
Enhanced Intrusion Detection System Based on Bat Algorithm-support
Vector Machine
Adriana-Cristina Enache and Valentin Sgˆarciu
Faculty of Automatic Control and Computer Science, University Politehnica of Bucharest, Bucharest, Romania
Keywords:
Intrusion Detection, SVM, Bat Algorithm, Binary Bat Algorithm, L´evy Flights.
Abstract:
As new security intrusions arise so does the demand for viable intrusion detection systems. These solutions
must deal with huge data volumes, high speed network traffics and countervail new and various types of
security threats. In this paper we combine existing technologies to construct an Anomaly based Intrusion
Detection System. Our approach improves the Support Vector Machine classifier by exploiting the advantages
of a new swarm intelligence algorithm inspired by the environment of microbats (Bat Algorithm). The main
contribution of our paper is the novel feature selection model based on Binary Bat Algorithm with L´evy
flights. To test our model we use the NSL-KDD data set and empirically prove that L´evy flights can upgrade
the exploration of standard Binary Bat Algorithm. Furthermore, our approach succeeds to enhance the default
SVM classifier and we obtain good performance measures in terms of accuracy (90.06%), attack detection rate
(95.05%) and false alarm rate (4.4%) for unknown attacks.
1 INTRODUCTION
Many of our activities imply using the Internet (on-
line payments, internet banking, social networks or
searching for informations) and almost all govern-
ment or private organizations store critical data over
the networks. This increasing usage and growing
speed of network connections has determined the pro-
liferation of various threats. In this context security
systems have become vital components. Despite the
recent advances, security incidents are on the rise.
IDS have become an indispensable component of al-
most every security infrastructure, mainly because
they provide a wall of defense and resist external at-
tacks effectively, where other traditional security sys-
tems cannot perform well.
Intrusion Detection Systems (IDS) monitor the
activities and events occurring in the systems and de-
cide if these are intrusive actions or normal usage of
the system. In general, IDS are classified on the ba-
sis of their data analysis technique as: misuse and
anomaly detection. The misuse method is very ac-
curate in detecting known attacks based on their sig-
natures that are stored in the database. The anomaly
detection approach automatically constructs a normal
behavior of the systems. This latter method can de-
tect new attacks but, it can also generate many false
alarms(Kukielka and Kotulski, 2014).
Since 1980, when Anderson introduced the first
IDS model, multiple techniques have been proposed
to improve these systems. Many researchers have fo-
cused their attention on the anomaly based IDS and
designed several approaches based on machine learn-
ing algorithms ( decision trees, neural networks or ge-
netic algorithms). There are many challenges to be
regarded when implementing an IDS such as offering
real-time responses with a high attack detection rate
and a low false alarm rate. Also, the large number of
features and difficulty to recognize the complex rela-
tionship between them makes classification a difficult
task. In order to address these issues, we propose a
Network Anomaly Intrusion Detection Model based
on Support Vector Machines(SVM) with Swarm In-
telligence(SI). Our approach has two main compo-
nents: feature selection and enhanced SVM classifier.
Support Vector Machine (SVM) has many advan-
tages that make it a suitable solution for intrusion de-
tection, such as: good generalization performances
and learning ability in high dimensional or noisy
datasets. Furthermore, SVM does not suffer from lo-
cal minima and its execution time runs fast. However,
a draw-back of this classifier is that its performance
depends on selection of the right parameters.
Recently, swarm intelligence (SI) algorithms have
attracted great interest, mainly because they are sim-
ple, flexible (can be applied to a variety of problems
such as optimization, data mining and so forth) and
robust (the algorithm will function even if some indi-
viduals fail to perform their tasks). Currently, there
are a variety of SI algorithms such as: ant colony op-
184
Enache A. and Sgârciu V..
Enhanced Intrusion Detection System Based on Bat Algorithm-support Vector Machine.
DOI: 10.5220/0005015501840189
In Proceedings of the 11th International Conference on Security and Cryptography (SECRYPT-2014), pages 184-189
ISBN: 978-989-758-045-1
Copyright
c
2014 SCITEPRESS (Science and Technology Publications, Lda.)

timization, particle swarm optimization (PSO), artifi-
cial bee colony algorithm, firefly algorithm, cuckoo
search or bat algorithm. These algorithms have been
combined with SVM to contruct improved IDS mod-
els and in most cases are used for two optimization
processes: feature selection and electing SVM param-
eters. Wang et. al. (Wang et al., 2009) present an IDS
based on PSO-SVM. They used Binary PSO to deter-
mine the best feature subset and Standard PSO to seek
for optimal SVM parameters. In 2010, a novel Arti-
ficial Bee Colony(ABC)-SVM approach is proposed
(Wang et al., 2010) and experiments on the KDD-
Cup99 dataset proved that ABC-SVM can obtain bet-
ter accuracy rate than PSO-SVM or GA-SVM. Pu et.
al. (Pu et al., 2012) improve SVM parameters with
the Ant Colony Algorithm by defining the input pa-
rameters as the ant’s position.
In this paper we use a relatively new metaheuris-
tic to improve the SVM classifier, the Bat Algorithm
(BA), which shows promising results (Yang, 2010a),
(Yang and He, 2013). Furthermore, we introduce an
innovative feature selection model that combines Bi-
nary Bat Algorithm (BBA) with L
´
evy flights and em-
pirically demonstrate that it can outperform the stan-
dard BBA when coupled with SVM.
The rest of this paper is organized as follows: first
we introduce the algorithms that will be used to con-
struct our IDS model. Next, we describe our ap-
proach, define the performance measures and show
our test results. Also, we compare our model with
other methods and indicate that it can obtain better
results. Finally, the conclusions and future work.
2 BACKGROUND OVERVIEW
2.1 Support Vector Machine
Support Vector Machine (SVM) is a binary super-
vised learning algorithm that searches for the opti-
mum hyperplane to separate the two classes. This
linear classifier conducts structural risk analysis of
statistical learning theory by selecting a number of
parameters based on the requirement of the margin
that separates the data points (Dua and Du, 2011b).
The hyperplane is defined as f(x) = w· x+ b, where
w is the weight vector and b is the bias. Our clas-
sifier defines a hyperplane and linearly separates the
two classes: anomaly and normal traffic. The points
closest to the hyperplane are called support vectors
and the distance between them is called the margin.
On the other hand, the dataset is not always lin-
early separable. This issue is solved by introducing
a slack variable and defining a soft margin. Further-
more, using kernel functions, we can transform the
nonlinear SVM into a linear problem by mapping the
dataset into a higher-dimensional feature space. For
our model we will use SVM with radial basis func-
tion (RBF), where the kernel function is:
K(x
i
, x) = exp(−
1
2σ
2
kx
i
− xk
2
) (1)
The RBF kernel function is a good solution be-
cause it has fewer controllable parameters and an ex-
cellent nonlinear forecasting performance. In the fol-
lowing we define the SVM controllable parameters
and explain their influence.
• The Regularization Parameter (C) - controls
the ”flexibility” of the hyperplane’s margins. In
other words, smallerC allows softer-marginsthus,
permits greater errors. Larger C produces a more
accurate model with harder margins but, the gen-
eralization performance of the classifier is worse.
• Kernel Parameter (σ) - is the constant variable
from the kernel function. This parameter reflects
the correlation among support vectors that define
the hyperplane and may cause overfitting or un-
derfitting of the classifier.
2.2 Bat Algorithm
Bat Algorithm (BA) was developed by Yang in 2010
(Yang, 2010a) and it was inspired by the echoloca-
tion of bats. These microbats emit a loud sound pulse
and change their pulse rate as the obstacle or prey is
closer. In order to define a smart bat algorithm, three
generalization rules have been formulated:
• All bats use echolocation to approximate the dif-
ference between an obstacle and a prey and sense
distance.
• Bats fly randomly and their movement is defined
by their position in space (x
i
) and velocity (v
i
).
These parameters are computed based on a vary-
ing wavelength (λ), frequency (freq
min
) and loud-
ness (A
0
) to search for prey. Moreover, bats can
modify the frequency of their emitted pulses and
the rate of pulse emission (r ∈ [0, 1]), depending
on the closeness of their target.
• The loudness can vary in multiple ways, but we
assume that it varies from a large value (A
0
) to a
minimum constant value (A
min
).
BA is a swarm intelligence algorithm which per-
forms searches using a population of agents. For
SVM parameter selection, BA will search for the best
C and σ based on the accuracy of SVM. Each agent
i has a current position x
i
= (x
i,1
, x
i,2
, ..., x
i,d
)
t
and a
EnhancedIntrusionDetectionSystemBasedonBatAlgorithm-supportVectorMachine
185

current flying velocity v
i
= (v
i,1
, v
i,2
, ..., v
i,d
)
t
, where
d is the problem dimension. To find the optimal po-
sition, each agent (or bat) updates its position and ve-
locity according to the following equations:
freq
i
= freq
min
+ ( freq
max
− freq
min
) ·β (2)
v
i, j
t
= v
i, j
t−1
+ (x
i, j
t−1
− x
best
j
) · f req
i
(3)
x
i, j
t
= x
i, j
t−1
+ v
i, j
t
(4)
where β ∈ [0, 1] is a random vector drawn from a uni-
form distribution. As stated earlier, the bat will de-
creases his loudness (A
i
) and increase his pulse emis-
sion rate (r
i
) when he is closer to the target:
A
i
t+1
= α· A
i
t
(5)
r
i
t+1
= r
i
0
· [1− e
−γ·t
] (6)
where α (0 < α < 1) and γ (γ > 0) are constants. At
each iteration, the fitness value is improved, while
A → 0 and r → r
0
. In order to ameliorate the vari-
ability of the discovered solutions, Yang uses random
walks to generate new solutions:
x
new
= x
old
+ δ· A
∗
t
(7)
where δ ∈ [−1, 1] is a random number and A
∗
t
is the
average loudness of all bats at iteration t.
In some ways we can state that BA is similar to
the popular PSO. The solution is denoted by the po-
sition of the particle, each individual from the swarm
has its own position and velocity which are updated
according to their fitness value. There are also some
significant differences, as BA uses random walks for
exploration (or diversification) and varies the loud-
ness and pulse rate in order to exploit the solution.
For PSO, exploitation is controlled by the use of the
global best and individual best solutions, while explo-
ration is done using two learning parameters(Yang,
2012).
2.3 Feature Selection
Feature selection methods can be divided into : scalar
methods (are less complex and select features individ-
ually) and vector methods (select a subset of features
based on a mutual relation between features)(Dua and
Du, 2011a). In the following we introduce the Binary
Bat Algorithm and explain how it can be adapted to
construct a vector approach feature selection.
2.3.1 Binary Bat Algorithm
The Binary Bat Algorithm(BBA) (Mirjalili et al.,
2013) is a modified version of BA that describes the
bat’s motion in a d-dimensional binary space. There-
fore, the position of a bat is defined as a vector of
binary coordinates and the bat can move across the
corners of a hypercube. Given bat i, its coordinates
are computed using a sigmoid function as follows:
x
i, j
=
(
−1 if S(v
i, j
) > δ
0 otherwise
(8)
Where, the sigmoid function is :
S(v
i, j
) =
1
1+ e
−v
i, j
(9)
and δ ∈ U(0, 1). Hence, the bat’s position can be
seen as a string of binary numbers. For the feature
selection process we want to determine the best fea-
ture subset that will enhance the performances of our
classifier. In order to adapt BBA for feature selection
we can consider the bat’s position as the subset of fea-
tures and the bat’s coordinates as the presence (if the
coordinate is one) or absence(if the coordinate is zero)
of a feature. The fitness function for BBA will be the
accuracy of SVM after it has been trained with the
subset of features represented by the bat’s position.
In order to elevate the exploration of BBA we
use L
´
evy flights for randomization. L
´
evy flights are
a random walk whose step length is drawn from a
L´evy distribution. Recent studies have shown that
L´evy flights can better searches in uncertain environ-
ments. L´evy flights have many applications and have
been observed among foraging pattern of spider mon-
keys or albatrosses (Yang, 2010b). This distribution
has been combined with other computational intelli-
gence algorithms, such as : cuckoo search(Yang and
Deb, 2009), firefly (Yang, 2009) or bat algorithm (Xie
et al., 2013). Here we exploit this distribution with
BBA for feature selection. Therefore, we substitute
equation (7) with:
x
new
= x
old
+ t
−η
· A
∗
t
(10)
where t
−η
is the L´evy flights distribution and 1 < η ≤
3 is a constant.
BBA feature selection tries to optimize the feature
subset at each iteration, such that the classifier’s accu-
racy enhances. The main steps of this algorithm are
given below:
a. Each bat has a position that defines the subset of
features. Based on this subset, the bat trains and
evaluates the SVM classifier.
b. After all bats have been evaluated the global opti-
mum fitness value of the swarm is determined.
c. Each bat improves its position and updates its
pulse rate and loudness as it approaches the best
solution. For this:
SECRYPT2014-InternationalConferenceonSecurityandCryptography
186
– the bat uses L
´
evy flights to randomize the solu-
tion, in which case will compute equation (10)
and the sigmoid function will be S(x
i, j
).
– otherwise, if the fitness value has not improved
(compared to the global best) the bat will up-
date his frequency and velocity. The sigmoid
function is given by equation (9).
– finally, if the new fitness value is better than the
global best, the bat will increase his pulse rate
and decrease his loudness. The global optimum
is modified.
d. All the steps from c. are covered by all bats from
the swarm and are reiterated, until the maximum
number of loops is reached.
3 PROPOSED MODEL
Our model has three main stages : first we apply BBA
with L´evy flights (BBAL) to determine the best sub-
set for SVM, next we use BA to determine the best
parameters for SVM. Finally, SVM detects network
attacks using the best parameters calculated above.
3.1 Data Set
In this paper we experimented with the NSL-KDD
data set, which contains network attacks. We chose
this dataset because it is publicly available and is
an improved version of KDD-Cup (Tavallaee et al.,
2009). The simulated attacks from NSL-KDD fall
into one of the followingcategories: Denial of Service
(DoS), User to Root (U2R), Remote to Local (R2L) or
Probing. Furthermore, there are two different groups
of files: training and testing. It is important to men-
tion that test data includes attack types not in the train-
ing data and therefore it will allow us to evaluate the
classifier for unknown attacks.
We randomly select 9,500 feature samples from
the 20% training file and 4,500 records from the test
file. Each record from the dataset has 41 features and
is labeled as either normal or an attack. These features
can be classified into three categories: content based
(13 features), connection based (9 features) and time
based (19 features). In order to improvethe prediction
ability of the classifier, we convert the symbolic val-
ues into integer values, as follows: protocol type ∈
[0, 2] , service ∈ [0, 69] and flag ∈ [0, 10]. We also
replace the class label with 0 for normal and 1 for at-
tack.
3.2 Evaluation
To evaluate our model we find the best subset of fea-
tures with BBAL and compare it with BBA. Also,
we train the SVM classifier with BA using the de-
termined feature subset and compare it with PSO.
This comparison is relevant because PSO is a popu-
lar swarm intelligence algorithm that has been widely
used for optimization problems.
3.2.1 Performance Measures
We estimate the effectiveness of our IDS model by
calculating three performance measures: attack de-
tection rate (ADR) (shows the model’s capability of
detecting attacks), false alarm rate (FAR) (measures
how many false alarms the model generates) and
accuracy (reveals the model’s capability of raising
proper alarms).
3.2.2 Model Setup
All experiments were performed using an Intel Core
2 Duo 2.8 GHz processor with 2 GB of RAM under
Ubuntu 10.04.4. We implemented the Swarm Intelli-
gence algorithms (BBA, BBAL, BA and PSO) in Java
on eclipse. For the SVM classifier we used Weka ver-
sion 3.6.10 (Hall et al., 2009). BBAL and BBA
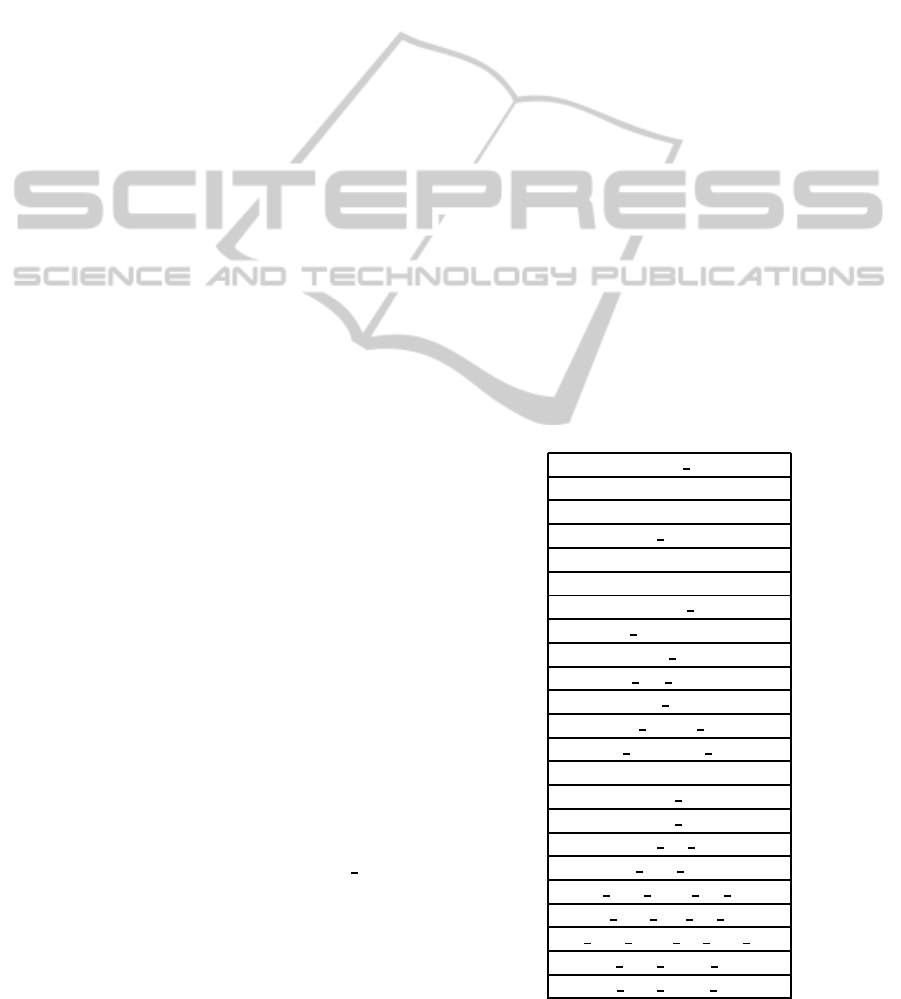
Table 1: Optimum feature subset selected by BBA-SVM.
protocol type
service
flag
src bytes
land
urgent
logged in
num compromised
num root
num file creations
num shells
num access files
num outbound cmds
count
serror rate
rerror rate
same srv rate
dst host count
dst host same srv rate
dst host diff srv rate
dst host same src port rate
dst host serror rate
dst host rerror rate
EnhancedIntrusionDetectionSystemBasedonBatAlgorithm-supportVectorMachine
187
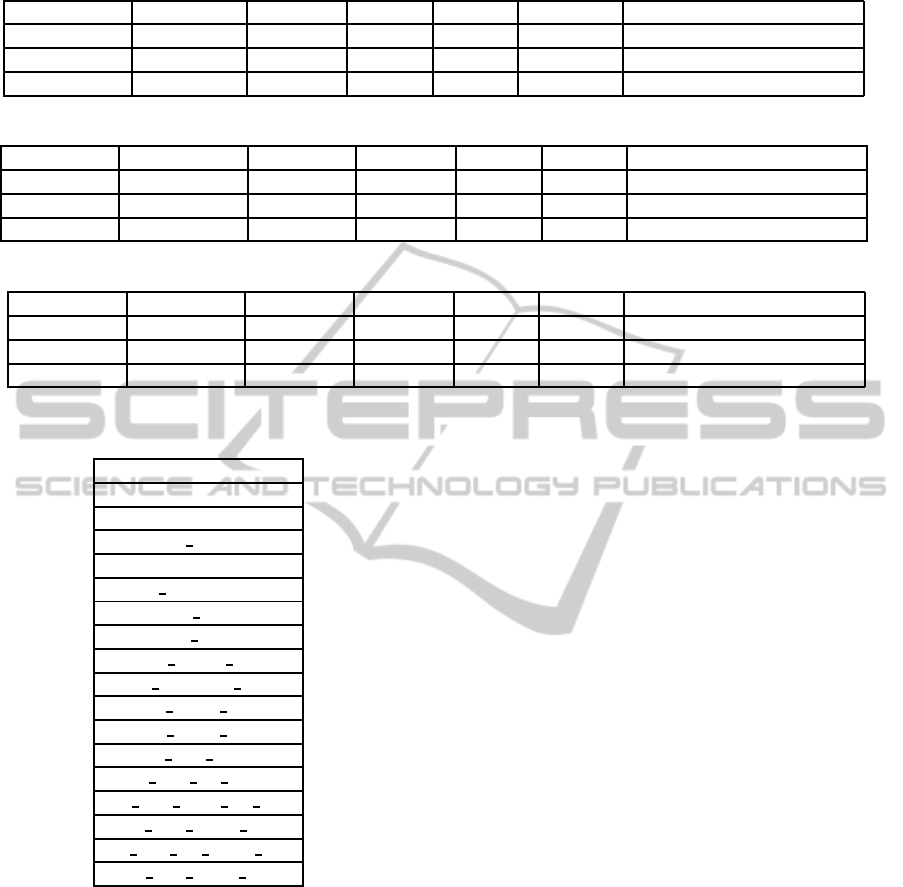
Table 3: Result comparison with determined feature subset
System Nb. of feat. Accuracy ADR FAR Test (sec.) Accuracy (training dataset)
SVM 41 78.933% 89.81% 7.288% 12.51 97.74%
BBA-SVM 23 79.022% 89.86% 7.377% 7.49 98.04%
BBAL-SVM 18 79.666% 91.22% 6.311% 6.82 98.31%
Table 4: Result comparison with the subset of features selected by BBA-SVM.
System C σ Accuracy ADR FAR Accuracy (training dataset)
SVM 1.0 0.5 79.022% 89.86% 7.377% 98.04%
PSO-SVM 110.9106619 5.945653 89% 92.26% 7.2% 98.89%
BA-SVM 65.488216 4.6051845 89.28% 92.38% 7.11% 99.05%
Table 5: Result comparison with the subset of features selected by BBAL-SVM.
System C σ Accuracy ADR FAR Accuracy (training dataset)
SVM 1.0 0.5 79.666% 91.22% 6.311% 98.31%
PSO-SVM 55.3817619 14.178919 89.93% 94.94% 4.488% 99.29%
BA-SVM 264.386988 5.252083 90.06% 95.05% 4.4% 99.31%
Table 2: Optimum feature subset selected by BBAL-SVM.
duration
service
flag
wrong fragment
urgent
num compromised
root shell
num shells
num access files
num outbound cmds
srv serror rate
srv rerror rate
dst host count
dst host srv count
dst host same srv rate
dst host serror rate
dst host srv serror rate
dst host rerror rate
have a swarm of 60 bats, the maximum number of
iterations is 200 and the problem dimension is 41 (the
number of features from the dataset). After several
tests we set the the maximum loudness ( A
0
=10),
the minimum pulse rate (r
0
= 0.9), the parameters
that control the convergence of the algorithm (γ = 0.1
and α = 0.9) and range the frequency between 0.8
and 1.0. We use η = 0.1 for L´evy flights. For BA
and PSO the maximum number of iterations is 100,
the problem dimension equals 2 (we need to optimize
two parameters C and σ) and range 1 ≤ C ≤ 500 and
0.0001 ≤ σ ≤ 50. BA has a population of 10 individ-
uals and the same parameters values as BBA, while
PSO has a population size of 20 individuals, learning
factors are c1 = 2.3 and c2 = 1.8 and inertia weight is
reduced from 0.9 to 0.5.
3.2.3 Results and Analysis
Tables 1 and 2 indicate the best subset of features de-
termined with BBAL-SVM and BBA-SVM, having
parameter C = 1.0 and σ = 0.5. BBAL obtains the
smallest number of features, reducing them by 43.9%.
BBA is more vulnerable to local optima than BBAL
but, it succeeds to simplify the number of features.
To evaluate these subset we use the training
dataset to build the model and the test dataset to eval-
uate it. Also, we perform a 3-fold cross validation
for the training dataset, in order to show the model’s
accuracy for known attacks. Results from Table 3 re-
veal the BBA-SVM subset givesslightly better perfor-
mances when compared to the initial dataset, leading
SVM to a higher classification rate, attack detection
rate and lower number of false alarms. On the other
hand, the BBAL subset, having a smaller number of
features, succeeds to enhance the classification abili-
ties of SVM and offers better results than BBA.
Furthermore, we also try to improve the SVM
classifier by selecting the proper input parameters.
For this we use two swarm intelligence algorithms
(PSO and BA) that will search for the best solution.
In other words, each individual of the swarm will at-
tempt to acquire a position, represented by the two
parameters, that will bring them a higher accuracy for
the classifier. The comparison between PSO and BA
for the two subsets is shown in Tables 4 and 5. We
can observe that both PSO and BA manage to boost
up the performance of the classifier by electing the
adequate parameters for SVM. As expected, the en-
SECRYPT2014-InternationalConferenceonSecurityandCryptography
188

hanced models perform better with the BBAL subset.
The attack detection rate for PSO-SVM with the BBA
subset is comparable with the standard BBAL-SVM.
Table 5 reveals PSO-SVM and BA-SVM, with the
BBAL subset, offer an improvement of almost 1.8%
for the false alarm rate and no more than 3.8% for the
attack detection rate. Results from Table 4 show the
false alarm rate is lightly significantly lower, while
the attack detection rate gains approximately 2.5%.
On the other hand, the accuracy for unknown attacks
is upgraded with almost 10% in all cases. This means
that our new classifier is able to raise proper alarms.
We must also remark that the difference between the
results given by PSO and BA is quite small. Further-
more, for known attacks, all approaches show good
accuracy results and the best is obtained by the BA-
SVM (99.31%).
4 CONCLUSIONS
In this paper we proposed a new NIDS model that
combines SVM with a recent swarm intelligence al-
gorithm, the Bat Algorithm. The main contribution
of this paper is the novel feature selection method
(BBAL) that succeeds to reduce the number of at-
tributes from the dataset while improving the predic-
tive accuracy, detection rate and false alarm rate of the
SVM classifier. To evaluate the effectiveness of the
proposed model we use the NSL-KDD network intru-
sion benchmark and compare it with the popular PSO
for our two subset of features. We showed that BBAL
can upgrade BBA for feature selection but, only when
combined with SVM. Therefore, our future work will
focus on combining BBAL with other classifiers and
comparing it to other feature selection approaches in
order to range its quality.
ACKNOWLEDGEMENTS
The work has been funded by the Sectoral Operational
Programme Human Resources Development 2007-
2013 of the Ministry of European Funds through the
Financial Agreement POSDRU/159/1.5/S/132395.
REFERENCES
Dua, S. and Du, X. (2011a). Classical machine-learning
paradigmsfor data mining. In Data Mining and Ma-
chine Learning in Cybersecurity, pages 23–56. Auer-
bach Publications Taylor and Francis Group.
Dua, S. and Du, X. (2011b). Machine learning for anomaly
detection. In Data Mining and Machine Learning in
Cybersecurity, pages 85–114. Auerbach Publications
Taylor and Francis Group.
Hall, M., Frank, E., Holmes, G., Pfahringer, B., Reutemann,
P., and Witten, I. H. (2009). The weka data mining
software: an update. SIGKDD Explor. Newsl., 11:10–
18.
Kukielka, P. and Kotulski, Z. (2014). New unknown attack
detection with the neural network-based ids. In The
State of the Art in Intrusion Prevention and Detection,
pages 259–284. Auerbach Publications.
Mirjalili, S., Mirjalili, S., and Yang, X.-S. (2013). Binary
bat algorithm. Neural Computing and Applications,
pages 1–19.
Pu, J., Xiao, L., Li, Y., and Dong, X. (2012). A detec-
tion method of network intrusion based on svm and
ant colony algorithm. In Proceedings of the National
Conference on Information Technology and Computer
Science, pages 153–156. Atlantis Press.
Tavallaee, M., Bagheri, E., Lu, W., and Ghorbani, A. A.
(2009). A detailed analysis of the KDD CUP 99 data
set. In Proceedings of the IEEE Symposium on Com-
putational Intelligence in Security and Defense Appli-
cations, pages 1–6. IEEE.
Wang, J., Hong, X., and R. Ren, T. L. (2009). A real-
time intrusion detection system based on pso-svm.
In Proceedings of the International Workshop on In-
formation Security and Application, pages 319–321.
ACADEMY PUBLISHER.
Wang, J., Li, T., and Ren, R. (2010). A real time IDSs
based on artificial bee colony-support vector machine
algorithm. In Proceedings in the International Work-
shop on Advanced Computational Intelligence, pages
91–96. IEEE.
Xie, J., Zhou, Y., and Chen, H. (2013). A novel bat algo-
rithm based on differential operator and l´evy flights
trajectory. Computational Intelligence and Neuro-
science, 2013.
Yang, X.-S. (2009). Firefly algorithm, l´evy flights and
global optimization. In Proceedings of the SGAI Inter-
national Conference on Artificial Intelligence, pages
209–218.
Yang, X.-S. (2010a). A new metaheuristic bat-inspired
algorithm. In Nature Inspired Cooperative Strate-
gies for Optimization (NICSO 2010), volume 284 of
Studies in Computational Intelligence, pages 65–74.
Springer Berlin Heidelberg.
Yang, X.-S. (2010b). Random walks and l´evy flights.
In Nature-Inspired Metaheuristic Algorithms Second
Edition, pages 11–20. Luniver Press.
Yang, X.-S. (2012). Swarm-based metaheuristic algorithms
and no-free-lunch theorems. In Theory and New Ap-
plications of Swarm Intelligence. InTech.
Yang, X.-S. and Deb, S. (2009). Cuckoo search via l´evy
flights. In Proceedings of the World Congress on Na-
ture & Biologically Inspired Computing, pages 210–
214. IEEE.
Yang, X.-S. and He, X. (2013). Bat algorithm: Literature
review and applications. International Journal of Bio-
Inspired Computation, 5(3):141–149.
EnhancedIntrusionDetectionSystemBasedonBatAlgorithm-supportVectorMachine
189
