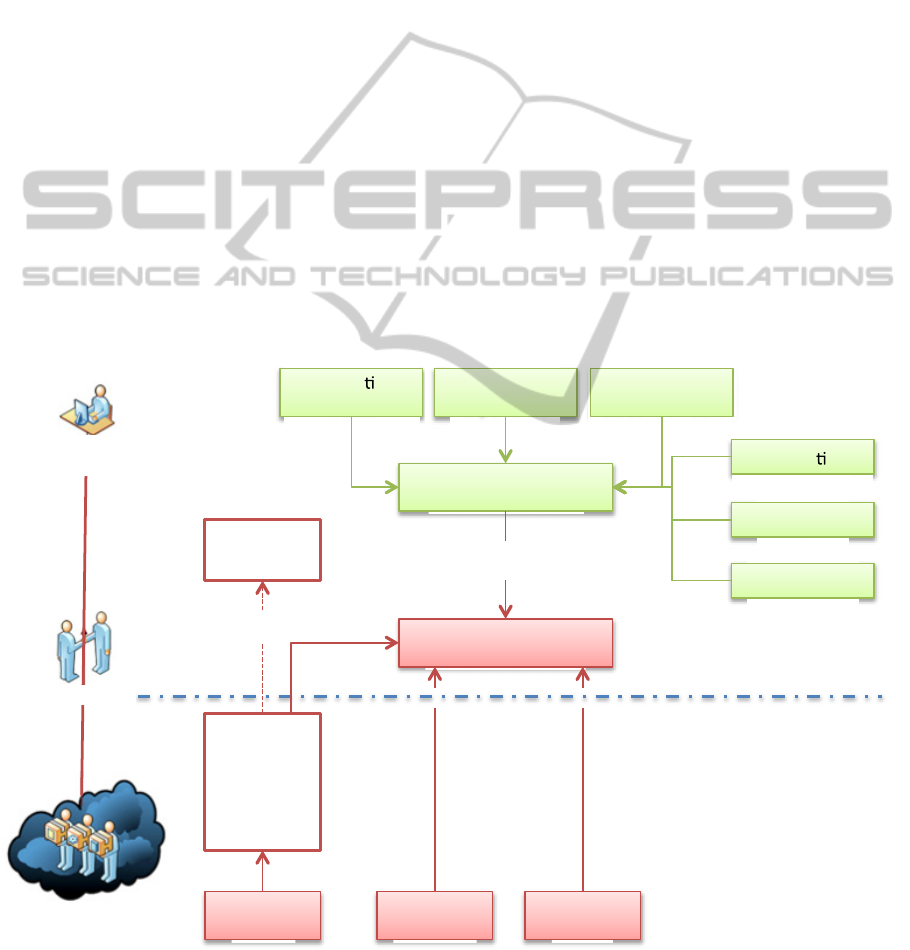
services, as shown in Figure 1 (Khorshed et al., 2012).
They affirm that cloud customers may form their
expectations based on their past experiences and
organizations’ needs. They are likely to conduct some
sort of survey before choosing a cloud service
provider similar to what people do before choosing an
Internet Service Provider (ISP). Customers are
Figure 1: Understanding Cloud Computing Gaps adapted from Khorshed et al. (2012).
Organiza ons’
Needs
Past
Experience
Survey
on
Cloud
Providers
Expected
Service
Confiden ality
Integrity
Availability
I
will
trust
you,
if
you
are
Transparent
Perceived
Service
GAP
You
need
to
trust
me
on
every
level.
My
company
policy
won’t
allow
me
to
be
100%
Transparent
Trust
Threats
Risks
GAP
Agreement
Cloud
Customer
Cloud
Service
Provider
CloudProviderTransparency-AViewfromCloudCustomers
31
expected to also establish to what extent providers
satisfy confidentiality, integrity and availability
requirements. On the other hand, cloud service
providers may promise a lot to entice a customer to
sign a deal, but harsh reality is frequently
accompanied by insurmountable barriers to keeping
some of their promises. Many potential cloud
customers are well aware of this, and are
consequentially still sitting on the sidelines. They will
not venture into cloud computing unless they get a
clear indication that all gaps are within acceptable
limits.
Durkee (2010) says that transparency is one of the
first steps to developing trust in a relationship, and
that the end customer must have a quantitative model
of the cloud’s behavior. The cloud provider must
provide details, under NDA if necessary, of the inner
workings of their cloud architecture as part of
developing a closer relationship with the customer.
Durkee also says that this transparency can only be
achieved if the billing models for the cloud clearly
communicate the value (and avoided costs) of using
the service. To achieve such clarity, the cloud vendor
has to be able to measure the true cost of computing
operations that the customer executes and bill for
them.
Pauley (2010) proposed an instrument for
evaluating the transparency of a cloud provider. It is
the only empirical evaluation that we found that
focuses on transparency in the cloud as a subject of
study. The study aims to help businesses assess the
transparency of a cloud provider’s security, privacy,
auditability, and service-level agreements the
Table 1: Pauley’s Cloud Provider Transparency Scorecard.
Aspect
Criteria Mentioned in
Interviews?
Business
factors
1. Length in years in business > 5?
2. Published security or privacy breaches?
3. Published outages?
4. Published data loss?
5. Similar customers?
6. Member of ENISA, CSA, CloudAudit, OCCI, or other
cloud standards groups?
7. Profitable or public?
No
Yes
Yes
Yes
Yes
No
No
Security 8. Portal area for security information?
9. Published security policy?
10. White paper on security standards?
11. Does the policy specifically address multi-
tenancy issues?
12. Email or online chat for questions?
13. ISO/IEC 27000 certified?
14. COBIT, NIST SP800-53 security certified?
15. Offer security professional services (assessment)?
16. Employees CISSP, CISM, or other security certified?
Yes
Yes
Yes
Yes
No
Partially
Partially
No
Partially
Privacy 17. Portal area for privacy information?
18. Published privacy policy?
19. White paper on privacy standards?
20. Email or online chat for questions?
21. Offer privacy professional services (assessment)?
22. Employees CIPP or other privacy certified?
Yes
Yes
Yes
No
No
Partially
External
audits or
certifications
23. SAS 70 Type II
24. PCI-DSS
25. SOX
26. HIPAA
No
No
No
No
Service-level
agreements
27. Does it offer an SLA?
28. Does the SLA apply to all services
29. ITIL-certified employees?
30. Publish outage and remediation?
Yes
No
No
Yes
CLOSER2015-5thInternationalConferenceonCloudComputingandServicesScience
32

the transparency of a cloud provider’s security,
privacy, auditability, and service-level agreements
via self-service Web portals and publications. Pauley
designed a scorecard (Table 1) to cover the
assessment areas frequently raised in his research,
and to begin to establish high-level criteria for
assessing provider transparency. He concludes that
further research is needed to determine the standard
for measuring provider transparency. In our research
we used a different strategy than Pauley; we have
interviewed customers of cloud services to see what
kind of information they would like to get from the
cloud providers.
3 METHODOLOGY
As part of the project, we were responsible for
running a set of stakeholder workshops for eliciting
requirements for accountability tools. In total, our
elicitation effort has involved more than 300
stakeholders, resulting in 149 stakeholder
requirements. The first workshop dealt with eliciting
initial accountability requirements, serving as a
reality-check on the three selected business use cases
we had constructed (Bernsmed et al., 2014). The
second workshop dealt with risk perception. The aim
was to focus on the notion of risk and trust assessment
of cloud services, future Internet services and
dynamic combinations of such services (mashups).
After the first two workshops, we decided to organize
multiple smaller, local workshops on each theme to
ease participation of cloud customers and end users.
The third set of workshops presented stakeholders
with accountability mechanisms to gather their
operational experiences and expectations about
accountability in the cloud.
Of particular importance to this study was the risk
workshop, where 15 tentative requirements related to
transparency where identified. This workshop
comprised 20 international stakeholders from the
manufacturing industry, telecom, service providers,
banking industry and academia, and the tentative
transparency requirements were subsequently
presented to our interviewees as a starting point for
the discussion.
In addition to the stakeholder requirements, we
have devised a set of high-level requirements which,
from an organizational perspective, set out what it
takes to be an accountable cloud provider (Jaatun et
al., 2014). These requirements intend to supplement
the requirements elicitation process by providing a set
of high-level "guiding light" requirements,
formulated as requirements that accountable
organizations should meet. In short, these
requirements state that an accountable organization
that processes personal and/or business confidential
data must 1) demonstrate willingness and capacity to
be responsible and answerable for its data practices 2)
define policies regarding their data practices, 3)
monitor their data practices, 4) correct policy
violations, and 5) demonstrate policy compliance.
From these activities we have created a repository
with requirements from all elicitation workshops, the
guiding lights requirements as well as a number of
more technical requirements that have originating
from the conceptual work and technical packages in
the project. These have been classified in terms of
whether they are functional requirements, which are
directly related to the actors involved in the cloud
service delivery chain, or requirements for
accountability mechanisms, which are related to the
tools and technologies that are being developed in the
project.
For refining and confirming the elicited
requirements of transparency, we have performed an
interview study with eight interviewees, followed by
an in-depth analysis of the collected information.
Invitations were sent to our list of contacts in
Norwegian software companies. Participation was
voluntary. Eight people accepted to participate in the
interviews. The participants were all IT security
experts working with cloud related projects. The
participants represented six different organizations: a
consultancy, 2 cloud service providers (1 public, 1
private), an application service provider, a
distribution service provider, and a tertiary education
institution.
The interviews were performed on Skype and
lasted about one hour. The main questions of the
interview were:
1. What is the most important information you
think should be provided to the cloud customer
when buying services from cloud service
providers?
2. In which parts would you like to be involved
in making the decisions? In which parts would
you like just to be informed of the decisions?
3. What would increase your trust that the data is
secure in this scenario?
4. What do you want to know about how the
provider corrects data security problems?
The eight interviews for this study were
transcribed into text documents based on the audio
recordings. For further analysis of the transcription,
we followed the Thematic Synthesis recommended
steps proposed by Cruzes and Dybå (2011). Thematic
synthesis is a method for identifying, analyzing, and
CloudProviderTransparency-AViewfromCloudCustomers
33

reporting patterns (themes) within data. It comprises
the identification of the main, recurrent or most
important (based on the specific question being
answered or the theoretical position of the reviewer)
issues or themes arising from a body of evidence. The
level of sophistication achieved by this method can
vary; ranging from simple description of all the
themes identified, through to analyses of how the
different themes relate to one another in a conceptual
map. Five steps were performed in this research:
initial reading of data/text (extraction), identification
of specific segments of text, labeling of segments of
text (coding), translation of codes into themes,
creation of the model and assessment of the
trustworthiness of the model.
4 RESULTS
For the question "What is the most important
information you think should be provided to the cloud
customer in this scenario?" the participants talked
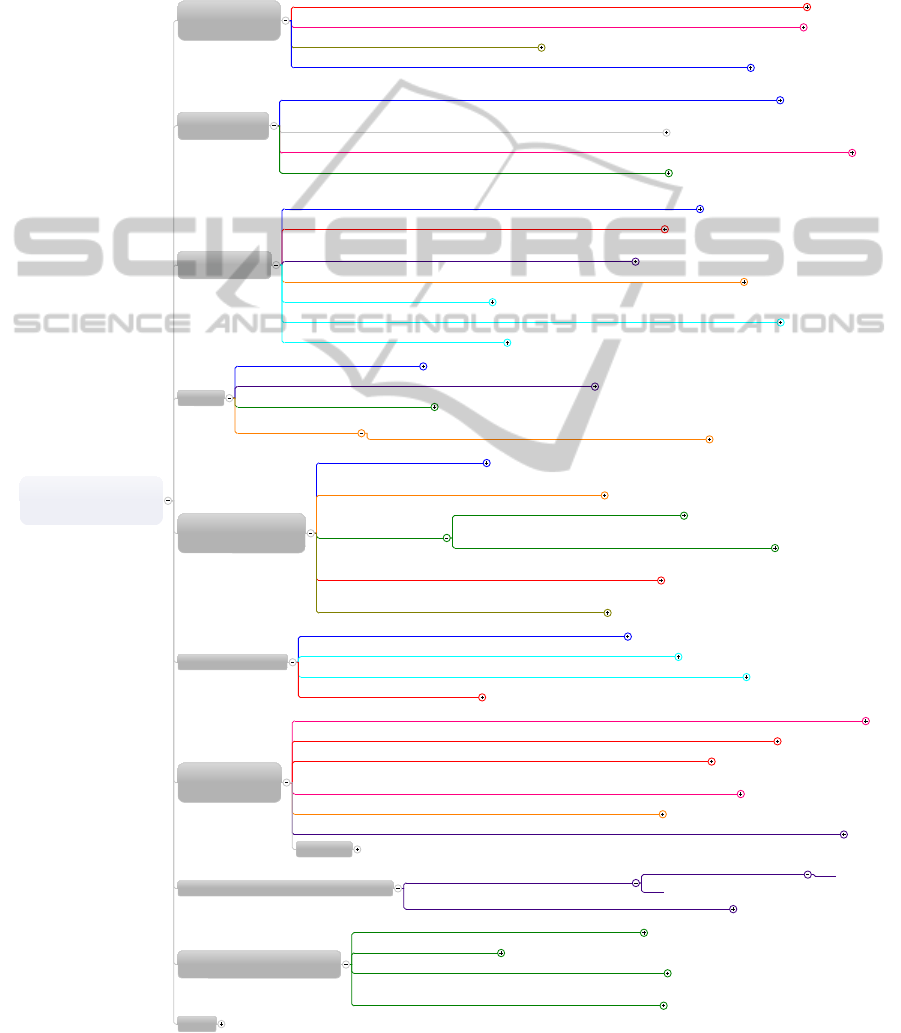
mostly about nine themes (Figure 2):
1. clear statements of what is possible to do
with the data,
2. conformance to data agreements,
3. how the provider handles data,
4. location,
5. who else other than the provider is
participant of the value chain,
6. multi-tenant situations,
7. what the provider does with the data,
8. procedures to leave the service
9. assurance that the user still owns the right to
the data.
One respondent commented that even though he
would like to have clear statements of what is possible
to do with the data: “100 pages document could be
written about this, but for some non-technical people
it would not help at all”. Another one said: “I would
like to have a [web] page where they could tell me
about security mechanisms, for example, firewalls,
backup etc.”
On the conformance to data agreements, the
respondents agree that having Data Agreements
helps, but it is mainly for technicians, not for non-
technical people. On how the provider handles data,
the respondents said that they would like to have
functional, technical and security related information
about how the providers handle the data. On location,
the respondents are concerned about where the data is
physically stored, and the legal jurisdiction of the
services. Another important piece of information is
about sub-providers, if there are any; where they are
located and whether they meet legal requirements of
the customer's location. Multi-tenant situations are a
concern of the customers, and they would like to have
this information transparent. Also, information on
how the providers ensure that data from one customer
will not be accessed by another customer.
It is also important for transparency to know what
the provider does to protect customers’ data. One
respondent said that he would like to have
information on: “How to protect the information or
how the information is protected; not much in detail
for the end-user, but only for enterprises.” It was also
highlighted that they would like to have the
procedures to leave the service and on how to move
data from one service to another transparent. Besides,
they would like to have the assurance that they still
own the rights to their data.
On the question "What would increase your trust
that the data is secure in this scenario?" the
participants mentioned eight different themes: 1)
upfront transparency; 2) community discussions, 3)
customer awareness; 4) way out; 5) reputation; 6)
encryption; 7) data processor agreements; and 8)
location.
Some answers were overlapping towards the
answers from the first question: upfront transparency,
location and conformance to data processor
agreement. Interesting answers for this question were
related to community discussions, customer
awareness and reputation. The respondents said that
it increases their trust in a cloud provider if they know
that the provider has an active security research team,
or participates in security communities. The
respondents also said that for security: “Customers
should be proactive and make sure that all the
documentation is there”. And another one commented
on the importance of having webpages telling what
customers could do to keep the data safe. Two
participants also mentioned “Way out”, meaning that
they would like to have webpages telling them what
to do to remove the data from the service provider.
On the questions: "In which parts would you like
to be involved in making the decisions? In which
parts would you like just to be informed of the
decisions?" it was surprising that the participants
mostly answered that they would like to be informed
but not really taking part of every decision (Figure 4);
the exceptions were when the provider was moving
data to another country, other parties are introduced
in the service provider value chain, or there are
significant changes in the initial terms of contract.
One participant said: “Some customers sometimes
have some requests, but in general they do not care
about taking part in the decisions”, and another one
CLOSER2015-5thInternationalConferenceonCloudComputingandServicesScience
34
said: “there are some decisions that we don't need to
explicitly know about, but it has to be regulated by
some other agreement about the responsibility of each
one towards the data”. One respondent also said: “I
would like to be involved in decisions on moving my
data to another country in most situations. Unless for
example a disaster and there is the need to move to
another country.” Some respondents said that they
would like to be informed when the data is transferred
from one actor to the next, one of them added: “For
example if calling to the call center your data will be
transferred to another country then the customers has
Figure 2: Important Upfront Information for Transparent Services.
What is the most important
information you think should
be provided to the cloud
customer in this scenario?
Clear statements
of what is possible
to do with the data
The providers should have some kind of standard certification level of description or standard language that they
have to make the situation easier to the buyer to evaluate which security level do we need, what is required from
us and what is the provider offering.
I would like to have a page that they could tell me about security mechanisms, for example, firewalls, backup etc
That I can choose what is possible to do with my data
100 pages document could be written about this but for some non-technical people it would not help.
Conformance to
Data Agreements
Data Agreement helps. How data is handled, how it is stored, the procedures. And having this documentation
available it helps. But mainly for technicians not for non technical people
For example, your data is encrypted in transferred and stored. In a safe harbor, And
also behave adhered to the norwegian data act or norwegian protection framework
Legal contracts sometimes are too big and overkilling. Something in between too high level information and the big contracts.
Show that follows the data handling agreement to the type of data that is in question.
How the Provider
handles data
What the provider does with the data. Of course, problems are the same as with old HOST
systems. You don't really know what the software provider does with your data.
Functional, technical and security wise information about how they handle the data.
If sensitive information is stored on the cloud, they should provide very good
information of how the data is stored and who has access to it.
How the providers will handle data. What is the responsibilities of the parts involved in the agreement
How do the providers manage their systems
All the security aspects of the data are important to be evidenced, before they get a contract with the provider
How many employees have access to the data.
Location
Geographically where my data is stored
Which country it is stored? We are very concerned that it is outside of Norway.
Location. Geographical and Legal location
Locations of the providers
It is important to know where it is located. It might be ok if its in Norway or
not, but it depends on the data the consumers will put on the cloud.
Who else other than the
provider is participant of
the value chain
Which provider is actually stored at.
Information about sub providers if there are. Where they are
located and whether they meet legal requirements of Norway.
What does the whole data
privacy stack looks like.
but providers are quite reluctant to comply to this.
Can other parties get access to your data? For example call centers?
That are located in another country for cost saving purposes?
Who are the participants of the cloud side. Which parties are involved. Are
there others involved? Is this a sole company providing the service?
I would like to know how the service is set up. Who is involved
with who. And that people can see how things are set up.
Multi Tenant Situations
If they are combining my data with other data about me in their servers.
How the customers are separated from each other, in case of multi-tenant services
How the providers assure that data from one customer will not be accessed by another customer.
How they protect the data privacy part.
What the provider
does to protect my
data
How to protect the information or how the information is protected not much in detail for the end-user, but only for enterprises.
That there are mechanisms that secure data not only for data loss but also for data privacy vulnerabilities.
A document that cover some kind of standard level of mechanisms for preventing intrusion.
The default should be maximum security as default and the user decides if they change to
another level of security. But it can also be that the enterprise decides which level they want to do.
The agreement go to the level of saying for example, we need two data centers.
I take for granted that secure rooms, security systems and backup are in place. but of course I would like to hear about it
Encryption
What are the procedures to leave the service?
How do I move data from one service to another?
It is needed good standardization of APIs.
5OL
5OL
What is the exit strategy? How can we be out of the service if we want?
Assurance that you still owns the
right to your data
Do you retain full rights to your data or you lose some of them?
What they can do with the data
Who actually have control of your data and what they can do with it?
Things that you can regulate in contract. Ensuring that the provider
can't sell your data, that the consumer has the rights to the data
Others
CloudProviderTransparency-AViewfromCloudCustomers
35
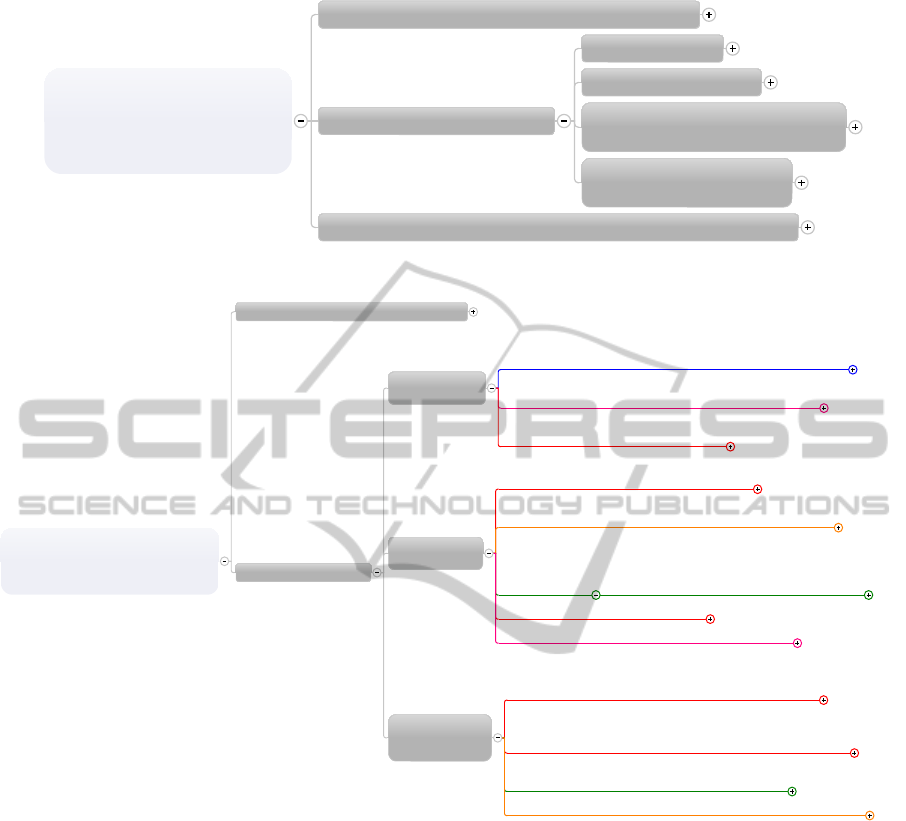
Figure 3: Transparency on Correction of Data Security Problems.
Figure 4: Involvement on making Decisions.
to be involved in the decision about that. So he can
take an informed decision.” On changes in the initial
terms of Contract, one respondent said: "the providers
should be very aware of what they changed since the
contract with the customer [was signed], and inform
them about the changes that happen. Never leave the
customer in the dark.”
When asked on what they would want to know
about how the provider corrects data security
problems, it was again surprising to learn that the
participants have not thought much on what they
could expect from the providers if some security issue
happens. Most of the respondents needed further
elaboration of the question before they would start
saying something. Then, the participants stated that
they would like to know what is planned before
something happens; when something happens they
want to know how the providers are handling the
situation, why the problem happened, and when will
the services be back online. Interesting was also the
fact that the participants wanted to know how the
providers are improving their services after
something happens, based on lessons learned. These
responses are collated in the taxonomy shown in
Figure 3.
5 DISCUSSION
After analyzing all the collected information we
compiled a list of requirements elicited in the
interviews, as shown in Table 2. The main “topics”
What do you want to
know about how the
provider corrects data
security problems?
Before Something Happens, what is planned
When Something Happens
what happened
why did it happened
what are the procedures that
they are taking to correct .
when will services be
back working normally.
After Something Happened,what are the lessons learned
In which parts would you like to be
involved in making the decisions?
In which parts would you like just to
be informed of the decisions?
Informed YES, taking part of decisions NO
Taking part of Decisions
Moving data to
another country
I would like to be involved in decisions on moving my data to
another country in most situations. Unless for example a disaster
and there is the need to move to another country.
I would like to be part of the decision if the service provider
move the location of the data, for example Ireland or US.
Country is important to know. The level of
trust is different from country to country.
Other Parties
will be involved
I want to be updated when other parties are
involved than the ones I have the contract with.
If they move the data, so someone else will handle the data on
behalf of them. For example, changes of sub providers.
Informed when
the data is trans-
ferred from one
actor to the next
For example if calling to the call centre your
data will be transferred to another country then
the consumer has to be involved in the decision
about that. So he can take an informed decision.
Is there any change in the value chain.
The service provider is merging with another company.
Changes in the
initial terms of
Contract
There should not be any changes on the initial information
that they gave to the customer at the contract time. And if
changes happen, the customer should be informed.
The providers should be very aware of what they changed since
the contract with the customer. And inform them about the
changes that happens. Never leave the customer in the dark.
Anything that changes the initial agreement that you
have with the provider
Anything that is outside of the initial agreement should be informed.
CLOSER2015-5thInternationalConferenceonCloudComputingandServicesScience
36

Table 2: List of Requirements from Transparency interviews.
List of Elicited Requirements
What is possible to
do with the data
The provider should show clear statements of what is possible to do with the data
The provider should allow the cloud customer to choose what is possible to do with
his/data data
The provider should have a page that they could tell the cloud customer about security
mechanisms, e.g., firewalls, backup etc.
The provider should have some kind of standard certification level of description or
standard language that they have to make the situation easier to the buyer to evaluate
which security level do we need, what is required from us and what is the provider
offering.
The provider should have a document explaining what are the procedures to leave the
service and take the data out of their servers.
The provider should have a document in which they describe the ownership of the data.
Conformance to
Data Agreement
The provider should make available the technical documentation on how data is handled,
how it is stored, and the procedures.
There should be documentation of procedures in different levels of abstraction, for
example for technical staff or for cloud subjects
The provider should show that they follow the data handling agreement to the type of
data that is in question.
The provider should provide geographical information of where the data is stored.
Data Handling
The provider should provide functional, technical and security wise information about
how they handle the data.
The provider should provide very good information of how the data is stored and who
has access to it.
Value chain
In case of using services from other parties, the provider should inform cloud customers
on what are the responsibilities of the parts involved in the agreement.
In case of using services from other parties, the provider should inform about the
existence of sub providers, where they are located and whether they meet legal
requirements of the country of the cloud customer.
Multi-Tenant
Services
The provider should inform the cloud customers on cases of multi-tenant services.
In case of multi-tenant services, the provider should inform how the customers are
separated from each other.
In case of multi-tenant services, the provider should inform how they assure that data
from one customer will not be accessed by another customer.
Protection of the
data
The provider should inform the cloud customer on how to protect the information or how
the information is protected not much in detail for the end-user, but only for enterprises.
The provider should have a document describing the mechanisms that secure data not
only for data loss but also for data privacy vulnerabilities.
Decisions
The cloud providers should get the consent of the cloud customer before moving the data
to another country, in cases where new parties will be involved in the value chain and
on changes on the initial terms of contract.
Correction of the
data
The cloud provider should have a document stating what are the procedures and
mechanisms planned for cases of security breaches on customers' data.
In case of security breaches, the cloud provider should inform the cloud customers on
what happened, why did it happen, what are the procedures they are taking to correct
the problem and when will services be normalized.
CloudProviderTransparency-AViewfromCloudCustomers
37

mentioned by the respondents were related to what is
possible to do with the data, conformance to data
agreements, data handling, value chain, multi-tenant
situations, protection of the data, decisions and
corrections of the data.
Pauley (2010) designed a scorecard reproduced in
Table 1 to cover the assessment areas frequently
raised in the research, and to begin to establish high-
level criteria for assessing provider transparency.
When comparing our list of elicited requirements to
Pauley’s scorecard (Table 2), we can see some slight
differences in the criteria that Pauley described as
information that should be provided by the cloud
providers and the information that the customers are
looking for (Table 2). In the criteria about the
business factors, the customers did not mention being
concerned about the number of years in business, nor
about membership of CSA, CloudAudit, OCCI, or
other cloud standards groups, or if the providers are
profitable or public. There is a possibility that the
respondents did not mention these criteria because (a)
companies in Norway are usually stable, and (b)
membership of a group or association does not in
itself guarantee good performance or compliance,
even if the group or association promotes a certain
standard.
On the security and privacy aspects, the customers
mentioned all the criteria, but they did not mention
directly the standards/certifying bodies, such as
ISO/IEC 27000, COBIT and NIST, but they
mentioned that it would be nice to know if the
provider was certified somehow, based on some
criteria. The customers also did not mention the need
to know about “external” audits. One of the reasons
for not mentioning security standards and
certification bodies may be that companies that we
have investigated are predominantly private
companies in Norway, where there are not strong
requirements from the certification bodies yet.
One important aspect not very much explored in
Pauley’s scorecard is that customers would like
providers to be transparent about what is possible to
do with the data. In addition, customers were quite
concerned about transparency on exit procedures
(“way out”) and ownership of the data. The concern
over data ownership is interesting seen in the light of
Hon et al. (2012), who found no evidence of cloud
contracts leading to loss of Intellectual Property
Rights.
Another aspect further mentioned by the
customers is on the decisions made on “ongoing”
services, where the customers would like that: “The
cloud providers should get the consent of the cloud
customer before moving the data to another country,
in cases where new parties will be involved in the
value chain and on changes on the initial terms of
contract.”
Physical location and legal jurisdiction, as well as
specific information on the value chain was a very
important aspect to be transparent about for the cloud
customers, and it was not explicitly mentioned in
Pauley’s scorecard.
The interviewees did not show a desire for the
kind of detailed information Durkee (2010) deems
necessary (the inner workings of their cloud
architecture as part of developing a closer relationship
with the customer), and as also pointed out by
Durkee, some respondents were also aware that the
costs of such clarity may be prohibitive, and we might
add that this level of disclosure seems highly unlikely
for ordinary customers of commodity cloud services.
Many of the transparency mechanisms that
customers expressed a desire for are actually being
developed by the A4Cloud project (Jaatun et al.,
2014). For end-users, the Data Track tool (Fischer-
Hübner et al., 2014) enhances transparency by
tracking which personal data has been released to
whom. Furthermore, a central theme of A4Cloud is
the development of the Accountability PrimeLife
Policy Language (A-PPL), which allows end users to
specify a privacy policy that also covers
accountability requirements, including transparency
(Azraoui et al., 2014). A4Cloud is developing an A-
PPL Engine which will serve as a Policy Decision
Point for the associated policies at each cloud
provider. Other tools developed by A4Cloud include
the Cloud Offerings Advisory Tool (COAT), which
allow cloud customers to select an appropriate cloud
provider based on relevant accountability
requirements, including transparency (Alnemr et al.,
2014). This will eventually allow transparency
requirements to be built into standard cloud service
level agreements (SLAs), where transparency is just
one of several security attributes (Jaatun et al., 2012).
6 CONCLUSIONS
Cloud computing has been receiving a great deal of
attention, not only in the academic field, but also
amongst the users and providers of IT services,
regulators and government agencies. The results from
our study focus on an important aspect of
accountability of the cloud services to customers:
transparency.
The customers made explicit all the information
that they would like the providers to be transparent
about. Much of this information can be easily
CLOSER2015-5thInternationalConferenceonCloudComputingandServicesScience
38

provided at a provider's website. Our contention is
that being transparent can be a business advantage,
and that cloud customers who are concerned with,
e.g., privacy of the data they put into the cloud, will
choose providers who can demonstrate transparency
over providers who cannot.
Our study increases the body of knowledge on the
criteria needed for more accountable and transparent
cloud services, and confirms the results from previous
studies on these criteria. The list of requirements in
Table 2 complements, in part, the existing criteria.
An area for future research is to further evaluate
how cloud providers currently make the information
required by cloud customers available. In addition,
what are the effects of having transparent services in
terms of costs and benefits to cloud customers and
providers. Besides, we plan to increase the number of
participants responding to our interview guide and
adding strength to the evidence provided in this paper.
Another aspect we would like to investigate, is if the
results will be different for users of the different types
of services (e.g., SaaS vs IaaS).
ACKNOWLEDGEMENTS
This paper is based on joint research in the EU FP7
A4CLOUD project, grant agreement no: 317550.
REFERENCES
AbuKhousa, E., Mohamed, N., and Al-Jaroodi, J., “e-health
cloud: Opportunities and challenges,” Future Internet,
vol. 4, no. 3, pp. 621–645, 2012.
Ahuja, S. P., Mani, S. and Zambrano, J., “A Survey of the
State of Cloud Computing in Healthcare,” Network and
Communication Technologies, vol. 1, no. 2, p. 12,
2012.
Alnemr, R., Pearson, S., Leenes, R., and Mhungu, R.,
“COAT: Cloud Offerings Advisory Tool”. Proc. of the
2014 IEEE International Conference on Cloud
Computing Technology and Science (CloudCom 2014)
95-100, 2014.
Azraoui, M., Elkhiyaoui, K., Önen, M., Bernsmed, K.,
Sendor, J., and Santana de Oliveira, A., “A-PPL: An
accountability policy language”, in DPM, 9th
International Workshop on Data Privacy Management,
10 September 2014.
Bernsmed, K., Tountopoulos, V., Brigden, P., Rübsamen,
T., Felici, M., Wainwright, N., Santana De Oliveira, A.,
Sendor, J., Sellami, M., and Royer, J.-C., “Consolidated
use case report”, A4Cloud Deliverable D23.2, October
2014 http://www.a4cloud.eu/sites/default/files/D23.2%
20Consolidated%20use%20case%20report.pdf.
Cruzes, D. S. and Dybå, T., Recommended Steps for
Thematic Synthesis in Software Engineering. ESEM
2011: 275-284, 2011.
Durkee, D., Why cloud computing will never be free.
Commun. ACM 53(5): 62-69 , 2010.
Felici, M., Koulouris, T. and Pearson, S., “Accountability
for Data Governance in Cloud Ecosystems”, Proc. of
the 2013 IEEE International Conference on Cloud
Computing Technology and Science (CloudCom
2013), 2013.
Fischer-Hübner, S., Angulo, J., and Pulls, T., “How can
Cloud Users be Supported in Deciding on, Tracking and
Controlling How their Data are Used?”, Privacy and
Identity Management for Emerging Services and
Technologies, IFIP Advances in Information and
Communication Technology Vol. 421, 2014, pp 77-92.
Gavrilov, G. and Trajkovik V., “Security and privacy issues
and requirements for healthcare cloud computing,” in
Proceedings of ICT Innovations, 2012.
Hon, W.K., Millard, C. and Walden, I., “Negotiating Cloud
Contracts - Looking at Clouds from Both Sides Now”
(May 9, 2012). 16 STAN. TECH. L. REV. 81 (2012);
Queen Mary School of Law Legal Studies Research
Paper No. 117/2012.
Jaatun, M.G., Bernsmed, K., and Undheim, A.: "Security
SLAs – an idea whose time has come?", Proc. CD-
ARES, Prague, LNCS Volume 7465, pp 123-130, 2012.
Jaatun, M.G., Pearson, S., Gittler, F., and Leenes, R.,
“Towards Strong Accountability for Cloud Service
Providers”, Proc. of the 2014 IEEE International
Conference on Cloud Computing Technology and
Science (CloudCom 2014), 2014.
Khorshed, M. T., Ali, A.S. and Wasimi, S.A.: A survey on
gaps, threat remediation challenges and some thoughts
for proactive attack detection in cloud computing.
Future Gener. Comput. Syst. 28(6), 833–851 (2012).
Kuo, A. M.-H., “Opportunities and challenges of cloud
computing to improve health care services,” J. Med.
Internet Res., vol. 13, no. 3, p. e67, 2011.
Onwubiko, C., (2010) "Security Issues to Cloud
Computing", in Cloud Computing: Principles, Systems
& Applications, (Eds) Nick Antonopoulos and Lee
Gillam, Springer-Verlag, August, 2010.
Paquette S., Jaegar, P. T. and Wilson, S. C. Identifying the
security risks associated with governmental use of
cloud computing, Journal of Government Information
Quarterly 27, pages 245-253, April, 2010.
Pauley, W.A., “Cloud Provider Transparency: An
Empirical Evaluation,” IEEE Security & Privacy (8)6,
pp. 32– 39, 2010.
Rodrigues, J. J., Torre, I. de la, Fernandez, G., and Lopez-
Coronado, M., “Analysis of the security and privacy
requirements of cloud-based electronic health records
systems,” J. Med. Internet Res., vol. 15, no. 8, p. e186,
2013.
Yang, H. and Tate, M., "A Descriptive Literature Review
and Classification of Cloud Computing Research,"
Communications of the Association for Information
Systems: Vol. 31, Article 2, 2012.
CloudProviderTransparency-AViewfromCloudCustomers
39
