
INTELLIGENT MOBILE SAFETY SYSTEM TO EDUCATIONAL
ORGANIZATION
Li-Shan Chen
Department of Information Management, Fortune Institute of Technology
No. 1-10, Nongchang Rd., Daliao Township, Kaohsiung County 83160, Kaohsiung, Taiwan (R.O.C.)
Keywords Swarm Intelligence, Active Ultra-High Frequency, RFID, Human-Computer-Interface, After-School
Remedial Education.
Abstract This study aims to develop safety system, and let the system become intelligent. We adopt the swarm
intelligence and active Ultra-High Frequency RFID for safety system, and develop friendly
human-computer-interface software for users use the personal digital assistants. We program the system and
software with Extensible Markup Language (XML) and C sharp language. If the users begin to search, the
kernel safety system automatically communicates with other RFID readers by agents, and the agents can
search the closer camera for users. This study’s result has successfully implemented to one educational
organization, and it would be helpful for the paterfamiliases to hold all situations about their children at the
educational organization. That will be great help in the grip of whole after-school remedial education,
teaching and learning situation. We select 100 paterfamiliases to test this system and software. It is revealed
that 93% of the paterfamilias are satisfied with the system (Strongly agree:25/100; Agree:68/100;
Disagree:5/100; Strongly disagree:2/100). The software searching correctness is 95% (Strongly agree:
30/100; Agree:65/100; Disagree:3/100; Strongly disagree:2/100).
1 INTRODUCTION
Technological developments in content-based
analysis of digital video information are undergoing
much progress, with ideas for fully automatic
systems now being proposed and demonstrated
(Hyowon, Alan, Noel, & Barry, 2006). Effective
agent teamwork requires information exchange to
be conducted in a proactive, selective, and
intelligent way (Fan, Wang, Sun, & Yen, 2006).
Self-managing systems (i.e. those that
self-configure, self-protect, self-heal and
self-optimize) are the solution to tackle the high
complexity inherent to these networks (Barco,
Lázaro, Díez, & Wille, 2008) Digital
representations are widely used for audiovisual
content, enabling the creation of large online
repositories of video, allowing access such as video
on demand (Justin & Timothy, 2006). Digital
artifacts created via transformational technologies
often embody implicit knowledge that must be
correctly interpreted to successfully act upon the
artifacts (Leonardi & Bailey, 2008) With continued
advances in communication network technology
and sensing technology, there is astounding growth
in the amount of data produced and made available
through cyberspace (Chen & Liu, 2006). Felfernig
et al., (2009) focus on the first aspect and present an
approach which supports knowledge engineers in
the identification of faults in user interface
descriptions. Chen (2009) adopts the Windows
Media Player along the RTP/RTSP protocol in order
to embed the mobile information system into the
users’ machines (personal digital assistants or smart
phones), and provides a solution (including
hardware solutions) to promote campus safety
management. He also combines the swarm
intelligence and Web Services to transform a
conventional library system into an intelligent
library system having high integrity, usability,
correctness, and reliability software for readers
(Chen, 2008, 2010). L. S. Chen, and S. L. Chen
(2007) built the intelligent system and developed a
knowledge base of the computer-parts. Jannach,
Leopold, Timmerer, and Hellwagner (2006) present
a novel, fully knowledge-based approach for
55
Chen L. (2010).
INTELLIGENT MOBILE SAFETY SYSTEM TO EDUCATIONAL ORGANIZATION.
In Proceedings of the International Conference on e-Business, pages 55-62
DOI: 10.5220/0002977900550062
Copyright
c
SciTePress

building such multimedia adaptation services,
addressing the above mentioned issues of openness,
extensibility, and concordance with existing and
upcoming standards.
This study adopts the swarm intelligence and
active Ultra-High Frequency RFID for safety
system, and develop friendly human computer
interface software for users use the personal digital
assistants (PDAs). We program the system and
software with Extensible Markup Language (XML)
and C sharp language. If the users begin to search,
the kernel safety system automatically
communicates with other RFID readers by agents,
and the agents can search the closer camera for
users.
2 RELATED WORK
2.1 For Mobile Communication
Malek and Frank (2006) have focused on
determining a near-optimal collision-free path
because of its importance in robot motion planning,
intelligent transportation systems, and any
autonomous mobile navigation system. A spanning
tree is based on the autoconfiguration of mobile ad
hoc networks and a novel approach for efficient
distributed address autoconfiguration (Li, Cai, &
Xu, 2007). Pavlou, Huigang, and Yajiong (2007)
build upon the principal–agent perspective to
propose a set of four uncertainty mitigating
factors—trust, Web site informativeness, product
diagnosticity, and social presence. A neural network
is trained to learn the correlations and relationships
that exist in a dataset (Kaikhah and Doddament,
2006). Gao and Zhang (2008) have proposed an
effective technique to determine the number and
distribution of equilibria and a new supervised
linear feature extraction technique for multiclass
classification problems particularly suited to the
nearest-neighbor classifier technique (Masip and
Vitria, 2008). Wang and Chen (2008) present a
new method for evaluating students’ answer scripts
using vague values, where the evaluating marks
awarded to the questions in the students’ answer
scripts are represented by vague values. Payne
(2008) examines the Web service paradigm from an
open multiagent system perspective and contrasts
the formally grounded knowledge-centric view of
agents with a pragmatic declarative bottom-up
approach adopted by Web services. The
location-based spatial queries having certain unique
characteristics can be revealed, which traditional
spatial query processing systems employed in
centralized databases do not address (Ku,
Zimmermann, & Wang , 2008). Lee and Wang
(2009) present an ontology-based computational
intelligent multi-agent system for Capability
Maturity Model Integration (CMMI) assessment.
Medium access control protocols have
quality-of-service support—topology-independent
link activation transmission scheduling—for mobile
code-division multiple-access ad hoc networks (Su,
Su, & Li, 2008). The context-aware query
processing system enhances the semantic content of
Web queries using two complementary knowledge
sources: lexicons and ontologies (Storey, Jones,
Sugumaran, & Purao, 2008). Yap, Tan, and Pang
(2008) propose the Explaining BN Inferences (EBI)
procedure for explaining how variables interact to
reach conclusions.
2.2 For RFID Systems
Broekmeulen, and Donselaar (2009) suggest a
replenishment policy for perishable products which
takes into account the age of inventories and which
requires only very simple calculations. Zhou (2009)
takes a different perspective by modeling item-level
information visibility in general. Delgado, Ros, and
Vila (2009) present a system that is able to process
the information provided by a Tagged World to
identify user’s behavior and to produce alarms in
dangerous situations. Abad et al., (2009) present
important advantages regarding conventional
traceability tools and currently used temperature
data loggers such as more memory, reusability, no
human participation, no tag visibility needed for
reading, possibility of reading many tags at the
same time and more resistance to humidity and
environmental conditions. Lee, and Chan (2009)
propose a genetic algorithm to determine such
locations in order to maximize the coverage of
customers. Also, the use of RFID is suggested to
count the quantities of collected items in collection
points and send the signal to the central return
center. Angeles (2009) looks at the perceived ability
of components of IT infrastructure integration and
supply chain process integration to predict specific
radio frequency identification (RFID) system
deployment outcomes exploration, exploitation,
operational efficiency, and market knowledge
creation.
ICE-B 2010 - International Conference on e-Business
56

2.3 For Swarm Intelligence
Tabu search and ant colony perform better for
large-sized problems, whereas simulated annealing
is optimal for small-sized problems and it is
therefore essential that a maintenance scheduling
optimizer can incorporate the options of shortening
the maintenance duration and/or deferring
maintenance tasks in the search for practical
maintenance schedules. Allahverdi and Al-Anzi
(2008) addressed a two-stage assembly flow-shop
scheduling problem with a weighted sum of
makespan and mean completion time criteria,
known as bicriteria. The learners and lecturers agree
that style-based ant colony systems can provide
useful supplementary learning paths (2008). Ant
colony intelligence (ACI) is proposed to be
combined with local agent coordination in order to
make autonomous agents adapt to changing
circumstances, thereby yielding efficient global
performance. This indicates that the ACO algorithm
is an optional compromise strategy between
preferable phase unwrapping precision and
time-consuming computations.
3 METHODOLOGY
This study adopts the active Ultra-High Frequency
RFID and swarm intelligence for safety system, and
develop friendly human computer interface
software for users use the personal computers or
notebooks. The system is developed in the
environment of: Microsoft Windows Server 2008,
Internet Information Services 7.0 (IIS 7.0),
Microsoft Structured Query Language (MS SQL)
Server 2008, and Visual Studio 2008 (VS 2008).
The programming languages are Extensible Markup
Language (XML) and C#.
3.1 RFID System Framework
Figure 1 shows the framework of RFID system.
3.2 Searching Design
The searching path of this study is from (Agents
Generator) to (Reader)
i
and the distance of
(Agents Generator) to (Reader)
i
is the closest, as
shown in Figure 2. The searching path begins at
(Agents Generator), and it has two choice. One is
(Reader)
1
, and the other is (Reader)
2
. Because the
Figure 1: Framework of RFID system.
Figure 2: Searching Path.
distance of (Agents Generator) to (Reader)
1
is
shorter than (Agents Generator) to (Reader)
2
, the
optimum searching path is (Agents Generator) to
(Reader)
1
. And so forth, the optimum searching path
is “(Agents Generator) →(Reader)
1
→(Reader)
3
→(Reader)
2
→…”. Figure 2 shows the searching
process. This study amends the ant algorithm of
Birattari, Pellegrini, and Dorigo (2007). It can let
the safety system become intelligent and mobility.
The design of the “Agents Generator” is very
important, and it is the kernel technology in this
study. The developing process is described as below.
(Note: The agents are seemed as the ants.)
3.3 Meaning of the Symbols
and Nouns
(a) n: The numbers of RFID readers
(b) m= Σ
k= 1to n
b
i
(t): The total agents
b
n
(t): The numbers of agents in the (Agents
Generator)
(c) d
ij
: The distant of (Agents Generator) to
(Reader)
i
; This study considers that it is
INTELLIGENT MOBILE SAFETY SYSTEM TO EDUCATIONAL ORGANIZATION
57

symmetrical; therefore, d
ij
is equal to d
ji
(d) τ
ij
(t): The intensity of pheromone upper edge
τ
i
j
(t) =
ρ
τ
i
j
(t) + Δτ
i
j
(1)
This study uses (Eq. 1) to update the
pheromone.
ρ:The parameters of pheromone evaporation
Δτ
ij
= Σ
k=1
to m Δτ
ij
k
(2)
(e) Δτ
ij
k
:The kth agent remains pheromone going
through the edge (i, j). It is defined as equation
3.
Q:The influential parameter of the pheromone
L
K
: The total length of the route, and the kth
agent goes all over the (Readers)
Δτ
ij
k
= Q / L
K
, The Kth agent goes through
edge (i, j) between time point t and (t + t
i
)
Δτ
ij
k
= 0, Otherwise
(3)
(f) R:The cycles counter agent goes through all
of the readers, and the R
max
is the upper limit
of R
(g) Tabu
k
(I): The record of the kth has gone
through the re, anaders the “I “is to mak a visit
to “Ith”reader. It can prevent the agent from
going back to cities already visited.
(h) μ
ij
: The inverse of the distance of (Agents
Generator) to (Reader)
i
μ
ij
= 1 / d
ij
(4)
(i) P
ij
k
(t): The probability that kth agent goes
from (Agents Generator) to (Reader)
i
Set Φ = k ∈ ( n – Tabu
k
( I ) )
P
ij
k
(t) =【τ
ij
(t)】
α
【
μ
ij
】
β
/
Σ
Φ
【τ
ik
(t)】
α
【
μ
ik
】
β
if j ∈ ( n – Tabu
k
( t ) )
(5)
Otherwise P
i
j
k
(t) = 0 (6)
The
α
and
β
are the important controlled
parameters of pheromone information and
μ
ij
.
3.4 Designing Steps
The designing steps are described below.
Step 1: Set t=0、R= 0 (”t” is the time counter, and
“R” is the cycles counter)For all edge (i, j),
Set τ
ij
(t) = Constant, Δτ
ij
(t) = 0. To put m
agents into n readers
Step 2: Set I=1 (”I” is Tabu list index). For k = 1 to
m (The record of the kth agent is listed in
Tabu
k
(I) at agents generator.)
Step 3: Set I= I +1. For k = 1 to m (Using equation
5 to decide (Reader)
i
and moving the kth
agent to (Reader)
i
recorded in Tabu
k
(I).)
Step 4: For k = 1 to m do .To move the kth agent
from Tabu
k
(n) to Tabu
k
(1) and calculate the
total length of all paths recorded, and update
the shortest path. To calculate each edge (i, j).
For k = 1 to m do. Δτ
i j
=Δτ
ij
+ Δτ
ij
k
Step 5: By τ
i j
( t + t
1
) = ρτ
i j
(t) + Δτ
i j
, Calculates τ
i j
( t + t
1
) for each edge (i, j). Set t = t + t
1
,
R = R + 1 for each edge (i, j). Set Δτ
ij
= 0 for
each edge (i, j)
Step 6: If ( R < R
max
) and (No entering in stop
situation) Then clear the entire Tabu list . Go
To Step 2. Else print the shortest path and
stop.
4 RESULTS AND DISCUSSION
4.1 Results
The safety system has been successfully developed,
as shown in Figure 3-8. Figure 3 is the “login
frame”, and Figure 4 is “Welcome frame”. There
are eight areas in this system; (1) The left side of
the gate, (2) The right side of the gate, (3) The
eastern side of the house, (4) House Back, (5)
Classroom 1, (6) Classroom 2, (7) Office, (8)
Leisure area, see as Figure 5. Figure 6, Figure 7,
and Figure 8 are searching results. For example, the
user “missyang” logins to the system. The system
will tell her that she has three children in the
educational organization. One is in the classroom 1,
Figure 3: Login Frame.
ICE-B 2010 - International Conference on e-Business
58

Figure 4: Welcome Frame.
Figure 5: Eight area.
another is in the classroom 2, and the other is in the
leisure area. The missyang can push the “Welcome”
key, and enter the choosing frame “Figure 5”. She
can choose and push the g, h, or j to watch her
children's situations.
Figure 6: Searching Results.
Figure 7: Searching Results.
INTELLIGENT MOBILE SAFETY SYSTEM TO EDUCATIONAL ORGANIZATION
59
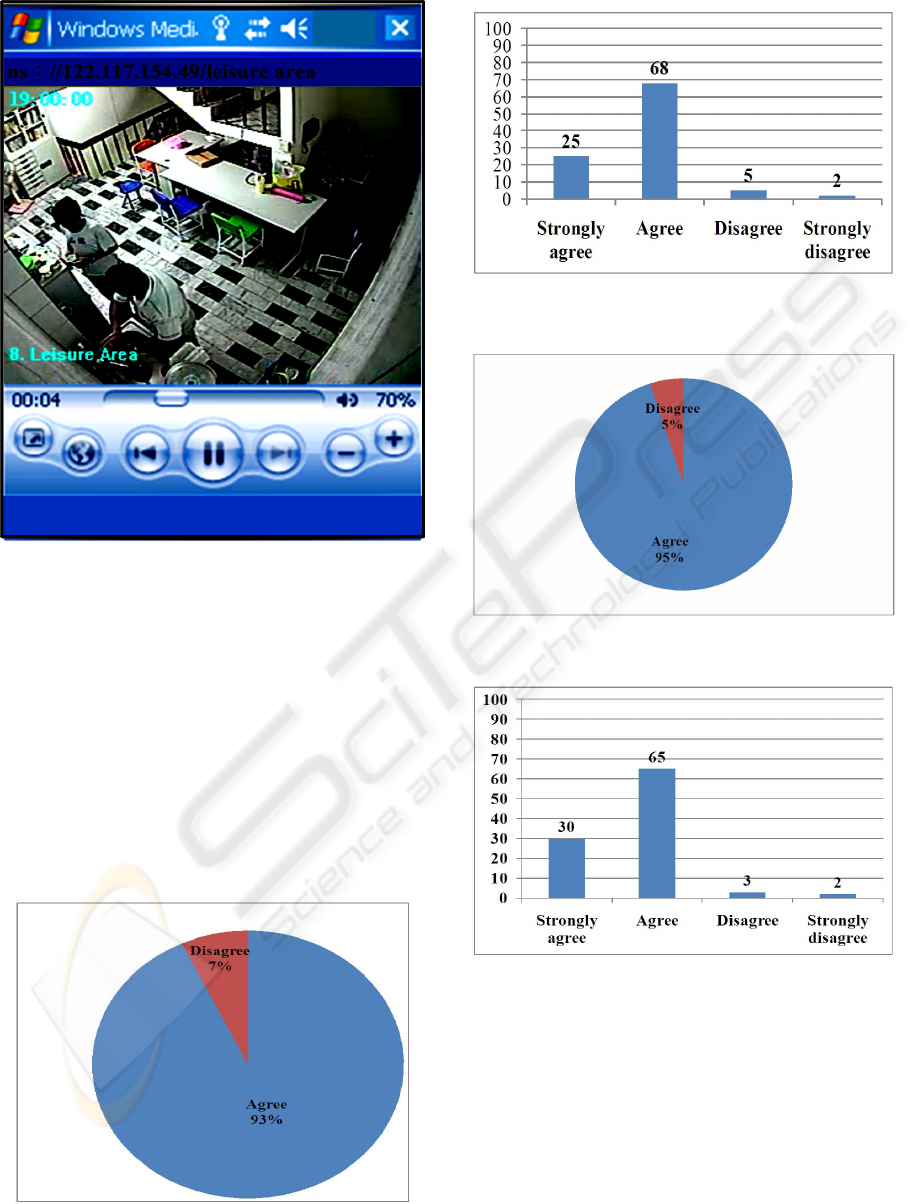
Figure 8: Searching Results.
4.2 Discussion
In this study, we select 100 paterfamiliases to test
this system and software. It is revealed that 74% of
the paterfamilias are satisfied with the system
(Strongly agree:25/100; Agree:68/100; Disagree:
5/100; Strongly disagree:2/100), see as Figure 9
and Figure 10.
The software searching correctness is 95%
(Strongly agree : 30/100; Agree : 65/100;
Disagree:3/100; Strongly disagree:2/100), see as
Figure 11 and Figure 12.
Figure 9: Satisfaction and Dissatisfaction.
Figure 10: Detail of satisfaction and dissatisfaction.
Figure 11: Software searching correctness.
Figure 12: Detail of software searching correctness.
5 CONCLUSIONS
This study aims to developed safety system, and let
the system become intelligent. This study used
artificial intelligence and active Ultra-High
Frequency RFID directly to guide paterfamilias
monitoring their children’s in-time images. Thus, it
could save the paterfamilias’ time on operating the
ICE-B 2010 - International Conference on e-Business
60

instrument. Even someone who has not the
professional knowledge about information
technology could use them skillfully. This study
also develops friendly human computer interface
software for users use the personal digital assistants.
The size of the software is 22 kilobits; therefore, the
software is not a liability for the users’ tools. This
study has successfully implemented to one
educational organization, and it would be helpful for
the paterfamiliases to hold all situations about their
children at the educational organization. That will
be great help in the grip of whole after-school
remedial education, teaching and learning situation.
ACKNOWLEDGEMENTS
This research is sponsored by Chin-Huo educational
organization. This is gratefully acknowledged.
REFERENCES
Abad, E., Palacio, F., Nuin, M., Zárate, A. G., Juarros,
A., Gómez, J. M., & Marco, S. (2009). RFID smart
tag for traceability and cold chain monitoring of
foods: Demonstration in an intercontinental fresh
fish logistic chain. Journal of Food Engineering, 93
(4), 394-399.
Allahverdi, A., & Al-Anzi, F. S. (2008). The two-stage
assembly flowshop scheduling problem with
bicriteria of makespan and mean completion time.
International Journal of Advanced Manufacturing
Technology, 37 (1-2), 166-177.
Angeles, R. (2009). Anticipated IT infrastructure and
supply chain integration capabilities for RFID and
their associated deployment outcomes. International
Journal of Information Management, 29 (3),
219-231.
Barco, R., Lázaro, P., Díez, L., & Wille, V. (2008).
Continuous versus discrete model in autodiagnosis
systems for wireless networks. IEEE Transactions
on Mobile Computing, 7 (6), 673-681.
Birattari, M., Pellegrini, P., & Dorigo, M. (2007). On the
invariance of ant colony optimization. IEEE
Transactions on Evolutionary Computation, 11 (6),
732-742.
Broekmeulen, R. A. C. M & Donselaar, K. H. V. (2009).
A heuristic to manage perishable inventory with
batch ordering, positive lead-times, and
time-varying demand. Computers & Operations
Research, 36 (11) , 3013-3018.
Chen, K., & Liu, L. (2006). iVIBRATE: Interactive
visualization-based framework for clustering large
datasets. ACM Transactions on Information Systems
(TOIS), 24 (2), 245-294.
Chen, L. S. (2008). Design and implementation of
intelligent library system. Library Collections,
Acquisitions, and Technical Services, 32 (3-4),
127-141.
Chen, L. S. (2009). Design and implementation of
intelligent mobile information system for campus
safety management. International Journal of
Organizational Innovation, 2, 320-340.
Chen, L. S. (2010). Applying swarm intelligence to a
library system. Library Collections, Acquisitions,
and Technical Services, 34 (1), 1-10.
Chen, L. S., & Chen, S. L. (2007). Collaborative Design
and Manufacture on Intelligent System. Journal of
the Chinese Society of Mechanical Engineers, 28(2),
233-242.
Delgado, M., Ros, M., & Vila, M. A. (2009). Correct
behavior identification system in a Tagged World.
Expert Systems with Applications, 36 (6),
9899-9906.
Fan, X., Wang, R., Sun, S., & Yen, J. (2006).
Context-Centric Needs Anticipation Using
Information Needs Graphs. Applied Intelligence,
24(1), 75–89.
Felfernig, A., Friedrich, G., Isak, K., Shchekotykhin, K.,
Teppan, E., & Jannach, D, (2009), Automated
debugging of recommender user interface
descriptions. Applied Intelligence, 31(1), 1–14.
Gao, B., & Zhang, W. (2008). Equilibria and their
bifurcations in a recurrent neural network involving
iterates of a transcendental function. IEEE
Transactions on Neural Networks, 19 (5), 782-794.
Hyowon, L., Alan, F. S., Noel, E. O’., & Barry, S.
(2006). User evaluation of Físchlár-News: An
automatic broadcast news delivery system. ACM
Transactions on Information Systems (TOIS), 24 (2),
145-189.
Jannach, D., Leopold, K., Timmerer, C., & Hellwagner,
C. H. (2006). A knowledge-based framework for
multimedia adaptation. Applied Intelligence, 24 (2),
109–125.
Justin, Z., & Timothy, C. H. (2006). Detection of video
sequences using compact signatures. ACM
Transactions on Information Systems (TOIS), 24 (1),
1-50.
Kaikhah, K., & Doddament, S. (2006). Discovering
Trends in Large Datasets Using Neural Networks.
Applied Intelligence, 24 (1), 51-60.
Ku, W. S., Zimmermann, R., & Wang, H. (2008).
Location-based spatial query processing with data
sharing in wireless broadcast environments. IEEE
Transactions on Mobile Computing, 7 (6), 778-791.
Lee, C. K. M., & Chan, T. M. (2009). Development of
RFID-based Reverse Logistics System. Expert
Systems with Applications, 36 (5), 9299-9307.
Lee, C. S., & Wang, M. H. (2009). Ontology-based
computational intelligent multi-agent and its
application to CMMI assessment. Applied
Intelligence, 30( 3), 203–219.
Leonardi, P. M., & Bailey, D. E. (2008).
Transformational Technologies and The Creation of
INTELLIGENT MOBILE SAFETY SYSTEM TO EDUCATIONAL ORGANIZATION
61

New Work Practices :Making Implicit Knowledge
Explicit in Task-Based Offshoring. MIS Quarterly,
32 (2), 411-436.
Li, L., Cai, Y., & Xu, X. (2007). Spanning-tree based
autoconfiguration for mobile ad hoc networks.
Wireless Personal Communications, 43 (4),
1465-1477.
Malek, M. R., & Frank, A. U. (2006). A mobile
computing approach for navigation purposes web
and wireless geographical information systems.
Lecture Notes in Computer Science 4295, 123-134.
Masip, D., & Vitria, J. (2008). Shared feature extraction
for nearest neighbor face recognition. IEEE
Transactions on Neural Networks, 19 (4) , 586-595.
Pavlou, P. A., Huigang, L., & Yajiong, X. (2007).
Understanding and mitigating uncertainty in online
exchange relationships: A principal—agent
perspective. MIS Quarterly, 31 (1), 105-136.
Payne, T. R. (2008). Web services from an agent
perspective. IEEE Intelligent Systems, 23 (2),
12-14.
Wang, H. Y., & Chen, S. M. (2008). Evaluating
students’ answerscripts using vague value. Applied
Intelligence, 28 (2), 183–193.
Storey, V. C., Jones, A. B., Sugumaran, V., & Purao. S.
(2008). A methodology for context-aware query
processing on the World Wide Web. Information
Systems Research, 19 (1), 3-25.
Su, Y. S., Su, S. L., & Li, J. S. (2008).
Topology-independent link activation scheduling
schemes for mobile CDMA ad hoc networks. IEEE
Transactions on Mobile Computing, 7 (5), 599-616.
Yap, G. E., Tan, A. H., & Pang, H. H. (2008). Explaining
inferences in Bayesian networks. Applied
Intelligence, 29(3), 263–278.
Zhou, W. (2009). RFID and item-level information
visibility. European Journal of Operational
Research , 198 (1), 252-258
ICE-B 2010 - International Conference on e-Business
62
