
INFORMATION-LEAKAGE IN
HYBRID RANDOMIZED PROTOCOLS
Stefan Rass and Peter Schartner
Institute of Applied Informatics, Universit¨at Klagenfurt, Universit¨atsstrasse 65-67, Klagenfurt, Austria
Keywords:
Information-theoretic security, Leakage-resilient cryptography, Protocol design, Game-theory, Multipath
transmission.
Abstract:
In light of the vast number of existing cryptographic protocols, performance tradeoffs become a major obstacle
when selecting one for practical usage. For instance, protocols known to be secure but inefficient compete
with others being efficient but offering less security. We tackle such tradeoffs by investigating sequences of
random protocol instances (randomized protocols) and analyzing the rate at which information leaks from
such a sequence. Remarkably, it can be demonstrated that the mutual information between an eavesdropped
ciphertext and the plain text decays exponentially fast with the length of the protocol sequence. Using simple
tools from game-theory, we devise a generic technique to assemble several protocols of different performance
into a single protocol, unifying the advantages of its ingredients. We call this a hybrid randomized protocol.
We illustrate our technique by using simplified multipath transmission as an example, while observing that
our general construction is in no way restricted to this scenario.
1 INTRODUCTION
Imagine an engineer being in charge of designing
the cryptographic protection for a given infrastruc-
ture. It is most advisable to choose from the vast
amount of available cryptographic primitives rather
than developing a novel proprietary solution. Exist-
ing protocols have the advantage of mostly being sci-
entifically well-studied and justified. However, most
of them are hardly comparable, so how should one
choose the best among the many? For instance, there
is AES with RSA-based key exchange, offering high
efficiency but merely conjectured security (resting on
computational intractability assumptions or empirical
evidence). On the contrary, there is multipath trans-
mission and quantum key distribution, known to offer
perfect secrecy at comparably high cost. A technique
to get the best of both worlds for a reasonable price is
certainly demanding, yet seems missing up to now.
Our contribution in this paper is a general construc-
tion that provides an affirmative answer to the follow-
ing problem:
Given a protocol Π
1
which is secure but de-
mands much bandwidth, and another protocol
Π
2
that is less secure but enjoys good effi-
ciency, can we somehow assemble those two
into a protocol that is efficient and secure?
Our solution will be a generic framework protocol
that takes several private message transmission pro-
tocols Π
1
,...,Π
n
as input and combines them into
a single protocol Π. Provided that at least one of
the ”input protocols”, say Π
1
, is perfectly secure, the
resulting scheme can be shown to be almost as se-
cure as Π
1
(theorem 4.2) and almost as efficient (in
terms of bandwidth demand) as the cheapest among
Π
1
,...,Π
n
(proposition 4.3). As the construction em-
ploys a random ensemble of instances from a class
of input protocols, we call this a hybrid randomized
protocol.
Research in the field of information-theoretic se-
curity has brought up a considerable number of cryp-
tographic primitives whose security does not hinge on
computational intractability conjectures. Often, this
comes at the price of increased efforts for key man-
agement, key establishment (e.g. via quantum key
distribution) or bandwidth demand (multipath trans-
mission is often based on Shamir’s threshold secret
sharing; it is known that every perfectly secure one-
round message transmission has a minimum relative
computational overhead of n/(n− 3t) for n bits to be
transmitted over t node-disjoint channels (cf. (Fitzi
et al., 2007)). Even if bandwidth is not the problem,
then finding t node-disjoint channels is yet another
significant obstacle in many networks). So one would
134
Rass S. and Schartner P..
INFORMATION-LEAKAGE IN HYBRID RANDOMIZED PROTOCOLS.
DOI: 10.5220/0003516401340143
In Proceedings of the International Conference on Security and Cryptography (SECRYPT-2011), pages 134-143
ISBN: 978-989-8425-71-3
Copyright
c
2011 SCITEPRESS (Science and Technology Publications, Lda.)

be willing to trade perfect secrecy for efficiency, and
our analysis shows how to do it safely.
The key observation made in this paper is that
perfect security can be created from arbitrarily weak
primitives in the sense that we do not need to be se-
cure in all cases, but only in an arbitrarily small frac-
tion of cases. In other words, once a – perhaps ex-
pensive – information-theoretically secure primitive
is available, we can easily turn it into a perfectly se-
cure and cheap system. The example application in
this paper will be private communication based on
multipath transmission.
Related Work: As we are after information-theoretic
secrecy, this work is closely related to information-
theory based cryptography, as well as conventional
cryptography. While previous approaches to perfectly
secure communication are mostly concrete ad-hoc so-
lutions, our contribution is a generic framework to
cook up a secure and efficient protocol from ingre-
dients that do not enjoy both features at the same
time. This is the major difference to the related
literature, as generic constructions are hardly avail-
able, if not absent at all. Generic constructions (to
which our results belong), are found rarely and widely
scattered throughout the literature (see the work of
(Fitzi et al., 2007; Srinathan et al., 2004) and refer-
ences therein; both of which can be used with our
generic construction). Among the few articles con-
cerned with generic security constructions are (Gu
et al., 2005), focusing on modeling mostly, (Noman,
2008), assuming a specific field of application, and
(Poels et al., 2005), hinging on a particular compu-
tational model. Our work is not restricted in any of
these ways, besides being about secure communica-
tion. In particular, our results can be used to make
otherwise costly primitives efficient, e.g. (Alomair
and Poovendran, 2009; Hanaoka et al., 2005; Kuro-
sawa and Suzuki, 2007). As far as conventional cryp-
tography is concerned, we will make use of a special
block-cipher mode, known as all-or-nothing transfor-
mation (AONT). This concept has been introduced in
(Rivest, 1997) and further studied in (Stinson, 2001).
Notably for us is also the field of leakage-resilient
cryptography (Alwen et al., 2009), though we deal
with Shannon-information leakage rather than phys-
ical attacks (through side-channels for instance). Our
work pursues similar goals as leakage-resilient cryp-
tography, yet uses different tools for that. In particu-
lar, we will utilize the framework of game-theoretic
security analysis, as proposed in (Rass and Schart-
ner, 2010). This approach will come handy and is,
for convenience of the reader, sketched in section 3,
stressing an example and repeating the basic results
required here.
Organization of the paper: we describe our security
and adversary model in section 2. In particular, we
will be after information-theoretic security, not call-
ing for any infeasibility conjectures. As the employed
framework is non-standard and thus not well-known,
we will use section 3 to describe how game-theory
can be used for security analysis of multipath trans-
mission. In particular, section 3.2 contains a brief
introduction to the theory of matrix games, which is
needed in the sequel. Our main result is the generic
construction given in section 4, along with the secu-
rity analysis culminating in theorem 4.2.
2 ADVERSARY AND SECURITY
MODEL
We assume a computationally unbounded passive
threshold adversary. That is, given a graph G = (V,E)
modeling the network at hand, at most t ≤ |V \ {s,r}|
nodes (excluding the sender s and receiver r) are un-
der control of an attacker. Without loss of generality,
we may assume the channels (u,v) ∈ E to be perfectly
protected, for otherwise we could simply insert an in-
termediate node w as u—w—v, whose compromis-
sion models an attack on the u—v-link.
The honest parties transmit a secret message M
from a sender s ∈ V to a non-adjacent receiver r ∈ V,
according to some protocol Π
x
(M), taking random
coin-flips x. Let trans(Π
x
(M)) denote the protocol
transcript, i.e. the set of all data that travels over
the network when the secret message M is sent us-
ing the parameters x. The adversary is assumed to
know the protocol Π, the network infrastructure, but
not the random coin-flips x (taking multipath trans-
mission as our case-study, this assumption is justified
since the parameter x is a local and thus secret input at
the sender’s side). Having a subset of nodes in G un-
der control, the adversary’s view isC ⊆ trans(Π
x
(M))
As the adversary is passive, we are not concerned
with reliability, and our main goals are privacy and
low bandwidth demand for the transmission from s
to r. In alignment with Shannon’s model of secret
communication (Shannon, 1949), the source s is a
Markov-process, drawing secret messages from its
stationary distribution.
Definition 2.1 (Security). Let Π
x
(M) be a protocol
using random coin-flips (protocol parameters) x for
transmitting a secret message M over a network. Let
the adversary’s view be C ⊆ trans(Π
x
(M)).
We call the protocol Π secure, if for any given ε >
0, one can choose (protocol parameters) x so that the
mutual information is I(M;C) < ε.
INFORMATION-LEAKAGE IN HYBRID RANDOMIZED PROTOCOLS
135

The idea behind randomized protocols is increas-
ing security by repeatedly executing a protocol while
enforcing the adversary to break all executions rather
than only a single one. This is an application of all-or-
nothing-transformations (Rivest, 1997). We will de-
scribe the construction for the particular case of a lin-
ear transformation, emphasizing that alternative con-
structions might do equally well. It is important to
notice that AONTs are usually a computationally se-
cure primitive, yet in the form we use it below, are
not resting on any complexity-theoretic intractability
assumption.
For a general protocolΠ
x
with some fixed parame-
ters and random coin-flips all represented by the input
x ∈ PS, call PS the parameter space of Π.
Definition 2.2 (Randomized Protocol). Let a proto-
col Π with parameter space PS be given. A ran-
domized protocol is a sequence {Π
x
i
|x
i
∼ F,i ∈ N},
where the distribution F is supported on PS, and
x ∼ F denotes the fact that the random parameter vec-
tors x
1
,x
2
,x
3
,... are drawn from the probability dis-
tribution F.
In section 3.2, we demonstrate how game theory
can be used to determine the optimal choice distribu-
tion F. In alignment with the terminology from game-
theory, we shall also call a particular parameter x ∈ PS
a strategy henceforth.
Security of a randomized protocol is ensured by
constructing it in a way such that the adversary must
extract information from all instances in the sequence
{Π(x
i
)|x
i
∼ F,i ∈ N} to gain insight on the secret in-
formation.
Bandwidth in our context captures the entire com-
munication overhead, and as such is not directly re-
lated to efficiency in the sense of short key-usage or
message-tags (Safavi-Naini et al., 2007).
3 SECURITY FROM
GAME-THEORY
For our construction and security analysis, we will
partially employ the framework introduced in (Rass
and Schartner, 2010). We will thus briefly review the
required concepts in this section.
3.1 Secure Multipath Transmission
It is known that multipath transmission (Ashwin Ku-
mar et al., 2002; Fitzi et al., 2007; Wang and
Desmedt, 2008) is one way of creating perfectly se-
cure end-to-end communication in the presence of
threshold adversaries. We will use such a scheme in a
very simplified version to describe the ideas underly-
ing the general construction in section 4. Similar con-
siderations, though not of game-theoretic flavor, are
found as well in (Srinathan et al., 2007; Araki, 2008).
Assume a multipath transmission from Alice to
Bob: Alice puts her secret message through a secret
sharing scheme with threshold k, and transmits each
share over its own distinct channel to the receiver,
where all these channels are assumed to be mutu-
ally node-disjoint. The scheme obviously works, as
long as the adversary Eve has less than k paths in-
tercepted
1
. Technically, Alice and the adversary Eve
play a game against each other, where Alice’s move
is the selection of paths (wires, channels), and Eve’s
move is a selection of compromised nodes. In this
simplified setting, the protocol Π
x
is the multipath
transmission scheme, and the parameter x is the par-
ticular choices of paths (explicitly including the ran-
dom coin flips used within the sharing is not required
for the example).
The problem is selecting these paths in the optimal
manner (provided that this is possible). In terms of
definition 2.2, if paths are selected on a random basis
to repeatedly transmit messages, then our task is to
find the optimal distribution F, according to which
these paths are chosen.
If Alice has n
1
choices for the paths, and Eve has
n
2
=
|V|−2
k
choices of subsets to be compromised, it
is easy to set up a (n
1
× n
2
)-tableau (matrix) A over
the set {0,1} with
a
ij
=
(
0, if Eve conquered ≥ k shares
1, otherwise,
(1)
so that the entry a
ij
indicates success (a
ij
= 1) or fail-
ure (a
ij
= 0) of Alice’s attempt to securely deliver her
secret over disjoint paths. The decision upon the value
of a
ij
is depending on the threshold of the secret-
sharing scheme and the adversary, and the commu-
nication overhead and computational effort for recon-
struction is depending on the chosen scheme.
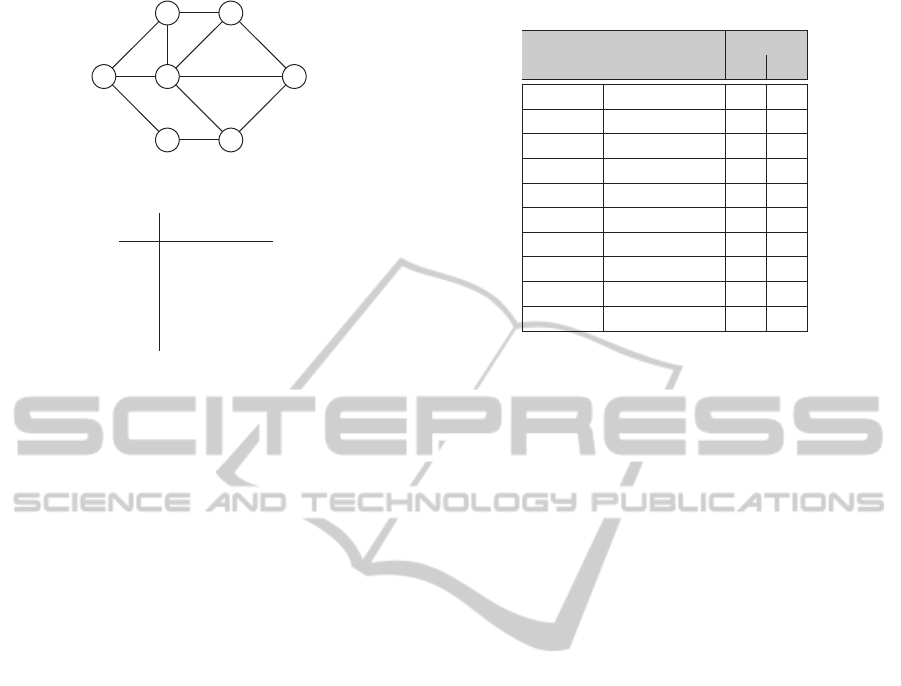
Example. Consider the network depicted in fig-
ure 1(a), and assume an adversary with threshold 2
and Alice (node s) executing a (2,2)-secret sharing
scheme to transmit her message to the receiver Bob
(node r). Her protocol parameter vector contains a se-
lection of two disjoint paths. Eve succeeds in extract-
ing the message if and only if she has compromised
both paths simultaneously. For the network shown in
1
Various criteria regarding the interplay between net-
work connectivity and the thresholds of the secret-sharing
and the adversary are found in (Franklin and Yung, 1995;
Franklin and Wright, 2000). We shall not go into details
here.
SECRYPT 2011 - International Conference on Security and Cryptography
136
1 2
3
4
5
s
r
(a) Transmission network
A s
E
1
s
E
2
s
E
3
s
A
1
0 1 1
s
A
2
1 0 1
s
A
3
1 1 0
(b) Game payoffs
Figure 1: Transmission game example.
figure 1(a), we end up identifying 9 admissible com-
binations of two paths, and Eve could have conquered
one pair from
5
2
= 10 possibilities (the complete list
is displayed in table 1). Making the decision for all
9×10 = 90 scenarios, we end up with a 9× 10-matrix
(we used a prototype implementation written in Java
to run examples).
If Alice chooses a strategy that performs worse
than another regardless what Eve does, then this strat-
egy would be a dumb choice and can (should) be
ignored. For player i, a strategy s
1
is said to dom-
inate another strategy s
0
, if the outcome under s
1
is at least as good as the outcome under s
0
, for all
(strategic) choices of the opponent, with strict in-
equality in at least one case. Formally, if s
i
,s
j
are at-
tack strategies with corresponding (payoffs) columns
c
i
= (a
1i
,...,a
ni
) and c
j
= (a
1j
,...,a
nj
), then s
i
dom-
inates s
j
, if and only if c
i
6= c
j
and c
i
≤ c
j
componen-
twise (recall that player 2’s objective is to minimize
the outcome, as he is the adversary and therefore the
”column-player”). Similarly, Eve will not attack in
a way that gives her a smaller chance of succeeding
than another in every possible scenario. To exemplify
this, consider the following two strategies for Alice,
referring to our multipath transmission example:
• s
A
0
: use paths s—3—5—r and s—1—2—r
• s
A
1
: use paths s—3—r and s—1—2—r
giving different outcomes depending on how Eve be-
haves; table 1 shows the complete list. Strategy s
A
1
obviously outperforms strategy s
A
0
, as giving as least
as good results in every case. Dominated strategies
are thus no more profitable than some other strategy,
and can thus safely be ignored either. Strategies with
all identical payoffs are obviously redundant and can
Table 1: Dominated strategies.
compromised payoff
strategy
nodes s
A
0
s
A
1
s
E
1
1,3 0 0
s
E
2
1,4 1 1
s
E
3
3,4 1 1
s
E
4
1,2 1 1
s
E
5
2,3 0 0
s
E
6
2,4 1 1
s
E
7
1,5 0 1
s
E
8
3,5 1 1
s
E
9
4,5 1 1
s
E
10
2,5 0 1
be ignored, thus the inequality condition c
i
6= c
j
above
is of no harm.
An analogous argument can be applied to the
columns. Carrying out this elimination of dominated
strategies repeatedly, we end up with a labeled 3× 3-
matrix, showing the outcomes for each combination
of relevant (i.e. undominated) strategies. This matrix
is depicted in figure 1(b). The corresponding strate-
gies for Alice in addition to s
1
from above are:
• s
A
2
: use paths s—4—5—r and s—1—2—r
• s
A
3
: use paths s—4—5—r and s—3—r
We will revisit the concept of dominance in section
4.4. Although the number of strategies can become
quite large for bigger networks, the number of un-
dominated strategies often remains small, as various
experiments using the Java-based implementation in-
dicated. This drastically reduces the computational
efforts tied to a game-theoretic treatment of crypto-
graphic protocols.
3.2 Elements of Matrix-Games
Let us introduce some basics of game-theory, stress-
ing the example for illustrative purposes. A fi-
nite non-cooperative n-person game is a triple Γ =
(N,PS,H), where N = {1, 2,...,n} is the set of play-
ers, PS = {PS
1
,...,PS
n
} is the family of finite strat-
egy spaces from which the players can choose their
actions, and H := {u
i
(x,y)|i ∈ N} is the set of pay-
offs for each player. These functions have the form
u
i
: PS
i
×PS
−i
→R, where PS
−i
is the cartesian prod-
uct
∏
j6=i
PS
j
, i.e. the joint strategy choices of i’s op-
ponents. A game is called zero-sum, if
∑
i∈N
u
i
= 0.
In our further treatment, we will exclusively refer to
two-person games, with player 1 being the honest pair
(s,r), and player 2 being the adversary. Furthermore,
our games will be zero-sum, adopting the worst-case
assumption that the adversary’s sole purpose is de-
INFORMATION-LEAKAGE IN HYBRID RANDOMIZED PROTOCOLS
137

feating the intended privacy of the transmission from
s to t.
Let us illustrate these concepts in terms of the
previous example, i.e. one-round multipath trans-
mission over the network G = (V,E): we have
the set of two players N = {s,adversary} with
strategy spaces PS
1
being Π’s parameter space
(ensembles of non-intersecting paths) and PS
2
=
{U ⊆ V \ {s,r}||U| ≤ t} (recall that the adversary
has threshold t). The payoff function for the honest
party (player 1) is exactly the indicator variable a
ij
given in equation (1). Hence, for this game (as well as
for finite games in general), the payoffs can be speci-
fied using matrices (hence the name matrix games).
A Nash-equilibrium for a (n-person) game Γ is
a joint strategy profile (s
∗
1
,...,s
∗
n
) ∈ PS
1
× ··· × PS
n
such that
u
i
(s
∗
i
,s
∗
−i
) ≥ u
i
(s
i
,s
∗
−i
) ∀s
i
∈ PS
i
∀i ∈ N, (2)
i.e. no player can gain by unilaterally deviating from
the equilibrium (as before, s
−i
denotes the vector with
the strategies of i’s opponents). It is easy construct ex-
amples where such profiles do not exist, but this can
be fixed by switching to randomized strategies: as-
sume an infinite number of repetitions of the game,
giving a sequence of payoffs for player 1. A mixed
strategy for the i-th player is a probability distribution
over PS
i
such that the expected payoff (i.e. the long-
run average) is maximized. Games as defined above
are trivially reformulated in terms of mixed strate-
gies, by replacing the payoff functions in (2) by their
expectations w.r.t. the mixed strategy, and replacing
PS
1
,...,PS
n
by the ensemble of probability distribu-
tions supported on PS
1
,...,PS
n
. We denote these sets
of mixed strategies by S(PS
1
),S(PS
2
),...,S(PS
n
).
For a two-player zero-sum matrix-game, as our ex-
ample gave rise to, the equilibrium condition (2) boils
down to
u(s
1
,s
∗
2
) ≤ u(s
∗
1
,s
∗
2
) ≤ u(s
∗
1
,s
2
), (3)
where u = u
1
= −u
2
and s
1
,s
2
are discrete proba-
bility distributions over PS
1
,PS
2
. Nash’s famous re-
sult (Nash, 1951) ensures the existence of such mixed
strategies in all finite games. The quantity
v(Γ) = max
s
1
∈S(PS
1
)
min
s
2
∈S(PS
2
)
u(s
1
,s
2
),
i.e. the best that player 1 can do, when player 2 tries
to maximize his own payoff (zero-sum regime), is
called the value of the game Γ. For matrix games,
it is easy to calculate this quantity by means of lin-
ear optimization (Gibbons, 1992). Obviously, using
zero-sum games might not accurately reflect the real
behavior of the adversary, yet it is a valid worst-case
scenario, since if the adversary has other intentions,
he will deviate from the 0-sum-equilibrium and thus
causing less damage that expected.
Hence, if Alice follows a zero-sum equilibrium
strategy when selecting her protocol parameters, then
the protocol will perform optimally in the long run. If
the payoff is an indicator variable, this means that Al-
ice can use the zero-sum equilibrium to find the opti-
mal rule for choosing the parameters for her protocol,
such that the probability of failure is minimized. In
other words, F (in definition 2.2) is precisely Alice’s
part in the Nash-profile. The quantity ρ(A) = 1−v(A)
can be interpreted as vulnerability, as it measures the
average rate of failure when executing the protocol
Π
x
repeatedly. For our example, we find v(A) = 2/3
and thus ρ(A) = 1 − v(A) = 1/3, provided that Alice
selects her paths with uniform probability (this is the
distribution F in definition 2.2).
Consequently, the average success rate in the zero-
sum regime lower-bounds the true success-rate, or, by
interpreting this success-rate as a probability, we have
Pr[Eve attacks successfully] ≤ 1− v(A) = ρ(A), (4)
whenever Alice draws her protocol parameters from
her equilibrium distribution F (cf. definition 2.2).
4 CONSTRUCTION OF
RANDOMIZED PROTOCOLS
Let us sketch the idea underlying our construction,
letting the details follow in the next section. Con-
sider Alice transmitting a sequence of plaintexts
M
1
,...,M
n
using n repetitions of a protocol Π with
a finite parameter space. Suppose that the proto-
col permits game-theoretic modeling so that in each
repetition i = 1,2, . . . , n, we can choose the param-
eters x
i
according to an optimal (Nash-equilibrium)
rule (i.e. maximizing the average success rate). Us-
ing an all-or-nothing transformation on the plain texts
M
1
,...,M
n
, we can enforce the adversary to succeed
in all n repetitions in order to extract a single message.
With an indicator variable for the k-th round, defined
as L
k
= 1 if and only if Π
x
k
fails to protect M
k
, we
have the following result (cf. (Rass and Schartner,
2010)):
Theorem 4.1. Fix any ε ≥ 0. Let a protocol Π with
parameter space PS
1
be given whose game-theoretic
payoff matrix is A ∈ {0,1}
|PS
1
|×|PS
2
|
for player 1 (hon-
est team ”Alice and Bob”), where PS
2
comprises all
attack strategies on Π. Let v(A) be the saddle-point
value of A, and put ρ(A) := 1− v(A). Suppose that
Alice runs n repetitions of the protocol Π, with pa-
rameters x
1
,...,x
n
drawn from the zero-sum (Nash-
)equilibrium rule for her. For the k-th round, define
SECRYPT 2011 - International Conference on Security and Cryptography
138

the indicator variable L
k
:= 1−a
ij
with i, j being the
strategies of player 1 and 2 in that round, so that
L
k
= 1 if and only if Π
x
k
fails. Then,
Pr
min
1≤k≤n
L
k
≥ ρ(A) + ε
≤ exp
−nε
2
2
.
Proof sketch. This result is established by first ob-
serving that the sum of n losses is upper-bounded
by nρ(A), using (4), and dividing by n for getting
the average loss. The minimum of losses obviously
lower-bounds the average, and the sum of losses can
be upper-bounded by a generalized version of Ho-
effding’s inequality, found in (Smith, 2005). The lat-
ter inequality is basically identical to Hoeffding’s re-
sult, except for its weaker stochastic independence
assumption, which is trivially satisfied in our set-
ting.
Our construction involves three steps:
1. Take a protocol Π allowing for a game-theoretic
modeling such as outlined in section 3. Make
sure that for the corresponding payoff matrix A,
we have ρ(A) = 1 − v(A) < 1.
2. Apply an all-or-nothing transformation to a se-
quence of plaintexts to be transmitted, and trans-
mit each resulting block using another instance of
Π with randomly chosen parameters.
3. Use theorem 4.1 to assure an exponentially small
chance to reveal any transmitted block, thus giv-
ing an overwhelming chance of keeping every-
thing secret (thanks to the all-or-nothing transfor-
mation).
In the next section, we put this to work, achieving
both, bandwidth efficiency and security at the same
time. The trick is to repeatedly and randomly switch
between protocols, one being secure and the other be-
ing efficient.
4.1 A Generic Protocol
In this section, we shall devise a generic construction
that allows for assembly of several protocols into a
single one such that retains security and improves the
performance. Let Π
1
,Π
2
denote two protocols, one
of which is secure but requires much bandwidth, the
other one being less secure but substantially more ef-
ficient. Assume that both protocols can be modeled as
described in section 3, giving rise to two binary matri-
ces A
1
,A
2
and quantities ρ(A
1
) = 1− v(A
1
),ρ(A
2
) =
1−v(A
2
) corresponding to Π
1
,Π
2
, respectively. Can-
didate protocols could, for instance, be multipath
transmissions using different thresholds or even dif-
ferent forms of secret sharing (such as polynomial
or Chinese remaindering based ones, etc.). Due to
the so-constructed protocol arising from two or more
other protocols, we call them hybrid (our construction
will be illustrated with two protocols, leaving the gen-
eralization to three or more as an obvious extension).
It is important to notice that the sender needs to fol-
low the Nash-profiles induced by the zero-sum games
A
1
,A
2
when running either protocol.
Let a sequence of stochastically independent messages
M
1
,... ,M
n
∈ F be given, where F is some (fixed) fi-
nite field. Without loss of generality, suppose that all
M
i
are equally long and drawn from the same source
(Alice) with entropy H(M
1
) = H(M
2
) = ... = H(M
n
).
Initialization: Select a switching probability p, satis-
fying 0 < p < 1. Let Q ∈ F
n×n
be an invertible
matrix over F having no zero entry. The matrix F
does not need to be secret, and can most trivially
be constructed by doing a Gauss-Jordan elimina-
tion ”backwards” (or by constructing Hadamard-
matrices if n− 1 is prime or a power of 2). Apply-
ing Q to the vector of messages (M
1
,... ,M
n
), we
end up with a vector of ”ciphertexts” C
1
,... ,C
n
.
Transmission: For i = 1,2,. ..,n, transmit C
i
by ran-
domly running either Π
1
with probability p, or
by executing Π
2
with probability 1 − p. In any
case, she selects current protocol parameters ac-
cording to her Nash-equilibrium strategy obtained
from the zero-sum games corresponding to the
game-matrices A
1
,A
2
for Π
1
,Π
2
respectively. The
receiver, upon getting all ”ciphertexts” C
1
,... ,C
n
can apply Q
−1
and the combining algorithm to re-
cover all plain text messages.
Figure 2: Randomized protocol Π composed from protocols
Π
1
,Π
2
.
The randomized protocol Π runs as shown in fig-
ure 2. The distribution F introduced in definition 2.2
is for both protocols obtained from their respective
Nash-equilibria.
Notice that assuming stochastic independence of
plaintexts might appear unusual, but is justifiable if
the sequence of ”messages” constitute a bunch of en-
cryption keys for subsequent encryption of payload.
4.2 Security Analysis
Theorem 4.2 constitutes our main result, regardingthe
efficiency and security of a randomized protocol.
Theorem 4.2. Let Π
1
,Π
2
be two protocols, with
game-matrices A
1
,A
2
over {0, 1} of the form
as sketched in section 3, giving the quantities
ρ(A
1
),ρ(A
2
). If min{ρ(A
1
),ρ(A
2
)} < 1, then the pro-
tocol Π as shown in figure 2 is secure in the following
INFORMATION-LEAKAGE IN HYBRID RANDOMIZED PROTOCOLS
139

sense: callC the adversary’s view on all n repetitions,
and let M = (M
1
,...,M
n
) denote the vector of n plain
text messages. Then, the information leakage I(M;C)
vanishes in the long run, i.e. I(M;C)→ 0 as n→∞.
Proof. The average rates of failure for both protocols
are ρ(A
1
) = 1− v(A
1
) and ρ(A
2
) = 1− v(A
2
), assum-
ing optimal (Nash-)strategies wheneverrunning Π
1
or
Π
2
. Without loss of generality, assume ρ(A
1
) < 1, and
(pessimistically), assume ρ(A
2
) = 1. This would cor-
respond to a case where Π
2
is doomed to failure (in
terms of secrecy) with probability 1. By switching
between Π
1
and Π
2
, we either get the (equilibrium)
outcome of Π
1
with probability p or observe a failure
(zero payoff) if Π
2
is chosen in the i-th round. The
resulting game-matrix A for Π (assuming ρ(Π
2
) = 1)
comes to A = pA
1
. The saddle-point mapping v(A)
is a homogeneous functional in A, so consequently,
ρ(A) = 1− pv(A) < 1 because 0 < pv(A
1
) = v(pA).
This average rate of failure cannot increase if Π
2
per-
forms better than we assumed, so the actual ρ(A) for
the real protocol Π
2
as well satisfies ρ(A) < 1 under a
random switching regime. To ease notation, we write
ρ for the rate of failure of the randomized protocol Π,
and note that ρ < 1 by our hypothesis.
By construction, the overall information flowing
over the network (disregarding any invertible trans-
formation performed by Π
1
or Π
2
) is (C
1
,...,C
n
)
T
=
Q· (M
1
,...,M
n
)
T
. Notice two core facts about the so-
constructed C
i
’s:
1. C
i
andC
j
are stochastically dependent for each i, j
2. If C
−i
denotes the vector of all C
j
’s excluding the
i-th entry, then
H(M
j
|C
−i
) = H(M
j
)
for all j = 1,2,...,n, as every M
j
is dependent
on M
i
because Q has no zero entries. Hence, if
the adversary’s view is C
−i
, he does not learn any-
thing, thanks to the all-or-nothing transformation
via Q.
Suppose C ⊆ {C
1
,...,C
n
} to be the adversary’s
view on the entire transmission (including all repeti-
tions). For an arbitrary i ≤ n, consider the information
C provides about M
i
. We have (by the second of the
above observations),
H(M
i
|C) =
(
0, if C suffices to disclose M
i
;
H(M
i
), otherwise.
Viewing these two cases within a probability tree per-
mits calculating the entropy as the sum of the root-
choice (”attack successful or not?”) and the weighted
sum of successive entropies (Shannon, 1948):
H(M
i
|C) = h(p
attack
) + (1− p
attack
)H(M
i
), (5)
where p
attack
is the likelihood of Eve disclosing M
i
upon her knowledge C, and h(x) := −[xlog(x) + (1−
x)log(1− x)] is the binary entropy function. Our task
is now upper-bounding p
attack
. This is done using the-
orem 4.1.
Introduce an indicator variable L
k
for each repeti-
tion (1 ≤ k ≤ n) that measure the loss in the k-th round
when transmitting C
k
:
L
k
=
(
1, if Eve catches C
k
;
0, otherwise.
By the all-or-nothing transformation, Eve is success-
ful in extracting M
i
from her information C, if and
only if L
1
= L
2
= .. . = L
n
= 1. If we choose ε :=
1− ρ > 0, then theorem 4.1 tells that
p
attack
= Pr
min
k=1,...,n
L
k
≥ ρ + ε
|{z}
=1
≤ exp
−
1
2
nε
2
,
and hence the probability of catching all messages
during an attack is exponentially small.
With this, we can lower-bound (5) as
H(M
i
|C) ≥
1− exp
−
1
2
nε
2
H(M
i
),
where we have used the fact that h(p
attack
) ≥ 0. Re-
calling that the mutual information is I(M
i
;C) =
H(M
i
) − H(M
i
|C), we end up concluding that within
n repetitions of a protocol, the mutual information be-
tween the secret M
i
and the full transcriptC (capturing
all repetitions) satisfies
I(M
i
;C) ≤ 2
−O (n)
· H(M
i
), (6)
Now, consider the (joint) mutual information
I(M;C) = I(M
1
,...,M
n
;C) in the following: observe
that Pr[C|M
i
] = Pr[C], sinceC involves more than just
M
i
, and can be considered as a ”one-time pad en-
crypted” version of M
i
for each i. Conversely, know-
ing the full transcript C indeed provides information
on M
i
, so we have the following view on the stochas-
tic dependencies among M
1
,...,M
n
and C (Bayesian
network):
C
M
1
M
2
M
n
···
It is easy to verify that the variable particular M
j
’s
are d-separated via C (cf. (Koski and Noble, 2009)),
and hence conditionally independent given C, i.e.
Pr[M
i
,M
j
|C] = Pr[M
i
|C]Pr[M
j
|C] . (7)
SECRYPT 2011 - International Conference on Security and Cryptography
140

This implies that I(M
1
,...,M
n
;C) ≤
∑
n
i=1
I(M
i
;C)
(we skip the tedious details here; the derivation is
found in the appendix).
Applying (6) to upper-bound the terms on the
right-hand side, we get
I(M;C) ≤ n2
−O (n)
n
∑
i=1
H(M
i
) = n2
−O (n)
H(M),
because the variables M
1
,M
2
,...,M
n
are stochasti-
cally independent. Hence, the information leakage
vanishes for long sequences of messages, because
n2
−O (n)
→0 as n→∞.
The number of iterations, and therefore the size
of the mixing matrix Q will eventually increase, and
one is free to choose p to find a reasonable balance
between security and computational cost. Still, the
scheme becomes more and more efficient for long se-
quences of messages (the effort for applying Q and
inverting it is polynomial anyway).
We wish to remark some important facts about
theorem 4.2:
Remark 1. The converse of theorem 4.2 is also true:
if min{ρ(A
1
),ρ(A
2
)} = 1, then v(A
1
) = v(A
2
) = 0.
This means that an adversary actually playing a
Nash-strategy in the zero-sum game will disclose any
secret content with probability 1. Consequently, the
joint randomized protocol Π can no longer be secure.
Remark 2. The dependencies introduced by the ma-
trix Q make the scheme vulnerable against a denial-
of-service, if only one of the C
i
’s becomes damaged.
So, the scheme is secure only against passive adver-
saries. Gaining resilience against an active adversary
is a yet open issue, but detecting such an incident is
very simple: any cryptographic checksum attached to
any plain text message M
i
(a single one suffices) will
most likely become invalidated when any of the C
j
’s
is modified. This can be detected on the receiver’s
side, thus making the scheme kind of non-malleable
at negligible additional cost.
4.3 Performance
The bandwidth demand analysis of our generic con-
struction is obvious, and hence its proof is omitted:
Proposition 4.3. The bandwidth demand of the hy-
brid randomized protocol Π’s can be lowered ar-
bitrarily close towards min{B(Π
1
),B(Π
2
)}, where
B(Π
1
),B(Π
2
) denote the bandwidth demands of
Π
1
,Π
2
, respectively.
Comparing our protocol to others in terms of
round- and communication-complexity is difficult,
as both features are inherited from the underlying
”input-protocols” and are thus subject to the partic-
ular implementation at hand. Hence, if the protocol
of (Fitzi et al., 2007) is used, one can achieve the the-
oretical one-round communication overhead in each
iteration, performing arbitrarily close to the theoreti-
cal minimum overhead. Similarly, one can instantiate
our construction with the two-round communication
scheme by (Srinathan et al., 2004), which is as well
close to the theoretical optimum in terms of overhead
for two-round schemes.
4.4 Attack Resilience from Dominance
The condition in theorem 4.2 that at least one of
Π
1
,Π
2
needs to exhibit a strictly positive chance of
success (i.e. v(A
i
) > 0 for at least one i) deserves a
closer look.
Loosely speaking, if we underestimated the adver-
sary’s capabilities, then there might be a way of en-
tirely breaking the protocol Π. In the game-theoretic
model, this manifests itself as a winning strategy for
player 2, making ρ(A
i
) = 1. We will derive a general
result (theorem 4.4) that provides hints on how to fix
the protocol (more precisely its game-theoretic pay-
off matrix) in order to avoid winning strategies for the
adversary.
Dominating (i.e. winning) strategies arise if
we underestimated the adversary’s capabilities, i.e.
threshold. Indeed, if the adversary does not have a
threshold or the threshold has mistakenly been as-
sumed too low, then one column in A
i
appears for
the adversary that outperforms all others in the sense
that v(A
i
) = 0 in this case. This new column corre-
sponds to a strategy that entirely breaks the protocol
and makes the whole transmission insecure. If we can
avoid this situation in at least one scenario, then secu-
rity can be fully restored. Our next result makes this
intuition rigorous.
Theorem 4.4. Take a real number M > 0. Let A ∈
[0,M]
n×m
be a game-matrix with value v(A) > 0. Ex-
tend A by one column c for the adversary, such that c
does not dominate all columns in A, and write (A|c)
for the so-extended matrix. Then v((A|c)) > 0.
Proof. Put B := (A|c) with the column c =
(c
1
,...,c
n
), and write e
i
for the i-th unit vector. Be-
cause c does not dominate every column in B, some
j > 0 with corresponding column c = (a
1j
,...,a
mj
)
exists, having a
ij
< c
j
at some index i ∈ {1,... , n}.
Let (x, y) be any strategy profile for the game in-
duced by the matrix B. If y = (0,...,0,1), then
v(B) = x
T
By = x
T
c = c
j
> a
ij
≥ 0 if x = e
i
is played.
Now, suppose that y 6= (0, 0,...,1) and write y =
(y
1
,...,y
m
,y
m+1
) = (y
1:m
,y
m+1
). Furthermore, let
INFORMATION-LEAKAGE IN HYBRID RANDOMIZED PROTOCOLS
141

(x
∗
,y
∗
) be a Nash-equilibrium of the game induced
by the matrix A. Assume that player 1 plays x
∗
, then
(x
∗
)
T
By equals
(x
∗
)
T
(A|c)
y
1:m
y
m+1
!
= (x
∗
)
T
Ay
1:m
+
≥0
z }| {
y
m+1
(x
∗
)
T
c
≥ (x
∗
)
T
Ay
1:m
.
From y
m+1
< 1 we deduce y
1:m
6= 0, and some λ :=
(
∑
m
i=1
y
i
)
−1
> 0 exists, rendering λy
1:m
a probability
distribution. From the saddle-point property (3) of the
equilibrium (x
∗
,y
∗
) in the game with matrix A, we get
v(A) = (x
∗
)
T
Ay
∗
≤ (x
∗
)
T
A(λy
1:m
)
and subsequently (x
∗
)
T
Ay
1:m
≥
1
λ
v(A) > 0. So, for
any adversarial strategy y, player 1 can find some x
giving positive revenue, so v(B) > 0.
Rephrasing the result, this means that if there is
a winning strategy for the adversary, then only one
scenario needs to be fixed in order to restore security
of the overall protocol.
Stressing the example from section 3 a last time,
a winning strategy s
E
4
for the adversary would corre-
spond to a new column in A, dominating all others.
We denote this matrix by A
1
. If there is at least one
entry (scenario) such that the adversary looses, then
security can be restored. In the example, the matrix A
1
has v(A
1
) = 0, while the matrix A
2
has v(A
2
) = 1/2.
A
1
s
E
1
s
E
2
s
E
3
s
E
4
s
A
1
0 1 1 0
s
A
2
1 0 1 0
s
A
3
1 1 0 0
A
2
s
E
1
s
E
2
s
E
3
s
E
4
s
A
1
0 1 1 1
s
A
2
1 0 1 0
s
A
3
1 1 0 0
5 REMARKS AND
CONCLUSIONS
It is known that the linear transformation of
M
1
,...,M
n
via the matrix Q used in the proof of theo-
rem 4.2 is insecure if the M
i
’s are in some well-known
redundancy scheme (the argument is the same as for
the insecurity of Vernam’s one-time pad when a key
is used twice). Hence, the framework protocol is best
suited for key-exchange and a later cryptographic ap-
plication (such as the one-time pad for instance). It
should, however, be noticed that the security proof
does not apply to lengthy messages being split into
several blocks, due to the assumption of stochastic in-
dependence among these blocks.
Therefore, a natural application of our construc-
tion is within infrastructures with back-bone net-
works, claiming to provide perfect security. If we ex-
clude attacks from an insider of an infrastructure, then
the outgoing gateway might collect traffic and trans-
mit a whole chunk of messages to another network
interface gateway, doing the decryption (according to
our framework protocol) and further dispatching of
messages within the other secure environment.
An open issue with our construction of the ran-
domized protocol is making it resilient against ac-
tive adversaries, as remark 2 merely permits detect-
ing a modification, but in no way prevents it. Finally,
it is interesting to notice a further conclusion drawn
from theorem 4.4 in light of remark 1: if the game-
theoretic model comes up with the average success-
rate 1, then this proves that there is an adversary, able
to break the entire scheme. Hence, if the thresh-
old assumptions is mistaken, theorem 4.4 tells that
pretty much the only way of remaining secure against
a non-threshold adversary is having an auxiliary se-
curity mechanism, which with some positive proba-
bility does work against this adversary. In the latter
case, however, theorem 4.2 ensures that we can fully
recover from such strong attacks.
REFERENCES
Alomair, B. and Poovendran, R. (2009). Information theo-
retically secure encryption with almost free authen-
tication. Journal of Universal Computer Science,
15(15):2937–2956.
Alwen, J., Dodis, Y., and Wichs, D. (2009). Survey: Leak-
age resilience and the bounded retrieval model. In
Kurosawa, K., editor, Proceedings of the 4th Interna-
tional Conference on Information-Theoretic Security
(ICITS), pages 1–18. Springer.
Araki, T. (2008). Almost secure 1-round message trans-
mission scheme with polynomial-time message de-
cryption. In Safavi-Naini, R., editor, Proceedings
of the 3rd International Conference on Information-
Theoretic Security (ICITS), pages 2–13. Springer.
Ashwin Kumar, M., Goundan, P. R., Srinathan, K., and
Pandu Rangan, C. (2002). On perfectly secure com-
munication over arbitrary networks. In PODC ’02:
Proceedings of the twenty-first annual symposium on
Principles of distributed computing, pages 193–202,
New York, NY, USA. ACM.
Fitzi, M., Franklin, M. K., Garay, J., and Vardhan, S. H.
(2007). Towards optimal and efficient perfectly secure
message transmission. In Vadhan, S., editor, Theory
of Cryptography, 4th Theory of Cryptography Confer-
ence, TCC 2007, Lecture Notes in Computer Science
LNCS 4392, pages 311–322. Springer.
Franklin, M. and Wright, R. (2000). Secure communication
in minimal connectivity models. Journal of Cryptol-
ogy, 13(1):9–30.
SECRYPT 2011 - International Conference on Security and Cryptography
142

Franklin, M. and Yung, M. (1995). Secure hypergraphs:
privacy from partial broadcast. In Proceedings of the
twenty-seventh annual ACM symposium on Theory of
computing, STOC ’95, pages 36–44, New York, NY,
USA. ACM.
Gibbons, R. (1992). A Primer in Game Theory. Pearson
Education Ltd.
Gu, Y., Fu, Y., Li, Y., and Dong, X. (2005). A generic
model for symbolic analyzing security protocols. In
The Fifth International Conference on Computer and
Information Technology (CIT), pages 680–684.
Hanaoka, G., Shikata, J., Hanaoka, Y., and Imai, H.
(2005). Unconditionally secure anonymous encryp-
tion and group authentication. The Computer Journal,
49(3):310–321.
Koski, T. and Noble, J. M. (2009). Bayesian Networks. Wi-
ley Series in Probability and Statistics. Wiley.
Kurosawa, K. and Suzuki, K. (2007). Almost secure (1-
round, n-channel) message transmission scheme. In
Desmedt, Y., editor, Proceedings of the Second Inter-
national Conference on Information-Theoretic Secu-
rity (ICTIS), pages 99–112. Springer.
Nash, J. F. (1951). Non-cooperative games. Annals of Math-
ematics, 54:286–295.
Noman, A. (2008). A generic framework for defining se-
curity environments of wireless sensor networks. In
International Conference on Electrical and Computer
Engineering (ICECE), pages 924–929.
Poels, K., Tuyls, P., and Schoenmakers, B. (2005).
Generic security proof of quantum key exchange us-
ing squeezed states. In Proceedings of the Inter-
national Symposium on Information Theory (ISIT),
pages 1612–1616.
Rass, S. and Schartner, P. (2010). A unified framework
for the analysis of availability, reliability and security,
with applications to quantum networks. IEEE Trans-
actions on Systems, Man, and Cybernetics – Part C:
Applications and Reviews, 40(5):107–119.
Rivest, R. L. (1997). All-or-nothing encryption and the
package transform. In Proceedings of the 4th Inter-
national Workshop on Fast Software Encryption, FSE
’97, pages 210–218, London, UK. Springer-Verlag.
Safavi-Naini, R., Wang, S., and Desmedt, Y. (2007). Un-
conditionally secure ring authentication. In Proceed-
ings of the 2nd ACM symposium on Information, com-
puter and communications security, ASIACCS ’07,
pages 173–181, New York, NY, USA. ACM.
Shannon, C. (1948). A mathematical theory of communica-
tion. Bell System Technical Journal, 27:379–423 and
623–656.
Shannon, C. (1949). Communication theory of secrecy sys-
tems. Bell System Technical Journal, 28:656–715.
Smith, W. D. (2005). Tail bound for sums of bounded ran-
dom variables. http://www.math.temple.edu/∼wds/
homepage/works.html.
Srinathan, K., Narayanan, A., and Pandu Rangan, C.
(2004). Optimal perfectly secure message transmis-
sion. In CRYPTO, pages 545–561.
Srinathan, K., Pandu Rangan, C., and Kumaresan, R.
(2007). On exponential lower bound for protocols for
reliable communication in networks. In Desmedt, Y.,
editor, Proceedings of the Second International Con-
ference on Information-Theoretic Security (ICTIS),
pages 89–98. Springer.
Stinson, D. R. (2001). Something about all or noth-
ing (transforms). Designs, Codes and Cryptography,
22:133–138.
Wang, Y. and Desmedt, Y. (2008). Perfectly secure message
transmission revisited. IEEE Transactions on Infor-
mation Theory, 54(6):2582–2595.
APPENDIX
Details to the Proof of Theorem 4.2. Recall the con-
ditional independence of M
i
and M
j
given C, which
manifests itself though formula 7, which was
Pr[M
i
,M
j
|C] = Pr[M
i
|C]Pr[M
j
|C] .
For the conditional entropy H(M
i
,M
j
|C) we find (de-
noting the respective densities as π, and letting all
sums run over all values of m
i
,m
j
,c)
H(M
i
,M
j
|C) = −
∑
π(m
i
,m
j
,c)logπ(m
i
,m
j
|c)
(7)
=
∑
π(m
i
,m
j
,c)log[π(m
i
|c)π(m
j
|c)]
= −
∑
π(m
i
,m
j
,c)logπ(m
i
|c)
−
∑
π(m
i
,m
j
,c)logπ(m
j
|c). (8)
Equation (7) implies for the joint distribution
Pr[M
i
,M
j
,C] = Pr[M
i
,M
j
|C]Pr[C] =
Pr[M
i
|C] Pr[M
j
|C] Pr[C] .
Plugging this into (8) gives
H(M
i
,M
j
|C) = −
∑
π(m
j
|c)
| {z }
≤1
π(m
i
|c)π(c)
| {z }
=π(m
i
,c)
logπ(m
i
|c)
−
∑
π(m
i
|c)
| {z }
≤1
π(m
j
|c)π(c)
| {z }
=π(m
j
,c)
logπ(m
j
|c)
≥ H(M
i
|C) + H(M
j
|C) (9)
From this, we obtain for the conditional information
for any fixed choice of i, j
I((M
i
,M
j
);C) = H(M
i
,M
j
) − H(M
i
,M
j
|C)
(9)
≤ H(M
i
) + H(M
j
) − (H(M
i
|C) + H(M
j
|C))
= I(M
i
;C) + I(M
j
;C)
and on iterating, I(M
1
,...,M
n
;C) ≤
∑
n
i=1
I(M
i
;C), re-
calling that the adversary does not conquer the full C
by our construction and theorem 4.1 applied to the
randomized protocol in figure 2.
INFORMATION-LEAKAGE IN HYBRID RANDOMIZED PROTOCOLS
143
